MN502 Assignment 2: Overview of Network Security in Healthcare
VerifiedAdded on 2023/02/03
|15
|1385
|20
Report
AI Summary
This report provides a comprehensive overview of network security within the healthcare industry. It begins by highlighting the increasing importance of maintaining vast amounts of patient data and the need for robust security measures. The report delves into the challenges of healthcare security, discussing the complexities of network architecture and recent technological advancements such as wireless networking, mobile monitoring, and cloud computing. It identifies the roles of key network devices like routers, switches, firewalls, and servers in establishing secure connections. The report also explores current and potential security issues, including poor funding, phishing, and the increased use of cloud computing. Furthermore, it suggests potential solutions, such as installing anti-virus software and implementing secure networking channels to mitigate threats and protect sensitive patient information. The conclusion emphasizes the critical need for proactive network security measures to safeguard patient data and maintain the integrity of healthcare operations.

Overview of network security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Healthcare care industry is rapidly growing enterprises of world so with a large healthcare
networks management they have to maintain huge amount of information. Health and human
services have to keep a huge bulk of patient records. These service providers must protect
confidentiality of data and reports.
Present study will be based on the challenges of healthcare security. Furthermore, it will
discuss network architecture and recent development of healthcare network. The study will
also provide a view about healthcare security threats and issues. This will present
methodologies for secured networks and focuses on developing skills by identifying network
based applications.
Healthcare care industry is rapidly growing enterprises of world so with a large healthcare
networks management they have to maintain huge amount of information. Health and human
services have to keep a huge bulk of patient records. These service providers must protect
confidentiality of data and reports.
Present study will be based on the challenges of healthcare security. Furthermore, it will
discuss network architecture and recent development of healthcare network. The study will
also provide a view about healthcare security threats and issues. This will present
methodologies for secured networks and focuses on developing skills by identifying network
based applications.
Health care network architecture
It can be a complex architecture where lot of medical information and patient data exists.
So to deal with this complexity, hospital management must plan a basic planning to
ease the work of maintaining large data.
This architecture is a basic overview which provides a comprehensive view about patients’
discharge and their admission and it also provides an exact number of staff members
who are attending current patients etc.
It is basically interconnection of those services which are offered to people to establish a
huge care network to quality services
It can be a complex architecture where lot of medical information and patient data exists.
So to deal with this complexity, hospital management must plan a basic planning to
ease the work of maintaining large data.
This architecture is a basic overview which provides a comprehensive view about patients’
discharge and their admission and it also provides an exact number of staff members
who are attending current patients etc.
It is basically interconnection of those services which are offered to people to establish a
huge care network to quality services
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Role of the following devices in building connections as
follows:
Routers: It is considered as a device which is used
to connect entire network to each other. This device
takes data from source to destination by adopting
the most efficient and route.
Switches: This creates a network which is
connected with server or a single network. It is
used to take data into small pieces called as
packets. Switches allow communication between
such devices which are connected in a single
network
follows:
Routers: It is considered as a device which is used
to connect entire network to each other. This device
takes data from source to destination by adopting
the most efficient and route.
Switches: This creates a network which is
connected with server or a single network. It is
used to take data into small pieces called as
packets. Switches allow communication between
such devices which are connected in a single
network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
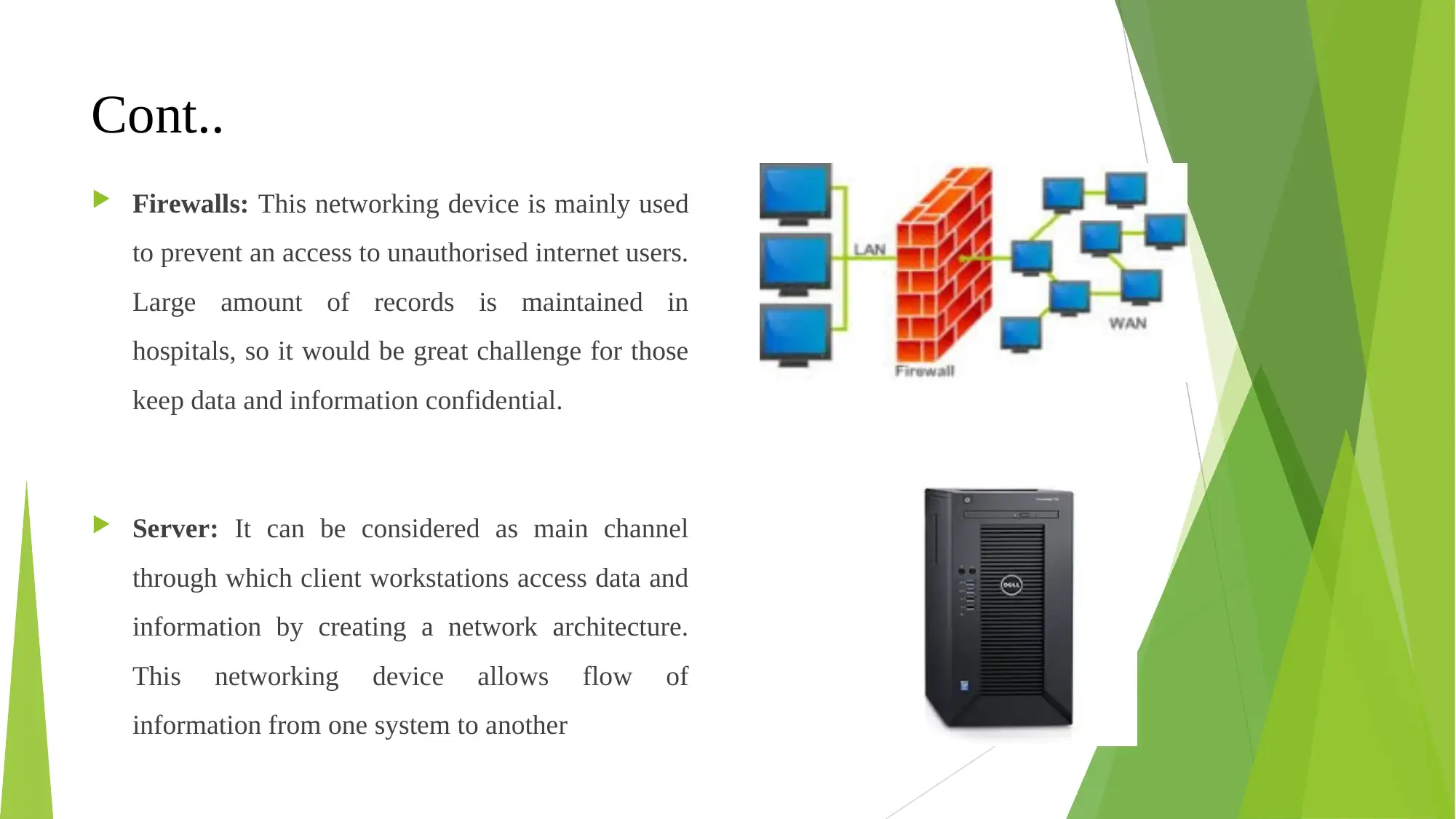
Cont..
Firewalls: This networking device is mainly used
to prevent an access to unauthorised internet users.
Large amount of records is maintained in
hospitals, so it would be great challenge for those
keep data and information confidential.
Server: It can be considered as main channel
through which client workstations access data and
information by creating a network architecture.
This networking device allows flow of
information from one system to another
Firewalls: This networking device is mainly used
to prevent an access to unauthorised internet users.
Large amount of records is maintained in
hospitals, so it would be great challenge for those
keep data and information confidential.
Server: It can be considered as main channel
through which client workstations access data and
information by creating a network architecture.
This networking device allows flow of
information from one system to another

Recent development
Recently healthcare centres have adopted an advanced mechanism and technology to
improve services. Hospitals have adopted a wireless networking technology in
monitoring their practices.
These future trends and wireless network include mobile monitoring, cloud computing
and various database secured online applications. Improvement in the machines and
infrastructure of hospital facilitates better quality services to patients which will be
resulted in individual’s improved health. Recent development has aimed at providing
quality based services [5]
Recently healthcare centres have adopted an advanced mechanism and technology to
improve services. Hospitals have adopted a wireless networking technology in
monitoring their practices.
These future trends and wireless network include mobile monitoring, cloud computing
and various database secured online applications. Improvement in the machines and
infrastructure of hospital facilitates better quality services to patients which will be
resulted in individual’s improved health. Recent development has aimed at providing
quality based services [5]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Importance of security in healthcare
Security concerns are considered as challenges for healthcare
networking system. Indeed, if these security issues are managed
properly then it would provide many opportunities for healthcare
centres.
Security of confidential data leads to proper functioning of hospitals.
Security concerns are considered as challenges for healthcare
networking system. Indeed, if these security issues are managed
properly then it would provide many opportunities for healthcare
centres.
Security of confidential data leads to proper functioning of hospitals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Some important features are as follows:
• It facilitates MRI scanners and ventilator machines for better treatment of health care.
• Potential impact of healthcare facilities has provided high quality services with
implementation of cybersecurity in healthcare enterprises.
• Timely performed audits of machinery ensures the proper functioning of hospitals.
• Network security is a prioritised task which maintains large source of data clients’
information regarding their disease, admitting and discharging formalities etc.
• It is also helpful in tracking activities of visitors.
• It will monitor practices of employees and patients inside the campus and this will also
provide orderly conduct of staff members.
• It facilitates MRI scanners and ventilator machines for better treatment of health care.
• Potential impact of healthcare facilities has provided high quality services with
implementation of cybersecurity in healthcare enterprises.
• Timely performed audits of machinery ensures the proper functioning of hospitals.
• Network security is a prioritised task which maintains large source of data clients’
information regarding their disease, admitting and discharging formalities etc.
• It is also helpful in tracking activities of visitors.
• It will monitor practices of employees and patients inside the campus and this will also
provide orderly conduct of staff members.
Three current or possible future potential security issues in healthcare networks
Healthcare and human services are improving day by day with this technological
advancement in the world. So it needs large security concerns towards the direction of
protecting health records of patients.
Poor healthcare funding affecting security- It is referred as those security concerns
which are related to poor funding capabilities.
Phishing-: It is a cybercrime practice which is concerned with virus and malware
activities
Increased use of cloud computing and online securities- It facilitates a huge database
storage application as the information is stored at the sever for its efficient use
Healthcare and human services are improving day by day with this technological
advancement in the world. So it needs large security concerns towards the direction of
protecting health records of patients.
Poor healthcare funding affecting security- It is referred as those security concerns
which are related to poor funding capabilities.
Phishing-: It is a cybercrime practice which is concerned with virus and malware
activities
Increased use of cloud computing and online securities- It facilitates a huge database
storage application as the information is stored at the sever for its efficient use
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cont..
Phishing- This type of activity occurs at the time of email attachment and texts are
considerably the biggest threat to industry. In the recent survey, Health Information
Sharing and Analysis Centre have analysed that fraudulent emails are the most
dangerous threat to healthcare industries.
Increased use of cloud computing and online securities- Cloud
computing is considered as a better way to maintain records and confidential
information. It also offers many benefits to healthcare centres such as proper use of
data and high quality services. It is also helps in reducing the cost.
26/09
/18
Phishing- This type of activity occurs at the time of email attachment and texts are
considerably the biggest threat to industry. In the recent survey, Health Information
Sharing and Analysis Centre have analysed that fraudulent emails are the most
dangerous threat to healthcare industries.
Increased use of cloud computing and online securities- Cloud
computing is considered as a better way to maintain records and confidential
information. It also offers many benefits to healthcare centres such as proper use of
data and high quality services. It is also helps in reducing the cost.
26/09
/18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Possible solution for threats
Threats are considered as those known challenges which need proper planning and
strategies to control activities. Many solutions can be applied to overcome these
networking security threats in healthcare. Hospital management have to look after the
secured database. For this they have to establish a secured networking channels and
anti-virus software so that effective data can be managed properly [8].
Threats are considered as those known challenges which need proper planning and
strategies to control activities. Many solutions can be applied to overcome these
networking security threats in healthcare. Hospital management have to look after the
secured database. For this they have to establish a secured networking channels and
anti-virus software so that effective data can be managed properly [8].

Solution are as follows :-
• Threat of phishing can be resolved by timely installation of anti-virus in computer systems.
Preventing the virus in the system can lead to secured data of the management.
• Hence, it minimises the negative impact of cybercrimes in hospitals. Absence of antivirus
application in hardware might be responsible for the harmful malicious activities thus leads
to loss of data and information.
• The software will identify threats and aware expert abut this. Furthermore, cloud computing
can be used in this. It will provide access to these applications and have secured password.
• Threat of phishing can be resolved by timely installation of anti-virus in computer systems.
Preventing the virus in the system can lead to secured data of the management.
• Hence, it minimises the negative impact of cybercrimes in hospitals. Absence of antivirus
application in hardware might be responsible for the harmful malicious activities thus leads
to loss of data and information.
• The software will identify threats and aware expert abut this. Furthermore, cloud computing
can be used in this. It will provide access to these applications and have secured password.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



