Overview of Network Security: Botnet Threats and Mitigation
VerifiedAdded on 2022/09/17
|12
|2233
|40
Report
AI Summary
This report provides a comprehensive overview of botnets, detailing their variations (IRC, P2P, and Hybrid), architecture, and operational methods. It explores the various threats posed by botnets, including DDoS attacks, spamming, phishing, and identity theft. The report discusses mitigation techniques and tools, such as patching systems, separating and distributing assets, and provides examples of botnet attacks like 3ve, Mirai, and Methbot. It concludes by emphasizing the significant threat botnets pose to network security and highlights the importance of proactive measures to protect against them. The report also includes references to relevant research papers and articles.

Running head: MN502 OVERVIEW OF NETWORK SECURITY
MN502 OVERVIEW OF NETWORK SECURITY
Name of the Student
Name of the University
Author Note
MN502 OVERVIEW OF NETWORK SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MN502 OVERVIEW OF NETWORK SECURITY 1
Table of Contents
Introduction:...............................................................................................................................3
Variations of Botnet:..................................................................................................................3
IRC botnet:.............................................................................................................................3
Peer to peer botnet:.................................................................................................................4
Hybrid botnet:........................................................................................................................5
Botnet architecture:....................................................................................................................5
Botnet operations and communication:......................................................................................6
Threats of botnet:.......................................................................................................................7
DDoS attack:..........................................................................................................................7
Spamming:.............................................................................................................................7
Phishing and Identity theft:....................................................................................................7
Mitigation techniques and tools:................................................................................................8
Patch systems to prevent Dos and other Exploits:.................................................................8
Separate and Distributed Assets:............................................................................................8
Botnet attacks:............................................................................................................................9
3ve - 2018...............................................................................................................................9
Mirai -2016:...........................................................................................................................9
Methbot -2016:.......................................................................................................................9
Conclusion:................................................................................................................................9
Table of Contents
Introduction:...............................................................................................................................3
Variations of Botnet:..................................................................................................................3
IRC botnet:.............................................................................................................................3
Peer to peer botnet:.................................................................................................................4
Hybrid botnet:........................................................................................................................5
Botnet architecture:....................................................................................................................5
Botnet operations and communication:......................................................................................6
Threats of botnet:.......................................................................................................................7
DDoS attack:..........................................................................................................................7
Spamming:.............................................................................................................................7
Phishing and Identity theft:....................................................................................................7
Mitigation techniques and tools:................................................................................................8
Patch systems to prevent Dos and other Exploits:.................................................................8
Separate and Distributed Assets:............................................................................................8
Botnet attacks:............................................................................................................................9
3ve - 2018...............................................................................................................................9
Mirai -2016:...........................................................................................................................9
Methbot -2016:.......................................................................................................................9
Conclusion:................................................................................................................................9

2MN502 OVERVIEW OF NETWORK SECURITY
References:...............................................................................................................................10
References:...............................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3MN502 OVERVIEW OF NETWORK SECURITY
Introduction:
A botnet is basically the collection of the devices that are connected by Internet that
can include servers, PCs, internet of things and mobile devices which are controlled and
infected though a common malware. The users can even unaware of the botnets infecting the
systems of them. The devices that are infected can be remotely controlled by cyber-criminals
and threat actors for some of the specific functions so that the malicious based operations will
be stay hidden for the users [1]. The botnets can be used commonly for sending spam emails,
engaging in clicking the fraud campaigning as well as generating malicious traffic for the
DDoS attack. The botnets impose social and economic costs on the users, network operators,
service providers as well as society as a whole. Without the having effective efforts for
mitigating them the botnets are having the potential to harm social and economic benefits of
Internet. The purpose of this paper is to discuss botnet technology, its effect, architecture and
at last the paper will provide a conclusion on the basis of entire report.
Variations of Botnet:
The botnets can be classified mainly into four type on the basis of C&C channels that
are used. They are:
i. IRC (Internet Relay Chat) botnet
ii. P2P (Peer to Peer) botnet
iii. HTTP (Hyper Text Transfer protocol) botnet
iv. Hybrid botnet.
IRC botnet:
The IRC Botnet is called as the push style model as the commands that are sent to the
botnets that are connected to the IRC channels from the botmaster. On the basis of the
Introduction:
A botnet is basically the collection of the devices that are connected by Internet that
can include servers, PCs, internet of things and mobile devices which are controlled and
infected though a common malware. The users can even unaware of the botnets infecting the
systems of them. The devices that are infected can be remotely controlled by cyber-criminals
and threat actors for some of the specific functions so that the malicious based operations will
be stay hidden for the users [1]. The botnets can be used commonly for sending spam emails,
engaging in clicking the fraud campaigning as well as generating malicious traffic for the
DDoS attack. The botnets impose social and economic costs on the users, network operators,
service providers as well as society as a whole. Without the having effective efforts for
mitigating them the botnets are having the potential to harm social and economic benefits of
Internet. The purpose of this paper is to discuss botnet technology, its effect, architecture and
at last the paper will provide a conclusion on the basis of entire report.
Variations of Botnet:
The botnets can be classified mainly into four type on the basis of C&C channels that
are used. They are:
i. IRC (Internet Relay Chat) botnet
ii. P2P (Peer to Peer) botnet
iii. HTTP (Hyper Text Transfer protocol) botnet
iv. Hybrid botnet.
IRC botnet:
The IRC Botnet is called as the push style model as the commands that are sent to the
botnets that are connected to the IRC channels from the botmaster. On the basis of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
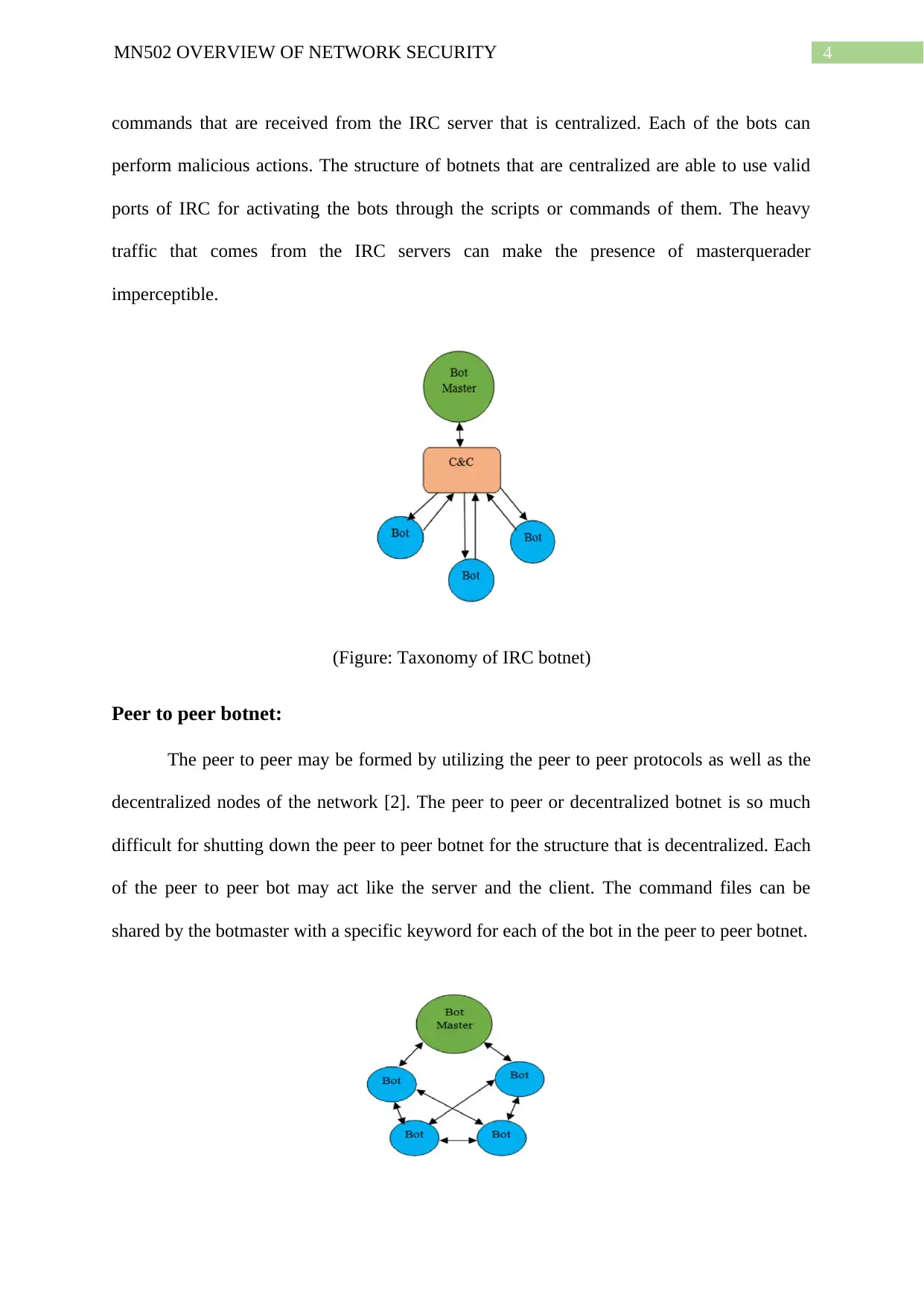
4MN502 OVERVIEW OF NETWORK SECURITY
commands that are received from the IRC server that is centralized. Each of the bots can
perform malicious actions. The structure of botnets that are centralized are able to use valid
ports of IRC for activating the bots through the scripts or commands of them. The heavy
traffic that comes from the IRC servers can make the presence of masterquerader
imperceptible.
(Figure: Taxonomy of IRC botnet)
Peer to peer botnet:
The peer to peer may be formed by utilizing the peer to peer protocols as well as the
decentralized nodes of the network [2]. The peer to peer or decentralized botnet is so much
difficult for shutting down the peer to peer botnet for the structure that is decentralized. Each
of the peer to peer bot may act like the server and the client. The command files can be
shared by the botmaster with a specific keyword for each of the bot in the peer to peer botnet.
commands that are received from the IRC server that is centralized. Each of the bots can
perform malicious actions. The structure of botnets that are centralized are able to use valid
ports of IRC for activating the bots through the scripts or commands of them. The heavy
traffic that comes from the IRC servers can make the presence of masterquerader
imperceptible.
(Figure: Taxonomy of IRC botnet)
Peer to peer botnet:
The peer to peer may be formed by utilizing the peer to peer protocols as well as the
decentralized nodes of the network [2]. The peer to peer or decentralized botnet is so much
difficult for shutting down the peer to peer botnet for the structure that is decentralized. Each
of the peer to peer bot may act like the server and the client. The command files can be
shared by the botmaster with a specific keyword for each of the bot in the peer to peer botnet.

5MN502 OVERVIEW OF NETWORK SECURITY
(Figure: Taxonomy P2P botnet)
Hybrid botnet:
The Hybrid botnet is actually a combination of two or more models of botnet like
P2P, IRC and HTTP botnets. This may follow both the decentralized or centralized
structures.
(Figure: Hybrid Botnet Structure)
Botnet architecture:
The botnets are usually having some of the features of architecture. They utilize the
protocols that are existed for the C&C communication [3]. They can be having the ability for
exploiting huge number of targets, spy for passwords, the DoS attacks, frustrate disassembly
software, defence mechanisms as well as hide themselves from the scan ports and local
systems for the vulnerabilities. The botnets are able to encrypt the C&C traffic.
(Figure: Taxonomy P2P botnet)
Hybrid botnet:
The Hybrid botnet is actually a combination of two or more models of botnet like
P2P, IRC and HTTP botnets. This may follow both the decentralized or centralized
structures.
(Figure: Hybrid Botnet Structure)
Botnet architecture:
The botnets are usually having some of the features of architecture. They utilize the
protocols that are existed for the C&C communication [3]. They can be having the ability for
exploiting huge number of targets, spy for passwords, the DoS attacks, frustrate disassembly
software, defence mechanisms as well as hide themselves from the scan ports and local
systems for the vulnerabilities. The botnets are able to encrypt the C&C traffic.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
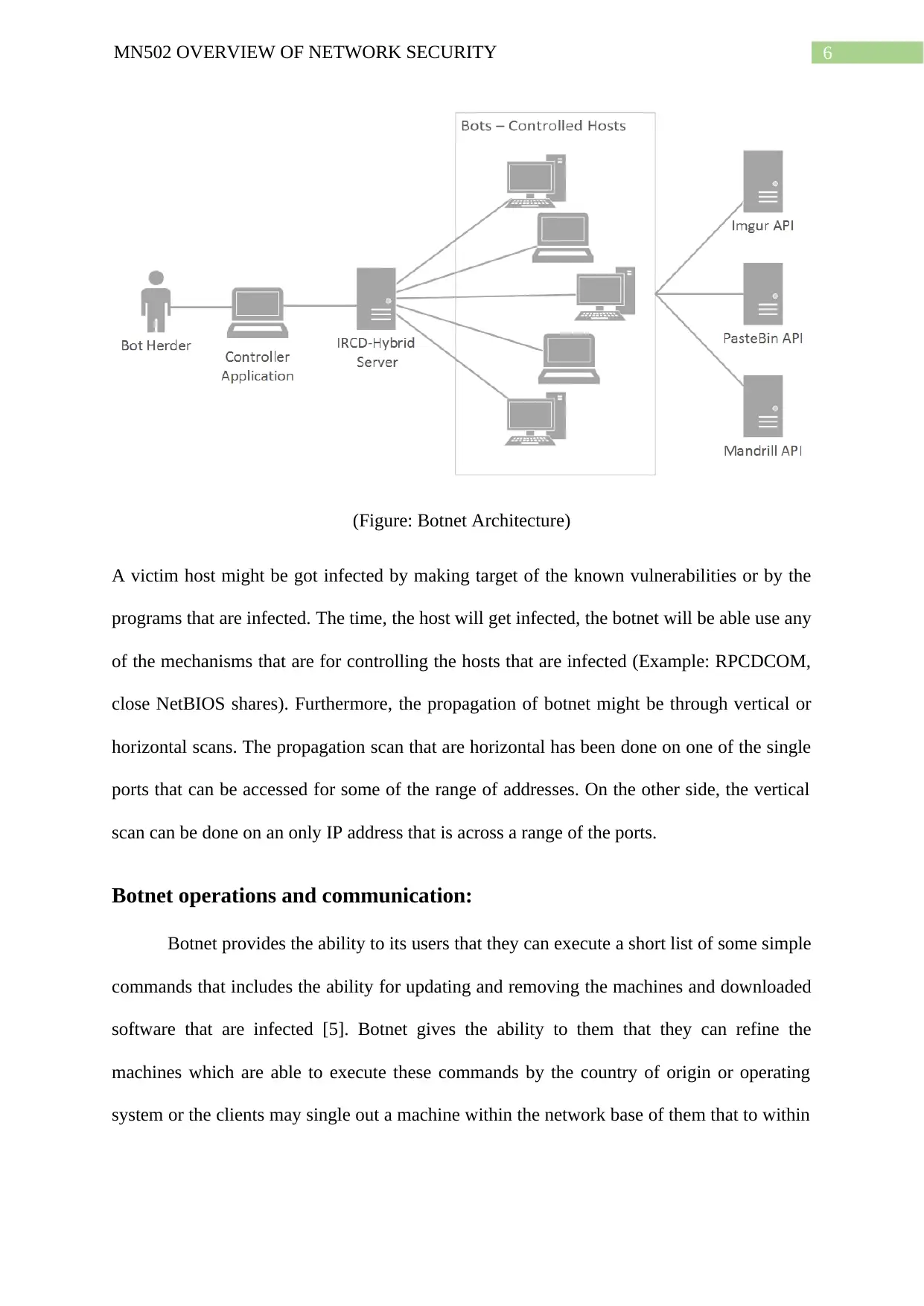
6MN502 OVERVIEW OF NETWORK SECURITY
(Figure: Botnet Architecture)
A victim host might be got infected by making target of the known vulnerabilities or by the
programs that are infected. The time, the host will get infected, the botnet will be able use any
of the mechanisms that are for controlling the hosts that are infected (Example: RPCDCOM,
close NetBIOS shares). Furthermore, the propagation of botnet might be through vertical or
horizontal scans. The propagation scan that are horizontal has been done on one of the single
ports that can be accessed for some of the range of addresses. On the other side, the vertical
scan can be done on an only IP address that is across a range of the ports.
Botnet operations and communication:
Botnet provides the ability to its users that they can execute a short list of some simple
commands that includes the ability for updating and removing the machines and downloaded
software that are infected [5]. Botnet gives the ability to them that they can refine the
machines which are able to execute these commands by the country of origin or operating
system or the clients may single out a machine within the network base of them that to within
(Figure: Botnet Architecture)
A victim host might be got infected by making target of the known vulnerabilities or by the
programs that are infected. The time, the host will get infected, the botnet will be able use any
of the mechanisms that are for controlling the hosts that are infected (Example: RPCDCOM,
close NetBIOS shares). Furthermore, the propagation of botnet might be through vertical or
horizontal scans. The propagation scan that are horizontal has been done on one of the single
ports that can be accessed for some of the range of addresses. On the other side, the vertical
scan can be done on an only IP address that is across a range of the ports.
Botnet operations and communication:
Botnet provides the ability to its users that they can execute a short list of some simple
commands that includes the ability for updating and removing the machines and downloaded
software that are infected [5]. Botnet gives the ability to them that they can refine the
machines which are able to execute these commands by the country of origin or operating
system or the clients may single out a machine within the network base of them that to within
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7MN502 OVERVIEW OF NETWORK SECURITY
a time that is given. The users are also able to customise the experience of them in botnet by
viewing the statistics of their network from the setting section.
Botnet is taking part in the illegal activities that may cause traffic in network that is
unwanted. Thus, the removal or detection of the botnets are so much important tasks. The
communication pattern is actually a sequence of the exchanged messages that are required for
a particular communication scenario. The network communication is like para mount for the
botnets.
Threats of botnet:
DDoS attack:
The DDoS attack which can cause so many services to the users and typically the
connectivity in the loss of connectivity in the network as well as services that are able to
consume bandwidth of network of the victim [4]. For launching a DDoS attack by utilizing
Botnet is having so many advantages which are including multiply of the attacks without
clear requirement of any of the IP addresses.
Spamming:
Spam is actually an email message related to the content of it that has been sent to
different recipients. A person who has involvement in the spamming is known as the
spammer. Forums, blogs and the social networking sites as well as many of the other sides
which accepts comments of visitors. Advertising in a wireless device that are undesired like
mobile devices are known as wireless spam.
Phishing and Identity theft:
Phishing is used for describing the spoof emails as well as the other tech related
deceptions to the fake receipts to give up their organisations and their personal sensitive and
a time that is given. The users are also able to customise the experience of them in botnet by
viewing the statistics of their network from the setting section.
Botnet is taking part in the illegal activities that may cause traffic in network that is
unwanted. Thus, the removal or detection of the botnets are so much important tasks. The
communication pattern is actually a sequence of the exchanged messages that are required for
a particular communication scenario. The network communication is like para mount for the
botnets.
Threats of botnet:
DDoS attack:
The DDoS attack which can cause so many services to the users and typically the
connectivity in the loss of connectivity in the network as well as services that are able to
consume bandwidth of network of the victim [4]. For launching a DDoS attack by utilizing
Botnet is having so many advantages which are including multiply of the attacks without
clear requirement of any of the IP addresses.
Spamming:
Spam is actually an email message related to the content of it that has been sent to
different recipients. A person who has involvement in the spamming is known as the
spammer. Forums, blogs and the social networking sites as well as many of the other sides
which accepts comments of visitors. Advertising in a wireless device that are undesired like
mobile devices are known as wireless spam.
Phishing and Identity theft:
Phishing is used for describing the spoof emails as well as the other tech related
deceptions to the fake receipts to give up their organisations and their personal sensitive and

8MN502 OVERVIEW OF NETWORK SECURITY
confidential information like financial account detail, social security number as well as other
security and identity information [7]. Some of the phishing mails are looking like realistic
and attractive and some of the others are constructed badly and crude. However, the major
goal of all that is to steal the information by deception.
Mitigation techniques and tools:
Stopping botnet attacks or mitigating them is a multifaceted procedure. There are
some of the aspects of mitigation which are having affect end users as well as DevOps roles
as well as a system admin. There are some existing mitigation techniques that are as follows:
Patch systems to prevent Dos and other Exploits:
It is including security patches and software updates for the routers as well as for the
other network firewalls, hardware, PCs, servers or some other workstations as well as some
other devices that are connected. The users have to change the default password as well as
they have to install the latest security patches and updates as the manufacturers have been
forbidden from using the standard passwords such as admin, password or 12345 out of the
box.
Separate and Distributed Assets:
The distributed and separate assets that are existed in the network for making them
harder for attacking [6]. Usually the security information and event management or the
system analytics system can be utilized for developing the rules that are for the filters through
giving allowance to the users to study the aspects such as signatures, payload, origin IP
addresses, HTTP headers, cookies as well as the JavaScript footprints.
confidential information like financial account detail, social security number as well as other
security and identity information [7]. Some of the phishing mails are looking like realistic
and attractive and some of the others are constructed badly and crude. However, the major
goal of all that is to steal the information by deception.
Mitigation techniques and tools:
Stopping botnet attacks or mitigating them is a multifaceted procedure. There are
some of the aspects of mitigation which are having affect end users as well as DevOps roles
as well as a system admin. There are some existing mitigation techniques that are as follows:
Patch systems to prevent Dos and other Exploits:
It is including security patches and software updates for the routers as well as for the
other network firewalls, hardware, PCs, servers or some other workstations as well as some
other devices that are connected. The users have to change the default password as well as
they have to install the latest security patches and updates as the manufacturers have been
forbidden from using the standard passwords such as admin, password or 12345 out of the
box.
Separate and Distributed Assets:
The distributed and separate assets that are existed in the network for making them
harder for attacking [6]. Usually the security information and event management or the
system analytics system can be utilized for developing the rules that are for the filters through
giving allowance to the users to study the aspects such as signatures, payload, origin IP
addresses, HTTP headers, cookies as well as the JavaScript footprints.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9MN502 OVERVIEW OF NETWORK SECURITY
Botnet attacks:
3ve - 2018
The attack was happened in the year 2018. 3ve botnet have given rise to three of the
interconnected as well as different sub operations, each of them was having the ability to
evade the investigation that to after the perpetrating advertisement fraud [9]. The attack
infected around 1.7 million of PCs as well as a large number of network servers which were
having the ability to generate fake traffic with the bots. The attack counterfeits around 5000
websites that were having 60000+ accounts.
Mirai -2016:
This attack infected the digital smart devices which were running on ARC processors
as well as turns those into the botnet. In the year, 2016 the attack was happened. The authors
launched a DDoS attack in the website of them. Over 6 million devices were infected by the
attack [8].
Methbot -2016:
This is the biggest ever malware that was a digital ad. It acquired over thousands of IP
addresses that was having US based ISps. Over 6000 domain and 250267 URLs was affected
by this attack [10].
Conclusion:
Thus, it can be concluded from the entire report that the botnet is threat to the network
security. The devices that are infected can be remotely controlled by cyber-criminals and
threat actors for some of the specific functions so that the malicious based operations will be
stay hidden for the users. the propagation of botnet might be through vertical or horizontal
scans. The propagation scan that are horizontal has been done on one of the single ports that
can be accessed for some of the range of addresses.
Botnet attacks:
3ve - 2018
The attack was happened in the year 2018. 3ve botnet have given rise to three of the
interconnected as well as different sub operations, each of them was having the ability to
evade the investigation that to after the perpetrating advertisement fraud [9]. The attack
infected around 1.7 million of PCs as well as a large number of network servers which were
having the ability to generate fake traffic with the bots. The attack counterfeits around 5000
websites that were having 60000+ accounts.
Mirai -2016:
This attack infected the digital smart devices which were running on ARC processors
as well as turns those into the botnet. In the year, 2016 the attack was happened. The authors
launched a DDoS attack in the website of them. Over 6 million devices were infected by the
attack [8].
Methbot -2016:
This is the biggest ever malware that was a digital ad. It acquired over thousands of IP
addresses that was having US based ISps. Over 6000 domain and 250267 URLs was affected
by this attack [10].
Conclusion:
Thus, it can be concluded from the entire report that the botnet is threat to the network
security. The devices that are infected can be remotely controlled by cyber-criminals and
threat actors for some of the specific functions so that the malicious based operations will be
stay hidden for the users. the propagation of botnet might be through vertical or horizontal
scans. The propagation scan that are horizontal has been done on one of the single ports that
can be accessed for some of the range of addresses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10MN502 OVERVIEW OF NETWORK SECURITY
References:
[1] Antonakakis, Manos, Tim April, Michael Bailey, Matt Bernhard, Elie Bursztein, Jaime
Cochran, Zakir Durumeric et al. "Understanding the mirai botnet." In 26th {USENIX}
Security Symposium ({USENIX} Security 17), pp. 1093-1110. 2017.
[2] Garcia, Sebastian, Martin Grill, Jan Stiborek, and Alejandro Zunino. "An empirical
comparison of botnet detection methods." computers & security 45: 100-123, 2014.
[3] Ranjan, Supranamaya. "Machine learning based botnet detection using real-time extracted
traffic features." U.S. Patent 8,682,812, issued March 25, 2014.
[4] Schiavoni, Stefano, Federico Maggi, Lorenzo Cavallaro, and Stefano Zanero. "Phoenix:
DGA-based botnet tracking and intelligence." In International Conference on Detection
of Intrusions and Malware, and Vulnerability Assessment, pp. 192-211. Springer, Cham,
2014.
[5] Abokhodair, Norah, Daisy Yoo, and David W. McDonald. "Dissecting a social botnet:
Growth, content and influence in Twitter." In Proceedings of the 18th ACM Conference
on Computer Supported Cooperative Work & Social Computing, pp. 839-851. ACM,
2015.
[6] Dainotti, Alberto, Alistair King, Kimberly Claffy, Ferdinando Papale, and Antonio
Pescapé. "Analysis of a/0 stealth scan from a botnet." IEEE/ACM Transactions on
Networking (TON)23, no. 2 : 341-354, 2015.
[7] Karim, Ahmad, Rosli Bin Salleh, Muhammad Shiraz, Syed Adeel Ali Shah, Irfan Awan,
and Nor Badrul Anuar. "Botnet detection techniques: review, future trends, and
issues." Journal of Zhejiang University SCIENCE C 15, no. 11 : 943-983, 2014.
[8] Hoque, Nazrul, Dhruba K. Bhattacharyya, and Jugal K. Kalita. "Botnet in DDoS attacks:
trends and challenges." IEEE Communications Surveys & Tutorials 17, no. 4 : 2242-
2270, 2015.
References:
[1] Antonakakis, Manos, Tim April, Michael Bailey, Matt Bernhard, Elie Bursztein, Jaime
Cochran, Zakir Durumeric et al. "Understanding the mirai botnet." In 26th {USENIX}
Security Symposium ({USENIX} Security 17), pp. 1093-1110. 2017.
[2] Garcia, Sebastian, Martin Grill, Jan Stiborek, and Alejandro Zunino. "An empirical
comparison of botnet detection methods." computers & security 45: 100-123, 2014.
[3] Ranjan, Supranamaya. "Machine learning based botnet detection using real-time extracted
traffic features." U.S. Patent 8,682,812, issued March 25, 2014.
[4] Schiavoni, Stefano, Federico Maggi, Lorenzo Cavallaro, and Stefano Zanero. "Phoenix:
DGA-based botnet tracking and intelligence." In International Conference on Detection
of Intrusions and Malware, and Vulnerability Assessment, pp. 192-211. Springer, Cham,
2014.
[5] Abokhodair, Norah, Daisy Yoo, and David W. McDonald. "Dissecting a social botnet:
Growth, content and influence in Twitter." In Proceedings of the 18th ACM Conference
on Computer Supported Cooperative Work & Social Computing, pp. 839-851. ACM,
2015.
[6] Dainotti, Alberto, Alistair King, Kimberly Claffy, Ferdinando Papale, and Antonio
Pescapé. "Analysis of a/0 stealth scan from a botnet." IEEE/ACM Transactions on
Networking (TON)23, no. 2 : 341-354, 2015.
[7] Karim, Ahmad, Rosli Bin Salleh, Muhammad Shiraz, Syed Adeel Ali Shah, Irfan Awan,
and Nor Badrul Anuar. "Botnet detection techniques: review, future trends, and
issues." Journal of Zhejiang University SCIENCE C 15, no. 11 : 943-983, 2014.
[8] Hoque, Nazrul, Dhruba K. Bhattacharyya, and Jugal K. Kalita. "Botnet in DDoS attacks:
trends and challenges." IEEE Communications Surveys & Tutorials 17, no. 4 : 2242-
2270, 2015.

11MN502 OVERVIEW OF NETWORK SECURITY
[9] García, Sebastián, Alejandro Zunino, and Marcelo Campo. "Survey on network‐based
botnet detection methods." Security and Communication Networks 7, no. 5 : 878-903,
2014.
[10] Kwon, Jonghoon, Jehyun Lee, Heejo Lee, and Adrian Perrig. "PsyBoG: A scalable
botnet detection method for large-scale DNS traffic." Computer Networks 97 : 48-73,
2016.
[9] García, Sebastián, Alejandro Zunino, and Marcelo Campo. "Survey on network‐based
botnet detection methods." Security and Communication Networks 7, no. 5 : 878-903,
2014.
[10] Kwon, Jonghoon, Jehyun Lee, Heejo Lee, and Adrian Perrig. "PsyBoG: A scalable
botnet detection method for large-scale DNS traffic." Computer Networks 97 : 48-73,
2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





