BN104 Operating Systems Assignment: Process, File, and Device Analysis
VerifiedAdded on 2023/06/04
|15
|1866
|478
Homework Assignment
AI Summary
This document presents a comprehensive solution to an Operating Systems assignment, addressing key concepts such as process management, file management, and device management. The assignment includes detailed explanations and diagrams related to disk scheduling algorithms (FCFS, SSTF, LOOK), including arm movement diagrams and head movement calculations. It also explores deadlock conditions, providing an explanation of the four necessary conditions and a visual representation of a deadlock situation using a resource-allocation graph. Furthermore, the assignment delves into file management, discussing the 'fmt' command in Linux, complete and relative file naming conventions. Finally, the solution covers several important Linux commands, including 'chmod', 'grep', 'ls', and 'mkdir', with examples and screenshots to illustrate their usage. References are provided at the end using IEEE referencing style.

Running head: OPERATING SYSTEM
Operating System
Name of the student:
Name of the University:
Author note:
Operating System
Name of the student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
OPERATING SYSTEM
Table of Contents
B. Q1..........................................................................................................................................2
a) Arm movement diagrams...................................................................................................2
b) Head movement calculations.............................................................................................4
B.Q2...........................................................................................................................................5
a) Deadlock Conditions..........................................................................................................5
b) Deadlock Situation.............................................................................................................7
c) File Management................................................................................................................8
B. Q3..........................................................................................................................................9
a).............................................................................................................................................9
OPERATING SYSTEM
Table of Contents
B. Q1..........................................................................................................................................2
a) Arm movement diagrams...................................................................................................2
b) Head movement calculations.............................................................................................4
B.Q2...........................................................................................................................................5
a) Deadlock Conditions..........................................................................................................5
b) Deadlock Situation.............................................................................................................7
c) File Management................................................................................................................8
B. Q3..........................................................................................................................................9
a).............................................................................................................................................9

2
OPERATING SYSTEM
B. Q1.
a) Arm movement diagrams
17 34 1 26 3 12 19 61 23
FCFS Arm movement diagram
OPERATING SYSTEM
B. Q1.
a) Arm movement diagrams
17 34 1 26 3 12 19 61 23
FCFS Arm movement diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
OPERATING SYSTEM
SSTF Arm movement diagram
OPERATING SYSTEM
SSTF Arm movement diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
OPERATING SYSTEM
LOOK Arm movement diagram
b) Head movement calculations
FCFS
Total head movements:
(40-17) + (17-34) + (34-1) + (1-26) + (26-3) + (3-12) + (12-19) + (19-61) + (61-23)
= 23+17+33+25+23+9+7+42+38
= 217
Average head movements: 217/9 = 24.111
SSTF
OPERATING SYSTEM
LOOK Arm movement diagram
b) Head movement calculations
FCFS
Total head movements:
(40-17) + (17-34) + (34-1) + (1-26) + (26-3) + (3-12) + (12-19) + (19-61) + (61-23)
= 23+17+33+25+23+9+7+42+38
= 217
Average head movements: 217/9 = 24.111
SSTF

5
OPERATING SYSTEM
Total head movements
(40-34) + (34-26) + (26-23) + (23-19) + (19-17) + (17-12) + (12-3) + (3-1) + (1-61)
= 6+8+3+4+2+5+9+2+60
= 99
Average head movements: 99/9 = 11
LOOK
Total head movements
(40-61) + (61-34) + (34-26) + (26-23) + (23-19) + (19-17) + (17-12) + (12-3) + (3-1)
= 21+27+8+3+4+2+5+9+2
= 81
Average head movements: 81/9 = 9
B.Q2.
a) Deadlock Conditions
In operating systems and concurrent computing, deadlock is referred to a system
where each of the members of a group of processes are waiting for resources to be allocated,
which are already allocated to other processes [7]. These processes are in-turn waiting for
other resources. In other words a when a process enters into an ever-lasting waiting state
when their coveted resources are held by other process, deadlock occurs [4]. There are four
prime reasons that lead to a deadlock in a multiprocessing system environment. They are as
follows:
OPERATING SYSTEM
Total head movements
(40-34) + (34-26) + (26-23) + (23-19) + (19-17) + (17-12) + (12-3) + (3-1) + (1-61)
= 6+8+3+4+2+5+9+2+60
= 99
Average head movements: 99/9 = 11
LOOK
Total head movements
(40-61) + (61-34) + (34-26) + (26-23) + (23-19) + (19-17) + (17-12) + (12-3) + (3-1)
= 21+27+8+3+4+2+5+9+2
= 81
Average head movements: 81/9 = 9
B.Q2.
a) Deadlock Conditions
In operating systems and concurrent computing, deadlock is referred to a system
where each of the members of a group of processes are waiting for resources to be allocated,
which are already allocated to other processes [7]. These processes are in-turn waiting for
other resources. In other words a when a process enters into an ever-lasting waiting state
when their coveted resources are held by other process, deadlock occurs [4]. There are four
prime reasons that lead to a deadlock in a multiprocessing system environment. They are as
follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
OPERATING SYSTEM
1. Mutual exclusion: When at least one of the resources are held by a process in a non-
sharable mode. This prevents the resource to be utilized by other process while one
process is already working on it.
2. Hold and wait or resource holding: When a process is holding on to one resource and
is waiting for another resource to be allocated which in-turn is waiting for other
resources to be released.
3. No pre-emption: Only the process that is holding onto a particular resource can
voluntarily release it on completion [4].
4. Circular wait: When each of the process within a particular working frame is waiting
for another resource to be released. Generally, considering a set of waiting processes
such as P = {P1, P2,… Pn}, where P1 is waiting for the resource R1 that is held by P2.
P2 is waiting for the resource R2 that is held by P3 and so on. This continues until Pn is
waiting for the resource Rn that is primarily held by P1. This is a typical example of a
deadlock situation due to Circular wait.
In this above example, process P1 is holding R1 and waiting for resource R2
whereas P2 is holding R2 and waiting for P1 to release R1.
OPERATING SYSTEM
1. Mutual exclusion: When at least one of the resources are held by a process in a non-
sharable mode. This prevents the resource to be utilized by other process while one
process is already working on it.
2. Hold and wait or resource holding: When a process is holding on to one resource and
is waiting for another resource to be allocated which in-turn is waiting for other
resources to be released.
3. No pre-emption: Only the process that is holding onto a particular resource can
voluntarily release it on completion [4].
4. Circular wait: When each of the process within a particular working frame is waiting
for another resource to be released. Generally, considering a set of waiting processes
such as P = {P1, P2,… Pn}, where P1 is waiting for the resource R1 that is held by P2.
P2 is waiting for the resource R2 that is held by P3 and so on. This continues until Pn is
waiting for the resource Rn that is primarily held by P1. This is a typical example of a
deadlock situation due to Circular wait.
In this above example, process P1 is holding R1 and waiting for resource R2
whereas P2 is holding R2 and waiting for P1 to release R1.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
OPERATING SYSTEM
b) Deadlock Situation
The above resource-allocation graph depicts a simple deadlock situation that has been
bred up in a system with 4 processes (P-A, P-B, P-C and P-D) and 5 different resources or
devices by the identifier (D1, D2, D3, D4 and D5). In this scenario, it is clear that a deadlock
prominently exists.
Here, process P-A is waiting for device D1 whereas D1 is assigned to process P-B. P-
B is holding onto D1 and in-turn waiting for device D3 to be released by P-C that is holding
onto D2. P-B and P-D needs to two separate devices to complete their tasks. P-B is therefore
holding onto a device D5 that is being requested by P-D. P-D has one resource held and
hence it is requesting two other resources and hopes to get one of them. D3 is being requested
by P-C but it is currently assigned to P-D which is also waiting for D4 and D5 that are
allocated and held up by P-A and P-B respectively. P-B will not release D5 unless it is
allowed access to D2.
OPERATING SYSTEM
b) Deadlock Situation
The above resource-allocation graph depicts a simple deadlock situation that has been
bred up in a system with 4 processes (P-A, P-B, P-C and P-D) and 5 different resources or
devices by the identifier (D1, D2, D3, D4 and D5). In this scenario, it is clear that a deadlock
prominently exists.
Here, process P-A is waiting for device D1 whereas D1 is assigned to process P-B. P-
B is holding onto D1 and in-turn waiting for device D3 to be released by P-C that is holding
onto D2. P-B and P-D needs to two separate devices to complete their tasks. P-B is therefore
holding onto a device D5 that is being requested by P-D. P-D has one resource held and
hence it is requesting two other resources and hopes to get one of them. D3 is being requested
by P-C but it is currently assigned to P-D which is also waiting for D4 and D5 that are
allocated and held up by P-A and P-B respectively. P-B will not release D5 unless it is
allowed access to D2.

8
OPERATING SYSTEM
Therefore, as it can be seen from the above scenario, none of the process will agree on
leaving the devices or resources that they are holding onto unless they are assigned their
wanted device. This will create a deadlock in the system.
c) File Management
I) The fmt command is used in LINUX as a formatter for the process of simplifying or
optimizing the texts in a file. Files can be formatted in terms of their width or length. The
fixed length technique is to implement the command fmt itself. This will format the text in the
file such that all one characters are out in the same line. The width option is used when the
number of characters to be put per line is needed to be mentioned [6].
Syntax: fmt –w VALUE FILE_NAME
This will format the file such that the texts are broken to form new lines with VALUE
number of characters per line.
II) Complete or absolute file naming is the process of providing the entire details of the
path that leads to the file. Therefore, the naming starts at the root directory and travels into
the sub-directories unless it reaches the file to be identified. The directories are traversed in
the naming convention with the help of / symbols.
Relative file or path names are those that do not require the assistance of the complete
path value to spot a directory or file. A relative path is generally characterized by naming
convention that does not start with a /. This signifies that the file naming has been initiated
from the current directory [1].
Example:
OPERATING SYSTEM
Therefore, as it can be seen from the above scenario, none of the process will agree on
leaving the devices or resources that they are holding onto unless they are assigned their
wanted device. This will create a deadlock in the system.
c) File Management
I) The fmt command is used in LINUX as a formatter for the process of simplifying or
optimizing the texts in a file. Files can be formatted in terms of their width or length. The
fixed length technique is to implement the command fmt itself. This will format the text in the
file such that all one characters are out in the same line. The width option is used when the
number of characters to be put per line is needed to be mentioned [6].
Syntax: fmt –w VALUE FILE_NAME
This will format the file such that the texts are broken to form new lines with VALUE
number of characters per line.
II) Complete or absolute file naming is the process of providing the entire details of the
path that leads to the file. Therefore, the naming starts at the root directory and travels into
the sub-directories unless it reaches the file to be identified. The directories are traversed in
the naming convention with the help of / symbols.
Relative file or path names are those that do not require the assistance of the complete
path value to spot a directory or file. A relative path is generally characterized by naming
convention that does not start with a /. This signifies that the file naming has been initiated
from the current directory [1].
Example:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
OPERATING SYSTEM
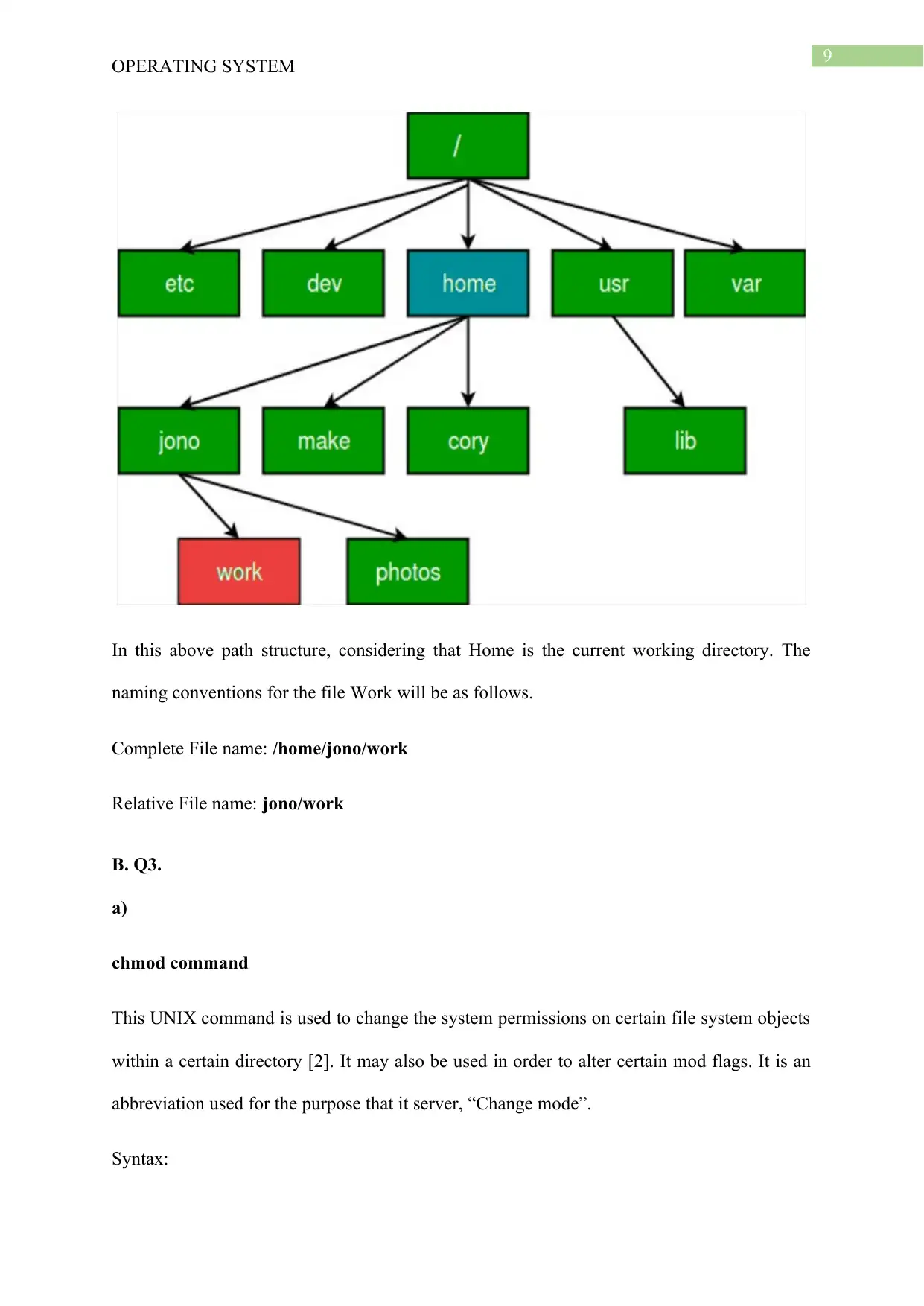
In this above path structure, considering that Home is the current working directory. The
naming conventions for the file Work will be as follows.
Complete File name: /home/jono/work
Relative File name: jono/work
B. Q3.
a)
chmod command
This UNIX command is used to change the system permissions on certain file system objects
within a certain directory [2]. It may also be used in order to alter certain mod flags. It is an
abbreviation used for the purpose that it server, “Change mode”.
Syntax:
OPERATING SYSTEM
In this above path structure, considering that Home is the current working directory. The
naming conventions for the file Work will be as follows.
Complete File name: /home/jono/work
Relative File name: jono/work
B. Q3.
a)
chmod command
This UNIX command is used to change the system permissions on certain file system objects
within a certain directory [2]. It may also be used in order to alter certain mod flags. It is an
abbreviation used for the purpose that it server, “Change mode”.
Syntax:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
OPERATING SYSTEM
chmod [Options]... Mode [,Mode]... file...
chmod [Options]... Numeric_Mode file...
4 = r (Read)
2 = w (Write)
1 = x (eXecute)
chmod [Options]... --reference=RFile file...
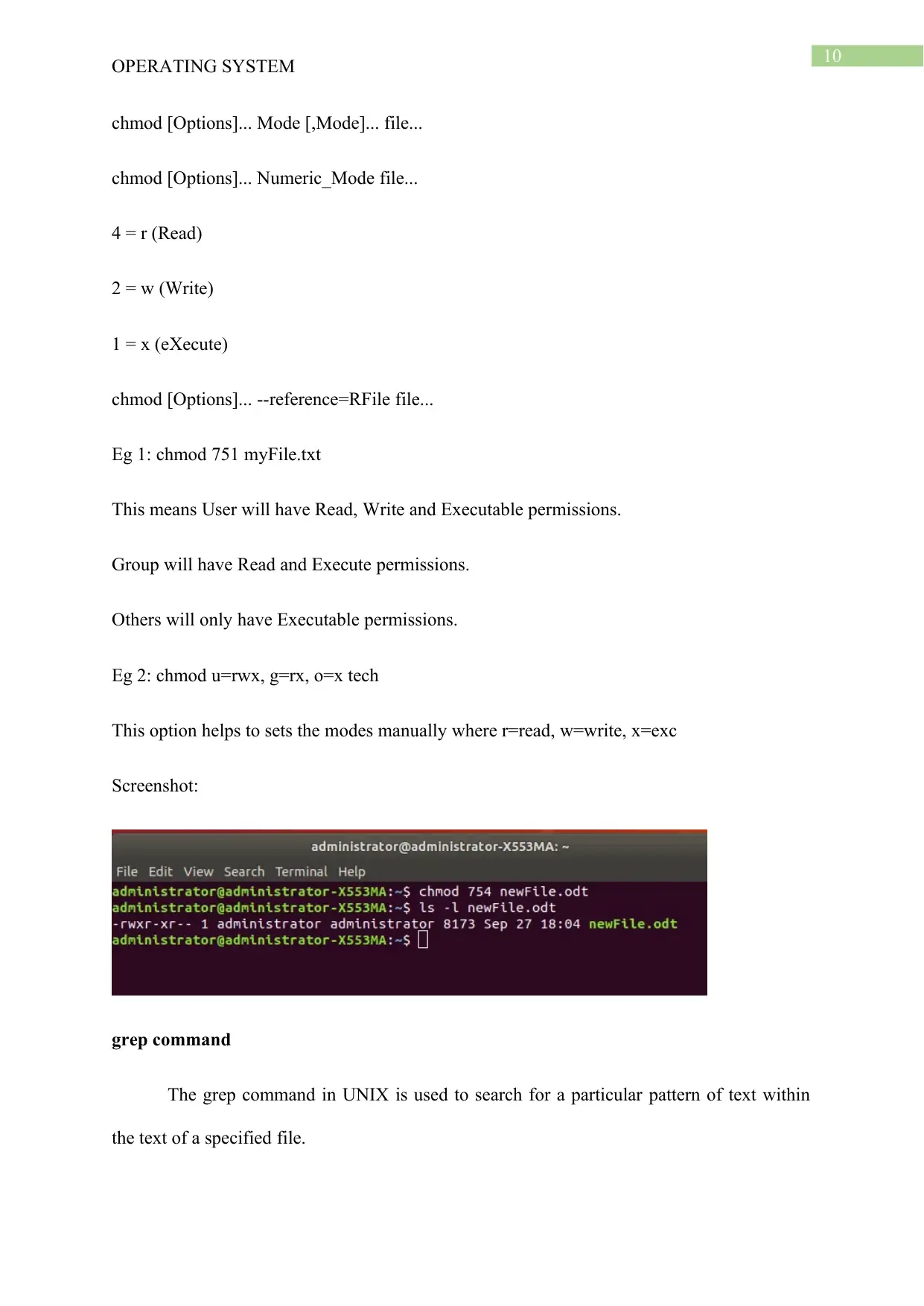
Eg 1: chmod 751 myFile.txt
This means User will have Read, Write and Executable permissions.
Group will have Read and Execute permissions.
Others will only have Executable permissions.
Eg 2: chmod u=rwx, g=rx, o=x tech
This option helps to sets the modes manually where r=read, w=write, x=exc
Screenshot:
grep command
The grep command in UNIX is used to search for a particular pattern of text within
the text of a specified file.
OPERATING SYSTEM
chmod [Options]... Mode [,Mode]... file...
chmod [Options]... Numeric_Mode file...
4 = r (Read)
2 = w (Write)
1 = x (eXecute)
chmod [Options]... --reference=RFile file...
Eg 1: chmod 751 myFile.txt
This means User will have Read, Write and Executable permissions.
Group will have Read and Execute permissions.
Others will only have Executable permissions.
Eg 2: chmod u=rwx, g=rx, o=x tech
This option helps to sets the modes manually where r=read, w=write, x=exc
Screenshot:
grep command
The grep command in UNIX is used to search for a particular pattern of text within
the text of a specified file.
11
OPERATING SYSTEM
Syntax: grep [options] patternText [file or files]
Some major Options:
-c : This prints only a count of the lines that match a pattern
-w : Match whole word
-i : Ignores, case for matching
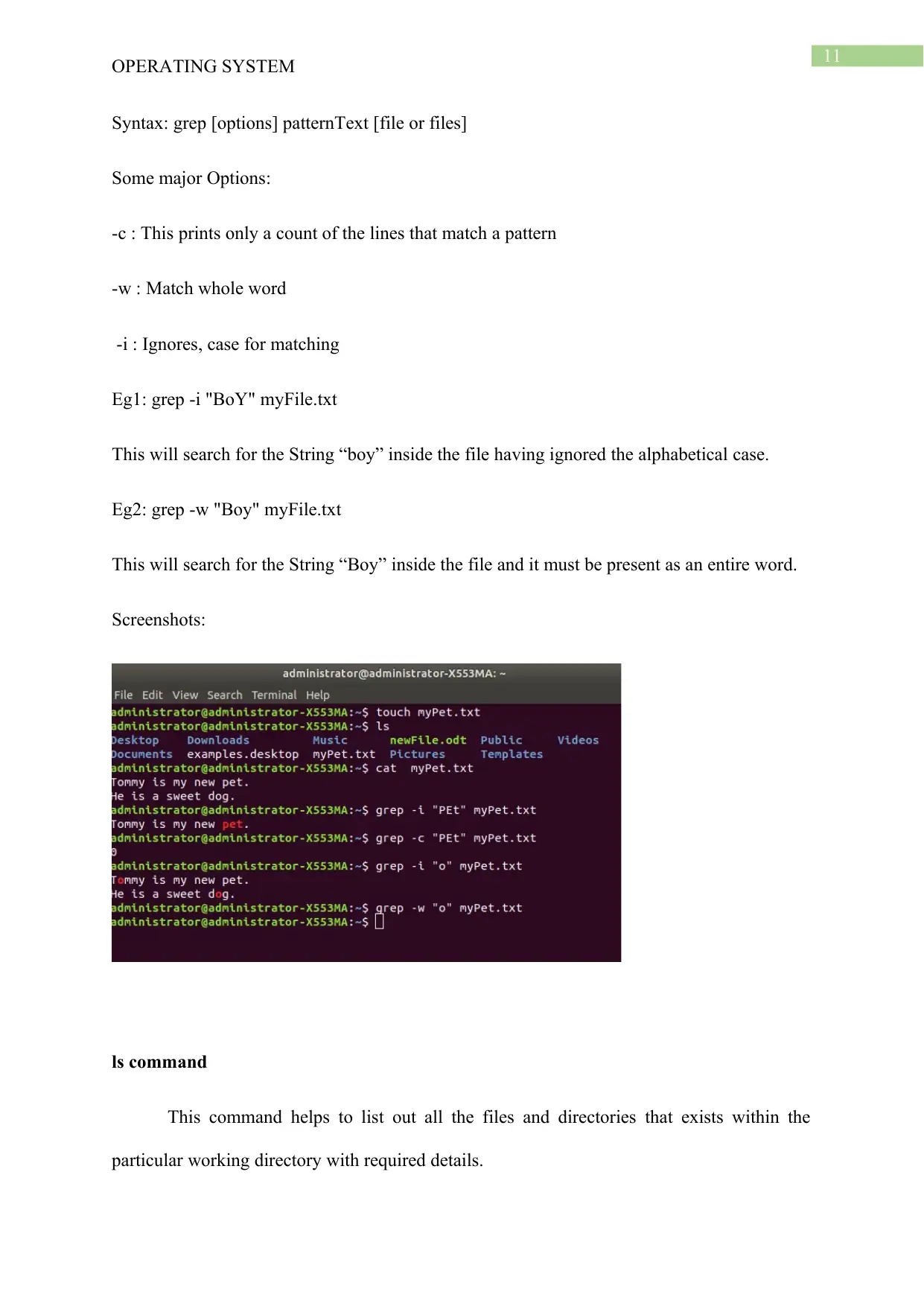
Eg1: grep -i "BoY" myFile.txt
This will search for the String “boy” inside the file having ignored the alphabetical case.
Eg2: grep -w "Boy" myFile.txt
This will search for the String “Boy” inside the file and it must be present as an entire word.
Screenshots:
ls command
This command helps to list out all the files and directories that exists within the
particular working directory with required details.
OPERATING SYSTEM
Syntax: grep [options] patternText [file or files]
Some major Options:
-c : This prints only a count of the lines that match a pattern
-w : Match whole word
-i : Ignores, case for matching
Eg1: grep -i "BoY" myFile.txt
This will search for the String “boy” inside the file having ignored the alphabetical case.
Eg2: grep -w "Boy" myFile.txt
This will search for the String “Boy” inside the file and it must be present as an entire word.
Screenshots:
ls command
This command helps to list out all the files and directories that exists within the
particular working directory with required details.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


