Comparative Analysis: Virtual Machines, Unikernals, and Dockers
VerifiedAdded on 2024/06/03
|23
|4269
|249
Report
AI Summary
This report provides a comprehensive overview of operating system level virtualization, exploring various techniques and technologies. It begins with an introduction to OS virtualization and its background, highlighting its role in enhancing security and accessibility. The discussion covers memory virtualization, detailing virtual memory addressing and demand paging, along with their advantages. CPU virtualization, including its layers and the role of rings, is examined next, followed by I/O devices virtualization. The report then delves into virtual machines, unikernels, and containers, offering a comparative analysis of their features and benefits. Finally, it explores the future trends in virtualization technology, emphasizing its continued evolution and importance in modern computing environments. The report concludes with references and a table of figures for easy navigation and understanding. Desklib provides this and many other solved assignments to help students.

Operating system level virtualization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Executive summary...........................................................................................................2
Introduction........................................................................................................................3
Background information.....................................................................................................3
Discussion..........................................................................................................................4
Memory virtualization.....................................................................................................4
CPU Virtualization..........................................................................................................8
I/O devices virtualization..............................................................................................10
Virtual machines...........................................................................................................12
Unikernals.....................................................................................................................14
Containers and Dockers...............................................................................................15
Virtual machine V/S Unikernals V/S Dockers and Containers.....................................16
Future of virtualization technology...............................................................................18
References.......................................................................................................................21
Executive summary...........................................................................................................2
Introduction........................................................................................................................3
Background information.....................................................................................................3
Discussion..........................................................................................................................4
Memory virtualization.....................................................................................................4
CPU Virtualization..........................................................................................................8
I/O devices virtualization..............................................................................................10
Virtual machines...........................................................................................................12
Unikernals.....................................................................................................................14
Containers and Dockers...............................................................................................15
Virtual machine V/S Unikernals V/S Dockers and Containers.....................................16
Future of virtualization technology...............................................................................18
References.......................................................................................................................21

Table of Figures
Figure 1 : Application level memory virtualization.............................................................6
Figure 2: Virtual to physical address translation................................................................7
Figure 3 : Process of demand paging...............................................................................9
Figure 4 : Layers of CPU virtualization............................................................................10
Figure 5 : Functioning of rings in non-virtualized and virtualized computing environment.
.........................................................................................................................................11
Figure 6 : Role of CPU in virtualization...........................................................................12
Figure 7 : Flow of I/O virtualization..................................................................................13
Figure 8 : layers in virtual machines................................................................................14
Figure 9 : system virtualization........................................................................................15
Figure 10 : process virtual machine.................................................................................16
Figure 11 : Universnal......................................................................................................17
Figure 12 : Traditional and container based virtualization...............................................18
Figure 13 : virtual machine..............................................................................................18
Figure 14 : Containers.....................................................................................................19
Figure 15 : Container within virtual machines.................................................................19
Figure 16 : Unikernals......................................................................................................20
Figure 1 : Application level memory virtualization.............................................................6
Figure 2: Virtual to physical address translation................................................................7
Figure 3 : Process of demand paging...............................................................................9
Figure 4 : Layers of CPU virtualization............................................................................10
Figure 5 : Functioning of rings in non-virtualized and virtualized computing environment.
.........................................................................................................................................11
Figure 6 : Role of CPU in virtualization...........................................................................12
Figure 7 : Flow of I/O virtualization..................................................................................13
Figure 8 : layers in virtual machines................................................................................14
Figure 9 : system virtualization........................................................................................15
Figure 10 : process virtual machine.................................................................................16
Figure 11 : Universnal......................................................................................................17
Figure 12 : Traditional and container based virtualization...............................................18
Figure 13 : virtual machine..............................................................................................18
Figure 14 : Containers.....................................................................................................19
Figure 15 : Container within virtual machines.................................................................19
Figure 16 : Unikernals......................................................................................................20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Executive summary
Operating System is the program that when primarily loaded into the system by the boot
program, handles all the other programs.it is used by different applications by to
complete their task by requesting OS services through application program interface . In
virtualization the framework divides the system into one or more executing
environments .It is a way of rationally isolating the system resources delivered
by mainframe computers between dissimilar applications .Operating System
virtualization is the way of using system software to allow the hardware of the system to
run different OS commands concurrently, resulting in various applications running
simultaneously on the system .This is a technique by which a simple single operating
system can be converted into a system to handle multiple applications run by multiple
users at a single time. Even though they all run parallel they do not interfere into each
other. The virtualized environment works on separate commands given by various users
working at the same time. The command given in one environment is processed
separately in separate operating system. The operating system uses its free end to
handle different users. All the users are differentiated and their commands are executed
by the virtualized operating system. This is a type of server virtualization. A virtual
version of OS enables multitasking and increases efficiency. Generally, installing and
configuring the system manually takes long time, but virtualizing the environment takes
less time leading to time savings. The OS level virtualization changes the working
environment of the system without changing the hardware of the system.
Operating System is the program that when primarily loaded into the system by the boot
program, handles all the other programs.it is used by different applications by to
complete their task by requesting OS services through application program interface . In
virtualization the framework divides the system into one or more executing
environments .It is a way of rationally isolating the system resources delivered
by mainframe computers between dissimilar applications .Operating System
virtualization is the way of using system software to allow the hardware of the system to
run different OS commands concurrently, resulting in various applications running
simultaneously on the system .This is a technique by which a simple single operating
system can be converted into a system to handle multiple applications run by multiple
users at a single time. Even though they all run parallel they do not interfere into each
other. The virtualized environment works on separate commands given by various users
working at the same time. The command given in one environment is processed
separately in separate operating system. The operating system uses its free end to
handle different users. All the users are differentiated and their commands are executed
by the virtualized operating system. This is a type of server virtualization. A virtual
version of OS enables multitasking and increases efficiency. Generally, installing and
configuring the system manually takes long time, but virtualizing the environment takes
less time leading to time savings. The OS level virtualization changes the working
environment of the system without changing the hardware of the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
This report discusses the operating system level virtualization also knows as the
emulation of computer operating system. An emulator is a software or hardware that
makes one computing system (host) to behave like another computing system (guest).
In OS virtualization the operating system of the computing machine is divided into
several parts and each part behaves as an individual separately working OS. There is
no interference by the guest to the host and vice versa. The guest is the virtualized OS
which shares the resources as the host system (Yu, 2007).
Background information
OS-level virtualization is an innovation that segments the working framework to make
several remote Virtual Machines. The condition of base working is divided into a flash
by using the virtual implementation of a virtual machine. Operating System virtualization
has been generally used to advance security, susceptibility and accessibility of the
present compound programming condition. These conditions are used with the asset
overhead and runtime that are irrelevant with the change in framework of current
registering. This report will include examine process of the Window NT and its OS parts
and extant in virtualization of OS level with the FVM that use on stage of window. There
are various benefits of the virtualization technologies are as follows:
Reduce the cost of operating and capital
Minimized the downtime or eliminate it
Increase responsiveness with the agility and IT productivity
Disaster recovery with continuity of greater business
Management of the simplified data centre
To keep malevolent portable code from trading work area's worthiness, an unknown
content is used for the finishing in a VM. Use the replica service for the scan purpose in
a VM that raised the exposure scanner of the virtualized services, these services is
used for the creation mode with checking process of the helplessness and benefits. The
execution behaviour of the browsers is managed by reducing the running page and with
This report discusses the operating system level virtualization also knows as the
emulation of computer operating system. An emulator is a software or hardware that
makes one computing system (host) to behave like another computing system (guest).
In OS virtualization the operating system of the computing machine is divided into
several parts and each part behaves as an individual separately working OS. There is
no interference by the guest to the host and vice versa. The guest is the virtualized OS
which shares the resources as the host system (Yu, 2007).
Background information
OS-level virtualization is an innovation that segments the working framework to make
several remote Virtual Machines. The condition of base working is divided into a flash
by using the virtual implementation of a virtual machine. Operating System virtualization
has been generally used to advance security, susceptibility and accessibility of the
present compound programming condition. These conditions are used with the asset
overhead and runtime that are irrelevant with the change in framework of current
registering. This report will include examine process of the Window NT and its OS parts
and extant in virtualization of OS level with the FVM that use on stage of window. There
are various benefits of the virtualization technologies are as follows:
Reduce the cost of operating and capital
Minimized the downtime or eliminate it
Increase responsiveness with the agility and IT productivity
Disaster recovery with continuity of greater business
Management of the simplified data centre
To keep malevolent portable code from trading work area's worthiness, an unknown
content is used for the finishing in a VM. Use the replica service for the scan purpose in
a VM that raised the exposure scanner of the virtualized services, these services is
used for the creation mode with checking process of the helplessness and benefits. The
execution behaviour of the browsers is managed by reducing the running page and with

the use of web crawler to recognise and remove the weakness of the websites and
browsers. To permit Windows desktop to give doubles that are halfway put away,
oversaw and fixed, we dispatch shared pairs in an extraordinary Virtual Machine whose
runtime condition is foreign made from a principal twofold server. Virtual machines used
the process of altering and seeing to secure the files on the server side and this process
are running on the customer VM but this process ignore the content to being protected
from the client side. In this complete process, require to find the contents of the
application with the structure of the FVM.
Discussion
Memory virtualization
Modern technology provides a facility of memory virtualization technique also
knows a virtual memory addressing. This technique is used when the computer
runs low on random access memory (RAM) to run any program or operation. The
computer uses virtual memory to support this scarcity of memory. Virtual memory
attaches the hard disk of the computer with the RAM of the computer to
temporary compensate the need of RAM.
Figure 1: Application level memory virtualization
browsers. To permit Windows desktop to give doubles that are halfway put away,
oversaw and fixed, we dispatch shared pairs in an extraordinary Virtual Machine whose
runtime condition is foreign made from a principal twofold server. Virtual machines used
the process of altering and seeing to secure the files on the server side and this process
are running on the customer VM but this process ignore the content to being protected
from the client side. In this complete process, require to find the contents of the
application with the structure of the FVM.
Discussion
Memory virtualization
Modern technology provides a facility of memory virtualization technique also
knows a virtual memory addressing. This technique is used when the computer
runs low on random access memory (RAM) to run any program or operation. The
computer uses virtual memory to support this scarcity of memory. Virtual memory
attaches the hard disk of the computer with the RAM of the computer to
temporary compensate the need of RAM.
Figure 1: Application level memory virtualization
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
The need of virtual memory arises with the fact that the physical memory i.e.,
RAM is limited and can only be used to some extent. The physical memory
available is of fixed size. Sometimes the space needed to run an operation or
program is not available on RAM and this leads to operation execution failure.
This problem of the system is solved by the virtual addressing technique. When
the system lacks the memory on RAM, it shifts some data from RAM to hard disc
into the paging file.
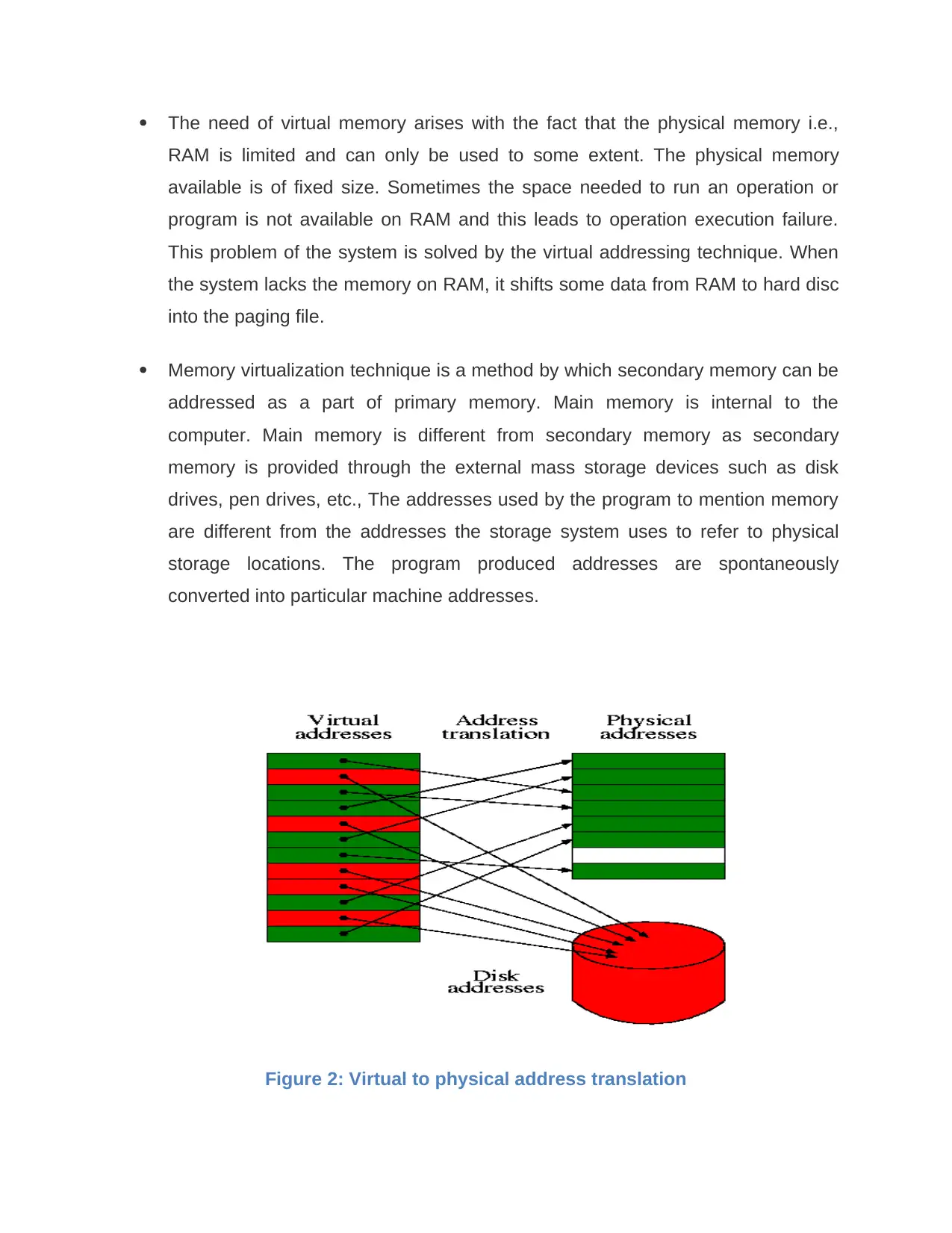
Memory virtualization technique is a method by which secondary memory can be
addressed as a part of primary memory. Main memory is internal to the
computer. Main memory is different from secondary memory as secondary
memory is provided through the external mass storage devices such as disk
drives, pen drives, etc., The addresses used by the program to mention memory
are different from the addresses the storage system uses to refer to physical
storage locations. The program produced addresses are spontaneously
converted into particular machine addresses.
Figure 2: Virtual to physical address translation
RAM is limited and can only be used to some extent. The physical memory
available is of fixed size. Sometimes the space needed to run an operation or
program is not available on RAM and this leads to operation execution failure.
This problem of the system is solved by the virtual addressing technique. When
the system lacks the memory on RAM, it shifts some data from RAM to hard disc
into the paging file.
Memory virtualization technique is a method by which secondary memory can be
addressed as a part of primary memory. Main memory is internal to the
computer. Main memory is different from secondary memory as secondary
memory is provided through the external mass storage devices such as disk
drives, pen drives, etc., The addresses used by the program to mention memory
are different from the addresses the storage system uses to refer to physical
storage locations. The program produced addresses are spontaneously
converted into particular machine addresses.
Figure 2: Virtual to physical address translation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Both software and hardware are used to implement the memory virtualization
technique. It maps the virtual address, i.e., the program generated an address,
with the physical memory address in computer memory. All memory references
created during the execution of any process or operation are logical addresses
that are converted dynamically into physical addresses.
When a process is executed it is not mandatory that all the pages or segments
are available in the RAM, this means that segments are needed to be loaded into
the main memory whenever needed. This process of loading the pages of
memory from secondary memory into main memory at runtime is known as
demand paging. Demand paging is the method of implementation of virtual
memory.
Page faults are the interruption occurred during the program execution when a
program wishes a data which is not currently available in primary memory. This
interruption starts system to fetch the data from virtual memory and bring it into
main memory. Invalid page faults arise when the system cannot discover the
requested files in virtual memory.
The process of demand paging includes following steps:
1. The system tries to access a page that is not available in the main memory
resulting in page fault or memory access fault.
2. Due to interrupt generated, the process of execution goes from run state to
blocking state. For bringing the process back in execution state the system
must get the page requested by the process.
3. Logical address space is searched for a required page.
technique. It maps the virtual address, i.e., the program generated an address,
with the physical memory address in computer memory. All memory references
created during the execution of any process or operation are logical addresses
that are converted dynamically into physical addresses.
When a process is executed it is not mandatory that all the pages or segments
are available in the RAM, this means that segments are needed to be loaded into
the main memory whenever needed. This process of loading the pages of
memory from secondary memory into main memory at runtime is known as
demand paging. Demand paging is the method of implementation of virtual
memory.
Page faults are the interruption occurred during the program execution when a
program wishes a data which is not currently available in primary memory. This
interruption starts system to fetch the data from virtual memory and bring it into
main memory. Invalid page faults arise when the system cannot discover the
requested files in virtual memory.
The process of demand paging includes following steps:
1. The system tries to access a page that is not available in the main memory
resulting in page fault or memory access fault.
2. Due to interrupt generated, the process of execution goes from run state to
blocking state. For bringing the process back in execution state the system
must get the page requested by the process.
3. Logical address space is searched for a required page.
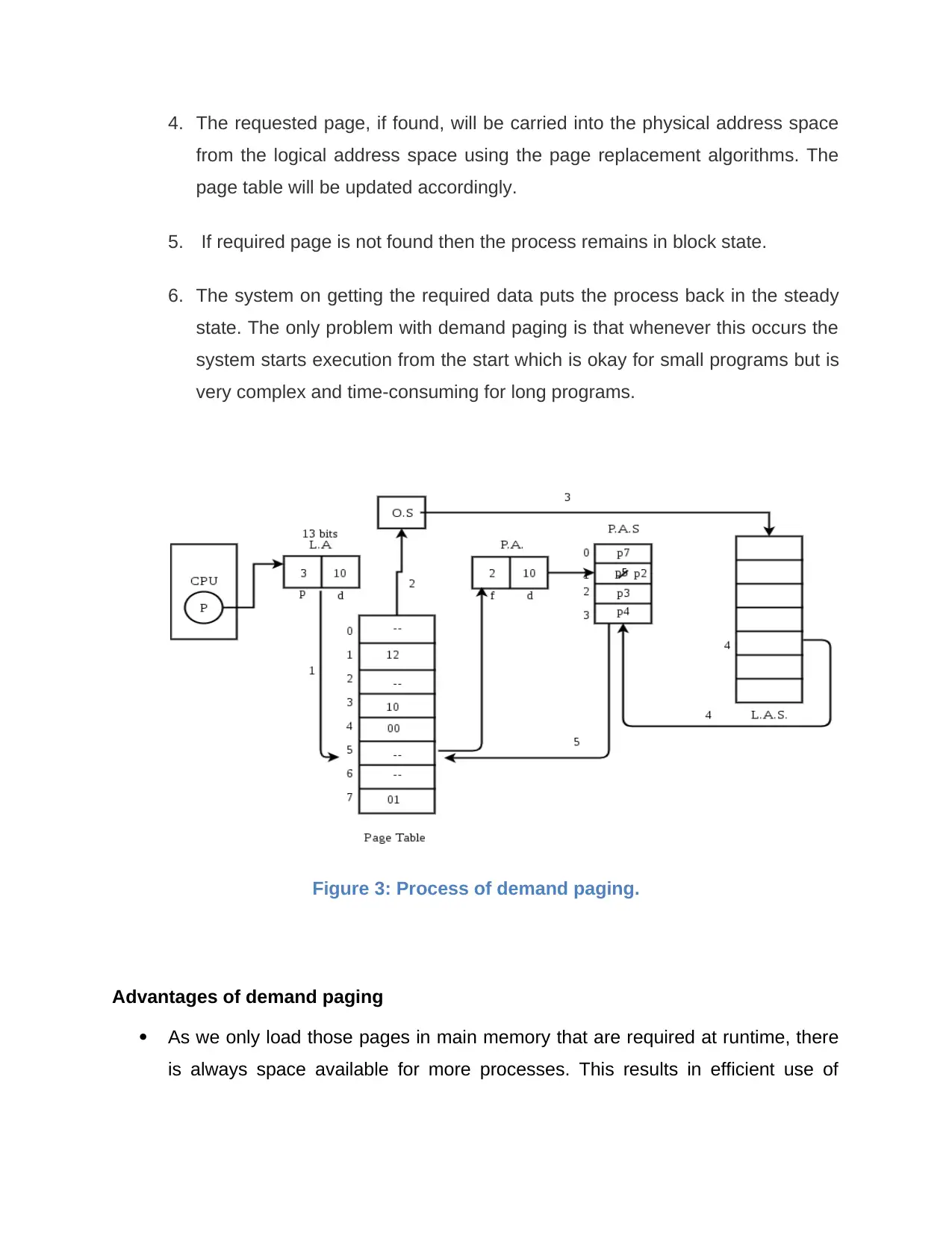
4. The requested page, if found, will be carried into the physical address space
from the logical address space using the page replacement algorithms. The
page table will be updated accordingly.
5. If required page is not found then the process remains in block state.
6. The system on getting the required data puts the process back in the steady
state. The only problem with demand paging is that whenever this occurs the
system starts execution from the start which is okay for small programs but is
very complex and time-consuming for long programs.
Figure 3: Process of demand paging.
Advantages of demand paging
As we only load those pages in main memory that are required at runtime, there
is always space available for more processes. This results in efficient use of
from the logical address space using the page replacement algorithms. The
page table will be updated accordingly.
5. If required page is not found then the process remains in block state.
6. The system on getting the required data puts the process back in the steady
state. The only problem with demand paging is that whenever this occurs the
system starts execution from the start which is okay for small programs but is
very complex and time-consuming for long programs.
Figure 3: Process of demand paging.
Advantages of demand paging
As we only load those pages in main memory that are required at runtime, there
is always space available for more processes. This results in efficient use of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

processor because at any instance of time there are always many processes in a
ready state.
Any process which is larger than the main memory itself can be executed
because of demand paging. The system automatically loads pages into main
memory whenever required (Obasuyi & Sari, 2015).
CPU Virtualization
CPU virtualization technique enables the computer to behave as several self-
governing working computers to run multiple operating systems concurrently on
the same device. This technology is also known as Vanderpool.
CPU virtualization increases system presentation and runs straight on the
processor. The elemental physical resources are utilized whenever needed and
the virtualization layer runs commands only as desired to make virtual machines
function as if they were running directly on distinct machines.
Each application program is denoted by an algorithm, i.e., series of instruction
and executed by a computer.
During the execution of any application or process, the algorithm is first
instructed to virtual computing environment an then that virtual environment is
mapped or connected to the physical CPU to run instruction through VVM.
ready state.
Any process which is larger than the main memory itself can be executed
because of demand paging. The system automatically loads pages into main
memory whenever required (Obasuyi & Sari, 2015).
CPU Virtualization
CPU virtualization technique enables the computer to behave as several self-
governing working computers to run multiple operating systems concurrently on
the same device. This technology is also known as Vanderpool.
CPU virtualization increases system presentation and runs straight on the
processor. The elemental physical resources are utilized whenever needed and
the virtualization layer runs commands only as desired to make virtual machines
function as if they were running directly on distinct machines.
Each application program is denoted by an algorithm, i.e., series of instruction
and executed by a computer.
During the execution of any application or process, the algorithm is first
instructed to virtual computing environment an then that virtual environment is
mapped or connected to the physical CPU to run instruction through VVM.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
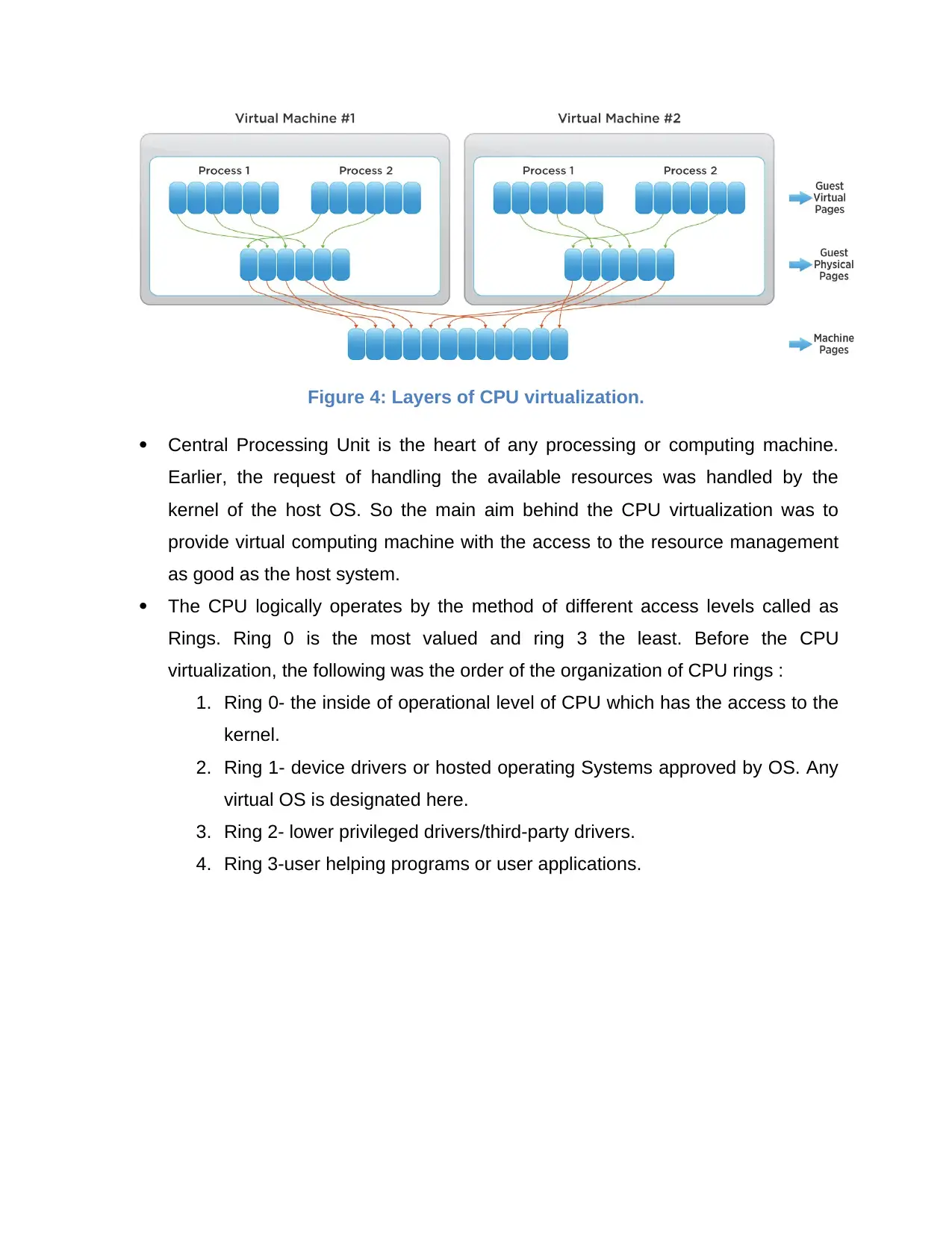
Figure 4: Layers of CPU virtualization.
Central Processing Unit is the heart of any processing or computing machine.
Earlier, the request of handling the available resources was handled by the
kernel of the host OS. So the main aim behind the CPU virtualization was to
provide virtual computing machine with the access to the resource management
as good as the host system.
The CPU logically operates by the method of different access levels called as
Rings. Ring 0 is the most valued and ring 3 the least. Before the CPU
virtualization, the following was the order of the organization of CPU rings :
1. Ring 0- the inside of operational level of CPU which has the access to the
kernel.
2. Ring 1- device drivers or hosted operating Systems approved by OS. Any
virtual OS is designated here.
3. Ring 2- lower privileged drivers/third-party drivers.
4. Ring 3-user helping programs or user applications.
Central Processing Unit is the heart of any processing or computing machine.
Earlier, the request of handling the available resources was handled by the
kernel of the host OS. So the main aim behind the CPU virtualization was to
provide virtual computing machine with the access to the resource management
as good as the host system.
The CPU logically operates by the method of different access levels called as
Rings. Ring 0 is the most valued and ring 3 the least. Before the CPU
virtualization, the following was the order of the organization of CPU rings :
1. Ring 0- the inside of operational level of CPU which has the access to the
kernel.
2. Ring 1- device drivers or hosted operating Systems approved by OS. Any
virtual OS is designated here.
3. Ring 2- lower privileged drivers/third-party drivers.
4. Ring 3-user helping programs or user applications.
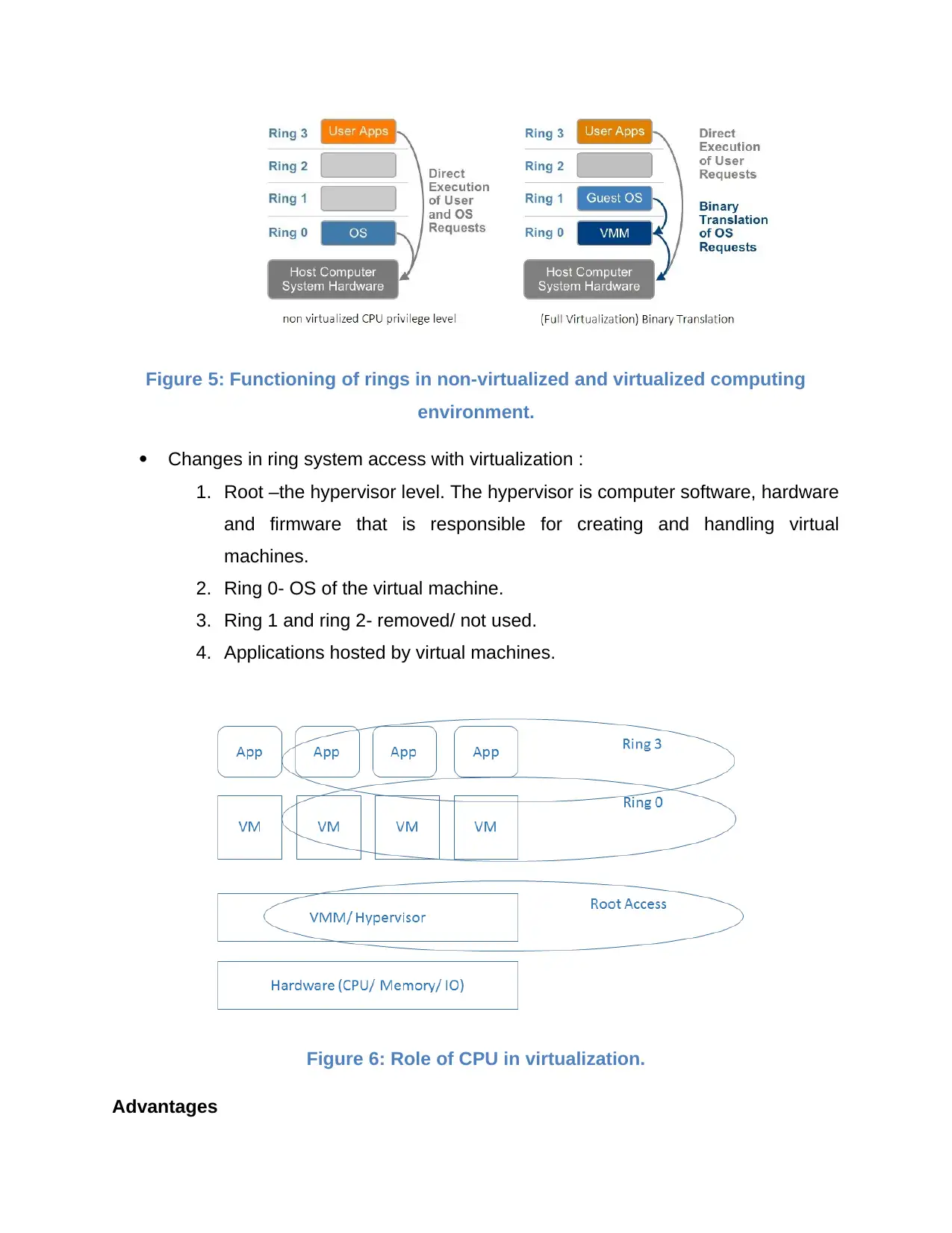
Figure 5: Functioning of rings in non-virtualized and virtualized computing
environment.
Changes in ring system access with virtualization :
1. Root –the hypervisor level. The hypervisor is computer software, hardware
and firmware that is responsible for creating and handling virtual
machines.
2. Ring 0- OS of the virtual machine.
3. Ring 1 and ring 2- removed/ not used.
4. Applications hosted by virtual machines.
Figure 6: Role of CPU in virtualization.
Advantages
environment.
Changes in ring system access with virtualization :
1. Root –the hypervisor level. The hypervisor is computer software, hardware
and firmware that is responsible for creating and handling virtual
machines.
2. Ring 0- OS of the virtual machine.
3. Ring 1 and ring 2- removed/ not used.
4. Applications hosted by virtual machines.
Figure 6: Role of CPU in virtualization.
Advantages
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





