Object Oriented Software Development Assignment - Fall Semester 2024
VerifiedAdded on 2023/03/17
|7
|1021
|93
Homework Assignment
AI Summary
This document presents a comprehensive solution to an object-oriented software development assignment, focusing on design patterns. The assignment begins with an exploration of creational design patterns, including abstract factory, builder, factory method, prototype, and singleton patterns. It then delves into two design problems: "Compute Price" and "Checkout." For the "Compute Price" problem, the proxy design pattern is chosen, and its components, merits, and security considerations are discussed, including the use of authenticator and authorization. For the "Checkout" problem, the composite design pattern is selected, and its components, benefits, and security measures, such as checkpoint and limited view are analyzed. The solution includes class diagrams and references to relevant literature, providing a detailed analysis of design patterns and their application in software development.

Running head: OBJECT ORIENTED SOFTWARE DEVELOPMENT
OBJECT ORIENTED SOFTWARE DEVELOPMENT
Name of the Student:
Name of the University:
Author Note:
OBJECT ORIENTED SOFTWARE DEVELOPMENT
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1OBJECT ORIENTED SOFTWARE DEVELOPMENT
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Design Problem 1 (Compute Price):......................................................................................3
Design Problem 2 (Checkout):...............................................................................................4
References..................................................................................................................................6
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Design Problem 1 (Compute Price):......................................................................................3
Design Problem 2 (Checkout):...............................................................................................4
References..................................................................................................................................6

2OBJECT ORIENTED SOFTWARE DEVELOPMENT
Question 1
The creational design patterns are used to abstract the instantiation process. This allows the
system to be independent of the creation, composition and representation of the objects in a
class. The creational patterns uses inheritance to create different instantiations of the class
and delegates the instantiation to another object in case of object instantiation. The use of the
creational design pattern shifts the focus towards a smaller group of fundamental behaviours
which repeats over time. This set of fundamental behaviours can be used to tackle more
complex classes and instantiate them. The five main types of creational design patterns are:
1. Abstract factory: It is used to provide a medium for creating the families of
dependent or related objects without mentioning their concrete classes. It is also
known as kit. The abstract factory is used when a system is independent of its
products, is configured with multiple families of its products, is needed to enforce a
group of related product objects and is needed to reveal the interfaces of a class
library of products. One of its main consequence is the isolation of the concrete
classes.
2. Builder: It is used to separate the complex object’s construction from its
representation so that the same process can be used to create many representations.
The builder pattern is used when the algorithm that is creating the complex object is
independent of the parts of the object and its assembling and the construction process
gives permission for creating multiple representations. Its main consequence is that it
lets the user differ the product’s internal representation.
3. Factory method: This method is used to defer the instantiation process from a class
to a subclass. It is also known as the virtual constructor. It is used when a class cannot
predict the class of objects it should create and when a class the subclasses needs to
mention the object it creates. Its main consequence is that it provide hooks for
subclasses.
4. Prototype: This pattern is used to create objects with a help of a pre created prototype
by copying this prototype. It is used when classes are instantiated at run time through
dynamic loading and when an instance of a class can have only a few combinations.
The main consequence of this pattern is the removing or adding of products at
runtime.
Question 1
The creational design patterns are used to abstract the instantiation process. This allows the
system to be independent of the creation, composition and representation of the objects in a
class. The creational patterns uses inheritance to create different instantiations of the class
and delegates the instantiation to another object in case of object instantiation. The use of the
creational design pattern shifts the focus towards a smaller group of fundamental behaviours
which repeats over time. This set of fundamental behaviours can be used to tackle more
complex classes and instantiate them. The five main types of creational design patterns are:
1. Abstract factory: It is used to provide a medium for creating the families of
dependent or related objects without mentioning their concrete classes. It is also
known as kit. The abstract factory is used when a system is independent of its
products, is configured with multiple families of its products, is needed to enforce a
group of related product objects and is needed to reveal the interfaces of a class
library of products. One of its main consequence is the isolation of the concrete
classes.
2. Builder: It is used to separate the complex object’s construction from its
representation so that the same process can be used to create many representations.
The builder pattern is used when the algorithm that is creating the complex object is
independent of the parts of the object and its assembling and the construction process
gives permission for creating multiple representations. Its main consequence is that it
lets the user differ the product’s internal representation.
3. Factory method: This method is used to defer the instantiation process from a class
to a subclass. It is also known as the virtual constructor. It is used when a class cannot
predict the class of objects it should create and when a class the subclasses needs to
mention the object it creates. Its main consequence is that it provide hooks for
subclasses.
4. Prototype: This pattern is used to create objects with a help of a pre created prototype
by copying this prototype. It is used when classes are instantiated at run time through
dynamic loading and when an instance of a class can have only a few combinations.
The main consequence of this pattern is the removing or adding of products at
runtime.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3OBJECT ORIENTED SOFTWARE DEVELOPMENT
5. Singleton: These pattern is used to create a single instance of a class with global
reach or access. It is used when there can only be one instance of a class and when the
only instance of a class can be extended using sub classing. The main consequence of
this is it gives the user controlled access to the single instance.
Question 2
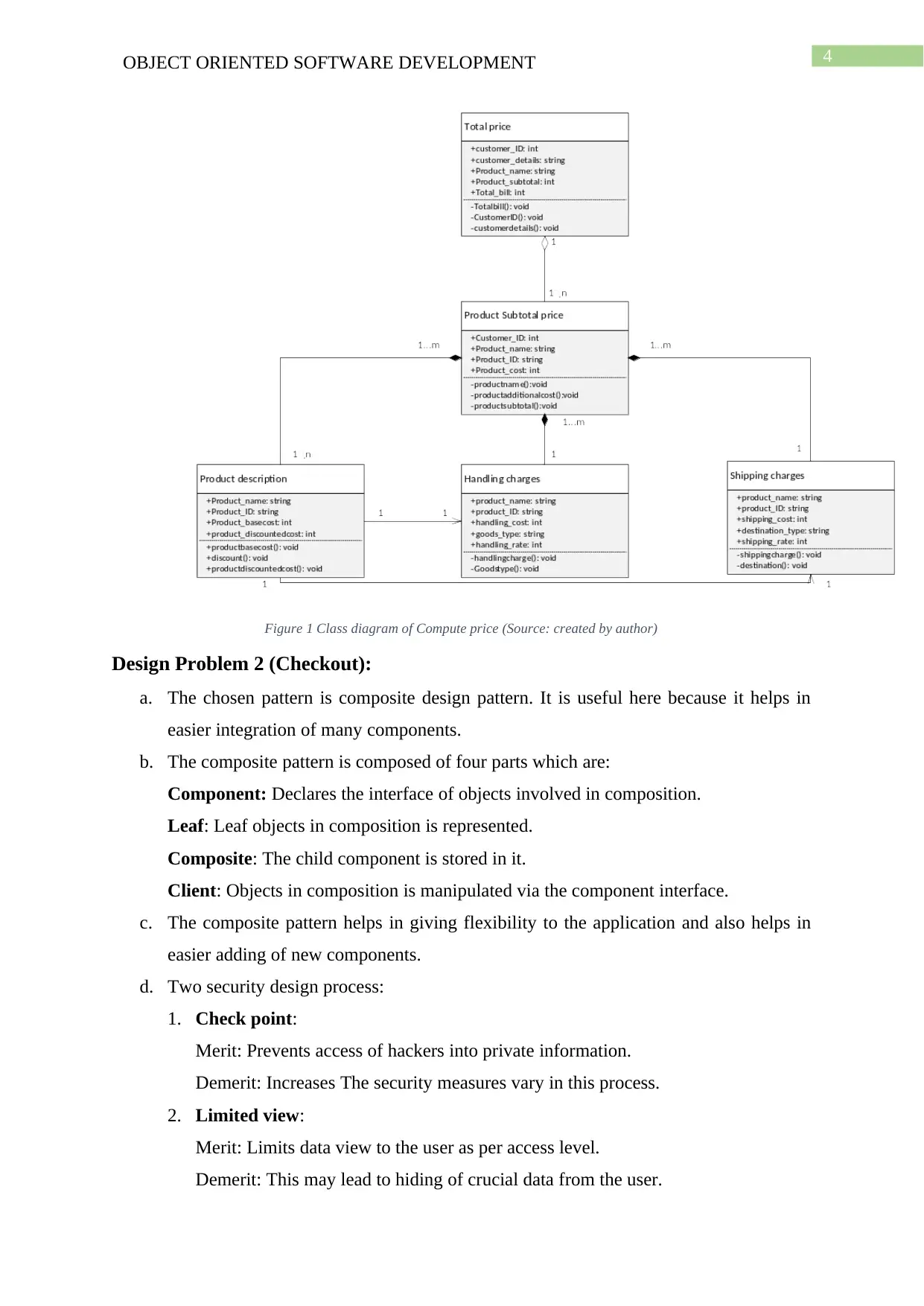
Design Problem 1 (Compute Price):
a. The chosen design pattern is proxy design pattern. The proxy design process will be
useful here because the compute price process is complex and this design process will
make it faster.
b. The four components of proxy pattern are:
Protective proxy: Acts as authorisation layer.
Smart proxy: Provides addition security layer.
Virtual proxy: Used in applications with multiple databases.
Remote proxy: Provides representation of local objects.
c. The proxy pattern increases the security of the shopping website and the compute
price process. The pattern also helps in avoiding the duplication of objects thus
making the application fast. Provides protection to the original objects from the
objects from outside the world.
d. Two security design process:
1. Authenticator:
Merit: Verifies who the user of the application is.
Demerit: Increases the complexity of the application.
2. Authorization:
Merit: It helps in the access of resources.
Demerit: The rules can only be associated with subjects and resource.
5. Singleton: These pattern is used to create a single instance of a class with global
reach or access. It is used when there can only be one instance of a class and when the
only instance of a class can be extended using sub classing. The main consequence of
this is it gives the user controlled access to the single instance.
Question 2
Design Problem 1 (Compute Price):
a. The chosen design pattern is proxy design pattern. The proxy design process will be
useful here because the compute price process is complex and this design process will
make it faster.
b. The four components of proxy pattern are:
Protective proxy: Acts as authorisation layer.
Smart proxy: Provides addition security layer.
Virtual proxy: Used in applications with multiple databases.
Remote proxy: Provides representation of local objects.
c. The proxy pattern increases the security of the shopping website and the compute
price process. The pattern also helps in avoiding the duplication of objects thus
making the application fast. Provides protection to the original objects from the
objects from outside the world.
d. Two security design process:
1. Authenticator:
Merit: Verifies who the user of the application is.
Demerit: Increases the complexity of the application.
2. Authorization:
Merit: It helps in the access of resources.
Demerit: The rules can only be associated with subjects and resource.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4OBJECT ORIENTED SOFTWARE DEVELOPMENT
Figure 1 Class diagram of Compute price (Source: created by author)
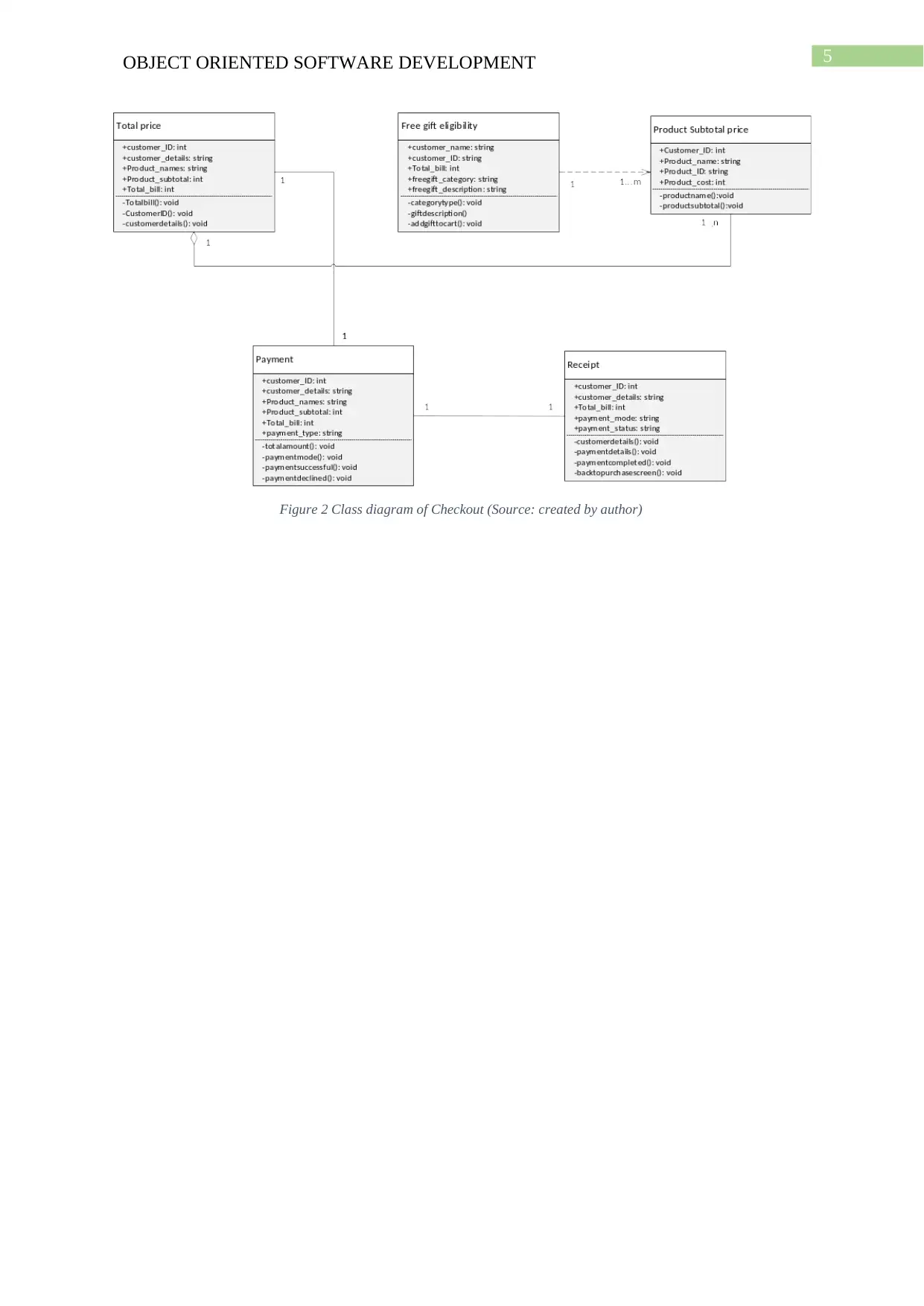
Design Problem 2 (Checkout):
a. The chosen pattern is composite design pattern. It is useful here because it helps in
easier integration of many components.
b. The composite pattern is composed of four parts which are:
Component: Declares the interface of objects involved in composition.
Leaf: Leaf objects in composition is represented.
Composite: The child component is stored in it.
Client: Objects in composition is manipulated via the component interface.
c. The composite pattern helps in giving flexibility to the application and also helps in
easier adding of new components.
d. Two security design process:
1. Check point:
Merit: Prevents access of hackers into private information.
Demerit: Increases The security measures vary in this process.
2. Limited view:
Merit: Limits data view to the user as per access level.
Demerit: This may lead to hiding of crucial data from the user.
Figure 1 Class diagram of Compute price (Source: created by author)
Design Problem 2 (Checkout):
a. The chosen pattern is composite design pattern. It is useful here because it helps in
easier integration of many components.
b. The composite pattern is composed of four parts which are:
Component: Declares the interface of objects involved in composition.
Leaf: Leaf objects in composition is represented.
Composite: The child component is stored in it.
Client: Objects in composition is manipulated via the component interface.
c. The composite pattern helps in giving flexibility to the application and also helps in
easier adding of new components.
d. Two security design process:
1. Check point:
Merit: Prevents access of hackers into private information.
Demerit: Increases The security measures vary in this process.
2. Limited view:
Merit: Limits data view to the user as per access level.
Demerit: This may lead to hiding of crucial data from the user.
5OBJECT ORIENTED SOFTWARE DEVELOPMENT
Figure 2 Class diagram of Checkout (Source: created by author)
Figure 2 Class diagram of Checkout (Source: created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OBJECT ORIENTED SOFTWARE DEVELOPMENT
References
[1] Gamma, E., Design patterns: elements of reusable object-oriented software. Pearson
Education India. 1995.
[2] Smith, B., Object-oriented programming. In AdvancED ActionScript 3.0: Design
Patterns (pp. 1-25). Apress. 2011.
References
[1] Gamma, E., Design patterns: elements of reusable object-oriented software. Pearson
Education India. 1995.
[2] Smith, B., Object-oriented programming. In AdvancED ActionScript 3.0: Design
Patterns (pp. 1-25). Apress. 2011.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




