IT410 W6 Project: Password Cracking, Entropy Calculation and Analysis
VerifiedAdded on 2022/08/13
|8
|1271
|56
Homework Assignment
AI Summary
This assignment is a project from IT410 focusing on password security and cracking. The student created three users with different password complexities on a virtual machine and used John the Ripper to crack them. The project details the password cracking process, including the use of commands like `useradd`, `unshadow`, and `john`. The entropy of each password was calculated using the formula from the Electronic Authentication Guideline, and the time taken to crack each password was recorded. The report also includes a bibliography of relevant research papers on social networking sites and knowledge-defined networking. The assignment aims to demonstrate understanding of password security, entropy calculation, and the practical application of password cracking tools.

Running head: NETWORKING
NETWORKING
Name of the Student:
Name of the University:
Author Note
NETWORKING
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKING
Step 1: Create 3 (three) users on a system of your choice
A virtual box has been used for creating three users in the systems. The name of the users
has been selected as User1, User2 and User3. All the users in the system have been assigned a
password and the passwords have been cracked here with the help of the tool known as John the
Ripper.
Password Cracking is referred to the means of discovering the passwords installed in a
computer without actually knowing it. It is done by obtaining the data file of the passwords
contained in the computer system and the cracking done by the guessing the passwords and rhe
using an algorithm in a repetitive iteration which would be using a number of combinations and
permutation to check with the password and discover them successfully. There are several
reasons for which password cracking can be done and there can also be malicious reason for
which password cracking is done. This might result in cybercrime. Hence, it is important that the
process should be performed with authentic intentions in mind. This can also occur when a
person has misplaced a password and a non-malicious password would be taking place in a
system. An example of this can be found when an admin checks the system and reveals some of
the passwords which are of less strength and hence can be revealed easily.
This is also done in checking the security of the systems and the nodes found vulnerable
have their passwords reset to a strong one.
NETWORKING
Step 1: Create 3 (three) users on a system of your choice
A virtual box has been used for creating three users in the systems. The name of the users
has been selected as User1, User2 and User3. All the users in the system have been assigned a
password and the passwords have been cracked here with the help of the tool known as John the
Ripper.
Password Cracking is referred to the means of discovering the passwords installed in a
computer without actually knowing it. It is done by obtaining the data file of the passwords
contained in the computer system and the cracking done by the guessing the passwords and rhe
using an algorithm in a repetitive iteration which would be using a number of combinations and
permutation to check with the password and discover them successfully. There are several
reasons for which password cracking can be done and there can also be malicious reason for
which password cracking is done. This might result in cybercrime. Hence, it is important that the
process should be performed with authentic intentions in mind. This can also occur when a
person has misplaced a password and a non-malicious password would be taking place in a
system. An example of this can be found when an admin checks the system and reveals some of
the passwords which are of less strength and hence can be revealed easily.
This is also done in checking the security of the systems and the nodes found vulnerable
have their passwords reset to a strong one.
2
NETWORKING
Step 2: Each user must have a password based on any of the following rules.
use different rules for different users.
Short (8 characters) dictionary word
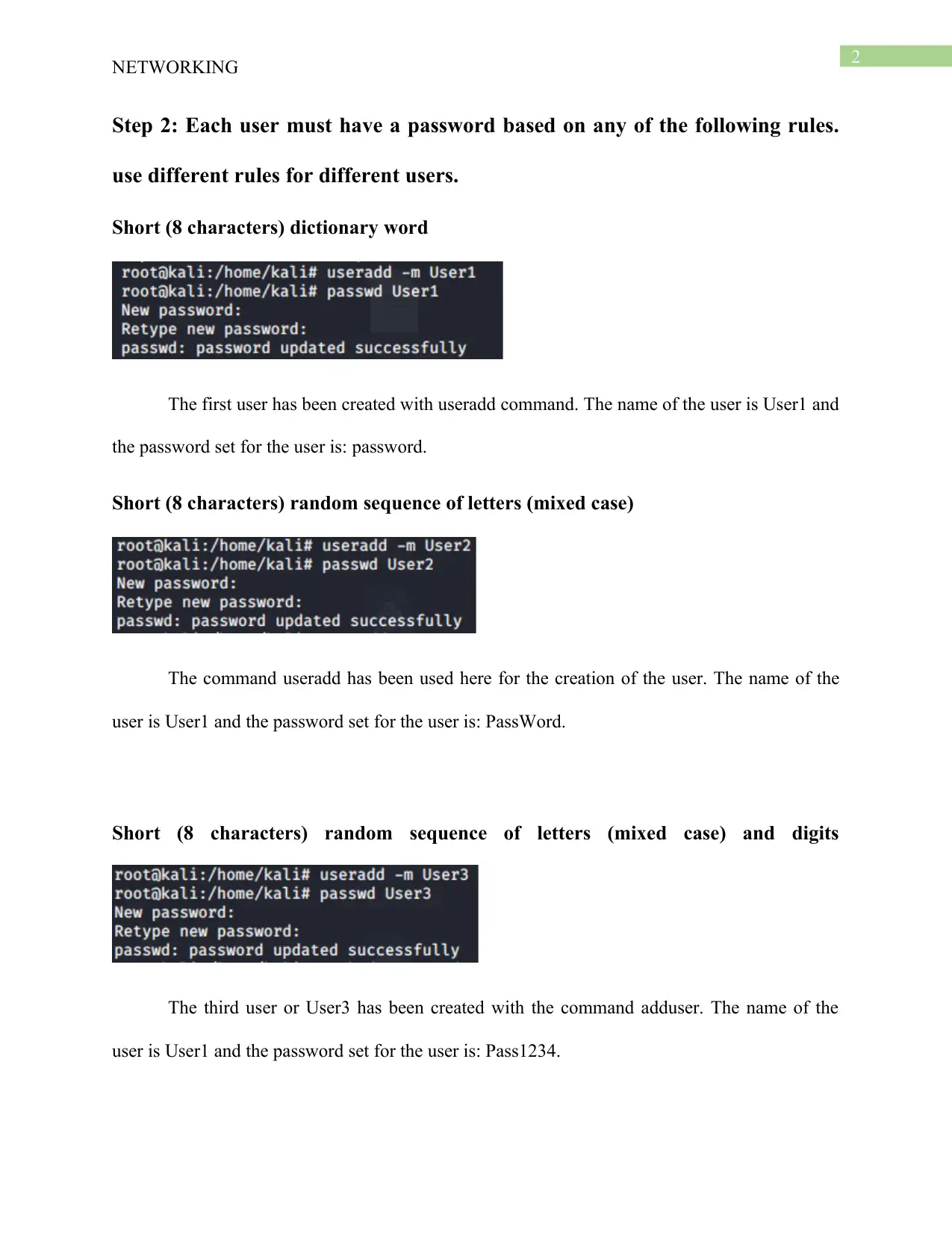
The first user has been created with useradd command. The name of the user is User1 and
the password set for the user is: password.
Short (8 characters) random sequence of letters (mixed case)
The command useradd has been used here for the creation of the user. The name of the
user is User1 and the password set for the user is: PassWord.
Short (8 characters) random sequence of letters (mixed case) and digits
The third user or User3 has been created with the command adduser. The name of the
user is User1 and the password set for the user is: Pass1234.
NETWORKING
Step 2: Each user must have a password based on any of the following rules.
use different rules for different users.
Short (8 characters) dictionary word
The first user has been created with useradd command. The name of the user is User1 and
the password set for the user is: password.
Short (8 characters) random sequence of letters (mixed case)
The command useradd has been used here for the creation of the user. The name of the
user is User1 and the password set for the user is: PassWord.
Short (8 characters) random sequence of letters (mixed case) and digits
The third user or User3 has been created with the command adduser. The name of the
user is User1 and the password set for the user is: Pass1234.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKING
Step 3: Use a password cracking utility of your choice to crack passwords of
your users
At first the checking for kali is done and the following output is received:
root@kali:~# john
John the Ripper password cracker, version 1.8.0.6-jumbo-1-bleeding [linux-x86-64-avx]
Copyright (c) 1996-2015 by Solar Designer and others
Homepage: http://www.openwall.com/john/
John the ripper comes in pre-installed the Kali system. John the ripper is designed in a
fast and feature-rich program and it is made up of a number of cracking modes which is fully
configurable for the practical needs. The tool is available at different operating systems and the
passwords for any type of users can be cracked using the tool. The following encryption has
types are being supported by the tool:
traditional DES-based,
NETWORKING
Step 3: Use a password cracking utility of your choice to crack passwords of
your users
At first the checking for kali is done and the following output is received:
root@kali:~# john
John the Ripper password cracker, version 1.8.0.6-jumbo-1-bleeding [linux-x86-64-avx]
Copyright (c) 1996-2015 by Solar Designer and others
Homepage: http://www.openwall.com/john/
John the ripper comes in pre-installed the Kali system. John the ripper is designed in a
fast and feature-rich program and it is made up of a number of cracking modes which is fully
configurable for the practical needs. The tool is available at different operating systems and the
passwords for any type of users can be cracked using the tool. The following encryption has
types are being supported by the tool:
traditional DES-based,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORKING
“bigcrypt”,
BSDI extended DES-based,
FreeBSD MD5-based (also used on Linux and in Cisco IOS),
OpenBSD Blowfish-based
Kerberos/AFS and Windows LM (DES-based) hashes, as well as DES-based tripcodes.
The normal crypt style routines are not being supported by the tool, however the tool is
consisting of tools which by itself have highly optimized modules for the different types of
passwords and the different architectures of the processor. Among the algorithms which are used
are the bitsice DES and this is not implemented within the crypt(3) API and hence, a more
powerful such as the one in John is used. Assembly language routines for several processor
architectures are used for x86-64 and x86 with SSE2.
Checking of the unshadow command is performed.
root@kali:~# unshadow
Usage: unshadow PASSWORD-FILE SHADOW-FILE
The process involves the hashing and decoding of the hashes. Firstly, the hashing has
been done with the following code:
root@kali:~# unshadow passwd shadow > unshadowed.txt
Secondly, the hashed file is used for fetching the passwords for the system.
root@kali:~# john --wordlist=/usr/share/john/password.lst --rules unshadowed.txt
NETWORKING
“bigcrypt”,
BSDI extended DES-based,
FreeBSD MD5-based (also used on Linux and in Cisco IOS),
OpenBSD Blowfish-based
Kerberos/AFS and Windows LM (DES-based) hashes, as well as DES-based tripcodes.
The normal crypt style routines are not being supported by the tool, however the tool is
consisting of tools which by itself have highly optimized modules for the different types of
passwords and the different architectures of the processor. Among the algorithms which are used
are the bitsice DES and this is not implemented within the crypt(3) API and hence, a more
powerful such as the one in John is used. Assembly language routines for several processor
architectures are used for x86-64 and x86 with SSE2.
Checking of the unshadow command is performed.
root@kali:~# unshadow
Usage: unshadow PASSWORD-FILE SHADOW-FILE
The process involves the hashing and decoding of the hashes. Firstly, the hashing has
been done with the following code:
root@kali:~# unshadow passwd shadow > unshadowed.txt
Secondly, the hashed file is used for fetching the passwords for the system.
root@kali:~# john --wordlist=/usr/share/john/password.lst --rules unshadowed.txt
5
NETWORKING
Step 4: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user1 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Here the length of the password is l. b is the set of data from which the password is to be selected
and H is the entropy of the password.
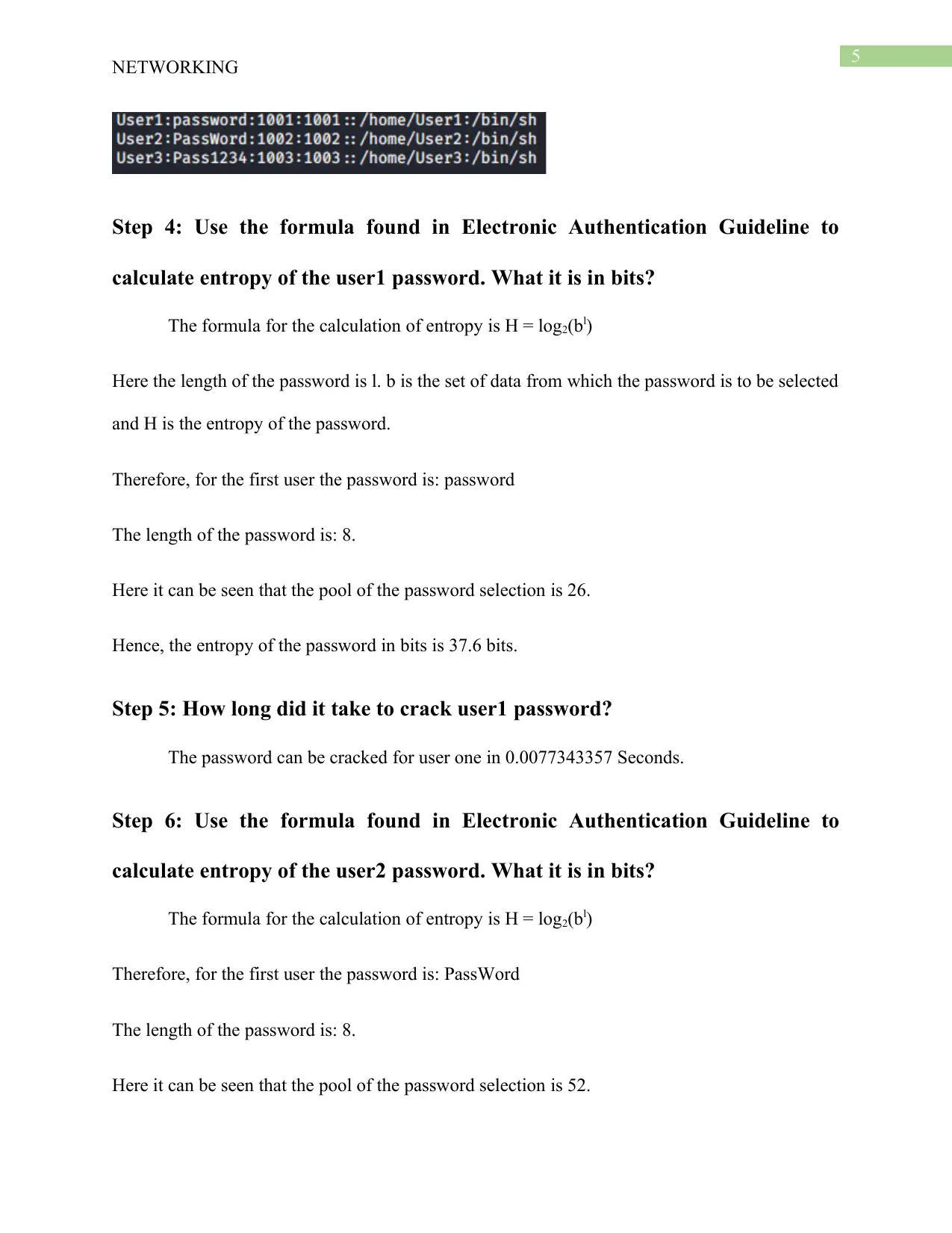
Therefore, for the first user the password is: password
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 26.
Hence, the entropy of the password in bits is 37.6 bits.
Step 5: How long did it take to crack user1 password?
The password can be cracked for user one in 0.0077343357 Seconds.
Step 6: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user2 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Therefore, for the first user the password is: PassWord
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 52.
NETWORKING
Step 4: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user1 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Here the length of the password is l. b is the set of data from which the password is to be selected
and H is the entropy of the password.
Therefore, for the first user the password is: password
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 26.
Hence, the entropy of the password in bits is 37.6 bits.
Step 5: How long did it take to crack user1 password?
The password can be cracked for user one in 0.0077343357 Seconds.
Step 6: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user2 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Therefore, for the first user the password is: PassWord
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 52.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKING
Hence, the entropy of the password in bits is 45.6 bits.
Step 7: How long did it take to crack user2 password?
The password can be cracked for user one in 2 Seconds.
Step 8: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user3 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Therefore, for the first user the password is: cleft cam synod
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 94.
Hence, the entropy of the password in bits is 52.4 bits.
Step 9: How long did it take to crack user3 password?
The password can be cracked for user three in 4 minutes.
NETWORKING
Hence, the entropy of the password in bits is 45.6 bits.
Step 7: How long did it take to crack user2 password?
The password can be cracked for user one in 2 Seconds.
Step 8: Use the formula found in Electronic Authentication Guideline to
calculate entropy of the user3 password. What it is in bits?
The formula for the calculation of entropy is H = log2(bl)
Therefore, for the first user the password is: cleft cam synod
The length of the password is: 8.
Here it can be seen that the pool of the password selection is 94.
Hence, the entropy of the password in bits is 52.4 bits.
Step 9: How long did it take to crack user3 password?
The password can be cracked for user three in 4 minutes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORKING
Bibliography
Kuss, D.J. and Griffiths, M.D., 2017. Social networking sites and addiction: Ten lessons learned.
International journal of environmental research and public health, 14(3), p.311.
Mestres, A., Rodriguez-Natal, A., Carner, J., Barlet-Ros, P., Alarcón, E., Solé, M., Muntés-
Mulero, V., Meyer, D., Barkai, S., Hibbett, M.J. and Estrada, G., 2017. Knowledge-defined
networking. ACM SIGCOMM Computer Communication Review, 47(3), pp.2-10.
NETWORKING
Bibliography
Kuss, D.J. and Griffiths, M.D., 2017. Social networking sites and addiction: Ten lessons learned.
International journal of environmental research and public health, 14(3), p.311.
Mestres, A., Rodriguez-Natal, A., Carner, J., Barlet-Ros, P., Alarcón, E., Solé, M., Muntés-
Mulero, V., Meyer, D., Barkai, S., Hibbett, M.J. and Estrada, G., 2017. Knowledge-defined
networking. ACM SIGCOMM Computer Communication Review, 47(3), pp.2-10.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



