CCNA Security: Padawans LTD Network Assessment, Security Policies
VerifiedAdded on 2023/05/28
|15
|3314
|291
Report
AI Summary
This report assesses the IT network security of Padawans LTD, identifying vulnerabilities such as the use of type 7 passwords, Telnet, lack of security policies, an ANY-ANY firewall rule, unrestricted inbound and outbound traffic, and open access to routers and switches. The report recommends implementing strong passwords, replacing Telnet with SSH, developing comprehensive security policies, configuring the firewall with specific rules, restricting inbound and outbound traffic, implementing a VPN, and controlling access to network devices. It also includes suggestions for physical and network security upgrades, guidelines for VPN and RADIUS implementation, and a network diagram created in Packet Tracer with 20 workstations, 2 servers, and 1 router. The goal is to enhance Padawans LTD's overall security posture and protect sensitive company resources.

Running head: IT NETWORK DESIGNING
1
IT Network Designing
Student Name
Institutional Affiliation
1
IT Network Designing
Student Name
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT NETWORK DESIGNING 2
Executive Summary
The increasing use of technology and internet has led to the emergence of several information
security threats. Hackers and other cyber criminals are continuously looking for ways to get
access to sensitive personal and company information and thus it is critical for every internet or
network user to ensure that proper security mechanisms and measures have been put in place to
protect their data. this document will analyze Padawans LTD current practices and propose
alternative solution to ensure better security of their IT resources such as data. UMUC Security
has been hired to analyze the current security needs of Padawans LTD and provide
recommendations on the best strategies and solutions to adopt in order to solve the current issues
that the company is facing.
Executive Summary
The increasing use of technology and internet has led to the emergence of several information
security threats. Hackers and other cyber criminals are continuously looking for ways to get
access to sensitive personal and company information and thus it is critical for every internet or
network user to ensure that proper security mechanisms and measures have been put in place to
protect their data. this document will analyze Padawans LTD current practices and propose
alternative solution to ensure better security of their IT resources such as data. UMUC Security
has been hired to analyze the current security needs of Padawans LTD and provide
recommendations on the best strategies and solutions to adopt in order to solve the current issues
that the company is facing.

IT NETWORK DESIGNING 3
Table of Contents
Executive Summary.........................................................................................................................2
Introduction......................................................................................................................................4
Benefits of Strong Passwords..........................................................................................................4
Security Issues Associated with Telnet...........................................................................................6
Security Polices...............................................................................................................................8
Firewall............................................................................................................................................9
Allow Inbound 80 and 443............................................................................................................10
Outbound Traffic...........................................................................................................................10
Implementing VPN........................................................................................................................10
Access Control List........................................................................................................................11
Conclusion.....................................................................................................................................12
Network Diagram..........................................................................................................................13
References......................................................................................................................................14
Table of Contents
Executive Summary.........................................................................................................................2
Introduction......................................................................................................................................4
Benefits of Strong Passwords..........................................................................................................4
Security Issues Associated with Telnet...........................................................................................6
Security Polices...............................................................................................................................8
Firewall............................................................................................................................................9
Allow Inbound 80 and 443............................................................................................................10
Outbound Traffic...........................................................................................................................10
Implementing VPN........................................................................................................................10
Access Control List........................................................................................................................11
Conclusion.....................................................................................................................................12
Network Diagram..........................................................................................................................13
References......................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT NETWORK DESIGNING 4
Introduction
The continued adoption and usage of technology has led to the rise and growth of information
security concerns. Controlling access to digital resources have become a critical concern to any
enterprise. As such, organizations have invested heavily in ensuring that their digital resources
are safe and protected to ensure that no unauthorized access is allowed. Companies have
employed different authentication strategies and mechanisms to ensure that only validated users
are allowed to access the resources. There are several techniques that have been invented to
verify users before being granted access such as use of passwords, personal identification
numbers, biometric identification, smartcards or keycards. One limitation for some techniques
such as keycards or smartcards is that it may get stolen and if it lands into the wrong hands it
may pose great risks to the organization. As such, to address such limitations, companies have
adopted the use of two or more authentication techniques such as using PIN and biometric
authentications, or password and one-time-pin sent to their mobile phones as SMS. Employing
the use of two mechanisms to verify a user has been considered one of the most effective
authentication techniques today. UMUC Security will prepare a report that will discuss the
information security threats facing Padawans LTD because of their current technology practice
and behaviors. Some of the practices and behaviors that this document will focus on include: the
risk of using the following technologies: type 7 passwords, telnet, lack of security policies,
ANY-ANY firewall rule, allowing inbound 80 and 443, allowing everything outbound, allowing
all employees to access switches and routers, and the benefits if implementing VPN.
Benefits of Strong Passwords
Password is one of the commonly used knowledge-based authentication techniques to verify the
identity of users. The use of passwords is popular because it is the least expensive and simplest
Introduction
The continued adoption and usage of technology has led to the rise and growth of information
security concerns. Controlling access to digital resources have become a critical concern to any
enterprise. As such, organizations have invested heavily in ensuring that their digital resources
are safe and protected to ensure that no unauthorized access is allowed. Companies have
employed different authentication strategies and mechanisms to ensure that only validated users
are allowed to access the resources. There are several techniques that have been invented to
verify users before being granted access such as use of passwords, personal identification
numbers, biometric identification, smartcards or keycards. One limitation for some techniques
such as keycards or smartcards is that it may get stolen and if it lands into the wrong hands it
may pose great risks to the organization. As such, to address such limitations, companies have
adopted the use of two or more authentication techniques such as using PIN and biometric
authentications, or password and one-time-pin sent to their mobile phones as SMS. Employing
the use of two mechanisms to verify a user has been considered one of the most effective
authentication techniques today. UMUC Security will prepare a report that will discuss the
information security threats facing Padawans LTD because of their current technology practice
and behaviors. Some of the practices and behaviors that this document will focus on include: the
risk of using the following technologies: type 7 passwords, telnet, lack of security policies,
ANY-ANY firewall rule, allowing inbound 80 and 443, allowing everything outbound, allowing
all employees to access switches and routers, and the benefits if implementing VPN.
Benefits of Strong Passwords
Password is one of the commonly used knowledge-based authentication techniques to verify the
identity of users. The use of passwords is popular because it is the least expensive and simplest
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT NETWORK DESIGNING 5
authentication method. Many companies have employed the use of passwords because not does
not require any additional hardware. However, even with the benefits associated with the use of
passwords, the type and strength of passwords matters and determines how safe your information
systems are (Bauman, 2018). Padawans LTD have employed the use of type 7 passwords which
can be store in different or a number of forms. However, type 7 passwords are not strong and or
encrypted. They are just encoded using weak cipher algorithm. Additionally, type 7 passwords
setup on one device can be decoded on another device making Padawans LTD devices that use
this type of password vulnerable and at risk of being accessed by unauthorized users. There exist
several online tools that have been developed to decode type 7 passwords as such, Padawans
LTD is advice to change to another stronger and more stable type of password.
Having strong and good passwords is and effective ways to secure company or personal
information from being modified, made public, or getting stolen. The following
recommendations are suggested for the company to adopt: the company should ensure that
employees have created complex and longer passwords. This involves using a mix of characters
such as special characters, numbers, and mixing both small and capital letters. Additionally, the
users should not use personal information to create passwords. This will ensure that even if
unauthorize users get access to the device, it will be difficult for them to guess the password. Fr
instance, having a password with 8 characters will require that the hacker/ attacker has to make
more that 100 million attempts to guess the password and every time you add a character to the
password to increase the possibility by 10 (Curran, Doherty, McCann & Turkington, 2011). It
will take a hacker longer time to crack or guess a complex or long password giving time to the
company to remotely wipe the device if it supports remote access.
authentication method. Many companies have employed the use of passwords because not does
not require any additional hardware. However, even with the benefits associated with the use of
passwords, the type and strength of passwords matters and determines how safe your information
systems are (Bauman, 2018). Padawans LTD have employed the use of type 7 passwords which
can be store in different or a number of forms. However, type 7 passwords are not strong and or
encrypted. They are just encoded using weak cipher algorithm. Additionally, type 7 passwords
setup on one device can be decoded on another device making Padawans LTD devices that use
this type of password vulnerable and at risk of being accessed by unauthorized users. There exist
several online tools that have been developed to decode type 7 passwords as such, Padawans
LTD is advice to change to another stronger and more stable type of password.
Having strong and good passwords is and effective ways to secure company or personal
information from being modified, made public, or getting stolen. The following
recommendations are suggested for the company to adopt: the company should ensure that
employees have created complex and longer passwords. This involves using a mix of characters
such as special characters, numbers, and mixing both small and capital letters. Additionally, the
users should not use personal information to create passwords. This will ensure that even if
unauthorize users get access to the device, it will be difficult for them to guess the password. Fr
instance, having a password with 8 characters will require that the hacker/ attacker has to make
more that 100 million attempts to guess the password and every time you add a character to the
password to increase the possibility by 10 (Curran, Doherty, McCann & Turkington, 2011). It
will take a hacker longer time to crack or guess a complex or long password giving time to the
company to remotely wipe the device if it supports remote access.

IT NETWORK DESIGNING 6
Another way that the company can adopt is to have a coding-system that users can use to
generate password for them which is more difficult to crack since the system will generate a
password with characters that is unlikely to form any sensible word (Gray, 2018). Also, if the
passwords are being sent online, the company should ensure that it has adopted encryption
techniques for such sensitive data. However, it is important to note that even with the strongest
passwords, it is still possible to crack as such the company should employ the use of two
authentication techniques such as using password and one-time-pin sent to their mobile phone.
Additionally, it is important to have a password policy that requires employees to change their
passwords after a specific period of time.
Security Issues Associated with Telnet
Telnet has been in existence for a very long time and is one of the earliest protocols for remote
login over the internet. It is a client-server protocol that offers the users with telnet client
application as a terminal session. However, telnet does not provide ay in-built security
mechanism, it is vulnerable and faces numerous security issues and risks limiting its use in
environments with untrusted network connections (Rfwireless-world, 2018). Padawans LTD
uses telnet over the internet increasing the risk of letting unauthorize users access sensitive
company information though eavesdropping. Additionally, the connection between the server
and the client making it easy for eavesdroppers to reconstruct the data being sent over the
internet once they have access to the TCP/IP packet flow and read the data being sent including
passwords, credit card numbers, usernames, and other sensitive information that may be sent
using telnet protocol. Attackers require little skills to enable them gain access to a network using
telnet. The figure below shows a typical telnet connection between two hosts.
Another way that the company can adopt is to have a coding-system that users can use to
generate password for them which is more difficult to crack since the system will generate a
password with characters that is unlikely to form any sensible word (Gray, 2018). Also, if the
passwords are being sent online, the company should ensure that it has adopted encryption
techniques for such sensitive data. However, it is important to note that even with the strongest
passwords, it is still possible to crack as such the company should employ the use of two
authentication techniques such as using password and one-time-pin sent to their mobile phone.
Additionally, it is important to have a password policy that requires employees to change their
passwords after a specific period of time.
Security Issues Associated with Telnet
Telnet has been in existence for a very long time and is one of the earliest protocols for remote
login over the internet. It is a client-server protocol that offers the users with telnet client
application as a terminal session. However, telnet does not provide ay in-built security
mechanism, it is vulnerable and faces numerous security issues and risks limiting its use in
environments with untrusted network connections (Rfwireless-world, 2018). Padawans LTD
uses telnet over the internet increasing the risk of letting unauthorize users access sensitive
company information though eavesdropping. Additionally, the connection between the server
and the client making it easy for eavesdroppers to reconstruct the data being sent over the
internet once they have access to the TCP/IP packet flow and read the data being sent including
passwords, credit card numbers, usernames, and other sensitive information that may be sent
using telnet protocol. Attackers require little skills to enable them gain access to a network using
telnet. The figure below shows a typical telnet connection between two hosts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
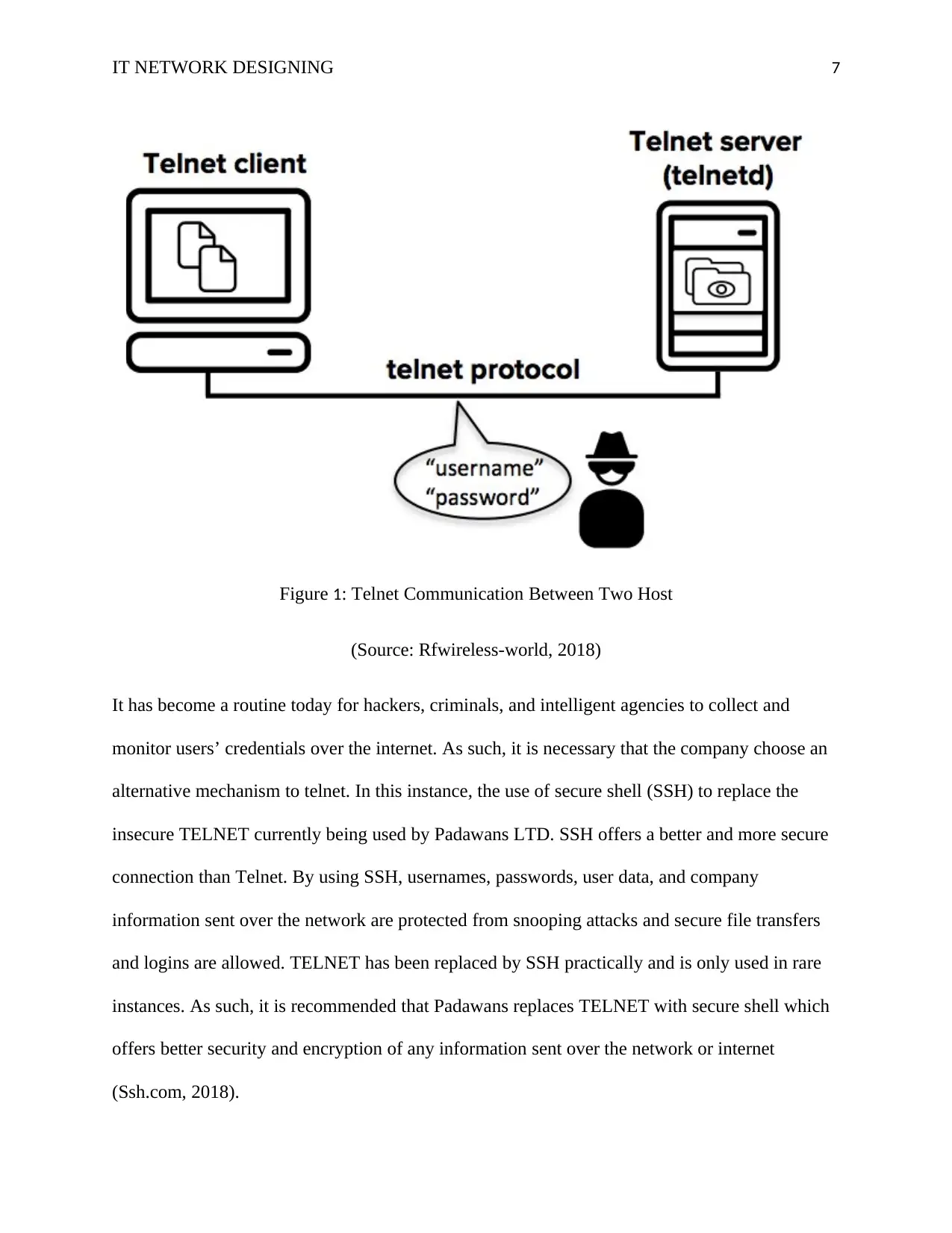
IT NETWORK DESIGNING 7
Figure 1: Telnet Communication Between Two Host
(Source: Rfwireless-world, 2018)
It has become a routine today for hackers, criminals, and intelligent agencies to collect and
monitor users’ credentials over the internet. As such, it is necessary that the company choose an
alternative mechanism to telnet. In this instance, the use of secure shell (SSH) to replace the
insecure TELNET currently being used by Padawans LTD. SSH offers a better and more secure
connection than Telnet. By using SSH, usernames, passwords, user data, and company
information sent over the network are protected from snooping attacks and secure file transfers
and logins are allowed. TELNET has been replaced by SSH practically and is only used in rare
instances. As such, it is recommended that Padawans replaces TELNET with secure shell which
offers better security and encryption of any information sent over the network or internet
(Ssh.com, 2018).
Figure 1: Telnet Communication Between Two Host
(Source: Rfwireless-world, 2018)
It has become a routine today for hackers, criminals, and intelligent agencies to collect and
monitor users’ credentials over the internet. As such, it is necessary that the company choose an
alternative mechanism to telnet. In this instance, the use of secure shell (SSH) to replace the
insecure TELNET currently being used by Padawans LTD. SSH offers a better and more secure
connection than Telnet. By using SSH, usernames, passwords, user data, and company
information sent over the network are protected from snooping attacks and secure file transfers
and logins are allowed. TELNET has been replaced by SSH practically and is only used in rare
instances. As such, it is recommended that Padawans replaces TELNET with secure shell which
offers better security and encryption of any information sent over the network or internet
(Ssh.com, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT NETWORK DESIGNING 8
Security Polices
Information security policies are very crucial to any company because it protects intellectual
property and critical and sensitive company resources by defining and outlining the
responsibilities of the employees in safeguarding company information. The risk of losing,
leaking or modifying information by employees is increased because Padawans do not have
security policies in place. As such, employees can do anything with the information they have
with them because they have not been given guidelines on how to protect and use company data.
Therefore, it is recommended that the company develop security policies. This is because
security policies are critical in supporting the mission and vision of the company (Deutsch,
2018). When coming up with security policies it is important to ensure that they meet the needs
of the company in achieving the vision and mission.
The security policies should be written because they are crucial to the company as it defines the
responsibility and the role of each employee in ensuring security. Security policies creates a
secure culture’ within the company. The policies the company implements and the details each
policy contains will determine how the company will grow (Dunham, 2018). The company
should define security policies that addresses both information and physical security issues
because it forms the basis for assessing the security requirements of the company. The following
security policies should be considered by Padawans LTD adoption (Lee & Kim, 2017):
Internet Usage
Social and email networking
Key control
Mobile device/PDA security
Visitor management
Security Polices
Information security policies are very crucial to any company because it protects intellectual
property and critical and sensitive company resources by defining and outlining the
responsibilities of the employees in safeguarding company information. The risk of losing,
leaking or modifying information by employees is increased because Padawans do not have
security policies in place. As such, employees can do anything with the information they have
with them because they have not been given guidelines on how to protect and use company data.
Therefore, it is recommended that the company develop security policies. This is because
security policies are critical in supporting the mission and vision of the company (Deutsch,
2018). When coming up with security policies it is important to ensure that they meet the needs
of the company in achieving the vision and mission.
The security policies should be written because they are crucial to the company as it defines the
responsibility and the role of each employee in ensuring security. Security policies creates a
secure culture’ within the company. The policies the company implements and the details each
policy contains will determine how the company will grow (Dunham, 2018). The company
should define security policies that addresses both information and physical security issues
because it forms the basis for assessing the security requirements of the company. The following
security policies should be considered by Padawans LTD adoption (Lee & Kim, 2017):
Internet Usage
Social and email networking
Key control
Mobile device/PDA security
Visitor management

IT NETWORK DESIGNING 9
Non-disclosure agreement
Firewall
Firewalls are very important in securing company network from malicious traffic and
applications that is transmitted over the network. However, what dictates the reliability of the
firewall are the rules that have been configured on the firewall. Padawans LTD have
implemented ANY-to-Any rule on their firewall and this rule has several limitations and security
issues. Any-any rule allows traffic from any source to any destination. With regards to network
security, this is the worst access control rule because it contradicts the principle of least privilege
and concept of denying traffic by default (Myo, 2015). Also, this rule allows traffic to company’s
web server from any source, allows access to RDP from any source, and allows access to my
SQL from any source. By allowing access to the critical company resources such as database,
webserver, and any traffic from any source, the company faces numerous security threats such as
SQL injection, malware infection, packet sniffing among other threats (Sophos, 2018). As such,
the company should ensure that it has employed the best firewall configuration practices and
completely do away with ANY-Any rule. The following are some of the best practices that are
recommended for Padawans LTD when configuring the firewall:
Block by default
Only allow specific traffic
Specify source IP addresses
Specify the destination IP address
Specify destination port
Non-disclosure agreement
Firewall
Firewalls are very important in securing company network from malicious traffic and
applications that is transmitted over the network. However, what dictates the reliability of the
firewall are the rules that have been configured on the firewall. Padawans LTD have
implemented ANY-to-Any rule on their firewall and this rule has several limitations and security
issues. Any-any rule allows traffic from any source to any destination. With regards to network
security, this is the worst access control rule because it contradicts the principle of least privilege
and concept of denying traffic by default (Myo, 2015). Also, this rule allows traffic to company’s
web server from any source, allows access to RDP from any source, and allows access to my
SQL from any source. By allowing access to the critical company resources such as database,
webserver, and any traffic from any source, the company faces numerous security threats such as
SQL injection, malware infection, packet sniffing among other threats (Sophos, 2018). As such,
the company should ensure that it has employed the best firewall configuration practices and
completely do away with ANY-Any rule. The following are some of the best practices that are
recommended for Padawans LTD when configuring the firewall:
Block by default
Only allow specific traffic
Specify source IP addresses
Specify the destination IP address
Specify destination port
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT NETWORK DESIGNING 10
Allow Inbound 80 and 443
Generally, port 443 and 80 are associated with the internet. Port 80/HTTP is associated with
world wide web (WWW) while port 443/HTTPS is the HTTP protocol over SSL/TLS. Allowing
inbound on port 80/443 poses significant threats to the company network. These ports being
open and is associated with web and internet traffic is rarely monitored. These opens up the
company to attacks such as browser-based attacks. As such, is the company wants to continue
allowing inbound traffic from these ports, it should ensure that they are monitored and the traffic
is filtered and analyzed for any malicious traffic or potential security attacks.
Outbound Traffic
Allowing all outbound traffic means that the company does not require any future rule
definitions. The cost of managing perimeter security will be reduced because there is no need to
specify any outbound rules. However, the company may save a lot of money but also increases
the security threats. By allowing everything outbound the company is likely to face distributed
denial of service attacks (DDoS). Secondly, employees with bad intentions or accidentally move
proprietary information outside the company network because of uncontrolled file transfers or
email communication. As such, the company needs to restrict outbound traffic just like it restricts
inbound traffic to ensure that unwanted outbound traffic filtered (Edwards, 2018). This can be
achieved by adding different traffic filters in the overall network security arsenal.
Implementing VPN
A virtual private network (VPN) is very important to any company or users using public network
because it brings an additional security layer. VPN enable users to protect any information sent
across different networks which may be vulnerable if it is just sent over public network
infrastructure. Padawans LTD needs to implement a VPN especially if the company have
Allow Inbound 80 and 443
Generally, port 443 and 80 are associated with the internet. Port 80/HTTP is associated with
world wide web (WWW) while port 443/HTTPS is the HTTP protocol over SSL/TLS. Allowing
inbound on port 80/443 poses significant threats to the company network. These ports being
open and is associated with web and internet traffic is rarely monitored. These opens up the
company to attacks such as browser-based attacks. As such, is the company wants to continue
allowing inbound traffic from these ports, it should ensure that they are monitored and the traffic
is filtered and analyzed for any malicious traffic or potential security attacks.
Outbound Traffic
Allowing all outbound traffic means that the company does not require any future rule
definitions. The cost of managing perimeter security will be reduced because there is no need to
specify any outbound rules. However, the company may save a lot of money but also increases
the security threats. By allowing everything outbound the company is likely to face distributed
denial of service attacks (DDoS). Secondly, employees with bad intentions or accidentally move
proprietary information outside the company network because of uncontrolled file transfers or
email communication. As such, the company needs to restrict outbound traffic just like it restricts
inbound traffic to ensure that unwanted outbound traffic filtered (Edwards, 2018). This can be
achieved by adding different traffic filters in the overall network security arsenal.
Implementing VPN
A virtual private network (VPN) is very important to any company or users using public network
because it brings an additional security layer. VPN enable users to protect any information sent
across different networks which may be vulnerable if it is just sent over public network
infrastructure. Padawans LTD needs to implement a VPN especially if the company have
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT NETWORK DESIGNING 11
employees who may need to access company information while working remotely because it
improves network security and safeguards sensitive information. Some of the benefits of using
VPN include (Bourque, 2018):
Improved security
Mobility- allows employees to work remotely and access company network securely
It is more affordable as compared to physical private network
However, the company should look out for specific features when choosing an effective VPN.
These features include:
Scalability
Reliability
Server location (incase the company chooses external VPN provider)
Therefore, it is recommended that Padawans LTD implement a VPN because it ensures data
security as much as it does not provide failsafe security. Additionally, it helps in preventing any
loss of data in the future proving to be a valuable investment for Padawans (Mitchell, 2018).
Access Control List
Access control list (ACL) is a very essential security mechanisms because it offers mapping
between services, groups, a user, and a set of permissions. Padawans requires an ACL that will
grant group members, users, and service members access to resources that are protected (Setapa
& Suhilah, 2014). ACL is made up of entries and each entry specifies groups, services, and users
with a list of permission that are given to those groups, services, and users. It is recommended
that default ACLs must not be deleted or modified. When creating an ACL ensure that you have
an open connection.
employees who may need to access company information while working remotely because it
improves network security and safeguards sensitive information. Some of the benefits of using
VPN include (Bourque, 2018):
Improved security
Mobility- allows employees to work remotely and access company network securely
It is more affordable as compared to physical private network
However, the company should look out for specific features when choosing an effective VPN.
These features include:
Scalability
Reliability
Server location (incase the company chooses external VPN provider)
Therefore, it is recommended that Padawans LTD implement a VPN because it ensures data
security as much as it does not provide failsafe security. Additionally, it helps in preventing any
loss of data in the future proving to be a valuable investment for Padawans (Mitchell, 2018).
Access Control List
Access control list (ACL) is a very essential security mechanisms because it offers mapping
between services, groups, a user, and a set of permissions. Padawans requires an ACL that will
grant group members, users, and service members access to resources that are protected (Setapa
& Suhilah, 2014). ACL is made up of entries and each entry specifies groups, services, and users
with a list of permission that are given to those groups, services, and users. It is recommended
that default ACLs must not be deleted or modified. When creating an ACL ensure that you have
an open connection.
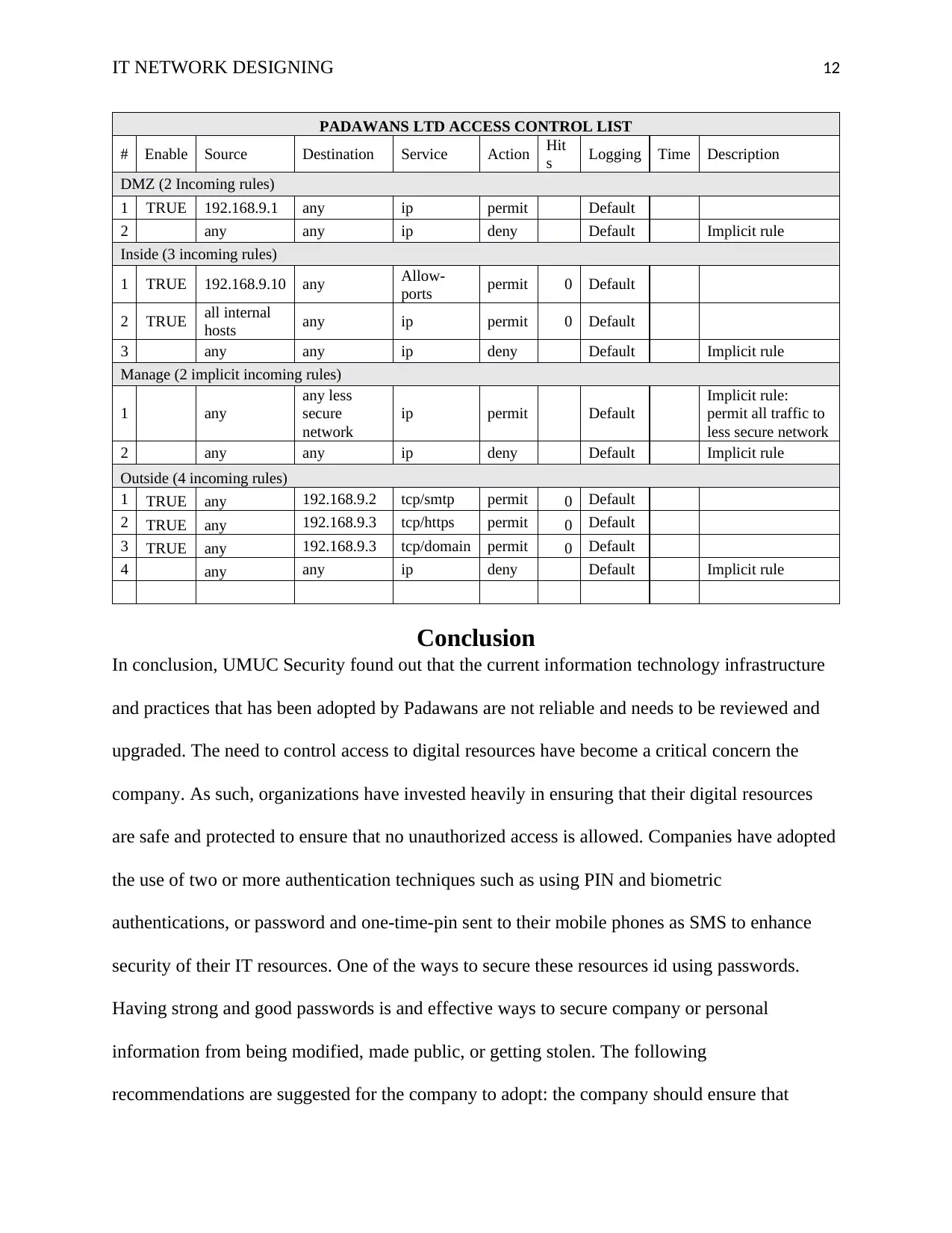
IT NETWORK DESIGNING 12
PADAWANS LTD ACCESS CONTROL LIST
# Enable Source Destination Service Action Hit
s Logging Time Description
DMZ (2 Incoming rules)
1 TRUE 192.168.9.1 any ip permit Default
2 any any ip deny Default Implicit rule
Inside (3 incoming rules)
1 TRUE 192.168.9.10 any Allow-
ports permit 0 Default
2 TRUE all internal
hosts any ip permit 0 Default
3 any any ip deny Default Implicit rule
Manage (2 implicit incoming rules)
1 any
any less
secure
network
ip permit Default
Implicit rule:
permit all traffic to
less secure network
2 any any ip deny Default Implicit rule
Outside (4 incoming rules)
1 TRUE any 192.168.9.2 tcp/smtp permit 0 Default
2 TRUE any 192.168.9.3 tcp/https permit 0 Default
3 TRUE any 192.168.9.3 tcp/domain permit 0 Default
4 any any ip deny Default Implicit rule
Conclusion
In conclusion, UMUC Security found out that the current information technology infrastructure
and practices that has been adopted by Padawans are not reliable and needs to be reviewed and
upgraded. The need to control access to digital resources have become a critical concern the
company. As such, organizations have invested heavily in ensuring that their digital resources
are safe and protected to ensure that no unauthorized access is allowed. Companies have adopted
the use of two or more authentication techniques such as using PIN and biometric
authentications, or password and one-time-pin sent to their mobile phones as SMS to enhance
security of their IT resources. One of the ways to secure these resources id using passwords.
Having strong and good passwords is and effective ways to secure company or personal
information from being modified, made public, or getting stolen. The following
recommendations are suggested for the company to adopt: the company should ensure that
PADAWANS LTD ACCESS CONTROL LIST
# Enable Source Destination Service Action Hit
s Logging Time Description
DMZ (2 Incoming rules)
1 TRUE 192.168.9.1 any ip permit Default
2 any any ip deny Default Implicit rule
Inside (3 incoming rules)
1 TRUE 192.168.9.10 any Allow-
ports permit 0 Default
2 TRUE all internal
hosts any ip permit 0 Default
3 any any ip deny Default Implicit rule
Manage (2 implicit incoming rules)
1 any
any less
secure
network
ip permit Default
Implicit rule:
permit all traffic to
less secure network
2 any any ip deny Default Implicit rule
Outside (4 incoming rules)
1 TRUE any 192.168.9.2 tcp/smtp permit 0 Default
2 TRUE any 192.168.9.3 tcp/https permit 0 Default
3 TRUE any 192.168.9.3 tcp/domain permit 0 Default
4 any any ip deny Default Implicit rule
Conclusion
In conclusion, UMUC Security found out that the current information technology infrastructure
and practices that has been adopted by Padawans are not reliable and needs to be reviewed and
upgraded. The need to control access to digital resources have become a critical concern the
company. As such, organizations have invested heavily in ensuring that their digital resources
are safe and protected to ensure that no unauthorized access is allowed. Companies have adopted
the use of two or more authentication techniques such as using PIN and biometric
authentications, or password and one-time-pin sent to their mobile phones as SMS to enhance
security of their IT resources. One of the ways to secure these resources id using passwords.
Having strong and good passwords is and effective ways to secure company or personal
information from being modified, made public, or getting stolen. The following
recommendations are suggested for the company to adopt: the company should ensure that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





