Security and Forensics: PatentWorks Ltd Expansion to Australia Report
VerifiedAdded on 2021/04/24
|13
|2756
|37
Report
AI Summary
This report analyzes the security and forensics aspects for PatentWorks Ltd, a New Zealand-based company, planning expansion to Australia, using Aconex Ltd as a benchmark. It begins by assessing operational security risks, including identifying sensitive data, potential threats, vulnerabilities, and implementing countermeasures. Best practices such as change management, access restriction, and disaster recovery planning are discussed. The report then outlines a business continuity and disaster recovery plan, covering organizational threats, business impact analysis, and the importance of regular updates and testing. Legal issues pertaining to IT resources and privacy in both New Zealand and Australia are examined, referencing relevant security controls and initiatives. Finally, an IT roadmap diagram is presented, visualizing the proposed IT infrastructure. The report concludes by emphasizing the dynamic nature of computer security and the need for robust plans to address cyber threats, ensuring business continuity, and complying with legal requirements.

Running head: SECURITY AND FORENSICS
Security and Forensics
(Aconex Limited)
Name of the student:
Name of the university:
Author Note
Security and Forensics
(Aconex Limited)
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY AND FORENSICS
Executive Summary
Aconex Ltd is popular provider of mobile and web-based collaboration at Australia. In PatentWorks
Ltd at New Zealand, security of IT infrastructure and cyber crime has turned out to be a rising
concern. The following study compares the companies of two different nations and analyzes the
aspects of security and forensics to expand the business to Australia. The motive is well illustrated
with an IT road-map diagram provided in the study.
Executive Summary
Aconex Ltd is popular provider of mobile and web-based collaboration at Australia. In PatentWorks
Ltd at New Zealand, security of IT infrastructure and cyber crime has turned out to be a rising
concern. The following study compares the companies of two different nations and analyzes the
aspects of security and forensics to expand the business to Australia. The motive is well illustrated
with an IT road-map diagram provided in the study.

2SECURITY AND FORENSICS
Table of Contents
1. Introduction:......................................................................................................................................3
2. Analysis of operational security risks for PatentWorks Ltd to expand to Australia:........................3
2.1. Steps regarding operational security:..........................................................................................3
2.2. Best practices for operational security:.......................................................................................5
3. Conducting Business Continuity and Disaster Recovery Plan for PatentWorks Ltd:.......................6
3.1. Business Continuity Plan:...........................................................................................................6
3.2. Development of Disaster Recovery Plan:...................................................................................7
4. Covering legal issues pertaining to IT resources and privacy when operating in New Zealand and
Australia:................................................................................................................................................8
5. IT road map diagram foe PatentWorks Ltd placing proper IT assets:.............................................10
6. Conclusion:......................................................................................................................................10
7. References:......................................................................................................................................12
Table of Contents
1. Introduction:......................................................................................................................................3
2. Analysis of operational security risks for PatentWorks Ltd to expand to Australia:........................3
2.1. Steps regarding operational security:..........................................................................................3
2.2. Best practices for operational security:.......................................................................................5
3. Conducting Business Continuity and Disaster Recovery Plan for PatentWorks Ltd:.......................6
3.1. Business Continuity Plan:...........................................................................................................6
3.2. Development of Disaster Recovery Plan:...................................................................................7
4. Covering legal issues pertaining to IT resources and privacy when operating in New Zealand and
Australia:................................................................................................................................................8
5. IT road map diagram foe PatentWorks Ltd placing proper IT assets:.............................................10
6. Conclusion:......................................................................................................................................10
7. References:......................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SECURITY AND FORENSICS
1. Introduction:
Computer forensics refers to the application of analysis and investigation techniques for
gathering and preserving evidences from specific computing devices which is suitable to present the
court of law (Wang, Uehara & Sasaki, 2015). On the other hand, cyber crime has been rising across
the world and security of IT infrastructure has been under huge threat.
Aconex Limited is a public and popular company in Australia that provides mobile and web-
based collaboration technologies for process management and project information ("Aconex:
Construction Management Software", 2018). To understand the security and forensic issues Aconex
is chosen whose organizational setup is provided and whose security infrastructure is been reviewed
in the study. This motive of the literature is to analyze the security and forensic features for
PatentWorks Ltd, New Zealand to expand to Australia, taking Aconex as an example.
The following report includes the assessment of operational security risks for PatentWorks
Ltd. Then, business continuity and disaster recovery plan is demonstrated. Next, various legal issues
pertaining to IT resources and privacy is discussed in this study. Lastly, a IT road map diagram is
illustrated for the suggested solution with placement of IT resources.
2. Analysis of operational security risks for PatentWorks Ltd to expand to
Australia:
2.1. Steps regarding operational security:
Steps Discussion
Identification of sensitive
data
This includes product research, intellectual property, customer
information, employee information and financial statements of the
1. Introduction:
Computer forensics refers to the application of analysis and investigation techniques for
gathering and preserving evidences from specific computing devices which is suitable to present the
court of law (Wang, Uehara & Sasaki, 2015). On the other hand, cyber crime has been rising across
the world and security of IT infrastructure has been under huge threat.
Aconex Limited is a public and popular company in Australia that provides mobile and web-
based collaboration technologies for process management and project information ("Aconex:
Construction Management Software", 2018). To understand the security and forensic issues Aconex
is chosen whose organizational setup is provided and whose security infrastructure is been reviewed
in the study. This motive of the literature is to analyze the security and forensic features for
PatentWorks Ltd, New Zealand to expand to Australia, taking Aconex as an example.
The following report includes the assessment of operational security risks for PatentWorks
Ltd. Then, business continuity and disaster recovery plan is demonstrated. Next, various legal issues
pertaining to IT resources and privacy is discussed in this study. Lastly, a IT road map diagram is
illustrated for the suggested solution with placement of IT resources.
2. Analysis of operational security risks for PatentWorks Ltd to expand to
Australia:
2.1. Steps regarding operational security:
Steps Discussion
Identification of sensitive
data
This includes product research, intellectual property, customer
information, employee information and financial statements of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SECURITY AND FORENSICS
present business.
Identification of possible
threats
For every category that is thought to be sensitive, the business must
identify the kind of threats that are present (Androulidakis, 2016).
However, they can wary of third parties to steal their data. Hence
they must watch out for various insider threats like disrupted
workers and negligent employees.
Analyzing security holes
and additional
vulnerabilities
The safeguarding processes must be analyzed and find out the
weaknesses and loopholes must be found out.
Appraising level of risk
related to all vulnerability
The vulnerabilities must be ranked utilizing factors like likelihood
of the occurring attack damage-extent that could suffer. This also
includes the time period and work they require to recover.
Get various
countermeasures in place
Lastly the operational security is to develop and deploy plan to
eradicate threats and mitigate various risks. It can involve updating
of hardware and generating new policies about sensitive data or train
people with sound company policies and security policies of Aconex
(Chambers et al., 2015). The countermeasures have been simple and
straightforward. Further, employees have been able to implement
measures needed on their counter-part with or without extra training.
present business.
Identification of possible
threats
For every category that is thought to be sensitive, the business must
identify the kind of threats that are present (Androulidakis, 2016).
However, they can wary of third parties to steal their data. Hence
they must watch out for various insider threats like disrupted
workers and negligent employees.
Analyzing security holes
and additional
vulnerabilities
The safeguarding processes must be analyzed and find out the
weaknesses and loopholes must be found out.
Appraising level of risk
related to all vulnerability
The vulnerabilities must be ranked utilizing factors like likelihood
of the occurring attack damage-extent that could suffer. This also
includes the time period and work they require to recover.
Get various
countermeasures in place
Lastly the operational security is to develop and deploy plan to
eradicate threats and mitigate various risks. It can involve updating
of hardware and generating new policies about sensitive data or train
people with sound company policies and security policies of Aconex
(Chambers et al., 2015). The countermeasures have been simple and
straightforward. Further, employees have been able to implement
measures needed on their counter-part with or without extra training.
5SECURITY AND FORENSICS
2.2. Best practices for operational security:
The following best practices are to be followed to implement comprehensive and robust
operational security programs.
Practices Discussion
Implementing precise
change management
processes
This must be followed by the employees of the PatentWorks Ltd while
any changes in network are to be performed. Every change must be
controlled and logged such that they can be audited and monitored
(Conheady & Leverett, 2014).
Restricting access to
network devices
through AAA
authentication
This is used as a thumb rule for accessing and sharing data.
Providing employees
with minimum access
It is necessary for performing tasks. The principle of minimum leverage
is to be practiced.
Implementing dual
control
It is to be assures that who has been working on their network and not the
exact person who is in charge of the security (Esposito et al., 2016).
Automating activities
to decrease necessity
of human intervention
It must be reminded that human beings are the weakest link for initiatives
of operational security of any organization. The reason is that they can
make mistakes and overlook details bypass processes and forget things.
Disaster recovery
planning and incident
response
They are always crucial components towards sound security posture.
Though operational security measures have been robust, one can have
plans to recognize risks, react to them and do away with potential
2.2. Best practices for operational security:
The following best practices are to be followed to implement comprehensive and robust
operational security programs.
Practices Discussion
Implementing precise
change management
processes
This must be followed by the employees of the PatentWorks Ltd while
any changes in network are to be performed. Every change must be
controlled and logged such that they can be audited and monitored
(Conheady & Leverett, 2014).
Restricting access to
network devices
through AAA
authentication
This is used as a thumb rule for accessing and sharing data.
Providing employees
with minimum access
It is necessary for performing tasks. The principle of minimum leverage
is to be practiced.
Implementing dual
control
It is to be assures that who has been working on their network and not the
exact person who is in charge of the security (Esposito et al., 2016).
Automating activities
to decrease necessity
of human intervention
It must be reminded that human beings are the weakest link for initiatives
of operational security of any organization. The reason is that they can
make mistakes and overlook details bypass processes and forget things.
Disaster recovery
planning and incident
response
They are always crucial components towards sound security posture.
Though operational security measures have been robust, one can have
plans to recognize risks, react to them and do away with potential
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY AND FORENSICS
damages (Ab Rahman & Choo, 2015).
Thus risk management has been involving ability to identify vulnerabilities and threats prior
they turn out to be problems. It is a proven fact that operational security forces the managers in
diving deeply to their operations and then figure out where the information could be easily breached.
Viewing the operations from the perspective of malicious third-party managers are allowed to spot
various vulnerabilities missed by them. This helps them implementing the exact countermeasures for
protecting sensitive information.
3. Conducting Business Continuity and Disaster Recovery Plan for PatentWorks
Ltd:
3.1. Business Continuity Plan:
This plan helps in assuring that business process are able to continue during period of
disaster or emergency. This takes plan during any fire or any other situation while business never
takes place under normal situation (McClain et al., 2015). The business requires looking at every
potential threat and devising BCPs to assure various continued operations that the threat can turn out
to be reality. The business continuity plan for PatentWorks Ltd has been involving various steps.
Assessment of organizational threats
List of preliminary activities needed to put operations of the company flowing.
Simply located contact information of management
Explaining of where the personnel must go as there is no disastrous event
Data about information backups and backup of organization site (Jaferian et al., 2014)
damages (Ab Rahman & Choo, 2015).
Thus risk management has been involving ability to identify vulnerabilities and threats prior
they turn out to be problems. It is a proven fact that operational security forces the managers in
diving deeply to their operations and then figure out where the information could be easily breached.
Viewing the operations from the perspective of malicious third-party managers are allowed to spot
various vulnerabilities missed by them. This helps them implementing the exact countermeasures for
protecting sensitive information.
3. Conducting Business Continuity and Disaster Recovery Plan for PatentWorks
Ltd:
3.1. Business Continuity Plan:
This plan helps in assuring that business process are able to continue during period of
disaster or emergency. This takes plan during any fire or any other situation while business never
takes place under normal situation (McClain et al., 2015). The business requires looking at every
potential threat and devising BCPs to assure various continued operations that the threat can turn out
to be reality. The business continuity plan for PatentWorks Ltd has been involving various steps.
Assessment of organizational threats
List of preliminary activities needed to put operations of the company flowing.
Simply located contact information of management
Explaining of where the personnel must go as there is no disastrous event
Data about information backups and backup of organization site (Jaferian et al., 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY AND FORENSICS
Maintaining collaboration among every facets of the organization
Buy-in from every employee in the organization
3.2. Development of Disaster Recovery Plan:
The plan is illustrated through the following table.
Assessment of potential
threats and various possible
reactions to them
The DR plan must consider entire spectrum of “potential
interrupters to business. Then a recovery plan must be spelt out
for the scenario. For instance as any cyber attack shuts down
one must have transit plan for that situation. The business should
anticipate potential disruptors that have been the most
probable. Cyber attack planning must be given precedence over
few natural disruptors in the planning (Elyas et al., 2015).
Business impact analysis
(BIA)
For effectively determining the DR priorities, every major
information system must e put through the business impact
analysis. It identifies and examines potential impacts like
reputation, contractual or legal, regulatory, safety or life or
economical of man-made or natural made events on business
operations.
Considering people There has been a common mistake done by various organizations
that DR plans have been focusing too much on technology and not
on process and people. IT is an enabler and one must never forget
to recover servers and data. The name of the critical people must be
identified who are charged with responding to crisis (Trappe, 2015).
Making updates Another major mistake done by businesses like PatentWorks Ltd is
Maintaining collaboration among every facets of the organization
Buy-in from every employee in the organization
3.2. Development of Disaster Recovery Plan:
The plan is illustrated through the following table.
Assessment of potential
threats and various possible
reactions to them
The DR plan must consider entire spectrum of “potential
interrupters to business. Then a recovery plan must be spelt out
for the scenario. For instance as any cyber attack shuts down
one must have transit plan for that situation. The business should
anticipate potential disruptors that have been the most
probable. Cyber attack planning must be given precedence over
few natural disruptors in the planning (Elyas et al., 2015).
Business impact analysis
(BIA)
For effectively determining the DR priorities, every major
information system must e put through the business impact
analysis. It identifies and examines potential impacts like
reputation, contractual or legal, regulatory, safety or life or
economical of man-made or natural made events on business
operations.
Considering people There has been a common mistake done by various organizations
that DR plans have been focusing too much on technology and not
on process and people. IT is an enabler and one must never forget
to recover servers and data. The name of the critical people must be
identified who are charged with responding to crisis (Trappe, 2015).
Making updates Another major mistake done by businesses like PatentWorks Ltd is

8SECURITY AND FORENSICS
that they never update their disaster recovery plans as changes are
made to the in internal systems. The DR plan is incomplete till they
have been considering every applications, systems and technologies
presently under use.
Priorities The DR plan requires to be tested regularly and individuals require
practicing those procedures. As not practiced properly the plan can
turn out to be effective.
Considering DRaaS During this consideration the providers must be asked how they
test or validate data recovery and workflows.
4. Covering legal issues pertaining to IT resources and privacy when operating in
New Zealand and Australia:
It consists of the following:
Competencies if Security Council of Australian Charter:
This security control should transform them to authority of world’s executive.
The secretary general of should increasingly provide submissions:
This must include various legal submissions under Article 99 and invite it to address
mandatory orders under Chapter 5 of the Charter (Watson & Dehghantanha, 2016).
Recommendatory competencies of Australia’s General Assembly:
This must be assimilated with processes of formation of global customary law. Secretary
Generals should use Annual Reports to General Assembly for drawing their attention towards threats
that they never update their disaster recovery plans as changes are
made to the in internal systems. The DR plan is incomplete till they
have been considering every applications, systems and technologies
presently under use.
Priorities The DR plan requires to be tested regularly and individuals require
practicing those procedures. As not practiced properly the plan can
turn out to be effective.
Considering DRaaS During this consideration the providers must be asked how they
test or validate data recovery and workflows.
4. Covering legal issues pertaining to IT resources and privacy when operating in
New Zealand and Australia:
It consists of the following:
Competencies if Security Council of Australian Charter:
This security control should transform them to authority of world’s executive.
The secretary general of should increasingly provide submissions:
This must include various legal submissions under Article 99 and invite it to address
mandatory orders under Chapter 5 of the Charter (Watson & Dehghantanha, 2016).
Recommendatory competencies of Australia’s General Assembly:
This must be assimilated with processes of formation of global customary law. Secretary
Generals should use Annual Reports to General Assembly for drawing their attention towards threats
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY AND FORENSICS
towards human security and to point out policies and recommendations. These aspects trough a
widespread consensus gets crystallized to norms of global customary law.
Role of International Court of Justice:
Lastly, there is the interpretative role of International Court of Justice for clarifying
responsibilities of the law to meet situations of current society. This includes the general assembly
and Security Council using their competencies for submitting requests to International Court of
Justice regarding Advisory Opinions. These are done over duties of states for cooperating for
protection and security of information of business (Giannoukos et al., 2015).
Further, according to Comprehensive National Cyber security Initiative three mutually
reinforcing initiatives must be undertaken.
Establishing front line of defense against current immediate threats:
Developing or creating shared situational awareness of network threats, events and
vulnerabilities under Federal Government and at last tribal, local and state governments. This also
includes private sector partners and ability to react fast to decrease present vulnerabilities and protect
intrusions.
Defending against complete spectrum of threats:
Developing of Australia’s counterintelligence abilities and rise security of supply chain
regarding primary information technologies.
Strengthening future of cyber security environment:
It includes of expanding of cyber education, redirecting and coordinating research and development
efforts around Federal Government.
towards human security and to point out policies and recommendations. These aspects trough a
widespread consensus gets crystallized to norms of global customary law.
Role of International Court of Justice:
Lastly, there is the interpretative role of International Court of Justice for clarifying
responsibilities of the law to meet situations of current society. This includes the general assembly
and Security Council using their competencies for submitting requests to International Court of
Justice regarding Advisory Opinions. These are done over duties of states for cooperating for
protection and security of information of business (Giannoukos et al., 2015).
Further, according to Comprehensive National Cyber security Initiative three mutually
reinforcing initiatives must be undertaken.
Establishing front line of defense against current immediate threats:
Developing or creating shared situational awareness of network threats, events and
vulnerabilities under Federal Government and at last tribal, local and state governments. This also
includes private sector partners and ability to react fast to decrease present vulnerabilities and protect
intrusions.
Defending against complete spectrum of threats:
Developing of Australia’s counterintelligence abilities and rise security of supply chain
regarding primary information technologies.
Strengthening future of cyber security environment:
It includes of expanding of cyber education, redirecting and coordinating research and development
efforts around Federal Government.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
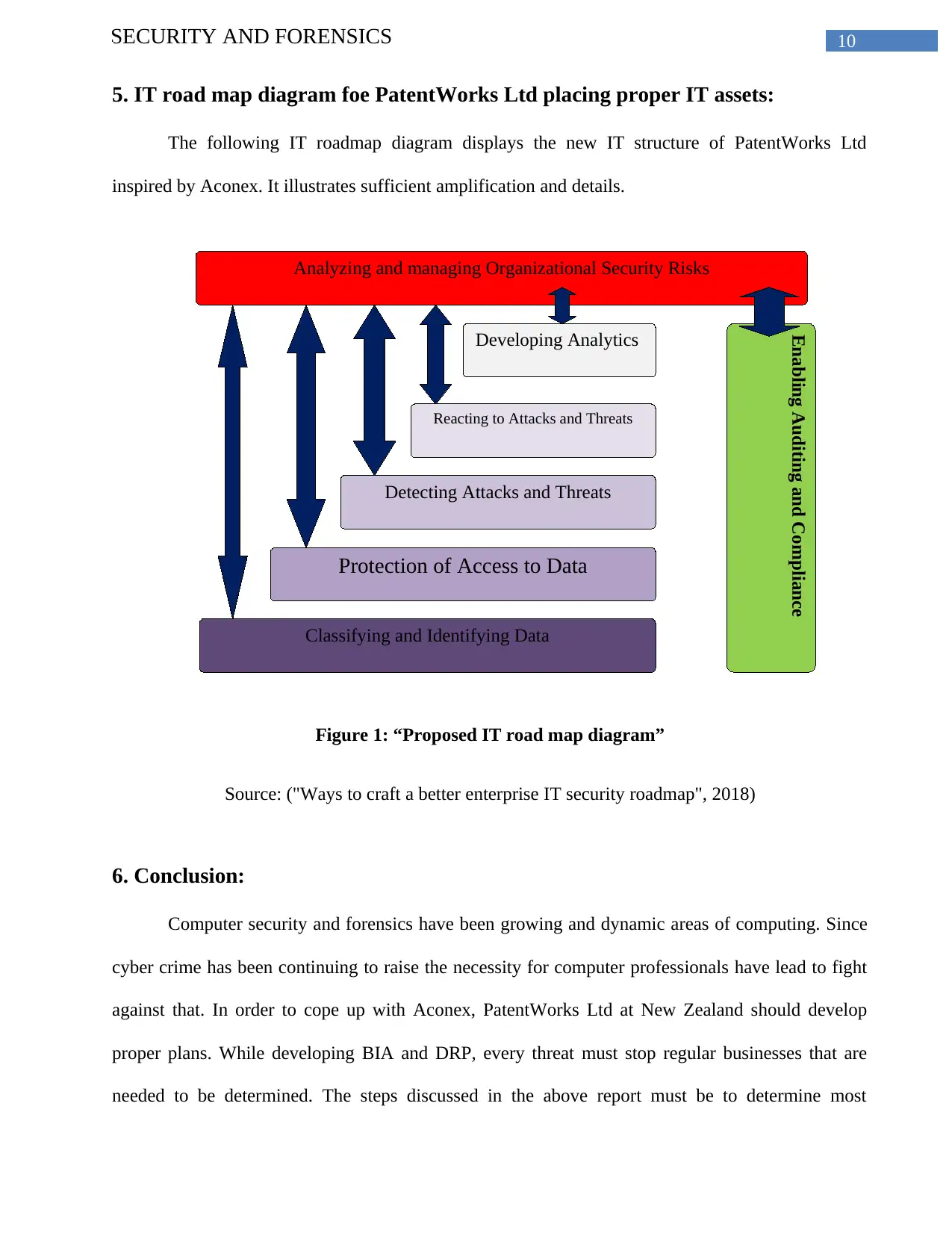
10SECURITY AND FORENSICS
Analyzing and managing Organizational Security Risks
Developing Analytics
Reacting to Attacks and Threats
Detecting Attacks and Threats
Protection of Access to Data
Classifying and Identifying Data
Enabling Auditing and Compliance
5. IT road map diagram foe PatentWorks Ltd placing proper IT assets:
The following IT roadmap diagram displays the new IT structure of PatentWorks Ltd
inspired by Aconex. It illustrates sufficient amplification and details.
Figure 1: “Proposed IT road map diagram”
Source: ("Ways to craft a better enterprise IT security roadmap", 2018)
6. Conclusion:
Computer security and forensics have been growing and dynamic areas of computing. Since
cyber crime has been continuing to raise the necessity for computer professionals have lead to fight
against that. In order to cope up with Aconex, PatentWorks Ltd at New Zealand should develop
proper plans. While developing BIA and DRP, every threat must stop regular businesses that are
needed to be determined. The steps discussed in the above report must be to determine most
Analyzing and managing Organizational Security Risks
Developing Analytics
Reacting to Attacks and Threats
Detecting Attacks and Threats
Protection of Access to Data
Classifying and Identifying Data
Enabling Auditing and Compliance
5. IT road map diagram foe PatentWorks Ltd placing proper IT assets:
The following IT roadmap diagram displays the new IT structure of PatentWorks Ltd
inspired by Aconex. It illustrates sufficient amplification and details.
Figure 1: “Proposed IT road map diagram”
Source: ("Ways to craft a better enterprise IT security roadmap", 2018)
6. Conclusion:
Computer security and forensics have been growing and dynamic areas of computing. Since
cyber crime has been continuing to raise the necessity for computer professionals have lead to fight
against that. In order to cope up with Aconex, PatentWorks Ltd at New Zealand should develop
proper plans. While developing BIA and DRP, every threat must stop regular businesses that are
needed to be determined. The steps discussed in the above report must be to determine most

11SECURITY AND FORENSICS
important tasks needed to carry on operations. It should include the necessary people and tools and
information required to continue operation. There must be list of people within management and
contact information involved in BIA and DR plan. The people must have their information of contact
at home. Since it is impossible to access to the office, they must be able to contact others and make
plans to resume operations at home offices and various offsite locations. It includes usage of data
backup and plans of disaster recovery. Further, various people must be included to create BIA and
DR Plan. The responsibility to create a BIA and DR plan must not fall on any one individual alone.
As per as legal issues towards IT resources and security is concerned while operating in Australia
and New Zealand the capacity and readiness of cyber security workforce for meeting the cyber
security mission is to be considered by PatentWorks Ltd. Proper training must be given to abide by
the law of cyber security and challenges must be issued during the provision of such training.
important tasks needed to carry on operations. It should include the necessary people and tools and
information required to continue operation. There must be list of people within management and
contact information involved in BIA and DR plan. The people must have their information of contact
at home. Since it is impossible to access to the office, they must be able to contact others and make
plans to resume operations at home offices and various offsite locations. It includes usage of data
backup and plans of disaster recovery. Further, various people must be included to create BIA and
DR Plan. The responsibility to create a BIA and DR plan must not fall on any one individual alone.
As per as legal issues towards IT resources and security is concerned while operating in Australia
and New Zealand the capacity and readiness of cyber security workforce for meeting the cyber
security mission is to be considered by PatentWorks Ltd. Proper training must be given to abide by
the law of cyber security and challenges must be issued during the provision of such training.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.