Networking Technologies Report: BTEC HND Computing, Unit 24
VerifiedAdded on 2020/06/04
|40
|9127
|81
Report
AI Summary
This report provides a comprehensive overview of networking technologies, addressing various aspects from fundamental concepts to practical implementation and maintenance. The report begins with an introduction to networking, defining its purpose and benefits, particularly in the context of a telecommunication company, Beta Communication Ltd. It explores different types of networks, including LAN, MAN, WAN, peer-based systems, and client-server systems, highlighting their advantages and disadvantages. The report then delves into the impact of current network technologies, such as FTP, SMTP, HTTP, IPV4, IPV6, and Ethernet, on a business. The report also covers the role of software and hardware components, server types, and workstation hardware interdependence. Furthermore, it details the design, implementation, testing, and documentation of a network system using simulation software, including testing functionalities and documenting results. Finally, the report concludes with recommendations for network enhancements and designs a maintenance schedule to support the networked system. The document aims to provide a practical understanding of networking technologies and their application in real-world scenarios.

Unit 24: Networking
Technologies
Technologies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Benefits of networking technologies and networking systems .......................................1
1.2 Impact of current network technologies .........................................................................5
1.3 Effective utilization of different networking system using protocols..............................8
M 1.................................................................................................................................................11
TASK 2..........................................................................................................................................11
2.1 Role of software and hardware components..................................................................11
2.2 Types of servers .............................................................................................................14
2.3 Interdependence of workstation hardware......................................................................15
M 2.................................................................................................................................................16
TASK 3.........................................................................................................................................18
TASK 4.........................................................................................................................................25
4.1 – Implement a network systems based on the proposed design. You are required to use me
ans of simulation software, establish a network according to the design in task 3..............25
4.2. Test network systems to meet user requirements. Your testing includes functionality of th
e network to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements........................................................................30
4.3. Document and analyse test result against expected results. While carrying out task 4.2, th
e testing of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.........................................................33
4.4. Recommend potential enhancement for the networked systems. Your discussions should i
nclude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment. 34
4.5. Design a maintenance schedule to support the network system. Your maintenance schedul
e should address various factors likepersonnel allocation, backup and recovery policy, maintai
ning security & integrity; and general administration to support the users..........................35
CONCLUSION..............................................................................................................................36
REFERENCES..............................................................................................................................37
INTRODUCTION...........................................................................................................................1
TASK 1............................................................................................................................................1
1.1 Benefits of networking technologies and networking systems .......................................1
1.2 Impact of current network technologies .........................................................................5
1.3 Effective utilization of different networking system using protocols..............................8
M 1.................................................................................................................................................11
TASK 2..........................................................................................................................................11
2.1 Role of software and hardware components..................................................................11
2.2 Types of servers .............................................................................................................14
2.3 Interdependence of workstation hardware......................................................................15
M 2.................................................................................................................................................16
TASK 3.........................................................................................................................................18
TASK 4.........................................................................................................................................25
4.1 – Implement a network systems based on the proposed design. You are required to use me
ans of simulation software, establish a network according to the design in task 3..............25
4.2. Test network systems to meet user requirements. Your testing includes functionality of th
e network to ensure that your developed network will operate seamlessly in a physical environ
ment so that it can satisfy user requirements........................................................................30
4.3. Document and analyse test result against expected results. While carrying out task 4.2, th
e testing of the network has produced a number of results. List the results you have found in ta
sk 4.2 by contrasting them with your expected results.........................................................33
4.4. Recommend potential enhancement for the networked systems. Your discussions should i
nclude how your developed network will cope with future changing needs and should address
possible enhancements of your network to satisfy needs of changing future environment. 34
4.5. Design a maintenance schedule to support the network system. Your maintenance schedul
e should address various factors likepersonnel allocation, backup and recovery policy, maintai
ning security & integrity; and general administration to support the users..........................35
CONCLUSION..............................................................................................................................36
REFERENCES..............................................................................................................................37

INTRODUCTION
Network is defined as connection of computers with an objective to share resources,
Process of exchanging information and data between systems is called networking technology.
Networking is defined as the structuring and making of network system by using cables and
bridges. It is used to manage network and telecommunication process of organisations. It plays
an important role in providing platform for communication purposes. It helps in connecting
people in by removing geographical limits. An important platform for networking technology is
internet.
Present report describes about benefits and constraints of various system of networking
and its types. Effect of current technology of network has been discussed in the report.
Furthermore, effective utilization of network is also explained. Role of software and hardware
elements and their applications has been illustrated. Types of servers and their selection ned in
company has been discussed. More over, inter dependence of workstation hardware with
network is also illustrated in the report.
TASK 1
1.1 Benefits of networking technologies and networking systems
According to the case study Beta communication Ltd is a telecommunication company.
The organisation was using stand alone PCs and dial up approach for their networking purposes.
Now the company is planing to build their own local are network system. Purpose of network in
the company to share their resources and information effectively (PSN .2017). There is major
role and benefits of networks in information sharing of the organisation. Some benefits of
network technology is as follows:
Sharing of information becomes easy by making us of networking technology in
organisation.
Networking systems makes it easy for sharing files and data remotely to different
connected computers (Brandwine and Hill, 2014).
Use of internal connected devices like printers and copiers helps in resource sharing.
In networking single internet link is share among PC's that helps in protecting system of
the organisation from hacking.
Network is defined as connection of computers with an objective to share resources,
Process of exchanging information and data between systems is called networking technology.
Networking is defined as the structuring and making of network system by using cables and
bridges. It is used to manage network and telecommunication process of organisations. It plays
an important role in providing platform for communication purposes. It helps in connecting
people in by removing geographical limits. An important platform for networking technology is
internet.
Present report describes about benefits and constraints of various system of networking
and its types. Effect of current technology of network has been discussed in the report.
Furthermore, effective utilization of network is also explained. Role of software and hardware
elements and their applications has been illustrated. Types of servers and their selection ned in
company has been discussed. More over, inter dependence of workstation hardware with
network is also illustrated in the report.
TASK 1
1.1 Benefits of networking technologies and networking systems
According to the case study Beta communication Ltd is a telecommunication company.
The organisation was using stand alone PCs and dial up approach for their networking purposes.
Now the company is planing to build their own local are network system. Purpose of network in
the company to share their resources and information effectively (PSN .2017). There is major
role and benefits of networks in information sharing of the organisation. Some benefits of
network technology is as follows:
Sharing of information becomes easy by making us of networking technology in
organisation.
Networking systems makes it easy for sharing files and data remotely to different
connected computers (Brandwine and Hill, 2014).
Use of internal connected devices like printers and copiers helps in resource sharing.
In networking single internet link is share among PC's that helps in protecting system of
the organisation from hacking.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Storage capacity of network connected devices gets increased.
Communication with suppliers and consumers of the company will also improve by
using networking systems.
Business of the organisation will become more efficient by using common database
which helps in avoiding data repetition
Centralized network supports in less requirement of IT.
There are four types networking system which have various benefits :
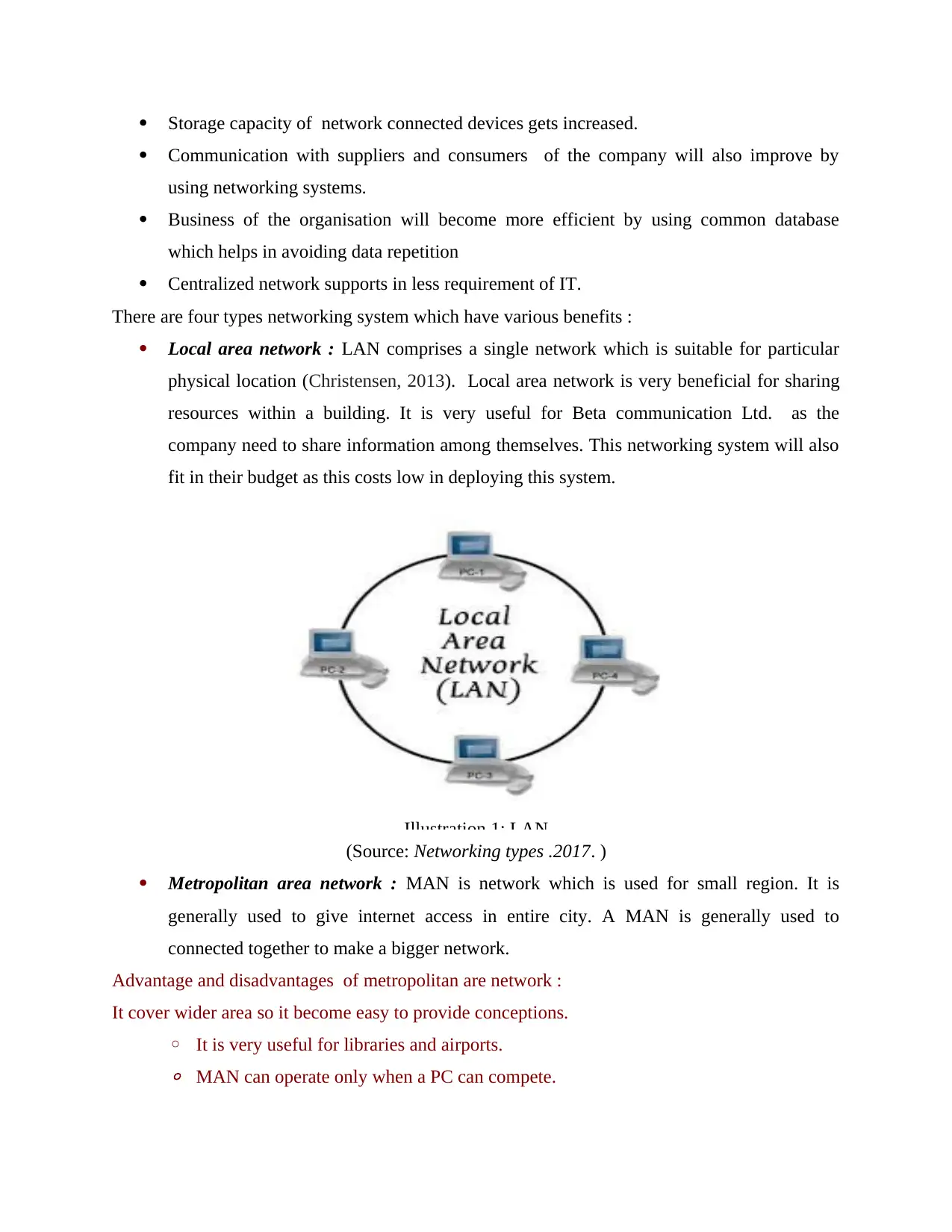
Local area network : LAN comprises a single network which is suitable for particular
physical location (Christensen, 2013). Local area network is very beneficial for sharing
resources within a building. It is very useful for Beta communication Ltd. as the
company need to share information among themselves. This networking system will also
fit in their budget as this costs low in deploying this system.
(Source: Networking types .2017. )
Metropolitan area network : MAN is network which is used for small region. It is
generally used to give internet access in entire city. A MAN is generally used to
connected together to make a bigger network.
Advantage and disadvantages of metropolitan are network :
It cover wider area so it become easy to provide conceptions.
◦ It is very useful for libraries and airports.
◦ MAN can operate only when a PC can compete.
Illustration 1: LAN
Communication with suppliers and consumers of the company will also improve by
using networking systems.
Business of the organisation will become more efficient by using common database
which helps in avoiding data repetition
Centralized network supports in less requirement of IT.
There are four types networking system which have various benefits :
Local area network : LAN comprises a single network which is suitable for particular
physical location (Christensen, 2013). Local area network is very beneficial for sharing
resources within a building. It is very useful for Beta communication Ltd. as the
company need to share information among themselves. This networking system will also
fit in their budget as this costs low in deploying this system.
(Source: Networking types .2017. )
Metropolitan area network : MAN is network which is used for small region. It is
generally used to give internet access in entire city. A MAN is generally used to
connected together to make a bigger network.
Advantage and disadvantages of metropolitan are network :
It cover wider area so it become easy to provide conceptions.
◦ It is very useful for libraries and airports.
◦ MAN can operate only when a PC can compete.
Illustration 1: LAN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wide area network : WAN is used to connect large area like whole country of region. It
contains various small networks like ;local and metropolitan area networks.
Advantages and disadvantages of WAN
WAN contains centralized IT structure due to which it eliminates the requirement of
buying servers.
Privacy level of the business information get increases using WAN.
It cost very high to setup WAN's.
Issue of maintenance is also there with WAN's Security breach problem is also with wide are networks.
Peer based network systems : in peer based network system two or more personal
computers are linked to share resources and information. Single universal bus is used to
connect PC's to transfer files. It can be used by Beta communication Ltd.
Advantages: It is easy to install per based networking systems. P2P is reliable networks
systems. Full time administrator is not required in this.
Disadvantage: In this system its becomes difficult to determine who is accessing the network.
Data backup is also difficult in this systems.
Client server based systems : It is made for end user who are termed as clients. These
clients can access information like files, documents and videos form the central computer
device which is called server (Da, He and Li, S., 2014). Cloud and clusters : In cloud computing file and data is saved on cloud system rather
than hard drive of computer. In clustering method two computers are linked in away so
that they can represent a single computer. It help in parallel processing. It is also
beneficial for the organisation.
Networking topologies: Networking topologies is an appropriate arrangement of networks I
order to connect different nodes. These are ring topology, start topology , mesh topology and bus
topology. In star topology nodes are connected in structure like star.
Ring topologies
contains various small networks like ;local and metropolitan area networks.
Advantages and disadvantages of WAN
WAN contains centralized IT structure due to which it eliminates the requirement of
buying servers.
Privacy level of the business information get increases using WAN.
It cost very high to setup WAN's.
Issue of maintenance is also there with WAN's Security breach problem is also with wide are networks.
Peer based network systems : in peer based network system two or more personal
computers are linked to share resources and information. Single universal bus is used to
connect PC's to transfer files. It can be used by Beta communication Ltd.
Advantages: It is easy to install per based networking systems. P2P is reliable networks
systems. Full time administrator is not required in this.
Disadvantage: In this system its becomes difficult to determine who is accessing the network.
Data backup is also difficult in this systems.
Client server based systems : It is made for end user who are termed as clients. These
clients can access information like files, documents and videos form the central computer
device which is called server (Da, He and Li, S., 2014). Cloud and clusters : In cloud computing file and data is saved on cloud system rather
than hard drive of computer. In clustering method two computers are linked in away so
that they can represent a single computer. It help in parallel processing. It is also
beneficial for the organisation.
Networking topologies: Networking topologies is an appropriate arrangement of networks I
order to connect different nodes. These are ring topology, start topology , mesh topology and bus
topology. In star topology nodes are connected in structure like star.
Ring topologies
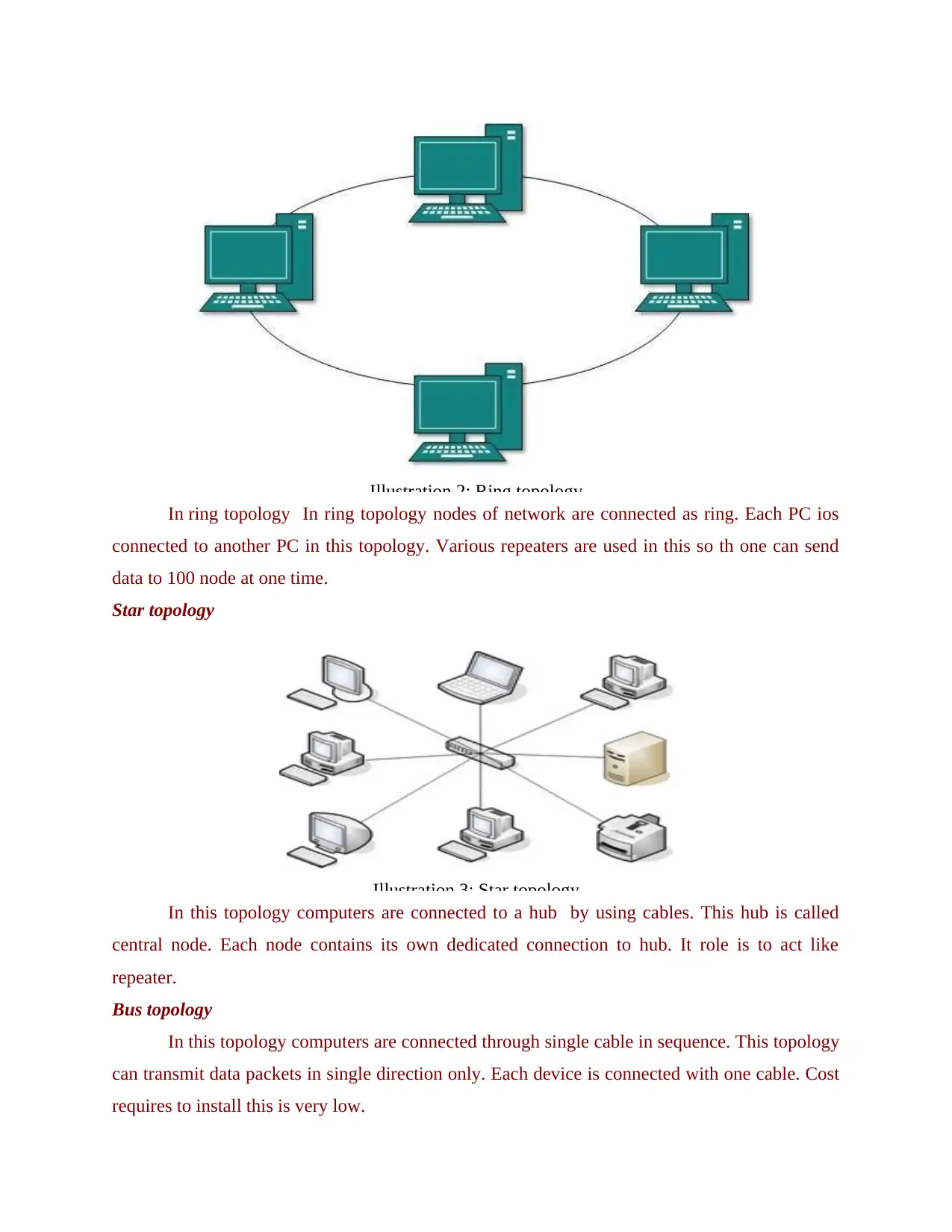
In ring topology In ring topology nodes of network are connected as ring. Each PC ios
connected to another PC in this topology. Various repeaters are used in this so th one can send
data to 100 node at one time.
Star topology
In this topology computers are connected to a hub by using cables. This hub is called
central node. Each node contains its own dedicated connection to hub. It role is to act like
repeater.
Bus topology
In this topology computers are connected through single cable in sequence. This topology
can transmit data packets in single direction only. Each device is connected with one cable. Cost
requires to install this is very low.
Illustration 3: Star topology
Illustration 2: Ring topology
connected to another PC in this topology. Various repeaters are used in this so th one can send
data to 100 node at one time.
Star topology
In this topology computers are connected to a hub by using cables. This hub is called
central node. Each node contains its own dedicated connection to hub. It role is to act like
repeater.
Bus topology
In this topology computers are connected through single cable in sequence. This topology
can transmit data packets in single direction only. Each device is connected with one cable. Cost
requires to install this is very low.
Illustration 3: Star topology
Illustration 2: Ring topology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Requirements for the organisation to install network
Beta communication Ltd. requires to analyse its communication methods, reporting hierarchy,
structure of the organisation. Local administrative rules and policies are need to be considered.
Further company will require Ethernet cables, modem, routers, switches, hubs repeaters etc to
install a network. Type of files and applications that need to be run on network should be
identified. Requirements for organisation to install a network are as follows:
Company should consider purpose of the network .Organisation requires networking variables
and maintenance of network. Company needs to understand physical networks and information
of active directory. Network structure of the area need to understand.
1.2 Impact of current network technologies
There is a huge impact of current network technologies on Beta communication Ltd.
Current network technologies an there effects are as follows:
File transfer protocol (FTP)
This protocol is a standard protocol which is used to transfer information and data form
one server to another one. It is a popular protocol which for upload and download process of
flies. This protocol uses TCP/ IP protocol for enabling transfer of data. In this client server
model is used to which is protected with SSL/ TLS. This enables file sharing through remote
computers. Data is transferred deficiently in this protocol. It provides authentication to user by
simple sign in protocol (Gubbi and et.al, 2013). Username and password are required by client
for authentication process. The FTP totally depends on client and server. It works in two mode
which are passive and active. In the active state client start initiating a session by sending a
command. This command is received by server and after that it make connection to client for
Illustration 4: Bus topology
Beta communication Ltd. requires to analyse its communication methods, reporting hierarchy,
structure of the organisation. Local administrative rules and policies are need to be considered.
Further company will require Ethernet cables, modem, routers, switches, hubs repeaters etc to
install a network. Type of files and applications that need to be run on network should be
identified. Requirements for organisation to install a network are as follows:
Company should consider purpose of the network .Organisation requires networking variables
and maintenance of network. Company needs to understand physical networks and information
of active directory. Network structure of the area need to understand.
1.2 Impact of current network technologies
There is a huge impact of current network technologies on Beta communication Ltd.
Current network technologies an there effects are as follows:
File transfer protocol (FTP)
This protocol is a standard protocol which is used to transfer information and data form
one server to another one. It is a popular protocol which for upload and download process of
flies. This protocol uses TCP/ IP protocol for enabling transfer of data. In this client server
model is used to which is protected with SSL/ TLS. This enables file sharing through remote
computers. Data is transferred deficiently in this protocol. It provides authentication to user by
simple sign in protocol (Gubbi and et.al, 2013). Username and password are required by client
for authentication process. The FTP totally depends on client and server. It works in two mode
which are passive and active. In the active state client start initiating a session by sending a
command. This command is received by server and after that it make connection to client for
Illustration 4: Bus topology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

enabling data transfer. This protocol can be used by Beta communication Ltd. for efficient and
secure transfer of data.
Simple mail transfer protocol (SMTP)
It is an standard protocol which is used for email transferring services. This protocol also
uses TCP/IP protocol to enable file transferring. It is used to upload mail directly on networks.
Simple mail transfer protocol use POP 3 service. It is an application layer model which helps in
enabling transmission of emails over internet. It is popular model which is used for
communication via email. In SMTP there are four types of keys which is use between client and
server. These keys are Mail user agent, mail submission agent , mail transfer agent and agent for
mail delivery.
Hyper text transfer protocol (HTTP)
It is a protocol in which particular set of rules are defined for transferring files. This
protocol support in transferring files such as sound, text, video and various type of multimedia
files. File are transferred on the World Wide Web. Users use HTTP whenever they open web
browser on their computers. It is an application protocol whose functioning totally depends on
TCP/IP suite. Hypertext is used in this protocol which gives references to various files which are
result of user request on browser (Istepanian, Laxminarayan and Pattichis, 2014).
IPV4
IPV4 is a fourth version of internet protocol. It is used widely data communication on
various type of networks (Jain and Paul, 2013). It is connection less protocol which is sued in
Ethernet services. Logical connection is provided by IPV4 for device identification. This
protocol is configured using no automatic and automatic configurations. These configurations
depends on the type of network. This protocol do not provides guarantee of duplicate data.
IPV6
This protocol is 6th version of internet protocol. It is used to fulfil the requirements of
more addresses for internet (Kim, and et.al 2014). This protocol overcomes the bugs of previous
version i.e. IPV4. This protocol do not requires manual configuration because it is an auto
configured protocol. It provides better masticasting. It has inbuilt authentication support. Header
format is simpler that that of IPV4. Thus internet protocol should be used while designing
network system for beta communication Ltd.
Ethernet
secure transfer of data.
Simple mail transfer protocol (SMTP)
It is an standard protocol which is used for email transferring services. This protocol also
uses TCP/IP protocol to enable file transferring. It is used to upload mail directly on networks.
Simple mail transfer protocol use POP 3 service. It is an application layer model which helps in
enabling transmission of emails over internet. It is popular model which is used for
communication via email. In SMTP there are four types of keys which is use between client and
server. These keys are Mail user agent, mail submission agent , mail transfer agent and agent for
mail delivery.
Hyper text transfer protocol (HTTP)
It is a protocol in which particular set of rules are defined for transferring files. This
protocol support in transferring files such as sound, text, video and various type of multimedia
files. File are transferred on the World Wide Web. Users use HTTP whenever they open web
browser on their computers. It is an application protocol whose functioning totally depends on
TCP/IP suite. Hypertext is used in this protocol which gives references to various files which are
result of user request on browser (Istepanian, Laxminarayan and Pattichis, 2014).
IPV4
IPV4 is a fourth version of internet protocol. It is used widely data communication on
various type of networks (Jain and Paul, 2013). It is connection less protocol which is sued in
Ethernet services. Logical connection is provided by IPV4 for device identification. This
protocol is configured using no automatic and automatic configurations. These configurations
depends on the type of network. This protocol do not provides guarantee of duplicate data.
IPV6
This protocol is 6th version of internet protocol. It is used to fulfil the requirements of
more addresses for internet (Kim, and et.al 2014). This protocol overcomes the bugs of previous
version i.e. IPV4. This protocol do not requires manual configuration because it is an auto
configured protocol. It provides better masticasting. It has inbuilt authentication support. Header
format is simpler that that of IPV4. Thus internet protocol should be used while designing
network system for beta communication Ltd.
Ethernet
Ether net is used widely to install LAN. It is a physical layer technology which is used to
connect LAN to computers. It is attached with both layers physical and data link in OSI model. It
describes two aspect of transmission that are data packet and frame. Each frame is covered by
data packet. It allows data seeped of 10 Mbps and at base T Ethernet and 100 Mbps at fats
Ethernet an 1000 Mbps at Gigabit Ethernet. Ethernet contains two layers which are physical and
data link layer. The frame in Ethernet involves payload of data with addressing information by
determining the MAC address. The address is send to bot sender and receiver.
Illustration 5: TCP/IP model
connect LAN to computers. It is attached with both layers physical and data link in OSI model. It
describes two aspect of transmission that are data packet and frame. Each frame is covered by
data packet. It allows data seeped of 10 Mbps and at base T Ethernet and 100 Mbps at fats
Ethernet an 1000 Mbps at Gigabit Ethernet. Ethernet contains two layers which are physical and
data link layer. The frame in Ethernet involves payload of data with addressing information by
determining the MAC address. The address is send to bot sender and receiver.
Illustration 5: TCP/IP model
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Token ring
It is also a type of LAN and in this structure PC's are connected in ring or star network
topology. All computers in the token ring are connected in shape of circle. For sending a
message computer gets a token and the message is attached to it. This message continuously
moves close to the network.
FDDI
It is fibre distributed data interface. It transmits data over the fibre optic cable. These
networks are also called token passing. Data rate up to 100 MBPS is provided by this network. It
incorporates two token rings form which one is for backup. It is used for interconnection of local
are networks. FDDI is based on token ring protocol. In addition to that this data interface
supports number of users at one time. FDDI is also called backbone of wide area network. This
interface consist of two token rings form which one is for use and one is for backup. It adds
capability to circuit switched network.
1.3 Effective utilization of different networking system using protocols
Networks protocols are used to ensure appropriate utilization of networks. There are
various model used to ensure proper use of networks. Some models are as follows:
OSI model
OSI model is an open system interconnection model which consist of 7 layers. This
model represents communication of application over network. It is used to ensure data
communication world wide (Leonardi, Huysman and Steinfield, 2013). It describes that systems
should be made which are able to communicate with one another. It also ensures compatibility of
systems. This model works on seven layers which are as follows: Physical layer : It is the lower most layer of the model. Role of this layer to establish
and deactivate physical connections. This layer is responsible for transmitting data over
the network. Analog signals are converted into digital signals in this layer. Encoding of
data is done in this layer.
Data link layer: This layer role is to synchronize the data which is to be transferred to
physical layer. Major role of this layer to transfer data without errors. Data frames are
It is also a type of LAN and in this structure PC's are connected in ring or star network
topology. All computers in the token ring are connected in shape of circle. For sending a
message computer gets a token and the message is attached to it. This message continuously
moves close to the network.
FDDI
It is fibre distributed data interface. It transmits data over the fibre optic cable. These
networks are also called token passing. Data rate up to 100 MBPS is provided by this network. It
incorporates two token rings form which one is for backup. It is used for interconnection of local
are networks. FDDI is based on token ring protocol. In addition to that this data interface
supports number of users at one time. FDDI is also called backbone of wide area network. This
interface consist of two token rings form which one is for use and one is for backup. It adds
capability to circuit switched network.
1.3 Effective utilization of different networking system using protocols
Networks protocols are used to ensure appropriate utilization of networks. There are
various model used to ensure proper use of networks. Some models are as follows:
OSI model
OSI model is an open system interconnection model which consist of 7 layers. This
model represents communication of application over network. It is used to ensure data
communication world wide (Leonardi, Huysman and Steinfield, 2013). It describes that systems
should be made which are able to communicate with one another. It also ensures compatibility of
systems. This model works on seven layers which are as follows: Physical layer : It is the lower most layer of the model. Role of this layer to establish
and deactivate physical connections. This layer is responsible for transmitting data over
the network. Analog signals are converted into digital signals in this layer. Encoding of
data is done in this layer.
Data link layer: This layer role is to synchronize the data which is to be transferred to
physical layer. Major role of this layer to transfer data without errors. Data frames are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

transmitted and received over this layer. Logical layer is made by this layer for managing
frame traffic on the network.
(Source: OSI .2017 ) Network layer: This layer is used to route the signal via different channels form one link
to the other. The layer is responsible for controlling network and subnet traffic. It is used
to decide the route of data (Suthaharan, 2014.). Transport payer: This layer is used to decide path of transmission of data. This layer is
responsible for doing Multiplexing and segmenting of data. Messages are received by
this layer from the session layer. It convert message into packets. These packet are passed
to the network layer. Session layer: This layer is responsible for managing conversation which takes place
between two distinct applications. The mail responsibility of this layer is to avoid data
losses over the networks (Christensen, 2013). Presentation layer: Role of this layer is to make data understandable and usable. This
layer converts data for the layer below it which is application layer. Compression,
encryption and conversion of data is done by this layer.
Illustration 6: OSI model
frame traffic on the network.
(Source: OSI .2017 ) Network layer: This layer is used to route the signal via different channels form one link
to the other. The layer is responsible for controlling network and subnet traffic. It is used
to decide the route of data (Suthaharan, 2014.). Transport payer: This layer is used to decide path of transmission of data. This layer is
responsible for doing Multiplexing and segmenting of data. Messages are received by
this layer from the session layer. It convert message into packets. These packet are passed
to the network layer. Session layer: This layer is responsible for managing conversation which takes place
between two distinct applications. The mail responsibility of this layer is to avoid data
losses over the networks (Christensen, 2013). Presentation layer: Role of this layer is to make data understandable and usable. This
layer converts data for the layer below it which is application layer. Compression,
encryption and conversion of data is done by this layer.
Illustration 6: OSI model

Application layer: This layer is at the topmost of the 7 layer architecture. This layer role
is to contain and control application programs.
TCP/ IP model for communication standard is as follows:
The model is 4 layer architecture model and it means transmission control protocol and internet
protocol. Layers of the model is as follows:
Layer 1 : Host to network layer
It is the lowest layer of the model and it is used to connect host for transmission of data
packets over it. This layers varies form host to host and network to network.
Layer 2: Internet layer
This layer is responsible for holding the entire architecture. It supports data packets to
travel from one destination to another. This layer uses internet protocol.
Layer 3: Transport layer
This layer's role is to determine path of data transmission. Multiplexing, segmenting and
data splitting is done in this layer. This layer adds header to the data packet.
Layer 4: Application layer
This layer allows flexibility to data for accessing other applications such as HTTP, FTP,
SMTP etc.
DHCP: It is dynamic host control protocol. It is used to provide fast and automatic access for
distributing IP address within the network. It is used to assign unique IP address to each device
on TCP/IP model. IP addressed of computers moved form one subnet to another. With the help
of DHCP whole process for assigning IP addresses is done automatically. When device on TCP/
IP is turned on and linked to a network then DHCP server sends request to server which is called
DHCP DISCOVER.
DNS: It Is the by which internet domains names are allocated and translated into IP's. It is a
hierarchical framework fro computer and other resources. Names to system are provided by
using worldwide directory service.
Routing protocols
Routing protocols describes communication of routers with each other. . A routing
protocol shares this messages first among close neighbours, and then end-to-end the
communication system. In this way , routers increase cognition of the topology of the
is to contain and control application programs.
TCP/ IP model for communication standard is as follows:
The model is 4 layer architecture model and it means transmission control protocol and internet
protocol. Layers of the model is as follows:
Layer 1 : Host to network layer
It is the lowest layer of the model and it is used to connect host for transmission of data
packets over it. This layers varies form host to host and network to network.
Layer 2: Internet layer
This layer is responsible for holding the entire architecture. It supports data packets to
travel from one destination to another. This layer uses internet protocol.
Layer 3: Transport layer
This layer's role is to determine path of data transmission. Multiplexing, segmenting and
data splitting is done in this layer. This layer adds header to the data packet.
Layer 4: Application layer
This layer allows flexibility to data for accessing other applications such as HTTP, FTP,
SMTP etc.
DHCP: It is dynamic host control protocol. It is used to provide fast and automatic access for
distributing IP address within the network. It is used to assign unique IP address to each device
on TCP/IP model. IP addressed of computers moved form one subnet to another. With the help
of DHCP whole process for assigning IP addresses is done automatically. When device on TCP/
IP is turned on and linked to a network then DHCP server sends request to server which is called
DHCP DISCOVER.
DNS: It Is the by which internet domains names are allocated and translated into IP's. It is a
hierarchical framework fro computer and other resources. Names to system are provided by
using worldwide directory service.
Routing protocols
Routing protocols describes communication of routers with each other. . A routing
protocol shares this messages first among close neighbours, and then end-to-end the
communication system. In this way , routers increase cognition of the topology of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 40
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





