Analysis of NFC Security, Wireless Networking Concepts and Ping Test
VerifiedAdded on 2023/06/10
|7
|1157
|119
Report
AI Summary
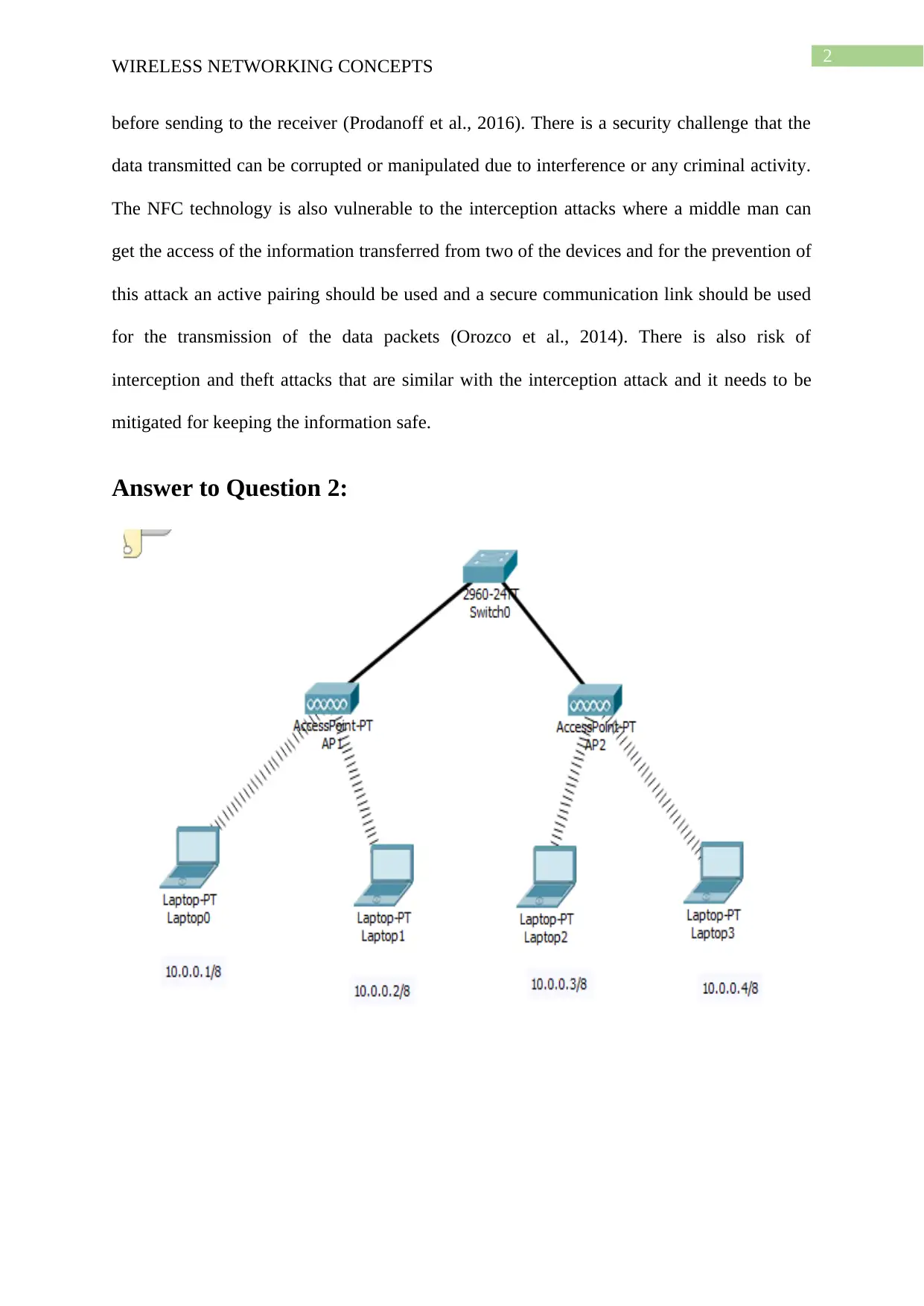
This report provides a comprehensive analysis of wireless networking concepts, with a specific focus on Near Field Communication (NFC) technology, its security vulnerabilities, and network configuration. It begins by explaining NFC's functionality, its modes of operation, and its reliance on RFID technology. The report then delves into the security challenges associated with NFC, including eavesdropping, data corruption, interception attacks, and theft risks, and proposes mitigation strategies such as secure communication channels and encryption. Furthermore, the document includes a practical analysis of wireless network configuration, including the use of ping tests to verify network connectivity, the impact of channel changes on access points, and the importance of matching passphrases for secure access. The report concludes by emphasizing the need for robust security measures to protect against potential breaches in NFC-enabled devices and wireless networks. Desklib provides this document along with numerous other solved assignments and resources for students.
1 out of 7













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)