Security Enhancement Plan for Next Gard: A Detailed Report
VerifiedAdded on 2023/06/15
|11
|2582
|64
Report
AI Summary
This report provides a comprehensive analysis and plan to enhance the security of Next Gard's organization. It details appropriate Microsoft Windows access controls, cryptography methods to protect organizational information, and a plan to thwart malicious code and activity. The report also formulates a plan to implement monitoring and analysis, details security guidelines for proxy servers and access control, and defines best practices for Next Gard's security. The conclusion summarizes the findings and recommendations, emphasizing the need for strict adherence to company policies, strong passwords, regular data backups, and two-factor authentication to mitigate risks from insider threats and external attacks. Desklib offers a range of similar documents and study tools for students.

REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................1
Research solutions and detail the appropriate Microsoft Windows access controls.......................1
Research and detail the cryptography methods to protect organizational information...................2
Research and devise a plan to thwart malicious code and activity..................................................3
Research and formulate a plan to implement monitoring and analysis...........................................4
Research and detail security guidelines for contains the two proxy servers and access control.....5
Research and define best practices for the security of Next Gard’s organization...........................5
Conclusion summarizing your findings and recommendations.......................................................6
The Network topology.....................................................................................................................7
References........................................................................................................................................8
Introduction......................................................................................................................................1
Research solutions and detail the appropriate Microsoft Windows access controls.......................1
Research and detail the cryptography methods to protect organizational information...................2
Research and devise a plan to thwart malicious code and activity..................................................3
Research and formulate a plan to implement monitoring and analysis...........................................4
Research and detail security guidelines for contains the two proxy servers and access control.....5
Research and define best practices for the security of Next Gard’s organization...........................5
Conclusion summarizing your findings and recommendations.......................................................6
The Network topology.....................................................................................................................7
References........................................................................................................................................8

Introduction
The objective of the project is based on the upgradation and securing the company with the
current network to enhance the organization efficiencies. It also focuses on designing access
control for the proper Microsoft Windows in order to enhance and handle the effective security
system.
Research solutions and detail the appropriate Microsoft
Windows access controls
The vulnerabilities and security holes are based on Microsoft software programs which is
considered to be the major target of security attacks. The major attacks focus on the Microsoft
Windows where there is a wide usage of the same by different organisations. The wide
vulnerabilities against the different Microsoft Windows lead to certain issues, where NextGard
need to focus on taking preventive measures to handle the Window Access Control policies.
The NextGard need to focus on improvement of access control through the use of auto-check in
order to search for the passwords that are complex for the IT administrator. The company needs
to formulate the policies along with ensuring the administrator with using a complex and strong
password to log into administrative account (Joshi & Karkade, 2015). The use of the strong
password is considered to be critical with deterring the unauthorised access into the company
with the network account. It is critical for the company to use strong password with unauthorised
individuals who will find challenging to crack. The company can make use of Smartcards to
securely handle the storage of personal information and enhancing the authentication.
The objective of the project is based on the upgradation and securing the company with the
current network to enhance the organization efficiencies. It also focuses on designing access
control for the proper Microsoft Windows in order to enhance and handle the effective security
system.
Research solutions and detail the appropriate Microsoft
Windows access controls
The vulnerabilities and security holes are based on Microsoft software programs which is
considered to be the major target of security attacks. The major attacks focus on the Microsoft
Windows where there is a wide usage of the same by different organisations. The wide
vulnerabilities against the different Microsoft Windows lead to certain issues, where NextGard
need to focus on taking preventive measures to handle the Window Access Control policies.
The NextGard need to focus on improvement of access control through the use of auto-check in
order to search for the passwords that are complex for the IT administrator. The company needs
to formulate the policies along with ensuring the administrator with using a complex and strong
password to log into administrative account (Joshi & Karkade, 2015). The use of the strong
password is considered to be critical with deterring the unauthorised access into the company
with the network account. It is critical for the company to use strong password with unauthorised
individuals who will find challenging to crack. The company can make use of Smartcards to
securely handle the storage of personal information and enhancing the authentication.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NextGard need to focus on the policy with ensuring that the employees are able to make use of
the computers of company for the business communication (Stallings, 2016). Here, all the
employees must communicate with the company emails and communication should be mainly on
NextGard business operations.
Research and detail the cryptography methods to protect
organizational information
The cryptography is mainly to protect against any information leakage through the process of
encryption. NextGard needs to focus on the development of better policy which will be able to
enhance the integrity, confidentiality and the authenticity of the system. The method involves the
use of the different encoded types of digital signatures which are set by asymmetric cryptography
or by the public key (Stallings & Tahiliani, 2014). The security policy is set where the company
includes document transferred with the document encryption. In order to decrypt the digital
signature, the user should properly able to verify the different public keys using a proper secured
private key which is of a document sender. The company should also employ with proper key
management to make the public as well as the private confidentiality key.
The encryption of data is through protecting the information of company, where encryption is the
best strategy which is for handling the data in the organisation. This is converted into any type of
unreadable form with only authorised users with decrypted key that can convert the data into a
readable form. The strategy is mainly about preventing unauthorised access to any type of data
company, with the encryption that tends to protect the data from any type of unauthorised access
mainly because there are some external intruders who are not able to read the data as they have
no access to the decrypted key (Kahate, 2013). The company needs to make use of these methods
the computers of company for the business communication (Stallings, 2016). Here, all the
employees must communicate with the company emails and communication should be mainly on
NextGard business operations.
Research and detail the cryptography methods to protect
organizational information
The cryptography is mainly to protect against any information leakage through the process of
encryption. NextGard needs to focus on the development of better policy which will be able to
enhance the integrity, confidentiality and the authenticity of the system. The method involves the
use of the different encoded types of digital signatures which are set by asymmetric cryptography
or by the public key (Stallings & Tahiliani, 2014). The security policy is set where the company
includes document transferred with the document encryption. In order to decrypt the digital
signature, the user should properly able to verify the different public keys using a proper secured
private key which is of a document sender. The company should also employ with proper key
management to make the public as well as the private confidentiality key.
The encryption of data is through protecting the information of company, where encryption is the
best strategy which is for handling the data in the organisation. This is converted into any type of
unreadable form with only authorised users with decrypted key that can convert the data into a
readable form. The strategy is mainly about preventing unauthorised access to any type of data
company, with the encryption that tends to protect the data from any type of unauthorised access
mainly because there are some external intruders who are not able to read the data as they have
no access to the decrypted key (Kahate, 2013). The company needs to make use of these methods
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

which are for protecting the data transferred from one to the other computer since the intruder
could hijack the data from network. This is through strategy like eavesdropping and sniffing,
where the company also need to make use of different cryptographic strategies in order to protect
the data of company which is set in transit through using the encryption forms. The company
also need to focus on decrypted keys which is confidential and for this there should be no
communication of decrypted keys to the third party or any unauthorised people (Perlman et al.,
2016).
Research and devise a plan to thwart malicious code and
activity
The Trojan horse is one of the malicious programs which is found to be looking like a normal
program which tends to hide any malicious code to gain a proper access to the confidential
information. This is done through the remote access where the virus can also manipulate the
legitimate users by passing the access control and then making use of the authentication process
to handle the spread of the malicious codes (Rhodes, 2013). The virus can affect the system with
creating different problems for the NextGard and so the logic bombs are the codes which are
inserted to trigger the malicious codes. The programmer can easily a plant the same to trigger the
malicious applications. One needs to design strategies about implementing some
countermeasures against the viruses, worms and the Trojan horse. The effectiveness is based on
installing the antivirus to computer systems (Kumar, 2015). The worms, and Trojan horse are
spreading when the user tend to download any of the attachment which contain the virus or the
worms. The company needs to provide with the better training skills to the company staff about
could hijack the data from network. This is through strategy like eavesdropping and sniffing,
where the company also need to make use of different cryptographic strategies in order to protect
the data of company which is set in transit through using the encryption forms. The company
also need to focus on decrypted keys which is confidential and for this there should be no
communication of decrypted keys to the third party or any unauthorised people (Perlman et al.,
2016).
Research and devise a plan to thwart malicious code and
activity
The Trojan horse is one of the malicious programs which is found to be looking like a normal
program which tends to hide any malicious code to gain a proper access to the confidential
information. This is done through the remote access where the virus can also manipulate the
legitimate users by passing the access control and then making use of the authentication process
to handle the spread of the malicious codes (Rhodes, 2013). The virus can affect the system with
creating different problems for the NextGard and so the logic bombs are the codes which are
inserted to trigger the malicious codes. The programmer can easily a plant the same to trigger the
malicious applications. One needs to design strategies about implementing some
countermeasures against the viruses, worms and the Trojan horse. The effectiveness is based on
installing the antivirus to computer systems (Kumar, 2015). The worms, and Trojan horse are
spreading when the user tend to download any of the attachment which contain the virus or the
worms. The company needs to provide with the better training skills to the company staff about

handling the trusted emails. The company need to install some trusted application package in the
computer system in order to avoid any kind of the bomb that is being in the Microsoft Windows.
Research and formulate a plan to implement monitoring
and analysis
The proper incident response is about the integral part with risk mitigation and overall security
policy. The NextGard focus on the implementation of computer auditing with two or three times
with ensuring the computer systems free from the malicious codes. The company needs to focus
on enforcing the policies to ensure that the employees follow a better IT policy. The IT security
incidents are based on accidentally handling the IT personnel who do not need to focus on the
policies of company or procedures. The NextGard generally focus on the testing policies with
ensuring that the company policies are completely clear (Manshaei et al, 2013).
Along with this, the company needs to focus on the latest patches which are being installed in the
computer system. Along with this, a proper development of the backup plan for the data is
helpful to protect the company which relates to the human and natural disasters. The backup data
needs to be stored with remote locations that allow the company to quickly restore and work on
business operations in order to prevent the loss of the data. Here, the company tends to take a
proper training program which is for the new and the experienced IT staff since many people
focus on vulnerability tend to pass through inexperience IT users (Pathan, 2016). The company
also need to develop a policy which is important for the employees to make use of strong
passwords. The company need to analyse and monitor the different system and the network
performance which is based on checking all the logging mechanisms like the applications related
to the specific logs, with events of operating system and intrusion detection system logs.
computer system in order to avoid any kind of the bomb that is being in the Microsoft Windows.
Research and formulate a plan to implement monitoring
and analysis
The proper incident response is about the integral part with risk mitigation and overall security
policy. The NextGard focus on the implementation of computer auditing with two or three times
with ensuring the computer systems free from the malicious codes. The company needs to focus
on enforcing the policies to ensure that the employees follow a better IT policy. The IT security
incidents are based on accidentally handling the IT personnel who do not need to focus on the
policies of company or procedures. The NextGard generally focus on the testing policies with
ensuring that the company policies are completely clear (Manshaei et al, 2013).
Along with this, the company needs to focus on the latest patches which are being installed in the
computer system. Along with this, a proper development of the backup plan for the data is
helpful to protect the company which relates to the human and natural disasters. The backup data
needs to be stored with remote locations that allow the company to quickly restore and work on
business operations in order to prevent the loss of the data. Here, the company tends to take a
proper training program which is for the new and the experienced IT staff since many people
focus on vulnerability tend to pass through inexperience IT users (Pathan, 2016). The company
also need to develop a policy which is important for the employees to make use of strong
passwords. The company need to analyse and monitor the different system and the network
performance which is based on checking all the logging mechanisms like the applications related
to the specific logs, with events of operating system and intrusion detection system logs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research and detail security guidelines for contains the
two proxy servers and access control
The internet access control and the proxy servers generally operate in the network environment
where the external intruders tend to make use of the different techniques. The examples for this
is eavesdropping and sniffing to steal all the important information from any network system of
the organisation. The firewall is considered to be an effective program that the company could
easily employ in order to block any type of external intruders who tend to gain major access to
the proxy server of the company (Van & Jajodia, 2014). The focus is mainly on the programs
related to firewall where there is a need to assist the company proxy servers as well. The firewall
will be able to provide a better protection along with making use of the different application
proxy gateway which is featured mainly on the advanced firewall setup. The type of firewall acts
is based on the hosting and restricting any kind of direct connection between the two. The
firewall also tends to make use of the authentication system through the use of ID and passwords
in order to control the access for the server. The application gateway is mainly to inspect and
work on the content of the network traffic which is mainly to permit or deny any kind of
unauthorised traffic in NextGard. The company is also able to use Dedicated Proxy Servers in
order to perform the validation and perfectly handle the analysis of the application protocols like
the HTTP (Daras & Rassias, 2015).
Research and define best practices for the security of
Next Gard’s organization.
The company NextGard need to focus on designing with Microsoft security policies where the
company employees need to follow it. The critical issue is about strict respect of the company
two proxy servers and access control
The internet access control and the proxy servers generally operate in the network environment
where the external intruders tend to make use of the different techniques. The examples for this
is eavesdropping and sniffing to steal all the important information from any network system of
the organisation. The firewall is considered to be an effective program that the company could
easily employ in order to block any type of external intruders who tend to gain major access to
the proxy server of the company (Van & Jajodia, 2014). The focus is mainly on the programs
related to firewall where there is a need to assist the company proxy servers as well. The firewall
will be able to provide a better protection along with making use of the different application
proxy gateway which is featured mainly on the advanced firewall setup. The type of firewall acts
is based on the hosting and restricting any kind of direct connection between the two. The
firewall also tends to make use of the authentication system through the use of ID and passwords
in order to control the access for the server. The application gateway is mainly to inspect and
work on the content of the network traffic which is mainly to permit or deny any kind of
unauthorised traffic in NextGard. The company is also able to use Dedicated Proxy Servers in
order to perform the validation and perfectly handle the analysis of the application protocols like
the HTTP (Daras & Rassias, 2015).
Research and define best practices for the security of
Next Gard’s organization.
The company NextGard need to focus on designing with Microsoft security policies where the
company employees need to follow it. The critical issue is about strict respect of the company
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

policies which is considered to be the best strategy to enhance the effectiveness of the security of
company. Along with this, there is a need to use strong passwords with employing the risk based
approach to security. The measures are based on identifying a form of hierarchical cyber security
policy with centralised forms along with updating the software. The cyber security updates are
important as they help in handling the malwares which are unknown and exploit the system
proficiency. The backup of the data regularly has been proven effective as it helps in gaining
relevance in the recent times where the advent of ransomware is mainly designed to encrypt the
data and block access till one tends to pay for a hefty sum for a decryption key. The use of the
principles with least privilege is set through allowing employees to access sensitive data. The
approach does not only pose any additional risk when considered with the terms of insider
threats along with allowing the external hackers to access to sensitive data (Kapoor & Yadav,
2016). The use of two-factor authentication is important security standard when it comes to
account protection along with handling passwords in a secured manner. The parts are set with
changing default passwords for the IoT devices. The internet enabled devices generally to come
with the set of default credentials with hard coded inside that are available on the internet. The
only way to make sure is about the devices to protect from being infected with changing any type
of default credentials. One needs to keep an eye on the privileged users with necessity to steal the
sensitive data and then go unnoticed. The best way to minimise the risks of the insider attack is
by the privileged users to limit the numbers and focus on making sure that the accounts tend to
get disabled when the person using them is also seen to be terminated (Anandkumar, 2015).
company. Along with this, there is a need to use strong passwords with employing the risk based
approach to security. The measures are based on identifying a form of hierarchical cyber security
policy with centralised forms along with updating the software. The cyber security updates are
important as they help in handling the malwares which are unknown and exploit the system
proficiency. The backup of the data regularly has been proven effective as it helps in gaining
relevance in the recent times where the advent of ransomware is mainly designed to encrypt the
data and block access till one tends to pay for a hefty sum for a decryption key. The use of the
principles with least privilege is set through allowing employees to access sensitive data. The
approach does not only pose any additional risk when considered with the terms of insider
threats along with allowing the external hackers to access to sensitive data (Kapoor & Yadav,
2016). The use of two-factor authentication is important security standard when it comes to
account protection along with handling passwords in a secured manner. The parts are set with
changing default passwords for the IoT devices. The internet enabled devices generally to come
with the set of default credentials with hard coded inside that are available on the internet. The
only way to make sure is about the devices to protect from being infected with changing any type
of default credentials. One needs to keep an eye on the privileged users with necessity to steal the
sensitive data and then go unnoticed. The best way to minimise the risks of the insider attack is
by the privileged users to limit the numbers and focus on making sure that the accounts tend to
get disabled when the person using them is also seen to be terminated (Anandkumar, 2015).

Conclusion summarizing your findings and
recommendations
NextGard need to focus on the proficiency of the system with specialisation in network
consulting services for the US companies. The organisation also need to focus on the different
printing servers and the proxy servers so that the data is not hacked or affected by the virus. With
this, there is a need to focus on working on company network with remote employees, business
partners, suppliers and vendors. The third-party access does not provide a major risk of insider
attacks but tend to open for the malware and the malicious hackers.
The major recommendation for the system is to change the temporary passwords with limiting
the scope of access that any type of third party users have. One needs to make sure about
allowing and connecting to the network, with user action monitoring that is set in conjunction
with one-time passwords to provide full logging user actions. This also allows one to detect any
malicious activities with conduct investigations as per the requirement.
recommendations
NextGard need to focus on the proficiency of the system with specialisation in network
consulting services for the US companies. The organisation also need to focus on the different
printing servers and the proxy servers so that the data is not hacked or affected by the virus. With
this, there is a need to focus on working on company network with remote employees, business
partners, suppliers and vendors. The third-party access does not provide a major risk of insider
attacks but tend to open for the malware and the malicious hackers.
The major recommendation for the system is to change the temporary passwords with limiting
the scope of access that any type of third party users have. One needs to make sure about
allowing and connecting to the network, with user action monitoring that is set in conjunction
with one-time passwords to provide full logging user actions. This also allows one to detect any
malicious activities with conduct investigations as per the requirement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
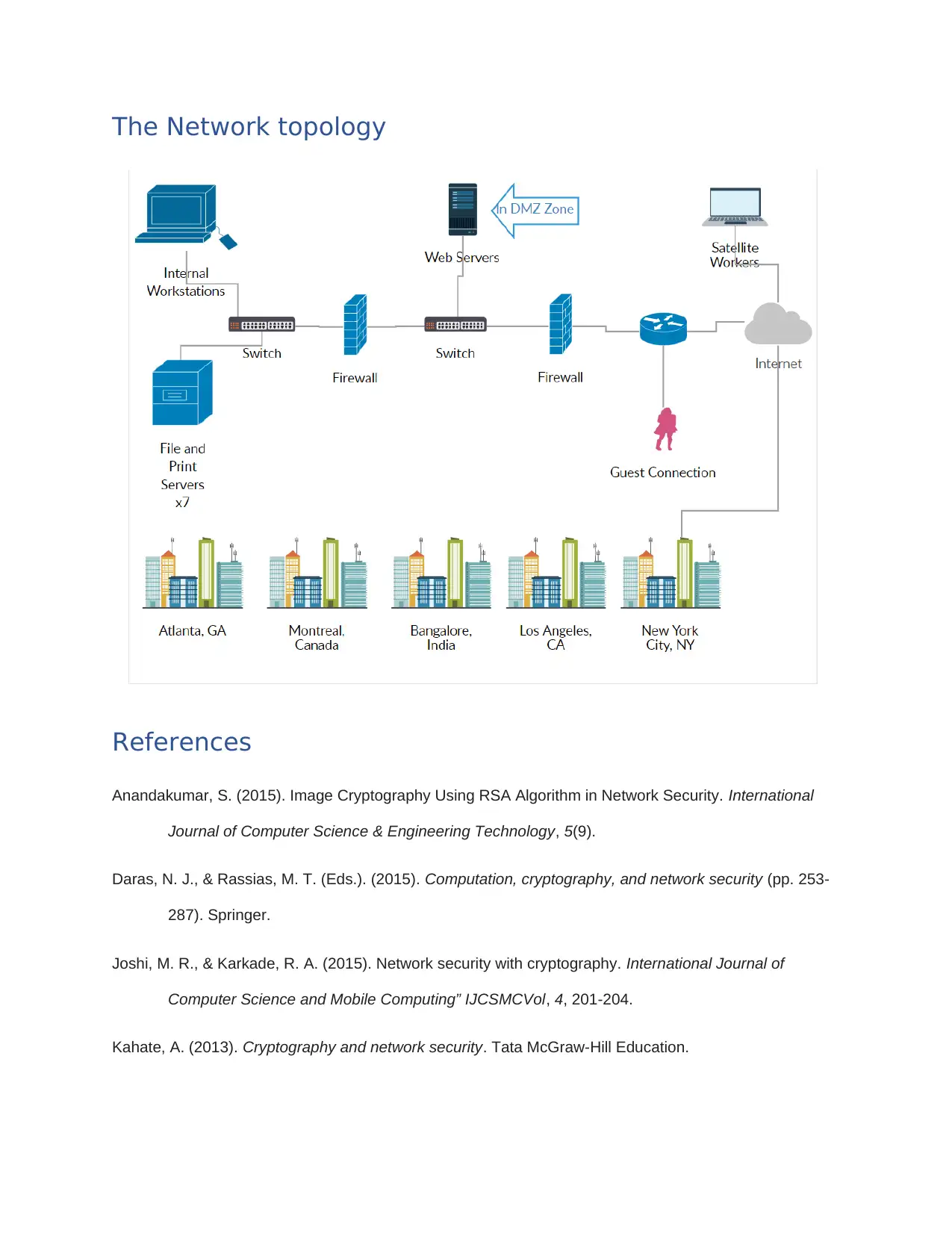
The Network topology
References
Anandakumar, S. (2015). Image Cryptography Using RSA Algorithm in Network Security. International
Journal of Computer Science & Engineering Technology, 5(9).
Daras, N. J., & Rassias, M. T. (Eds.). (2015). Computation, cryptography, and network security (pp. 253-
287). Springer.
Joshi, M. R., & Karkade, R. A. (2015). Network security with cryptography. International Journal of
Computer Science and Mobile Computing” IJCSMCVol, 4, 201-204.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
References
Anandakumar, S. (2015). Image Cryptography Using RSA Algorithm in Network Security. International
Journal of Computer Science & Engineering Technology, 5(9).
Daras, N. J., & Rassias, M. T. (Eds.). (2015). Computation, cryptography, and network security (pp. 253-
287). Springer.
Joshi, M. R., & Karkade, R. A. (2015). Network security with cryptography. International Journal of
Computer Science and Mobile Computing” IJCSMCVol, 4, 201-204.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Kapoor, V., & Yadav, R. (2016). A Hybrid Cryptography Technique for Improving Network
Security. International Journal of Computer Applications (0975–8887) Volume.
Kumar, S. N. (2015). Review on Network Security and Cryptography. International Transaction of
Electrical and Computer Engineers System, 3(1), 1-11.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets network
security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN, VANET. CRC
press.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a public
world. Pearson Education India.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill Education.
Stallings, W. (2016). Cryptography and network security: principles and practice. Pearson.
Stallings, W., & Tahiliani, M. P. (2014). Cryptography and network security: principles and practice (Vol.
6). London: Pearson.
Van Tilborg, H. C., & Jajodia, S. (Eds.). (2014). Encyclopedia of cryptography and security. Springer
Science & Business Media.
Security. International Journal of Computer Applications (0975–8887) Volume.
Kumar, S. N. (2015). Review on Network Security and Cryptography. International Transaction of
Electrical and Computer Engineers System, 3(1), 1-11.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory meets network
security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN, VANET. CRC
press.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a public
world. Pearson Education India.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill Education.
Stallings, W. (2016). Cryptography and network security: principles and practice. Pearson.
Stallings, W., & Tahiliani, M. P. (2014). Cryptography and network security: principles and practice (Vol.
6). London: Pearson.
Van Tilborg, H. C., & Jajodia, S. (Eds.). (2014). Encyclopedia of cryptography and security. Springer
Science & Business Media.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




