MN623 Cyber Security and Analytics: Password Cracking Tools Analysis
VerifiedAdded on 2022/09/16
|13
|1457
|17
Report
AI Summary
This report provides an overview of password cracking tools, focusing on John the Ripper and RainbowCrack. It details the functionalities, comparisons, and practical applications of these tools in cybersecurity. The report explains how John the Ripper is used for cracking Linux passwords through dictionary attacks and SSH keys, while also demonstrating RainbowCrack's hash-breaking capabilities. A comparative analysis highlights the ease of use and features of each tool, along with discussions on penetration testing, including anonymous FTP authentication, directory traversal, and cross-site scripting vulnerabilities. The report concludes by emphasizing the inherent risks of password cracking and methods to prevent successful attacks, offering insights for both users and administrators. References are provided for further reading.

1
Password cracking tools
Student’s Name:
Institution Affiliation:
Password cracking tools
Student’s Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Introduction
John the Ripper is the most widely known and used around the world since it is a free tool to
carry out cyber security tasks. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers around the
world. There are likewise a few distinctive "network constructs" that are overseen by the network
and contain an assortment of additional highlights. John the Ripper has three remaining tasks at
hand:
Producing hashed passwords of several users
Producing passwords of several users
Comparing the real passwords and the cracked hash of the password[1]
Rainbow Crack is the second most used cracking password tool after John the Ripper according
to[3]. Capacity of this product is to break hash. The direct method to split hash is animal power.
In savage power approach, all competitor plaintexts and comparing hashes are figured
individually. The registered hashes are contrasted and the objective hash. On the off chance that
one of them coordinates, the plaintext is found. Generally the procedure proceeds until wrap up
all competitor plain texts[2].
In time-memory tradeoff approach, the errand of hash registering is done progress of time with
the outcomes put away in documents called "rainbow table". From that point forward, hashes can
be turned upward from the rainbow tables at whatever point required. The pre-calculation
procedure needs a few times the exertion of full key space animal power. In any case, when the
Introduction
John the Ripper is the most widely known and used around the world since it is a free tool to
carry out cyber security tasks. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers around the
world. There are likewise a few distinctive "network constructs" that are overseen by the network
and contain an assortment of additional highlights. John the Ripper has three remaining tasks at
hand:
Producing hashed passwords of several users
Producing passwords of several users
Comparing the real passwords and the cracked hash of the password[1]
Rainbow Crack is the second most used cracking password tool after John the Ripper according
to[3]. Capacity of this product is to break hash. The direct method to split hash is animal power.
In savage power approach, all competitor plaintexts and comparing hashes are figured
individually. The registered hashes are contrasted and the objective hash. On the off chance that
one of them coordinates, the plaintext is found. Generally the procedure proceeds until wrap up
all competitor plain texts[2].
In time-memory tradeoff approach, the errand of hash registering is done progress of time with
the outcomes put away in documents called "rainbow table". From that point forward, hashes can
be turned upward from the rainbow tables at whatever point required. The pre-calculation
procedure needs a few times the exertion of full key space animal power. In any case, when the

3
one time pre-calculation is finished, the table query execution can be hundreds or multiple times
quicker than beast power[3].
Outline
JTR. JTR is the most widely known and used around the world since it is a free tool to
carry out cyber security tasks. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers
around the world.
Rainbowcrack. Rainbow Crack is the second most used cracking password tool after
John the Ripper according to[3]. Capacity of this product is to break hash. The direct
method to split hash is animal power. In savage power approach, all competitor plaintexts
and comparing hashes are figured individually.
Comparison between John the Ripper and Rainbowcrack. John the Ripper is much easier
to use as compared to Rainbowcrack.
Secret key splitting is an undeniable danger. There are various strategies that can be
utilized in an assault that have been depicted. Approaches to forestall effective assaults
by programmers for use by the two clients and chairmen have been examined. A usage of
two hashing calculations was created to be tried for proficiency and their outcomes have
been accounted for[5].
Demonstration
John the ripper
Executing John the ripper
one time pre-calculation is finished, the table query execution can be hundreds or multiple times
quicker than beast power[3].
Outline
JTR. JTR is the most widely known and used around the world since it is a free tool to
carry out cyber security tasks. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers
around the world.
Rainbowcrack. Rainbow Crack is the second most used cracking password tool after
John the Ripper according to[3]. Capacity of this product is to break hash. The direct
method to split hash is animal power. In savage power approach, all competitor plaintexts
and comparing hashes are figured individually.
Comparison between John the Ripper and Rainbowcrack. John the Ripper is much easier
to use as compared to Rainbowcrack.
Secret key splitting is an undeniable danger. There are various strategies that can be
utilized in an assault that have been depicted. Approaches to forestall effective assaults
by programmers for use by the two clients and chairmen have been examined. A usage of
two hashing calculations was created to be tried for proficiency and their outcomes have
been accounted for[5].
Demonstration
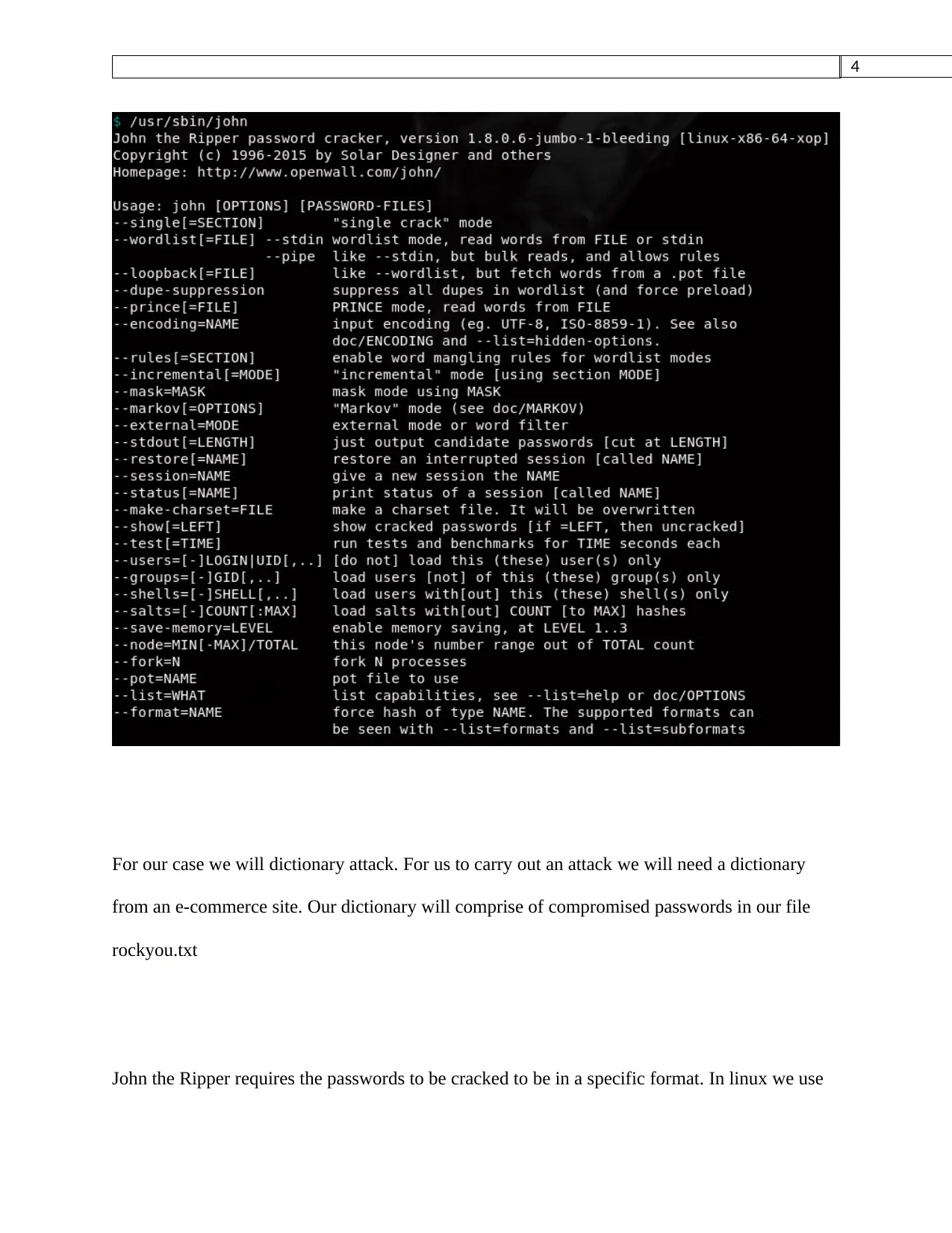
John the ripper
Executing John the ripper
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
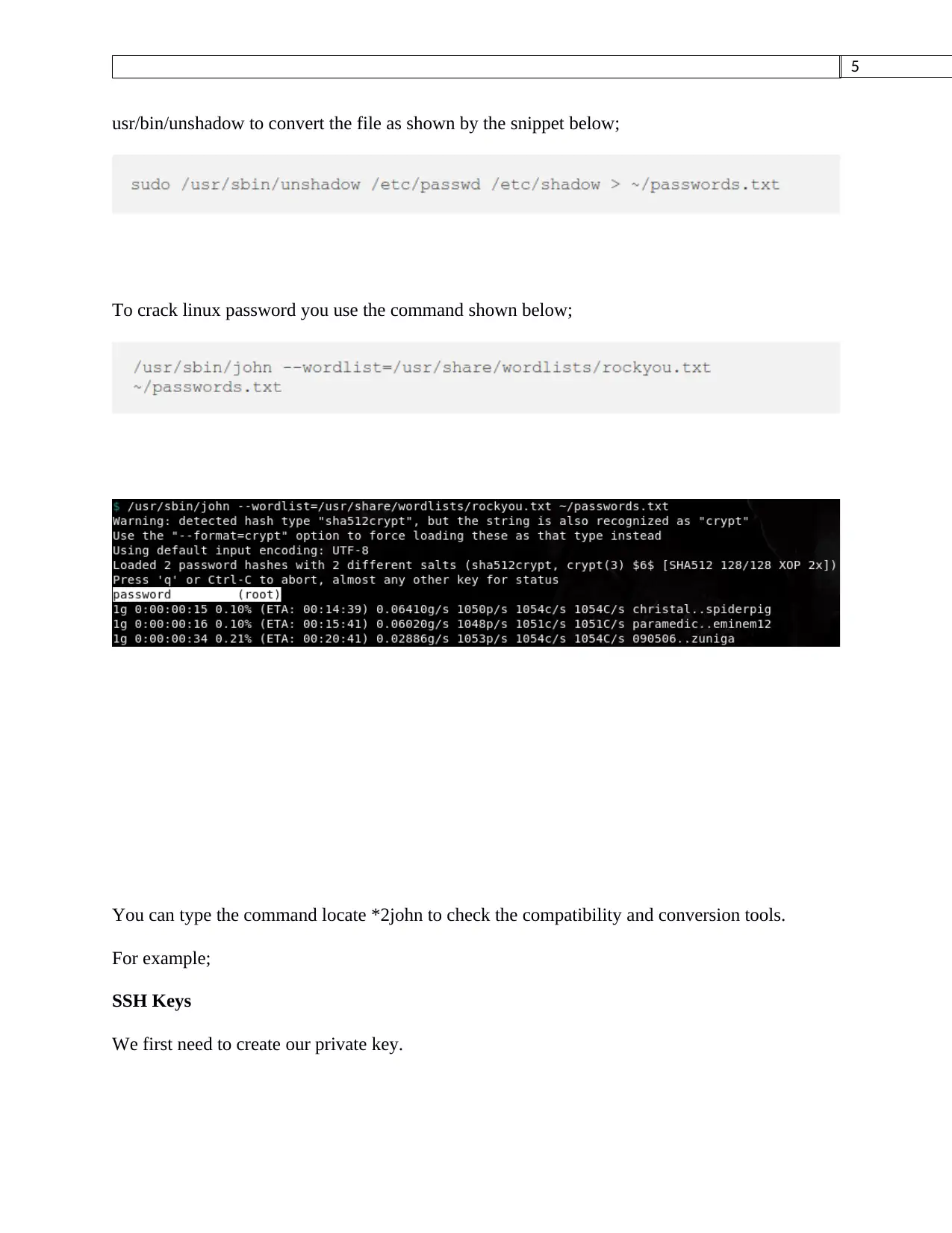
For our case we will dictionary attack. For us to carry out an attack we will need a dictionary
from an e-commerce site. Our dictionary will comprise of compromised passwords in our file
rockyou.txt
John the Ripper requires the passwords to be cracked to be in a specific format. In linux we use
For our case we will dictionary attack. For us to carry out an attack we will need a dictionary
from an e-commerce site. Our dictionary will comprise of compromised passwords in our file
rockyou.txt
John the Ripper requires the passwords to be cracked to be in a specific format. In linux we use
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
usr/bin/unshadow to convert the file as shown by the snippet below;
To crack linux password you use the command shown below;
You can type the command locate *2john to check the compatibility and conversion tools.
For example;
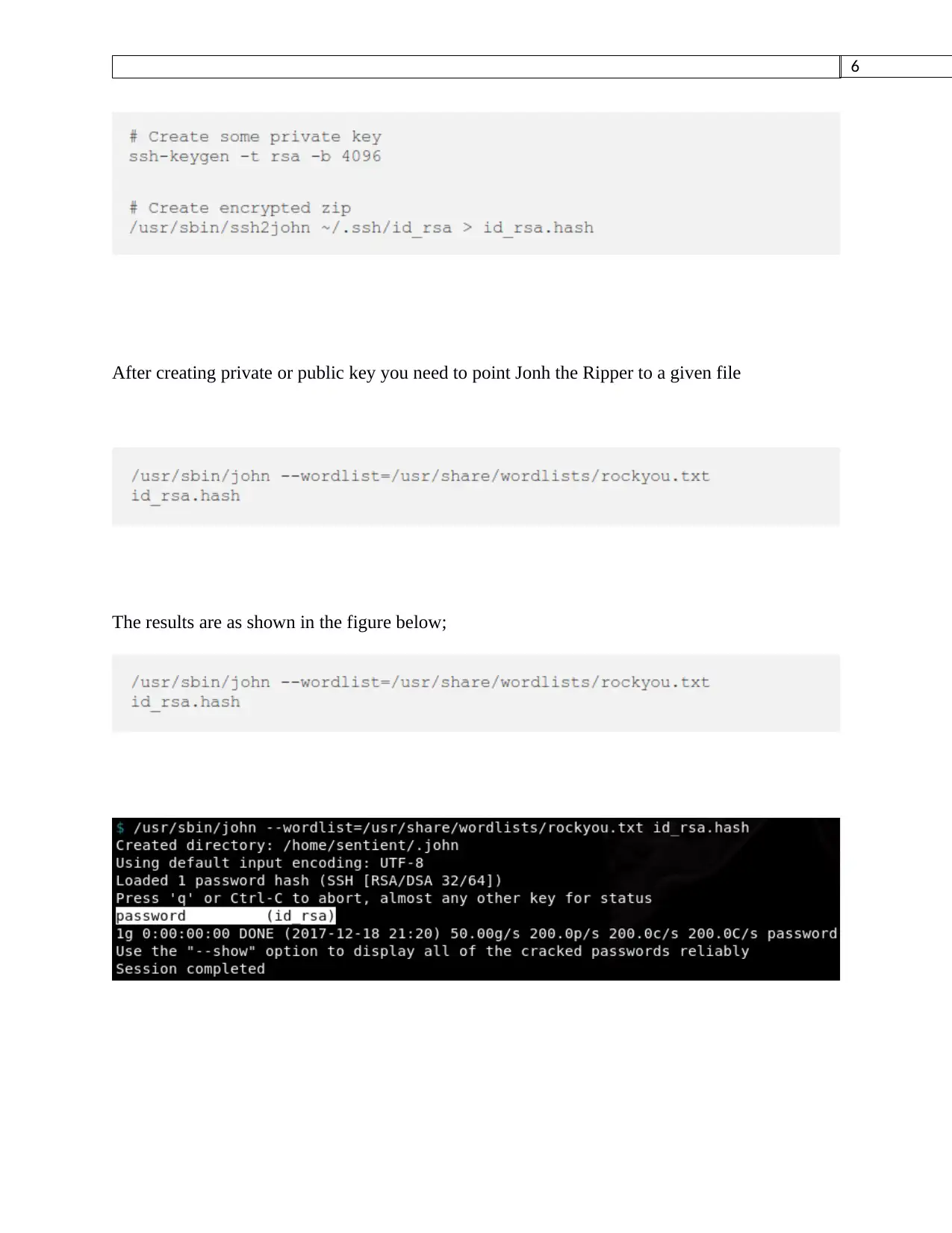
SSH Keys
We first need to create our private key.
usr/bin/unshadow to convert the file as shown by the snippet below;
To crack linux password you use the command shown below;
You can type the command locate *2john to check the compatibility and conversion tools.
For example;
SSH Keys
We first need to create our private key.
6
After creating private or public key you need to point Jonh the Ripper to a given file
The results are as shown in the figure below;
After creating private or public key you need to point Jonh the Ripper to a given file
The results are as shown in the figure below;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
Rainbowcrack
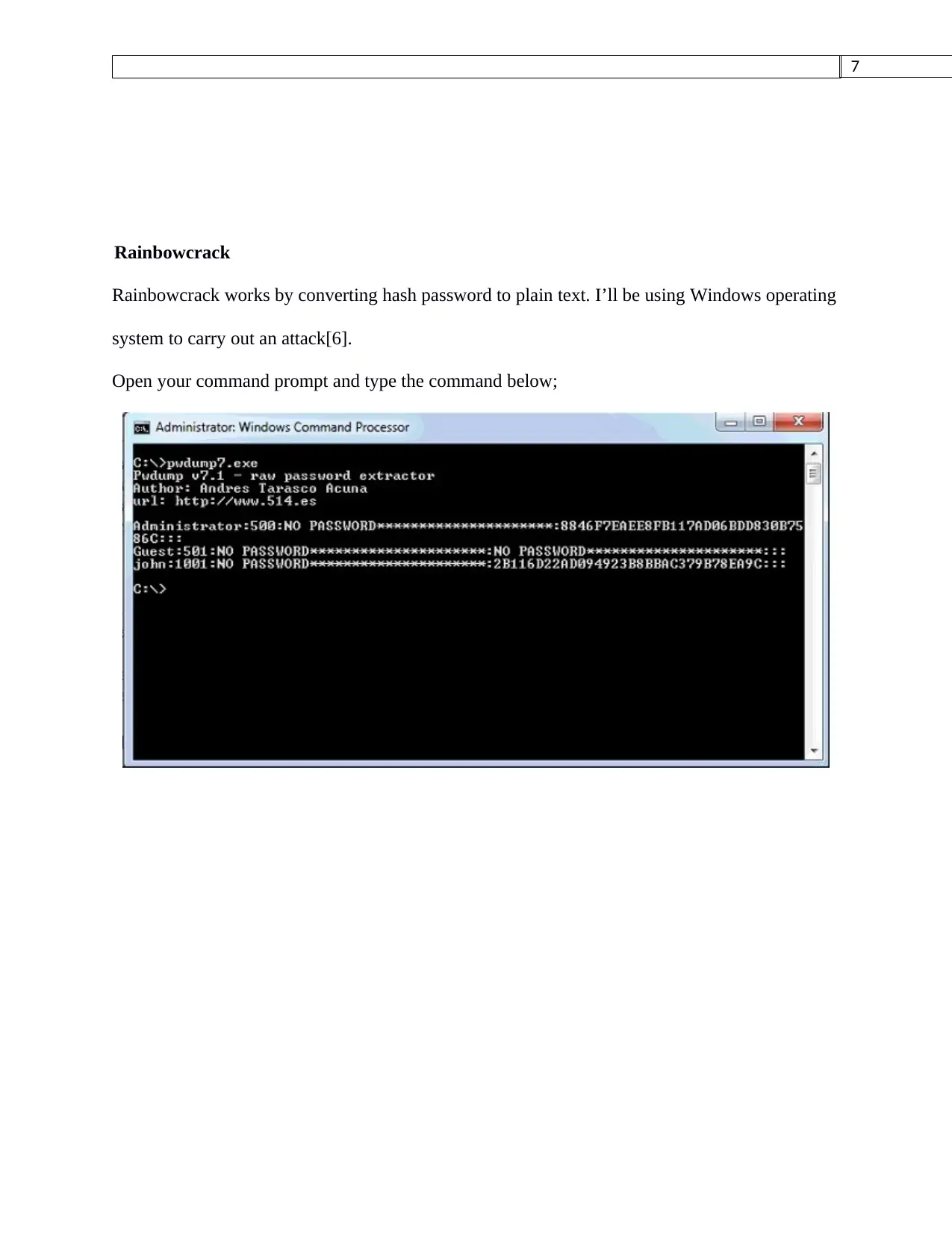
Rainbowcrack works by converting hash password to plain text. I’ll be using Windows operating
system to carry out an attack[6].
Open your command prompt and type the command below;
Rainbowcrack
Rainbowcrack works by converting hash password to plain text. I’ll be using Windows operating
system to carry out an attack[6].
Open your command prompt and type the command below;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8
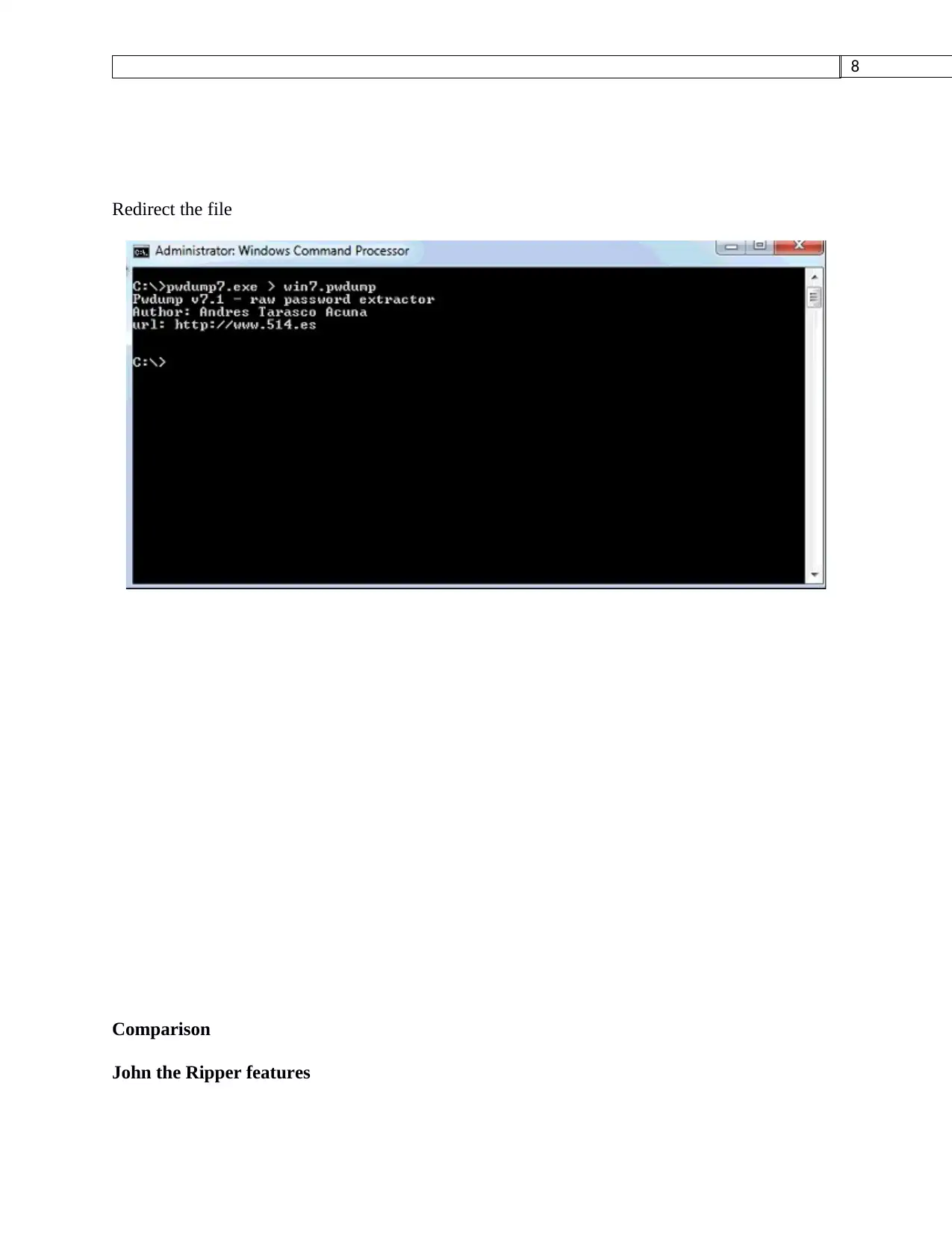
Redirect the file
Comparison
John the Ripper features
Redirect the file
Comparison
John the Ripper features

9
1. Perfect with most working frameworks and CPU designs
2. Can run consequently by utilizing crons
3. Interruption and Resume alternatives for any output
4. Gives you a chance to characterize custom letters while building lexicon assault records
5. Permits beast power customization rules
Rainbowcrack
1. Accessible rerminal-based and GUI-accommodating interface
2. Functions admirably with multi-center processors
3. Rainbow table age, sort, transformation and query
4. Backing for GPU speeding up (Nvidia CUDA and AMD OpenCL)
Analysis
John the Ripper
This is a quick and well known neighborhood secret phrase splitting application from Openwall.
It was made with the goal of identifying frail UNIX passwords however can likewise effectively
break feeble Windows LM hashes [7].
RainbowCrack
This incredibly famous secret word breaking application utilizes rainbow tables produced from
the application itself to locate a coordinating secret word hash[8].
1. Perfect with most working frameworks and CPU designs
2. Can run consequently by utilizing crons
3. Interruption and Resume alternatives for any output
4. Gives you a chance to characterize custom letters while building lexicon assault records
5. Permits beast power customization rules
Rainbowcrack
1. Accessible rerminal-based and GUI-accommodating interface
2. Functions admirably with multi-center processors
3. Rainbow table age, sort, transformation and query
4. Backing for GPU speeding up (Nvidia CUDA and AMD OpenCL)
Analysis
John the Ripper
This is a quick and well known neighborhood secret phrase splitting application from Openwall.
It was made with the goal of identifying frail UNIX passwords however can likewise effectively
break feeble Windows LM hashes [7].
RainbowCrack
This incredibly famous secret word breaking application utilizes rainbow tables produced from
the application itself to locate a coordinating secret word hash[8].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
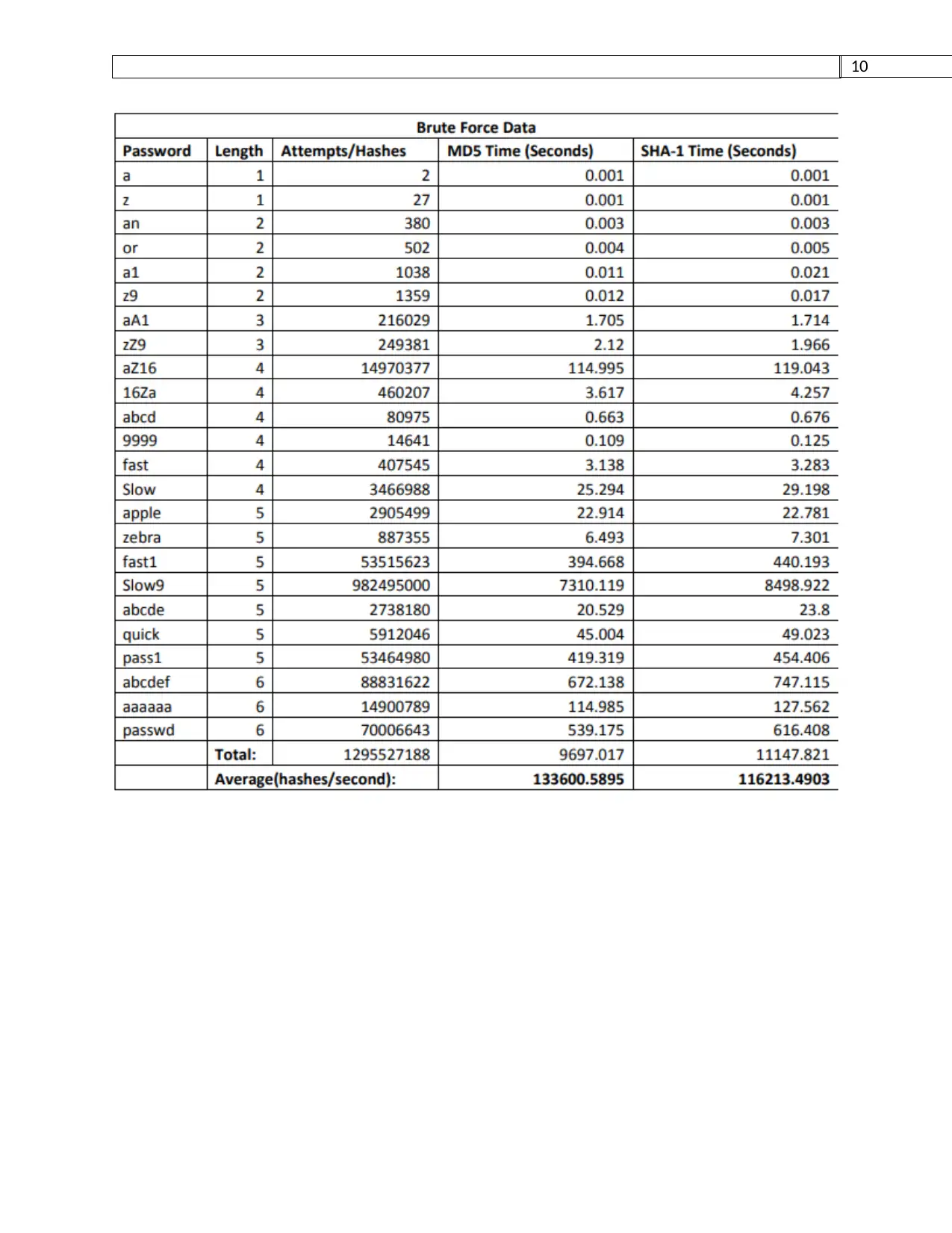
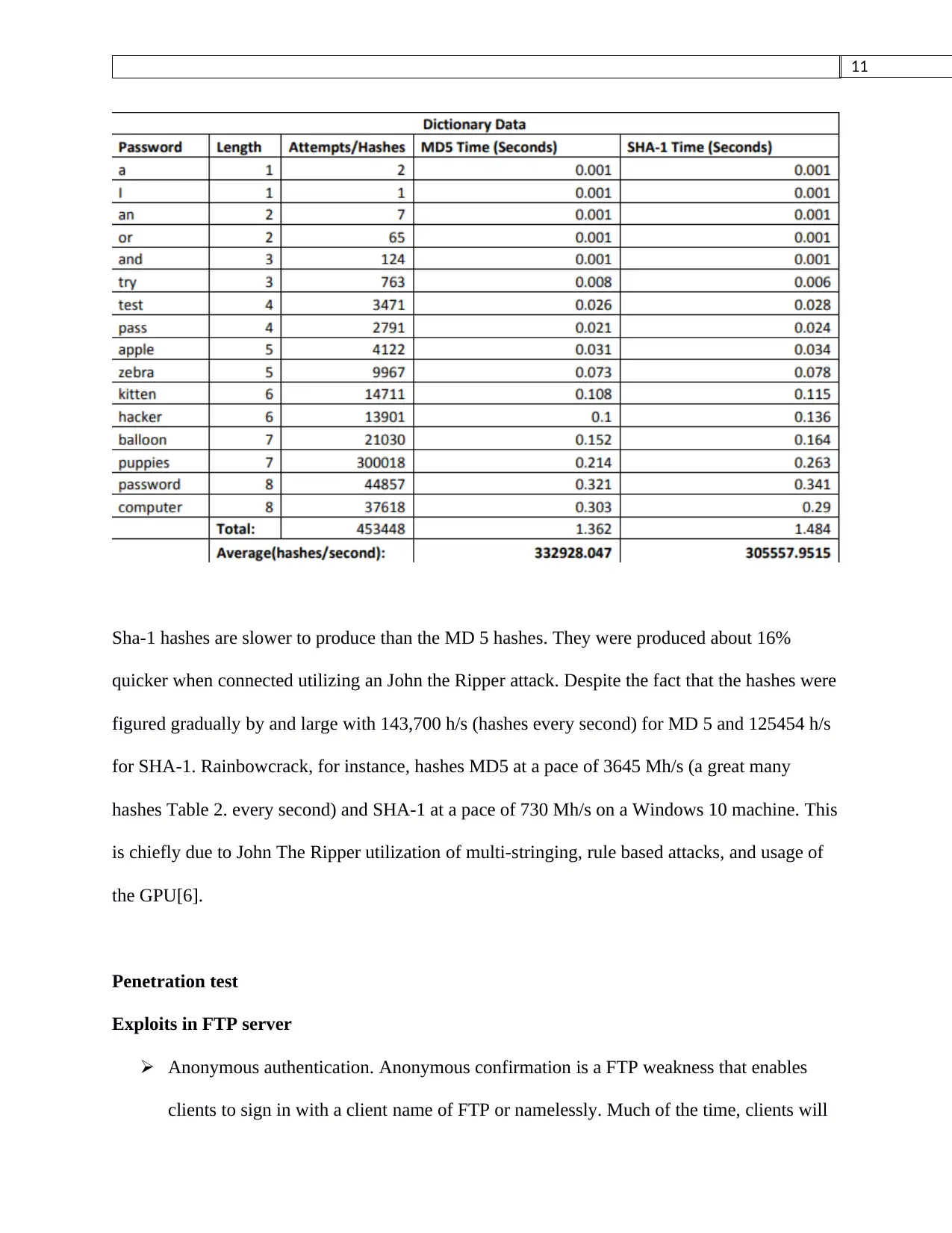
Sha-1 hashes are slower to produce than the MD 5 hashes. They were produced about 16%
quicker when connected utilizing an John the Ripper attack. Despite the fact that the hashes were
figured gradually by and large with 143,700 h/s (hashes every second) for MD 5 and 125454 h/s
for SHA-1. Rainbowcrack, for instance, hashes MD5 at a pace of 3645 Mh/s (a great many
hashes Table 2. every second) and SHA-1 at a pace of 730 Mh/s on a Windows 10 machine. This
is chiefly due to John The Ripper utilization of multi-stringing, rule based attacks, and usage of
the GPU[6].
Penetration test
Exploits in FTP server
Anonymous authentication. Anonymous confirmation is a FTP weakness that enables
clients to sign in with a client name of FTP or namelessly. Much of the time, clients will
Sha-1 hashes are slower to produce than the MD 5 hashes. They were produced about 16%
quicker when connected utilizing an John the Ripper attack. Despite the fact that the hashes were
figured gradually by and large with 143,700 h/s (hashes every second) for MD 5 and 125454 h/s
for SHA-1. Rainbowcrack, for instance, hashes MD5 at a pace of 3645 Mh/s (a great many
hashes Table 2. every second) and SHA-1 at a pace of 730 Mh/s on a Windows 10 machine. This
is chiefly due to John The Ripper utilization of multi-stringing, rule based attacks, and usage of
the GPU[6].
Penetration test
Exploits in FTP server
Anonymous authentication. Anonymous confirmation is a FTP weakness that enables
clients to sign in with a client name of FTP or namelessly. Much of the time, clients will

12
give their email address as the secret word.
Directory traversal attack. Another FTP helplessness incorporates index traversal assaults
in which the fruitful assault overwrites or makes unapproved records that are put away
outside of the web root envelope[8].
Cross site scripting. Cross site scripting is sending of data from one website form to
another website. Most of the current programming languages framework have cope this
issue by use of csrf request and tokens.
Measure to prevent attack in FTP server
Remove all anonymous logins
Ensure that FTP server is secure for transferring data and files
Remove access of FTP through Firewall
Conclusion
Secret key splitting is an undeniable danger. There are various strategies that can be utilized in
an assault that have been depicted. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers around the
world. Approaches to forestall effective assaults by programmers for use by the two clients and
chairmen have been examined. A usage of two hashing calculations was created to be tried for
proficiency and their outcomes have been accounted for.
give their email address as the secret word.
Directory traversal attack. Another FTP helplessness incorporates index traversal assaults
in which the fruitful assault overwrites or makes unapproved records that are put away
outside of the web root envelope[8].
Cross site scripting. Cross site scripting is sending of data from one website form to
another website. Most of the current programming languages framework have cope this
issue by use of csrf request and tokens.
Measure to prevent attack in FTP server
Remove all anonymous logins
Ensure that FTP server is secure for transferring data and files
Remove access of FTP through Firewall
Conclusion
Secret key splitting is an undeniable danger. There are various strategies that can be utilized in
an assault that have been depicted. John the Ripper is mostly used in cracking linux related
passwords. It is free tool that is being maintained and updated by many developers around the
world. Approaches to forestall effective assaults by programmers for use by the two clients and
chairmen have been examined. A usage of two hashing calculations was created to be tried for
proficiency and their outcomes have been accounted for.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




