Operating Systems Vulnerability Assessment Project Report
VerifiedAdded on 2022/09/01
|17
|1293
|29
Project
AI Summary
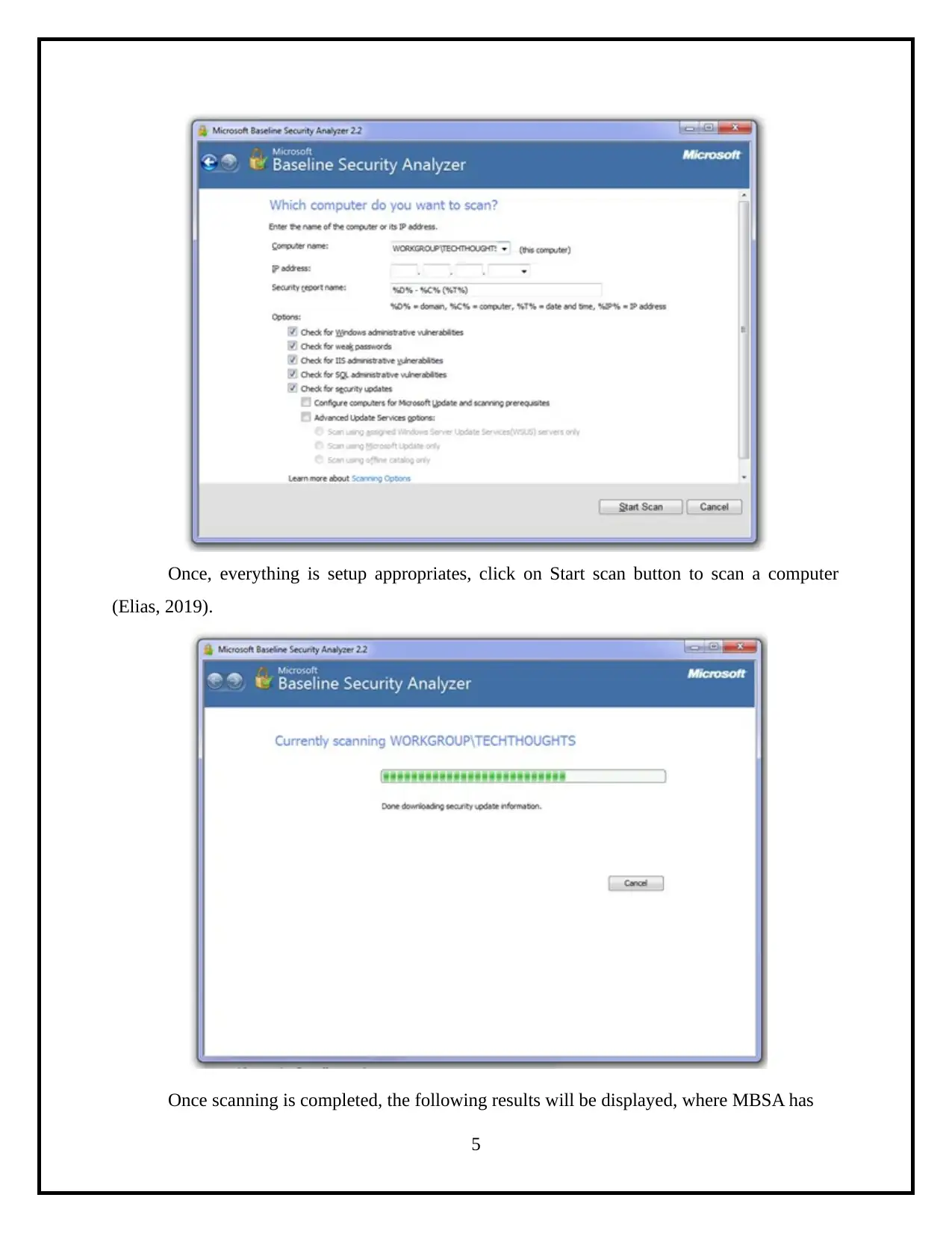
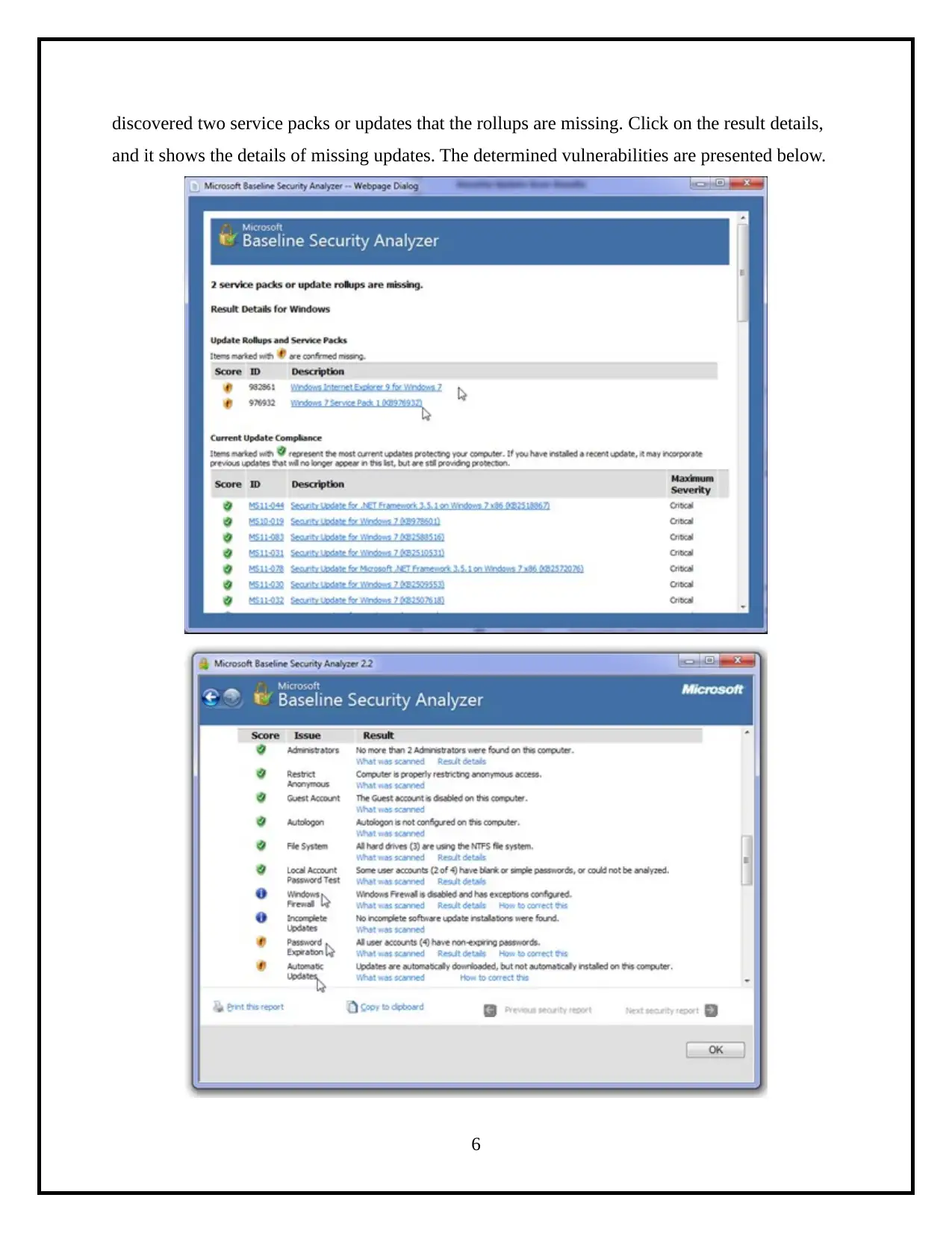
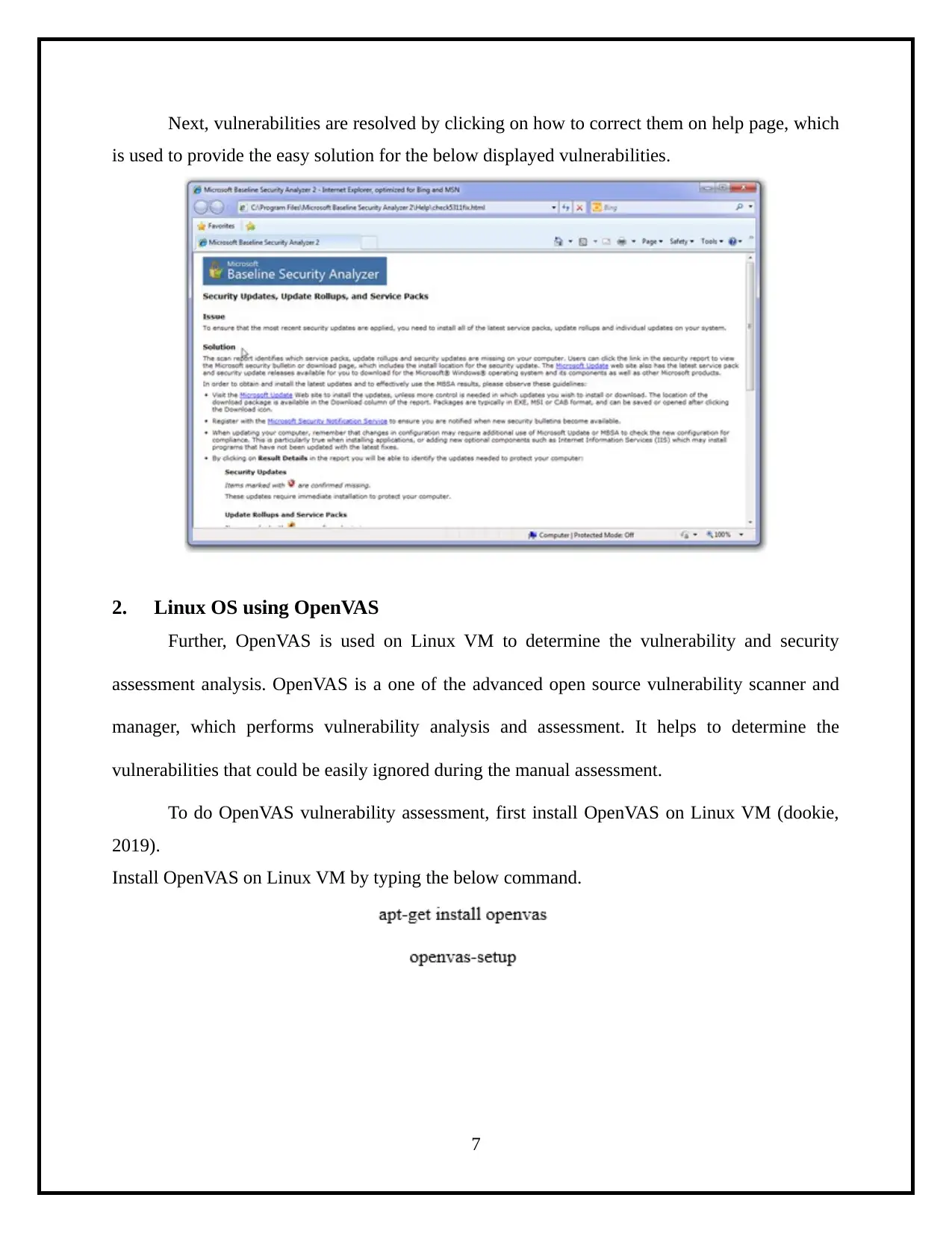
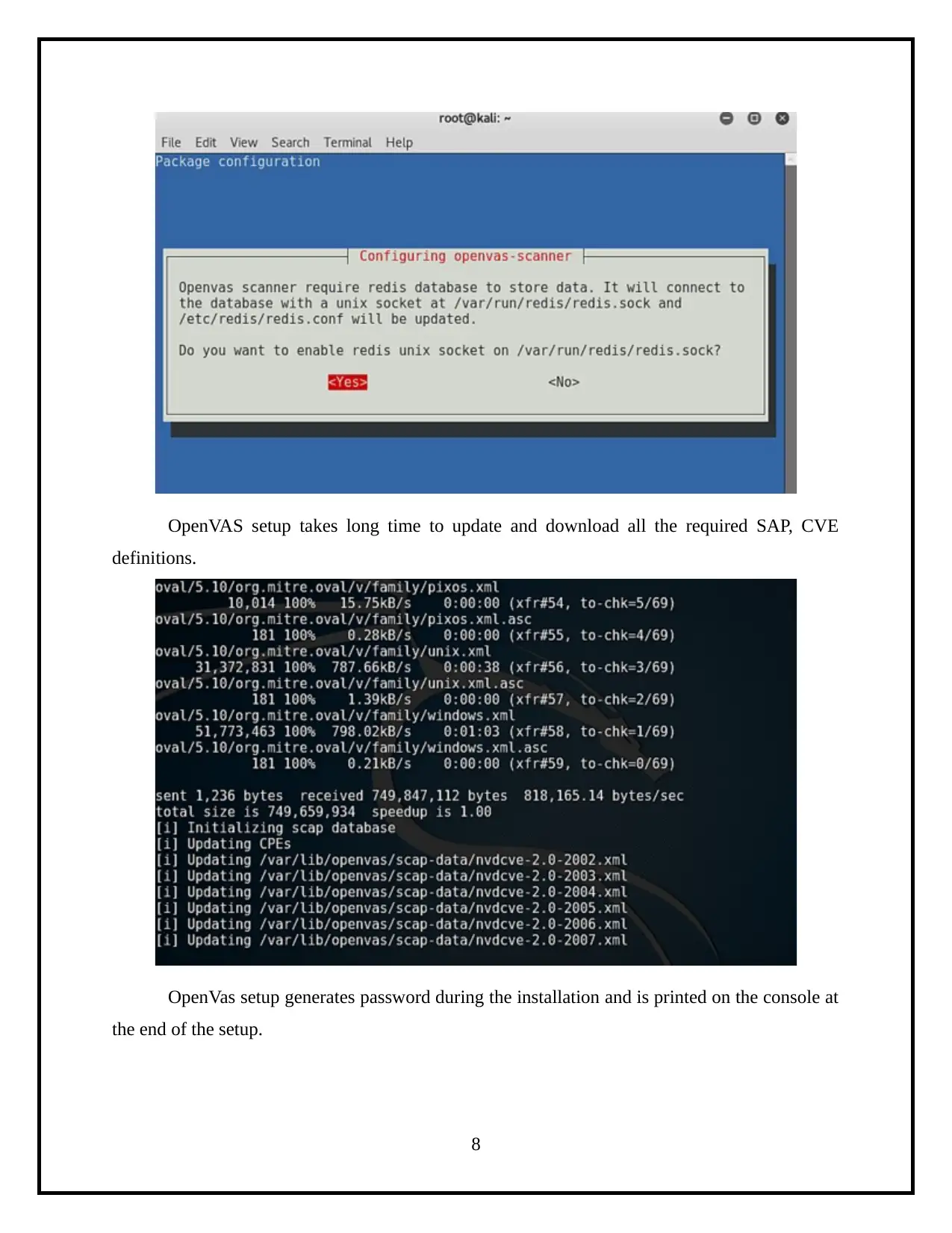
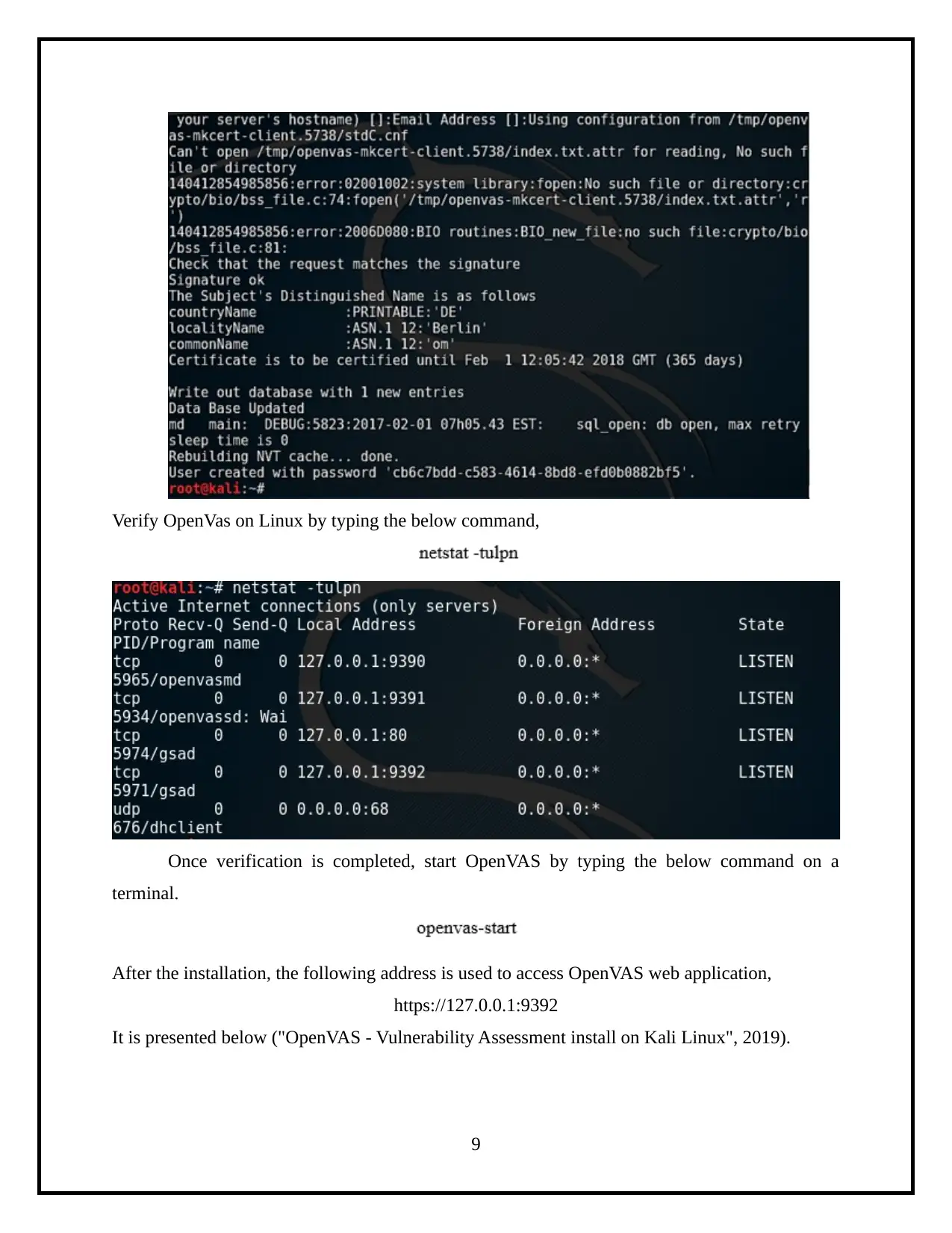
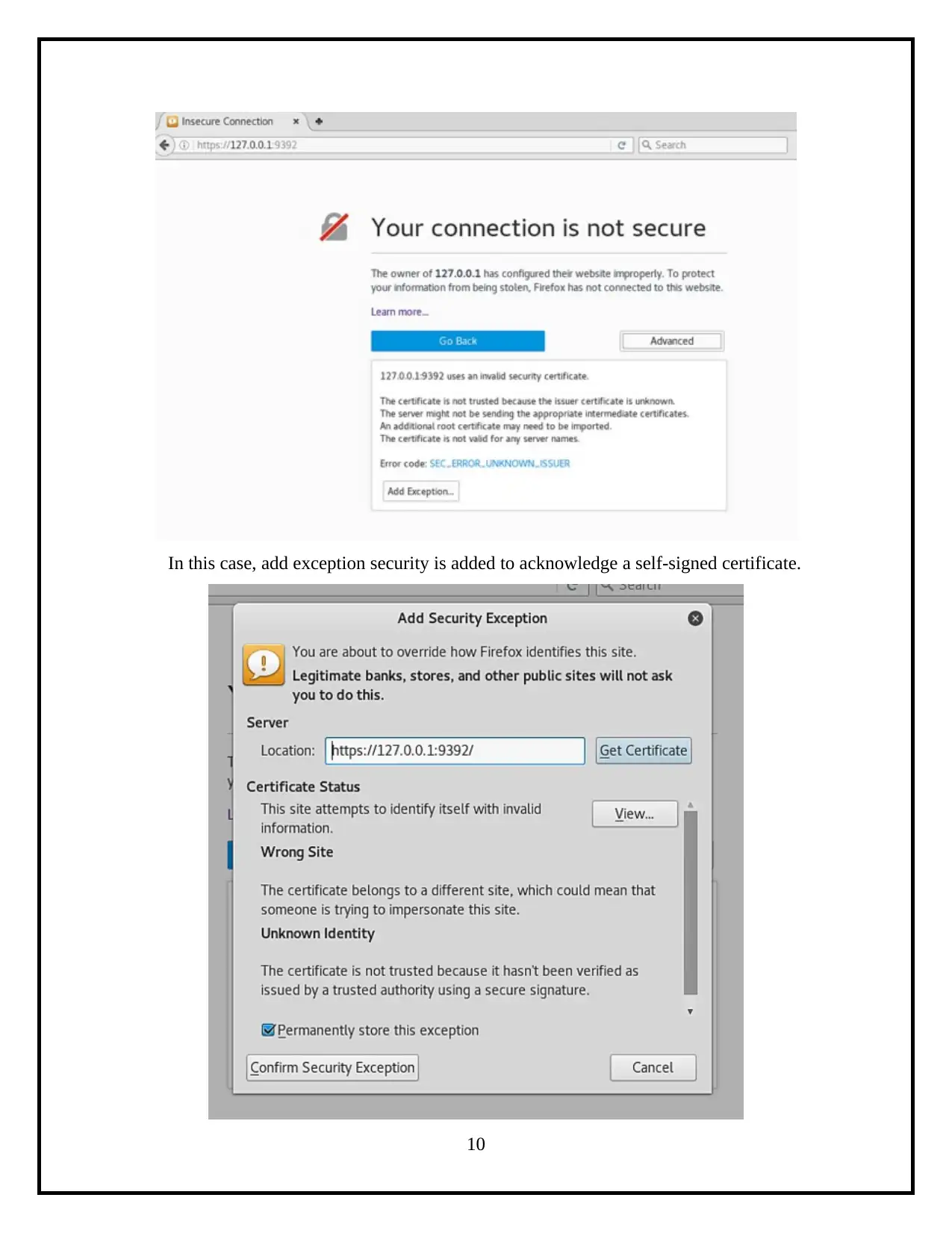
This project details the process of assessing operating system vulnerabilities in both Windows and Linux environments. The assessment utilizes Microsoft Baseline Security Analyzer (MBSA) for Windows and OpenVAS for Linux, two widely-used tools for identifying security misconfigurations and missing updates. The project involves the installation, configuration, and execution of these tools, followed by an analysis of the scan results to identify vulnerabilities. Specifically, the report demonstrates the use of MBSA to identify missing service packs and updates on a Windows system, and OpenVAS to detect vulnerabilities on a Linux system. The final step involves creating a comprehensive security assessment report summarizing the findings, including the identified vulnerabilities, their severity levels, and potential remediation steps. The report highlights administrative vulnerabilities and weak passwords, and provides a clear overview of the security posture of the assessed systems.
1 out of 17









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)