NIT1202 Operating Systems Assignment 1: Review and Algorithm Analysis
VerifiedAdded on 2022/11/23
|11
|1494
|372
Homework Assignment
AI Summary
This document presents a comprehensive solution to an Operating Systems assignment, addressing key concepts such as memory management, processor scheduling, and algorithm analysis. The solution begins with a review of a research paper on hardware support for embedded operating system security, summarizing the article's content, conclusions, and providing a personal evaluation. The assignment then delves into memory allocation algorithms, including best-fit and first-fit, and explores the differences between internal and external fragmentation. Further sections analyze page numbers, displacement calculations, and failure/success ratios in memory management. The solution also covers processor scheduling techniques like FCFS and SJN, calculating turnaround times and average turnaround times. Finally, the assignment explores FCFS, SJN, SRT and Round Robin scheduling algorithms, providing detailed execution timelines. The solution is designed to help students understand and solve operating systems problems. Desklib provides access to past papers and solved assignments for students.

BACHELOR OF IT
0
NIT1202 Operating Systems
0
NIT1202 Operating Systems
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BACHELOR OF IT
1
Table of Contents
Question 1.............................................................................................................................................2
Summary of the paper........................................................................................................................2
Conclusion.........................................................................................................................................2
Personal evaluation of the paper........................................................................................................2
Question 2.............................................................................................................................................3
A: best-fit algorithm..........................................................................................................................3
B: first fit algorithm...........................................................................................................................3
Question 3:............................................................................................................................................3
Question 4.............................................................................................................................................3
A: pages needed for storing the complete jobs..................................................................................3
B: page numbers and displacement....................................................................................................3
Question 5:............................................................................................................................................4
A: the failure and success ratios........................................................................................................4
B: failure rate and success ratio.........................................................................................................4
C: conclusion.....................................................................................................................................5
Question 6.............................................................................................................................................5
A: FCFS technique............................................................................................................................5
B: SJN technique...............................................................................................................................5
Question 7.............................................................................................................................................6
A: FCFS............................................................................................................................................6
B: SJN...............................................................................................................................................6
C: SRT...............................................................................................................................................7
D: Round robin..................................................................................................................................7
References...........................................................................................................................................10
1
Table of Contents
Question 1.............................................................................................................................................2
Summary of the paper........................................................................................................................2
Conclusion.........................................................................................................................................2
Personal evaluation of the paper........................................................................................................2
Question 2.............................................................................................................................................3
A: best-fit algorithm..........................................................................................................................3
B: first fit algorithm...........................................................................................................................3
Question 3:............................................................................................................................................3
Question 4.............................................................................................................................................3
A: pages needed for storing the complete jobs..................................................................................3
B: page numbers and displacement....................................................................................................3
Question 5:............................................................................................................................................4
A: the failure and success ratios........................................................................................................4
B: failure rate and success ratio.........................................................................................................4
C: conclusion.....................................................................................................................................5
Question 6.............................................................................................................................................5
A: FCFS technique............................................................................................................................5
B: SJN technique...............................................................................................................................5
Question 7.............................................................................................................................................6
A: FCFS............................................................................................................................................6
B: SJN...............................................................................................................................................6
C: SRT...............................................................................................................................................7
D: Round robin..................................................................................................................................7
References...........................................................................................................................................10

BACHELOR OF IT
2
Question 1
Summary of the paper
The title of this journal paper is Hardware Support for Embedded Operating System
Security which was written in the year 2017. This journal paper is completely based on the
operating system and the authors reviewed the security concern and hardware support for the
embedded operating system. The purpose of this paper is to analyse the significance of
operating system (Pouraghily, Wolf, & Tessier, 2017). According to the researchers, security
is a very serious concern faced by consumers while using operating systems in computer
devices. Such kind of issues directly impact on the personal data or information of consumers
and also increase security risks for the software developers.
After analysing this paper it is identified that internet connected embedded systems
have limited abilities to defend themselves against security threats and attacks. In this journal
paper, the authors proposed a hardware-based monitoring process which can easily detect the
security risks and threats from the operating system (Silberschatz, Gagne, & Galvin, (2018).
Moreover, the researchers critically reviewed the importance of security and effective
operating system in the field of computer devices and analysed the opinions of other
researchers. After analysing this paper it is identified that the hacker's attacks on the
operating system used by consumers which helped them for controlling and obtaining the
private detail of consumers.
Conclusion
In this journal paper, the authors show a hardware-based security system which can
ensure the correct execution of operating systems and applications in the computer devices.
From this study, it is concluded that the operating system is a common platform used by
hackers for entering into the consumer’s personal accounts. This journal paper indicated that
the developed mechanism is more effective for identifying the security risks and attack linked
with the operating systems. The authors believe that this research study provided a platform
to the readers for understanding security risks linked with embedded processing and
operating systems.
Personal evaluation of the paper
As per my understanding, the authors provide in-depth analysis about the research
topic but security is an effective research topic which made the investigation more
2
Question 1
Summary of the paper
The title of this journal paper is Hardware Support for Embedded Operating System
Security which was written in the year 2017. This journal paper is completely based on the
operating system and the authors reviewed the security concern and hardware support for the
embedded operating system. The purpose of this paper is to analyse the significance of
operating system (Pouraghily, Wolf, & Tessier, 2017). According to the researchers, security
is a very serious concern faced by consumers while using operating systems in computer
devices. Such kind of issues directly impact on the personal data or information of consumers
and also increase security risks for the software developers.
After analysing this paper it is identified that internet connected embedded systems
have limited abilities to defend themselves against security threats and attacks. In this journal
paper, the authors proposed a hardware-based monitoring process which can easily detect the
security risks and threats from the operating system (Silberschatz, Gagne, & Galvin, (2018).
Moreover, the researchers critically reviewed the importance of security and effective
operating system in the field of computer devices and analysed the opinions of other
researchers. After analysing this paper it is identified that the hacker's attacks on the
operating system used by consumers which helped them for controlling and obtaining the
private detail of consumers.
Conclusion
In this journal paper, the authors show a hardware-based security system which can
ensure the correct execution of operating systems and applications in the computer devices.
From this study, it is concluded that the operating system is a common platform used by
hackers for entering into the consumer’s personal accounts. This journal paper indicated that
the developed mechanism is more effective for identifying the security risks and attack linked
with the operating systems. The authors believe that this research study provided a platform
to the readers for understanding security risks linked with embedded processing and
operating systems.
Personal evaluation of the paper
As per my understanding, the authors provide in-depth analysis about the research
topic but security is an effective research topic which made the investigation more
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BACHELOR OF IT
3
interesting. This research study is related to my experience because I have faced various
kinds of security threats and risks while utilizing embedded operating systems. Moreover, the
researchers identified the risks factors linked with the embedded operating systems by which
readers or students can gain their skills in the field of the operating system.
Question 2
A: best-fit algorithm
As per the provided information, the job A is added to the block 3, Job B is added in
the empty block or waiting job C is added to the block 4 and job D is added to the block 1.
B: first fit algorithm
As per the provided data, the job A is added to the block 1, job B is in the waiting
process, job C is added to the block 2, and job D is in the waiting process.
Question 3:
As compared with the external fragmentation, the internal fragmentation occurs when
the reminiscence deliver leave extra memory in the system (Tech Difference, 2016).
Moreover, the internal fragmentation occurs in the field of page frame while external
fragmentation occurs between numbers of segmentation used in the system.
Therefore, the external fragmentation might be preferred due to their compaction
features which provide a platform to the consumers to use free space in the segmentation. It is
identified that in terms of efficiency the external fragmentation is more effective rather than
internal so, consumers may be used external fragmentation in the system (Stack over Flow,
2016).
Question 4
A: pages needed for storing the complete jobs
The total numbers of pages required can be calculated with the below equation:
(471/100) + 1= 5
Therefore, here total 5 pages are needed to store the entire jobs.
3
interesting. This research study is related to my experience because I have faced various
kinds of security threats and risks while utilizing embedded operating systems. Moreover, the
researchers identified the risks factors linked with the embedded operating systems by which
readers or students can gain their skills in the field of the operating system.
Question 2
A: best-fit algorithm
As per the provided information, the job A is added to the block 3, Job B is added in
the empty block or waiting job C is added to the block 4 and job D is added to the block 1.
B: first fit algorithm
As per the provided data, the job A is added to the block 1, job B is in the waiting
process, job C is added to the block 2, and job D is in the waiting process.
Question 3:
As compared with the external fragmentation, the internal fragmentation occurs when
the reminiscence deliver leave extra memory in the system (Tech Difference, 2016).
Moreover, the internal fragmentation occurs in the field of page frame while external
fragmentation occurs between numbers of segmentation used in the system.
Therefore, the external fragmentation might be preferred due to their compaction
features which provide a platform to the consumers to use free space in the segmentation. It is
identified that in terms of efficiency the external fragmentation is more effective rather than
internal so, consumers may be used external fragmentation in the system (Stack over Flow,
2016).
Question 4
A: pages needed for storing the complete jobs
The total numbers of pages required can be calculated with the below equation:
(471/100) + 1= 5
Therefore, here total 5 pages are needed to store the entire jobs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BACHELOR OF IT
4
B: page numbers and displacement
There are following calculating can be used for findings numbers of pages and exact
displacements
(100*0) +0= 0
Here, numbers of pages= 0 and displacement= 0
(100*1) +0= 100
Numbers of pages= 1 and displacement= 0
(132*1) +0= 132
Page number= 1 and displacement= 32
(100*2) +0= 200
Page number = 2 and displacement = 0
(100*3) +0= 300
Page number= 3 and displacement= 0
(100*4) +71=471
Page number= 4 and displacement= 71
Question 5:
A: the failure and success ratios
The failure rate is given as 10/12= 83%
The success rate is given as 2/12= 17%
4
B: page numbers and displacement
There are following calculating can be used for findings numbers of pages and exact
displacements
(100*0) +0= 0
Here, numbers of pages= 0 and displacement= 0
(100*1) +0= 100
Numbers of pages= 1 and displacement= 0
(132*1) +0= 132
Page number= 1 and displacement= 32
(100*2) +0= 200
Page number = 2 and displacement = 0
(100*3) +0= 300
Page number= 3 and displacement= 0
(100*4) +71=471
Page number= 4 and displacement= 71
Question 5:
A: the failure and success ratios
The failure rate is given as 10/12= 83%
The success rate is given as 2/12= 17%

BACHELOR OF IT
5
B: failure rate and success ratio
As per the given information the failure ratio and success ratio is given as:
Failure ratio= 75%
Success ratio= 25%
C: conclusion
It is concluded that adding more numbers of pages in the system using a FIFO
algorithm can impact on the level of failure rate that means it reduces the rate of failure and
increases the rate of success ratio. It is identified that adding numbers of page frames can
impact on the efficiency of the system in an effective manner.
Question 6
A: FCFS technique
As per the given information Job A = 12, Job B = 2, Job C = 15, Job D = 7, and Job E
= 3 ms. so, the order of processing the allocated job is A>B>C>D>E.
The total time required for data processing and filling 5 jobs is 39 milliseconds.
5
B: failure rate and success ratio
As per the given information the failure ratio and success ratio is given as:
Failure ratio= 75%
Success ratio= 25%
C: conclusion
It is concluded that adding more numbers of pages in the system using a FIFO
algorithm can impact on the level of failure rate that means it reduces the rate of failure and
increases the rate of success ratio. It is identified that adding numbers of page frames can
impact on the efficiency of the system in an effective manner.
Question 6
A: FCFS technique
As per the given information Job A = 12, Job B = 2, Job C = 15, Job D = 7, and Job E
= 3 ms. so, the order of processing the allocated job is A>B>C>D>E.
The total time required for data processing and filling 5 jobs is 39 milliseconds.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BACHELOR OF IT
6
Therefore, the turnaround time for each job is given as:
For, job A= 12 ms, job B= 15 ms, job C= 30 ms, job D= 37 ms, and job E= 40 ms.
However, the average turnaround time required is given below:
(12+15+30+37+40)/5 = 26.8 milliseconds
B: SJN technique
In this situation, the order of processing is B>E>D>A>C and complete time required
for performing five jobs is 39 milliseconds (12+2+15+7+3).
Below data shows the turnaround time of each job:
For, job B= 2 ms
Job E= 5 ms
Job D= 12 ms
Job A= 24 ms
Job C= 39 ms
Therefore, the average turnaround time required is given as:
(12+15+30+37+40)/5= 26.80 milliseconds
6
Therefore, the turnaround time for each job is given as:
For, job A= 12 ms, job B= 15 ms, job C= 30 ms, job D= 37 ms, and job E= 40 ms.
However, the average turnaround time required is given below:
(12+15+30+37+40)/5 = 26.8 milliseconds
B: SJN technique
In this situation, the order of processing is B>E>D>A>C and complete time required
for performing five jobs is 39 milliseconds (12+2+15+7+3).
Below data shows the turnaround time of each job:
For, job B= 2 ms
Job E= 5 ms
Job D= 12 ms
Job A= 24 ms
Job C= 39 ms
Therefore, the average turnaround time required is given as:
(12+15+30+37+40)/5= 26.80 milliseconds
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
BACHELOR OF IT
7
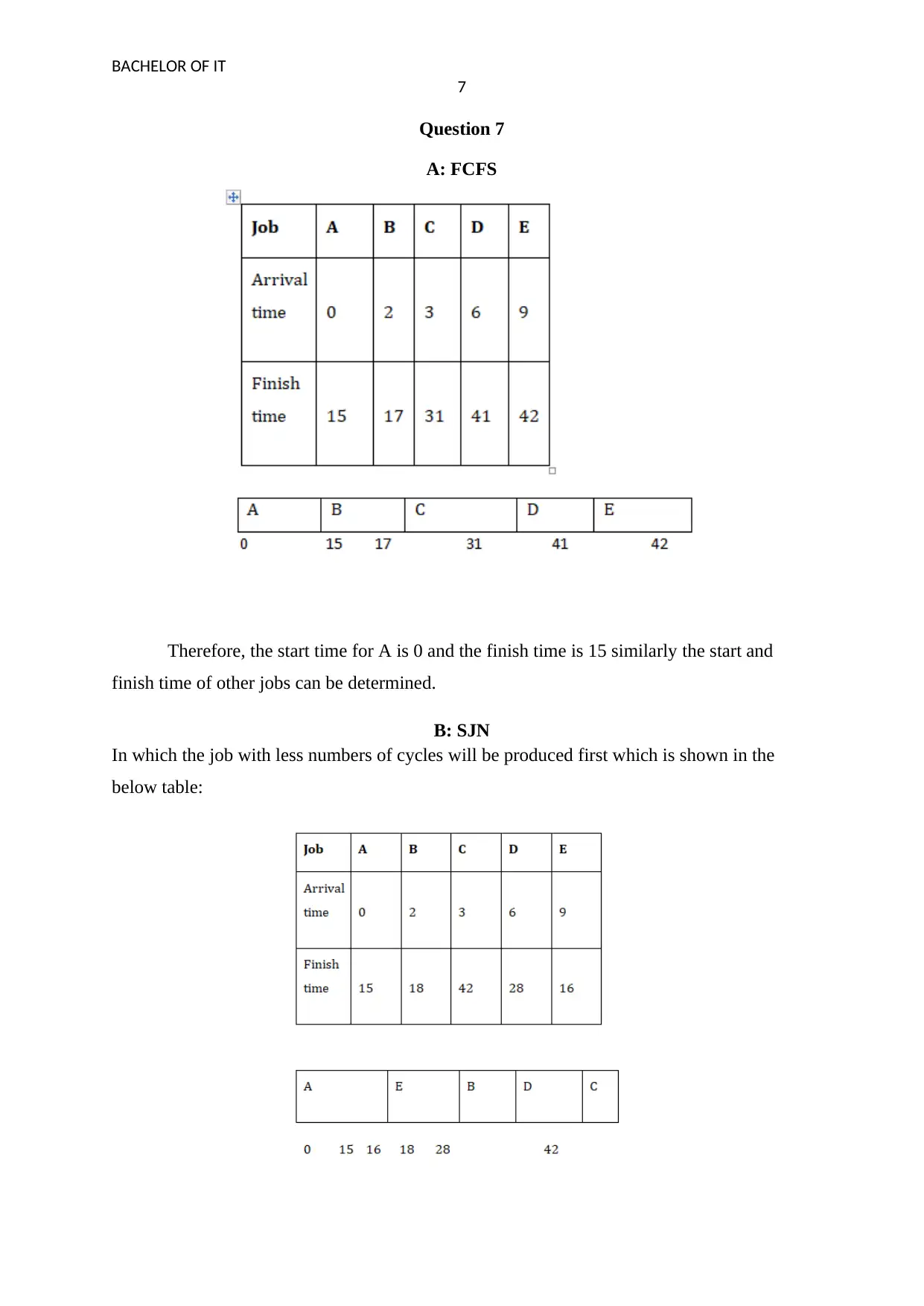
Question 7
A: FCFS
Therefore, the start time for A is 0 and the finish time is 15 similarly the start and
finish time of other jobs can be determined.
B: SJN
In which the job with less numbers of cycles will be produced first which is shown in the
below table:
7
Question 7
A: FCFS
Therefore, the start time for A is 0 and the finish time is 15 similarly the start and
finish time of other jobs can be determined.
B: SJN
In which the job with less numbers of cycles will be produced first which is shown in the
below table:

BACHELOR OF IT
8
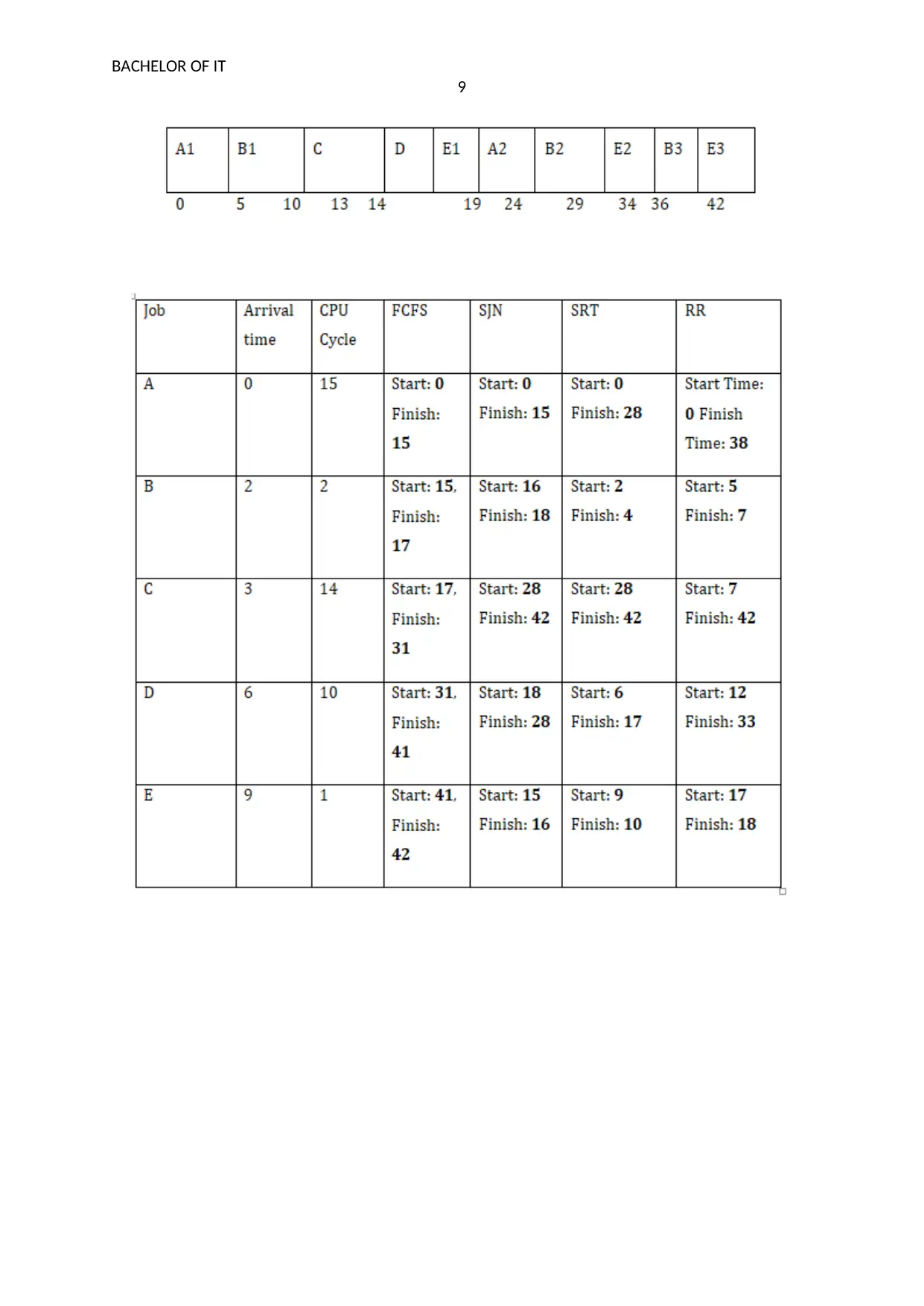
C: SRT
Such kind of approach permits the job with less time and the arrival and finish time of
all jobs are described below:
D: Round robin
In the round robin job A is started from 0 and finish at 28 seconds which is described
below in a tabular form:
8
C: SRT
Such kind of approach permits the job with less time and the arrival and finish time of
all jobs are described below:
D: Round robin
In the round robin job A is started from 0 and finish at 28 seconds which is described
below in a tabular form:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
BACHELOR OF IT
9
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BACHELOR OF IT
10
References
Pouraghily, A., Wolf, T., & Tessier, R. (2017). Hardware support for embedded operating
system security. In 2017 IEEE 28th International Conference on Application-specific
Systems, Architectures and Processors (ASAP), 12(2), 61-66
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
Stack Over Flow. (2016). Internal and external fragmentation. Retrieved from:
https://stackoverflow.com/questions/1200694/internal-and-external-fragmentation/
43870017
Tech Difference. (2016). Difference Between Internal and External fragmentation. Retrieved
from: https://techdifferences.com/difference-between-internal-and-external-
fragmentation.html
10
References
Pouraghily, A., Wolf, T., & Tessier, R. (2017). Hardware support for embedded operating
system security. In 2017 IEEE 28th International Conference on Application-specific
Systems, Architectures and Processors (ASAP), 12(2), 61-66
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
Stack Over Flow. (2016). Internal and external fragmentation. Retrieved from:
https://stackoverflow.com/questions/1200694/internal-and-external-fragmentation/
43870017
Tech Difference. (2016). Difference Between Internal and External fragmentation. Retrieved
from: https://techdifferences.com/difference-between-internal-and-external-
fragmentation.html
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




