Comprehensive Report: ONOS Implementation, Security, and Performance
VerifiedAdded on 2019/12/03
|22
|4475
|384
Report
AI Summary
This report details the implementation of the Open Network Operating System (ONOS) for Cognizant, a medium-sized company establishing a network in Manchester, UK. The report covers the selection of ONOS as the preferred NOS due to its open-source nature and suitability for Software Defined Networking (SDN). It outlines the hardware and software requirements for ONOS installation, including Ubuntu Linux, Java, and specific ONOS parameters. The report emphasizes the importance of disaster recovery planning, security policies, and performance monitoring. It describes the implementation plan, including IP address allocation, and security policies such as password management and patch management. The report also includes illustrations of the LAN setup, ONOS components, and performance monitoring processes, providing a comprehensive overview of the network implementation, security considerations, and performance management strategies.

Network Operating System
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................4
TASK 1 Network operating system principles................................................................................4
1.1 Selection of NOS...................................................................................................................4
1.2 Disaster recovery availability and security in context of NOS..............................................5
1.3 ................................................................................................................................................6
TASK 2 ...........................................................................................................................................6
2.1 Detail plan of implementation of NOS .................................................................................6
2.2 Plan and evolution of disaster recovery plan for ONOS......................................................10
TASK 3..........................................................................................................................................11
3.1 & 3.2 Implementation and configuration of NOS...............................................................11
Installation of LAN network in Cognizant company ...............................................................13
TASK 4 manage network operating systems.................................................................................17
4.1 Performance baseline for the Manchester branch................................................................17
4.2 Performance monitoring report............................................................................................18
4.3 Describes the effective way to manage and monitor the performance of the network.......20
CONCLUSION..............................................................................................................................21
References .....................................................................................................................................22
2
Introduction......................................................................................................................................4
TASK 1 Network operating system principles................................................................................4
1.1 Selection of NOS...................................................................................................................4
1.2 Disaster recovery availability and security in context of NOS..............................................5
1.3 ................................................................................................................................................6
TASK 2 ...........................................................................................................................................6
2.1 Detail plan of implementation of NOS .................................................................................6
2.2 Plan and evolution of disaster recovery plan for ONOS......................................................10
TASK 3..........................................................................................................................................11
3.1 & 3.2 Implementation and configuration of NOS...............................................................11
Installation of LAN network in Cognizant company ...............................................................13
TASK 4 manage network operating systems.................................................................................17
4.1 Performance baseline for the Manchester branch................................................................17
4.2 Performance monitoring report............................................................................................18
4.3 Describes the effective way to manage and monitor the performance of the network.......20
CONCLUSION..............................................................................................................................21
References .....................................................................................................................................22
2

Illustration Index
Illustration 1: LAN setup...............................................................................................................14
Illustration 2: ONOS......................................................................................................................15
Illustration 3: Network graph and flow manager...........................................................................16
Illustration 4: Performance measurement process at Manchester..................................................18
Illustration 5: Performance monitoring .........................................................................................19
Illustration 6: Test performance monitoring .................................................................................20
3
Illustration 1: LAN setup...............................................................................................................14
Illustration 2: ONOS......................................................................................................................15
Illustration 3: Network graph and flow manager...........................................................................16
Illustration 4: Performance measurement process at Manchester..................................................18
Illustration 5: Performance monitoring .........................................................................................19
Illustration 6: Test performance monitoring .................................................................................20
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Network operating system can be defined as a computer operating system that is
designed to support different workstations of computer. It mainly includes remote access,
connectivity of network devices as well as storage of data with fell network security. There are
different NOS used by organizations such as Artisoft's LANtastic, Banyan VINES, Novell's
NetWare, and Microsoft's LAN Manager etc. The present report is based on the Medium sized
company named as Cognizant. Company wants to establish a network system in Manchester,
UK and also wants to span their network on two floors. Moreover, the overall planning and
designing of the network connection is described in this report with the overall hardware and
software requirements. For this purpose, remote desktop support is essential and it is quite
essential for network manager to allocate the minimal amount of support. In addition to this,
Cognizant can expand their business operations by setting their performance baseline as well as
security and scaling aspects. Disaster recovery methods and security concerns are described in
the present report as per the selected network operating system.
TASK 1 NETWORK OPERATING SYSTEM PRINCIPLES
1.1 Selection of NOS
As a network manager it is quite essential for me to develop a best network operating
system for Cognizant through which company can expand their business operations effectively.
There are different types of operating system some of which are open source or free of charge. It
is the best way to provide a platform to company to operate different application software. With
the help of the Network operating system company can easily manage all their network resources
(Cheng and et.al, 2011). There are different types of NOS such as: Artisoft's LANtastic: This type of NOS Mainly supports a wide variety of computer
operating system. These are the different computer operating system such as Windows
XP, Windows NT etc. It is a user friendly NOS and people can easily go through its
installation process. It also provides a chatting feature that allows all network PCs to
communicate with each other. In addition to this, it is very easy and simple to maintain
and it does not requires any extra cost for maintenance.
4
Network operating system can be defined as a computer operating system that is
designed to support different workstations of computer. It mainly includes remote access,
connectivity of network devices as well as storage of data with fell network security. There are
different NOS used by organizations such as Artisoft's LANtastic, Banyan VINES, Novell's
NetWare, and Microsoft's LAN Manager etc. The present report is based on the Medium sized
company named as Cognizant. Company wants to establish a network system in Manchester,
UK and also wants to span their network on two floors. Moreover, the overall planning and
designing of the network connection is described in this report with the overall hardware and
software requirements. For this purpose, remote desktop support is essential and it is quite
essential for network manager to allocate the minimal amount of support. In addition to this,
Cognizant can expand their business operations by setting their performance baseline as well as
security and scaling aspects. Disaster recovery methods and security concerns are described in
the present report as per the selected network operating system.
TASK 1 NETWORK OPERATING SYSTEM PRINCIPLES
1.1 Selection of NOS
As a network manager it is quite essential for me to develop a best network operating
system for Cognizant through which company can expand their business operations effectively.
There are different types of operating system some of which are open source or free of charge. It
is the best way to provide a platform to company to operate different application software. With
the help of the Network operating system company can easily manage all their network resources
(Cheng and et.al, 2011). There are different types of NOS such as: Artisoft's LANtastic: This type of NOS Mainly supports a wide variety of computer
operating system. These are the different computer operating system such as Windows
XP, Windows NT etc. It is a user friendly NOS and people can easily go through its
installation process. It also provides a chatting feature that allows all network PCs to
communicate with each other. In addition to this, it is very easy and simple to maintain
and it does not requires any extra cost for maintenance.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Novell's NetWare: This network operating system is totally based on the XNS protocol
architecture (Hart, 2013). There are various desktops available in the market and it
provide comprehensive support to all the system such as DOS, Windows, Macintosh,
UNIX etc. One of the main feature is that it supports the open source and licensed both
operating system. Open Network operating system: It is an SDN network operating system for all the
service providers. It was open sourced on December 5, 2014. It is basically architected
for performance, high availability, scale out and well defined abstractions and interfaced.
In addition to this, it can be stated that ONOS operating system comprises ON.Lab.
Microsoft LAN manager: LAN manager is a NOS that is designed and supported by the
Microsoft and runs under the Microsoft OS. This system also supports a good
multitasking functions as well as other OS such as DOS, Windows etc.
As per the given scenario, Cognizant uses ONOS (Open network operating system) is
being used as it is a open sources and it is based on the software define network. It bring out the
innovation and openness to the internet and cloud infrastructure with the help of the open source
tools and platforms. It helps the company in establishing local area network and sharing all the
information remotely. It also helps in distributing control platform for large scale networks and
focus on the reliability and scalability.
1.2 Disaster recovery availability and security in context of NOS
Nowadays in any organization one of the major concern is to go through the best network
availability. Disaster recovery can be define as a area through which company can go through the
security planning of all of the negative events. All such negative events includes anything that
puts an organization's operations at risk such as hacking, cyber attacks etc. At the time of using
any NOS the major problem is faced by the IT director is some sudden damages such as
physical damages to equipment like computer, routers as well as information loss. While using
ONOS company can get secure and effective disc backups (Karsai and et.al, 2011). In order to
overcome with the problems of sudden damages IT manager need to adopt best backup plans so
that they can keep their data secure. Managing and controlling the internal and external interrupts
in the network system is define as a process of disaster recovery. Moreover, it can be stated that
5
architecture (Hart, 2013). There are various desktops available in the market and it
provide comprehensive support to all the system such as DOS, Windows, Macintosh,
UNIX etc. One of the main feature is that it supports the open source and licensed both
operating system. Open Network operating system: It is an SDN network operating system for all the
service providers. It was open sourced on December 5, 2014. It is basically architected
for performance, high availability, scale out and well defined abstractions and interfaced.
In addition to this, it can be stated that ONOS operating system comprises ON.Lab.
Microsoft LAN manager: LAN manager is a NOS that is designed and supported by the
Microsoft and runs under the Microsoft OS. This system also supports a good
multitasking functions as well as other OS such as DOS, Windows etc.
As per the given scenario, Cognizant uses ONOS (Open network operating system) is
being used as it is a open sources and it is based on the software define network. It bring out the
innovation and openness to the internet and cloud infrastructure with the help of the open source
tools and platforms. It helps the company in establishing local area network and sharing all the
information remotely. It also helps in distributing control platform for large scale networks and
focus on the reliability and scalability.
1.2 Disaster recovery availability and security in context of NOS
Nowadays in any organization one of the major concern is to go through the best network
availability. Disaster recovery can be define as a area through which company can go through the
security planning of all of the negative events. All such negative events includes anything that
puts an organization's operations at risk such as hacking, cyber attacks etc. At the time of using
any NOS the major problem is faced by the IT director is some sudden damages such as
physical damages to equipment like computer, routers as well as information loss. While using
ONOS company can get secure and effective disc backups (Karsai and et.al, 2011). In order to
overcome with the problems of sudden damages IT manager need to adopt best backup plans so
that they can keep their data secure. Managing and controlling the internal and external interrupts
in the network system is define as a process of disaster recovery. Moreover, it can be stated that
5

security is the major concern that company should follow and for this purpose they need to adopt
various security controls in order to prevent unauthorized access. For this purpose, Cognizant has
developed a disaster recovery and business continuity plan.
1.3
There are different types of NOS available in the market. As per the given requirements
and considerations Cognizant has adopted ONOS. The operational need of company can be
fulfill by adopting this system. They can easily go through the proper network implementation
plan through which they can set up 30 and 40 computers on two different floors. This ONOS
provides them high features on low maintenance cost (LAWRENZ, 2013). There are different
service provider networks are available as WAN core backbone, Metro networks, Cellular access
networks, wired access etc. In the present scenario, the disaster recovery practices for current
NOS company can further use disaster recovery module. It can further managed by the database
cloud backups as well as services. It is essential to recognize all the threats and issues that
occurs. In order to prevent the damages a action plan should be developed. Security is the major
concern of any company as they need to keep their data secure and protect. With the help of
following several security issues company can manage all the damages and keep them secure.
The ON.Lab is a non profit organization founded by SDN investor which brings innovative ideas
from leading edge and deliver high quality service open source platforms. Due to the free
availability it is quite essential to keep full security. For this purpose Denial of services (DOS)
will be used when deserializing malformed packets in ONOS. When attackers try to exploit the
DOS flaw they only need to be able to send malicious crafted packets through the switched
controlled by ONOS. In addition to this, most of the SDN controller includes the host tracking as
well as allow host to migrate between different physical locations in the network.
TASK 2
2.1 Detail plan of implementation of ONOS
For the better implementation of the selected NOS it is quite essential for company to
fulfill all the requirements such as hardware, software requirements as well as best backup
methods and security policies that company should use.
6
various security controls in order to prevent unauthorized access. For this purpose, Cognizant has
developed a disaster recovery and business continuity plan.
1.3
There are different types of NOS available in the market. As per the given requirements
and considerations Cognizant has adopted ONOS. The operational need of company can be
fulfill by adopting this system. They can easily go through the proper network implementation
plan through which they can set up 30 and 40 computers on two different floors. This ONOS
provides them high features on low maintenance cost (LAWRENZ, 2013). There are different
service provider networks are available as WAN core backbone, Metro networks, Cellular access
networks, wired access etc. In the present scenario, the disaster recovery practices for current
NOS company can further use disaster recovery module. It can further managed by the database
cloud backups as well as services. It is essential to recognize all the threats and issues that
occurs. In order to prevent the damages a action plan should be developed. Security is the major
concern of any company as they need to keep their data secure and protect. With the help of
following several security issues company can manage all the damages and keep them secure.
The ON.Lab is a non profit organization founded by SDN investor which brings innovative ideas
from leading edge and deliver high quality service open source platforms. Due to the free
availability it is quite essential to keep full security. For this purpose Denial of services (DOS)
will be used when deserializing malformed packets in ONOS. When attackers try to exploit the
DOS flaw they only need to be able to send malicious crafted packets through the switched
controlled by ONOS. In addition to this, most of the SDN controller includes the host tracking as
well as allow host to migrate between different physical locations in the network.
TASK 2
2.1 Detail plan of implementation of ONOS
For the better implementation of the selected NOS it is quite essential for company to
fulfill all the requirements such as hardware, software requirements as well as best backup
methods and security policies that company should use.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In order to install ONOS network operating system network administrator need to download
SPRING-OPEN version of the ONOS controller source code. In order to run this on the Ubutnu
Linux environment.
sudo apt-get install openjdk-7-jdk openjdk-7-doc openjdk-7-jre-lib
git clone
Download the tar file
tar xzf zookeeper-3.4.6.tar.gz
Run the controller set up
cd ~/spring-open
./onos.sh setup
Compile the controller setup
mvn clean
mvn compile
Run the controller
./onos.sh start
Hardware requirements: ONOS can also be described as a network controller which control all
the data networks with the help of the adapter layers.
7
SPRING-OPEN version of the ONOS controller source code. In order to run this on the Ubutnu
Linux environment.
sudo apt-get install openjdk-7-jdk openjdk-7-doc openjdk-7-jre-lib
git clone
Download the tar file
tar xzf zookeeper-3.4.6.tar.gz
Run the controller set up
cd ~/spring-open
./onos.sh setup
Compile the controller setup
mvn clean
mvn compile
Run the controller
./onos.sh start
Hardware requirements: ONOS can also be described as a network controller which control all
the data networks with the help of the adapter layers.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Dual Intel Xeon E5-2670v2 2.5GHz Processors - 10 real cores/20 hyper-threaded cores
per processor;
32GB 1600MHz DDR3 DRAM;
1Gbps Network interface card;
Ubuntu 14.04 OS;
Time synchronization among cluster nodes using ptpd.
Routers Switches (At the time of development of connection)
Software requirement
Java HotSpot(TM) 64-Bit Server VM; version 1.8.0_31
JAVA_OPTS="${JAVA_OPTS:--Xms8G -Xmx8G}"
onos-1.1.0 snapshot: commit a31e13471ee626abce2bc43c413fab17586f4fc3
Additional case-specific ONOS parameters
At the time of configuring ONOS network administrator should behave in a conservative
manner. They need to propose two features that could be applied to ONOS i.e.:
Application authentication
Permission based accessed control
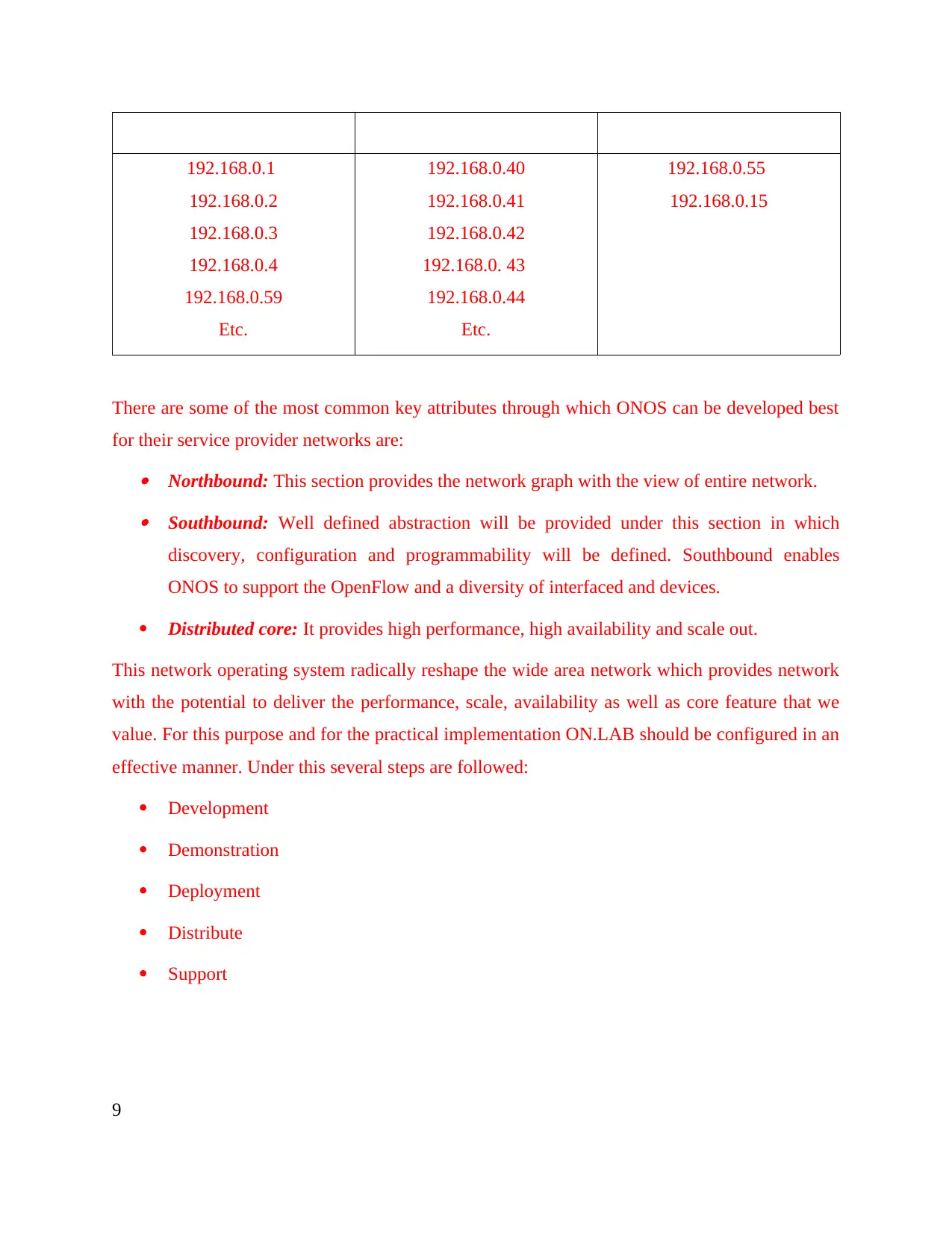
c) It is essential to have a proper IP address allocation for all the computers and servers as well
as network printers in order to keep full security. For this purpose there are primary, secondary
as well as virtual IP address configuration is done by the analyst.
Primary IP address creates a mapping between the attached networks and the physical
interfaces on a system.
For 1st floor computers For 2nd floor computers For network printers
8
per processor;
32GB 1600MHz DDR3 DRAM;
1Gbps Network interface card;
Ubuntu 14.04 OS;
Time synchronization among cluster nodes using ptpd.
Routers Switches (At the time of development of connection)
Software requirement
Java HotSpot(TM) 64-Bit Server VM; version 1.8.0_31
JAVA_OPTS="${JAVA_OPTS:--Xms8G -Xmx8G}"
onos-1.1.0 snapshot: commit a31e13471ee626abce2bc43c413fab17586f4fc3
Additional case-specific ONOS parameters
At the time of configuring ONOS network administrator should behave in a conservative
manner. They need to propose two features that could be applied to ONOS i.e.:
Application authentication
Permission based accessed control
c) It is essential to have a proper IP address allocation for all the computers and servers as well
as network printers in order to keep full security. For this purpose there are primary, secondary
as well as virtual IP address configuration is done by the analyst.
Primary IP address creates a mapping between the attached networks and the physical
interfaces on a system.
For 1st floor computers For 2nd floor computers For network printers
8
192.168.0.1
192.168.0.2
192.168.0.3
192.168.0.4
192.168.0.59
Etc.
192.168.0.40
192.168.0.41
192.168.0.42
192.168.0. 43
192.168.0.44
Etc.
192.168.0.55
192.168.0.15
There are some of the most common key attributes through which ONOS can be developed best
for their service provider networks are: Northbound: This section provides the network graph with the view of entire network. Southbound: Well defined abstraction will be provided under this section in which
discovery, configuration and programmability will be defined. Southbound enables
ONOS to support the OpenFlow and a diversity of interfaced and devices.
Distributed core: It provides high performance, high availability and scale out.
This network operating system radically reshape the wide area network which provides network
with the potential to deliver the performance, scale, availability as well as core feature that we
value. For this purpose and for the practical implementation ON.LAB should be configured in an
effective manner. Under this several steps are followed:
Development
Demonstration
Deployment
Distribute
Support
9
192.168.0.2
192.168.0.3
192.168.0.4
192.168.0.59
Etc.
192.168.0.40
192.168.0.41
192.168.0.42
192.168.0. 43
192.168.0.44
Etc.
192.168.0.55
192.168.0.15
There are some of the most common key attributes through which ONOS can be developed best
for their service provider networks are: Northbound: This section provides the network graph with the view of entire network. Southbound: Well defined abstraction will be provided under this section in which
discovery, configuration and programmability will be defined. Southbound enables
ONOS to support the OpenFlow and a diversity of interfaced and devices.
Distributed core: It provides high performance, high availability and scale out.
This network operating system radically reshape the wide area network which provides network
with the potential to deliver the performance, scale, availability as well as core feature that we
value. For this purpose and for the practical implementation ON.LAB should be configured in an
effective manner. Under this several steps are followed:
Development
Demonstration
Deployment
Distribute
Support
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

d) Security policy is the set of requirements which are required to set a path to a specific
objectives. There are various security policies followed by company while implementing the
NOS such as: Password management: System analyst needs to go through the proper password
management while using ONOS (Open network operating system) so that no one can
hack the passwords easily. For the better password management some points should be
followed by IT manager such as: Identification, authentication, multi-factor
authentication, strong authentication. At the time of log-in user needs to provide his
identity so anybody else cannot use it. Cognizant can easily keep all their customers and
employee's data secure by providing them unique passwords (Hennessy, 2013).
Patch management: It is the best strategy adopted by Cognizant through which they can
decide what patches should be applied on what applications. Successful patch
management policies can help with security audits and compliance audits.
Further, the planning needs to be implemented for file server management. After
adopting this network operating system there are various services provided by server such as
chatting and e-mail server. After implementing this NOS company can access all the data
remotely and easily communicate with each other on different floors. There are various other
services provided that file sharing, modification in database as well as uploading the content in
information system.
2.2 Plan and evolution of disaster recovery plan for ONOS
The disaster may be occur in the company due to external and internal factors and it
directly impact on the networking system of the company. The plan should be in such type which
run the company after human intervention or natural disasters. The following the plan helps the
company to make a plan for recovery (Peterson, 2011).
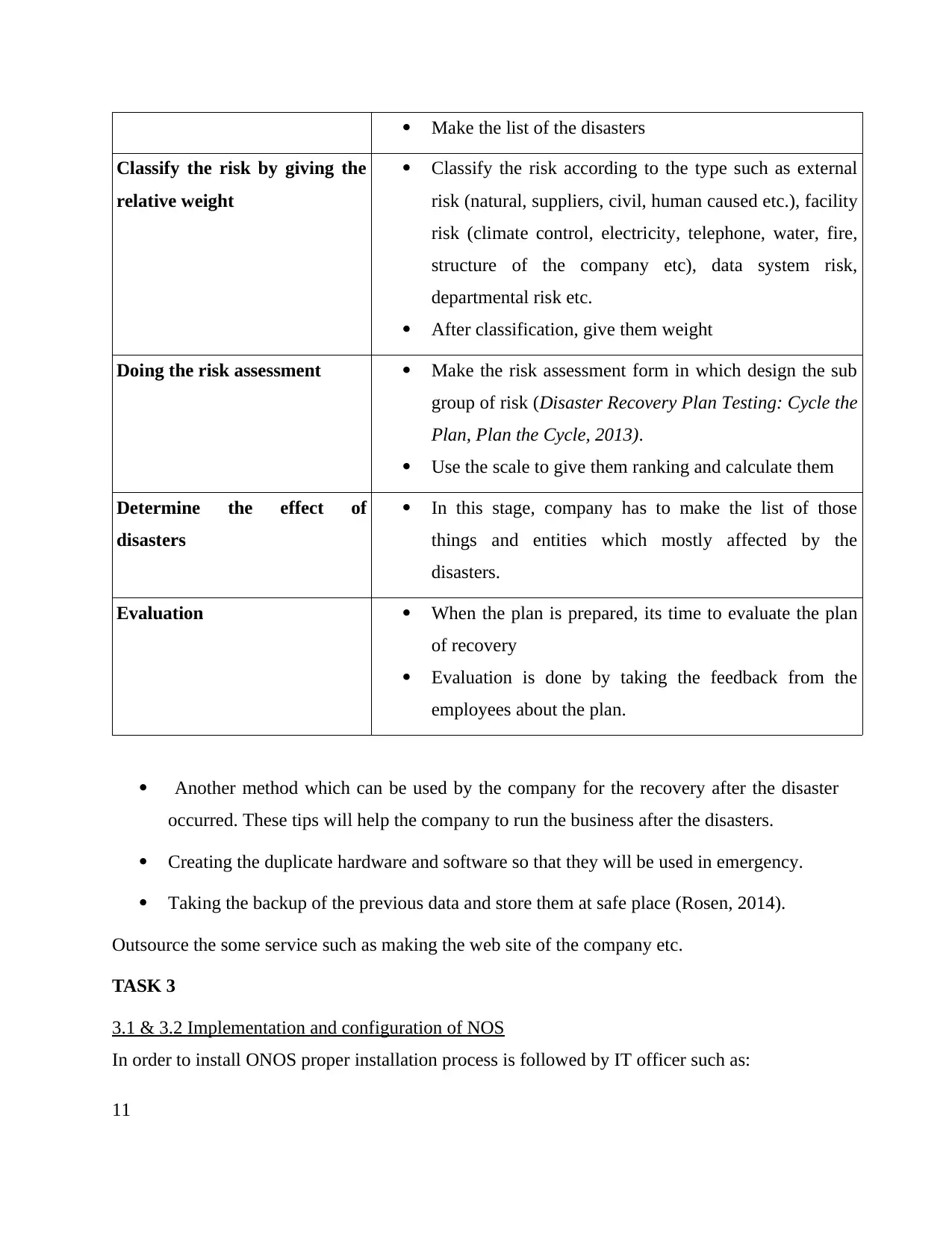
Stages Explanation
Identification and analysis of
disasters
Identify the risk or treats of disasters
Analyse the disasters
10
objectives. There are various security policies followed by company while implementing the
NOS such as: Password management: System analyst needs to go through the proper password
management while using ONOS (Open network operating system) so that no one can
hack the passwords easily. For the better password management some points should be
followed by IT manager such as: Identification, authentication, multi-factor
authentication, strong authentication. At the time of log-in user needs to provide his
identity so anybody else cannot use it. Cognizant can easily keep all their customers and
employee's data secure by providing them unique passwords (Hennessy, 2013).
Patch management: It is the best strategy adopted by Cognizant through which they can
decide what patches should be applied on what applications. Successful patch
management policies can help with security audits and compliance audits.
Further, the planning needs to be implemented for file server management. After
adopting this network operating system there are various services provided by server such as
chatting and e-mail server. After implementing this NOS company can access all the data
remotely and easily communicate with each other on different floors. There are various other
services provided that file sharing, modification in database as well as uploading the content in
information system.
2.2 Plan and evolution of disaster recovery plan for ONOS
The disaster may be occur in the company due to external and internal factors and it
directly impact on the networking system of the company. The plan should be in such type which
run the company after human intervention or natural disasters. The following the plan helps the
company to make a plan for recovery (Peterson, 2011).
Stages Explanation
Identification and analysis of
disasters
Identify the risk or treats of disasters
Analyse the disasters
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Make the list of the disasters
Classify the risk by giving the
relative weight
Classify the risk according to the type such as external
risk (natural, suppliers, civil, human caused etc.), facility
risk (climate control, electricity, telephone, water, fire,
structure of the company etc), data system risk,
departmental risk etc.
After classification, give them weight
Doing the risk assessment Make the risk assessment form in which design the sub
group of risk (Disaster Recovery Plan Testing: Cycle the
Plan, Plan the Cycle, 2013).
Use the scale to give them ranking and calculate them
Determine the effect of
disasters
In this stage, company has to make the list of those
things and entities which mostly affected by the
disasters.
Evaluation When the plan is prepared, its time to evaluate the plan
of recovery
Evaluation is done by taking the feedback from the
employees about the plan.
Another method which can be used by the company for the recovery after the disaster
occurred. These tips will help the company to run the business after the disasters.
Creating the duplicate hardware and software so that they will be used in emergency.
Taking the backup of the previous data and store them at safe place (Rosen, 2014).
Outsource the some service such as making the web site of the company etc.
TASK 3
3.1 & 3.2 Implementation and configuration of NOS
In order to install ONOS proper installation process is followed by IT officer such as:
11
Classify the risk by giving the
relative weight
Classify the risk according to the type such as external
risk (natural, suppliers, civil, human caused etc.), facility
risk (climate control, electricity, telephone, water, fire,
structure of the company etc), data system risk,
departmental risk etc.
After classification, give them weight
Doing the risk assessment Make the risk assessment form in which design the sub
group of risk (Disaster Recovery Plan Testing: Cycle the
Plan, Plan the Cycle, 2013).
Use the scale to give them ranking and calculate them
Determine the effect of
disasters
In this stage, company has to make the list of those
things and entities which mostly affected by the
disasters.
Evaluation When the plan is prepared, its time to evaluate the plan
of recovery
Evaluation is done by taking the feedback from the
employees about the plan.
Another method which can be used by the company for the recovery after the disaster
occurred. These tips will help the company to run the business after the disasters.
Creating the duplicate hardware and software so that they will be used in emergency.
Taking the backup of the previous data and store them at safe place (Rosen, 2014).
Outsource the some service such as making the web site of the company etc.
TASK 3
3.1 & 3.2 Implementation and configuration of NOS
In order to install ONOS proper installation process is followed by IT officer such as:
11

1. Driver Installation: All the hardware and software requirements should be fulfilled such as:
Hardware Requirements
Dual Intel Xeon E5-2670v2 2.5GHz Processors - 10 real cores/20 hyper-threaded cores
per processor;
32GB 1600MHz DDR3 DRAM;
1Gbps Network interface card;
Ubuntu 14.04 OS; Time synchronization among cluster nodes using ptpd.
Software requirement
Java HotSpot(TM) 64-Bit Server VM; version 1.8.0_31
JAVA_OPTS="${JAVA_OPTS:--Xms8G -Xmx8G}"
onos-1.1.0 snapshot: commit a31e13471ee626abce2bc43c413fab17586f4fc3
Additional case-specific ONOS parameters
2. Pre-Installation Requirement: Some of the pre-installation requirement are as follows: some
supporting files are required such as:
Installation of Java, Maven and Karaf
Ubuntu Server 14.04 LTS 64-bit
2GB or more RAM
2 or more processors
Java 8 JDK (Oracle Java recommended; OpenJDK is not as thoroughly tested)
Apache Maven 3.3.1
git
bash (for packaging & testing)
Apache Karaf 3.0.3
12
Hardware Requirements
Dual Intel Xeon E5-2670v2 2.5GHz Processors - 10 real cores/20 hyper-threaded cores
per processor;
32GB 1600MHz DDR3 DRAM;
1Gbps Network interface card;
Ubuntu 14.04 OS; Time synchronization among cluster nodes using ptpd.
Software requirement
Java HotSpot(TM) 64-Bit Server VM; version 1.8.0_31
JAVA_OPTS="${JAVA_OPTS:--Xms8G -Xmx8G}"
onos-1.1.0 snapshot: commit a31e13471ee626abce2bc43c413fab17586f4fc3
Additional case-specific ONOS parameters
2. Pre-Installation Requirement: Some of the pre-installation requirement are as follows: some
supporting files are required such as:
Installation of Java, Maven and Karaf
Ubuntu Server 14.04 LTS 64-bit
2GB or more RAM
2 or more processors
Java 8 JDK (Oracle Java recommended; OpenJDK is not as thoroughly tested)
Apache Maven 3.3.1
git
bash (for packaging & testing)
Apache Karaf 3.0.3
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




