Project Report: Development of an Online Mobile Shopping Application
VerifiedAdded on 2023/04/23
|22
|3826
|322
Report
AI Summary
This project report details the development of an Android-based online mobile application designed for product purchasing. The report covers various aspects, including project objectives, opportunity analysis, and a comprehensive feasibility study encompassing operational, financial, and technical considerations. It addresses project risk management by identifying potential threats and proposing mitigation techniques. The work breakdown structure (WBS) outlines the project's phases, from project management to system grounding. The report further discusses the influence of the WBS on the system and presents project milestones. The application aims to facilitate product purchases directly from vendors, offering features like product access, shopping carts, and online payment methods, ultimately providing users with a convenient and accessible e-commerce experience. It emphasizes the importance of security, user experience, and system efficiency.

Running head: Mobile Application
A project Report
On
ONLINE MOBILE APPLICATION
Name of the Student
Name of the University
Name of the Author
A project Report
On
ONLINE MOBILE APPLICATION
Name of the Student
Name of the University
Name of the Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1Online shopping system
Table of Contents
Introduction:...............................................................................................................................3
Project Objectives:.....................................................................................................................3
Project Opportunity:...................................................................................................................4
Feasibility Study:.......................................................................................................................4
Operational Feasibility:..........................................................................................................5
Financial Feasibility:..............................................................................................................5
Technical Feasibility:.............................................................................................................6
Project Risk Management:.........................................................................................................7
Identification Project Threats...............................................................................................8
Threat Influence.....................................................................................................................8
Threat Management Technique..............................................................................................8
Work Break-Down Structure:..................................................................................................10
1. Implementation and Establishment of Project management.........................................10
2. Business Necessity........................................................................................................10
3. System Architecture......................................................................................................11
4. Technical Essentiality...................................................................................................11
5. Implementation of the System......................................................................................12
6. System Testing..............................................................................................................12
Table of Contents
Introduction:...............................................................................................................................3
Project Objectives:.....................................................................................................................3
Project Opportunity:...................................................................................................................4
Feasibility Study:.......................................................................................................................4
Operational Feasibility:..........................................................................................................5
Financial Feasibility:..............................................................................................................5
Technical Feasibility:.............................................................................................................6
Project Risk Management:.........................................................................................................7
Identification Project Threats...............................................................................................8
Threat Influence.....................................................................................................................8
Threat Management Technique..............................................................................................8
Work Break-Down Structure:..................................................................................................10
1. Implementation and Establishment of Project management.........................................10
2. Business Necessity........................................................................................................10
3. System Architecture......................................................................................................11
4. Technical Essentiality...................................................................................................11
5. Implementation of the System......................................................................................12
6. System Testing..............................................................................................................12

2Online shopping system
7. System Utilization Development..................................................................................12
8. Grounding.....................................................................................................................13
Project milestone statement:................................................................................................13
Influence of Work Breakdown Structure in the system:......................................................14
Accumulations of the Proposed System:..................................................................................15
Work breakdown structure with its Resource relation:........................................................16
Assumption of the Project Outcome:...................................................................................16
Conclusion:..............................................................................................................................17
Reference List..........................................................................................................................19
7. System Utilization Development..................................................................................12
8. Grounding.....................................................................................................................13
Project milestone statement:................................................................................................13
Influence of Work Breakdown Structure in the system:......................................................14
Accumulations of the Proposed System:..................................................................................15
Work breakdown structure with its Resource relation:........................................................16
Assumption of the Project Outcome:...................................................................................16
Conclusion:..............................................................................................................................17
Reference List..........................................................................................................................19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3Online shopping system
Introduction:
The purpose of this project is to implement an application on mobile platform which
will portray an application of Product Purchasing through internet. The central aim of the
approached application is to develop a specific Product purchasing System through internet
into Android Platform.
The approached application will offer several functionalities which includes the
method to access the desired products and buy them directly from the vendor via internet,
thus no negotiators interruption is needed. The approached application is an e-commerce
application. Proposed electronic commerce system is developed to facilitate the user with the
functionalities of product purchasing directly from the vendor through internet (Schafer et al.,
2017). It will provide a benefits of buying products via internet from anywhere any time to
the Android user. Therefore, the user facilitate with the advantage of purchasing goods from
their preferable vendors as well as will get a home delivery service (Einav et al., 2014).
Project Objectives:
This project is proposed in order to develop an Android based online application to
purchase goods online from the existing vendor. In order to implement this e-commerce
application, it needs a strong support from web service provider. Primary aim of this
approached system is to implement an efficient and a comprehensive web application. This
system will be developed on an Android platform along with the website view. It will also
provide the users a shopping facility from independent locations. This application is an
android based mobile application thus, it offers the customer the facility to buy product from
anytime anywhere.
Introduction:
The purpose of this project is to implement an application on mobile platform which
will portray an application of Product Purchasing through internet. The central aim of the
approached application is to develop a specific Product purchasing System through internet
into Android Platform.
The approached application will offer several functionalities which includes the
method to access the desired products and buy them directly from the vendor via internet,
thus no negotiators interruption is needed. The approached application is an e-commerce
application. Proposed electronic commerce system is developed to facilitate the user with the
functionalities of product purchasing directly from the vendor through internet (Schafer et al.,
2017). It will provide a benefits of buying products via internet from anywhere any time to
the Android user. Therefore, the user facilitate with the advantage of purchasing goods from
their preferable vendors as well as will get a home delivery service (Einav et al., 2014).
Project Objectives:
This project is proposed in order to develop an Android based online application to
purchase goods online from the existing vendor. In order to implement this e-commerce
application, it needs a strong support from web service provider. Primary aim of this
approached system is to implement an efficient and a comprehensive web application. This
system will be developed on an Android platform along with the website view. It will also
provide the users a shopping facility from independent locations. This application is an
android based mobile application thus, it offers the customer the facility to buy product from
anytime anywhere.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4Online shopping system
Project Opportunity:
The online purchasing application is entirely concerning with buying and saleing the
products as well as desired services through internet from customer preferable shop without
any physically movement. The approached online purchasing application will provide various
beneficial operations such as accessing of goods via internet, goods shopping, payment
through internet as well as a facility of home delivery. Accompanying these beneficial
operations, the shopping Cart also offers several beneficial functionalities like a user can pick
any preferable item and then drop it to the shopping cart and resume product accessing until
the final selection of user. The customer can also modify goods quantity from the shopping
cart any time before placing the order and user can remove the item too.
In this proposed online shopping application, the cash on delivery facility is not
present thus, the customer must familiar with the process of online payment.
Feasibility Study:
Based on the study of Cheng et al., (2015) the feasibility analysis is conduct to
determine the usefulness of the approached system. This approached system has accounted
three probable factors to determine feasibility of the approached system such as Operational
Feasibility, Financial Feasibility and Technical Feasibility.
Project Opportunity:
The online purchasing application is entirely concerning with buying and saleing the
products as well as desired services through internet from customer preferable shop without
any physically movement. The approached online purchasing application will provide various
beneficial operations such as accessing of goods via internet, goods shopping, payment
through internet as well as a facility of home delivery. Accompanying these beneficial
operations, the shopping Cart also offers several beneficial functionalities like a user can pick
any preferable item and then drop it to the shopping cart and resume product accessing until
the final selection of user. The customer can also modify goods quantity from the shopping
cart any time before placing the order and user can remove the item too.
In this proposed online shopping application, the cash on delivery facility is not
present thus, the customer must familiar with the process of online payment.
Feasibility Study:
Based on the study of Cheng et al., (2015) the feasibility analysis is conduct to
determine the usefulness of the approached system. This approached system has accounted
three probable factors to determine feasibility of the approached system such as Operational
Feasibility, Financial Feasibility and Technical Feasibility.

5Online shopping system
Operational Feasibility:
The inspection procedure is basically focused on how the proposed application is
meeting all the desired needs of the administrator as well as the customer. This approached
application will considered as the probable operational system if it able to addressed all its
necessities of admin after the installation of the application ( Rezzouk et al., 2015).
Following the study of Kebede et al., (2015) the study of Operational feasible inspection is
performed based on the following factors:
Proposed application will improve the comprehensive performance.
To address these aspects, the application will give enough value to the customer, and
will provide them various operational activities.
The proposed system will provide an enhanced market value to the vendor.
The proposed system will allow the user a worldwide accessing facility.
Following this study of operational feasibility factors of the approached application, it is
considered that the application has surely met all the mentioned factors. Hence, the system is
operationally feasible.
Financial Feasibility:
Mostly utilized process to analysing the usefulness of the approached application is
the Financial Feasibility inspection. When the profit of the system crosses overall cost of the
approached system, then only the application will proceed further for development process.
Operational Feasibility:
The inspection procedure is basically focused on how the proposed application is
meeting all the desired needs of the administrator as well as the customer. This approached
application will considered as the probable operational system if it able to addressed all its
necessities of admin after the installation of the application ( Rezzouk et al., 2015).
Following the study of Kebede et al., (2015) the study of Operational feasible inspection is
performed based on the following factors:
Proposed application will improve the comprehensive performance.
To address these aspects, the application will give enough value to the customer, and
will provide them various operational activities.
The proposed system will provide an enhanced market value to the vendor.
The proposed system will allow the user a worldwide accessing facility.
Following this study of operational feasibility factors of the approached application, it is
considered that the application has surely met all the mentioned factors. Hence, the system is
operationally feasible.
Financial Feasibility:
Mostly utilized process to analysing the usefulness of the approached application is
the Financial Feasibility inspection. When the profit of the system crosses overall cost of the
approached system, then only the application will proceed further for development process.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6Online shopping system
Based on the study of Gao et al., (2016) the economical feasibility inspection will be
performed on the basis of the mentioned factors below:
The application should consist inexpensive Hardware as well as Software
specifications.
The entire cost will be less expensive while representing it in global platforms.
It must be highly profitable while performing in the global platform.
Low cost maintenance of the developed system.
Following this study of financial feasibility factors of the approached application, it is
considered that the approached application has surely met all the mentioned factors. Hence,
the system is economically feasible.
In order to provide the system application more efficiency, the system should offers
various ways to contact the admin, and it should also enhance its web page structure. The
application must offer cash on delivery procedure for product buying.
Technical Feasibility:
This inspection is basically focused on the hardware as well as the software
equipment. Accompanying those specifications furthermore it involves few essential
technical influence that are the software reliability, access of the accurate product, data
security, future extension of the gadget and technical validity ( Lui et al., 2017).
Based on the study of Gao et al., (2016) the economical feasibility inspection will be
performed on the basis of the mentioned factors below:
The application should consist inexpensive Hardware as well as Software
specifications.
The entire cost will be less expensive while representing it in global platforms.
It must be highly profitable while performing in the global platform.
Low cost maintenance of the developed system.
Following this study of financial feasibility factors of the approached application, it is
considered that the approached application has surely met all the mentioned factors. Hence,
the system is economically feasible.
In order to provide the system application more efficiency, the system should offers
various ways to contact the admin, and it should also enhance its web page structure. The
application must offer cash on delivery procedure for product buying.
Technical Feasibility:
This inspection is basically focused on the hardware as well as the software
equipment. Accompanying those specifications furthermore it involves few essential
technical influence that are the software reliability, access of the accurate product, data
security, future extension of the gadget and technical validity ( Lui et al., 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Online shopping system
Technical feasibility inspection will be accomplished based on these following factors:
Existence technology for the system installation.
Proposed application must be modified by the administrator. The admin should be
permitted to modify the system.
Hardware as well as the software specification of the approached system must be
liable with accurate privacy, back up and security.
Proposed application is enough efficient to store the information for further use.
Proposed application is enough efficient to dispense the customer a correct reply and
should permit the number of the customer regardless to access the system.
Followed by the analysis of the technical feasibility factors of the approached application,
it can be expressed that the approached application has addressed all the mentioned factors
perfectly. Therefore, the approached application is technically feasible.
Project Risk Management:
Although, there are various advantages of product purchasing via internet, it also
contains of several major threat factors. After, studying the threat aspects of the proposed
shopping system, it can be stated that these threats have significant influence on the
approached application. However, various threats are there in the proposed shopping system,
these threats can be handled if the administrator and the customer obey some risk
Technical feasibility inspection will be accomplished based on these following factors:
Existence technology for the system installation.
Proposed application must be modified by the administrator. The admin should be
permitted to modify the system.
Hardware as well as the software specification of the approached system must be
liable with accurate privacy, back up and security.
Proposed application is enough efficient to store the information for further use.
Proposed application is enough efficient to dispense the customer a correct reply and
should permit the number of the customer regardless to access the system.
Followed by the analysis of the technical feasibility factors of the approached application,
it can be expressed that the approached application has addressed all the mentioned factors
perfectly. Therefore, the approached application is technically feasible.
Project Risk Management:
Although, there are various advantages of product purchasing via internet, it also
contains of several major threat factors. After, studying the threat aspects of the proposed
shopping system, it can be stated that these threats have significant influence on the
approached application. However, various threats are there in the proposed shopping system,
these threats can be handled if the administrator and the customer obey some risk

8Online shopping system
management technique. The following table contains the entire detail about the proposed
system threat identification, its influence and management technique.
management technique. The following table contains the entire detail about the proposed
system threat identification, its influence and management technique.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
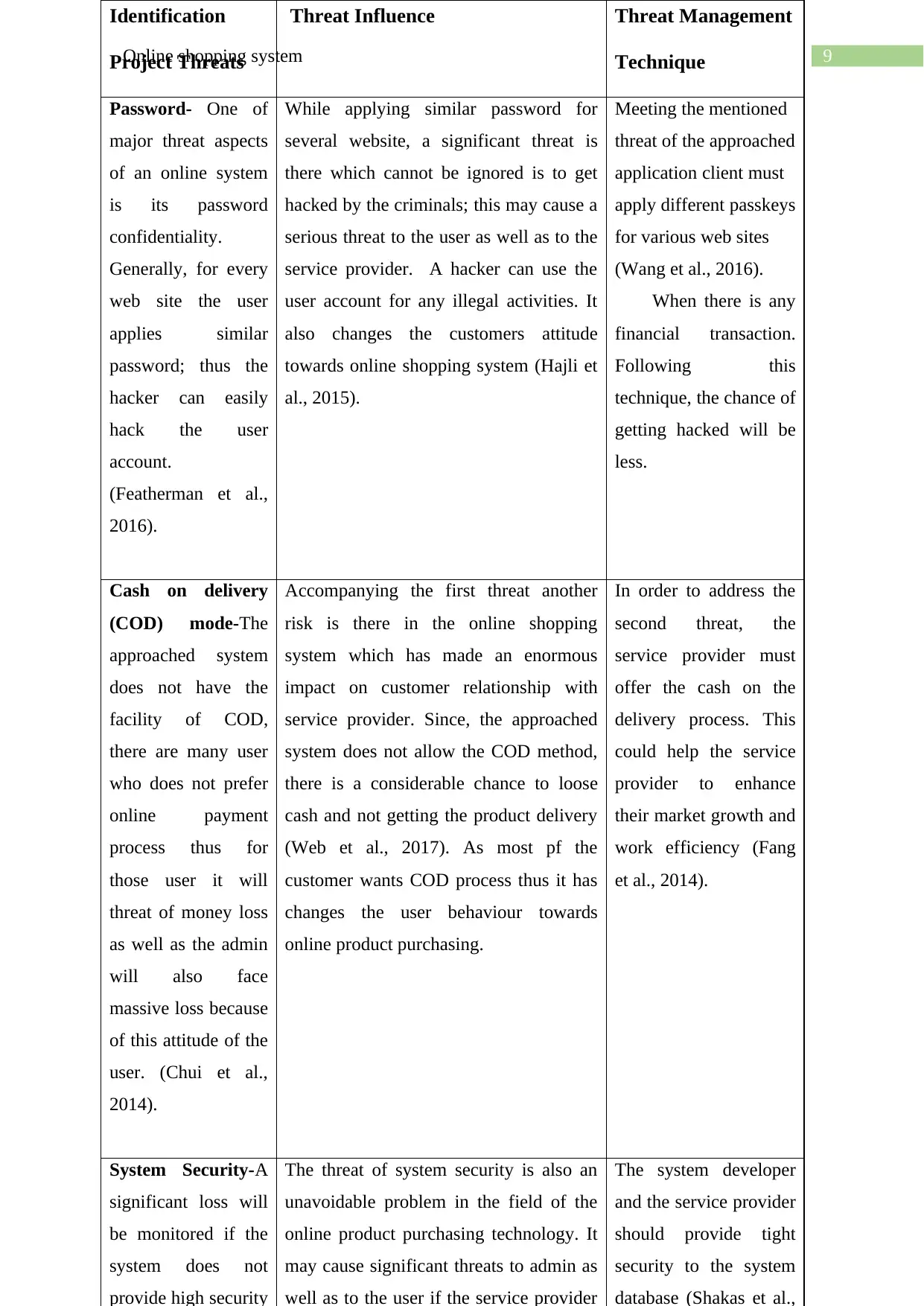
9Online shopping system
Identification
Project Threats
Threat Influence Threat Management
Technique
Password- One of
major threat aspects
of an online system
is its password
confidentiality.
Generally, for every
web site the user
applies similar
password; thus the
hacker can easily
hack the user
account.
(Featherman et al.,
2016).
While applying similar password for
several website, a significant threat is
there which cannot be ignored is to get
hacked by the criminals; this may cause a
serious threat to the user as well as to the
service provider. A hacker can use the
user account for any illegal activities. It
also changes the customers attitude
towards online shopping system (Hajli et
al., 2015).
Meeting the mentioned
threat of the approached
application client must
apply different passkeys
for various web sites
(Wang et al., 2016).
When there is any
financial transaction.
Following this
technique, the chance of
getting hacked will be
less.
Cash on delivery
(COD) mode-The
approached system
does not have the
facility of COD,
there are many user
who does not prefer
online payment
process thus for
those user it will
threat of money loss
as well as the admin
will also face
massive loss because
of this attitude of the
user. (Chui et al.,
2014).
Accompanying the first threat another
risk is there in the online shopping
system which has made an enormous
impact on customer relationship with
service provider. Since, the approached
system does not allow the COD method,
there is a considerable chance to loose
cash and not getting the product delivery
(Web et al., 2017). As most pf the
customer wants COD process thus it has
changes the user behaviour towards
online product purchasing.
In order to address the
second threat, the
service provider must
offer the cash on the
delivery process. This
could help the service
provider to enhance
their market growth and
work efficiency (Fang
et al., 2014).
System Security-A
significant loss will
be monitored if the
system does not
provide high security
The threat of system security is also an
unavoidable problem in the field of the
online product purchasing technology. It
may cause significant threats to admin as
well as to the user if the service provider
The system developer
and the service provider
should provide tight
security to the system
database (Shakas et al.,
Identification
Project Threats
Threat Influence Threat Management
Technique
Password- One of
major threat aspects
of an online system
is its password
confidentiality.
Generally, for every
web site the user
applies similar
password; thus the
hacker can easily
hack the user
account.
(Featherman et al.,
2016).
While applying similar password for
several website, a significant threat is
there which cannot be ignored is to get
hacked by the criminals; this may cause a
serious threat to the user as well as to the
service provider. A hacker can use the
user account for any illegal activities. It
also changes the customers attitude
towards online shopping system (Hajli et
al., 2015).
Meeting the mentioned
threat of the approached
application client must
apply different passkeys
for various web sites
(Wang et al., 2016).
When there is any
financial transaction.
Following this
technique, the chance of
getting hacked will be
less.
Cash on delivery
(COD) mode-The
approached system
does not have the
facility of COD,
there are many user
who does not prefer
online payment
process thus for
those user it will
threat of money loss
as well as the admin
will also face
massive loss because
of this attitude of the
user. (Chui et al.,
2014).
Accompanying the first threat another
risk is there in the online shopping
system which has made an enormous
impact on customer relationship with
service provider. Since, the approached
system does not allow the COD method,
there is a considerable chance to loose
cash and not getting the product delivery
(Web et al., 2017). As most pf the
customer wants COD process thus it has
changes the user behaviour towards
online product purchasing.
In order to address the
second threat, the
service provider must
offer the cash on the
delivery process. This
could help the service
provider to enhance
their market growth and
work efficiency (Fang
et al., 2014).
System Security-A
significant loss will
be monitored if the
system does not
provide high security
The threat of system security is also an
unavoidable problem in the field of the
online product purchasing technology. It
may cause significant threats to admin as
well as to the user if the service provider
The system developer
and the service provider
should provide tight
security to the system
database (Shakas et al.,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10Online shopping system
Work Break-Down Structure:
Work breakdown structure helps to give an outline of any system that defines all the pivotal
attributes and operations of that specific system.
1. Implementation and Establishment of Project management
1.1. Partnership Management Plan.
1.2. Service procurement and management Plan.
1.3. Project opportunity improvement.
1.4. Threat Management Strategy.
1.5. Superiority management Strategy.
1.6. Economics management.
1.7. Strategy of structuring the work flow.
1.8. File management Procedure.
2. Business Necessity
2.1. Investigation of existing application.
2.2. Investigation of existing systems documentation and human resources.
2.3. Contract Regulator.
2.4. Inspection management.
2.5. Reporting.
i. User end.
ii. User management.
Work Break-Down Structure:
Work breakdown structure helps to give an outline of any system that defines all the pivotal
attributes and operations of that specific system.
1. Implementation and Establishment of Project management
1.1. Partnership Management Plan.
1.2. Service procurement and management Plan.
1.3. Project opportunity improvement.
1.4. Threat Management Strategy.
1.5. Superiority management Strategy.
1.6. Economics management.
1.7. Strategy of structuring the work flow.
1.8. File management Procedure.
2. Business Necessity
2.1. Investigation of existing application.
2.2. Investigation of existing systems documentation and human resources.
2.3. Contract Regulator.
2.4. Inspection management.
2.5. Reporting.
i. User end.
ii. User management.

11Online shopping system
iii. Technical system management.
iv. Third party interruption.
2.6. Repercussion estimation of the application
i. Third party interruption.
ii. Estimation of provision data.
2.7. Definition of the proposed business strategy.
2.8. Work flow structure of the proposed system.
2.9. UI essentiality.
2.10. Technical Necessity.
2.11. Essential Documentation.
3. System Architecture
3.1. Description of system activities.
3.2. Progress Report.
3.3. N-tier logic.
3.4. Database Structure.
4. Technical Essentiality
4.1. Specification of selected platform.
4.2. Language Description.
4.3. User Signup procedure.
iii. Technical system management.
iv. Third party interruption.
2.6. Repercussion estimation of the application
i. Third party interruption.
ii. Estimation of provision data.
2.7. Definition of the proposed business strategy.
2.8. Work flow structure of the proposed system.
2.9. UI essentiality.
2.10. Technical Necessity.
2.11. Essential Documentation.
3. System Architecture
3.1. Description of system activities.
3.2. Progress Report.
3.3. N-tier logic.
3.4. Database Structure.
4. Technical Essentiality
4.1. Specification of selected platform.
4.2. Language Description.
4.3. User Signup procedure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





