Analysis of PayTM: Threats, Vulnerabilities, and Mitigation Strategies
VerifiedAdded on 2020/03/23
|23
|5949
|89
Report
AI Summary
This report provides a comprehensive analysis of PayTM, a prominent e-commerce and payments bank company in India. It begins with an introduction to PayTM's business model, highlighting its role in the Indian market and its integration of mobile wallets and online payments. The report then delves into the decomposition of PayTM, detailing its services, including e-commerce transactions, bill payments, and collaborations with companies like UBER and IRCTC. The impact of PayTM on the Indian economy and its role in promoting digital transactions are also discussed. The core of the report focuses on the threats associated with PayTM, including human element vulnerabilities, e-commerce server risks, and malicious code attacks such as viruses, worms, Trojan horses, and logic bombs. Transmission threats, including denial-of-service attacks and ping of death, are also examined. Finally, the report explores various control measures and security strategies to mitigate these threats, offering insights into protecting PayTM and its users from cyber security risks.

Running head: PAYTM
PayTM
Name of the Student
Name of the University
Author’s note
PayTM
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PAYTM
Table of Contents
1. Introduction................................................................................................................2
2. Decomposition of PayTM..........................................................................................2
PayTM in India Development....................................................................................3
3. Threats associated with PayTM.................................................................................4
4. Vulnerabilities associated with PayTM...................................................................11
5. Control measures to mitigate the threats associated with PayTM...........................14
6. Conclusion................................................................................................................18
7. References................................................................................................................19
PAYTM
Table of Contents
1. Introduction................................................................................................................2
2. Decomposition of PayTM..........................................................................................2
PayTM in India Development....................................................................................3
3. Threats associated with PayTM.................................................................................4
4. Vulnerabilities associated with PayTM...................................................................11
5. Control measures to mitigate the threats associated with PayTM...........................14
6. Conclusion................................................................................................................18
7. References................................................................................................................19

2
PAYTM
1. Introduction
PayTM is e-commerce enterprise and is Payments Bank Company. Their company is
purely B2C e-commerce based.
This report will highlight the decomposition of the PayTM application. PayTM’s
impact on Indian society will be elaborated in details. Various kinds of threats associated
with PayTM will be discussed in details. Along with the threats, the vulnerabilities will be
showcased in the report. The security measures will be well discussed as well in the report.
2. Decomposition of PayTM
The company named One97 is one of the e-commerce enterprises and they cater the
services like mobile wallets, OTA bookings and revenue payments generation. PayTM is
apart of this organization. PayTM is not only e-commerce enterprise, rather it is Payments
Bank Company (Akazue 2015). They utilize a single commission system model to conduct
their business activities and their business is purely B2C e-commerce based. PayTM provides
their service via their websites and mobile applications, they integrate wallet and payment on
the online platform. The customers choose products according to their convenience, put it in
the cart, apply promo codes and finally order them. Later the seller prepares the item for
dispatch and then ships it to the customer. The whole shipping procedure is carried out by
courier service. The seller gets his revenue by selling the item to the customers. PayTM
charges only twenty percent of the revenues of the product and in turn provide customers to
the sellers. The other business that is carried out by PayTM is payments bank.
PayTM can be utilized for paying the utility bills. The customers pay for the DTH
bills, phone bills, electricity bills via the e-wallet facility of PayTM. The customers are not
limited to that, they pay their loans and home EMI, insurance premiums via e-wallets of
PAYTM
1. Introduction
PayTM is e-commerce enterprise and is Payments Bank Company. Their company is
purely B2C e-commerce based.
This report will highlight the decomposition of the PayTM application. PayTM’s
impact on Indian society will be elaborated in details. Various kinds of threats associated
with PayTM will be discussed in details. Along with the threats, the vulnerabilities will be
showcased in the report. The security measures will be well discussed as well in the report.
2. Decomposition of PayTM
The company named One97 is one of the e-commerce enterprises and they cater the
services like mobile wallets, OTA bookings and revenue payments generation. PayTM is
apart of this organization. PayTM is not only e-commerce enterprise, rather it is Payments
Bank Company (Akazue 2015). They utilize a single commission system model to conduct
their business activities and their business is purely B2C e-commerce based. PayTM provides
their service via their websites and mobile applications, they integrate wallet and payment on
the online platform. The customers choose products according to their convenience, put it in
the cart, apply promo codes and finally order them. Later the seller prepares the item for
dispatch and then ships it to the customer. The whole shipping procedure is carried out by
courier service. The seller gets his revenue by selling the item to the customers. PayTM
charges only twenty percent of the revenues of the product and in turn provide customers to
the sellers. The other business that is carried out by PayTM is payments bank.
PayTM can be utilized for paying the utility bills. The customers pay for the DTH
bills, phone bills, electricity bills via the e-wallet facility of PayTM. The customers are not
limited to that, they pay their loans and home EMI, insurance premiums via e-wallets of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PAYTM
PayTM. The customers first transfer their money from their respective bank to their
respective e-wallets of PayTM. The transactions are then continued through e-wallets. Other
than that they sell gold via their websites. PayTM acquires a high commission while
customers buy any items from their site (Akazue, Aghaulor and Ajenaghughrure 2015). The
customers also prefer to pay their bills online via PayTM as they can get discounts or
coupons on each purchase. PayTM also charges a minimal fee while customers want to use
promo codes or coupons. Once they put the money from the bank to their e-wallet of PayTM
they will not be able to put it back to their bank account. The customers can use the e-wallet
money according to their convenience at any time.
The e-wallet is a source of income for PayTM. In India, at the time of
dfemonetization, PayTM e-wallet comes handy and then the customers use the money of their
e-wallet account to purchase their valuables and everything (Akazue 2015). PayTM has
collaborated with UBER and IRCTC. The customers can now travel UBER cars from their
PayTM e-wallet. They cater around about three percent discount to the transaction total and
the rest they pay the rest to the sellers.
PayTM in India Development
The e-commerce industry has flourished to a great extent due to the advent of PayTM
and with the usage of smartphones, tablets the e-commerce has become more predominant.
The compound annual growth has increased in India up to thirty-four percent since the year
2019 solely because of PayTM. This is the reason, the public sectors are adopting e-
commerce to enhance their activities (Aljawarneh 2015). PayTM is making India digital and
the India Prime Minister advised Indian citizens to use PayTM at the time of demonetization.
The Prime Minister motive is to make digital and along with that, he wants to make India
corruption free. Thus he has taken the approach to use PayTM and also suggest everyone.
The Government wants to impose a right amount of tax on every item and if anyone pays via
PAYTM
PayTM. The customers first transfer their money from their respective bank to their
respective e-wallets of PayTM. The transactions are then continued through e-wallets. Other
than that they sell gold via their websites. PayTM acquires a high commission while
customers buy any items from their site (Akazue, Aghaulor and Ajenaghughrure 2015). The
customers also prefer to pay their bills online via PayTM as they can get discounts or
coupons on each purchase. PayTM also charges a minimal fee while customers want to use
promo codes or coupons. Once they put the money from the bank to their e-wallet of PayTM
they will not be able to put it back to their bank account. The customers can use the e-wallet
money according to their convenience at any time.
The e-wallet is a source of income for PayTM. In India, at the time of
dfemonetization, PayTM e-wallet comes handy and then the customers use the money of their
e-wallet account to purchase their valuables and everything (Akazue 2015). PayTM has
collaborated with UBER and IRCTC. The customers can now travel UBER cars from their
PayTM e-wallet. They cater around about three percent discount to the transaction total and
the rest they pay the rest to the sellers.
PayTM in India Development
The e-commerce industry has flourished to a great extent due to the advent of PayTM
and with the usage of smartphones, tablets the e-commerce has become more predominant.
The compound annual growth has increased in India up to thirty-four percent since the year
2019 solely because of PayTM. This is the reason, the public sectors are adopting e-
commerce to enhance their activities (Aljawarneh 2015). PayTM is making India digital and
the India Prime Minister advised Indian citizens to use PayTM at the time of demonetization.
The Prime Minister motive is to make digital and along with that, he wants to make India
corruption free. Thus he has taken the approach to use PayTM and also suggest everyone.
The Government wants to impose a right amount of tax on every item and if anyone pays via
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PAYTM
PayTM then it will be impossible for the anyone to evade tax, every transaction of money
will be recorded and this data will be available online and in the database of PayTM. Thus as
the transaction will be recorded everytime the corruption will significantly reduce (Awan and
Memon 2016). Thus PayTM has made significant impacts on the Indian economy and this
software is gradually becoming famous at every corner of India.It is hoped the whole India
will digitalise with the aid of PayTM.
Fig 1: PayTM and its services
(Source: Awan and Memon 2016, pp-425)
3. Threats associated with PayTM
The threats associated with e-commerce are as follows-
Human elements
The main motto of the business owners must be to secure their workplace first and
PayTM is no exception. PayTM may have the highest security architecture but have to
PAYTM
PayTM then it will be impossible for the anyone to evade tax, every transaction of money
will be recorded and this data will be available online and in the database of PayTM. Thus as
the transaction will be recorded everytime the corruption will significantly reduce (Awan and
Memon 2016). Thus PayTM has made significant impacts on the Indian economy and this
software is gradually becoming famous at every corner of India.It is hoped the whole India
will digitalise with the aid of PayTM.
Fig 1: PayTM and its services
(Source: Awan and Memon 2016, pp-425)
3. Threats associated with PayTM
The threats associated with e-commerce are as follows-
Human elements
The main motto of the business owners must be to secure their workplace first and
PayTM is no exception. PayTM may have the highest security architecture but have to

5
PAYTM
consider the insiders. The insiders may steal the vital information of the system and the
database also there can be another kind of data breach as well. The data can be leaked and the
whole system and the database will be vulnerable to threats. Again, the employees show
laziness and they do not bother installing security software in their system. The lack of
antivirus software can put the database in risks and so the important data like customers' data
can be at risk as well. Also, some employees do not want to change because so they do not
install the software (Becker, Alper and Lee 2014). Even they do not want to change the
operating system, hardware and software components as well, this leads to the disruption and
thus the system becomes vulnerable to threats and risks. That is why PayTMneds to take
proactive steps to mitigate those risks related to human elements.
Threats related to e-commerce servers
PayTM include all the sensitive information of the customers alongside the sensitive
information of the employees. The intruders garner that information and exploit the system
for their advantages. Thus the hackers carried out their attacks via the ransomware and
malware. The attack also involves the DDoS attacks and phishing schemes. By means of
phishing the intruders acquire the personal information of the customers and in this way, the
customers' bank account details can be hacked. Even the DDoS attacks are equally
dangerous, the authorized users will not be allowed to access their own system. The other
type of threats that is related to the server is a technological failure of the system. The
computer system can fail due to the loss of packets (Deshmukh, Chhangani and Thampi
2016). The weak network configuration can be the cause of the failure as well. Again
sometimes the software codes on basis of which a software is developed get corrupted or
bugs can be found while the software is tested. Therefore, PayTM must be aware of their
website as well as the mobile site. Misconfiguration can cause harm to the severe extent to
these companies. The customers can lose their hard earned money by this misconfiguration or
PAYTM
consider the insiders. The insiders may steal the vital information of the system and the
database also there can be another kind of data breach as well. The data can be leaked and the
whole system and the database will be vulnerable to threats. Again, the employees show
laziness and they do not bother installing security software in their system. The lack of
antivirus software can put the database in risks and so the important data like customers' data
can be at risk as well. Also, some employees do not want to change because so they do not
install the software (Becker, Alper and Lee 2014). Even they do not want to change the
operating system, hardware and software components as well, this leads to the disruption and
thus the system becomes vulnerable to threats and risks. That is why PayTMneds to take
proactive steps to mitigate those risks related to human elements.
Threats related to e-commerce servers
PayTM include all the sensitive information of the customers alongside the sensitive
information of the employees. The intruders garner that information and exploit the system
for their advantages. Thus the hackers carried out their attacks via the ransomware and
malware. The attack also involves the DDoS attacks and phishing schemes. By means of
phishing the intruders acquire the personal information of the customers and in this way, the
customers' bank account details can be hacked. Even the DDoS attacks are equally
dangerous, the authorized users will not be allowed to access their own system. The other
type of threats that is related to the server is a technological failure of the system. The
computer system can fail due to the loss of packets (Deshmukh, Chhangani and Thampi
2016). The weak network configuration can be the cause of the failure as well. Again
sometimes the software codes on basis of which a software is developed get corrupted or
bugs can be found while the software is tested. Therefore, PayTM must be aware of their
website as well as the mobile site. Misconfiguration can cause harm to the severe extent to
these companies. The customers can lose their hard earned money by this misconfiguration or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PAYTM
computer failure. There is also a risk of operating system failure as well. The Windows
operating system can fail, can get corrupted, can get attacked by the virus so the unstable
operating system is another failure that must be taken into account. Again the-the threats
associated with the hackers can be classified into the active attack and passive attack (Europe
2014). The malicious activities include the monitoring the insecure transmission over the
Internet and so this a passive attack, the other attack is the active attack where the data
transmission is not only monitored but also it is modified for selfish needs of the intruders.
Malicious Code Attacks
Viruses and Worms
The virus and the worms are the two major threarts or better can be said for the
enemies for the ecommerce and the electronic payment enterpriss like PayTM. A worm
basically spreads without any human interaction and it replicates itself and causes harm to
greater extent whereas the virus is the dangerous threat which spread by the hackers and
though it is less harmful compared to the worms yet the virus can be equally devastating as
well. The virus requires a file attached and if that file is opened somehow the virus spreads
into the system (Fetscher 2016). The virus makes serious damage to the files stored on the
hard disk, so sometimes the hard drive requires formatting to get back to the initial scenario.
In this way, the PayTM can face huge data loss due to virus attacks. Also due to the worm's
attacks, many computer systems can stop functioning thus affecting the e-commerce server
like PayTM server. Due to the ceratin shut down of systems the customers may face issues
while they are transacting money or carrying on online shopping.
Trojan Horses
PAYTM
computer failure. There is also a risk of operating system failure as well. The Windows
operating system can fail, can get corrupted, can get attacked by the virus so the unstable
operating system is another failure that must be taken into account. Again the-the threats
associated with the hackers can be classified into the active attack and passive attack (Europe
2014). The malicious activities include the monitoring the insecure transmission over the
Internet and so this a passive attack, the other attack is the active attack where the data
transmission is not only monitored but also it is modified for selfish needs of the intruders.
Malicious Code Attacks
Viruses and Worms
The virus and the worms are the two major threarts or better can be said for the
enemies for the ecommerce and the electronic payment enterpriss like PayTM. A worm
basically spreads without any human interaction and it replicates itself and causes harm to
greater extent whereas the virus is the dangerous threat which spread by the hackers and
though it is less harmful compared to the worms yet the virus can be equally devastating as
well. The virus requires a file attached and if that file is opened somehow the virus spreads
into the system (Fetscher 2016). The virus makes serious damage to the files stored on the
hard disk, so sometimes the hard drive requires formatting to get back to the initial scenario.
In this way, the PayTM can face huge data loss due to virus attacks. Also due to the worm's
attacks, many computer systems can stop functioning thus affecting the e-commerce server
like PayTM server. Due to the ceratin shut down of systems the customers may face issues
while they are transacting money or carrying on online shopping.
Trojan Horses
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PAYTM
PayTM requires updating of the server and the database that is why sometimes they
download patches for the software. To enhance the security and also to enhance the business
operations sometimes the e-commerce organisations like PayTM downloaded software to
scale up the business operations, however, if that software is not downloaded from any
trusted website then there can be a chance of Trojan virus attack. Also along with that, the
defence mechanisms should proactively work in these scenarios. Therefore, there is a chance
of data breach all the time (Flanagin et al. 2014). If the employees of the organization by
mistake explore the software, the virus will spread throughout the system and make it
vulnerable. They will steal all the vital and sensitive operation of the database.
Logic Bombs
A logic bomb is somewhat similar to Trojan Horse and works in an almost similar
way. This virus software release the rogue code after an application is deployed in the e-
commerce server after a significant amount of time.
Transmission Threats
Denial of Service Attacks
The Denial of Service Attack is responsible for denying authorised access of the
users. The authorized users access the system and found that the system has been hacked and
is being controlled by any other person or individuals, the intruders if access the PayTM
server, then this can be disastrous. The customer's bank account details and the account
money and the e-wallet money will be compromised as a result of the attack. They can leak
the sensitive information, they can even use to shut down the server. The shutdown of the
server will cease all the information of the PayTM and the company can face huge loss for
that (Franco 2014). There is another kind of Denial of Service Attack. In this case, one master
PAYTM
PayTM requires updating of the server and the database that is why sometimes they
download patches for the software. To enhance the security and also to enhance the business
operations sometimes the e-commerce organisations like PayTM downloaded software to
scale up the business operations, however, if that software is not downloaded from any
trusted website then there can be a chance of Trojan virus attack. Also along with that, the
defence mechanisms should proactively work in these scenarios. Therefore, there is a chance
of data breach all the time (Flanagin et al. 2014). If the employees of the organization by
mistake explore the software, the virus will spread throughout the system and make it
vulnerable. They will steal all the vital and sensitive operation of the database.
Logic Bombs
A logic bomb is somewhat similar to Trojan Horse and works in an almost similar
way. This virus software release the rogue code after an application is deployed in the e-
commerce server after a significant amount of time.
Transmission Threats
Denial of Service Attacks
The Denial of Service Attack is responsible for denying authorised access of the
users. The authorized users access the system and found that the system has been hacked and
is being controlled by any other person or individuals, the intruders if access the PayTM
server, then this can be disastrous. The customer's bank account details and the account
money and the e-wallet money will be compromised as a result of the attack. They can leak
the sensitive information, they can even use to shut down the server. The shutdown of the
server will cease all the information of the PayTM and the company can face huge loss for
that (Franco 2014). There is another kind of Denial of Service Attack. In this case, one master
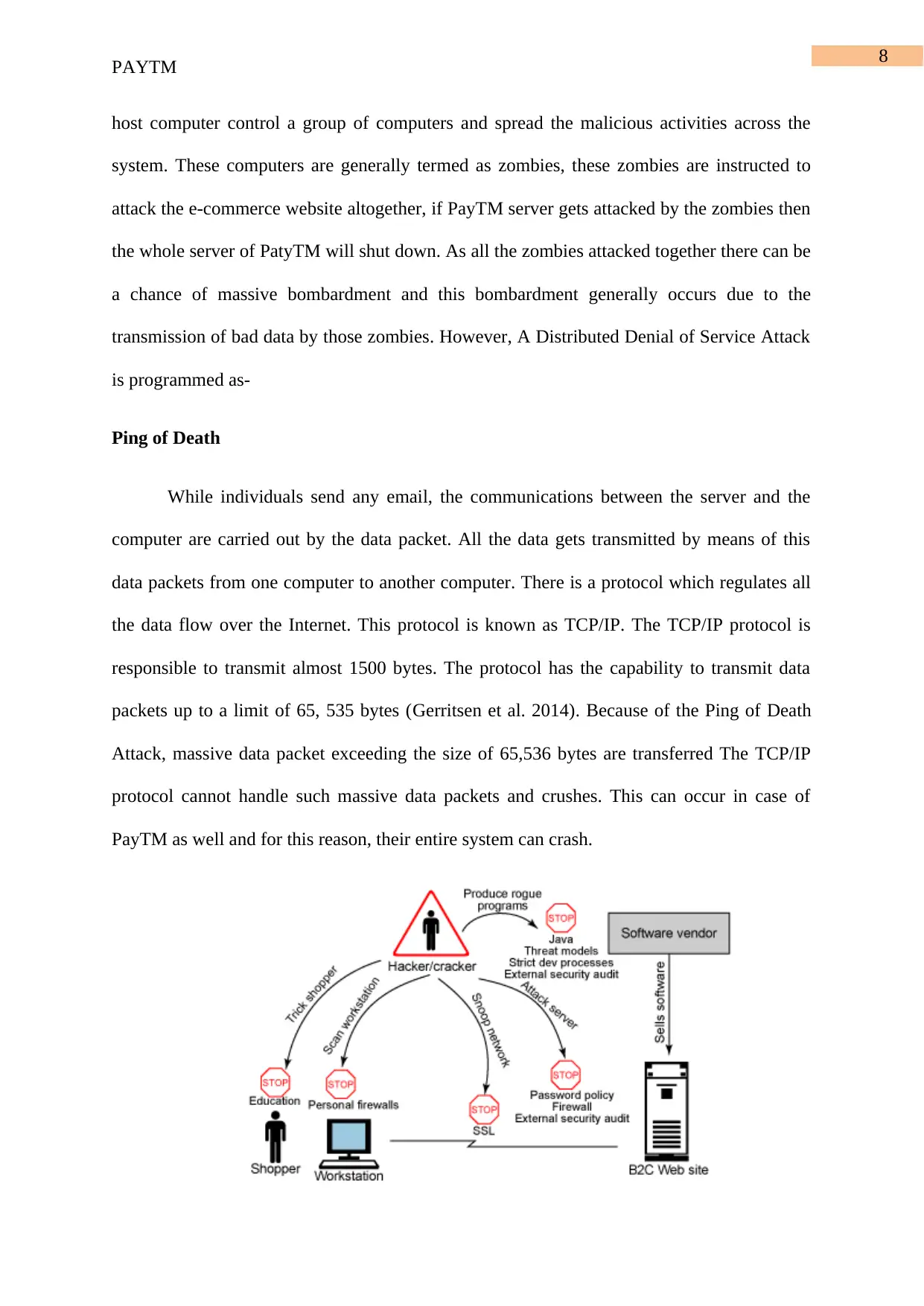
8
PAYTM
host computer control a group of computers and spread the malicious activities across the
system. These computers are generally termed as zombies, these zombies are instructed to
attack the e-commerce website altogether, if PayTM server gets attacked by the zombies then
the whole server of PatyTM will shut down. As all the zombies attacked together there can be
a chance of massive bombardment and this bombardment generally occurs due to the
transmission of bad data by those zombies. However, A Distributed Denial of Service Attack
is programmed as-
Ping of Death
While individuals send any email, the communications between the server and the
computer are carried out by the data packet. All the data gets transmitted by means of this
data packets from one computer to another computer. There is a protocol which regulates all
the data flow over the Internet. This protocol is known as TCP/IP. The TCP/IP protocol is
responsible to transmit almost 1500 bytes. The protocol has the capability to transmit data
packets up to a limit of 65, 535 bytes (Gerritsen et al. 2014). Because of the Ping of Death
Attack, massive data packet exceeding the size of 65,536 bytes are transferred The TCP/IP
protocol cannot handle such massive data packets and crushes. This can occur in case of
PayTM as well and for this reason, their entire system can crash.
PAYTM
host computer control a group of computers and spread the malicious activities across the
system. These computers are generally termed as zombies, these zombies are instructed to
attack the e-commerce website altogether, if PayTM server gets attacked by the zombies then
the whole server of PatyTM will shut down. As all the zombies attacked together there can be
a chance of massive bombardment and this bombardment generally occurs due to the
transmission of bad data by those zombies. However, A Distributed Denial of Service Attack
is programmed as-
Ping of Death
While individuals send any email, the communications between the server and the
computer are carried out by the data packet. All the data gets transmitted by means of this
data packets from one computer to another computer. There is a protocol which regulates all
the data flow over the Internet. This protocol is known as TCP/IP. The TCP/IP protocol is
responsible to transmit almost 1500 bytes. The protocol has the capability to transmit data
packets up to a limit of 65, 535 bytes (Gerritsen et al. 2014). Because of the Ping of Death
Attack, massive data packet exceeding the size of 65,536 bytes are transferred The TCP/IP
protocol cannot handle such massive data packets and crushes. This can occur in case of
PayTM as well and for this reason, their entire system can crash.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PAYTM
Fig 2: PayTM Threats
(Source: Gerritsen et al. 2014, pp- 169-235)
SYN Flooding
SYN Flooding involves the connectivity between the client and server computer in the
PayTM premises. A connection is made via message acknowledgement. At first, the client
computer sends messages, the server computer, in turn, sends acknowledgement regarding
the same. This is known as ACK (synchronisation) message. In order to successfully
complete the connectivity, the client computer sends ACK message to the server. At this
point, the e-commerce server becomes vulnerable to attack (Hossain 2016). This remains a
half-open connection and taking advantage of this half-open connection, phony messages can
be sent to the PayTM server. These Phony Messages are responsible for overloading the
server's memory and also the process power thus leads to system crash.
Threats to PayTM customers
The threats associated with the PayTM servers are-
Phishing Attacks
Phishing is generally carried out by intruders to hack individuals accounts. In this
scenario, the effect can be devastating. As PayTm contains the bank details as well as money
in the e-wallet. The intruders copy the HTML code of PayTM and can develop a look-alike
PayTM website. The customers unknowingly can enter the credentials into that website and
can fall into the trap.If the customers enter the credentials bank details then there will be a
chance of losing hard earned money. This can cause havoc inside the PayTM. They will lose
the customer base, can lose the reputation and ultimately this may lead to disaster. Also, the
intruders carry out their phishing attacks via websites (Jotwani and Dutta 2016). The hackers
PAYTM
Fig 2: PayTM Threats
(Source: Gerritsen et al. 2014, pp- 169-235)
SYN Flooding
SYN Flooding involves the connectivity between the client and server computer in the
PayTM premises. A connection is made via message acknowledgement. At first, the client
computer sends messages, the server computer, in turn, sends acknowledgement regarding
the same. This is known as ACK (synchronisation) message. In order to successfully
complete the connectivity, the client computer sends ACK message to the server. At this
point, the e-commerce server becomes vulnerable to attack (Hossain 2016). This remains a
half-open connection and taking advantage of this half-open connection, phony messages can
be sent to the PayTM server. These Phony Messages are responsible for overloading the
server's memory and also the process power thus leads to system crash.
Threats to PayTM customers
The threats associated with the PayTM servers are-
Phishing Attacks
Phishing is generally carried out by intruders to hack individuals accounts. In this
scenario, the effect can be devastating. As PayTm contains the bank details as well as money
in the e-wallet. The intruders copy the HTML code of PayTM and can develop a look-alike
PayTM website. The customers unknowingly can enter the credentials into that website and
can fall into the trap.If the customers enter the credentials bank details then there will be a
chance of losing hard earned money. This can cause havoc inside the PayTM. They will lose
the customer base, can lose the reputation and ultimately this may lead to disaster. Also, the
intruders carry out their phishing attacks via websites (Jotwani and Dutta 2016). The hackers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
PAYTM
first send a mail, if the customers see the email and open it and click the link then they will be
sent to that phishing link, if they enter the personal details then there will be a chance of data
hack.
Data Packet Sniffing
When the customers are using PayTM in their smartphone the hackers use a sniffer to
gain entry into their insecure network. This leads to network hijack, and in this way the data
can be breached. The hackers take control of the network and the data flow, the sensitive
information transmitting via air via an insecure network can be compromised, in this way the
customers' privacy can be threatened.
IP spoofing
The attackers via IP spoofing change the source from where the data packet is
transmitting, from this it can be seen that the data packet is flowing from a source and that
source does not belong to the attackers. PayTM can be attacked via IP spoofing and it is
difficult to find out the real culprit (Khari and Singh 2014). The hackers can take advantage
of the scenario and can attack PayTM multiple times.
Port Scanning
The hackers via this port scanning can detect what type of service is running currently
in PayTM server and in this way the attackers will find out the flaws or weakness and try to
exploit that weakness to enter into the system and damage the system.
Backdoors
While the web developers develop a website for e-commerce and electronic payment,
they leave backdoors to keep an eye on the code developed, this helps the developers to
PAYTM
first send a mail, if the customers see the email and open it and click the link then they will be
sent to that phishing link, if they enter the personal details then there will be a chance of data
hack.
Data Packet Sniffing
When the customers are using PayTM in their smartphone the hackers use a sniffer to
gain entry into their insecure network. This leads to network hijack, and in this way the data
can be breached. The hackers take control of the network and the data flow, the sensitive
information transmitting via air via an insecure network can be compromised, in this way the
customers' privacy can be threatened.
IP spoofing
The attackers via IP spoofing change the source from where the data packet is
transmitting, from this it can be seen that the data packet is flowing from a source and that
source does not belong to the attackers. PayTM can be attacked via IP spoofing and it is
difficult to find out the real culprit (Khari and Singh 2014). The hackers can take advantage
of the scenario and can attack PayTM multiple times.
Port Scanning
The hackers via this port scanning can detect what type of service is running currently
in PayTM server and in this way the attackers will find out the flaws or weakness and try to
exploit that weakness to enter into the system and damage the system.
Backdoors
While the web developers develop a website for e-commerce and electronic payment,
they leave backdoors to keep an eye on the code developed, this helps the developers to

11
PAYTM
access the code quickly and process it whenever applicable (Lebeau et al. 2013). The
intruders take advantage of this loophole, the backdoors should be removed as soon as
possible before the website goes live, otherwise, e-commerce site like PayTM can severely
suffer from this backdoor.
4. Vulnerabilities associated with PayTM
i. The session identifiers which can be predictable: The Base 64 can be taken into
consideration by the hackers. The hackers also reverse engineer the algorithm for their selfish
needs.
ii. Overly dependent on client-side validation: The attackers can alter or modify the
browser settings and the browser history and disables JavaScript to skip the security and
validity process and can enter the system.
iii. SQL injection: The attackers can find out the SQL injection risks and the
vulnerabilities. They can exploit the PayTM database at will and can acquire the sensitive
information of the database (Niranjanamurthy and Chahar 2013).
iv. Unauthorised execution of operations: The attackers acquiring sensitive
information and session token can explore the system and the database making both the
system and the database vulnerable to attack. In this way, the system can lose authorization.
PAYTM
access the code quickly and process it whenever applicable (Lebeau et al. 2013). The
intruders take advantage of this loophole, the backdoors should be removed as soon as
possible before the website goes live, otherwise, e-commerce site like PayTM can severely
suffer from this backdoor.
4. Vulnerabilities associated with PayTM
i. The session identifiers which can be predictable: The Base 64 can be taken into
consideration by the hackers. The hackers also reverse engineer the algorithm for their selfish
needs.
ii. Overly dependent on client-side validation: The attackers can alter or modify the
browser settings and the browser history and disables JavaScript to skip the security and
validity process and can enter the system.
iii. SQL injection: The attackers can find out the SQL injection risks and the
vulnerabilities. They can exploit the PayTM database at will and can acquire the sensitive
information of the database (Niranjanamurthy and Chahar 2013).
iv. Unauthorised execution of operations: The attackers acquiring sensitive
information and session token can explore the system and the database making both the
system and the database vulnerable to attack. In this way, the system can lose authorization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
