A Detailed Report on Generating Digital Certificates Using OpenSSL
VerifiedAdded on 2024/06/04
|20
|4422
|319
Report
AI Summary
This report provides a comprehensive overview of generating digital certificates using OpenSSL. It begins by explaining the fundamentals of digital certificates, including their basis in asymmetric cryptography and the standard X.509 format. The report details the process of generating and validating digital certificates, highlighting the importance of certification authorities and the steps involved in ensuring trustworthiness. It then delves into OpenSSL, describing its architecture, its role in implementing SSL/TLS protocols, and its applications in securing communications. The report further explains how to use OpenSSL to create a personal certification authority for signing digital certificates used for internal organizational communications. The report concludes by emphasizing the importance of secure website configuration using SSL and HTTPS protocols. The document is available on Desklib, a platform offering a wide array of study resources for students.

Assignment 3
Using OpenSSL to generate Digital Certificates
1
Using OpenSSL to generate Digital Certificates
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Executive Summary.....................................................................................................................................3
Introduction.................................................................................................................................................4
Basis of Digital Certificate............................................................................................................................5
Use of Asymmetric Cryptography............................................................................................................5
Digital Certificate Format.........................................................................................................................7
Generation of Digital Certificate..............................................................................................................8
Validation of Digital Certificate................................................................................................................9
OpenSSL Fundamentals.............................................................................................................................10
OpenSSL Architecture............................................................................................................................10
SSL and TLS protocols in OpenSSL.........................................................................................................11
OpenSSL applications for implementing SSL/TLS...................................................................................13
Generation of Digital Certificates..............................................................................................................14
Conclusion.................................................................................................................................................16
References.................................................................................................................................................17
Table of Figures
Figure 1 Public key and Private Key Concept...............................................................................................6
Figure 2 Digital certificate Format...............................................................................................................7
Figure 3 Generation of Digital Certificate....................................................................................................8
Figure 4 OpenSSL Architecture..................................................................................................................10
Figure 5 SSL and TLS protocol layer in OpenSSL........................................................................................11
2
Executive Summary.....................................................................................................................................3
Introduction.................................................................................................................................................4
Basis of Digital Certificate............................................................................................................................5
Use of Asymmetric Cryptography............................................................................................................5
Digital Certificate Format.........................................................................................................................7
Generation of Digital Certificate..............................................................................................................8
Validation of Digital Certificate................................................................................................................9
OpenSSL Fundamentals.............................................................................................................................10
OpenSSL Architecture............................................................................................................................10
SSL and TLS protocols in OpenSSL.........................................................................................................11
OpenSSL applications for implementing SSL/TLS...................................................................................13
Generation of Digital Certificates..............................................................................................................14
Conclusion.................................................................................................................................................16
References.................................................................................................................................................17
Table of Figures
Figure 1 Public key and Private Key Concept...............................................................................................6
Figure 2 Digital certificate Format...............................................................................................................7
Figure 3 Generation of Digital Certificate....................................................................................................8
Figure 4 OpenSSL Architecture..................................................................................................................10
Figure 5 SSL and TLS protocol layer in OpenSSL........................................................................................11
2

Executive Summary
Digital Certificates have become an important part of Internet Security. Digital certificates have
provided the authentication for private key in networking entities. It is an electronic document that
has been used to verify that a user has been assigned a public key and a corresponding private key
which he can use for transmitting data under his name. This digital certificate is being signed by a
Certification Authority. This paper deals with the creation of digital certificates and how these
certificates are issued and what all it contains.
This paper also deals with the problems associated with the management of certificates and a
different approach has been adopted in this to create digital certificates by using a command line
script. OpenSSL tool has been used for building a governmental certification authority that can be
used to sign digital certificates that can be used by an individual for internal communications inside
an organization. It has also discussed the challenges faced in adopting this new approach and
writing scripts as per command line scripting language for the creation of X 509 certificates.
The process and methodologies involved in the process of creation of an individual’s very own
certification authority and digital certificates have been reviewed in this paper. The need to create
own certificates using OpenSSL tool has also been reviewed and its necessity been discussed and
understood, the solution has been adopted and new solutions and approaches are also been
discovered to get the better results. Configuring a website with SSL layer also allows it to work more
securely over the internet and can adopt the protocol HTTPS over HTTP (Cross, 2015).
3
Digital Certificates have become an important part of Internet Security. Digital certificates have
provided the authentication for private key in networking entities. It is an electronic document that
has been used to verify that a user has been assigned a public key and a corresponding private key
which he can use for transmitting data under his name. This digital certificate is being signed by a
Certification Authority. This paper deals with the creation of digital certificates and how these
certificates are issued and what all it contains.
This paper also deals with the problems associated with the management of certificates and a
different approach has been adopted in this to create digital certificates by using a command line
script. OpenSSL tool has been used for building a governmental certification authority that can be
used to sign digital certificates that can be used by an individual for internal communications inside
an organization. It has also discussed the challenges faced in adopting this new approach and
writing scripts as per command line scripting language for the creation of X 509 certificates.
The process and methodologies involved in the process of creation of an individual’s very own
certification authority and digital certificates have been reviewed in this paper. The need to create
own certificates using OpenSSL tool has also been reviewed and its necessity been discussed and
understood, the solution has been adopted and new solutions and approaches are also been
discovered to get the better results. Configuring a website with SSL layer also allows it to work more
securely over the internet and can adopt the protocol HTTPS over HTTP (Cross, 2015).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The increasing number of people and businesses over the internet has made access faster and
cheaper which makes people communicate more over the internet to provide a bigger and better
platform for their businesses to grow and get a new boost in its economy. The Internet has always
been an open platform for communication without any security protocols which criminals thought as
a great opportunity to exploit this era changing technology to get fraudulent gains. Only after this
increasing rate of crimes, it became a necessity to include security protocols so that communication
over the Internet becomes secure and resistant to the threats and security attacks that were
booming by the criminals. Public Key Infrastructure (PKI) is one of the architectures by which all
security properties can be achieved within a communication. A digital certificate is a means to use all
the applications of PKI. OpenSSL and Digital certificate concept has also been discussed here along
with the results of some research papers. OpenSSL helps in creating our own Digital certificate
signed by own certification authority.
4
The increasing number of people and businesses over the internet has made access faster and
cheaper which makes people communicate more over the internet to provide a bigger and better
platform for their businesses to grow and get a new boost in its economy. The Internet has always
been an open platform for communication without any security protocols which criminals thought as
a great opportunity to exploit this era changing technology to get fraudulent gains. Only after this
increasing rate of crimes, it became a necessity to include security protocols so that communication
over the Internet becomes secure and resistant to the threats and security attacks that were
booming by the criminals. Public Key Infrastructure (PKI) is one of the architectures by which all
security properties can be achieved within a communication. A digital certificate is a means to use all
the applications of PKI. OpenSSL and Digital certificate concept has also been discussed here along
with the results of some research papers. OpenSSL helps in creating our own Digital certificate
signed by own certification authority.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Basics of Digital Certificate
A digital certificate is a way to get the knowledge of which key has been assigned to a user for their
involvement in the communication process and transmission of data over the network to other
parties. The receiving party can get to know the sender of the message by using the attached digital
certificate along with the message. Both the sender and receiver is required to attach their
certificates along with the messages to authenticate themselves so that no unauthorized user can
use the false identity of a person while sending any illegal or questionable messages over the
internet (Cross, 2015).
Use of Asymmetric Cryptography
In the creation of digital certificates, asymmetric cryptography has been used where a sender
encrypts the data or message with his public key and sends the encrypted message to the receiver
and he decrypts the data with the help of his own private key. Here in this scenario, the keys used
for both encryption and decryption are different and hence it makes asymmetric cryptography. This
situation can also be viewed as the sender signed or sealed the confidential message with his digital
authentication proof or digital signature by attaching his digital certificate to it.
The concept of Public and Private Key
There are two types of keys that are used in the process of encryption and decryption. A person
owns both public and private key if he is involved in any sort of communication. The public key of
the owner is known to every person involved in the communication processor it can be said that it is
open to everyone. This key is used for encrypting a data and never used for decrypting any type of
data as every person has the access to the public key. The private key owned by a person is known
to only that person and no other person has access to it. In other terms, it is a secret key that is used
for decryption of a data such that only the person that owns the particular private key can decrypt a
data and get access to it. Digital certificates have been issued to a user with the mention of their
public key in it so that it can be used as a proof that they are the authorized owner of a particular
public key and no other person use it without presenting a properly authorized digital certificate
(Cross, 2015).
5
A digital certificate is a way to get the knowledge of which key has been assigned to a user for their
involvement in the communication process and transmission of data over the network to other
parties. The receiving party can get to know the sender of the message by using the attached digital
certificate along with the message. Both the sender and receiver is required to attach their
certificates along with the messages to authenticate themselves so that no unauthorized user can
use the false identity of a person while sending any illegal or questionable messages over the
internet (Cross, 2015).
Use of Asymmetric Cryptography
In the creation of digital certificates, asymmetric cryptography has been used where a sender
encrypts the data or message with his public key and sends the encrypted message to the receiver
and he decrypts the data with the help of his own private key. Here in this scenario, the keys used
for both encryption and decryption are different and hence it makes asymmetric cryptography. This
situation can also be viewed as the sender signed or sealed the confidential message with his digital
authentication proof or digital signature by attaching his digital certificate to it.
The concept of Public and Private Key
There are two types of keys that are used in the process of encryption and decryption. A person
owns both public and private key if he is involved in any sort of communication. The public key of
the owner is known to every person involved in the communication processor it can be said that it is
open to everyone. This key is used for encrypting a data and never used for decrypting any type of
data as every person has the access to the public key. The private key owned by a person is known
to only that person and no other person has access to it. In other terms, it is a secret key that is used
for decryption of a data such that only the person that owns the particular private key can decrypt a
data and get access to it. Digital certificates have been issued to a user with the mention of their
public key in it so that it can be used as a proof that they are the authorized owner of a particular
public key and no other person use it without presenting a properly authorized digital certificate
(Cross, 2015).
5
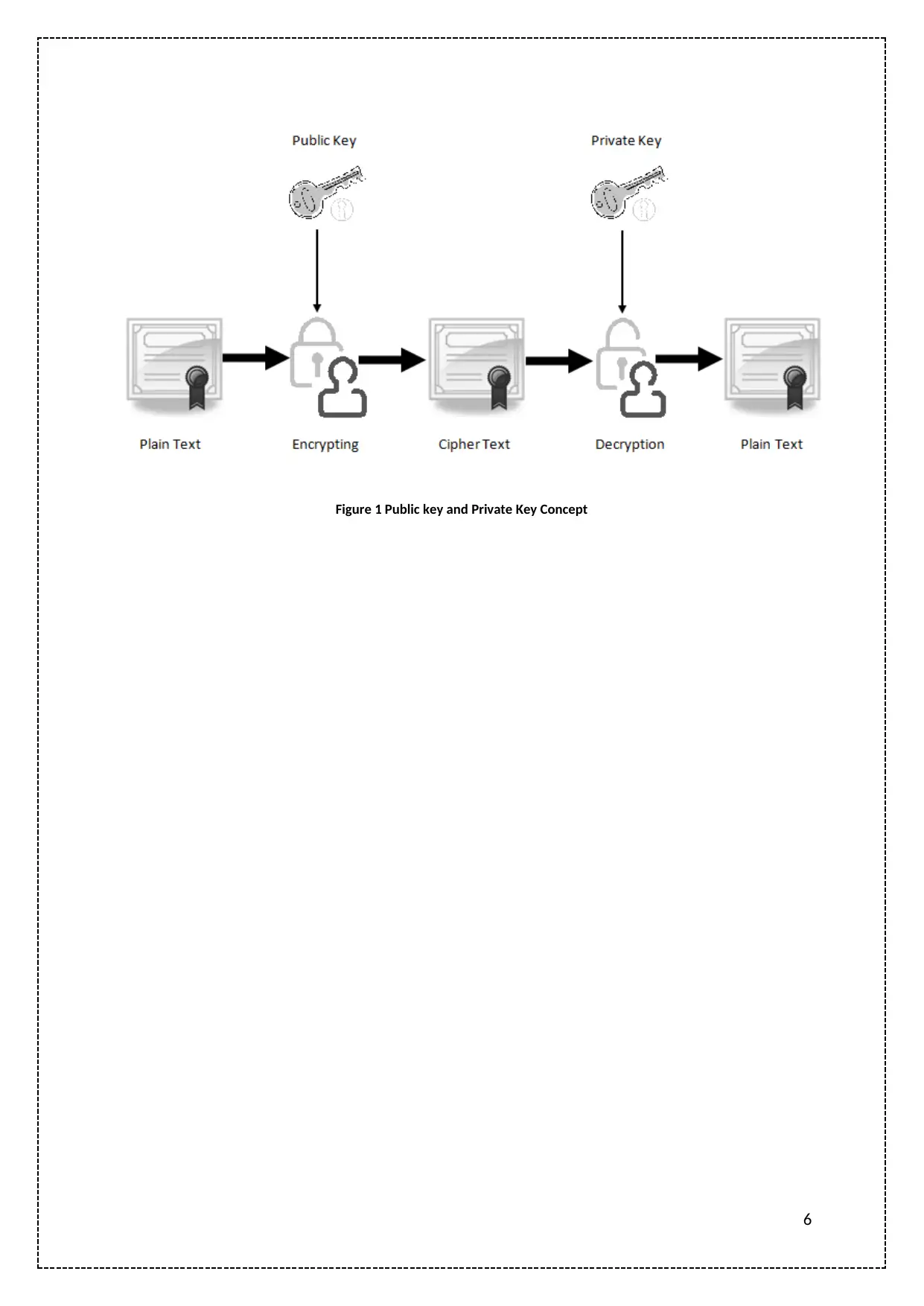
Figure 1 Public key and Private Key Concept
6
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
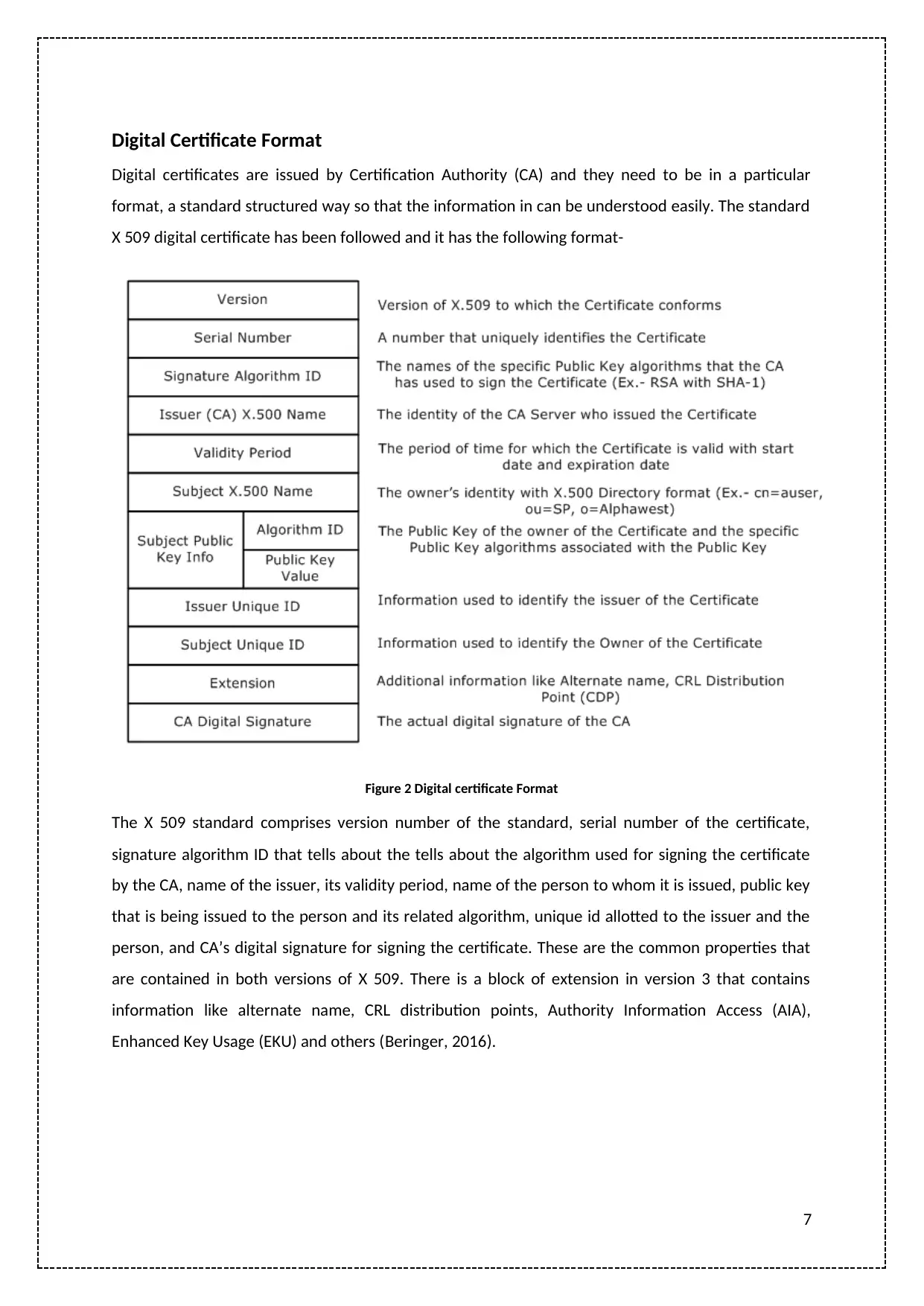
Digital Certificate Format
Digital certificates are issued by Certification Authority (CA) and they need to be in a particular
format, a standard structured way so that the information in can be understood easily. The standard
X 509 digital certificate has been followed and it has the following format-
Figure 2 Digital certificate Format
The X 509 standard comprises version number of the standard, serial number of the certificate,
signature algorithm ID that tells about the tells about the algorithm used for signing the certificate
by the CA, name of the issuer, its validity period, name of the person to whom it is issued, public key
that is being issued to the person and its related algorithm, unique id allotted to the issuer and the
person, and CA’s digital signature for signing the certificate. These are the common properties that
are contained in both versions of X 509. There is a block of extension in version 3 that contains
information like alternate name, CRL distribution points, Authority Information Access (AIA),
Enhanced Key Usage (EKU) and others (Beringer, 2016).
7
Digital certificates are issued by Certification Authority (CA) and they need to be in a particular
format, a standard structured way so that the information in can be understood easily. The standard
X 509 digital certificate has been followed and it has the following format-
Figure 2 Digital certificate Format
The X 509 standard comprises version number of the standard, serial number of the certificate,
signature algorithm ID that tells about the tells about the algorithm used for signing the certificate
by the CA, name of the issuer, its validity period, name of the person to whom it is issued, public key
that is being issued to the person and its related algorithm, unique id allotted to the issuer and the
person, and CA’s digital signature for signing the certificate. These are the common properties that
are contained in both versions of X 509. There is a block of extension in version 3 that contains
information like alternate name, CRL distribution points, Authority Information Access (AIA),
Enhanced Key Usage (EKU) and others (Beringer, 2016).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Generation of Digital Certificate
There are a set of steps that need to be followed to request and get digital certificates. Firstly a
person needs to request for the generation of a pair of public and private key from an authorized
company. Then the person needs to gather and submit all the required documents and information
for his identification like fingerprints, email address, etc. Then he can request for issuing of a
certificate for his pair of keys, for which all of his documents are verified and validated and then
after confirmation the certification authority signs the digital certificate and issue it to the person
(Zhu, 2016).
Figure 3 Generation of Digital Certificate
8
There are a set of steps that need to be followed to request and get digital certificates. Firstly a
person needs to request for the generation of a pair of public and private key from an authorized
company. Then the person needs to gather and submit all the required documents and information
for his identification like fingerprints, email address, etc. Then he can request for issuing of a
certificate for his pair of keys, for which all of his documents are verified and validated and then
after confirmation the certification authority signs the digital certificate and issue it to the person
(Zhu, 2016).
Figure 3 Generation of Digital Certificate
8

Validation of Digital Certificate
After acquiring the certificate, Windows perform a set of steps for validating the trustworthiness of
the certificate before it can be used in further communication. For this, firstly the origin of certificate
issuing is obtained and the verification of CAs is done. Then the validation of issuer’s certificate and
the digital signature is verified. After the chain building process that is done to check the authenticity
of the certificate, revocation process is done to check no certificate is revoked. This validation
process ensures that the certificates are fully tested and can be trusted. It authenticates the user at
both sending and receiving point to ensure the integrity of the messages. And any irregularity in the
creation of digital certificate can prove to be very dangerous and can create troubles in the
communication network. Hence it is important that each and every digital certificate is verified
before release with all steps to ensure complete surety in securing system (Zhu, 2016).
9
After acquiring the certificate, Windows perform a set of steps for validating the trustworthiness of
the certificate before it can be used in further communication. For this, firstly the origin of certificate
issuing is obtained and the verification of CAs is done. Then the validation of issuer’s certificate and
the digital signature is verified. After the chain building process that is done to check the authenticity
of the certificate, revocation process is done to check no certificate is revoked. This validation
process ensures that the certificates are fully tested and can be trusted. It authenticates the user at
both sending and receiving point to ensure the integrity of the messages. And any irregularity in the
creation of digital certificate can prove to be very dangerous and can create troubles in the
communication network. Hence it is important that each and every digital certificate is verified
before release with all steps to ensure complete surety in securing system (Zhu, 2016).
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

OpenSSL Fundamentals
OpenSSL is a command line scripting tool that has been used to simplify the tasks of Public key
Infrastructure (PKI) and HTTPS or SSL layer over HTTP. It is a software application library that is used
for securing communication and provide authentication of the person present at the receiving end.
It is widely used in web server to provide security to a large number of websites. OpenSSL has been
used to create an individual’s own digital certificate inside an organization and to acquire more
security while browsing a website by using HTTPS protocol. It has been provided with a number of
encryption algorithms and ciphers to protect the network and data. OpenSSL has been provided with
a pre-built form but a newer version can also be created by rebuilding the open source code and
making slight changes in it. It is a software application library that is used for securing
communication and provide authentication of the person present at the receiving end. It is widely
used in web server to provide security to a large number of websites (Wong, 2015).
OpenSSL Architecture
OpenSSL is a kit providing cryptographic tools that are used for free implementation of security
protocol layers such as Secure Socket Layer (SSL) and Transport Layer Security (TLS). It is also used in
implementing tasks for PKI cryptographic commands. The OpenSSL tool includes configuration file
and command lines along with the predefined source code, header files, and executable libraries.
Apart from creating digital certificates, it has also been used in creating a message digest, SSL and
TLS testing programs, RSA key parameters, and ciphers for encrypting and decryption processes. It
contains an EVP interface that changes the ciphers for different algorithms without changing the
source code. The architecture of OpenSSL has been described below (Beringer, 2016).
10
OpenSSL is a command line scripting tool that has been used to simplify the tasks of Public key
Infrastructure (PKI) and HTTPS or SSL layer over HTTP. It is a software application library that is used
for securing communication and provide authentication of the person present at the receiving end.
It is widely used in web server to provide security to a large number of websites. OpenSSL has been
used to create an individual’s own digital certificate inside an organization and to acquire more
security while browsing a website by using HTTPS protocol. It has been provided with a number of
encryption algorithms and ciphers to protect the network and data. OpenSSL has been provided with
a pre-built form but a newer version can also be created by rebuilding the open source code and
making slight changes in it. It is a software application library that is used for securing
communication and provide authentication of the person present at the receiving end. It is widely
used in web server to provide security to a large number of websites (Wong, 2015).
OpenSSL Architecture
OpenSSL is a kit providing cryptographic tools that are used for free implementation of security
protocol layers such as Secure Socket Layer (SSL) and Transport Layer Security (TLS). It is also used in
implementing tasks for PKI cryptographic commands. The OpenSSL tool includes configuration file
and command lines along with the predefined source code, header files, and executable libraries.
Apart from creating digital certificates, it has also been used in creating a message digest, SSL and
TLS testing programs, RSA key parameters, and ciphers for encrypting and decryption processes. It
contains an EVP interface that changes the ciphers for different algorithms without changing the
source code. The architecture of OpenSSL has been described below (Beringer, 2016).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
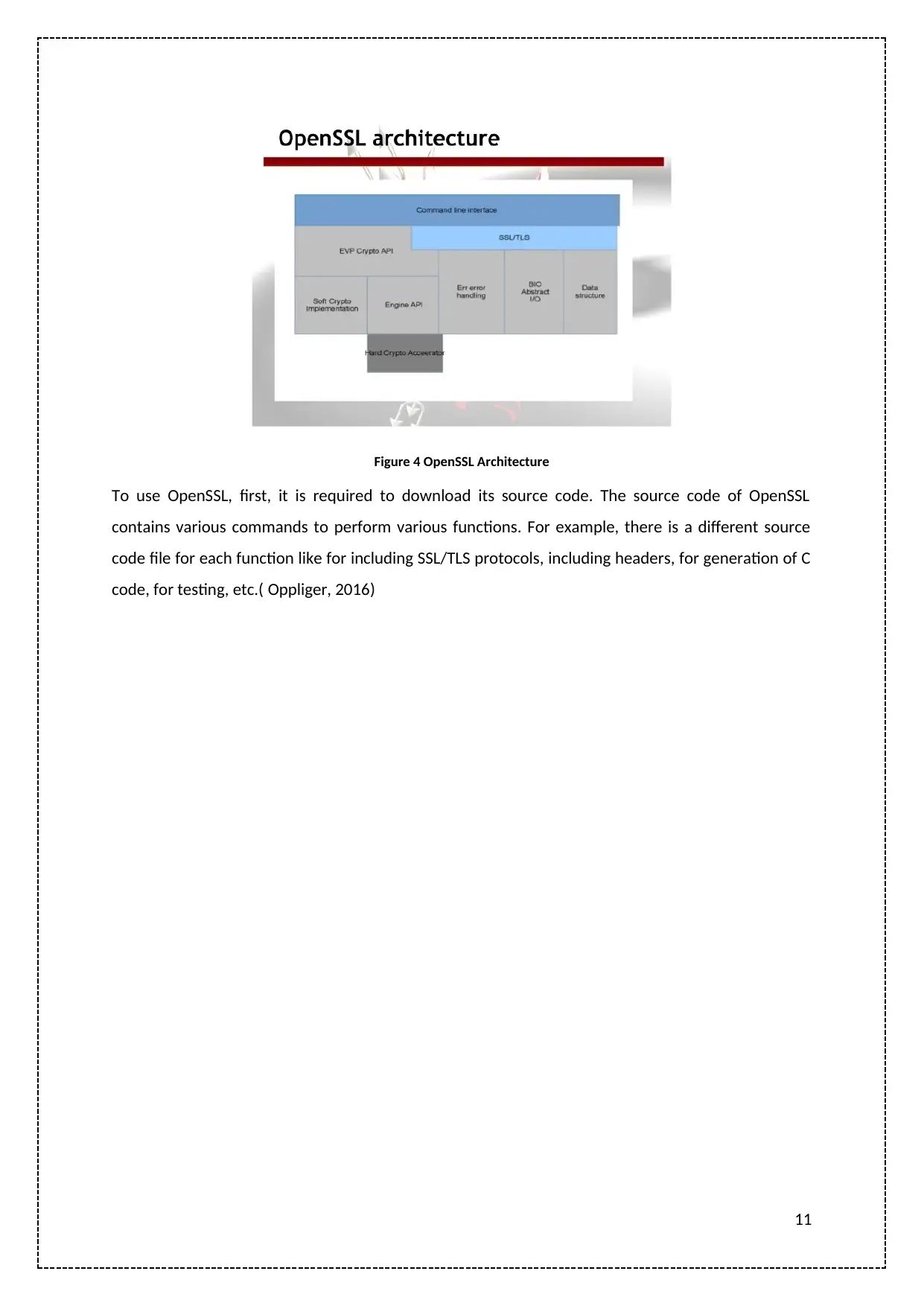
Figure 4 OpenSSL Architecture
To use OpenSSL, first, it is required to download its source code. The source code of OpenSSL
contains various commands to perform various functions. For example, there is a different source
code file for each function like for including SSL/TLS protocols, including headers, for generation of C
code, for testing, etc.( Oppliger, 2016)
11
To use OpenSSL, first, it is required to download its source code. The source code of OpenSSL
contains various commands to perform various functions. For example, there is a different source
code file for each function like for including SSL/TLS protocols, including headers, for generation of C
code, for testing, etc.( Oppliger, 2016)
11
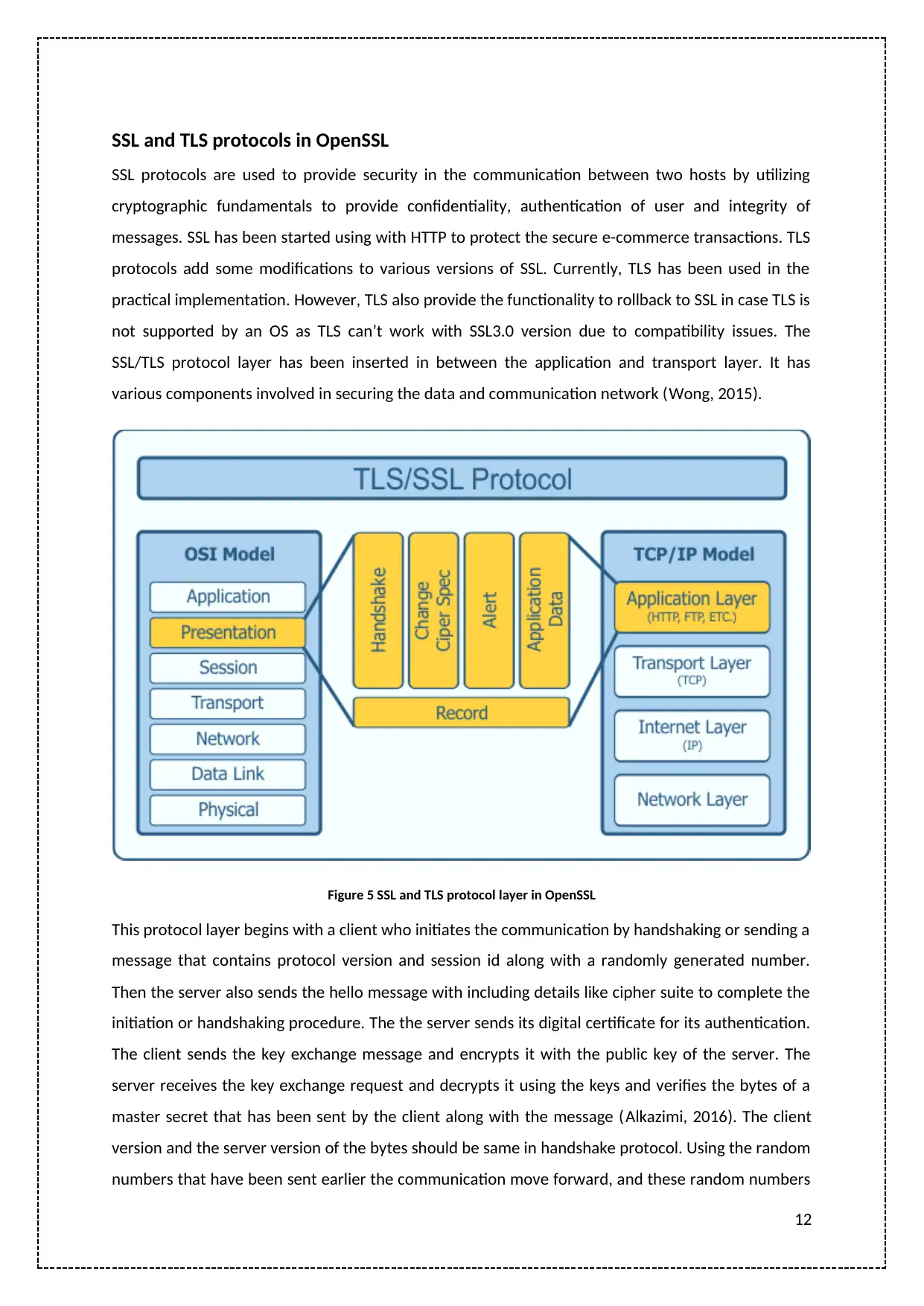
SSL and TLS protocols in OpenSSL
SSL protocols are used to provide security in the communication between two hosts by utilizing
cryptographic fundamentals to provide confidentiality, authentication of user and integrity of
messages. SSL has been started using with HTTP to protect the secure e-commerce transactions. TLS
protocols add some modifications to various versions of SSL. Currently, TLS has been used in the
practical implementation. However, TLS also provide the functionality to rollback to SSL in case TLS is
not supported by an OS as TLS can’t work with SSL3.0 version due to compatibility issues. The
SSL/TLS protocol layer has been inserted in between the application and transport layer. It has
various components involved in securing the data and communication network (Wong, 2015).
Figure 5 SSL and TLS protocol layer in OpenSSL
This protocol layer begins with a client who initiates the communication by handshaking or sending a
message that contains protocol version and session id along with a randomly generated number.
Then the server also sends the hello message with including details like cipher suite to complete the
initiation or handshaking procedure. The the server sends its digital certificate for its authentication.
The client sends the key exchange message and encrypts it with the public key of the server. The
server receives the key exchange request and decrypts it using the keys and verifies the bytes of a
master secret that has been sent by the client along with the message (Alkazimi, 2016). The client
version and the server version of the bytes should be same in handshake protocol. Using the random
numbers that have been sent earlier the communication move forward, and these random numbers
12
SSL protocols are used to provide security in the communication between two hosts by utilizing
cryptographic fundamentals to provide confidentiality, authentication of user and integrity of
messages. SSL has been started using with HTTP to protect the secure e-commerce transactions. TLS
protocols add some modifications to various versions of SSL. Currently, TLS has been used in the
practical implementation. However, TLS also provide the functionality to rollback to SSL in case TLS is
not supported by an OS as TLS can’t work with SSL3.0 version due to compatibility issues. The
SSL/TLS protocol layer has been inserted in between the application and transport layer. It has
various components involved in securing the data and communication network (Wong, 2015).
Figure 5 SSL and TLS protocol layer in OpenSSL
This protocol layer begins with a client who initiates the communication by handshaking or sending a
message that contains protocol version and session id along with a randomly generated number.
Then the server also sends the hello message with including details like cipher suite to complete the
initiation or handshaking procedure. The the server sends its digital certificate for its authentication.
The client sends the key exchange message and encrypts it with the public key of the server. The
server receives the key exchange request and decrypts it using the keys and verifies the bytes of a
master secret that has been sent by the client along with the message (Alkazimi, 2016). The client
version and the server version of the bytes should be same in handshake protocol. Using the random
numbers that have been sent earlier the communication move forward, and these random numbers
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



