COIT20263 Information Security: Risk Assessment at NTN Nursing School
VerifiedAdded on 2024/07/29
|11
|2558
|326
Report
AI Summary
This report provides an analysis of information security management at NTN, a private nursing school with campuses in Sydney, Darwin, and Cairns. It outlines the organization's need for a robust security program to protect sensitive health information and critical systems from various risks, including natural disasters and human errors. The report discusses the role of information security, identifies key risks such as data loss and leakage, and details a risk management approach involving assessment and control. Furthermore, it emphasizes the importance of security principles, information asset protection, and the implementation of security frameworks to ensure the confidentiality, integrity, and availability of data within the NTN organization.

COIT20263
Information Security Management
Assessment Item 1
Written Assessment
Student Name:
Student ID
Information Security Management
Assessment Item 1
Written Assessment
Student Name:
Student ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive summary
For this assignment, there is a private nursing school NTN situated in Australia. The main
campus of NTN is present in Sydney and there is two satellite campus of NTN located in Darwin
and Cairns. The NTN provides the internship and training to students of nursing school. The
NTN has made an agreement with these three hospitals located in Sydney, Darwin and Cairns to
provide training to students. These all three centres are connected via internet.
The main aim of the nursing school NTN for establishing the ‘Privacy and Security of Personal
Health Information Policy’ is to manage the information associated with the organization wisely
and to keep the information private and not be shared with anonymous users. For implementing
this, the NTN has hired a staff team by a Chief Information Security Officer (CISO). The NTN
wants to implement the security program so that their institution information can be secure and
can be free from risks. The critical system of the organization includes mobile phones, laptops,
personal computers and other telecommunication devices. The risks include natural disasters,
human errors and intentionally errors. For overcome these all types of error the organization
wants to implement the security management system in their organization.
The role of the information security staff is to protect and keep the information safe and
confidential and protect the system from malicious activities. It also used to protect the system
from physical threats and risks. The confidential and sensitive information need extra care and
security as they are important for the organization. The meaning of risk assessment for the
information security means to define a strong procedure, process to provide security to the
system and provide another level of security to the organization. For any organization, the
information security program is mandatory to keep their data safe (Peltier, 2016).
The various types of risk that can be associated with the organization like NTN are supply chain
risk, inventory risk, security risk and legal liability risk. So for handling such type of risk, an
effective risk management strategy needs to be implemented in the organization.
1
For this assignment, there is a private nursing school NTN situated in Australia. The main
campus of NTN is present in Sydney and there is two satellite campus of NTN located in Darwin
and Cairns. The NTN provides the internship and training to students of nursing school. The
NTN has made an agreement with these three hospitals located in Sydney, Darwin and Cairns to
provide training to students. These all three centres are connected via internet.
The main aim of the nursing school NTN for establishing the ‘Privacy and Security of Personal
Health Information Policy’ is to manage the information associated with the organization wisely
and to keep the information private and not be shared with anonymous users. For implementing
this, the NTN has hired a staff team by a Chief Information Security Officer (CISO). The NTN
wants to implement the security program so that their institution information can be secure and
can be free from risks. The critical system of the organization includes mobile phones, laptops,
personal computers and other telecommunication devices. The risks include natural disasters,
human errors and intentionally errors. For overcome these all types of error the organization
wants to implement the security management system in their organization.
The role of the information security staff is to protect and keep the information safe and
confidential and protect the system from malicious activities. It also used to protect the system
from physical threats and risks. The confidential and sensitive information need extra care and
security as they are important for the organization. The meaning of risk assessment for the
information security means to define a strong procedure, process to provide security to the
system and provide another level of security to the organization. For any organization, the
information security program is mandatory to keep their data safe (Peltier, 2016).
The various types of risk that can be associated with the organization like NTN are supply chain
risk, inventory risk, security risk and legal liability risk. So for handling such type of risk, an
effective risk management strategy needs to be implemented in the organization.
1

Table of Contents
Executive summary......................................................................................................................... 2
Introduction......................................................................................................................................4
Discussion........................................................................................................................................5
Conclusion..................................................................................................................................... 11
References......................................................................................................................................12
List of Figures
Figure 1 Information security risk management..............................................................................9
2
Executive summary......................................................................................................................... 2
Introduction......................................................................................................................................4
Discussion........................................................................................................................................5
Conclusion..................................................................................................................................... 11
References......................................................................................................................................12
List of Figures
Figure 1 Information security risk management..............................................................................9
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The role of the information security is to protect the sensitive and confidential data on the
organization system and keep the system from malicious activities. The other role of information
security is to manage the risk effectively and to reduce the chances of risk arising. The sensitive
information associated with the organization is simply stored in the system. The sensitive
information is not changed or alter it simply directly store in the system. The risk management
for the organization should be proper as it will directly affect the organization. The risk
assessment process needs to be properly handled as it will take the internal process of the
organization. The various types of risk that can be associated with the organization like NTN are
supply chain risk, inventory risk, security risk and legal liability risk. So for handling such type
of risk, an effective risk management strategy needs to be implemented in the organization.
For this assignment, there is a nursing school located in Australia named NTN. The main campus
of NTN is present in Sydney and there is two satellite campus of NTN located in Darwin and
Cairns. The NTN provides the internship and training to students of nursing school. The NTN
has made an agreement with these three hospitals located in Sydney, Darwin and Cairns to
provide training to students. These all three centres are connected via internet (Hasanah and
Wibisono, 2017).
In the main campus Sydney, the lectures, tutorial and laboratory classes are conducted and the
other satellite campus gets these lectures via live video streaming. The instructors and students
directly communicate through internet. The NTN organization also provides telemedicine and
healthcare service within a radius of 200 km to needy people.
The main objective of the organization is to develop and establish an information security
management system in the organization so that the risk associated with the organization can be
reduced and the system can become cost-effective. The systems that need security are personal
computers, laptops and cellular phones. The risk associated with the organization is natural
disasters, any malicious activities or intentionally physical damage to the system.
3
The role of the information security is to protect the sensitive and confidential data on the
organization system and keep the system from malicious activities. The other role of information
security is to manage the risk effectively and to reduce the chances of risk arising. The sensitive
information associated with the organization is simply stored in the system. The sensitive
information is not changed or alter it simply directly store in the system. The risk management
for the organization should be proper as it will directly affect the organization. The risk
assessment process needs to be properly handled as it will take the internal process of the
organization. The various types of risk that can be associated with the organization like NTN are
supply chain risk, inventory risk, security risk and legal liability risk. So for handling such type
of risk, an effective risk management strategy needs to be implemented in the organization.
For this assignment, there is a nursing school located in Australia named NTN. The main campus
of NTN is present in Sydney and there is two satellite campus of NTN located in Darwin and
Cairns. The NTN provides the internship and training to students of nursing school. The NTN
has made an agreement with these three hospitals located in Sydney, Darwin and Cairns to
provide training to students. These all three centres are connected via internet (Hasanah and
Wibisono, 2017).
In the main campus Sydney, the lectures, tutorial and laboratory classes are conducted and the
other satellite campus gets these lectures via live video streaming. The instructors and students
directly communicate through internet. The NTN organization also provides telemedicine and
healthcare service within a radius of 200 km to needy people.
The main objective of the organization is to develop and establish an information security
management system in the organization so that the risk associated with the organization can be
reduced and the system can become cost-effective. The systems that need security are personal
computers, laptops and cellular phones. The risk associated with the organization is natural
disasters, any malicious activities or intentionally physical damage to the system.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Discussion
A. Company overview
The NTN is private nursing schools which provide internship and training to the students of
nursing school. The main campus is located in situated. The organization has two other satellite
campus located in Darwin and Cairns. The organization also provides telemedicine and
healthcare service to the community within a radius of 200 km. This service is provided to the
needed people. a team of doctor travels in a vehicle name home-care and provides medical
facilities to the needy people. The lecture, tutorials and laboratory classes are conducted in the
main campus Sydney and the live video is streamed to the satellite campus, Darwin and Cairns.
At a time 400 people can take the session 200 from the main campus and 100 each from another
satellite campus Darwin and Cairns. The NTN has now recently hired a staff to its information
security division to maintain the security within the organization information system.
B. Information security
The role of the information security is to protect the confidential and sensitive information
available on the organization system and protect from the malicious activities and threats, It also
used to minimize the risk arises and to reduce the risk impact on the organization. The sensitive
information of the organization is simply stored in the system and which need to be protected
safe from outside users. The risk assessment means to the analyze the risk, its impacts and the
strategies to overcome the risk. The risk mitigation steps are important as they are used to avoid
the risk and to reduce the effect of the risk on the organization like NTN. These steps provide the
other level of safety and security to the information system of the organization (Kiedrowicz and
Stanik, 2015.).
C. Risk associated
The risk is a situation in which affect the organization performance and can lead to problems for
the organization like NTN. In the following section, the risk associated with NTN organization
will be discussed briefly.
4
A. Company overview
The NTN is private nursing schools which provide internship and training to the students of
nursing school. The main campus is located in situated. The organization has two other satellite
campus located in Darwin and Cairns. The organization also provides telemedicine and
healthcare service to the community within a radius of 200 km. This service is provided to the
needed people. a team of doctor travels in a vehicle name home-care and provides medical
facilities to the needy people. The lecture, tutorials and laboratory classes are conducted in the
main campus Sydney and the live video is streamed to the satellite campus, Darwin and Cairns.
At a time 400 people can take the session 200 from the main campus and 100 each from another
satellite campus Darwin and Cairns. The NTN has now recently hired a staff to its information
security division to maintain the security within the organization information system.
B. Information security
The role of the information security is to protect the confidential and sensitive information
available on the organization system and protect from the malicious activities and threats, It also
used to minimize the risk arises and to reduce the risk impact on the organization. The sensitive
information of the organization is simply stored in the system and which need to be protected
safe from outside users. The risk assessment means to the analyze the risk, its impacts and the
strategies to overcome the risk. The risk mitigation steps are important as they are used to avoid
the risk and to reduce the effect of the risk on the organization like NTN. These steps provide the
other level of safety and security to the information system of the organization (Kiedrowicz and
Stanik, 2015.).
C. Risk associated
The risk is a situation in which affect the organization performance and can lead to problems for
the organization like NTN. In the following section, the risk associated with NTN organization
will be discussed briefly.
4
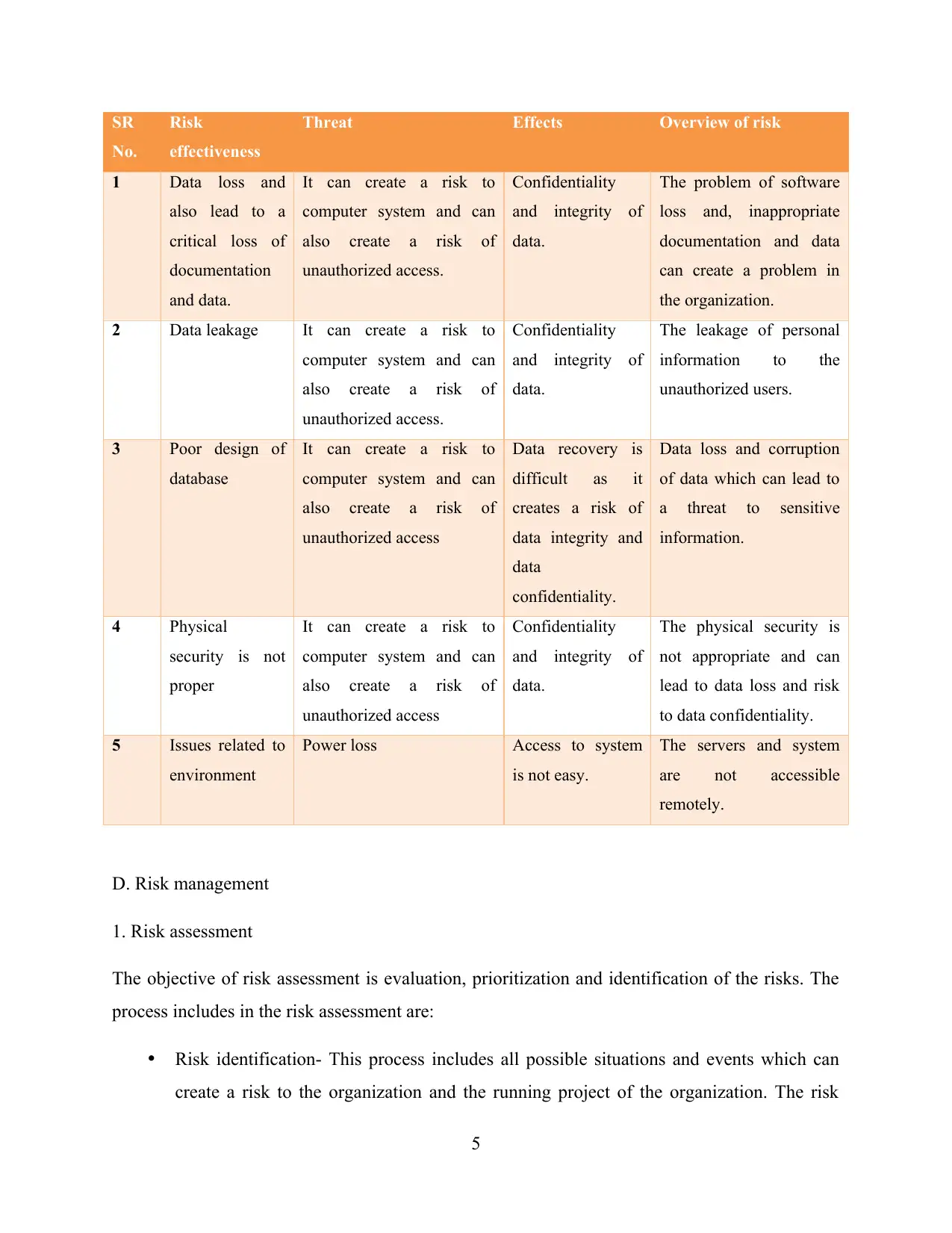
SR
No.
Risk
effectiveness
Threat Effects Overview of risk
1 Data loss and
also lead to a
critical loss of
documentation
and data.
It can create a risk to
computer system and can
also create a risk of
unauthorized access.
Confidentiality
and integrity of
data.
The problem of software
loss and, inappropriate
documentation and data
can create a problem in
the organization.
2 Data leakage It can create a risk to
computer system and can
also create a risk of
unauthorized access.
Confidentiality
and integrity of
data.
The leakage of personal
information to the
unauthorized users.
3 Poor design of
database
It can create a risk to
computer system and can
also create a risk of
unauthorized access
Data recovery is
difficult as it
creates a risk of
data integrity and
data
confidentiality.
Data loss and corruption
of data which can lead to
a threat to sensitive
information.
4 Physical
security is not
proper
It can create a risk to
computer system and can
also create a risk of
unauthorized access
Confidentiality
and integrity of
data.
The physical security is
not appropriate and can
lead to data loss and risk
to data confidentiality.
5 Issues related to
environment
Power loss Access to system
is not easy.
The servers and system
are not accessible
remotely.
D. Risk management
1. Risk assessment
The objective of risk assessment is evaluation, prioritization and identification of the risks. The
process includes in the risk assessment are:
Risk identification- This process includes all possible situations and events which can
create a risk to the organization and the running project of the organization. The risk
5
No.
Risk
effectiveness
Threat Effects Overview of risk
1 Data loss and
also lead to a
critical loss of
documentation
and data.
It can create a risk to
computer system and can
also create a risk of
unauthorized access.
Confidentiality
and integrity of
data.
The problem of software
loss and, inappropriate
documentation and data
can create a problem in
the organization.
2 Data leakage It can create a risk to
computer system and can
also create a risk of
unauthorized access.
Confidentiality
and integrity of
data.
The leakage of personal
information to the
unauthorized users.
3 Poor design of
database
It can create a risk to
computer system and can
also create a risk of
unauthorized access
Data recovery is
difficult as it
creates a risk of
data integrity and
data
confidentiality.
Data loss and corruption
of data which can lead to
a threat to sensitive
information.
4 Physical
security is not
proper
It can create a risk to
computer system and can
also create a risk of
unauthorized access
Confidentiality
and integrity of
data.
The physical security is
not appropriate and can
lead to data loss and risk
to data confidentiality.
5 Issues related to
environment
Power loss Access to system
is not easy.
The servers and system
are not accessible
remotely.
D. Risk management
1. Risk assessment
The objective of risk assessment is evaluation, prioritization and identification of the risks. The
process includes in the risk assessment are:
Risk identification- This process includes all possible situations and events which can
create a risk to the organization and the running project of the organization. The risk
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

identification strategies are risk review, proper planning, and prepare a related risk of the
organization. The previous project risk should be undertaken so that the risk from
running project can be eliminated. The risk associated with the project need to be review
and all related techniques related to the risk solving need to be made to overcoming the
risk.
Risk prioritization- The risk can be categorized into categories according to its effects
and consequences on the organization. If any risk has more chance to occur and it’s after
effects are more hazardous than its priority is set to maximum so that it can be resolved
first before handling any other risk. The main objective is to highlight the top priority
risk which is more hazardous for the organization.
2. Risk control
The objective of risk control is to design some plan and strategies so that identified risk can be
resolved easily. The process includes risk control is risk mitigation and risk planning and to
handle the risk effectively. As the risk is categorized according to priority the next step is to
manage the risk. For this, the management of risk is an important and main object to reduce the
consequence of the risk. These steps help to reduce the chance of the risk. The risk is monitored
continuously as the risk mitigation steps are implemented in the organization.
E. Information Security
For the security management system, the risk needs to be properly managed. The security
management is important to step for the security phase. The information system can be
considered as the cyclic process for the information security management step. The risk needs to
be properly managed and all the risk mitigation needs to be properly implemented to reduce the
risk effects on the organization.
For the information security there can be considered security principles for information system
networks and security which are described below:
6
organization. The previous project risk should be undertaken so that the risk from
running project can be eliminated. The risk associated with the project need to be review
and all related techniques related to the risk solving need to be made to overcoming the
risk.
Risk prioritization- The risk can be categorized into categories according to its effects
and consequences on the organization. If any risk has more chance to occur and it’s after
effects are more hazardous than its priority is set to maximum so that it can be resolved
first before handling any other risk. The main objective is to highlight the top priority
risk which is more hazardous for the organization.
2. Risk control
The objective of risk control is to design some plan and strategies so that identified risk can be
resolved easily. The process includes risk control is risk mitigation and risk planning and to
handle the risk effectively. As the risk is categorized according to priority the next step is to
manage the risk. For this, the management of risk is an important and main object to reduce the
consequence of the risk. These steps help to reduce the chance of the risk. The risk is monitored
continuously as the risk mitigation steps are implemented in the organization.
E. Information Security
For the security management system, the risk needs to be properly managed. The security
management is important to step for the security phase. The information system can be
considered as the cyclic process for the information security management step. The risk needs to
be properly managed and all the risk mitigation needs to be properly implemented to reduce the
risk effects on the organization.
For the information security there can be considered security principles for information system
networks and security which are described below:
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

a. Awareness- The awareness regarding with the information security needs to be well
spread among the participants and the importance of the information security also needs
to be widespread.
b. Responsibility- The every individual of the organization is equally responsible for
maintaining the information security for the organization.
c. Ethics- The ethics should be maintained within the organization staff.
d. Risk assessment- The risk assessment activities need to be properly done in regular time.
e. Security management- The participants should contribute equally to maintain the data
security within the organization (Cherdantseva, et.al., 2016.).
F. Information assets
For any organization, the information is the key part which needs to be protected and appropriate
safeguard needs to be implemented in the organization. As the information includes client
information the information can be termed as sensitive information. The data and information
must be taken care of safely and it should be kept safe from outside users. The information can
be stored in system in many various forms like:
a. Documents and papers
b. Electronic data
c. Information attain by individual
G. Information security risk management and its various frameworks
The information security risk management system is used to develop the strong operating, secure
safeguards against threats. The loss of confidentiality, integrity, availability, reliability and
authenticity of information or data can affect the organization NTN. For the organization NTN
the data need to protect and to be preserved.
In the next section the framework for the risk management system is described here:
7
spread among the participants and the importance of the information security also needs
to be widespread.
b. Responsibility- The every individual of the organization is equally responsible for
maintaining the information security for the organization.
c. Ethics- The ethics should be maintained within the organization staff.
d. Risk assessment- The risk assessment activities need to be properly done in regular time.
e. Security management- The participants should contribute equally to maintain the data
security within the organization (Cherdantseva, et.al., 2016.).
F. Information assets
For any organization, the information is the key part which needs to be protected and appropriate
safeguard needs to be implemented in the organization. As the information includes client
information the information can be termed as sensitive information. The data and information
must be taken care of safely and it should be kept safe from outside users. The information can
be stored in system in many various forms like:
a. Documents and papers
b. Electronic data
c. Information attain by individual
G. Information security risk management and its various frameworks
The information security risk management system is used to develop the strong operating, secure
safeguards against threats. The loss of confidentiality, integrity, availability, reliability and
authenticity of information or data can affect the organization NTN. For the organization NTN
the data need to protect and to be preserved.
In the next section the framework for the risk management system is described here:
7
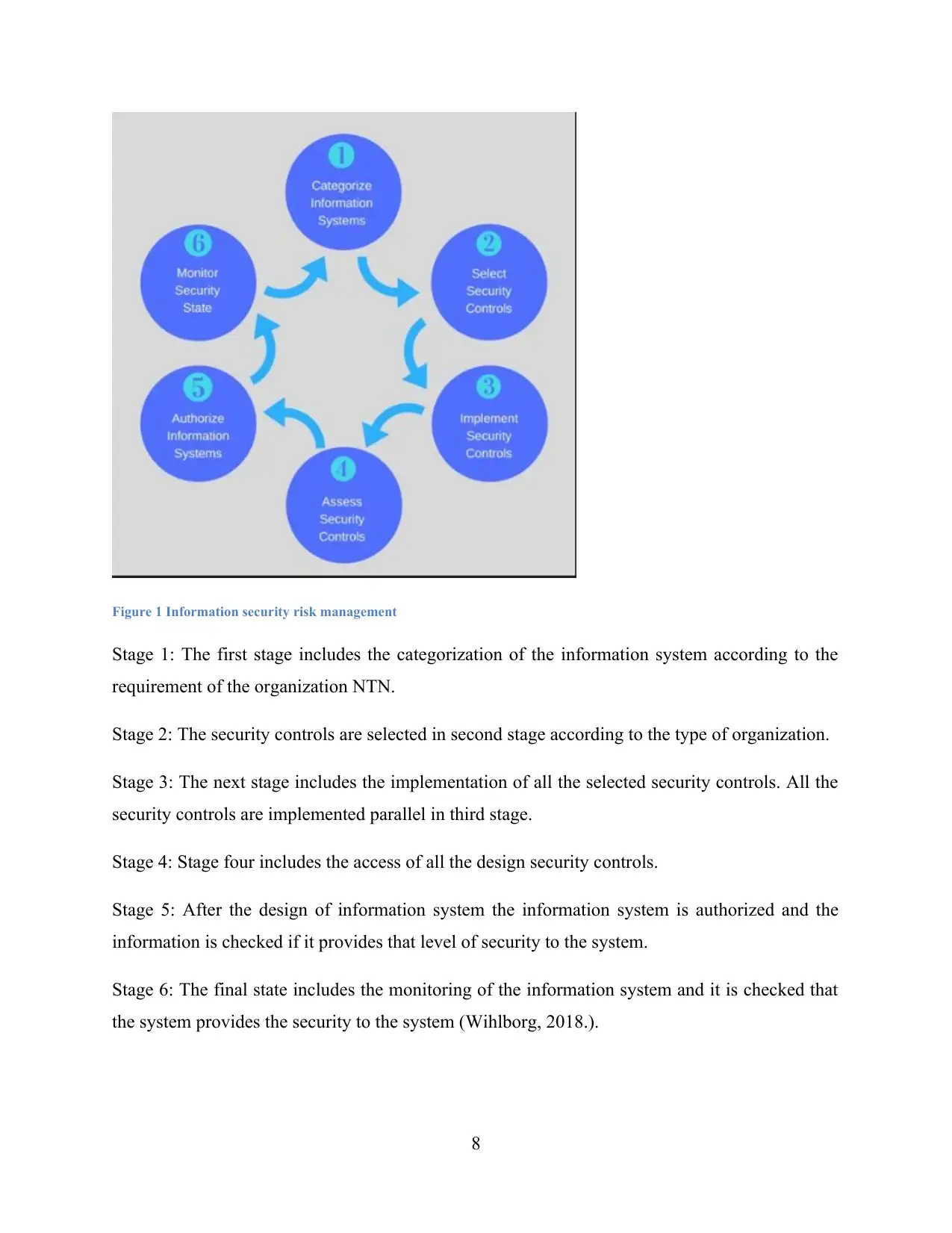
Figure 1 Information security risk management
Stage 1: The first stage includes the categorization of the information system according to the
requirement of the organization NTN.
Stage 2: The security controls are selected in second stage according to the type of organization.
Stage 3: The next stage includes the implementation of all the selected security controls. All the
security controls are implemented parallel in third stage.
Stage 4: Stage four includes the access of all the design security controls.
Stage 5: After the design of information system the information system is authorized and the
information is checked if it provides that level of security to the system.
Stage 6: The final state includes the monitoring of the information system and it is checked that
the system provides the security to the system (Wihlborg, 2018.).
8
Stage 1: The first stage includes the categorization of the information system according to the
requirement of the organization NTN.
Stage 2: The security controls are selected in second stage according to the type of organization.
Stage 3: The next stage includes the implementation of all the selected security controls. All the
security controls are implemented parallel in third stage.
Stage 4: Stage four includes the access of all the design security controls.
Stage 5: After the design of information system the information system is authorized and the
information is checked if it provides that level of security to the system.
Stage 6: The final state includes the monitoring of the information system and it is checked that
the system provides the security to the system (Wihlborg, 2018.).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Conclusion
For any organization like NTN, the information system is very important as there is always a risk
of data loss and data leakage which can affect the organization. The risk management process
should also include in the organization because it will provide the advanced security features to
the organization like NTN. The risk mitigation steps are used to reduce the impact of risk on the
organization. In this assignment, the information security policy is discussed for the organization
NTN. As the organization provide lecture, tutorials to students via internet the medium should be
secure and the information should not be leaked to any third party. It should be secure so that
sensitive information cannot be a leak. The use of password should be there so that the data
integrity and data confidentiality is maintained in the organization like NTN.
9
For any organization like NTN, the information system is very important as there is always a risk
of data loss and data leakage which can affect the organization. The risk management process
should also include in the organization because it will provide the advanced security features to
the organization like NTN. The risk mitigation steps are used to reduce the impact of risk on the
organization. In this assignment, the information security policy is discussed for the organization
NTN. As the organization provide lecture, tutorials to students via internet the medium should be
secure and the information should not be leaked to any third party. It should be secure so that
sensitive information cannot be a leak. The use of password should be there so that the data
integrity and data confidentiality is maintained in the organization like NTN.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers & security,
56, pp.1-27.
Hasanah, U. and Wibisono, S., 2017, October. Technical Integrity Management System. In
SPE/IATMI Asia Pacific Oil & Gas Conference and Exhibition. Society of Petroleum Engineers.
Kiedrowicz, M. and Stanik, J., 2015. Selected aspects of risk management in respect of security
of the document lifecycle management system with multiple levels of sensitivity. Information
Management in Practice,(eds) BF Kubiak and J. Maślankowski, pp.231-249.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Wihlborg, C., 2018. Systemic risk and the organization of the financial system: overview.
Journal of Financial Economic Policy.
10
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers & security,
56, pp.1-27.
Hasanah, U. and Wibisono, S., 2017, October. Technical Integrity Management System. In
SPE/IATMI Asia Pacific Oil & Gas Conference and Exhibition. Society of Petroleum Engineers.
Kiedrowicz, M. and Stanik, J., 2015. Selected aspects of risk management in respect of security
of the document lifecycle management system with multiple levels of sensitivity. Information
Management in Practice,(eds) BF Kubiak and J. Maślankowski, pp.231-249.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Wihlborg, C., 2018. Systemic risk and the organization of the financial system: overview.
Journal of Financial Economic Policy.
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





