Computer Networks Assignment: Online Shopping, Cookies, and TCP
VerifiedAdded on 2023/06/07
|8
|1947
|475
Homework Assignment
AI Summary
This assignment solution delves into the application of computer networks principles within the context of online shopping and web technologies. Part 1 explores the use of cookies in tracking user behavior and managing sessions on an online shopping website, illustrating the step-by-step process of cookie utilization from client request to server response. It also examines the deployment of banner advertisements, detailing how cookies are used to track clicks and redirect users to external websites. Part 2 provides a comprehensive analysis of TCP connection establishment, data transfer, and termination. It breaks down the TCP segment structure, detailing the role of SYN, SYN+ACK, and ACK segments, along with the sequence and acknowledgment numbers, window sizes, and data bytes transferred across different phases of communication. The solution also explains the role of FIN segments in connection termination and provides segment tables to illustrate the flow of data and control information, including the port numbers involved in the communication process.

Computer Networks
Solution
Solution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. A). Online shopping has recently evolved due to advanced technology. So, to make the interaction
with the customer there must be a better understanding of what the customer need and behaviors to be
specific. This has been made possible by use of cookies to collect information and behaviors on a certain
website and all these provides a good background and know of what to display on the webpage and what
not to display (Braun, Münz, and Carle, 2010).
The diagram shows how cookies are used in an online shopping site in six different steps:
Step 1
The client wants to retrieve some information about toys from the besttoys.com website, so GET is used
because the client want to retrieve or get something (Howard, 2008.). The besttoys.com web server loads
the information as per the client request and a customer file is saved in the webserver with an ID 12343 to
identify that specific client which is a shopping cart where list of what client wants to shop is stored.
Step 2:
The server responds to the client request with the web page having different types of toys. At the same
time, a vendor file is created and in the client browser with the same ID 12343 as the customer file saved
in the web server of the besttoys.com and keeps on updating with client information. Also a cookie is set
which will be used to track the client (Huang, 2010). Whenever the client requests for something from
that specific website, it would be fast to log in. That cookie may last forever provided it is not destroyed.
Step 3
The web page the client is displayed contains different toys’ images which may act like links.The client
clicks an image of a certain toy on that web page, that image acts as a link to retrieval of more
information concerning that image which in turn is sent a request to the server where that request is send
together with the cookie: 12343.
with the customer there must be a better understanding of what the customer need and behaviors to be
specific. This has been made possible by use of cookies to collect information and behaviors on a certain
website and all these provides a good background and know of what to display on the webpage and what
not to display (Braun, Münz, and Carle, 2010).
The diagram shows how cookies are used in an online shopping site in six different steps:
Step 1
The client wants to retrieve some information about toys from the besttoys.com website, so GET is used
because the client want to retrieve or get something (Howard, 2008.). The besttoys.com web server loads
the information as per the client request and a customer file is saved in the webserver with an ID 12343 to
identify that specific client which is a shopping cart where list of what client wants to shop is stored.
Step 2:
The server responds to the client request with the web page having different types of toys. At the same
time, a vendor file is created and in the client browser with the same ID 12343 as the customer file saved
in the web server of the besttoys.com and keeps on updating with client information. Also a cookie is set
which will be used to track the client (Huang, 2010). Whenever the client requests for something from
that specific website, it would be fast to log in. That cookie may last forever provided it is not destroyed.
Step 3
The web page the client is displayed contains different toys’ images which may act like links.The client
clicks an image of a certain toy on that web page, that image acts as a link to retrieval of more
information concerning that image which in turn is sent a request to the server where that request is send
together with the cookie: 12343.

Step 4
After the server receives the request from the client, it displays back the page containing all the
information about the price of the image toy the client clicked. Then, that information is updated in the
customer file which is saved in the web server side (Lund et al., 2010). The cookie which was sent
together with the request is the one that helps the web server to track that specific client file from their
server and then is updated until the customer or client finishes to shop.
Step 5
Then, the customer requests from the same site information about the payment of the toy clicked, the
same thing happens, the request is sent together with the cookie: 12343, thus helping the server in
updating the file for that specific client.
Step 6
All through the cookie has been getting information about the client, so the request of the client about the
payment, is responded efficiently where an order confirmation web page is displayed on the client
browser according to what the client has selected from the webpage.
1. B). The banner advert is not hosted at the web server of the current website that it is being advertised
from. Deakin University is displaying an advert of a product in its website where it is paid by the
advertising company in accordance with the number of clicks of that advert which is linked to the
manufacturers’ web server.
The advertising company has to keep tracks of the number of clicks or visitors to the manufacturer’s
website using that banner advert, so application of cookies is a preferred option to track the visitors.
After the server receives the request from the client, it displays back the page containing all the
information about the price of the image toy the client clicked. Then, that information is updated in the
customer file which is saved in the web server side (Lund et al., 2010). The cookie which was sent
together with the request is the one that helps the web server to track that specific client file from their
server and then is updated until the customer or client finishes to shop.
Step 5
Then, the customer requests from the same site information about the payment of the toy clicked, the
same thing happens, the request is sent together with the cookie: 12343, thus helping the server in
updating the file for that specific client.
Step 6
All through the cookie has been getting information about the client, so the request of the client about the
payment, is responded efficiently where an order confirmation web page is displayed on the client
browser according to what the client has selected from the webpage.
1. B). The banner advert is not hosted at the web server of the current website that it is being advertised
from. Deakin University is displaying an advert of a product in its website where it is paid by the
advertising company in accordance with the number of clicks of that advert which is linked to the
manufacturers’ web server.
The advertising company has to keep tracks of the number of clicks or visitors to the manufacturer’s
website using that banner advert, so application of cookies is a preferred option to track the visitors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
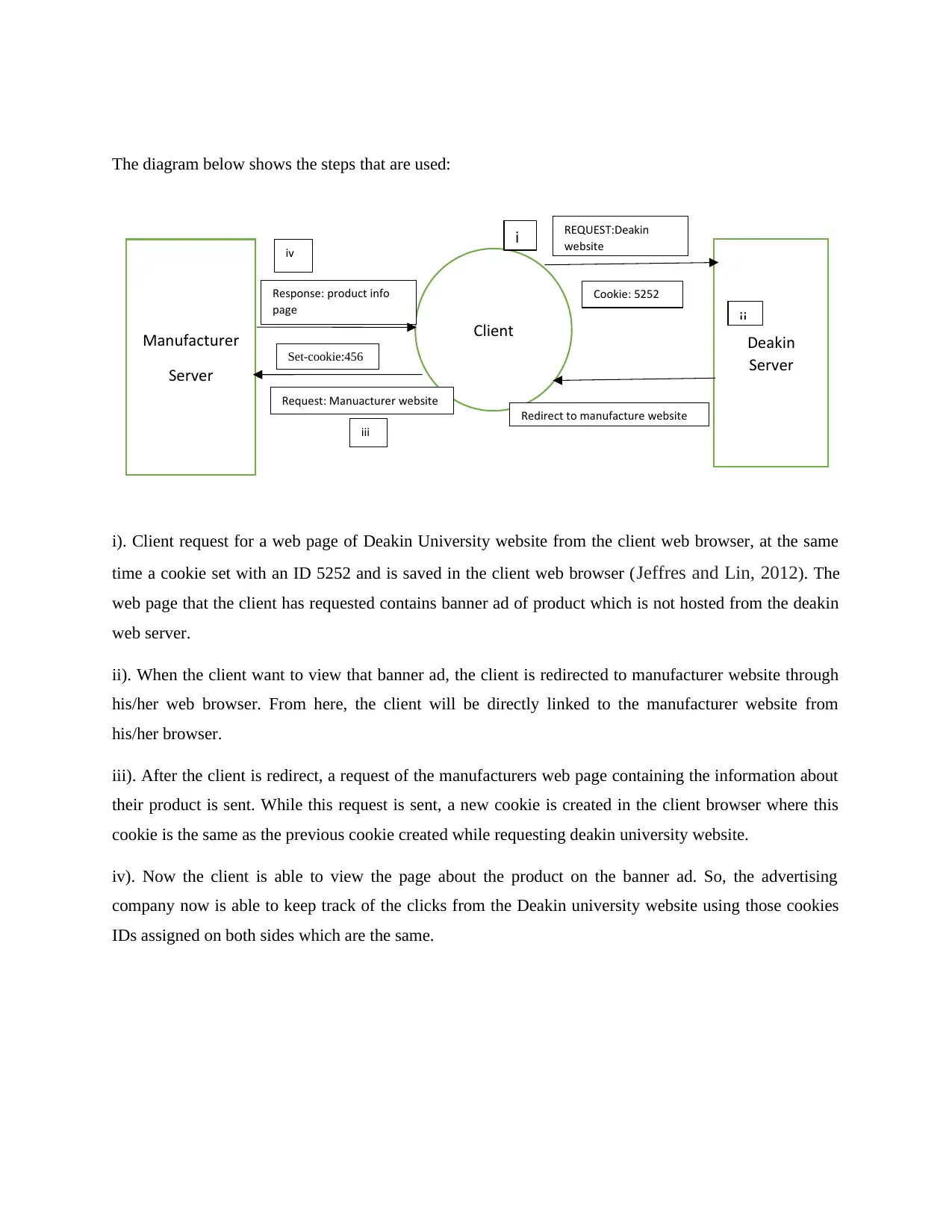
The diagram below shows the steps that are used:
i). Client request for a web page of Deakin University website from the client web browser, at the same
time a cookie set with an ID 5252 and is saved in the client web browser (Jeffres and Lin, 2012). The
web page that the client has requested contains banner ad of product which is not hosted from the deakin
web server.
ii). When the client want to view that banner ad, the client is redirected to manufacturer website through
his/her web browser. From here, the client will be directly linked to the manufacturer website from
his/her browser.
iii). After the client is redirect, a request of the manufacturers web page containing the information about
their product is sent. While this request is sent, a new cookie is created in the client browser where this
cookie is the same as the previous cookie created while requesting deakin university website.
iv). Now the client is able to view the page about the product on the banner ad. So, the advertising
company now is able to keep track of the clicks from the Deakin university website using those cookies
IDs assigned on both sides which are the same.
Client Deakin
Server
Manufacturer
Server
REQUEST:Deakin
website
Cookie: 5252
Request: Manuacturer website
Redirect to manufacture website
Set-cookie:456
i
ii
iv
iii
Response: product info
page
i). Client request for a web page of Deakin University website from the client web browser, at the same
time a cookie set with an ID 5252 and is saved in the client web browser (Jeffres and Lin, 2012). The
web page that the client has requested contains banner ad of product which is not hosted from the deakin
web server.
ii). When the client want to view that banner ad, the client is redirected to manufacturer website through
his/her web browser. From here, the client will be directly linked to the manufacturer website from
his/her browser.
iii). After the client is redirect, a request of the manufacturers web page containing the information about
their product is sent. While this request is sent, a new cookie is created in the client browser where this
cookie is the same as the previous cookie created while requesting deakin university website.
iv). Now the client is able to view the page about the product on the banner ad. So, the advertising
company now is able to keep track of the clicks from the Deakin university website using those cookies
IDs assigned on both sides which are the same.
Client Deakin
Server
Manufacturer
Server
REQUEST:Deakin
website
Cookie: 5252
Request: Manuacturer website
Redirect to manufacture website
Set-cookie:456
i
ii
iv
iii
Response: product info
page
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
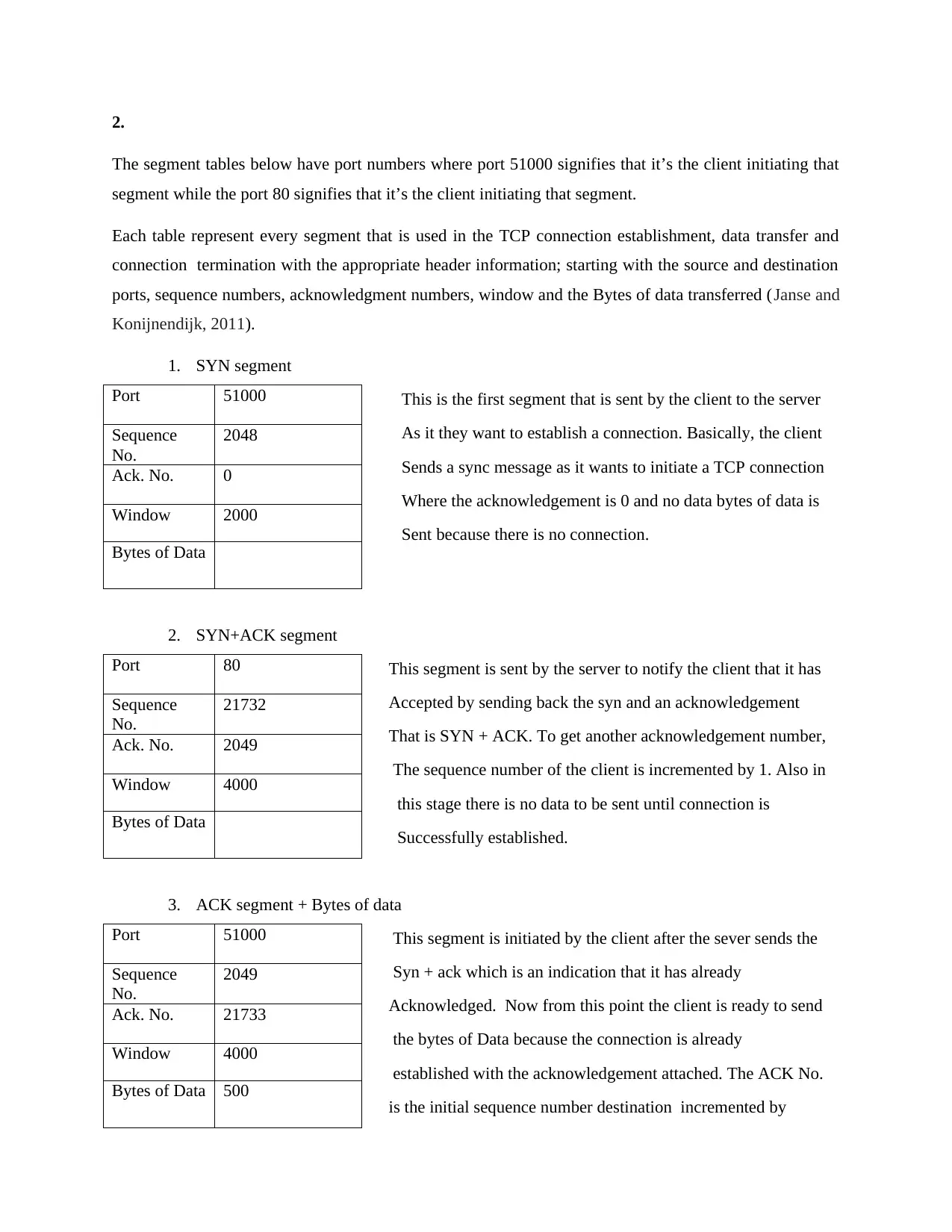
2.
The segment tables below have port numbers where port 51000 signifies that it’s the client initiating that
segment while the port 80 signifies that it’s the client initiating that segment.
Each table represent every segment that is used in the TCP connection establishment, data transfer and
connection termination with the appropriate header information; starting with the source and destination
ports, sequence numbers, acknowledgment numbers, window and the Bytes of data transferred (Janse and
Konijnendijk, 2011).
1. SYN segment
This is the first segment that is sent by the client to the server
As it they want to establish a connection. Basically, the client
Sends a sync message as it wants to initiate a TCP connection
Where the acknowledgement is 0 and no data bytes of data is
Sent because there is no connection.
2. SYN+ACK segment
This segment is sent by the server to notify the client that it has
Accepted by sending back the syn and an acknowledgement
That is SYN + ACK. To get another acknowledgement number,
The sequence number of the client is incremented by 1. Also in
this stage there is no data to be sent until connection is
Successfully established.
3. ACK segment + Bytes of data
This segment is initiated by the client after the sever sends the
Syn + ack which is an indication that it has already
Acknowledged. Now from this point the client is ready to send
the bytes of Data because the connection is already
established with the acknowledgement attached. The ACK No.
is the initial sequence number destination incremented by
Port 51000
Sequence
No.
2048
Ack. No. 0
Window 2000
Bytes of Data
Port 80
Sequence
No.
21732
Ack. No. 2049
Window 4000
Bytes of Data
Port 51000
Sequence
No.
2049
Ack. No. 21733
Window 4000
Bytes of Data 500
The segment tables below have port numbers where port 51000 signifies that it’s the client initiating that
segment while the port 80 signifies that it’s the client initiating that segment.
Each table represent every segment that is used in the TCP connection establishment, data transfer and
connection termination with the appropriate header information; starting with the source and destination
ports, sequence numbers, acknowledgment numbers, window and the Bytes of data transferred (Janse and
Konijnendijk, 2011).
1. SYN segment
This is the first segment that is sent by the client to the server
As it they want to establish a connection. Basically, the client
Sends a sync message as it wants to initiate a TCP connection
Where the acknowledgement is 0 and no data bytes of data is
Sent because there is no connection.
2. SYN+ACK segment
This segment is sent by the server to notify the client that it has
Accepted by sending back the syn and an acknowledgement
That is SYN + ACK. To get another acknowledgement number,
The sequence number of the client is incremented by 1. Also in
this stage there is no data to be sent until connection is
Successfully established.
3. ACK segment + Bytes of data
This segment is initiated by the client after the sever sends the
Syn + ack which is an indication that it has already
Acknowledged. Now from this point the client is ready to send
the bytes of Data because the connection is already
established with the acknowledgement attached. The ACK No.
is the initial sequence number destination incremented by
Port 51000
Sequence
No.
2048
Ack. No. 0
Window 2000
Bytes of Data
Port 80
Sequence
No.
21732
Ack. No. 2049
Window 4000
Bytes of Data
Port 51000
Sequence
No.
2049
Ack. No. 21733
Window 4000
Bytes of Data 500
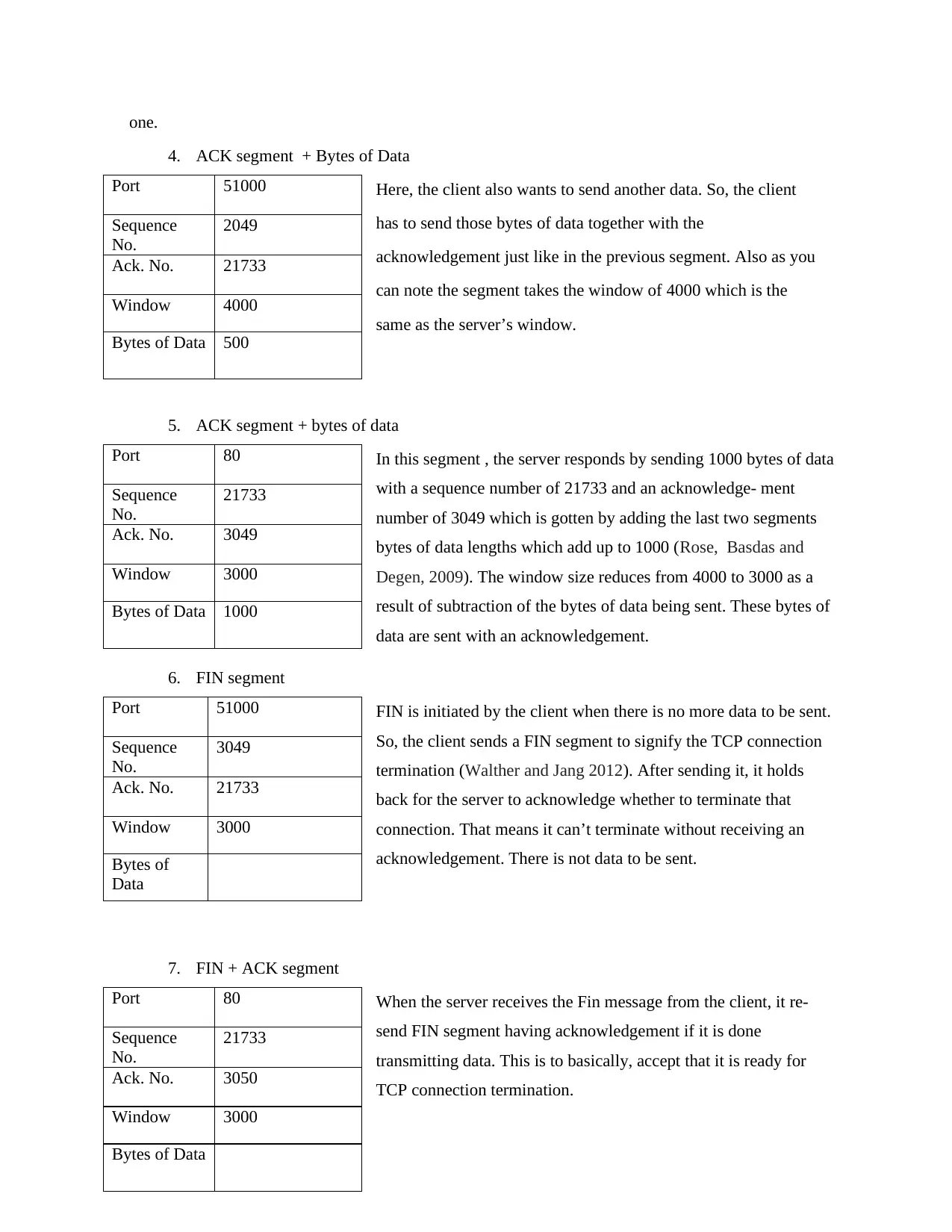
one.
4. ACK segment + Bytes of Data
Here, the client also wants to send another data. So, the client
has to send those bytes of data together with the
acknowledgement just like in the previous segment. Also as you
can note the segment takes the window of 4000 which is the
same as the server’s window.
5. ACK segment + bytes of data
In this segment , the server responds by sending 1000 bytes of data
with a sequence number of 21733 and an acknowledge- ment
number of 3049 which is gotten by adding the last two segments
bytes of data lengths which add up to 1000 (Rose, Basdas and
Degen, 2009). The window size reduces from 4000 to 3000 as a
result of subtraction of the bytes of data being sent. These bytes of
data are sent with an acknowledgement.
6. FIN segment
FIN is initiated by the client when there is no more data to be sent.
So, the client sends a FIN segment to signify the TCP connection
termination (Walther and Jang 2012). After sending it, it holds
back for the server to acknowledge whether to terminate that
connection. That means it can’t terminate without receiving an
acknowledgement. There is not data to be sent.
7. FIN + ACK segment
When the server receives the Fin message from the client, it re-
send FIN segment having acknowledgement if it is done
transmitting data. This is to basically, accept that it is ready for
TCP connection termination.
Port 51000
Sequence
No.
2049
Ack. No. 21733
Window 4000
Bytes of Data 500
Port 80
Sequence
No.
21733
Ack. No. 3049
Window 3000
Bytes of Data 1000
Port 51000
Sequence
No.
3049
Ack. No. 21733
Window 3000
Bytes of
Data
Port 80
Sequence
No.
21733
Ack. No. 3050
Window 3000
Bytes of Data
4. ACK segment + Bytes of Data
Here, the client also wants to send another data. So, the client
has to send those bytes of data together with the
acknowledgement just like in the previous segment. Also as you
can note the segment takes the window of 4000 which is the
same as the server’s window.
5. ACK segment + bytes of data
In this segment , the server responds by sending 1000 bytes of data
with a sequence number of 21733 and an acknowledge- ment
number of 3049 which is gotten by adding the last two segments
bytes of data lengths which add up to 1000 (Rose, Basdas and
Degen, 2009). The window size reduces from 4000 to 3000 as a
result of subtraction of the bytes of data being sent. These bytes of
data are sent with an acknowledgement.
6. FIN segment
FIN is initiated by the client when there is no more data to be sent.
So, the client sends a FIN segment to signify the TCP connection
termination (Walther and Jang 2012). After sending it, it holds
back for the server to acknowledge whether to terminate that
connection. That means it can’t terminate without receiving an
acknowledgement. There is not data to be sent.
7. FIN + ACK segment
When the server receives the Fin message from the client, it re-
send FIN segment having acknowledgement if it is done
transmitting data. This is to basically, accept that it is ready for
TCP connection termination.
Port 51000
Sequence
No.
2049
Ack. No. 21733
Window 4000
Bytes of Data 500
Port 80
Sequence
No.
21733
Ack. No. 3049
Window 3000
Bytes of Data 1000
Port 51000
Sequence
No.
3049
Ack. No. 21733
Window 3000
Bytes of
Data
Port 80
Sequence
No.
21733
Ack. No. 3050
Window 3000
Bytes of Data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
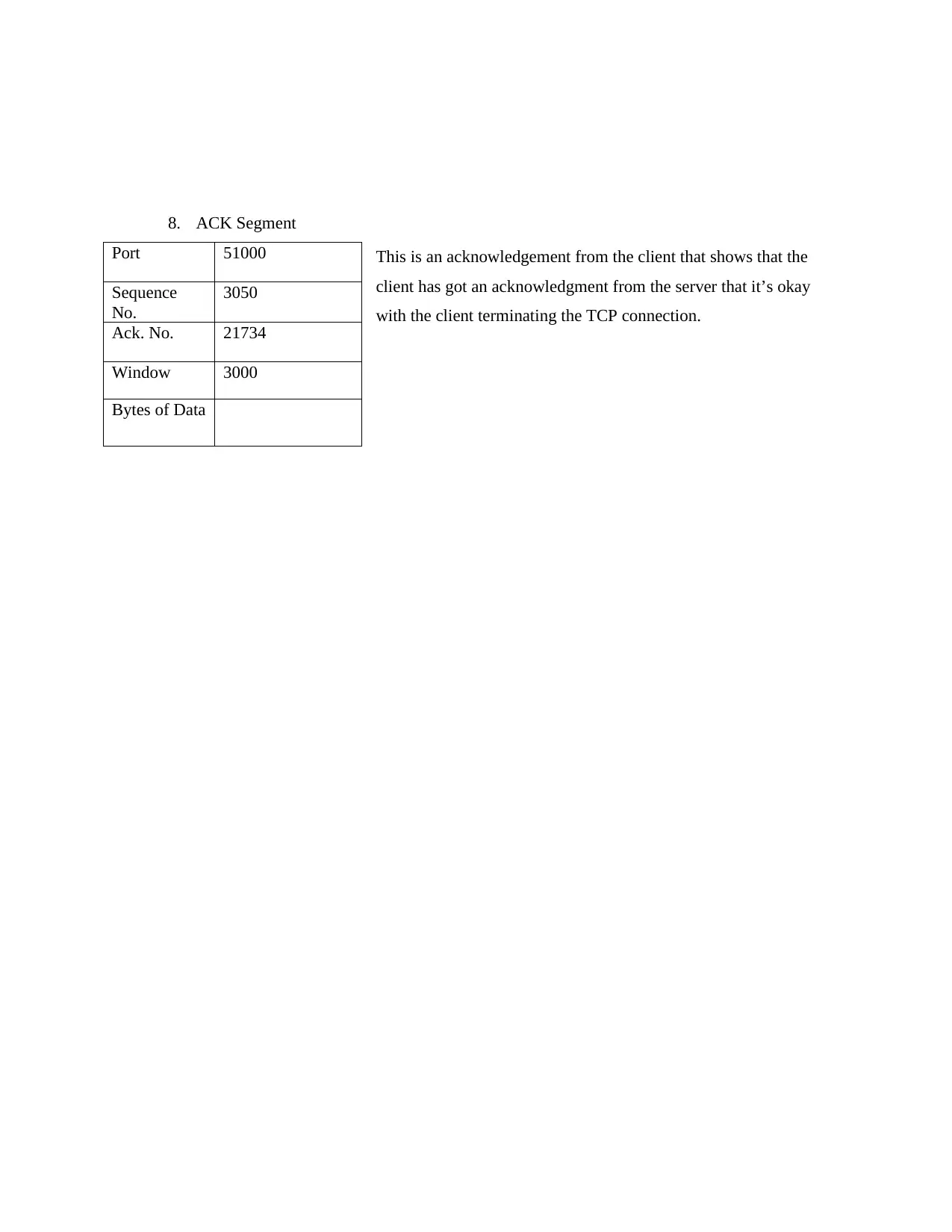
8. ACK Segment
This is an acknowledgement from the client that shows that the
client has got an acknowledgment from the server that it’s okay
with the client terminating the TCP connection.
Port 51000
Sequence
No.
3050
Ack. No. 21734
Window 3000
Bytes of Data
This is an acknowledgement from the client that shows that the
client has got an acknowledgment from the server that it’s okay
with the client terminating the TCP connection.
Port 51000
Sequence
No.
3050
Ack. No. 21734
Window 3000
Bytes of Data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Braun, L., Münz, G. and Carle, G., 2010, April. Packet sampling for worm and botnet detection in TCP
connections. In Network Operations and Management Symposium (NOMS), 2010 IEEE (pp. 264-271).
IEEE.
Howard, R.G., 2008. The vernacular web of participatory media. Critical Studies in Media
Communication, 25(5), pp.490-513.
Huang, M.H., 2010. Designing website attributes to induce experiential encounters. computers in Human
Behavior, 19(4), pp.425-442.
Lund, P.K., Petry, S.M., Croteau, C.S., Okumura, K.K. and Carroll, D.A., Google Inc, 2010. Source
reputation information system with blocking of TCP connections from sources of electronic messages.
U.S. Patent 7,788,359.
Janse, G. and Konijnendijk, C.C., 2011. Communication between science, policy and citizens in public
participation in urban forestry websites—Experiences from the Neighbourwoods project. Urban Forestry
& Urban Greening, 6(1), pp.23-40.
Jeffres, L.W. and Lin, C.A., 2012. Metropolitan websites as urban communication. Journal of Computer-
Mediated Communication, 11(4), pp.957-980.
Rose, G., Basdas, B. and Degen, M., 2009. Using websites to disseminate research on urban
spatialities. Geography Compass, 3(6), pp.2098-2108.
Walther, J.B. and Jang, J.W., 2012. Communication processes in participatory websites. Journal of
Computer-Mediated Communication, 18(1), pp.2-15.
Braun, L., Münz, G. and Carle, G., 2010, April. Packet sampling for worm and botnet detection in TCP
connections. In Network Operations and Management Symposium (NOMS), 2010 IEEE (pp. 264-271).
IEEE.
Howard, R.G., 2008. The vernacular web of participatory media. Critical Studies in Media
Communication, 25(5), pp.490-513.
Huang, M.H., 2010. Designing website attributes to induce experiential encounters. computers in Human
Behavior, 19(4), pp.425-442.
Lund, P.K., Petry, S.M., Croteau, C.S., Okumura, K.K. and Carroll, D.A., Google Inc, 2010. Source
reputation information system with blocking of TCP connections from sources of electronic messages.
U.S. Patent 7,788,359.
Janse, G. and Konijnendijk, C.C., 2011. Communication between science, policy and citizens in public
participation in urban forestry websites—Experiences from the Neighbourwoods project. Urban Forestry
& Urban Greening, 6(1), pp.23-40.
Jeffres, L.W. and Lin, C.A., 2012. Metropolitan websites as urban communication. Journal of Computer-
Mediated Communication, 11(4), pp.957-980.
Rose, G., Basdas, B. and Degen, M., 2009. Using websites to disseminate research on urban
spatialities. Geography Compass, 3(6), pp.2098-2108.
Walther, J.B. and Jang, J.W., 2012. Communication processes in participatory websites. Journal of
Computer-Mediated Communication, 18(1), pp.2-15.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





