Cybersecurity/HIPAA Audit Report: Newark Memorial Hospital Project
VerifiedAdded on 2019/09/23
|7
|504
|93
Report
AI Summary
This report presents a comprehensive cybersecurity and HIPAA audit plan for a healthcare project, specifically at Newark Memorial Hospital. The report outlines the project's structure, including roles and responsibilities, as well as the organizational chart. It details staffing management, including the acquisition and training of personnel, to ensure effective project execution. The document also includes a RACI chart, which clarifies the responsibilities of each team member. Finally, the report includes sections for approvals and acceptance, signifying the completion and validation of the project plan. This report is a valuable resource for understanding the key components of managing a cybersecurity and HIPAA compliance project within a healthcare setting.

Human Resource Management Plan
[Newark Memorial Hospital]
CYBERSECURITY/HIPAA SECURITY
AUDIT]
9/2/2016
[Newark Memorial Hospital]
CYBERSECURITY/HIPAA SECURITY
AUDIT]
9/2/2016
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
TABLE OF CONTENTS
REVISIONS........................................................................................................................................1
INTRODUCTION.................................................................................................................................2
ROLES AND RESPONSIBILITIES.........................................................................................................2
PROJECT ORGANIZATIONAL CHARTS...............................................................................................2
STAFFING MANAGEMENT.................................................................................................................4
PROJECT TEAM TRAINING................................................................................................................5
ACCEPTANCE....................................................................................................................................5
CYBERSECURITY/HIPAA SECURITY AUDIT]
TABLE OF CONTENTS
REVISIONS........................................................................................................................................1
INTRODUCTION.................................................................................................................................2
ROLES AND RESPONSIBILITIES.........................................................................................................2
PROJECT ORGANIZATIONAL CHARTS...............................................................................................2
STAFFING MANAGEMENT.................................................................................................................4
PROJECT TEAM TRAINING................................................................................................................5
ACCEPTANCE....................................................................................................................................5
Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
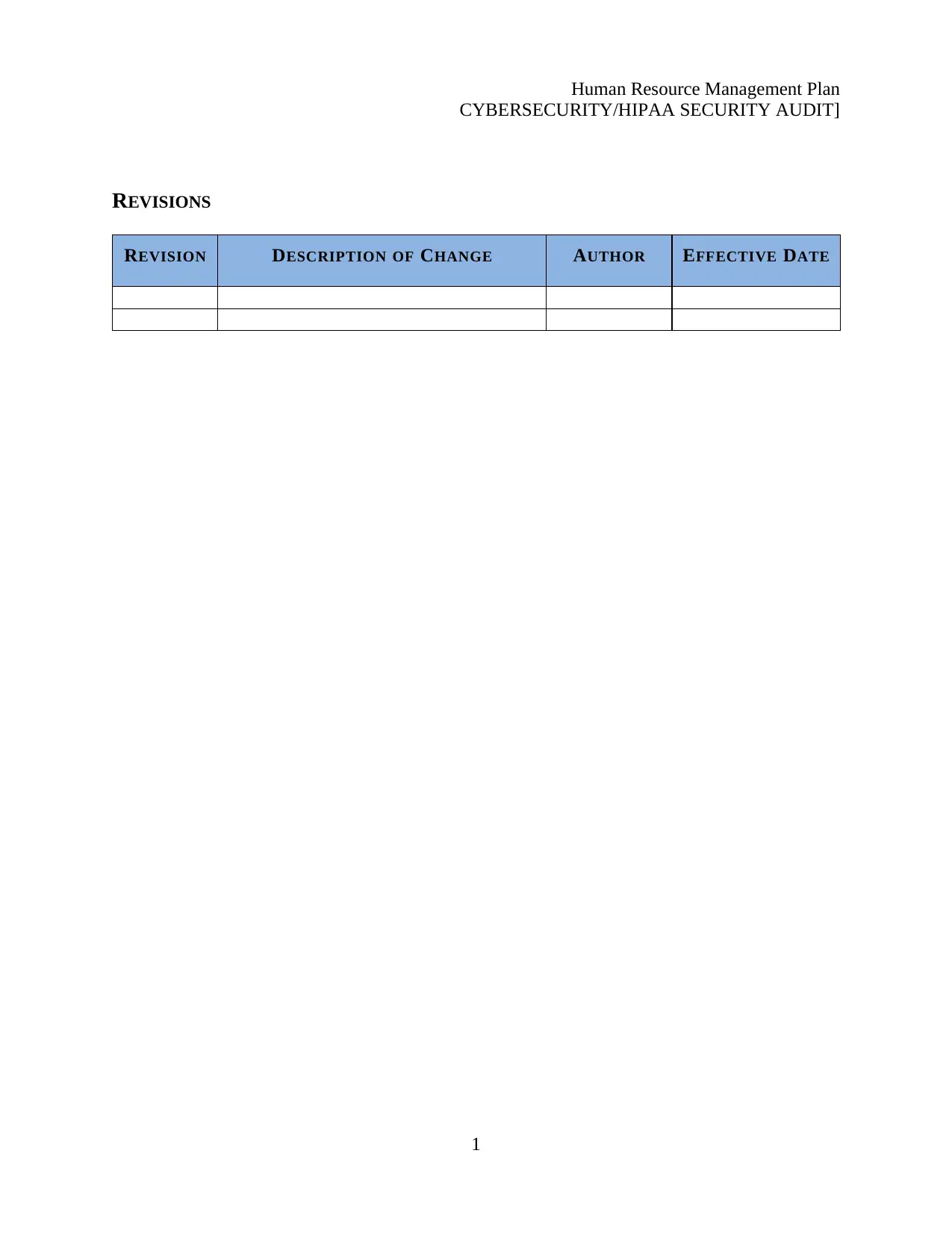
REVISIONS
REVISION DESCRIPTION OF CHANGE AUTHOR EFFECTIVE DATE
1
CYBERSECURITY/HIPAA SECURITY AUDIT]
REVISIONS
REVISION DESCRIPTION OF CHANGE AUTHOR EFFECTIVE DATE
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
INTRODUCTION
The purpose of HR Plan is to ensure that the staffing needs of the project stays fulfilled. This HR
plan shows various aspects of the plan in different sections.
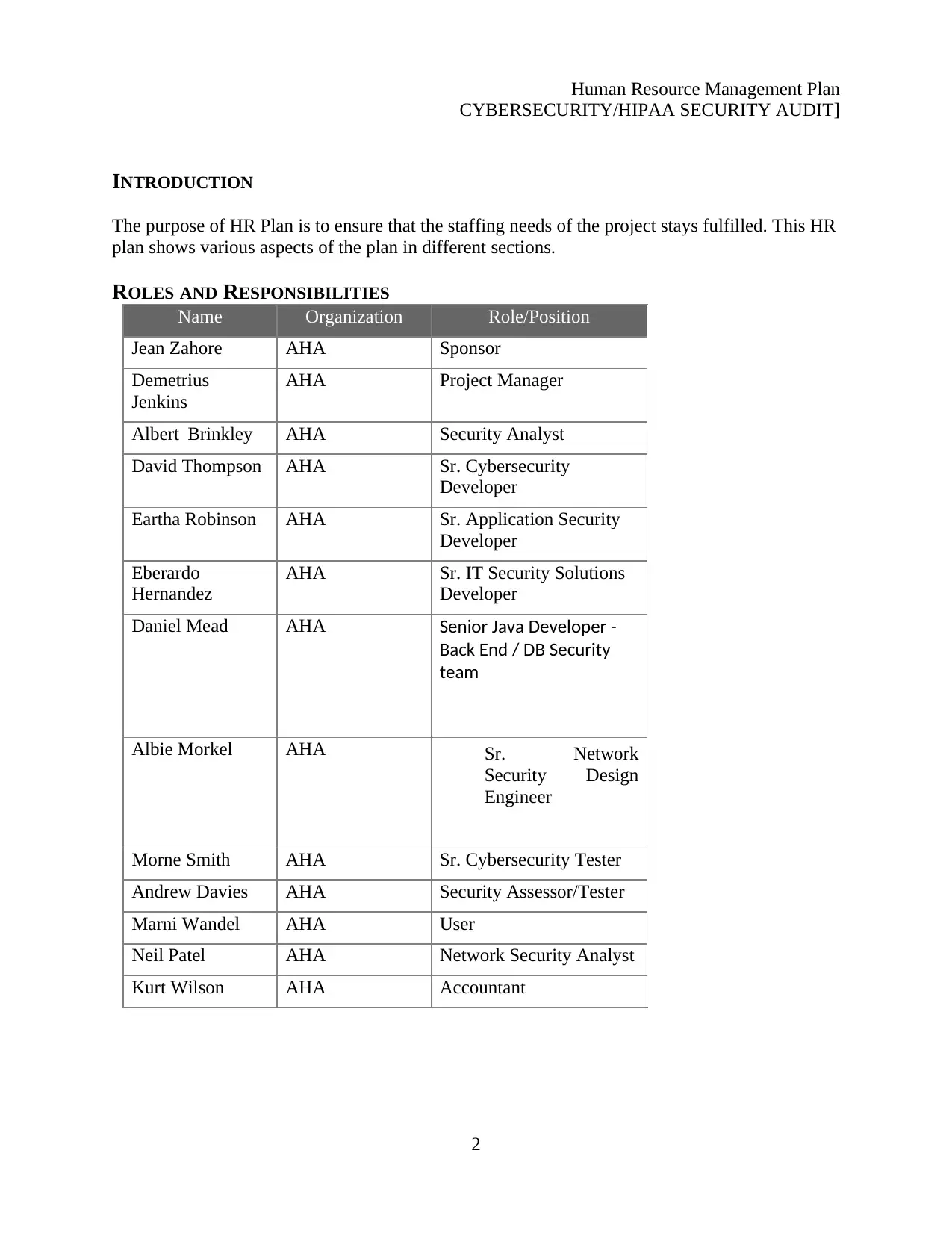
ROLES AND RESPONSIBILITIES
Name Organization Role/Position
Jean Zahore AHA Sponsor
Demetrius
Jenkins
AHA Project Manager
Albert Brinkley AHA Security Analyst
David Thompson AHA Sr. Cybersecurity
Developer
Eartha Robinson AHA Sr. Application Security
Developer
Eberardo
Hernandez
AHA Sr. IT Security Solutions
Developer
Daniel Mead AHA Senior Java Developer -
Back End / DB Security
team
Albie Morkel AHA Sr. Network
Security Design
Engineer
Morne Smith AHA Sr. Cybersecurity Tester
Andrew Davies AHA Security Assessor/Tester
Marni Wandel AHA User
Neil Patel AHA Network Security Analyst
Kurt Wilson AHA Accountant
2
CYBERSECURITY/HIPAA SECURITY AUDIT]
INTRODUCTION
The purpose of HR Plan is to ensure that the staffing needs of the project stays fulfilled. This HR
plan shows various aspects of the plan in different sections.
ROLES AND RESPONSIBILITIES
Name Organization Role/Position
Jean Zahore AHA Sponsor
Demetrius
Jenkins
AHA Project Manager
Albert Brinkley AHA Security Analyst
David Thompson AHA Sr. Cybersecurity
Developer
Eartha Robinson AHA Sr. Application Security
Developer
Eberardo
Hernandez
AHA Sr. IT Security Solutions
Developer
Daniel Mead AHA Senior Java Developer -
Back End / DB Security
team
Albie Morkel AHA Sr. Network
Security Design
Engineer
Morne Smith AHA Sr. Cybersecurity Tester
Andrew Davies AHA Security Assessor/Tester
Marni Wandel AHA User
Neil Patel AHA Network Security Analyst
Kurt Wilson AHA Accountant
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
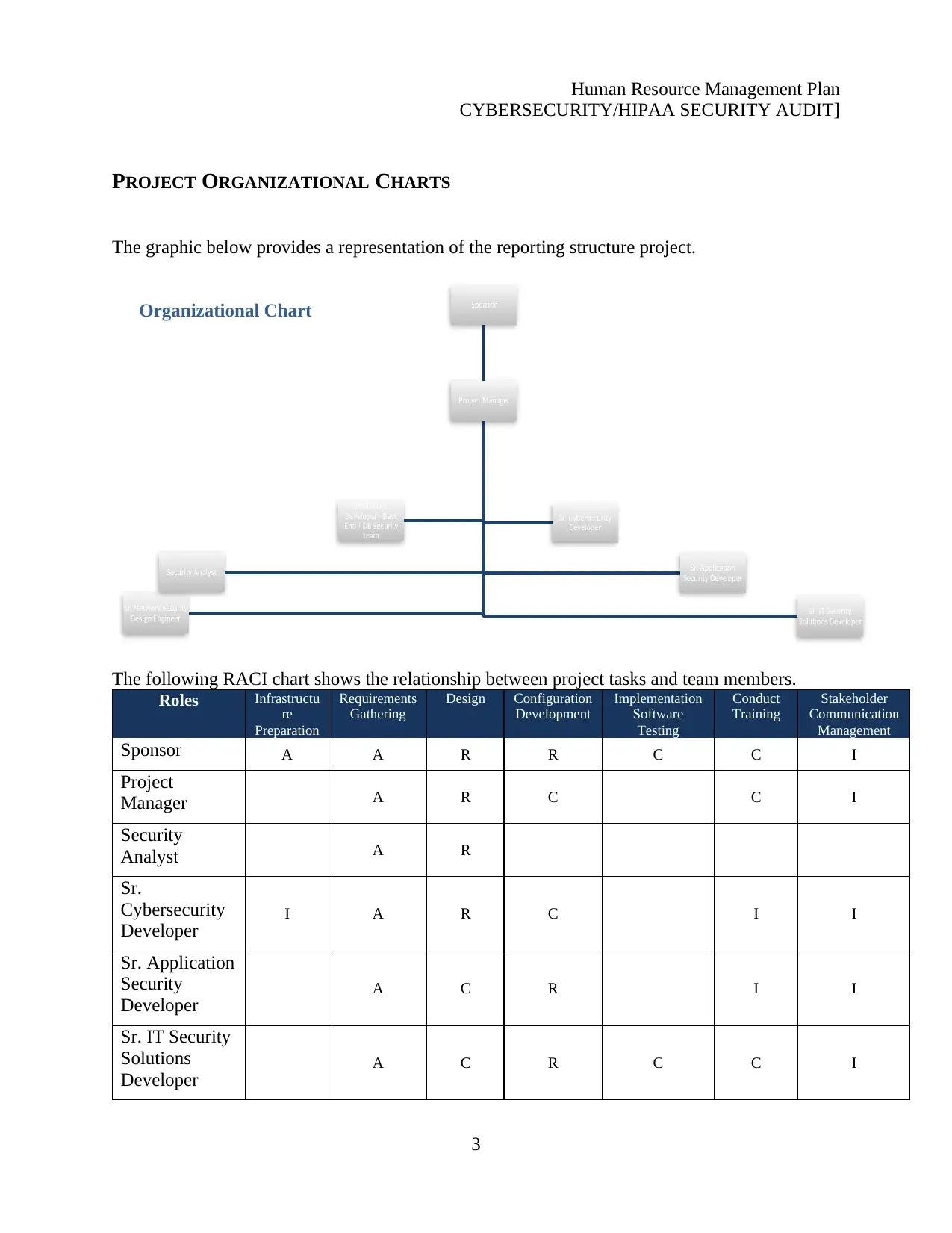
PROJECT ORGANIZATIONAL CHARTS
The graphic below provides a representation of the reporting structure project.
The following RACI chart shows the relationship between project tasks and team members.
Roles Infrastructu
re
Preparation
Requirements
Gathering
Design Configuration
Development
Implementation
Software
Testing
Conduct
Training
Stakeholder
Communication
Management
Sponsor A A R R C C I
Project
Manager A R C C I
Security
Analyst A R
Sr.
Cybersecurity
Developer I A R C I I
Sr. Application
Security
Developer A C R I I
Sr. IT Security
Solutions
Developer A C R C C I
3
Sponsor
Project Manager
Sr. Cybersecurity
Developer
Sr. Application
Security Developer
Sr. IT Security
Solutions Developer
Senior Java
Developer - Back
End / DB Security
team
Sr. Network Security
Design Engineer
Security Analyst
Organizational Chart
CYBERSECURITY/HIPAA SECURITY AUDIT]
PROJECT ORGANIZATIONAL CHARTS
The graphic below provides a representation of the reporting structure project.
The following RACI chart shows the relationship between project tasks and team members.
Roles Infrastructu
re
Preparation
Requirements
Gathering
Design Configuration
Development
Implementation
Software
Testing
Conduct
Training
Stakeholder
Communication
Management
Sponsor A A R R C C I
Project
Manager A R C C I
Security
Analyst A R
Sr.
Cybersecurity
Developer I A R C I I
Sr. Application
Security
Developer A C R I I
Sr. IT Security
Solutions
Developer A C R C C I
3
Sponsor
Project Manager
Sr. Cybersecurity
Developer
Sr. Application
Security Developer
Sr. IT Security
Solutions Developer
Senior Java
Developer - Back
End / DB Security
team
Sr. Network Security
Design Engineer
Security Analyst
Organizational Chart
Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
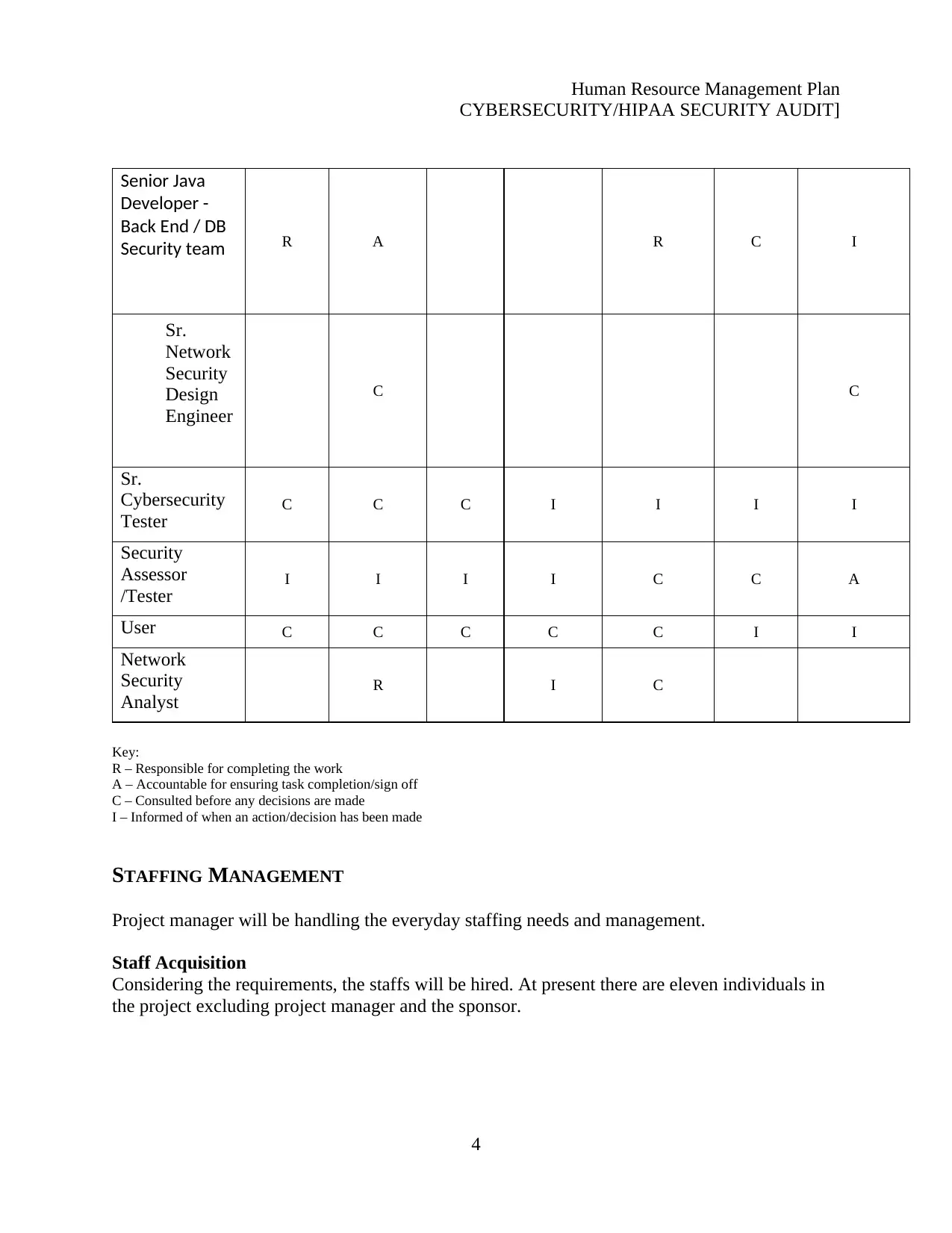
Senior Java
Developer -
Back End / DB
Security team R A R C I
Sr.
Network
Security
Design
Engineer
C C
Sr.
Cybersecurity
Tester C C C I I I I
Security
Assessor
/Tester I I I I C C A
User C C C C C I I
Network
Security
Analyst R I C
Key:
R – Responsible for completing the work
A – Accountable for ensuring task completion/sign off
C – Consulted before any decisions are made
I – Informed of when an action/decision has been made
STAFFING MANAGEMENT
Project manager will be handling the everyday staffing needs and management.
Staff Acquisition
Considering the requirements, the staffs will be hired. At present there are eleven individuals in
the project excluding project manager and the sponsor.
4
CYBERSECURITY/HIPAA SECURITY AUDIT]
Senior Java
Developer -
Back End / DB
Security team R A R C I
Sr.
Network
Security
Design
Engineer
C C
Sr.
Cybersecurity
Tester C C C I I I I
Security
Assessor
/Tester I I I I C C A
User C C C C C I I
Network
Security
Analyst R I C
Key:
R – Responsible for completing the work
A – Accountable for ensuring task completion/sign off
C – Consulted before any decisions are made
I – Informed of when an action/decision has been made
STAFFING MANAGEMENT
Project manager will be handling the everyday staffing needs and management.
Staff Acquisition
Considering the requirements, the staffs will be hired. At present there are eleven individuals in
the project excluding project manager and the sponsor.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Human Resource Management Plan
CYBERSECURITY/HIPAA SECURITY AUDIT]
PROJECT TEAM TRAINING
Training will be provided to the team at the beginning of the project. At the completion of the
project, the performance of the staffs will be assessed and rewards will be given.
ACCEPTANCE
Approved by:
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Executive Sponsor
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Business Sponsor
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Project Director/Manager
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Stakeholder
5
CYBERSECURITY/HIPAA SECURITY AUDIT]
PROJECT TEAM TRAINING
Training will be provided to the team at the beginning of the project. At the completion of the
project, the performance of the staffs will be assessed and rewards will be given.
ACCEPTANCE
Approved by:
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Executive Sponsor
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Business Sponsor
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Project Director/Manager
___________________________________________ Date:____________________
<Approvers Name>
CYBERSECURITY/HIPAA SECURITY AUDIT] Stakeholder
5
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



