Capstone Project: Council Elections via Online Electronic Voting
VerifiedAdded on 2020/04/07
|7
|1139
|194
Capstone Project
AI Summary
This capstone project explores the feasibility and implementation of an online electronic voting system for council elections, specifically focusing on the City of Yule. The project begins with a feasibility study and delves into detailed requirement analysis, outlining both functional and non-functional specifications. It addresses user authentication, secure vote casting, and result calculation. A cost-benefit analysis is provided, estimating the project's financial implications, and a comprehensive risk analysis identifies potential threats such as information breaches, availability attacks, and malicious codes, proposing mitigation strategies for each. The final recommendation emphasizes the importance of administrative and technical security controls, along with agile project management methodologies, to ensure the project's success and meet all objectives. The project references several academic sources to support its findings and recommendations.

Capstone project case study
Council Elections via Online Electronic Voting
City of Yule
9/19/2017
Council Elections via Online Electronic Voting
City of Yule
9/19/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Council Elections via Online Electronic Voting
Table of Contents
Feasibility Study..........................................................................................................................................3
Requirement Analysis..............................................................................................................................3
Functional Requirements.....................................................................................................................3
Non-Functional Requirements.............................................................................................................3
Cost-Benefit Analysis..............................................................................................................................4
Risk Analysis...........................................................................................................................................4
Final Recommendation............................................................................................................................6
References...................................................................................................................................................7
2
Table of Contents
Feasibility Study..........................................................................................................................................3
Requirement Analysis..............................................................................................................................3
Functional Requirements.....................................................................................................................3
Non-Functional Requirements.............................................................................................................3
Cost-Benefit Analysis..............................................................................................................................4
Risk Analysis...........................................................................................................................................4
Final Recommendation............................................................................................................................6
References...................................................................................................................................................7
2

Council Elections via Online Electronic Voting
Feasibility Study
Requirement Analysis
Council Elections via Online Electronic Voting is a system that will involve many of the
functional and non-functional specifications. The system will make it easier to collect and
calculate the votes in a secure manner.
Functional Requirements
Display of the candidates that have stood up for the elections on the online portal to allow
the citizens to view and vote.
A brief background of every candidate such as name, work done in the past etc.
User authentication by validating the user login id and the use of biometric identification
of the user.
Ability to the people to cast their vote by clicking on the name of their desired candidate.
Ability to make sure that one only vote is cast through one id.
An acknowledgement shall be sent to the registered email id of the person for the
acceptance of the vote.
Calculation of the number of votes that are cast for each of the candidate.
Calculation of the final results.
Non-Functional Requirements
The system shall be available at the time of the voting so that the users may access it
without any hurdles (Chung, 2013).
The system shall be reliable so that the vote is cast for the candidate that they have
selected and valid information is displayed and stored.
The system shall showcase good performance so that the users do not face any lags or
enhanced response time for any of their action.
The system shall be easy to maintain and upgrade.
The system shall be usable in nature such that it is designed and deployed as per the
functional aspects associated with it (Eeles, 2015).
3
Feasibility Study
Requirement Analysis
Council Elections via Online Electronic Voting is a system that will involve many of the
functional and non-functional specifications. The system will make it easier to collect and
calculate the votes in a secure manner.
Functional Requirements
Display of the candidates that have stood up for the elections on the online portal to allow
the citizens to view and vote.
A brief background of every candidate such as name, work done in the past etc.
User authentication by validating the user login id and the use of biometric identification
of the user.
Ability to the people to cast their vote by clicking on the name of their desired candidate.
Ability to make sure that one only vote is cast through one id.
An acknowledgement shall be sent to the registered email id of the person for the
acceptance of the vote.
Calculation of the number of votes that are cast for each of the candidate.
Calculation of the final results.
Non-Functional Requirements
The system shall be available at the time of the voting so that the users may access it
without any hurdles (Chung, 2013).
The system shall be reliable so that the vote is cast for the candidate that they have
selected and valid information is displayed and stored.
The system shall showcase good performance so that the users do not face any lags or
enhanced response time for any of their action.
The system shall be easy to maintain and upgrade.
The system shall be usable in nature such that it is designed and deployed as per the
functional aspects associated with it (Eeles, 2015).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Council Elections via Online Electronic Voting
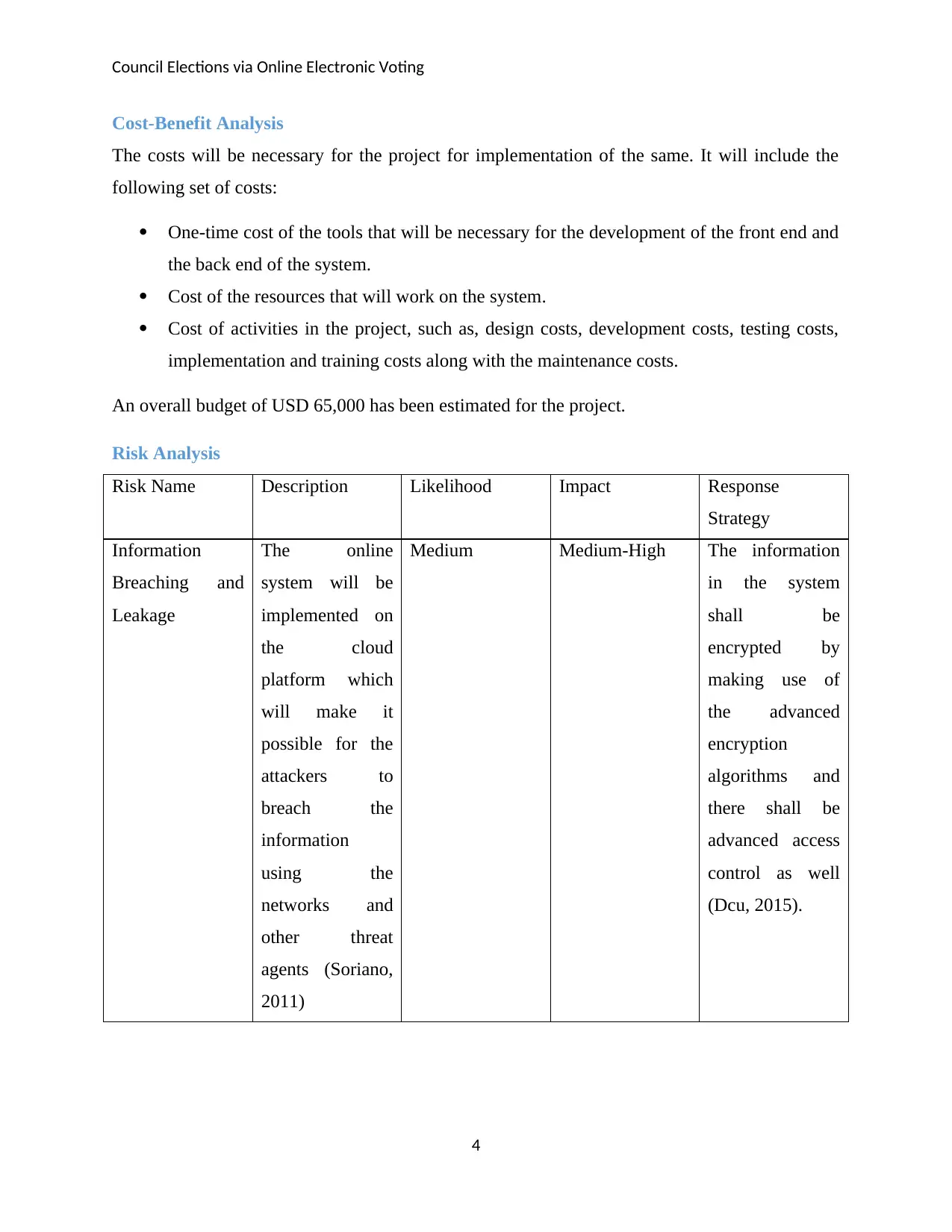
Cost-Benefit Analysis
The costs will be necessary for the project for implementation of the same. It will include the
following set of costs:
One-time cost of the tools that will be necessary for the development of the front end and
the back end of the system.
Cost of the resources that will work on the system.
Cost of activities in the project, such as, design costs, development costs, testing costs,
implementation and training costs along with the maintenance costs.
An overall budget of USD 65,000 has been estimated for the project.
Risk Analysis
Risk Name Description Likelihood Impact Response
Strategy
Information
Breaching and
Leakage
The online
system will be
implemented on
the cloud
platform which
will make it
possible for the
attackers to
breach the
information
using the
networks and
other threat
agents (Soriano,
2011)
Medium Medium-High The information
in the system
shall be
encrypted by
making use of
the advanced
encryption
algorithms and
there shall be
advanced access
control as well
(Dcu, 2015).
4
Cost-Benefit Analysis
The costs will be necessary for the project for implementation of the same. It will include the
following set of costs:
One-time cost of the tools that will be necessary for the development of the front end and
the back end of the system.
Cost of the resources that will work on the system.
Cost of activities in the project, such as, design costs, development costs, testing costs,
implementation and training costs along with the maintenance costs.
An overall budget of USD 65,000 has been estimated for the project.
Risk Analysis
Risk Name Description Likelihood Impact Response
Strategy
Information
Breaching and
Leakage
The online
system will be
implemented on
the cloud
platform which
will make it
possible for the
attackers to
breach the
information
using the
networks and
other threat
agents (Soriano,
2011)
Medium Medium-High The information
in the system
shall be
encrypted by
making use of
the advanced
encryption
algorithms and
there shall be
advanced access
control as well
(Dcu, 2015).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Council Elections via Online Electronic Voting
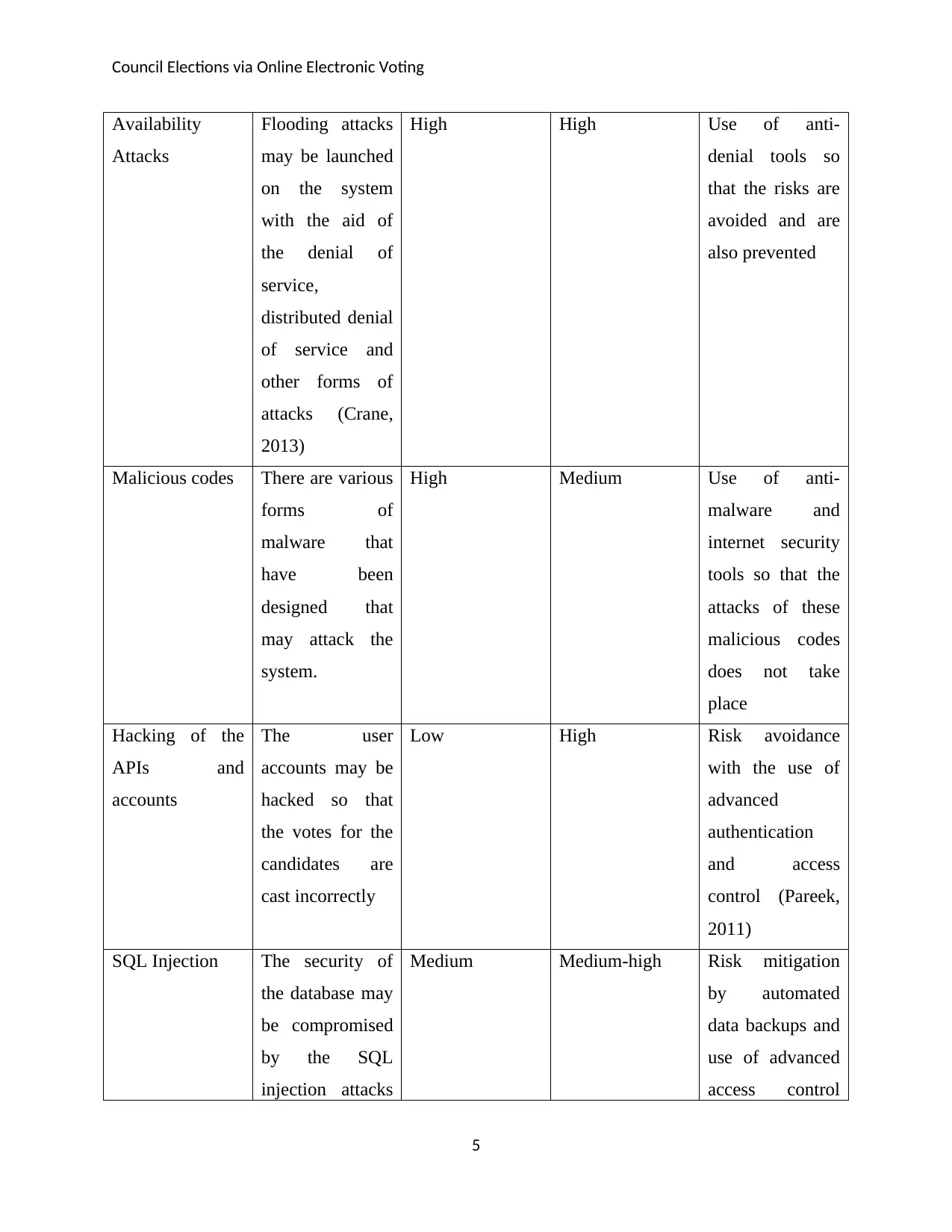
Availability
Attacks
Flooding attacks
may be launched
on the system
with the aid of
the denial of
service,
distributed denial
of service and
other forms of
attacks (Crane,
2013)
High High Use of anti-
denial tools so
that the risks are
avoided and are
also prevented
Malicious codes There are various
forms of
malware that
have been
designed that
may attack the
system.
High Medium Use of anti-
malware and
internet security
tools so that the
attacks of these
malicious codes
does not take
place
Hacking of the
APIs and
accounts
The user
accounts may be
hacked so that
the votes for the
candidates are
cast incorrectly
Low High Risk avoidance
with the use of
advanced
authentication
and access
control (Pareek,
2011)
SQL Injection The security of
the database may
be compromised
by the SQL
injection attacks
Medium Medium-high Risk mitigation
by automated
data backups and
use of advanced
access control
5
Availability
Attacks
Flooding attacks
may be launched
on the system
with the aid of
the denial of
service,
distributed denial
of service and
other forms of
attacks (Crane,
2013)
High High Use of anti-
denial tools so
that the risks are
avoided and are
also prevented
Malicious codes There are various
forms of
malware that
have been
designed that
may attack the
system.
High Medium Use of anti-
malware and
internet security
tools so that the
attacks of these
malicious codes
does not take
place
Hacking of the
APIs and
accounts
The user
accounts may be
hacked so that
the votes for the
candidates are
cast incorrectly
Low High Risk avoidance
with the use of
advanced
authentication
and access
control (Pareek,
2011)
SQL Injection The security of
the database may
be compromised
by the SQL
injection attacks
Medium Medium-high Risk mitigation
by automated
data backups and
use of advanced
access control
5
Council Elections via Online Electronic Voting
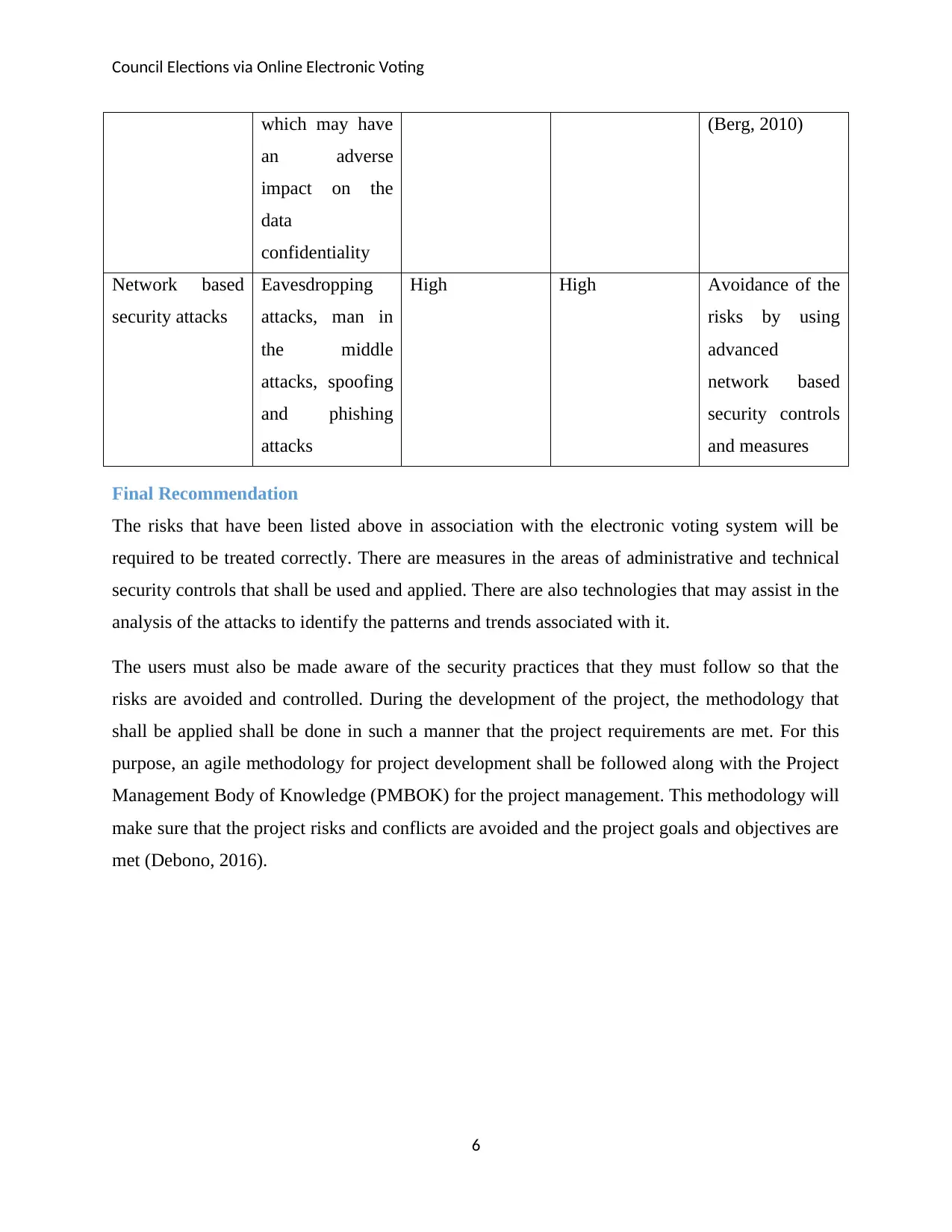
which may have
an adverse
impact on the
data
confidentiality
(Berg, 2010)
Network based
security attacks
Eavesdropping
attacks, man in
the middle
attacks, spoofing
and phishing
attacks
High High Avoidance of the
risks by using
advanced
network based
security controls
and measures
Final Recommendation
The risks that have been listed above in association with the electronic voting system will be
required to be treated correctly. There are measures in the areas of administrative and technical
security controls that shall be used and applied. There are also technologies that may assist in the
analysis of the attacks to identify the patterns and trends associated with it.
The users must also be made aware of the security practices that they must follow so that the
risks are avoided and controlled. During the development of the project, the methodology that
shall be applied shall be done in such a manner that the project requirements are met. For this
purpose, an agile methodology for project development shall be followed along with the Project
Management Body of Knowledge (PMBOK) for the project management. This methodology will
make sure that the project risks and conflicts are avoided and the project goals and objectives are
met (Debono, 2016).
6
which may have
an adverse
impact on the
data
confidentiality
(Berg, 2010)
Network based
security attacks
Eavesdropping
attacks, man in
the middle
attacks, spoofing
and phishing
attacks
High High Avoidance of the
risks by using
advanced
network based
security controls
and measures
Final Recommendation
The risks that have been listed above in association with the electronic voting system will be
required to be treated correctly. There are measures in the areas of administrative and technical
security controls that shall be used and applied. There are also technologies that may assist in the
analysis of the attacks to identify the patterns and trends associated with it.
The users must also be made aware of the security practices that they must follow so that the
risks are avoided and controlled. During the development of the project, the methodology that
shall be applied shall be done in such a manner that the project requirements are met. For this
purpose, an agile methodology for project development shall be followed along with the Project
Management Body of Knowledge (PMBOK) for the project management. This methodology will
make sure that the project risks and conflicts are avoided and the project goals and objectives are
met (Debono, 2016).
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Council Elections via Online Electronic Voting
References
Berg, H. (2010). Risk Management: Procedures, Methods and Experiences. [online] Available
at: http://ww.gnedenko-forum.org/Journal/2010/022010/RTA_2_2010-09.pdf [Accessed 18 Sep.
2017].
Chung, L. (2013). Non-Functional Requirements. [online] Available at:
https://www.utdallas.edu/~chung/SYSM6309/NFR-18-4-on-1.pdf [Accessed 19 Sep. 2017].
Crane, L. (2013). Introduction to Risk Management. [online] Available at:
http://extensionrme.org/pubs/IntroductionToRiskManagement.pdf [Accessed 18 Sep. 2017].
Dcu (2015). Introduction to Risk Management. [online] Available at:
https://www.dcu.ie/sites/default/files/ocoo/pdfs/Risk%20Mgt%20Training%20Slides.pdf
[Accessed 18 Sep. 2017].
Debono, R. (2016). Project Risk Management. [online] Available at:
http://www.isaca.org/chapters11/Malta/Documents/Events/210416%20-%20Mark_Debono%20-
%20Understanding_Risk_in_the_Field_of_Project_Management.pdf [Accessed 18 Sep. 2017].
Eeles, P. (2015). Non-Functional Requirements. [online] Available at:
http://www.architecting.co.uk/presentations/NFRs.pdf [Accessed 19 Sep. 2017].
Pareek, R. (2011). Network Security: An Approach towards Secure Computing. [online]
Available at: https://www.rroij.com/open-access/network-security-an-approach-towards-secure-
computing-160-163.pdf [Accessed 16 Sep. 2017].
Soriano, M. (2011). Information and Network Security. [online] Available at:
http://improvet.cvut.cz/project/download/C2EN/Information_and_network_security.pdf
[Accessed 18 Sep. 2017].
7
References
Berg, H. (2010). Risk Management: Procedures, Methods and Experiences. [online] Available
at: http://ww.gnedenko-forum.org/Journal/2010/022010/RTA_2_2010-09.pdf [Accessed 18 Sep.
2017].
Chung, L. (2013). Non-Functional Requirements. [online] Available at:
https://www.utdallas.edu/~chung/SYSM6309/NFR-18-4-on-1.pdf [Accessed 19 Sep. 2017].
Crane, L. (2013). Introduction to Risk Management. [online] Available at:
http://extensionrme.org/pubs/IntroductionToRiskManagement.pdf [Accessed 18 Sep. 2017].
Dcu (2015). Introduction to Risk Management. [online] Available at:
https://www.dcu.ie/sites/default/files/ocoo/pdfs/Risk%20Mgt%20Training%20Slides.pdf
[Accessed 18 Sep. 2017].
Debono, R. (2016). Project Risk Management. [online] Available at:
http://www.isaca.org/chapters11/Malta/Documents/Events/210416%20-%20Mark_Debono%20-
%20Understanding_Risk_in_the_Field_of_Project_Management.pdf [Accessed 18 Sep. 2017].
Eeles, P. (2015). Non-Functional Requirements. [online] Available at:
http://www.architecting.co.uk/presentations/NFRs.pdf [Accessed 19 Sep. 2017].
Pareek, R. (2011). Network Security: An Approach towards Secure Computing. [online]
Available at: https://www.rroij.com/open-access/network-security-an-approach-towards-secure-
computing-160-163.pdf [Accessed 16 Sep. 2017].
Soriano, M. (2011). Information and Network Security. [online] Available at:
http://improvet.cvut.cz/project/download/C2EN/Information_and_network_security.pdf
[Accessed 18 Sep. 2017].
7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




