NIT6130 Research Methodology: Privacy Preservation in Cloud Computing
VerifiedAdded on 2023/06/05
|15
|2898
|229
Report
AI Summary
This report outlines a research methodology for addressing privacy preservation in cloud computing, focusing on data security. It begins by identifying the research problem and reorganizing collected literature, emphasizing privacy issues linked to cloud computing. The report discusses qualitative and quantitative methodologies, selecting a qualitative approach for its ability to comprehend views and perspectives. It reviews existing methodologies, analyzing data security challenges and their relevance. The proposed methodology involves a qualitative research design, utilizing literature review of previous research articles. The study identifies benefits, such as incorporating diverse sources for a deep understanding of cloud computing issues, and limitations, such as considering stakeholder perceptions. This document, available on Desklib, provides students with a valuable resource for understanding research methodologies in cloud computing.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 3 – METHODOLOGY
by
Rachid Hamadi
Student ID: 30099999
ASSIGNMENT 3 – METHODOLOGY
by
Rachid Hamadi
Student ID: 30099999
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Table of Contents...............................................................................................................................ii
List of Tables....................................................................................................................................iii
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................2
1.1.1 Research Problem Statement.............................................................................................2
1.1.2 Reorganized Collected Literature......................................................................................2
1.2 Types of Methodology.............................................................................................................3
1.2.1 Qualitative and Quantitative Methodologies.....................................................................3
1.2.2 Type of Chosen Methodology...........................................................................................5
1.3 Review of the Existing Methodologies.....................................................................................5
1.3.1 Selected Sub-Problem.......................................................................................................5
1.3.2 Analysis of the Selected Methodologies............................................................................6
1.3.3 Relevance of the Research Problem..................................................................................7
1.3.4 Summary of the Reviewed Methodologies........................................................................7
1.4 Proposed Methodology.............................................................................................................9
1.4.1 Identification and Justification..........................................................................................9
1.4.2 Benefits and Limitations....................................................................................................9
1.4.3 Framework and Explanation............................................................................................10
List of References............................................................................................................................12
ii
Table of Contents...............................................................................................................................ii
List of Tables....................................................................................................................................iii
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................2
1.1.1 Research Problem Statement.............................................................................................2
1.1.2 Reorganized Collected Literature......................................................................................2
1.2 Types of Methodology.............................................................................................................3
1.2.1 Qualitative and Quantitative Methodologies.....................................................................3
1.2.2 Type of Chosen Methodology...........................................................................................5
1.3 Review of the Existing Methodologies.....................................................................................5
1.3.1 Selected Sub-Problem.......................................................................................................5
1.3.2 Analysis of the Selected Methodologies............................................................................6
1.3.3 Relevance of the Research Problem..................................................................................7
1.3.4 Summary of the Reviewed Methodologies........................................................................7
1.4 Proposed Methodology.............................................................................................................9
1.4.1 Identification and Justification..........................................................................................9
1.4.2 Benefits and Limitations....................................................................................................9
1.4.3 Framework and Explanation............................................................................................10
List of References............................................................................................................................12
ii

List of Tables
1Reorganized collected literature...........................................................................................2
2Summary of reviewed methodologies....................................................................................9
iii
1Reorganized collected literature...........................................................................................2
2Summary of reviewed methodologies....................................................................................9
iii
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Chapter 1
Methodology
In this section, the paper will look into the study research design, the study area, population and
the sample population, the sampling technique, the data collection instruments and the methods
of data analysis.
The purpose of this assignment is to identify an appropriate methodology for our research topic related to
privacy preservation in cloud computing
This document is structured as follows. First a review, analysis and summary of the existing
methodologies reported in the collected literatures will be given. Then, the methodology to be used will
be proposed to solve the selected research problem. My research will adopt. There were three peer
reviewed articles on cloud computing that were analyzed in the literature review to collect
necessary data and make a solid conclusion on the issue of privacy and security in cloud
computing.
1
Methodology
In this section, the paper will look into the study research design, the study area, population and
the sample population, the sampling technique, the data collection instruments and the methods
of data analysis.
The purpose of this assignment is to identify an appropriate methodology for our research topic related to
privacy preservation in cloud computing
This document is structured as follows. First a review, analysis and summary of the existing
methodologies reported in the collected literatures will be given. Then, the methodology to be used will
be proposed to solve the selected research problem. My research will adopt. There were three peer
reviewed articles on cloud computing that were analyzed in the literature review to collect
necessary data and make a solid conclusion on the issue of privacy and security in cloud
computing.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.1 Research Problem and Reorganized Collected Literature
1.1.1 Research Problem Statement
There are several privacy issues linked with cloud computing. This issue has raised a lot of
concern as people are losing sensitive information to malicious individuals who use these data
for their own benefit and to cause harm.
1.1.2 Reorganized Collected Literature
Research Problem Sub-problem Collected Literature
Problem 1 Sub-problem 1 Literature 1
Literature 2
…
Privacy issues linked
with cloud computing
The issues of privacy in
cloud computing can be
grouped into two; that is
privacy issues that
clients using the cloud
network face and the
security issues that
cloud computing service
providers face.
1Reorganized collected literature
2
1.1.1 Research Problem Statement
There are several privacy issues linked with cloud computing. This issue has raised a lot of
concern as people are losing sensitive information to malicious individuals who use these data
for their own benefit and to cause harm.
1.1.2 Reorganized Collected Literature
Research Problem Sub-problem Collected Literature
Problem 1 Sub-problem 1 Literature 1
Literature 2
…
Privacy issues linked
with cloud computing
The issues of privacy in
cloud computing can be
grouped into two; that is
privacy issues that
clients using the cloud
network face and the
security issues that
cloud computing service
providers face.
1Reorganized collected literature
2

1.2 Types of Methodology
1.2.1 Qualitative and Quantitative Methodologies
There are several research methodologies but the two most common research methodologies
include qualitative and quantitative research. Qualitative research is basically an investigation.
The use of qualitative research is to improve the comprehension of vital details, opinions, and
inspirations. The qualitative research approach conveys visualizations into the problematic or
assists in growing of thoughts or grounds for probable quantitative research.
Additionally, qualitative research is useful in exposing tendencies in hypothesis and thoughts,
and dive deeper into the issue in question.
The collected data differs in terms of their forms and structure. Some of the shared approach of
qualitative research design include a focus on collections, contribution and distinct conferences.
On the other hand, quantitative Research is utilized to specify issues by strategy for delivering
statistical data or information that can be moulded into reasonable figures. It is utilized to
measure arrogances, considerations, performances, and other particular factors and misrepresent
results from a more noteworthy sample population. Quantitative Research utilizes quantifiable
data to express facts and find outlines in analysis. Quantitative information gathering approaches
are inexhaustible more composed than Qualitative information gathering approaches.
Quantitative information gathering approaches include various strategies for reviews.
Likewise, In quantitative research the point is to determine the connection between a certain
independent variable and another dependent variable in a population. Quantitative research
3
1.2.1 Qualitative and Quantitative Methodologies
There are several research methodologies but the two most common research methodologies
include qualitative and quantitative research. Qualitative research is basically an investigation.
The use of qualitative research is to improve the comprehension of vital details, opinions, and
inspirations. The qualitative research approach conveys visualizations into the problematic or
assists in growing of thoughts or grounds for probable quantitative research.
Additionally, qualitative research is useful in exposing tendencies in hypothesis and thoughts,
and dive deeper into the issue in question.
The collected data differs in terms of their forms and structure. Some of the shared approach of
qualitative research design include a focus on collections, contribution and distinct conferences.
On the other hand, quantitative Research is utilized to specify issues by strategy for delivering
statistical data or information that can be moulded into reasonable figures. It is utilized to
measure arrogances, considerations, performances, and other particular factors and misrepresent
results from a more noteworthy sample population. Quantitative Research utilizes quantifiable
data to express facts and find outlines in analysis. Quantitative information gathering approaches
are inexhaustible more composed than Qualitative information gathering approaches.
Quantitative information gathering approaches include various strategies for reviews.
Likewise, In quantitative research the point is to determine the connection between a certain
independent variable and another dependent variable in a population. Quantitative research
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

outlines are either enlightening (subjects typically estimated once) or trial (subjects estimated
when a treatment). A graphic report sets up just relationship between factors. An experiment
builds up causality. For a precise gauge of the connection between variables, an sample study for
the most part needs an hundreds or even a thousands of subjects; a trial, particularly a hybrid,
may require just several subjects. The gauge of the relationship is more averse to be one-sided on
the off chance that you have a high cooperation rate in an sample chosen haphazardly from a
population. In tests, bias is additionally more improbable if subjects are arbitrarily allocated to
treatments, and if subjects and specialists are oblivious to the character of the treatment. In all
experiments, subject qualities can influence the relationship one is researching. Limit their
impact either by utilizing a less heterogeneous sample of subjects or ideally by estimating the
attributes and incorporating them in the investigation.
Qualitative data is the one which can only be described but not measured, whereas quantitative
data can be measured. So, the qualitative data develop a hypothesis, while the quantitative
research test the hypothesis by means of statistical analysis.
This paper will make use of qualitative research methodology because the method is every so
often viewed as a antecedent to quantitative research, as it is generally used in the generation of
possible ideas and leads that are useful in formulation of realistic and testable hypothesis. This
hypothesis can subsequently be much more comprehensively tested and analyzed mathematically
using standard quantitative methods of research. Basing on this reason, qualitative methods are
usually related to survey design methods as well as individual case studies as a method of
reinforcing and evaluating findings.
4
when a treatment). A graphic report sets up just relationship between factors. An experiment
builds up causality. For a precise gauge of the connection between variables, an sample study for
the most part needs an hundreds or even a thousands of subjects; a trial, particularly a hybrid,
may require just several subjects. The gauge of the relationship is more averse to be one-sided on
the off chance that you have a high cooperation rate in an sample chosen haphazardly from a
population. In tests, bias is additionally more improbable if subjects are arbitrarily allocated to
treatments, and if subjects and specialists are oblivious to the character of the treatment. In all
experiments, subject qualities can influence the relationship one is researching. Limit their
impact either by utilizing a less heterogeneous sample of subjects or ideally by estimating the
attributes and incorporating them in the investigation.
Qualitative data is the one which can only be described but not measured, whereas quantitative
data can be measured. So, the qualitative data develop a hypothesis, while the quantitative
research test the hypothesis by means of statistical analysis.
This paper will make use of qualitative research methodology because the method is every so
often viewed as a antecedent to quantitative research, as it is generally used in the generation of
possible ideas and leads that are useful in formulation of realistic and testable hypothesis. This
hypothesis can subsequently be much more comprehensively tested and analyzed mathematically
using standard quantitative methods of research. Basing on this reason, qualitative methods are
usually related to survey design methods as well as individual case studies as a method of
reinforcing and evaluating findings.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.2.2 Type of Chosen Methodology
I will make use of qualitative methodology as it helps in comprehension of views and
perspectives. The method offers clear vision to diverse issues in addition to developing theories
and concepts of likely quantitative research.
With detailed analysis looking into problems, the qualitative approach also would help in
discovering individual and new thoughts towards the subject matter. The method makes use of
different kinds of structured and semi structured approaches to data collection including
discussions, interviews, journal exercises and the participation of others.
1.3 Review of the Existing Methodologies
1.3.1 Selected Sub-Problem
Data security will be the main issue the research paper will focus on.
1.3.2 Analysis of the Selected Methodologies
The prime goal of the cloud computing service providers is to give sufficient security to its
clients as the services are utilized in important business endeavors and also in government
associations. Be that as it may, it is discovered that there are several issues identified with the
integration of the cloud computing in various kinds of undertakings, for example, the security
issues, information issues, legal issues and dependability issues.
Xia et al. (2016) notes that there are two classifications of issues in a company one from the
perspective of the inner partners and the other is from the perspective of the outer partners. The
5
I will make use of qualitative methodology as it helps in comprehension of views and
perspectives. The method offers clear vision to diverse issues in addition to developing theories
and concepts of likely quantitative research.
With detailed analysis looking into problems, the qualitative approach also would help in
discovering individual and new thoughts towards the subject matter. The method makes use of
different kinds of structured and semi structured approaches to data collection including
discussions, interviews, journal exercises and the participation of others.
1.3 Review of the Existing Methodologies
1.3.1 Selected Sub-Problem
Data security will be the main issue the research paper will focus on.
1.3.2 Analysis of the Selected Methodologies
The prime goal of the cloud computing service providers is to give sufficient security to its
clients as the services are utilized in important business endeavors and also in government
associations. Be that as it may, it is discovered that there are several issues identified with the
integration of the cloud computing in various kinds of undertakings, for example, the security
issues, information issues, legal issues and dependability issues.
Xia et al. (2016) notes that there are two classifications of issues in a company one from the
perspective of the inner partners and the other is from the perspective of the outer partners. The
5

cloud computing is utilized to store and recover vital data, essential projects and frameworks up
and running into the server.
Furthermore, Sun et al. (2014) emphasizes that the security issues related with cloud computing
are of numerous kinds, for example, the risks originating from the merchants of the distinctive
endeavors who utilize cloud servers for a significant lot of time and furthermore from the global
legal information exchange between two associations.
Similarly, Tari et al. (2014) outlines that cloud computing is one of the strategies by which the
internal and in addition the outer partners of an undertaking speak with one another to achieve
higher efficiency for the association. It very well may be seen that in a few circumstances the
vendors of an organization need to give a type of security to the customers on the security issue,
thus varied forms of cloud computing infrastructure such as IaaS is required. Be that as it may,
there are diverse sorts of security issues related with each cloud computing services as outlined
below;
Data Breaches: Some hacker could access our data and misuse that data. As the data is
present in the servers of the service provide, so to always at risk.
Account hijacking: An account can be taken over by an unauthorized party and data
present be misused.
Insider Threat: The employees in an organization can have access to some data which
they are restricted from using without supervision. They may end up misusing the data.
6
and running into the server.
Furthermore, Sun et al. (2014) emphasizes that the security issues related with cloud computing
are of numerous kinds, for example, the risks originating from the merchants of the distinctive
endeavors who utilize cloud servers for a significant lot of time and furthermore from the global
legal information exchange between two associations.
Similarly, Tari et al. (2014) outlines that cloud computing is one of the strategies by which the
internal and in addition the outer partners of an undertaking speak with one another to achieve
higher efficiency for the association. It very well may be seen that in a few circumstances the
vendors of an organization need to give a type of security to the customers on the security issue,
thus varied forms of cloud computing infrastructure such as IaaS is required. Be that as it may,
there are diverse sorts of security issues related with each cloud computing services as outlined
below;
Data Breaches: Some hacker could access our data and misuse that data. As the data is
present in the servers of the service provide, so to always at risk.
Account hijacking: An account can be taken over by an unauthorized party and data
present be misused.
Insider Threat: The employees in an organization can have access to some data which
they are restricted from using without supervision. They may end up misusing the data.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Malware Addition: viruses or malicious code can be injected into the organization or a
person account in an attempt to corrupt files or gain access to some hidden information.
This may go unnoticed as it would seem as if the cloud software is running normally.
1.3.3 Relevance of the Research Problem
The research problem, that is security of data with advancement of IT infrastructure is of high relevance.
The paper is useful in discussing on data integrity, data confidentiality, data privacy and data availability
1.3.4 Summary of the Reviewed Methodologies
Literature # Research Problem Methodology Your Sub-problem Relevance
A privacy-
preserving
and copy-
deterrence
content-
based
image
retrieval
scheme in
cloud
computing.
For the purposes of
preserving privacy
of data, sensitive
images have to be
encrypted before
outsourcing thus
making the plain text
sphere to be
ineffectual
Qualitative
approach was
used to
researching on
different forms
in which data
have been
encrypted and
stored to
enhance data
security.
Data encryption is
yet to be wholly
used by
organizations.
Data encryption
and decryption is
challenging for
most users of IT
infrastructure.
High - data
encryption is
particularly
relevant to
enhance
privacy and
security of
information.
Data
security
and privacy
in cloud
computing.
Data security has
constantly been the
main problem in
information
technology.
Within the
environment of
cloud computing,
Qualitative
approach was
used looking
into detail
different
research
materials to
discuss data
integrity, data
confidentiality,
data privacy and
data availability
Security of data
has been an issue
of concern with
many platforms
requiring
permission to
access personal
data
High - The
paper is useful
in discussing
on data
integrity, data
confidentiality,
data privacy
and data
availability
7
person account in an attempt to corrupt files or gain access to some hidden information.
This may go unnoticed as it would seem as if the cloud software is running normally.
1.3.3 Relevance of the Research Problem
The research problem, that is security of data with advancement of IT infrastructure is of high relevance.
The paper is useful in discussing on data integrity, data confidentiality, data privacy and data availability
1.3.4 Summary of the Reviewed Methodologies
Literature # Research Problem Methodology Your Sub-problem Relevance
A privacy-
preserving
and copy-
deterrence
content-
based
image
retrieval
scheme in
cloud
computing.
For the purposes of
preserving privacy
of data, sensitive
images have to be
encrypted before
outsourcing thus
making the plain text
sphere to be
ineffectual
Qualitative
approach was
used to
researching on
different forms
in which data
have been
encrypted and
stored to
enhance data
security.
Data encryption is
yet to be wholly
used by
organizations.
Data encryption
and decryption is
challenging for
most users of IT
infrastructure.
High - data
encryption is
particularly
relevant to
enhance
privacy and
security of
information.
Data
security
and privacy
in cloud
computing.
Data security has
constantly been the
main problem in
information
technology.
Within the
environment of
cloud computing,
Qualitative
approach was
used looking
into detail
different
research
materials to
discuss data
integrity, data
confidentiality,
data privacy and
data availability
Security of data
has been an issue
of concern with
many platforms
requiring
permission to
access personal
data
High - The
paper is useful
in discussing
on data
integrity, data
confidentiality,
data privacy
and data
availability
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
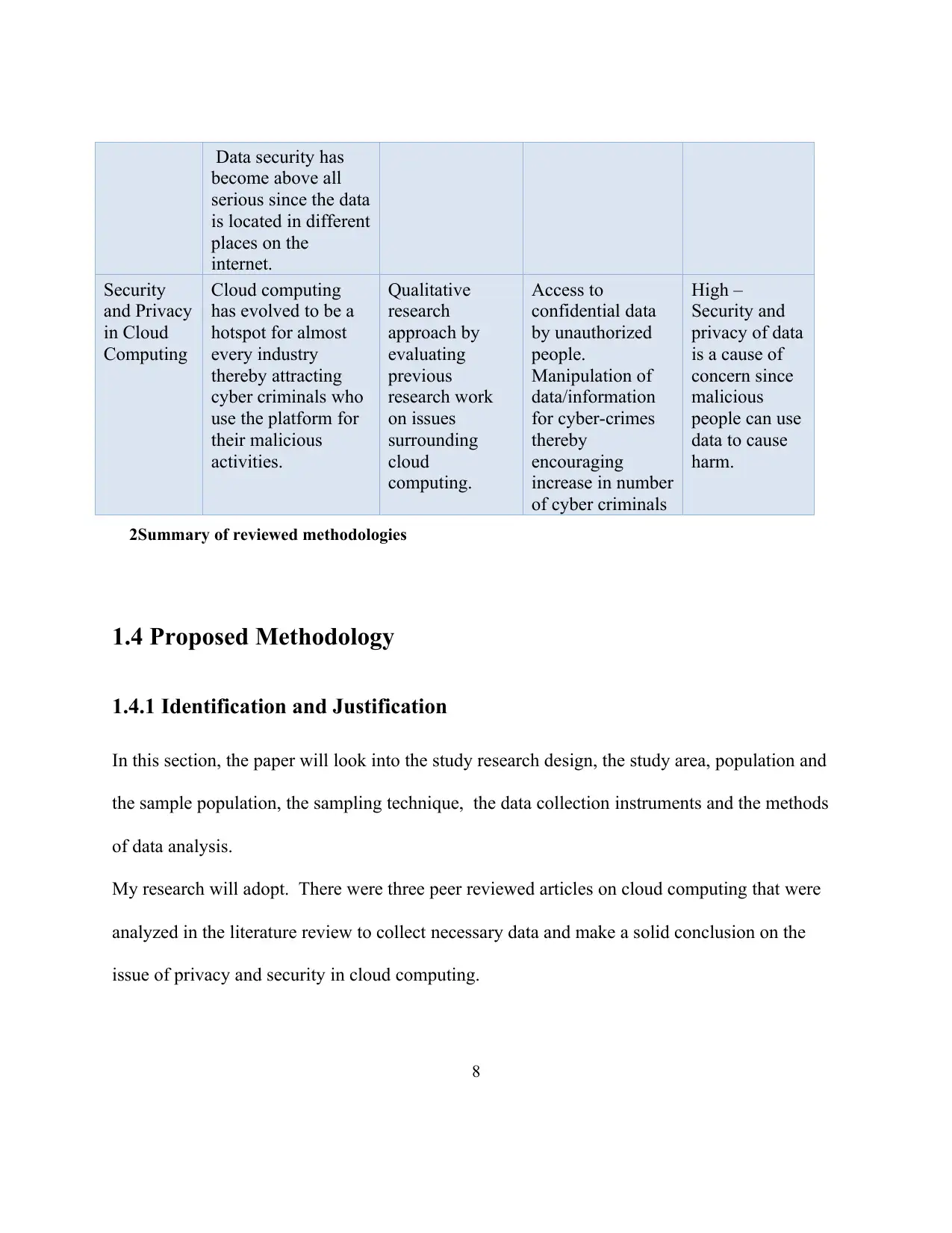
Data security has
become above all
serious since the data
is located in different
places on the
internet.
Security
and Privacy
in Cloud
Computing
Cloud computing
has evolved to be a
hotspot for almost
every industry
thereby attracting
cyber criminals who
use the platform for
their malicious
activities.
Qualitative
research
approach by
evaluating
previous
research work
on issues
surrounding
cloud
computing.
Access to
confidential data
by unauthorized
people.
Manipulation of
data/information
for cyber-crimes
thereby
encouraging
increase in number
of cyber criminals
High –
Security and
privacy of data
is a cause of
concern since
malicious
people can use
data to cause
harm.
2Summary of reviewed methodologies
1.4 Proposed Methodology
1.4.1 Identification and Justification
In this section, the paper will look into the study research design, the study area, population and
the sample population, the sampling technique, the data collection instruments and the methods
of data analysis.
My research will adopt. There were three peer reviewed articles on cloud computing that were
analyzed in the literature review to collect necessary data and make a solid conclusion on the
issue of privacy and security in cloud computing.
8
become above all
serious since the data
is located in different
places on the
internet.
Security
and Privacy
in Cloud
Computing
Cloud computing
has evolved to be a
hotspot for almost
every industry
thereby attracting
cyber criminals who
use the platform for
their malicious
activities.
Qualitative
research
approach by
evaluating
previous
research work
on issues
surrounding
cloud
computing.
Access to
confidential data
by unauthorized
people.
Manipulation of
data/information
for cyber-crimes
thereby
encouraging
increase in number
of cyber criminals
High –
Security and
privacy of data
is a cause of
concern since
malicious
people can use
data to cause
harm.
2Summary of reviewed methodologies
1.4 Proposed Methodology
1.4.1 Identification and Justification
In this section, the paper will look into the study research design, the study area, population and
the sample population, the sampling technique, the data collection instruments and the methods
of data analysis.
My research will adopt. There were three peer reviewed articles on cloud computing that were
analyzed in the literature review to collect necessary data and make a solid conclusion on the
issue of privacy and security in cloud computing.
8

1.4.2 Benefits and Limitations
Benefits of the study
The study is beneficial as it incorporates information from various sources useful in providing a
deep understanding of issues surrounding cloud computing technologies
Limitations of the study methodology
In this study, the perceptions, opinions and options of all stakeholders involved with the use of
Information technology infrastructure are sought and taken into account to give outline some of
the most significant issues in cloud computing.
1.4.3 Framework and Explanation
Research design
The paper a qualitative research design approach given that the approach best served to answer
the questions and the purposes of the study. The qualitative research is one in which several
research articles on the topic in question are studied by evaluating the data collected which is
considered to be representative of the subject matter. This is to say, only sample research
documents are studied, and findings from these articles are expected to be generalized to the
entire research.
Population of the study
Given that a qualitative approach was used, there was no specific target population under study.
Literature review of previous research articles was used for the study.
Method of data collection
9
Benefits of the study
The study is beneficial as it incorporates information from various sources useful in providing a
deep understanding of issues surrounding cloud computing technologies
Limitations of the study methodology
In this study, the perceptions, opinions and options of all stakeholders involved with the use of
Information technology infrastructure are sought and taken into account to give outline some of
the most significant issues in cloud computing.
1.4.3 Framework and Explanation
Research design
The paper a qualitative research design approach given that the approach best served to answer
the questions and the purposes of the study. The qualitative research is one in which several
research articles on the topic in question are studied by evaluating the data collected which is
considered to be representative of the subject matter. This is to say, only sample research
documents are studied, and findings from these articles are expected to be generalized to the
entire research.
Population of the study
Given that a qualitative approach was used, there was no specific target population under study.
Literature review of previous research articles was used for the study.
Method of data collection
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





