Operating System Installation Presentation - Recommendations
VerifiedAdded on 2023/01/19
|9
|494
|93
Presentation
AI Summary
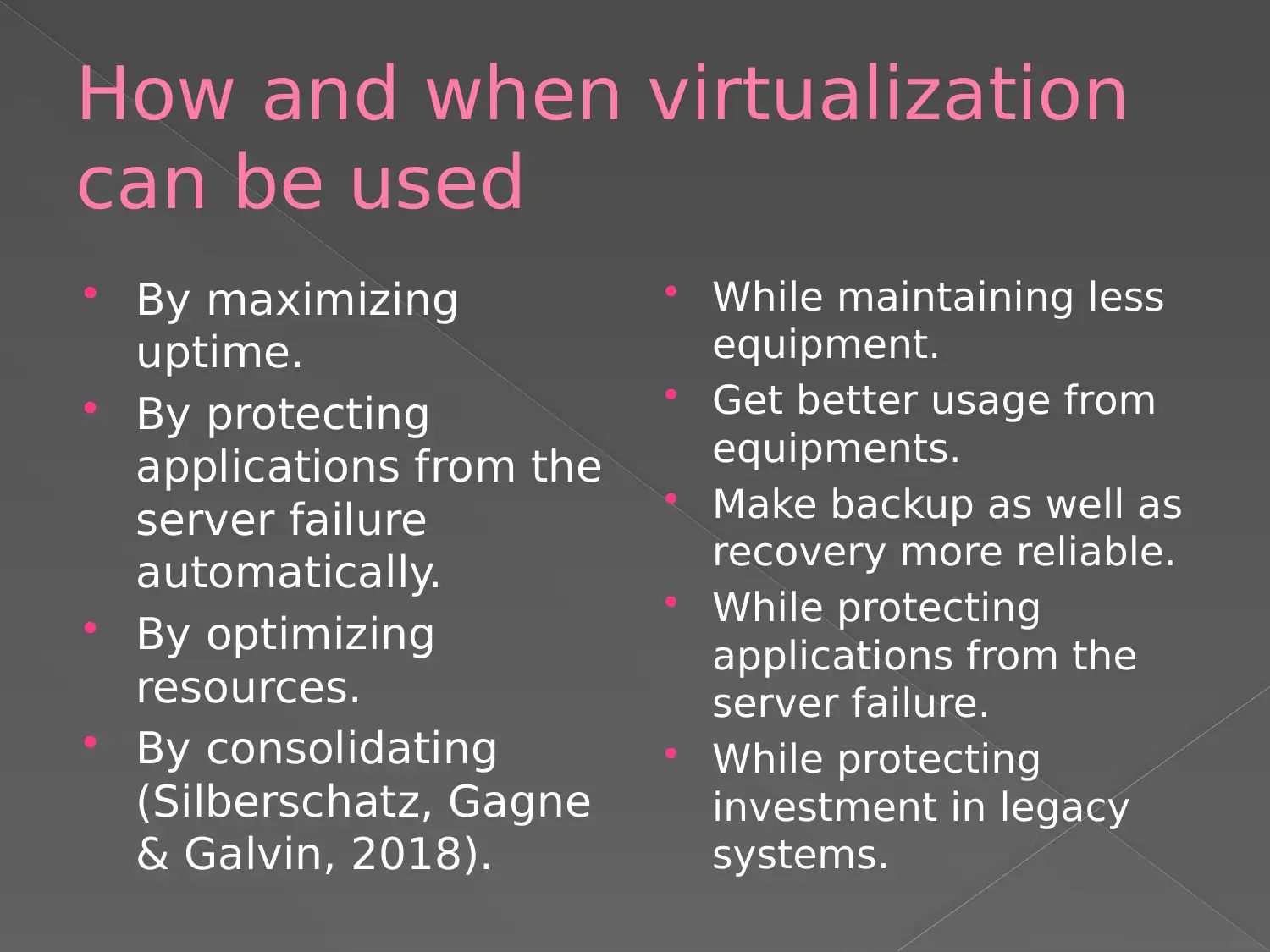
This presentation delves into the complexities of operating system installation, addressing common challenges such as setup errors, hardware recognition issues, and activation problems. It provides practical recommendations for overcoming these obstacles, including the importance of creating backups, uninstalling unnecessary applications, and addressing driver incompatibilities. The presentation also emphasizes the significance of pre and post-installation tasks, such as accessing oracle portals and configuring the system. Furthermore, it explores the benefits of virtualization, including maximizing uptime, protecting applications from server failures, and optimizing resource utilization. The presentation concludes by discussing how these steps affect system performance and the value they provide to organizations, such as reduced hardware costs, improved disaster recovery, and increased productivity. The presentation is supported by academic references like Silberschatz, Gagne & Galvin, and Cheng, Ding & Deng.
1 out of 9









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)