Analysis of the Relationship Between NIST and FISMA Compliance
VerifiedAdded on 2022/12/20
|5
|859
|27
Report
AI Summary
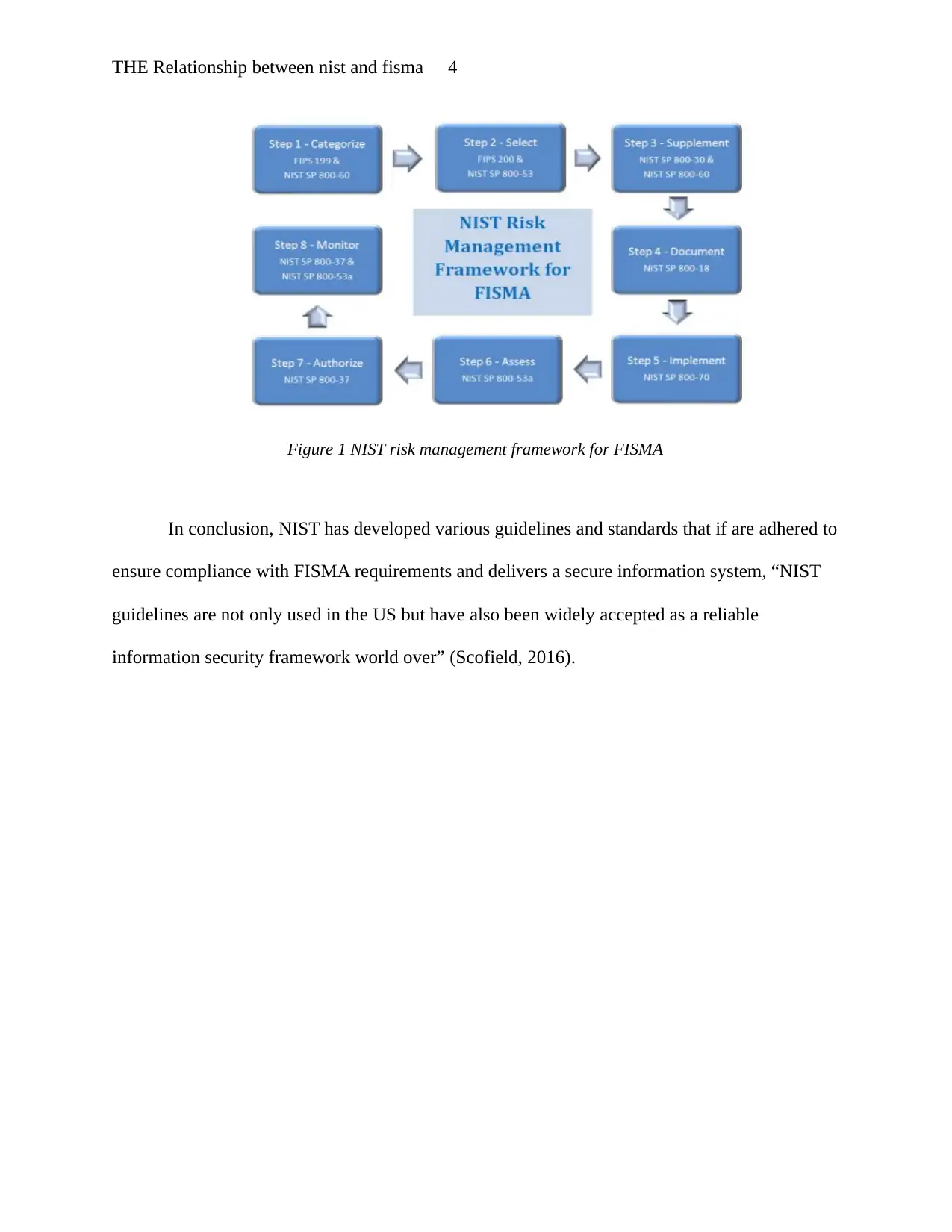
This report examines the critical relationship between the National Institute of Standards and Technology (NIST) and the Federal Information Security Management Act (FISMA) in the context of information security. It underscores the importance of protecting organizational data, highlighting the need for confidentiality, integrity, and availability. The report discusses FISMA's role in safeguarding U.S. federal government information systems and the delegation of guideline development to NIST. NIST's standards, categorized into FIPS, Guidance Documents, and Security-Related Publications, are detailed, with a focus on the SP 800 series, including SP 800-37 and SP 800-53. The report further outlines NIST's nine-step process for ensuring FISMA compliance and concludes with the global acceptance of NIST guidelines as a reliable information security framework. The report references several sources including the work of Whitman & Mattord, Howard, Miller, Shankar, and Scofield to support its claims.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)