Cyber Security and Analytics: Password Cracking Tools Analysis
VerifiedAdded on 2022/12/29
|13
|1437
|92
Practical Assignment
AI Summary
This assignment provides an overview of password cracking tools, specifically focusing on John the Ripper and Rainbow Crack. The paper details the functionalities of each tool, including their methodologies for cracking passwords, such as brute force and dictionary attacks, and the use of rainbow tables. The assignment includes practical demonstrations, outlining the installation process on Ubuntu and the command-line usage of the tools. It also discusses penetration testing, particularly FTP server testing using Kali Linux, covering reconnaissance, scanning, access gaining, and track covering phases. The paper concludes by emphasizing the importance of understanding password cracking techniques for securing systems and preventing unauthorized access. The bibliography provides relevant sources for further study.

Running head: CYBER SECURITY AND ANALYTICS
CYBER SECURITY AND ANALYTICS
Name of the Student
Name of the University
Author Note
CYBER SECURITY AND ANALYTICS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBER SECURITY AND ANALYTICS 1
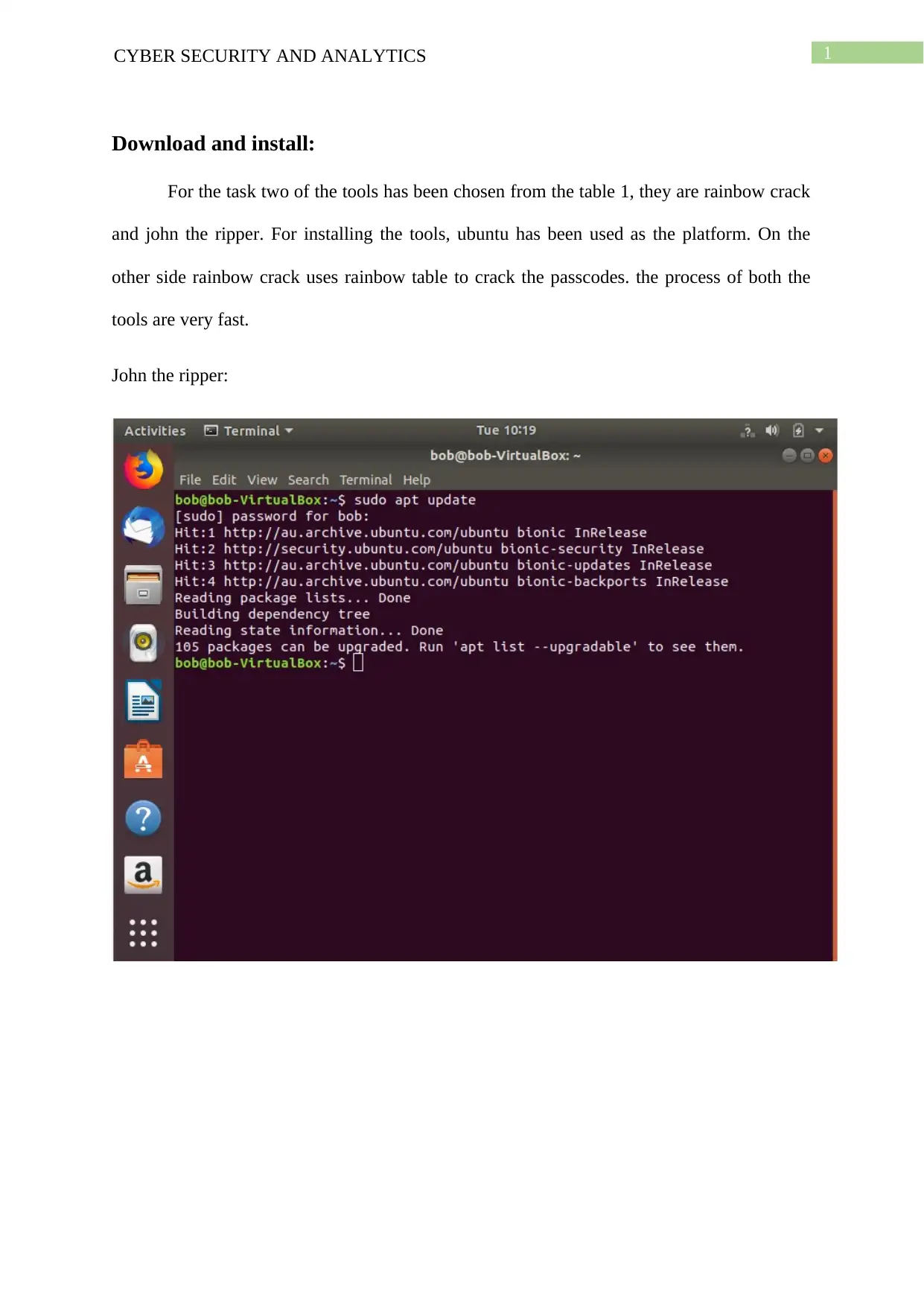
Download and install:
For the task two of the tools has been chosen from the table 1, they are rainbow crack
and john the ripper. For installing the tools, ubuntu has been used as the platform. On the
other side rainbow crack uses rainbow table to crack the passcodes. the process of both the
tools are very fast.
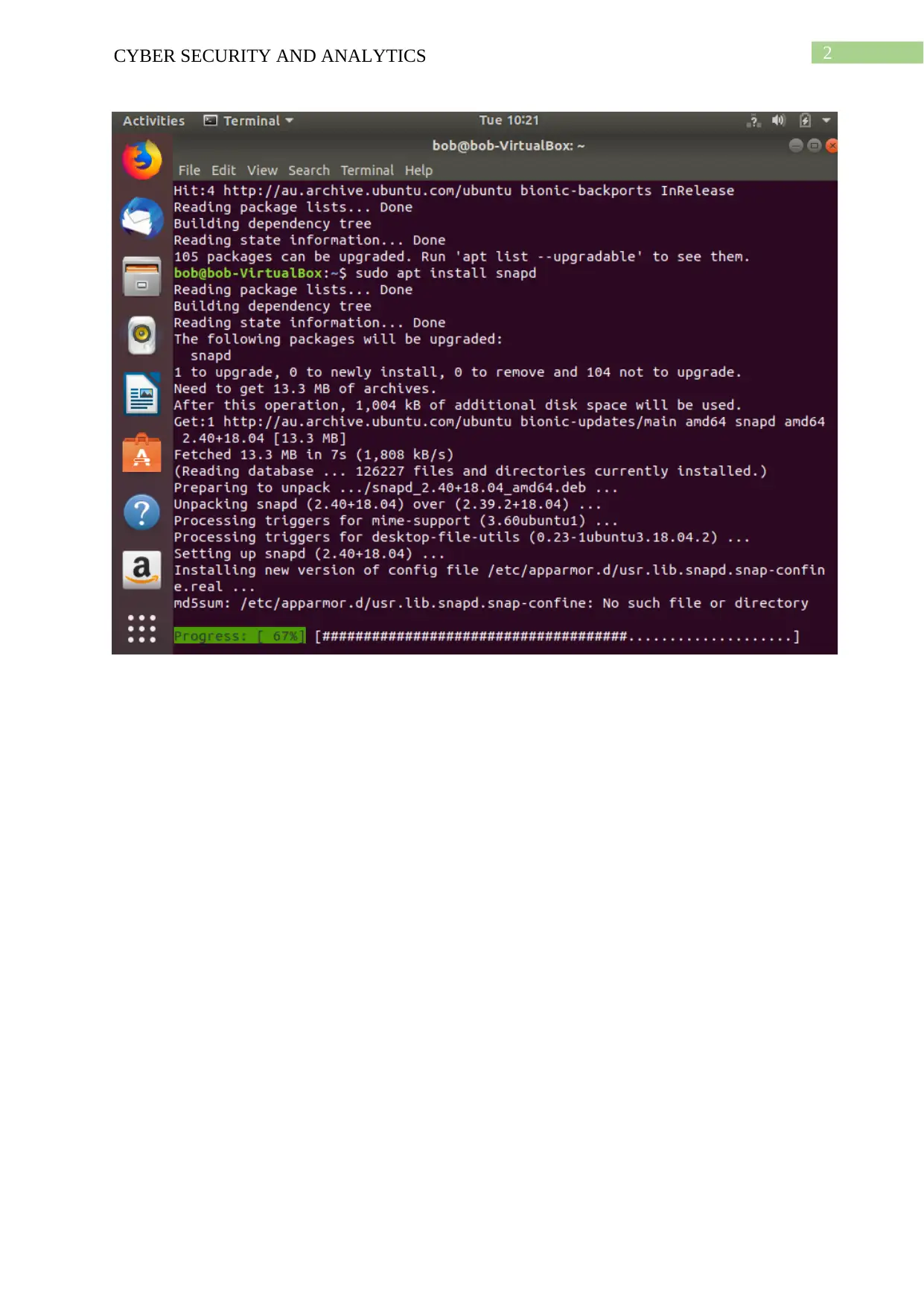
John the ripper:
Download and install:
For the task two of the tools has been chosen from the table 1, they are rainbow crack
and john the ripper. For installing the tools, ubuntu has been used as the platform. On the
other side rainbow crack uses rainbow table to crack the passcodes. the process of both the
tools are very fast.
John the ripper:
2CYBER SECURITY AND ANALYTICS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CYBER SECURITY AND ANALYTICS
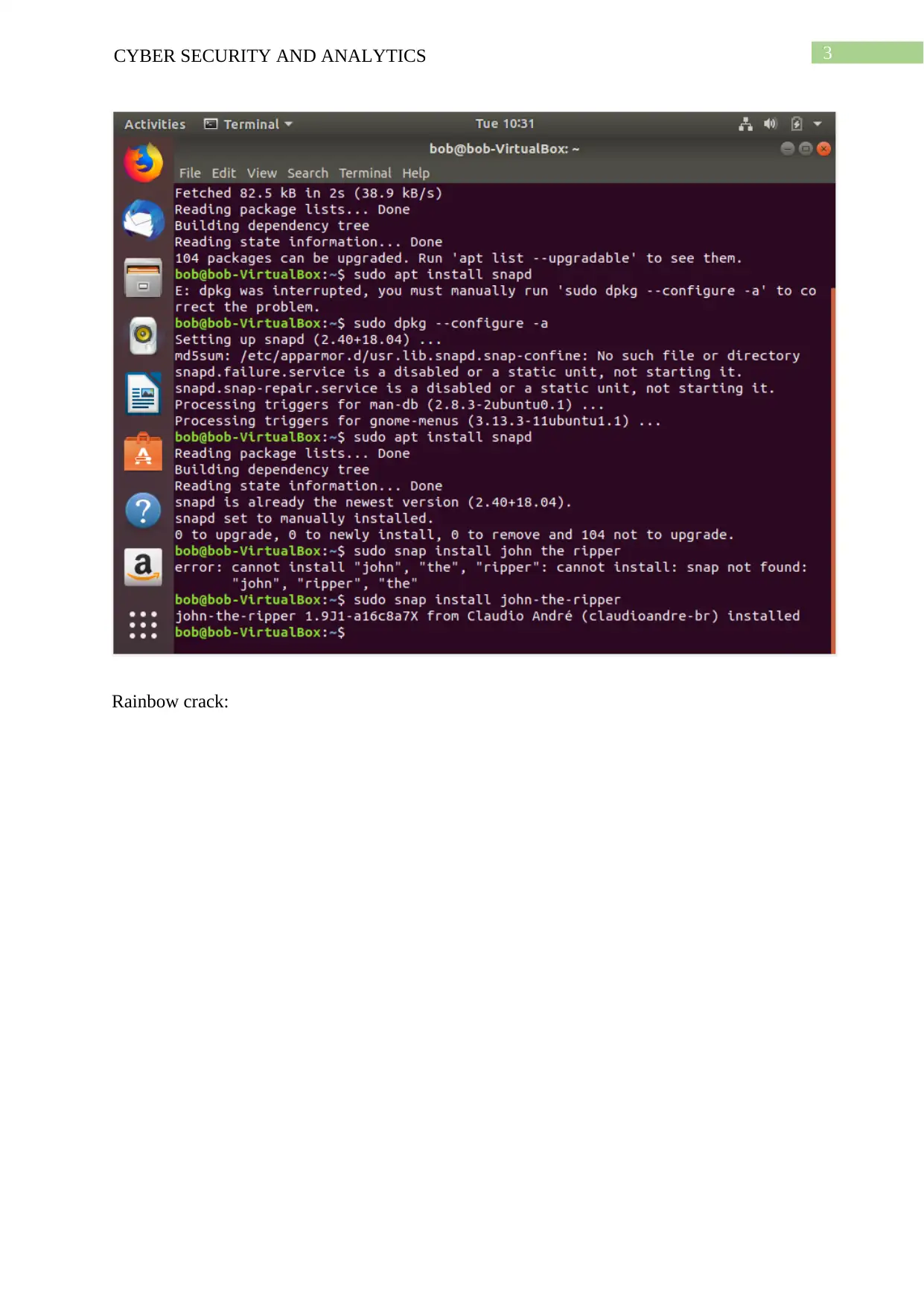
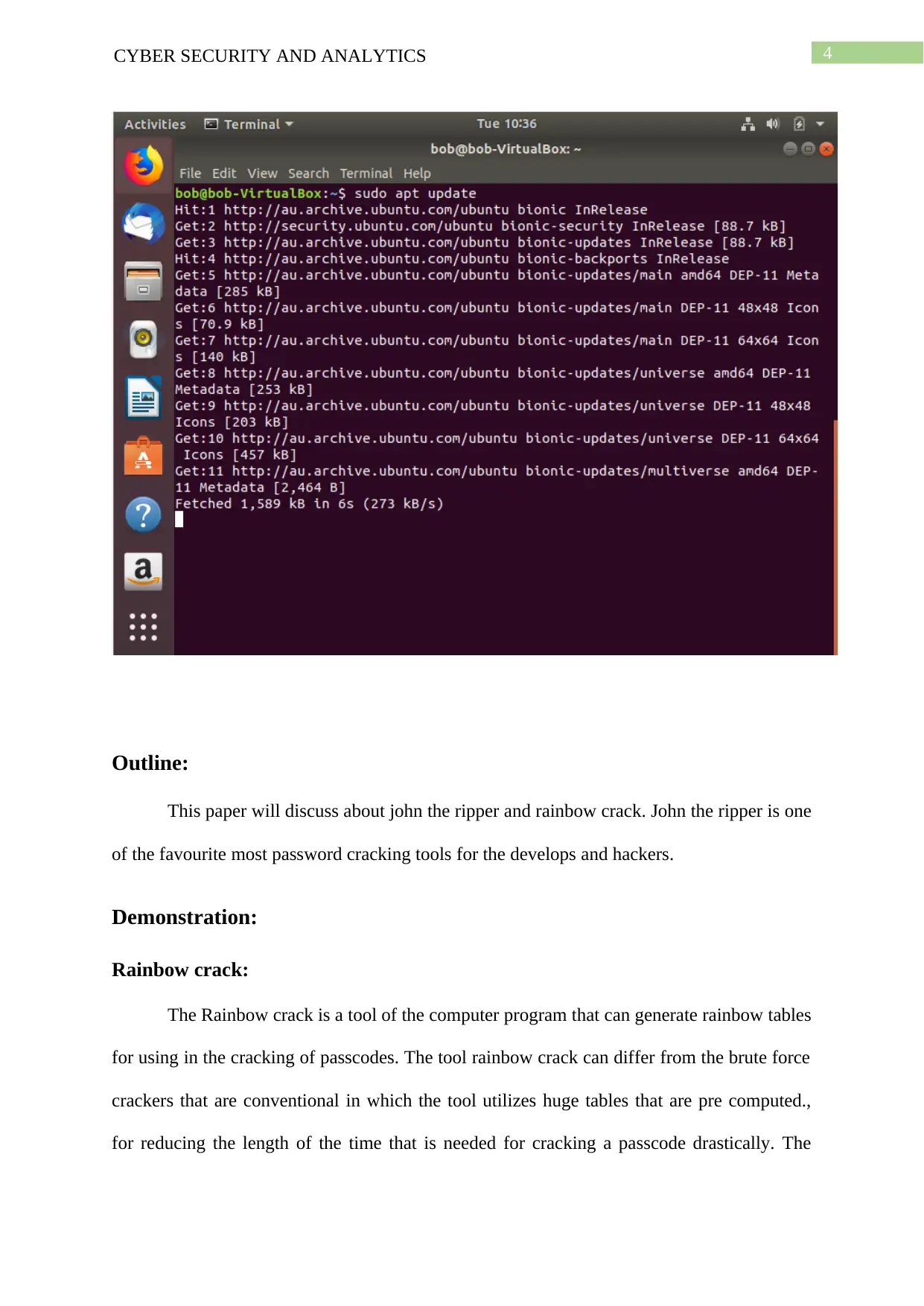
Rainbow crack:
Rainbow crack:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY AND ANALYTICS
Outline:
This paper will discuss about john the ripper and rainbow crack. John the ripper is one
of the favourite most password cracking tools for the develops and hackers.
Demonstration:
Rainbow crack:
The Rainbow crack is a tool of the computer program that can generate rainbow tables
for using in the cracking of passcodes. The tool rainbow crack can differ from the brute force
crackers that are conventional in which the tool utilizes huge tables that are pre computed.,
for reducing the length of the time that is needed for cracking a passcode drastically. The
Outline:
This paper will discuss about john the ripper and rainbow crack. John the ripper is one
of the favourite most password cracking tools for the develops and hackers.
Demonstration:
Rainbow crack:
The Rainbow crack is a tool of the computer program that can generate rainbow tables
for using in the cracking of passcodes. The tool rainbow crack can differ from the brute force
crackers that are conventional in which the tool utilizes huge tables that are pre computed.,
for reducing the length of the time that is needed for cracking a passcode drastically. The

5CYBER SECURITY AND ANALYTICS
technology of rainbow cracking can work on a concept that is so simple. Instead of cracking
the passcodes, the tool also has the ability to compute the hashes within the rainbow tables.
Hence the tool takes very less time compared to the methods that are traditional.
The tools that are included in the package of rainbow crack tool are:
rcrack: rainbow table password cracker.
“smith-@bob-Virtualbox: ~$ rcrack
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: /rcrack path [path] [...] -h hash
./rcrack path [path] [...] -l hash_list_file
./rcrack path [path] [...] -lm pwdump_file
./rcrack path [path] [...] -ntlm pwdump_file
path: directory where rainbow tables (*.rt, *.rtc) are stored
-h hash: load single hash
-l hash_list_file: load hashes from a file, each hash in a line
-lm pwdump_file: load lm hashes from pwdump file
-ntlm pwdump_file: load ntlm hashes from pwdump file
implemented hash algorithms:
lm HashLen=8 PlaintextLen=0-7
ntlm HashLen=16 PlaintextLen=0-15
md5 HashLen=16 PlaintextLen=0-15
sha1 HashLen=20 PlaintextLen=0-20
sha256 HashLen=32 PlaintextLen=0-20
examples:
./rcrack . -h 5d41402abc4b2a76b9719d911017c592
technology of rainbow cracking can work on a concept that is so simple. Instead of cracking
the passcodes, the tool also has the ability to compute the hashes within the rainbow tables.
Hence the tool takes very less time compared to the methods that are traditional.
The tools that are included in the package of rainbow crack tool are:
rcrack: rainbow table password cracker.
“smith-@bob-Virtualbox: ~$ rcrack
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: /rcrack path [path] [...] -h hash
./rcrack path [path] [...] -l hash_list_file
./rcrack path [path] [...] -lm pwdump_file
./rcrack path [path] [...] -ntlm pwdump_file
path: directory where rainbow tables (*.rt, *.rtc) are stored
-h hash: load single hash
-l hash_list_file: load hashes from a file, each hash in a line
-lm pwdump_file: load lm hashes from pwdump file
-ntlm pwdump_file: load ntlm hashes from pwdump file
implemented hash algorithms:
lm HashLen=8 PlaintextLen=0-7
ntlm HashLen=16 PlaintextLen=0-15
md5 HashLen=16 PlaintextLen=0-15
sha1 HashLen=20 PlaintextLen=0-20
sha256 HashLen=32 PlaintextLen=0-20
examples:
./rcrack . -h 5d41402abc4b2a76b9719d911017c592
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER SECURITY AND ANALYTICS
./rcrack . -l hash.txt”
Rt2rt:
“smith-@bob-Virtualbox:~$ rtc2rt
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: ./rtc2rt path”
Rtgen:
“smith-@bob-Virtualbox:~$: rtgen
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: rtgen hash_algorithm charset plaintext_len_min plaintext_len_max table_index
chain_len chain_num part_index
rtgen hash_algorithm charset plaintext_len_min plaintext_len_max table_index -bench
hash algorithms implemented:
lm HashLen=8 PlaintextLen=0-7
ntlm HashLen=16 PlaintextLen=0-15
md5 HashLen=16 PlaintextLen=0-15
sha1 HashLen=20 PlaintextLen=0-20
sha256 HashLen=32 PlaintextLen=0-20
examples:
rtgen md5 loweralpha 1 7 0 1000 1000 0
rtgen md5 loweralpha 1 7 0 -bench”
./rcrack . -l hash.txt”
Rt2rt:
“smith-@bob-Virtualbox:~$ rtc2rt
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: ./rtc2rt path”
Rtgen:
“smith-@bob-Virtualbox:~$: rtgen
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: rtgen hash_algorithm charset plaintext_len_min plaintext_len_max table_index
chain_len chain_num part_index
rtgen hash_algorithm charset plaintext_len_min plaintext_len_max table_index -bench
hash algorithms implemented:
lm HashLen=8 PlaintextLen=0-7
ntlm HashLen=16 PlaintextLen=0-15
md5 HashLen=16 PlaintextLen=0-15
sha1 HashLen=20 PlaintextLen=0-20
sha256 HashLen=32 PlaintextLen=0-20
examples:
rtgen md5 loweralpha 1 7 0 1000 1000 0
rtgen md5 loweralpha 1 7 0 -bench”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY AND ANALYTICS
Rtsort:
“smith-@bob-Virtualbox:~$: rtsort
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: ./rtsort path”
John the ripper:
The tool john the ripper is one of the most popular passcode cracking tools. This is
having the capability for implementing the brute force attacks, single crack mode and the
dictionary attack which is basically for exploiting the flaws of common password. The tool
was designed originally for the Unix based operating systems. The tools are available for
most of the platforms that are common. The open source and free version are distributed
generally as the source code. However, a commercial version of the tool john the ripper is
also available that is known as john the ripper pro.
The has format that are supported by the tool are as follows:
Crypt:
“$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
Rtsort:
“smith-@bob-Virtualbox:~$: rtsort
RainbowCrack 1.7
Copyright 2017 RainbowCrack Project. All rights reserved.
http://project-rainbowcrack.com/
usage: ./rtsort path”
John the ripper:
The tool john the ripper is one of the most popular passcode cracking tools. This is
having the capability for implementing the brute force attacks, single crack mode and the
dictionary attack which is basically for exploiting the flaws of common password. The tool
was designed originally for the Unix based operating systems. The tools are available for
most of the platforms that are common. The open source and free version are distributed
generally as the source code. However, a commercial version of the tool john the ripper is
also available that is known as john the ripper pro.
The has format that are supported by the tool are as follows:
Crypt:
“$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".

8CYBER SECURITY AND ANALYTICS
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt”
Des:
$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt
$ john --format=des hashes.txt”
John the ripper uses mainly brute force attack and dictionary attack for cracking the
passwords.
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt”
Des:
$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt
$ john --format=des hashes.txt”
John the ripper uses mainly brute force attack and dictionary attack for cracking the
passwords.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY AND ANALYTICS
Time taken for cracking the passwords and ease of access:
The tool john the ripper has taken less time than the other password cracking tools. As
the tool john the ripper uses advanced methods for cracking passcodes.
John the ripper was designed for both the features rich and fast. As the tool is having some of
the advanced features than the other tools.
The tool john the ripper was designed originally for the Unix based operating
systems. The tool is available for most of the platforms that are common. The open source
and free version are distributed generally as the source code. The technology of rainbow
cracking can work on a concept that is so simple. Instead of cracking the passcodes, the tool
also has the ability to compute the hashes within the rainbow tables. Hence the tool takes
very less time compared to the methods that are traditional.
Penetration testing:
FTP or file transfer protocol is used for the transfer of files between a network using
the connections of IP. It is a server-client protocol. It works on TCP, so it requires two
channels of communication. Kali Linux is used for penetration testing and it is based on
Ubuntu. The phases of penetration testing in FTP server are as follows:
• Reconnaissance
• Scanning
• Access gaining
• Maintenance of the access
• Covering the tracks.
Time taken for cracking the passwords and ease of access:
The tool john the ripper has taken less time than the other password cracking tools. As
the tool john the ripper uses advanced methods for cracking passcodes.
John the ripper was designed for both the features rich and fast. As the tool is having some of
the advanced features than the other tools.
The tool john the ripper was designed originally for the Unix based operating
systems. The tool is available for most of the platforms that are common. The open source
and free version are distributed generally as the source code. The technology of rainbow
cracking can work on a concept that is so simple. Instead of cracking the passcodes, the tool
also has the ability to compute the hashes within the rainbow tables. Hence the tool takes
very less time compared to the methods that are traditional.
Penetration testing:
FTP or file transfer protocol is used for the transfer of files between a network using
the connections of IP. It is a server-client protocol. It works on TCP, so it requires two
channels of communication. Kali Linux is used for penetration testing and it is based on
Ubuntu. The phases of penetration testing in FTP server are as follows:
• Reconnaissance
• Scanning
• Access gaining
• Maintenance of the access
• Covering the tracks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY AND ANALYTICS
Conclusion:
The password cracking is one of procedure that is for gaining the access which is not
authorised to the restricted systems. By using algorithms and common passcodes the
passwords can be guessed. Both the tools john the ripper and rainbow crack use different
methods but the purpose of them is similar, password cracking.
Conclusion:
The password cracking is one of procedure that is for gaining the access which is not
authorised to the restricted systems. By using algorithms and common passcodes the
passwords can be guessed. Both the tools john the ripper and rainbow crack use different
methods but the purpose of them is similar, password cracking.

11CYBER SECURITY AND ANALYTICS
Bibliography:
[1]"VULNERABILITY ASSESSMENT & PENETRATION TESTING
(VAPT)", International Journal of Recent Trends in Engineering and Research, vol. 4, no. 3,
pp. 326-330, 2018. Available: 10.23883/ijrter.2018.4135.tru9k.
[2]J. Doshi and B. Trivedi, "Comparison of Vulnerability Assessment and Penetration
Testing", International Journal of Applied Information Systems, vol. 8, no. 6, pp. 51-53,
2015. Available: 10.5120/ijais15-451326.
[3]Openwall.com, "John the Ripper password cracker", Openwall.com, 2019. [Online].
Available: https://www.openwall.com/john/. [Accessed: 03- Sep- 2019].
[4]Project-rainbowcrack.com, "RainbowCrack - Crack Hashes with Rainbow
Tables", Project-rainbowcrack.com, 2019. [Online]. Available: http://project-
rainbowcrack.com/. [Accessed: 03- Sep- 2019].
[5]İ. Kara, "Detection, Technical Analysis of Brute Force Attack", Sakarya University
Journal of Computer and Information Sciences, 2019. Available:
10.35377/saucis.02.02.561844.
[6]A. SATOH, Y. NAKAMURA and T. IKENAGA, "A New Approach to Identify User
Authentication Methods toward SSH Dictionary Attack Detection", IEICE Transactions on
Information and Systems, vol. 98, no. 4, pp. 760-768, 2015. Available:
10.1587/transinf.2014icp0005.
Bibliography:
[1]"VULNERABILITY ASSESSMENT & PENETRATION TESTING
(VAPT)", International Journal of Recent Trends in Engineering and Research, vol. 4, no. 3,
pp. 326-330, 2018. Available: 10.23883/ijrter.2018.4135.tru9k.
[2]J. Doshi and B. Trivedi, "Comparison of Vulnerability Assessment and Penetration
Testing", International Journal of Applied Information Systems, vol. 8, no. 6, pp. 51-53,
2015. Available: 10.5120/ijais15-451326.
[3]Openwall.com, "John the Ripper password cracker", Openwall.com, 2019. [Online].
Available: https://www.openwall.com/john/. [Accessed: 03- Sep- 2019].
[4]Project-rainbowcrack.com, "RainbowCrack - Crack Hashes with Rainbow
Tables", Project-rainbowcrack.com, 2019. [Online]. Available: http://project-
rainbowcrack.com/. [Accessed: 03- Sep- 2019].
[5]İ. Kara, "Detection, Technical Analysis of Brute Force Attack", Sakarya University
Journal of Computer and Information Sciences, 2019. Available:
10.35377/saucis.02.02.561844.
[6]A. SATOH, Y. NAKAMURA and T. IKENAGA, "A New Approach to Identify User
Authentication Methods toward SSH Dictionary Attack Detection", IEICE Transactions on
Information and Systems, vol. 98, no. 4, pp. 760-768, 2015. Available:
10.1587/transinf.2014icp0005.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
