IT Security Issues in Cloud Database: A Capstone Project Paper
VerifiedAdded on 2023/06/11
|13
|2201
|304
Capstone Project
AI Summary
This capstone project paper addresses the critical issue of IT security in cloud-based databases within an IT services organization. It begins by outlining the organization's evolution, core functions, and enabling technologies, highlighting the increasing reliance on cloud technology. The central business problem identified is the lack of security for sensitive information, leading to potential misuse and infringement of data due to innovative threat agents. Supporting research emphasizes the growing impact of cybercrimes on IT services. The paper then explores the organizational impact, detailing the risks faced by stakeholders like customers, end-users, the company board, IT and finance teams. Potential solutions, including encryption, firewall security, and limited user access, are discussed, along with previous attempts to address these issues. The recommended solution involves implementing biometric security measures to enhance information system protection. Implementation considerations include technology innovation, infrastructure development, and resource allocation. Finally, the paper reflects on the application of coursework from UONA, highlighting the significance of the project in understanding and deploying improved operational development, concluding that technology innovation is crucial for ensuring effective and secure utilization of cloud-based IT services.

CAPSTONE PROJECT PAPER
by
Student Name
Submitted in Partial Fulfillment of the Requirements for the
[MSIT/MBA/MSCS] Degree Program
University of North America
Year
by
Student Name
Submitted in Partial Fulfillment of the Requirements for the
[MSIT/MBA/MSCS] Degree Program
University of North America
Year
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The alignment of the activities had been formed for developing the implication of the
operations for listing the smart processing of the IT services. However, the security issues of
the cloud based database have been acting as major threat for the organization. The
innovative threat agent had resulted in forming the major threat for the organization and it
also formed the major factor for harming the utilization of the information technology. The
misuse and infringement of the data acted as a major problem for the organization.
i
The alignment of the activities had been formed for developing the implication of the
operations for listing the smart processing of the IT services. However, the security issues of
the cloud based database have been acting as major threat for the organization. The
innovative threat agent had resulted in forming the major threat for the organization and it
also formed the major factor for harming the utilization of the information technology. The
misuse and infringement of the data acted as a major problem for the organization.
i

Section 1
Introduction
1.1 Description of Organization
1.1.1 Evolution of the organization (history)
The IT services organization has been growing ever since the last few decades with the
advent of smarter method of technology innovation and provision for the development
of the activities (Shabana et al., 2016). The IT services started with the advent of the
computer technology. Initially Dos based data support system was introduced and many
organizations started using it for their operations. However, with the possible technology
innovations, the database technology has also seen remarkable growth and development.
The innovation technology has also seen considerable growth and development. The
alignment of the activities would also show the considerations of the improved
technology development.
1.1.2 Core Functions
The implication of the operations had been successively aligned for forming the
development of technology favoring the modification of services. The alignment of the
activities would also be formed for developing the implication of the operations for
listing the smart processing of the IT services (Singh et al., 2016). The effective services
and development had been supported for the implication of the cloud based technology
services for the customers. The allocation of the effective services had helped them for
forming the effective utilization of the functions. It is possible that the supportive
development of the operations like,
Technology Support
1
Introduction
1.1 Description of Organization
1.1.1 Evolution of the organization (history)
The IT services organization has been growing ever since the last few decades with the
advent of smarter method of technology innovation and provision for the development
of the activities (Shabana et al., 2016). The IT services started with the advent of the
computer technology. Initially Dos based data support system was introduced and many
organizations started using it for their operations. However, with the possible technology
innovations, the database technology has also seen remarkable growth and development.
The innovation technology has also seen considerable growth and development. The
alignment of the activities would also show the considerations of the improved
technology development.
1.1.2 Core Functions
The implication of the operations had been successively aligned for forming the
development of technology favoring the modification of services. The alignment of the
activities would also be formed for developing the implication of the operations for
listing the smart processing of the IT services (Singh et al., 2016). The effective services
and development had been supported for the implication of the cloud based technology
services for the customers. The allocation of the effective services had helped them for
forming the effective utilization of the functions. It is possible that the supportive
development of the operations like,
Technology Support
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Customer Services
Portal Deployment
Maintenance renewal
1.1.3 Enabling Technologies
The management of the services has supported the effective innovation and
development. The use of the innovations had helped in developing the improved
technology development (Sen, 2015). The cloud based technology has been supported
by the IT service organization. The deployment of the technology innovation would also
help in forming the alignment of the activities. The cloud innovation and support would
form the allocation of the activities. The technology innovation would support the
diversified actions for the listing the deployment of the activities.
1.2 Business Problem
The IT service organizations have been facing the core problem of lack of security
of information with the technology innovation. The business development had supported the
management of the activities and forming the utilization and forming the implicational
development of the activities. The security issues of the cloud based database have been
acting as major threat for the organization. The innovative threat agents have resulted in
forming the major threat for the organization and it would also form the major factor for
harming the utilization of the information technology. The misuse and infringement of the
data is a major problem for the organization.
1.3 Supporting Research
According to Loo et al., (2016), the various cyber crimes and threats have formed
the major impact for harming the development of the IT services. The effective alignment
2
Portal Deployment
Maintenance renewal
1.1.3 Enabling Technologies
The management of the services has supported the effective innovation and
development. The use of the innovations had helped in developing the improved
technology development (Sen, 2015). The cloud based technology has been supported
by the IT service organization. The deployment of the technology innovation would also
help in forming the alignment of the activities. The cloud innovation and support would
form the allocation of the activities. The technology innovation would support the
diversified actions for the listing the deployment of the activities.
1.2 Business Problem
The IT service organizations have been facing the core problem of lack of security
of information with the technology innovation. The business development had supported the
management of the activities and forming the utilization and forming the implicational
development of the activities. The security issues of the cloud based database have been
acting as major threat for the organization. The innovative threat agents have resulted in
forming the major threat for the organization and it would also form the major factor for
harming the utilization of the information technology. The misuse and infringement of the
data is a major problem for the organization.
1.3 Supporting Research
According to Loo et al., (2016), the various cyber crimes and threats have formed
the major impact for harming the development of the IT services. The effective alignment
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

had resulted in causing the issues of management and activities. The recent attacks on the
computer devices has resulted in making people aware of the situation and withdrawing role
for the development of the activities. Fernandes et al. (2014) have stated that the various
cyber threats of the organization have resulted in the growth of problems for the
organization. The research problems would result in forming the major setback for the
growth of technology development. It is possible that the development of the major
problems for the organization would result in forming the hindrances for the allowance of
the activities. According to Thayananthan and Albeshri (2015), the threat agents have
resulted in harming the implication of the innovation technology and forming the major
setback for the development of the operational issues.
Section 2
Impact
2.1 Organizational Impact
The security issues have resulted in forming the major problems for the completion
of the project activities. The alignment of the operations had supported the activities for
listing the major alignment of the activities (Hossain, Fotouhi & Hasan, 2015). The
development of the successive alignment would allow the utilization of the improved
operation development. The organization would have to face severe issues of the
development factors and alignment of the activities forming the implication of the project
development. The impact of the project organization had formed the development of the
successive implementation of the activities. The issues have resulted in forming the major
setback for the organization.
3
computer devices has resulted in making people aware of the situation and withdrawing role
for the development of the activities. Fernandes et al. (2014) have stated that the various
cyber threats of the organization have resulted in the growth of problems for the
organization. The research problems would result in forming the major setback for the
growth of technology development. It is possible that the development of the major
problems for the organization would result in forming the hindrances for the allowance of
the activities. According to Thayananthan and Albeshri (2015), the threat agents have
resulted in harming the implication of the innovation technology and forming the major
setback for the development of the operational issues.
Section 2
Impact
2.1 Organizational Impact
The security issues have resulted in forming the major problems for the completion
of the project activities. The alignment of the operations had supported the activities for
listing the major alignment of the activities (Hossain, Fotouhi & Hasan, 2015). The
development of the successive alignment would allow the utilization of the improved
operation development. The organization would have to face severe issues of the
development factors and alignment of the activities forming the implication of the project
development. The impact of the project organization had formed the development of the
successive implementation of the activities. The issues have resulted in forming the major
setback for the organization.
3
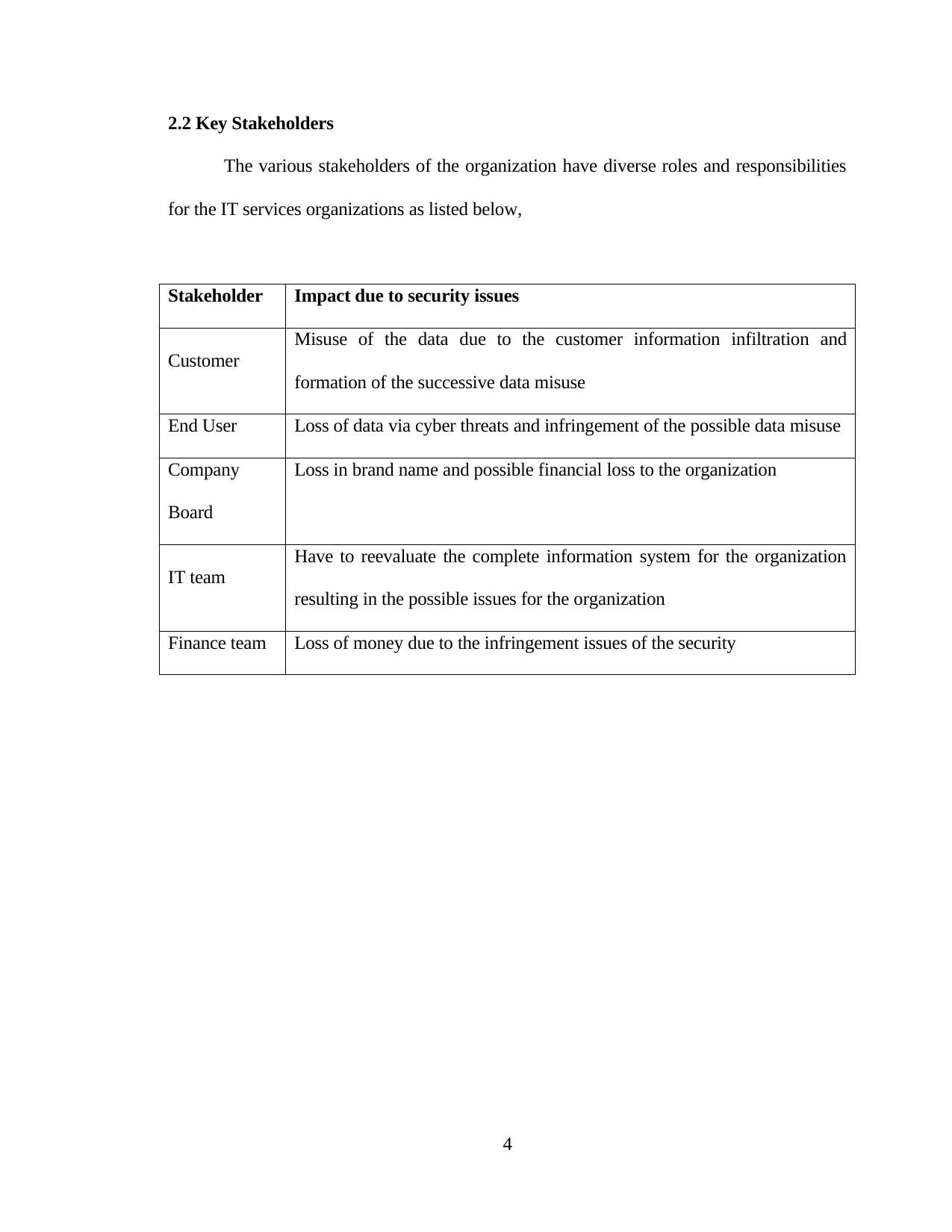
2.2 Key Stakeholders
The various stakeholders of the organization have diverse roles and responsibilities
for the IT services organizations as listed below,
Stakeholder Impact due to security issues
Customer
Misuse of the data due to the customer information infiltration and
formation of the successive data misuse
End User Loss of data via cyber threats and infringement of the possible data misuse
Company
Board
Loss in brand name and possible financial loss to the organization
IT team
Have to reevaluate the complete information system for the organization
resulting in the possible issues for the organization
Finance team Loss of money due to the infringement issues of the security
4
The various stakeholders of the organization have diverse roles and responsibilities
for the IT services organizations as listed below,
Stakeholder Impact due to security issues
Customer
Misuse of the data due to the customer information infiltration and
formation of the successive data misuse
End User Loss of data via cyber threats and infringement of the possible data misuse
Company
Board
Loss in brand name and possible financial loss to the organization
IT team
Have to reevaluate the complete information system for the organization
resulting in the possible issues for the organization
Finance team Loss of money due to the infringement issues of the security
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Section 3
Solutions
3.1 Potential Solutions
The security issues of the organization can be sorted out by the use of the effective
and infused technology innovation development (Janowitz, 2017). The solutions of the
organization had been aligned for the management of the activities for forming the
alignment of the operations. The potential solution of the project activities had been formed
for the utilization of the innovative technologies and operations. The support and
development of the operations had also supported the implication of the activities for
forming the utilization of the effective activity development. The solutions for the security
are use of,
Encryption and authorization
Firewall Security for the information
Limited User Access in the system
3.2 Previous Attempts to Solve Problem (if applicable)
There have been various possible attempts for resolving the issues of the
organization and forming the limitation of the activities forming the management of the
operational issues for the organization (Rao & Selvamani, 2015). The alignment issues can
be resolved using the formation of the successive development of the improved security
functions. The alignment of the security functions would probably help the organization for
listing the opportunities forming the development of the activities for listing the deployment.
The listing of the activities had supported the implication for forming the management of
the activities.
5
Solutions
3.1 Potential Solutions
The security issues of the organization can be sorted out by the use of the effective
and infused technology innovation development (Janowitz, 2017). The solutions of the
organization had been aligned for the management of the activities for forming the
alignment of the operations. The potential solution of the project activities had been formed
for the utilization of the innovative technologies and operations. The support and
development of the operations had also supported the implication of the activities for
forming the utilization of the effective activity development. The solutions for the security
are use of,
Encryption and authorization
Firewall Security for the information
Limited User Access in the system
3.2 Previous Attempts to Solve Problem (if applicable)
There have been various possible attempts for resolving the issues of the
organization and forming the limitation of the activities forming the management of the
operational issues for the organization (Rao & Selvamani, 2015). The alignment issues can
be resolved using the formation of the successive development of the improved security
functions. The alignment of the security functions would probably help the organization for
listing the opportunities forming the development of the activities for listing the deployment.
The listing of the activities had supported the implication for forming the management of
the activities.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6

Section 4
Recommendations
4.1 Recommended Solution
Implication of the Biometric solution would align for listing the development of the
security operations and it would also form the utilization for keeping the information system
secured. The deployment of the biometric solution would allow the utilization for the
formation of the deployed development. The biometric solution would help in ensuring that
unauthorized activities resulting in the major setback for the development of the activities
would form the issues for the organizational development.
4.2 Implementation Considerations
The implementation would consider the utilization of the innovative technology for
developing the improved operation development (Chelli, 2015). The deployment of the
activities would favor the support and utilization of the innovative technology implication.
The biometric security would require,
Abundance of technology innovation
Formation of the infrastructure for the activities
Security online development
However, the deployment of the technology would consume a sufficient amount of
resources in terms of money, human, and materials. The complete infrastructure renovation
would be required for the implication.
7
Recommendations
4.1 Recommended Solution
Implication of the Biometric solution would align for listing the development of the
security operations and it would also form the utilization for keeping the information system
secured. The deployment of the biometric solution would allow the utilization for the
formation of the deployed development. The biometric solution would help in ensuring that
unauthorized activities resulting in the major setback for the development of the activities
would form the issues for the organizational development.
4.2 Implementation Considerations
The implementation would consider the utilization of the innovative technology for
developing the improved operation development (Chelli, 2015). The deployment of the
activities would favor the support and utilization of the innovative technology implication.
The biometric security would require,
Abundance of technology innovation
Formation of the infrastructure for the activities
Security online development
However, the deployment of the technology would consume a sufficient amount of
resources in terms of money, human, and materials. The complete infrastructure renovation
would be required for the implication.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Section 5
Contribution from Coursework
5.1 Application of Learning
The use of the technology innovation would require a great deal for skill sets and
alignment of the knowledge for the technology innovation. The implication of the activities
would also be helpful for aligning the utilization of the activities. The study at UONA
provided a great deal of understanding the prospect of using existing literature and
deploying improved operation development. The learning management had supported the
utilization of the activities for forming the alignment of the improved operation
development via learning and innovation.
5.2 Significance of Project
The project of study had helped in forming the understanding for the alignment of
the improved innovation for the project development. The various study materials had
supported the alignment of the utilization of the operations forming the deployment of the
complete innovation.
5.3 Reflections
I had been using the technology innovation is formed for listing the utilization of the
activities for aligning the implication of the development. The study helped me in forming
the gain in the knowledge and skill sets for the development of the improved activity
development. The implication of the project study was also helpful for forming the
utilization of the operations and listing the innovation of the successful technology
development.
8
Contribution from Coursework
5.1 Application of Learning
The use of the technology innovation would require a great deal for skill sets and
alignment of the knowledge for the technology innovation. The implication of the activities
would also be helpful for aligning the utilization of the activities. The study at UONA
provided a great deal of understanding the prospect of using existing literature and
deploying improved operation development. The learning management had supported the
utilization of the activities for forming the alignment of the improved operation
development via learning and innovation.
5.2 Significance of Project
The project of study had helped in forming the understanding for the alignment of
the improved innovation for the project development. The various study materials had
supported the alignment of the utilization of the operations forming the deployment of the
complete innovation.
5.3 Reflections
I had been using the technology innovation is formed for listing the utilization of the
activities for aligning the implication of the development. The study helped me in forming
the gain in the knowledge and skill sets for the development of the improved activity
development. The implication of the project study was also helpful for forming the
utilization of the operations and listing the innovation of the successful technology
development.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Section 6
Conclusions
6.1 Conclusions
It can be concluded that the utilization of the technology innovation would be
helpful for supporting the implication of the activities and formation of the operations so
that the effective utilization of the innovation can be achieved. The study had shown that the
limited access to the technology innovation would support the implication of the improved
activity development. The alignment of the activities would also support the utilization of
the processes for listing the innovation development operations. The utilization of the
improved activity development would help them for forming the utilization of the improved
operation development.
9
Conclusions
6.1 Conclusions
It can be concluded that the utilization of the technology innovation would be
helpful for supporting the implication of the activities and formation of the operations so
that the effective utilization of the innovation can be achieved. The study had shown that the
limited access to the technology innovation would support the implication of the improved
activity development. The alignment of the activities would also support the utilization of
the processes for listing the innovation development operations. The utilization of the
improved activity development would help them for forming the utilization of the improved
operation development.
9

References
Chelli, K. (2015, July). Security issues in wireless sensor networks: attacks and
countermeasures. In Proceedings of the World Congress on Engineering (Vol. 1, pp. 1-3).
Fernandes, D. A., Soares, L. F., Gomes, J. V., Freire, M. M., & Inácio, P. R. (2014).
Security issues in cloud environments: a survey. International Journal of Information
Security, 13(2), 113-170.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015, June). Towards an analysis of security
issues, challenges, and open problems in the internet of things. In Services (SERVICES),
2015 IEEE World Congress on (pp. 21-28). IEEE.
Janowitz, M. (2017). The professional soldier: A social and political portrait. Simon and
Schuster.
Loo, J., Mauri, J. L., & Ortiz, J. H. (Eds.). (2016). Mobile ad hoc networks: current status
and future trends. CRC Press.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Rao, R. V., & Selvamani, K. (2015). Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, 204-209.
Sen, J. (2015). Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Shabana, K., Fida, N., Khan, F., Jan, S. R., & Rehman, M. U. (2016). Security issues and
attacks in Wireless Sensor Networks. International Journal of Advanced Research in
Computer Science and Electronics Engineering (IJARCSEE), 5(7), pp-81.
10
Chelli, K. (2015, July). Security issues in wireless sensor networks: attacks and
countermeasures. In Proceedings of the World Congress on Engineering (Vol. 1, pp. 1-3).
Fernandes, D. A., Soares, L. F., Gomes, J. V., Freire, M. M., & Inácio, P. R. (2014).
Security issues in cloud environments: a survey. International Journal of Information
Security, 13(2), 113-170.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015, June). Towards an analysis of security
issues, challenges, and open problems in the internet of things. In Services (SERVICES),
2015 IEEE World Congress on (pp. 21-28). IEEE.
Janowitz, M. (2017). The professional soldier: A social and political portrait. Simon and
Schuster.
Loo, J., Mauri, J. L., & Ortiz, J. H. (Eds.). (2016). Mobile ad hoc networks: current status
and future trends. CRC Press.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Rao, R. V., & Selvamani, K. (2015). Data security challenges and its solutions in cloud
computing. Procedia Computer Science, 48, 204-209.
Sen, J. (2015). Security and privacy issues in cloud computing. In Cloud Technology:
Concepts, Methodologies, Tools, and Applications (pp. 1585-1630). IGI Global.
Shabana, K., Fida, N., Khan, F., Jan, S. R., & Rehman, M. U. (2016). Security issues and
attacks in Wireless Sensor Networks. International Journal of Advanced Research in
Computer Science and Electronics Engineering (IJARCSEE), 5(7), pp-81.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





