Operating Systems Assignment 1 Solution, NIT1202, May 2019
VerifiedAdded on 2023/03/20
|17
|2929
|32
Homework Assignment
AI Summary
This document presents a comprehensive solution to an Operating Systems assignment, addressing key concepts such as memory management, process scheduling algorithms, and system security. The solution begins with a review of an academic article on operating system security vulnerabilities, comparing different OS versions and their susceptibility to cyber threats. It then delves into memory management, providing solutions to questions on best-fit and first-fit algorithms, internal and external fragmentation, and page calculations. The assignment also covers process scheduling, including FCFS, SJN, SRT, and Round Robin algorithms, with detailed explanations and examples. The document provides a detailed analysis of each algorithm and calculates turnaround times and success rates. This assignment solution is a valuable resource for students studying operating systems and related topics.

College of Engineering and Science
NIT1202 Operating Systems
MAY 14, 2019
omer uzun
S4623308
NIT1202 Operating Systems
MAY 14, 2019
omer uzun
S4623308
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIT1202 Operating Systems
1
Table of Contents
Question 1.............................................................................................................................................2
Summary of article............................................................................................................................2
Conclusion.........................................................................................................................................2
Evaluation of article...........................................................................................................................3
Question 2.............................................................................................................................................3
A: Best fit algorithm...........................................................................................................................3
B: First fit algorithm...........................................................................................................................3
Question 3:............................................................................................................................................3
Difference between internal fragmentation and external fragmentation.........................................3
Question 4:............................................................................................................................................4
A. Numbers of pages required to store the job.............................................................................4
B. Page numbers and exact displacement for every byte address.................................................4
Question 5:............................................................................................................................................5
Question 6:............................................................................................................................................6
Question 7:............................................................................................................................................7
A. FCFS algorithm...........................................................................................................................7
B. SJN process................................................................................................................................8
C. SRT system.................................................................................................................................9
D. Round Robin..............................................................................................................................9
References...........................................................................................................................................11
1
Table of Contents
Question 1.............................................................................................................................................2
Summary of article............................................................................................................................2
Conclusion.........................................................................................................................................2
Evaluation of article...........................................................................................................................3
Question 2.............................................................................................................................................3
A: Best fit algorithm...........................................................................................................................3
B: First fit algorithm...........................................................................................................................3
Question 3:............................................................................................................................................3
Difference between internal fragmentation and external fragmentation.........................................3
Question 4:............................................................................................................................................4
A. Numbers of pages required to store the job.............................................................................4
B. Page numbers and exact displacement for every byte address.................................................4
Question 5:............................................................................................................................................5
Question 6:............................................................................................................................................6
Question 7:............................................................................................................................................7
A. FCFS algorithm...........................................................................................................................7
B. SJN process................................................................................................................................8
C. SRT system.................................................................................................................................9
D. Round Robin..............................................................................................................................9
References...........................................................................................................................................11

NIT1202 Operating Systems
2
Question 1
Summary of the article
The title of the journal paper is “comparing security vulnerability by operating
system environment” that was written by Dongkyun Seo and Kyyngho lee in the year
2017. This journal paper is completely based on the operating systems and security
vulnerabilities occurred in the operating system (Seo, & Lee, 2017). The purpose of this
paper is to evaluate the concept of an operating system and compare security issues
faced by operating systems. According to the authors, operating systems such as
Windows XP, 7 and 8 have several security vulnerabilities which impact on the
performance of operating systems used in the computer devices.
It is analysed that most of the hackers targeted operating systems in order to
access the personal data and information of consumers. In this research paper, the
authors compared numerous systems and versions of operating systems in order to
understand the security risks occurred in operating systems. Moreover, the authors
involved windows XP operating system in their research and analyse the security
vulnerabilities and risks produced in the field of the operating system. The researchers
identified that around 1947 security vulnerabilities occur in administrator accounts and
775 vulnerabilities occur in the normal consumer’s accounts. It is suggested that the
lack of privacy and utilization of unauthorized servers are very major factors that
enhance the level of security threats and vulnerabilities in operating systems
(Silberschatz, Gagne, & Galvin, 2018). However, the rate of security vulnerabilities is
very less in the case of Windows XP rather than 7 and 8 operating systems because XP
dies not to support more features. From the discussion, it is concluded that Windows 7
has a large percentage of vulnerabilities and security threats because it provides more
features to the users which are directly linked with the cyber-crimes. This journal paper
shows the risks and issues faced by operating systems and also compared various kinds
of operating systems for understanding security risks and vulnerabilities.
Conclusion
This paper focused on the security issues faced by operating schemes and
compared dissimilar kinds of operating schemes utilized in computer devices. After
2
Question 1
Summary of the article
The title of the journal paper is “comparing security vulnerability by operating
system environment” that was written by Dongkyun Seo and Kyyngho lee in the year
2017. This journal paper is completely based on the operating systems and security
vulnerabilities occurred in the operating system (Seo, & Lee, 2017). The purpose of this
paper is to evaluate the concept of an operating system and compare security issues
faced by operating systems. According to the authors, operating systems such as
Windows XP, 7 and 8 have several security vulnerabilities which impact on the
performance of operating systems used in the computer devices.
It is analysed that most of the hackers targeted operating systems in order to
access the personal data and information of consumers. In this research paper, the
authors compared numerous systems and versions of operating systems in order to
understand the security risks occurred in operating systems. Moreover, the authors
involved windows XP operating system in their research and analyse the security
vulnerabilities and risks produced in the field of the operating system. The researchers
identified that around 1947 security vulnerabilities occur in administrator accounts and
775 vulnerabilities occur in the normal consumer’s accounts. It is suggested that the
lack of privacy and utilization of unauthorized servers are very major factors that
enhance the level of security threats and vulnerabilities in operating systems
(Silberschatz, Gagne, & Galvin, 2018). However, the rate of security vulnerabilities is
very less in the case of Windows XP rather than 7 and 8 operating systems because XP
dies not to support more features. From the discussion, it is concluded that Windows 7
has a large percentage of vulnerabilities and security threats because it provides more
features to the users which are directly linked with the cyber-crimes. This journal paper
shows the risks and issues faced by operating systems and also compared various kinds
of operating systems for understanding security risks and vulnerabilities.
Conclusion
This paper focused on the security issues faced by operating schemes and
compared dissimilar kinds of operating schemes utilized in computer devices. After
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NIT1202 Operating Systems
3
analysing this paper it is concluded that windows 7 produce a large number of security
vulnerabilities in the system as compare to the Windows XP and Windows 8 operating
system because it has more changing options and features. The researchers show that
consumers can disable unnecessary Windows services in order to reduce the rate of
security risks and vulnerabilities in computer devices.
Evaluation of the article
According to my opinion, there are major two topics that made the paper more
interesting which include security vulnerabilities occurred in operating systems and
Compare the difference in user privileges. I have also faced such kinds of security issues
while using Windows 7 in services such as web browsing and emails where I received
fraud and spam emails from hackers.
Question 2
A: Best fit algorithm
As per the best-fit algorithm, the block request can be owed to the minimum free
divider that meets the obligation of the memory process. Such kind of process initially
searches the complete list of free partitions and uses the smallest memory size which is
adequate. After that, it determines a memory size which is close to the actual memory
request (Gupta, Khichar, Rathi, & Singh, 2018).
According to the given question the job A will be allocated to the Block 3, Job B
will be empty or waiting, Job C will be given to Block 4 and Job D will be allocated to the
Block 1.
B: First fit algorithm
In such kind of algorithm, memory can be allocated to the first free partition
which can accommodate the process. It finishes after finding the initial suitable free
partition (Raj, Kumar, & Jelciana, 2018).
So, as per the given question Job, A will be apportioned to the block 1, Job B will
be empty, Job C will be apportioned to the Block 2 and Job D will be empty because
there is no partition available in the memory system.
3
analysing this paper it is concluded that windows 7 produce a large number of security
vulnerabilities in the system as compare to the Windows XP and Windows 8 operating
system because it has more changing options and features. The researchers show that
consumers can disable unnecessary Windows services in order to reduce the rate of
security risks and vulnerabilities in computer devices.
Evaluation of the article
According to my opinion, there are major two topics that made the paper more
interesting which include security vulnerabilities occurred in operating systems and
Compare the difference in user privileges. I have also faced such kinds of security issues
while using Windows 7 in services such as web browsing and emails where I received
fraud and spam emails from hackers.
Question 2
A: Best fit algorithm
As per the best-fit algorithm, the block request can be owed to the minimum free
divider that meets the obligation of the memory process. Such kind of process initially
searches the complete list of free partitions and uses the smallest memory size which is
adequate. After that, it determines a memory size which is close to the actual memory
request (Gupta, Khichar, Rathi, & Singh, 2018).
According to the given question the job A will be allocated to the Block 3, Job B
will be empty or waiting, Job C will be given to Block 4 and Job D will be allocated to the
Block 1.
B: First fit algorithm
In such kind of algorithm, memory can be allocated to the first free partition
which can accommodate the process. It finishes after finding the initial suitable free
partition (Raj, Kumar, & Jelciana, 2018).
So, as per the given question Job, A will be apportioned to the block 1, Job B will
be empty, Job C will be apportioned to the Block 2 and Job D will be empty because
there is no partition available in the memory system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIT1202 Operating Systems
4
Question 3:
Difference between internal fragmentation and external fragmentation
The memory fragmentation happens in the system when a computer device
involves memory which is technically free but the computer system cannot use them. It
is analysed that both these fragmentations are defined as the free interplanetary in the
computer memory (Tech Difference, 2016). The major difference between these
fragmentations is that internal fragmentation happens when the reminiscence provider
leaves additional interplanetary in the recollection blocks but external fragmentation
leaves memory block between portions of assigned memory (Hanrieder, 2015). It is
identified that the internal fragmentation occurs in the page frames but external
fragmentation occurs between various kinds of segments. The issue of interior
fragmentation may be resolved by dividing the retention into various blocks which is
less expensive but the resolution of external fragmentation is more expensive which is
another difference between both fragmentation processes.
However, the external fragmentation might prefer because of their compaction
properties that mean wasted space can be used for another purpose. Moreover, such
type of fragmentation is more effective and reliable as compared to the internal
fragmentation and it can be reclaimed in the process (Vocialta, & Molinari, 2015). Due
to all these key points, it is suggested that external fragmentation may be preferred
rather than other fragmentation.
Question 4:
A. Numbers of pages required to store the job
As per the question, the package includes around 471 bytes and every page frame
can store 100 bytes of information at a time. So to broad the job of 471 bytes total
numbers of pages can be calculated as:
(471/100) + 1= 5
So, a total of 5 pages are required to store the complete job.
4
Question 3:
Difference between internal fragmentation and external fragmentation
The memory fragmentation happens in the system when a computer device
involves memory which is technically free but the computer system cannot use them. It
is analysed that both these fragmentations are defined as the free interplanetary in the
computer memory (Tech Difference, 2016). The major difference between these
fragmentations is that internal fragmentation happens when the reminiscence provider
leaves additional interplanetary in the recollection blocks but external fragmentation
leaves memory block between portions of assigned memory (Hanrieder, 2015). It is
identified that the internal fragmentation occurs in the page frames but external
fragmentation occurs between various kinds of segments. The issue of interior
fragmentation may be resolved by dividing the retention into various blocks which is
less expensive but the resolution of external fragmentation is more expensive which is
another difference between both fragmentation processes.
However, the external fragmentation might prefer because of their compaction
properties that mean wasted space can be used for another purpose. Moreover, such
type of fragmentation is more effective and reliable as compared to the internal
fragmentation and it can be reclaimed in the process (Vocialta, & Molinari, 2015). Due
to all these key points, it is suggested that external fragmentation may be preferred
rather than other fragmentation.
Question 4:
A. Numbers of pages required to store the job
As per the question, the package includes around 471 bytes and every page frame
can store 100 bytes of information at a time. So to broad the job of 471 bytes total
numbers of pages can be calculated as:
(471/100) + 1= 5
So, a total of 5 pages are required to store the complete job.

NIT1202 Operating Systems
5
B. Page numbers and exact displacement for every byte addresses
From the given data and information numbers of pages and exact displacement can
be determined as:
(100*0) +0= 0
Which means page number is 0, displacement is 0 and the address of data is 0.
(100*1) +0= 100
That means Page 1= displacement is 0 and the address of data is 100
(132*1) +0= 132
Which means Page 1= displacement is 32 and the address of data is 132
(100*2) +0= 200
For page 2= displacement is 0 and the address of data is 200
(100*3) +0= 300
Here page 3= displacement is 0 and the value of the address is 300
(100*4) +71=471
So, page 4= displacement is 71 and the value of the address is 400.
Question 5:
a. As per the given question, the major memory of the system is composed of 3
pages frames for public utilization.
Page
requested:
a b a c d a e f g c b g
Page frame 1 a a a a d d d f f f b b
5
B. Page numbers and exact displacement for every byte addresses
From the given data and information numbers of pages and exact displacement can
be determined as:
(100*0) +0= 0
Which means page number is 0, displacement is 0 and the address of data is 0.
(100*1) +0= 100
That means Page 1= displacement is 0 and the address of data is 100
(132*1) +0= 132
Which means Page 1= displacement is 32 and the address of data is 132
(100*2) +0= 200
For page 2= displacement is 0 and the address of data is 200
(100*3) +0= 300
Here page 3= displacement is 0 and the value of the address is 300
(100*4) +71=471
So, page 4= displacement is 71 and the value of the address is 400.
Question 5:
a. As per the given question, the major memory of the system is composed of 3
pages frames for public utilization.
Page
requested:
a b a c d a e f g c b g
Page frame 1 a a a a d d d f f f b b
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NIT1202 Operating Systems
6
Page frame 2 b b b b a a a g g g g
Page frame 3 c c c e e e c c c
Interrupt: * * * * * * * * * *
The failure rate = 10/12= 83%
The success rate= 2/12= 17%
b. After analysing the given question and fundamental concept of FIFO algorithm it
is identified that failure and success ratios can be calculated as:
Here, 9 pages interrupt occurred out of 12 pages request due to which the failure rate is
75% and the success rate is around 25%.
c. The general conclusion of the example
Page
requested:
a b a c d a e f g c b g
Page frame 1 a a a a a a e e e e e e
Page frame 2 b b b b b b f f f b b
Page frame 3 c c c c c g g g g
Page frame 4 d d d d d c c c
Interrupt: * * * * * * * * *
6
Page frame 2 b b b b a a a g g g g
Page frame 3 c c c e e e c c c
Interrupt: * * * * * * * * * *
The failure rate = 10/12= 83%
The success rate= 2/12= 17%
b. After analysing the given question and fundamental concept of FIFO algorithm it
is identified that failure and success ratios can be calculated as:
Here, 9 pages interrupt occurred out of 12 pages request due to which the failure rate is
75% and the success rate is around 25%.
c. The general conclusion of the example
Page
requested:
a b a c d a e f g c b g
Page frame 1 a a a a a a e e e e e e
Page frame 2 b b b b b b f f f b b
Page frame 3 c c c c c g g g g
Page frame 4 d d d d d c c c
Interrupt: * * * * * * * * *
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIT1202 Operating Systems
7
After analysing and evaluating the given question it is concluded that by including
numbers of pages with the help of the FIFO algorithm can decrease the level of failure
and enhance the rate of success. Moreover, the additional page frames have potential to
enhance the performance of practicality and the improvement in the system would be
higher if the program had a small working set that reduces the rate of the number of
fault pages.
Question 6:
A. As per the given question Job A= 12, Job B= 2, Job C= 15, Job D= 7 and Job E=
3 ms and the order of processing the assigned job is given as A>B>C>D>E (He, 2012).
Moreover, the total time needed for processing all five jobs is given as
12+2+15+73= 39 Ms
However, the turnaround time for Job A= 12 milliseconds
Similarly, for Job B= 15 ms
For Job C= 30 ms
For Job D= 37 ms
For Job E= 40 ms
So, the average turnaround time is determined as:
(12+15+30+37+40)/5 = 26.8 milliseconds
B. As per the given scenario, the order of processing the assigned jobs are
B>E>D>A>C and total time needed to perform these jobs is 12+2+15+7+3= 39
milliseconds.
In order to find average turnaround time for all jobs first we required to
determine the turnaround time of each job which is given below:
For job B= 2 ms
For job E= 5 ms
7
After analysing and evaluating the given question it is concluded that by including
numbers of pages with the help of the FIFO algorithm can decrease the level of failure
and enhance the rate of success. Moreover, the additional page frames have potential to
enhance the performance of practicality and the improvement in the system would be
higher if the program had a small working set that reduces the rate of the number of
fault pages.
Question 6:
A. As per the given question Job A= 12, Job B= 2, Job C= 15, Job D= 7 and Job E=
3 ms and the order of processing the assigned job is given as A>B>C>D>E (He, 2012).
Moreover, the total time needed for processing all five jobs is given as
12+2+15+73= 39 Ms
However, the turnaround time for Job A= 12 milliseconds
Similarly, for Job B= 15 ms
For Job C= 30 ms
For Job D= 37 ms
For Job E= 40 ms
So, the average turnaround time is determined as:
(12+15+30+37+40)/5 = 26.8 milliseconds
B. As per the given scenario, the order of processing the assigned jobs are
B>E>D>A>C and total time needed to perform these jobs is 12+2+15+7+3= 39
milliseconds.
In order to find average turnaround time for all jobs first we required to
determine the turnaround time of each job which is given below:
For job B= 2 ms
For job E= 5 ms

NIT1202 Operating Systems
8
For job D= 12 ms
For job A= 24 ms
For job C= 39 ms
So, the average turnaround time is (12+15+30+37+40)/5= 26.80 milliseconds
Question 7:
A. FCFS algorithm
AS per the FCFS algorithm, the job which is entered in the system will be
executed (Behera, Pattanayak, & Mallick, 2012).
A B C D E
0 15 17 31 41 42
So, from the above table it is evaluated that for job The start time is 0 and the finish
time is 15. The schedule of arriving time is BCDE and timeline is from 0 to 42 sec.
B. SJN process
It is observed that SJN system processes jobs based on numbers of CPU cycles. So, in
the given scenario the job with less CPU cycle will be processed initially rather than
other.
Job A B C D E
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 15 17 31 41 42
8
For job D= 12 ms
For job A= 24 ms
For job C= 39 ms
So, the average turnaround time is (12+15+30+37+40)/5= 26.80 milliseconds
Question 7:
A. FCFS algorithm
AS per the FCFS algorithm, the job which is entered in the system will be
executed (Behera, Pattanayak, & Mallick, 2012).
A B C D E
0 15 17 31 41 42
So, from the above table it is evaluated that for job The start time is 0 and the finish
time is 15. The schedule of arriving time is BCDE and timeline is from 0 to 42 sec.
B. SJN process
It is observed that SJN system processes jobs based on numbers of CPU cycles. So, in
the given scenario the job with less CPU cycle will be processed initially rather than
other.
Job A B C D E
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 15 17 31 41 42
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NIT1202 Operating Systems
9
Arrival
time 0 2 3 6 9
Finish
time 15 18 42 28 16
A E B D C
0 15 16 18 28 42
Therefore, in the case of SJN algorithm job A will be completed within 15 minutes by
the arrival time of another job.
C. SRT system
It is identified that the SRT system permits the job with minimum times to complete
their first cycle. So, in the given question jobs about to complete will be executed
initially.
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 18 28 6 7 42
A B E A D C
0 6 7 15 18 28 42
9
Arrival
time 0 2 3 6 9
Finish
time 15 18 42 28 16
A E B D C
0 15 16 18 28 42
Therefore, in the case of SJN algorithm job A will be completed within 15 minutes by
the arrival time of another job.
C. SRT system
It is identified that the SRT system permits the job with minimum times to complete
their first cycle. So, in the given question jobs about to complete will be executed
initially.
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 18 28 6 7 42
A B E A D C
0 6 7 15 18 28 42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NIT1202 Operating Systems
10
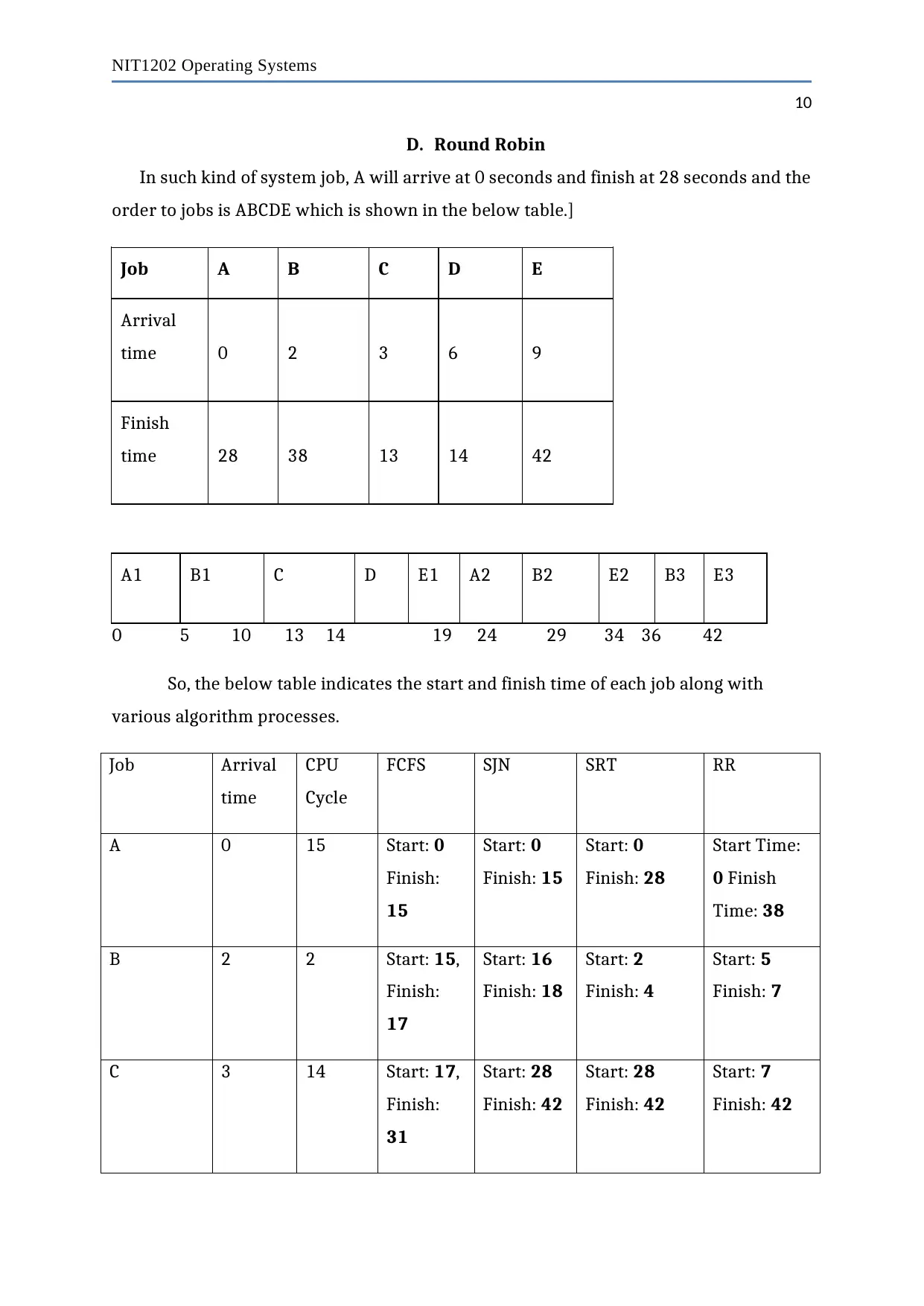
D. Round Robin
In such kind of system job, A will arrive at 0 seconds and finish at 28 seconds and the
order to jobs is ABCDE which is shown in the below table.]
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 28 38 13 14 42
A1 B1 C D E1 A2 B2 E2 B3 E3
0 5 10 13 14 19 24 29 34 36 42
So, the below table indicates the start and finish time of each job along with
various algorithm processes.
Job Arrival
time
CPU
Cycle
FCFS SJN SRT RR
A 0 15 Start: 0
Finish:
15
Start: 0
Finish: 15
Start: 0
Finish: 28
Start Time:
0 Finish
Time: 38
B 2 2 Start: 15,
Finish:
17
Start: 16
Finish: 18
Start: 2
Finish: 4
Start: 5
Finish: 7
C 3 14 Start: 17,
Finish:
31
Start: 28
Finish: 42
Start: 28
Finish: 42
Start: 7
Finish: 42
10
D. Round Robin
In such kind of system job, A will arrive at 0 seconds and finish at 28 seconds and the
order to jobs is ABCDE which is shown in the below table.]
Job A B C D E
Arrival
time 0 2 3 6 9
Finish
time 28 38 13 14 42
A1 B1 C D E1 A2 B2 E2 B3 E3
0 5 10 13 14 19 24 29 34 36 42
So, the below table indicates the start and finish time of each job along with
various algorithm processes.
Job Arrival
time
CPU
Cycle
FCFS SJN SRT RR
A 0 15 Start: 0
Finish:
15
Start: 0
Finish: 15
Start: 0
Finish: 28
Start Time:
0 Finish
Time: 38
B 2 2 Start: 15,
Finish:
17
Start: 16
Finish: 18
Start: 2
Finish: 4
Start: 5
Finish: 7
C 3 14 Start: 17,
Finish:
31
Start: 28
Finish: 42
Start: 28
Finish: 42
Start: 7
Finish: 42
NIT1202 Operating Systems
11
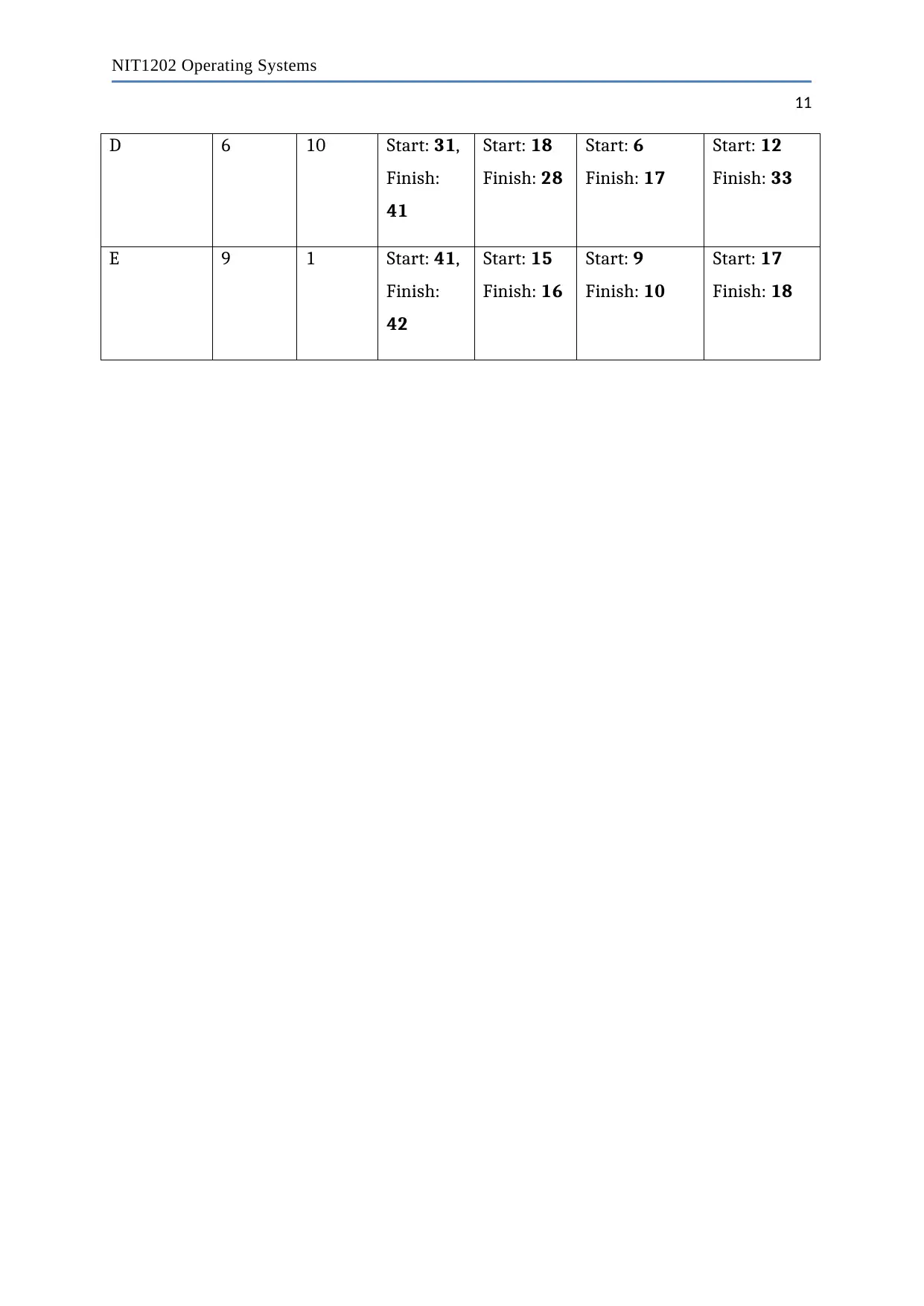
D 6 10 Start: 31,
Finish:
41
Start: 18
Finish: 28
Start: 6
Finish: 17
Start: 12
Finish: 33
E 9 1 Start: 41,
Finish:
42
Start: 15
Finish: 16
Start: 9
Finish: 10
Start: 17
Finish: 18
11
D 6 10 Start: 31,
Finish:
41
Start: 18
Finish: 28
Start: 6
Finish: 17
Start: 12
Finish: 33
E 9 1 Start: 41,
Finish:
42
Start: 15
Finish: 16
Start: 9
Finish: 10
Start: 17
Finish: 18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



