BN104/BN104D Operating Systems: Process, Deadlock and UNIX Commands
VerifiedAdded on 2023/06/11
|10
|1349
|124
Report
AI Summary
This report provides a comprehensive overview of key operating system concepts. It begins by examining disk scheduling algorithms like FCFS, SSTF, and LOOK, comparing their performance in terms of track traversal. The report then delves into the race condition, explaining its occurrence in critical sections and illustrating it with an example of concurrent thread access to shared data. Furthermore, it discusses deadlock, using a resource allocation graph to demonstrate its presence. File formatting techniques, including fixed-length, variable-length, relative, and complete files, are also explored. Finally, the report explains essential Linux commands such as grep, chmod, wc, and ls, detailing their syntax, options, and functionalities. Desklib provides more resources for students seeking help with similar assignments.

Running head: OPERATING SYSTEM
OPERATING SYSTEM
Name of the Student:
Name of the University:
Author Note:
OPERATING SYSTEM
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1OPERATING SYSTEM
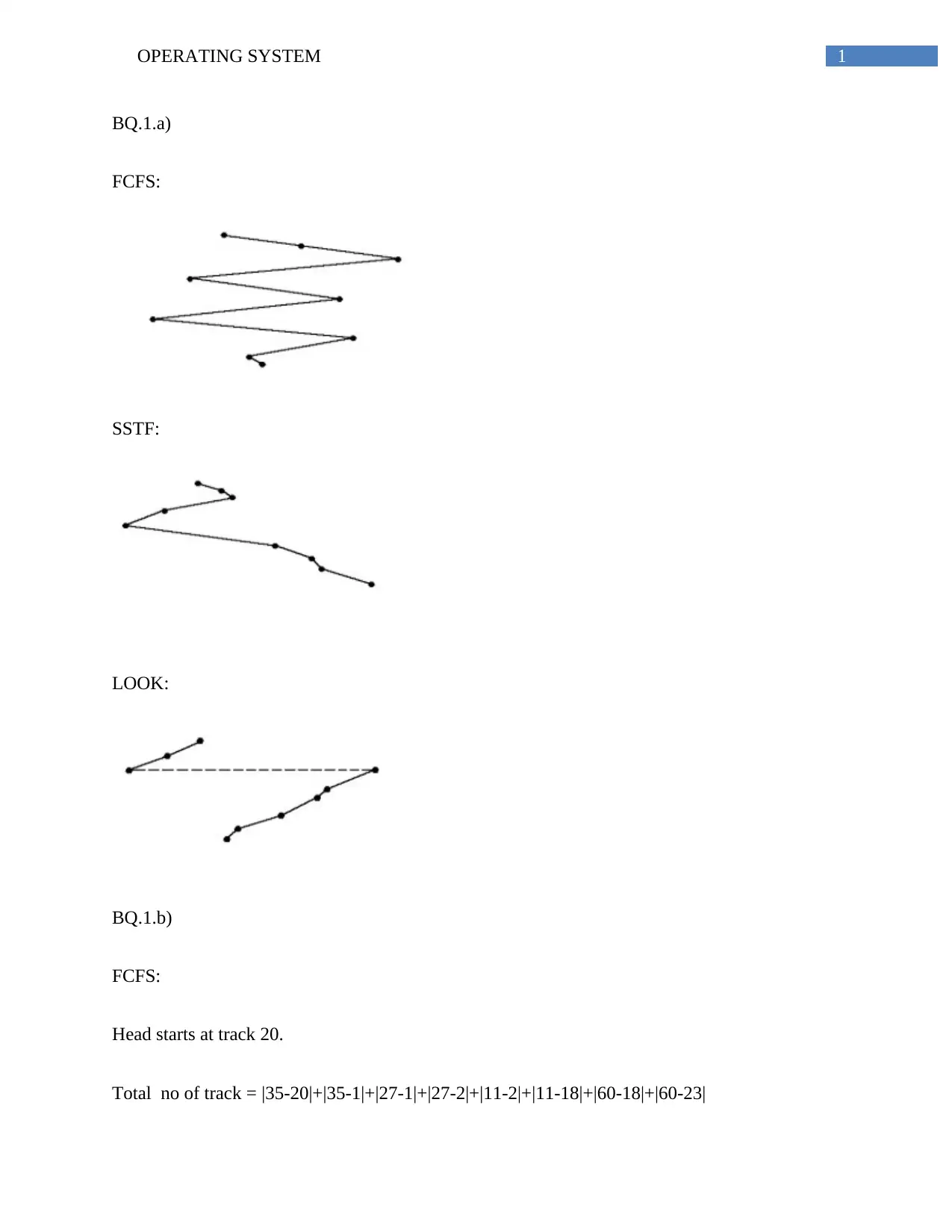
BQ.1.a)
FCFS:
SSTF:
LOOK:
BQ.1.b)
FCFS:
Head starts at track 20.
Total no of track = |35-20|+|35-1|+|27-1|+|27-2|+|11-2|+|11-18|+|60-18|+|60-23|
BQ.1.a)
FCFS:
SSTF:
LOOK:
BQ.1.b)
FCFS:
Head starts at track 20.
Total no of track = |35-20|+|35-1|+|27-1|+|27-2|+|11-2|+|11-18|+|60-18|+|60-23|

2OPERATING SYSTEM
= 195
Total no of tracks= 0-60=61
SSFT:
Total No of tracks = |20-18|+|23-18|+|27-23|+|35-27|+|35-11|+|11-2|+|2-1|+|60-1|
= 2+5+4+8+24+9+1+59
=112
Look:
Total n o of tracks= |20-18|+|18-11|+|11-2|+|2-1|+|23-1|+|23-35|+|35-60|
=2+7+9+1+22+12+25
= 78
BQ.2.a)
Race round condition:
Race round condition is the special condition happens in the critical section. The code in the
critical section can be accessed by the multiple thread [1]. The race round condition defines that
condition where two or more threads want to read or write on the shared data and the final data
depends on who runs precisely.
Example:
= 195
Total no of tracks= 0-60=61
SSFT:
Total No of tracks = |20-18|+|23-18|+|27-23|+|35-27|+|35-11|+|11-2|+|2-1|+|60-1|
= 2+5+4+8+24+9+1+59
=112
Look:
Total n o of tracks= |20-18|+|18-11|+|11-2|+|2-1|+|23-1|+|23-35|+|35-60|
=2+7+9+1+22+12+25
= 78
BQ.2.a)
Race round condition:
Race round condition is the special condition happens in the critical section. The code in the
critical section can be accessed by the multiple thread [1]. The race round condition defines that
condition where two or more threads want to read or write on the shared data and the final data
depends on who runs precisely.
Example:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3OPERATING SYSTEM
Two or more threads want to access the same shared data will lead to the happening of the race
round condition. Suppose, thread A and the thread B shared the variable which is count by 1.
Thread A increases the count of 1 while thread B decreases the count of 1 [1]. Now, if the count
value is 10, the difference operation will yield different result of the count and this can be
happened if the count is not protected using the mutual exclusion. In case if both the statements
are not protected, while thread A will execute the operation on the count A , the system may
switch to execute to the thread B. In this case the problem may arise.
BQ.2.b)
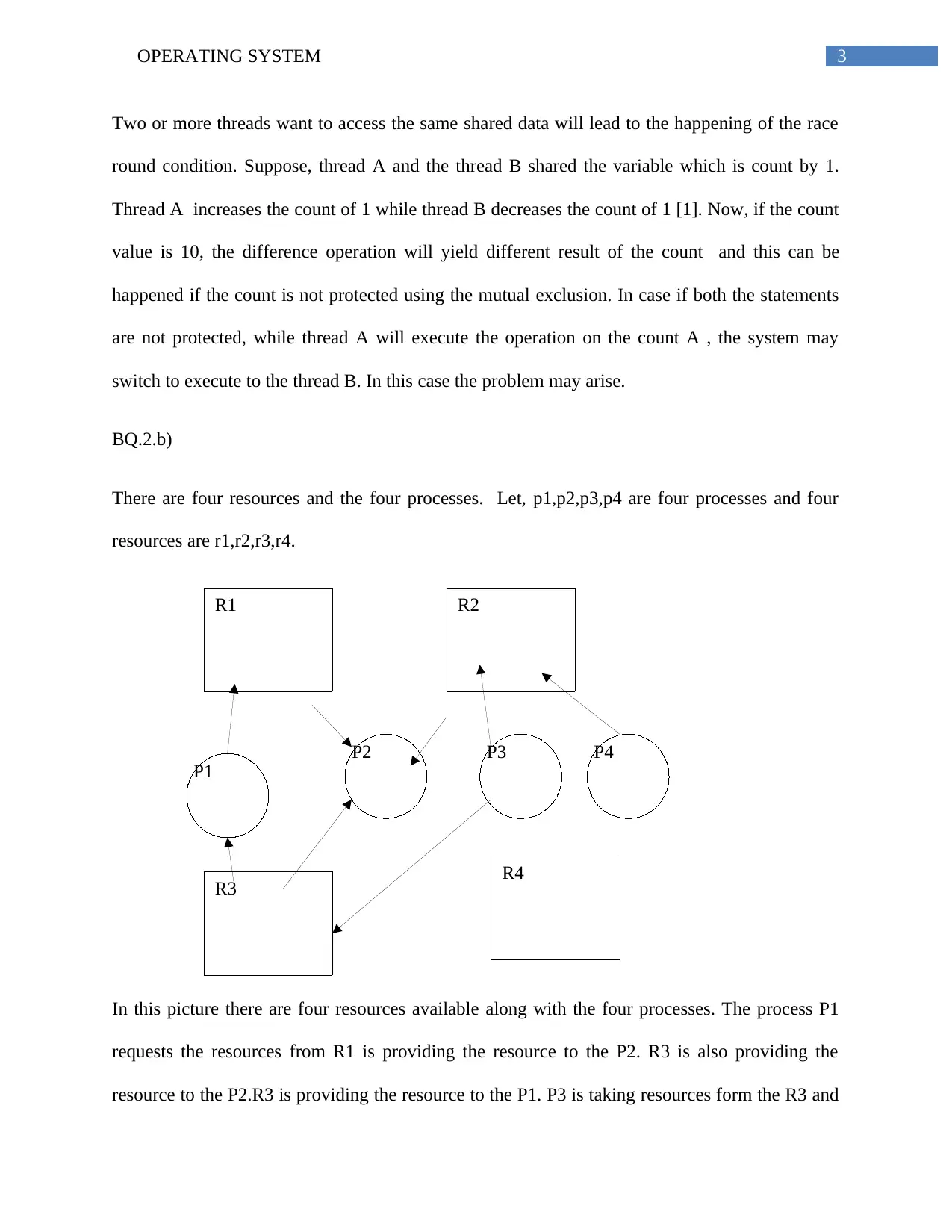
There are four resources and the four processes. Let, p1,p2,p3,p4 are four processes and four
resources are r1,r2,r3,r4.
Rr
In this picture there are four resources available along with the four processes. The process P1
requests the resources from R1 is providing the resource to the P2. R3 is also providing the
resource to the P2.R3 is providing the resource to the P1. P3 is taking resources form the R3 and
R1 R2
R3 R4
P1
P2 P3 P4
Two or more threads want to access the same shared data will lead to the happening of the race
round condition. Suppose, thread A and the thread B shared the variable which is count by 1.
Thread A increases the count of 1 while thread B decreases the count of 1 [1]. Now, if the count
value is 10, the difference operation will yield different result of the count and this can be
happened if the count is not protected using the mutual exclusion. In case if both the statements
are not protected, while thread A will execute the operation on the count A , the system may
switch to execute to the thread B. In this case the problem may arise.
BQ.2.b)
There are four resources and the four processes. Let, p1,p2,p3,p4 are four processes and four
resources are r1,r2,r3,r4.
Rr
In this picture there are four resources available along with the four processes. The process P1
requests the resources from R1 is providing the resource to the P2. R3 is also providing the
resource to the P2.R3 is providing the resource to the P1. P3 is taking resources form the R3 and
R1 R2
R3 R4
P1
P2 P3 P4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4OPERATING SYSTEM
R2. P4 is taking the resource from R2. The resource R4 is not accessed by the any process. In the
entire system the cycle is present so it can be said that the deadlock is present.
BQ.2.c)
Fixed length file formatting:
In fixed length file formatting system the text files are formatted by the specified pad characters,
left and right alignment and the column widths. In this case, each paragraph or the rows has the
one complete record. Each row can contain many pieces of the data. Within the each column the
data is padded with the spaces. The data can be aligned to left to the right. The number of
characters used in the each column has same character and the alignment.
Example:
There are 2o characters in the first column and alignment is left. The data contains in it is the
NAME.
Second column contains the 10 characters and is left aligned. It contains the information about
the STATE.
Variable length file formatting:
In case of the variable length file format, the file can use a length prefix. It mean that they
contain prefix which helps to identify the length of the record.. Each of the record contains the
length of the record. The length of the record must be in the prefix of the record and it is the 16
bit binary number which includes the prefix of the 2 byte length. The separator is used in the
variable length file formats.
R2. P4 is taking the resource from R2. The resource R4 is not accessed by the any process. In the
entire system the cycle is present so it can be said that the deadlock is present.
BQ.2.c)
Fixed length file formatting:
In fixed length file formatting system the text files are formatted by the specified pad characters,
left and right alignment and the column widths. In this case, each paragraph or the rows has the
one complete record. Each row can contain many pieces of the data. Within the each column the
data is padded with the spaces. The data can be aligned to left to the right. The number of
characters used in the each column has same character and the alignment.
Example:
There are 2o characters in the first column and alignment is left. The data contains in it is the
NAME.
Second column contains the 10 characters and is left aligned. It contains the information about
the STATE.
Variable length file formatting:
In case of the variable length file format, the file can use a length prefix. It mean that they
contain prefix which helps to identify the length of the record.. Each of the record contains the
length of the record. The length of the record must be in the prefix of the record and it is the 16
bit binary number which includes the prefix of the 2 byte length. The separator is used in the
variable length file formats.

5OPERATING SYSTEM
Example:
Type deposit_list=record
Bname: char(20)
Relative file:
The relative file name contains the relative key, which is a record number that represents the
location and the reference from where the file begins [2]. The transmission modes for in the
relative file are sequential , dynamic and random. The relative record number works in
maintaining the sequence.
Example:
The file in the first record has the relative number 1, the tenth file in the record has the record
number of 10.The length of the records can be of the fixed and the variable length.
Complete file:
The complete file is associated with the inclusion and driver letter in the Linux.
BQ.3.a)
Linux commands:
grep:
Brief introduction of the function: This command is used for the searching of the regular
expression against a text [3]. This command is used in the linux which can deals with the
Example:
Type deposit_list=record
Bname: char(20)
Relative file:
The relative file name contains the relative key, which is a record number that represents the
location and the reference from where the file begins [2]. The transmission modes for in the
relative file are sequential , dynamic and random. The relative record number works in
maintaining the sequence.
Example:
The file in the first record has the relative number 1, the tenth file in the record has the record
number of 10.The length of the records can be of the fixed and the variable length.
Complete file:
The complete file is associated with the inclusion and driver letter in the Linux.
BQ.3.a)
Linux commands:
grep:
Brief introduction of the function: This command is used for the searching of the regular
expression against a text [3]. This command is used in the linux which can deals with the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6OPERATING SYSTEM
multiple files and the stream of output. The main function of the this command is to search the
specified text in the line. There are three variations of the grep syntax- egrep,fgrep,rgrep.
The basic syntax : in a file named ‘rain’ in which it is written “It is raining. Raining makes the
day dull”.
In case if the ‘raining’ is needed to be searched.
$ grep “raining” rain
Syntax: grep “string _to_be_searched” filename
The other two options of the grep command are egrep and fgrep.
Chmod: In Linux operating system eaxh of the files ahs some set of rules, which are associated
with the access of the file [3]. These rules are called file modes.chmod operation can change the
modes of the files.
Syntax: chmod options permissions filename
Example: chmod 754 filename.
4 is equivalent to “read”
2 is equivalent to “write”
1 is equivalent to “execute”
0 is equivalent to “ no permission”
multiple files and the stream of output. The main function of the this command is to search the
specified text in the line. There are three variations of the grep syntax- egrep,fgrep,rgrep.
The basic syntax : in a file named ‘rain’ in which it is written “It is raining. Raining makes the
day dull”.
In case if the ‘raining’ is needed to be searched.
$ grep “raining” rain
Syntax: grep “string _to_be_searched” filename
The other two options of the grep command are egrep and fgrep.
Chmod: In Linux operating system eaxh of the files ahs some set of rules, which are associated
with the access of the file [3]. These rules are called file modes.chmod operation can change the
modes of the files.
Syntax: chmod options permissions filename
Example: chmod 754 filename.
4 is equivalent to “read”
2 is equivalent to “write”
1 is equivalent to “execute”
0 is equivalent to “ no permission”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7OPERATING SYSTEM
Here 7 is the combination of 4+2+1 =7 (read, write and execute)
There are some of the options available in the chmod command- they are
-c= changes
-f= quiet mode
-v= verbose mode.
Wc: wc represents the word count in the newlines [3]. The function of the wc prints the newline,
byte and the word for the each file. Wc represents the standard input.
Syntax: wc[OPTION]------[FILE]
There are various options available in the wc options-
-c,--bytes= prints the byte code
-m,--chars= print the count of the character.
-l,--lines= print the count of the newline.
Is: It shows the list of the contents in the directory.
Here 7 is the combination of 4+2+1 =7 (read, write and execute)
There are some of the options available in the chmod command- they are
-c= changes
-f= quiet mode
-v= verbose mode.
Wc: wc represents the word count in the newlines [3]. The function of the wc prints the newline,
byte and the word for the each file. Wc represents the standard input.
Syntax: wc[OPTION]------[FILE]
There are various options available in the wc options-
-c,--bytes= prints the byte code
-m,--chars= print the count of the character.
-l,--lines= print the count of the newline.
Is: It shows the list of the contents in the directory.
8OPERATING SYSTEM
Syntax: ls [option]------[File]
There are various options available for the ls. Some of them are
-a,--all= not ignoring the entries starting with .
--author= with –l, author name is needed to be printed for the each line.
-b,--escape=printing of the octal escape of the characters which are non graphic in nature.
Syntax: ls [option]------[File]
There are various options available for the ls. Some of them are
-a,--all= not ignoring the entries starting with .
--author= with –l, author name is needed to be printed for the each line.
-b,--escape=printing of the octal escape of the characters which are non graphic in nature.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9OPERATING SYSTEM
References
[1] Eslamimehr, Mahdi, and Jens Palsberg. "Race directed scheduling of concurrent
programs." In ACM SIGPLAN Notices, vol. 49, no. 8, pp. 301-314. ACM, 2014.
[2] Lee, Changman, Dongho Sim, Joo Young Hwang, and Sangyeun Cho. "F2FS: A New
File System for Flash Storage." In FAST, pp. 273-286. 2015.
[3] LaForest, Mark. "Automatic administration of UNIX commands." U.S. Patent 9,268,608,
issued February 23, 2016.
References
[1] Eslamimehr, Mahdi, and Jens Palsberg. "Race directed scheduling of concurrent
programs." In ACM SIGPLAN Notices, vol. 49, no. 8, pp. 301-314. ACM, 2014.
[2] Lee, Changman, Dongho Sim, Joo Young Hwang, and Sangyeun Cho. "F2FS: A New
File System for Flash Storage." In FAST, pp. 273-286. 2015.
[3] LaForest, Mark. "Automatic administration of UNIX commands." U.S. Patent 9,268,608,
issued February 23, 2016.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
