CMP73001 Assignment 3: Vulnerability Assessment and BIA Report
VerifiedAdded on 2022/11/12
|18
|4153
|192
Report
AI Summary
This report details a penetration test and business impact analysis (BIA) conducted for MyHealth Company, a healthcare provider. The report begins with an introduction outlining the company's IT infrastructure and the need for robust security policies. Task 1 focuses on penetration testing, explaining its importance, phases, and various vulnerability types like SQL injections, XSS, and malware. Task 2 explores secure systems, networks, and applications, including VPN configurations and firewall/IDS implementations. Task 3 addresses personnel security, particularly social engineering threats. Task 4 presents the BIA, recommending RTO, RPO, and MTD values for key business processes and assessing the impact of disruptions. The report concludes by analyzing the effectiveness of implemented security controls and provides BIA tables before and after implementation.
Running Head: Pen test and BIA 0
Pen test and BIA
Report
Student name
Pen test and BIA
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pen test and BIA 1
Table of Contents
Introduction.................................................................................................................................................2
Task 1: Penetration testing..........................................................................................................................2
1-(a).........................................................................................................................................................2
1-(b).........................................................................................................................................................3
2-(a) Role 3 (i)..........................................................................................................................................3
2-(a) Role 3 (ii).........................................................................................................................................5
SQL Injections:.....................................................................................................................................5
Cross Site Scripting (XSS).....................................................................................................................5
Broken Authentication.........................................................................................................................5
3...............................................................................................................................................................5
Malware..............................................................................................................................................5
DDoS....................................................................................................................................................6
Social engineering................................................................................................................................6
Phishing...............................................................................................................................................6
Man-in-the-Middle..............................................................................................................................7
Ransomware........................................................................................................................................7
Task 2: Secure Systems / Networks / Applications......................................................................................8
1- Individual:............................................................................................................................................8
Remote access VPN:............................................................................................................................8
Site-to-site VPN:..................................................................................................................................8
2- Role1:..................................................................................................................................................9
Task 3: Managing personnel security........................................................................................................10
Task 4: Business Impact Analysis...............................................................................................................10
Task 5: Report template............................................................................................................................13
Table of Contents
Introduction.................................................................................................................................................2
Task 1: Penetration testing..........................................................................................................................2
1-(a).........................................................................................................................................................2
1-(b).........................................................................................................................................................3
2-(a) Role 3 (i)..........................................................................................................................................3
2-(a) Role 3 (ii).........................................................................................................................................5
SQL Injections:.....................................................................................................................................5
Cross Site Scripting (XSS).....................................................................................................................5
Broken Authentication.........................................................................................................................5
3...............................................................................................................................................................5
Malware..............................................................................................................................................5
DDoS....................................................................................................................................................6
Social engineering................................................................................................................................6
Phishing...............................................................................................................................................6
Man-in-the-Middle..............................................................................................................................7
Ransomware........................................................................................................................................7
Task 2: Secure Systems / Networks / Applications......................................................................................8
1- Individual:............................................................................................................................................8
Remote access VPN:............................................................................................................................8
Site-to-site VPN:..................................................................................................................................8
2- Role1:..................................................................................................................................................9
Task 3: Managing personnel security........................................................................................................10
Task 4: Business Impact Analysis...............................................................................................................10
Task 5: Report template............................................................................................................................13

Pen test and BIA 2
References.................................................................................................................................................14
References.................................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Pen test and BIA 3
Introduction
Health sector companies provide different service to their clients using information technologies. It is
necessary to use information technology to increase the efficiency of different processes, such as clinical
services, patient’s appointments, healthcare products, and many more. My health company provides
healthcare products, and clinical services as well as research of the cancer-related disease. There are
many other facilities for patients, which are provided by the company. The company has many
information assets to manage different facilities and services. The company requires security policies to
secure its information assets, such as computer systems, servers, internetworking devices, databases,
and many others. In addition, the Australian government provides cybersecurity policies to safe
information assets from different types of cybercrime (ACSC, 2017).
Information assets are having many security risks. Therefore, it is necessary to mitigate those risks
through mitigation strategies, which are provided by the government to all the companies, which are
using information assets for their various services (ACSC, 2019). Cyber-attacks make a huge impact on
many things on a company, such as reputation, financial loss, business continuity, and many others.
Information systems are required high security from the cyber-attacks ( Bradford, 2018). In addition,
information assets are having huge value. Therefore, it is highly required for strong security policies to
make them secure (Andrijcic & Horowitz, 2016).
Task 1: Penetration testing
1-(a)
Penetration testing uses to test websites to find different issues, which makes a huge impact of the
performance of websites, which is related to the reputation, and business of a company (guru99.com,
2019). In addition, Penetration testing is a type of security testing, which is used to find out insecure
areas of the website, system, and applications. It provides different vulnerabilities of the system, which
are the main cause of cyber-attacks (Arlitsch & Edelman, 2014). Vulnerability creates different risks for
the system, which contains data of patients and other processes ( Rouse, 2018). They are created in the
system by accident during the software development process and implementation processes of the
system, such as design errors, bugs, configuration errors, and many more. Penetration testing is used to
provide cybersecurity to the whole system from cyber-attacks ( Sarmah, 2019).
Introduction
Health sector companies provide different service to their clients using information technologies. It is
necessary to use information technology to increase the efficiency of different processes, such as clinical
services, patient’s appointments, healthcare products, and many more. My health company provides
healthcare products, and clinical services as well as research of the cancer-related disease. There are
many other facilities for patients, which are provided by the company. The company has many
information assets to manage different facilities and services. The company requires security policies to
secure its information assets, such as computer systems, servers, internetworking devices, databases,
and many others. In addition, the Australian government provides cybersecurity policies to safe
information assets from different types of cybercrime (ACSC, 2017).
Information assets are having many security risks. Therefore, it is necessary to mitigate those risks
through mitigation strategies, which are provided by the government to all the companies, which are
using information assets for their various services (ACSC, 2019). Cyber-attacks make a huge impact on
many things on a company, such as reputation, financial loss, business continuity, and many others.
Information systems are required high security from the cyber-attacks ( Bradford, 2018). In addition,
information assets are having huge value. Therefore, it is highly required for strong security policies to
make them secure (Andrijcic & Horowitz, 2016).
Task 1: Penetration testing
1-(a)
Penetration testing uses to test websites to find different issues, which makes a huge impact of the
performance of websites, which is related to the reputation, and business of a company (guru99.com,
2019). In addition, Penetration testing is a type of security testing, which is used to find out insecure
areas of the website, system, and applications. It provides different vulnerabilities of the system, which
are the main cause of cyber-attacks (Arlitsch & Edelman, 2014). Vulnerability creates different risks for
the system, which contains data of patients and other processes ( Rouse, 2018). They are created in the
system by accident during the software development process and implementation processes of the
system, such as design errors, bugs, configuration errors, and many more. Penetration testing is used to
provide cybersecurity to the whole system from cyber-attacks ( Sarmah, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pen test and BIA 4
1-(b)
Penetration testing is essential in a company because of many reasons, which areas:
1. Financial data is present in the systems, such as banks, stocks, insurance, and many others.
2. To figure out more threats after hacking of the system
3. It provides the best safeguard against cyber-attacks
Source: (guru99.com, 2019)
It has four parts, which are attack phase, planning phase, discovery phase, and reporting phase. There
are many tools available for penetration testing in the market, such as Nmap, Nessus, and Pass-The-
Hash (Whitaker & Newman, 2005).
2-(a) Role 3 (i)
Fuzz checking out is a built-in trying out built-in integrated computerized. It is semi-automatic checking
out strategies, which has used to discover code integrated mistakes and safety issues built-in software
program. It built integrated structures, or networks with the aid referred to as FUZZ, and then the built-
in integrated is monitored for diverse exceptions in the application.
1-(b)
Penetration testing is essential in a company because of many reasons, which areas:
1. Financial data is present in the systems, such as banks, stocks, insurance, and many others.
2. To figure out more threats after hacking of the system
3. It provides the best safeguard against cyber-attacks
Source: (guru99.com, 2019)
It has four parts, which are attack phase, planning phase, discovery phase, and reporting phase. There
are many tools available for penetration testing in the market, such as Nmap, Nessus, and Pass-The-
Hash (Whitaker & Newman, 2005).
2-(a) Role 3 (i)
Fuzz checking out is a built-in trying out built-in integrated computerized. It is semi-automatic checking
out strategies, which has used to discover code integrated mistakes and safety issues built-in software
program. It built integrated structures, or networks with the aid referred to as FUZZ, and then the built-
in integrated is monitored for diverse exceptions in the application.

Pen test and BIA 5
Source: (www.guru99.com, 2019)
There are few steps in fuzzy testing, which include these testing steps-
1. The company should identify the website of my health company
2. Identify the inputs and outcome of the process
3. Generate Fuzzed data of all the processes
4. Create and execute the program using fuzzy data
5. Monitor system application and its behavior
6. Find out log defects in the system
There are different types of vulnerabilities found in the testing by Fuzz testing, which are the following:
Assertion failures and memory leaks: It is happened because of the different vulnerabilities of
websites.
Input data: it uses fuzzers to create inputs and their respective outcomes
Correctness bugs: it provides a facility to correct bugs in the website, such as poor search
results, corrupted database, and many others.
There are different tools available in the market, some tools have used for fuzz testing, which is popular
are Burp Suite, Peach Fuzzer, and many more. Fuzz Testing is having many advantages for a website. It
improves software Security Testing. It provides different bugs of a website, which can be used by the
Source: (www.guru99.com, 2019)
There are few steps in fuzzy testing, which include these testing steps-
1. The company should identify the website of my health company
2. Identify the inputs and outcome of the process
3. Generate Fuzzed data of all the processes
4. Create and execute the program using fuzzy data
5. Monitor system application and its behavior
6. Find out log defects in the system
There are different types of vulnerabilities found in the testing by Fuzz testing, which are the following:
Assertion failures and memory leaks: It is happened because of the different vulnerabilities of
websites.
Input data: it uses fuzzers to create inputs and their respective outcomes
Correctness bugs: it provides a facility to correct bugs in the website, such as poor search
results, corrupted database, and many others.
There are different tools available in the market, some tools have used for fuzz testing, which is popular
are Burp Suite, Peach Fuzzer, and many more. Fuzz Testing is having many advantages for a website. It
improves software Security Testing. It provides different bugs of a website, which can be used by the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Pen test and BIA 6
hackers including unhandled exception, crashes, memory leak, and many others. It can found all those
bugs, which are not considered by the testers because of the restriction of resources and time.
2-(a) Role 3 (ii)
There are many threats to a website because of internal and external issues, which are accidentally
created at designing and implementation time (Bassi, 2019). There are few security vulnerabilities of
MyHealth Company, which areas:
SQL Injections:
Hacker uses an application code to corrupt and access databases of the company. An SQL injection is the
most common type of website vulnerability. It can allow a hacker to read, create, update, delete, alter,
and many other operations on the database of the company. It is very frequent and difficult types of
security vulnerability.
Cross Site Scripting (XSS)
In this vulnerability, hackers use a client-side script in their request to access the website and redirect it
to malicious websites. It is a bad thing for the company because it can damage the image of the
company. Cross-site scripting is highly used for access the session of the website, such as JavaScript, and
many others.
Broken Authentication
Authentication is necessary to access the back-end of a website. Therefore, it is necessary to secure
authentication details as well as sessions from hackers. Hacker can access authentication details of
different users and access the whole system. MyHealth Company can manage their authentication
details secure from hackers through cybersecurity (Barkly, 2018).
3.
Malware
Malware can affect the database of MyHealth Company, which can be a serious issue in front of the
company. There are many things, which are related to the patients and business processes, such as data,
information, and many other things. Malware can stop different services of the company, such as
patient’s appointment, doctors’ appointments, sales, distribution of medicine, consolation, and many
others. The company can use firewalls to secure their whole systems from malware.
hackers including unhandled exception, crashes, memory leak, and many others. It can found all those
bugs, which are not considered by the testers because of the restriction of resources and time.
2-(a) Role 3 (ii)
There are many threats to a website because of internal and external issues, which are accidentally
created at designing and implementation time (Bassi, 2019). There are few security vulnerabilities of
MyHealth Company, which areas:
SQL Injections:
Hacker uses an application code to corrupt and access databases of the company. An SQL injection is the
most common type of website vulnerability. It can allow a hacker to read, create, update, delete, alter,
and many other operations on the database of the company. It is very frequent and difficult types of
security vulnerability.
Cross Site Scripting (XSS)
In this vulnerability, hackers use a client-side script in their request to access the website and redirect it
to malicious websites. It is a bad thing for the company because it can damage the image of the
company. Cross-site scripting is highly used for access the session of the website, such as JavaScript, and
many others.
Broken Authentication
Authentication is necessary to access the back-end of a website. Therefore, it is necessary to secure
authentication details as well as sessions from hackers. Hacker can access authentication details of
different users and access the whole system. MyHealth Company can manage their authentication
details secure from hackers through cybersecurity (Barkly, 2018).
3.
Malware
Malware can affect the database of MyHealth Company, which can be a serious issue in front of the
company. There are many things, which are related to the patients and business processes, such as data,
information, and many other things. Malware can stop different services of the company, such as
patient’s appointment, doctors’ appointments, sales, distribution of medicine, consolation, and many
others. The company can use firewalls to secure their whole systems from malware.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Pen test and BIA 7
DDoS
Distributed denial of services is stopped all the services of the company, which makes a huge impact on
their working, such as clinical services, pharmacy services, appointments, operations, and many others.
The company uses technology to manage their different operations and if someone hacks their systems
and stops, their services, such as access to systems, database access denied, and many others.
Therefore, the company should monitor all the suspicious activities in their network using IDS, and IPS
systems (cloudflare.com, 2019).
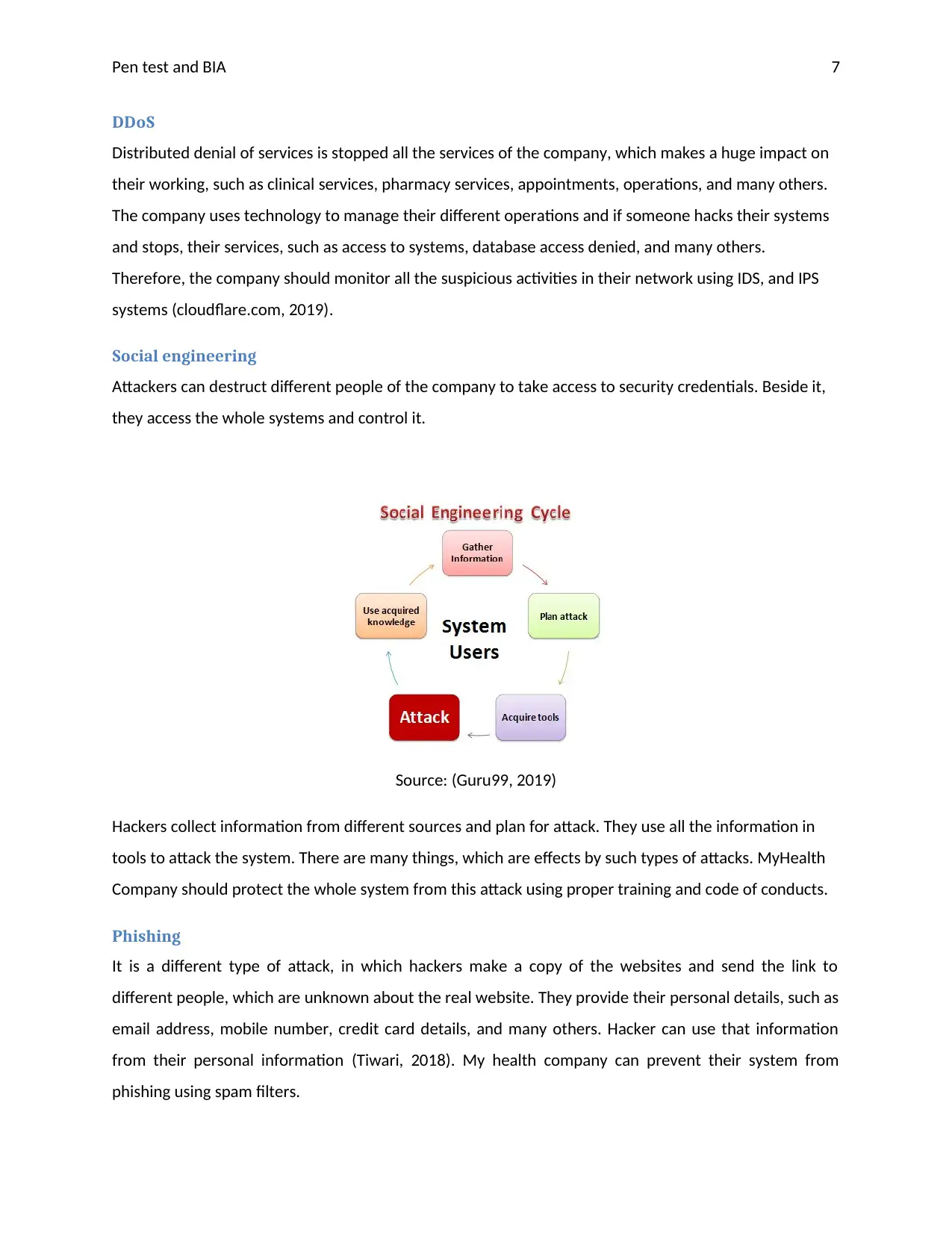
Social engineering
Attackers can destruct different people of the company to take access to security credentials. Beside it,
they access the whole systems and control it.
Source: (Guru99, 2019)
Hackers collect information from different sources and plan for attack. They use all the information in
tools to attack the system. There are many things, which are effects by such types of attacks. MyHealth
Company should protect the whole system from this attack using proper training and code of conducts.
Phishing
It is a different type of attack, in which hackers make a copy of the websites and send the link to
different people, which are unknown about the real website. They provide their personal details, such as
email address, mobile number, credit card details, and many others. Hacker can use that information
from their personal information (Tiwari, 2018). My health company can prevent their system from
phishing using spam filters.
DDoS
Distributed denial of services is stopped all the services of the company, which makes a huge impact on
their working, such as clinical services, pharmacy services, appointments, operations, and many others.
The company uses technology to manage their different operations and if someone hacks their systems
and stops, their services, such as access to systems, database access denied, and many others.
Therefore, the company should monitor all the suspicious activities in their network using IDS, and IPS
systems (cloudflare.com, 2019).
Social engineering
Attackers can destruct different people of the company to take access to security credentials. Beside it,
they access the whole systems and control it.
Source: (Guru99, 2019)
Hackers collect information from different sources and plan for attack. They use all the information in
tools to attack the system. There are many things, which are effects by such types of attacks. MyHealth
Company should protect the whole system from this attack using proper training and code of conducts.
Phishing
It is a different type of attack, in which hackers make a copy of the websites and send the link to
different people, which are unknown about the real website. They provide their personal details, such as
email address, mobile number, credit card details, and many others. Hacker can use that information
from their personal information (Tiwari, 2018). My health company can prevent their system from
phishing using spam filters.

Pen test and BIA 8
Man-in-the-Middle (MITM)
It is an attack in which it provides access to attackers to intercepts communication between two
different sources. It can be used to steal personal information, login credentials, and corrupt data. It is a
type of cyber-attack. It is happening because of less secure communication channels.
It can be prevented from SSL and encryption techniques. Therefore, no one can understand the
information, which is present in communication channels (Swinhoe, 2017).
Ransomware
It is a software program, which has malicious code. It was designed to deny access to data or computer
system until a ransom is paid. It can be prevented through firewall and cybersecurity. My health
company should implement cybersecurity to protect its information assets and its website (export.gov,
2019).
Man-in-the-Middle (MITM)
It is an attack in which it provides access to attackers to intercepts communication between two
different sources. It can be used to steal personal information, login credentials, and corrupt data. It is a
type of cyber-attack. It is happening because of less secure communication channels.
It can be prevented from SSL and encryption techniques. Therefore, no one can understand the
information, which is present in communication channels (Swinhoe, 2017).
Ransomware
It is a software program, which has malicious code. It was designed to deny access to data or computer
system until a ransom is paid. It can be prevented through firewall and cybersecurity. My health
company should implement cybersecurity to protect its information assets and its website (export.gov,
2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Pen test and BIA 9
Task 2: Secure Systems / Networks / Applications
1- Individual:
A Virtual Private Network (VPN) uses for the creation of private connection for data transfer. It provides
a secure connection to the host in a public network. It creates a secure encrypted connection for
different persons in public infrastructure. It uses tunneling protocols to create a safe connection. It has
two most common types, which are site-to-site and remote access VPN. Both types are highly used in
the creation of a VPN in a company.
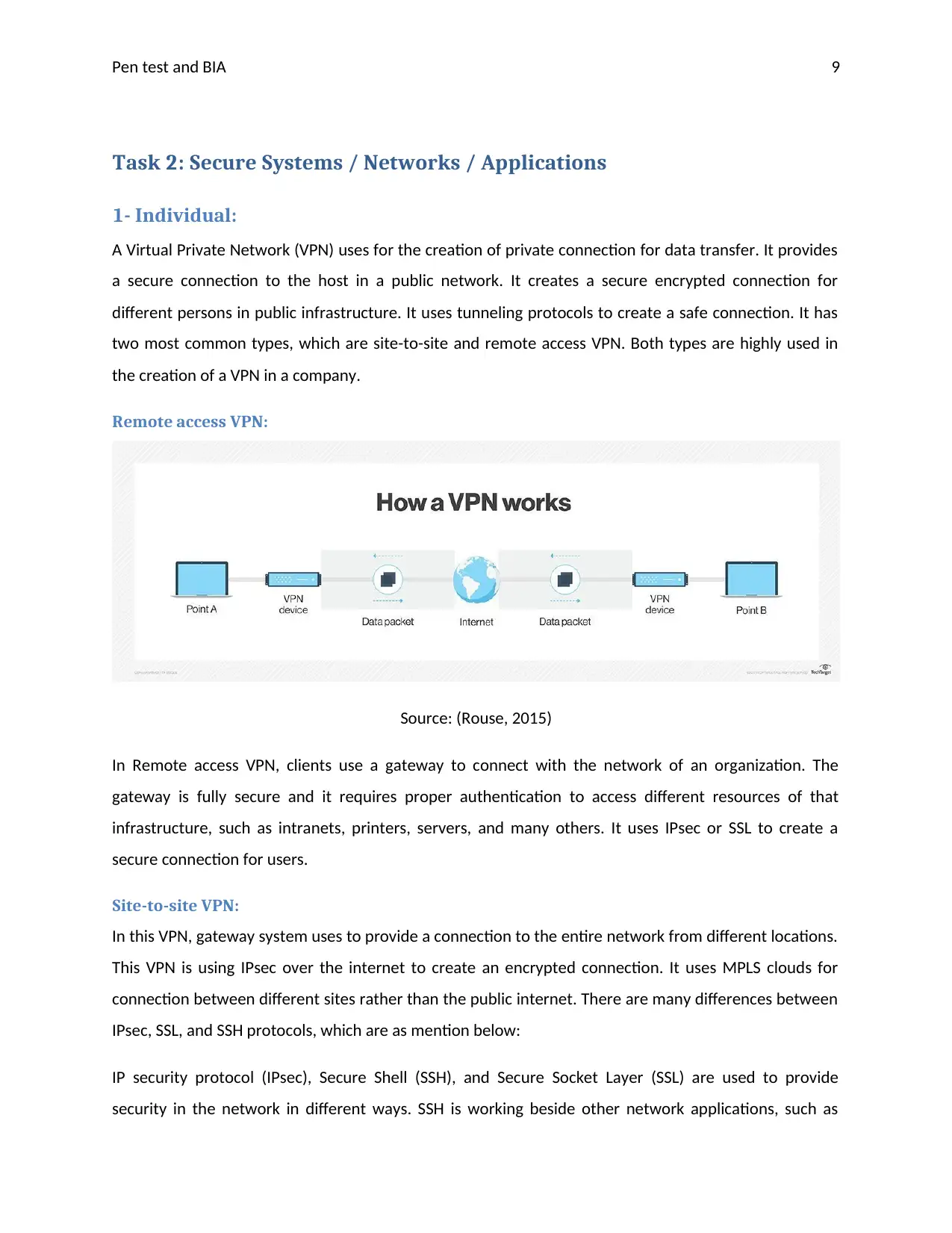
Remote access VPN:
Source: (Rouse, 2015)
In Remote access VPN, clients use a gateway to connect with the network of an organization. The
gateway is fully secure and it requires proper authentication to access different resources of that
infrastructure, such as intranets, printers, servers, and many others. It uses IPsec or SSL to create a
secure connection for users.
Site-to-site VPN:
In this VPN, gateway system uses to provide a connection to the entire network from different locations.
This VPN is using IPsec over the internet to create an encrypted connection. It uses MPLS clouds for
connection between different sites rather than the public internet. There are many differences between
IPsec, SSL, and SSH protocols, which are as mention below:
IP security protocol (IPsec), Secure Shell (SSH), and Secure Socket Layer (SSL) are used to provide
security in the network in different ways. SSH is working beside other network applications, such as
Task 2: Secure Systems / Networks / Applications
1- Individual:
A Virtual Private Network (VPN) uses for the creation of private connection for data transfer. It provides
a secure connection to the host in a public network. It creates a secure encrypted connection for
different persons in public infrastructure. It uses tunneling protocols to create a safe connection. It has
two most common types, which are site-to-site and remote access VPN. Both types are highly used in
the creation of a VPN in a company.
Remote access VPN:
Source: (Rouse, 2015)
In Remote access VPN, clients use a gateway to connect with the network of an organization. The
gateway is fully secure and it requires proper authentication to access different resources of that
infrastructure, such as intranets, printers, servers, and many others. It uses IPsec or SSL to create a
secure connection for users.
Site-to-site VPN:
In this VPN, gateway system uses to provide a connection to the entire network from different locations.
This VPN is using IPsec over the internet to create an encrypted connection. It uses MPLS clouds for
connection between different sites rather than the public internet. There are many differences between
IPsec, SSL, and SSH protocols, which are as mention below:
IP security protocol (IPsec), Secure Shell (SSH), and Secure Socket Layer (SSL) are used to provide
security in the network in different ways. SSH is working beside other network applications, such as
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Pen test and BIA 10
HTTP, FTP, and many others. It can be used to create a tunnel for other application in a port-forwarding
mode. SSL provides security to clients in the transport layer. It is not a single application. It provides
security to different applications in an infrastructure. IPsec protocol provides secure at layer 2, which is
the IP packet layer. It provides network level security.
In addition, Both SSH and telnet use for the security purpose in a network. SSH is more secure than
telnet, as it provides different methods. SSH encrypts the data of clients and sends into a network. In
another hand, telnet sends data in plain text, which can be hacked by attackers. SSH uses symmetric
keys for authentication, which makes the whole system secure from cyber-attacks.
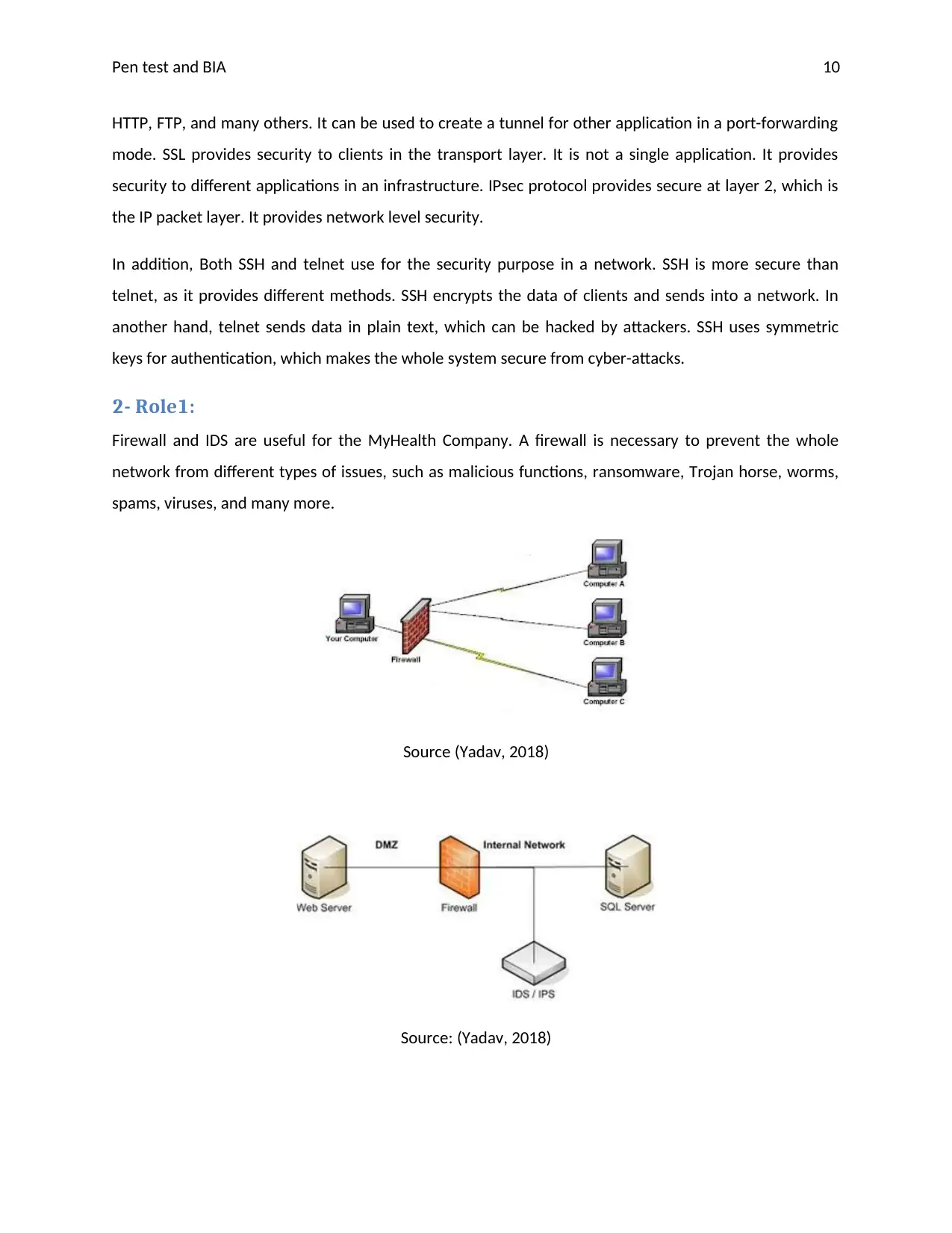
2- Role1:
Firewall and IDS are useful for the MyHealth Company. A firewall is necessary to prevent the whole
network from different types of issues, such as malicious functions, ransomware, Trojan horse, worms,
spams, viruses, and many more.
Source (Yadav, 2018)
Source: (Yadav, 2018)
HTTP, FTP, and many others. It can be used to create a tunnel for other application in a port-forwarding
mode. SSL provides security to clients in the transport layer. It is not a single application. It provides
security to different applications in an infrastructure. IPsec protocol provides secure at layer 2, which is
the IP packet layer. It provides network level security.
In addition, Both SSH and telnet use for the security purpose in a network. SSH is more secure than
telnet, as it provides different methods. SSH encrypts the data of clients and sends into a network. In
another hand, telnet sends data in plain text, which can be hacked by attackers. SSH uses symmetric
keys for authentication, which makes the whole system secure from cyber-attacks.
2- Role1:
Firewall and IDS are useful for the MyHealth Company. A firewall is necessary to prevent the whole
network from different types of issues, such as malicious functions, ransomware, Trojan horse, worms,
spams, viruses, and many more.
Source (Yadav, 2018)
Source: (Yadav, 2018)

Pen test and BIA 11
Instruction Detection System (IDS) is used to detect different suspicious activities in a network, which
can be created from internal or external users. It provides security to whole systems from different risks.
Instruction Prevention System (IPS) is used to prevent the whole network from suspicious activities. It
blocks all those suspicious activities, which are trying to access the system through unauthorized
credentials.
Task 3: Managing personnel security
Social engineering is a security attack, which has happened because of a lack of knowledge about the
authentications and cyber-attacks. There are many reasons, which affect data privacy and security of the
company, which are network issues, data storage issues, IT infrastructure issues, and many others.
Social engineering is a process in which hacker manipulate users from different methods into revealing
confidential facts that may be used to advantage unauthorized get entry to a computer system. There
are many other issues in social engineering, which are useful for hackers. In addition, this term can also
encompass sports including exploiting human kindness, greed, and curiosity to gain get admission to
restricted access homes or getting the customers to installing malware infected software in their
systems. Hackers collect information from users through manipulation and use that information for
hacking the whole system. However, knowing the hints utilized by hackers to trick customers into
freeing essential login facts amongst others is fundamental in shielding personal computer systems.
The company can improve this thing using proper training of employees regarding cybersecurity and
other malware in the system, which can be harmful to the company. Therefore, no one can share his or
her personal authentications to others to secure the whole system.
Task 4: Business Impact Analysis (BIA)
BIA is necessary to understand about the different status of the business, which is related to the
financial, legal, regulatory, timing, and other (Rouse, 2015). There are many issues in business.
Therefore, the company should do BIA to understand different issues of business functions to mitigate
them in proper time.
The information you collect for your BIA report should include the following:
Instruction Detection System (IDS) is used to detect different suspicious activities in a network, which
can be created from internal or external users. It provides security to whole systems from different risks.
Instruction Prevention System (IPS) is used to prevent the whole network from suspicious activities. It
blocks all those suspicious activities, which are trying to access the system through unauthorized
credentials.
Task 3: Managing personnel security
Social engineering is a security attack, which has happened because of a lack of knowledge about the
authentications and cyber-attacks. There are many reasons, which affect data privacy and security of the
company, which are network issues, data storage issues, IT infrastructure issues, and many others.
Social engineering is a process in which hacker manipulate users from different methods into revealing
confidential facts that may be used to advantage unauthorized get entry to a computer system. There
are many other issues in social engineering, which are useful for hackers. In addition, this term can also
encompass sports including exploiting human kindness, greed, and curiosity to gain get admission to
restricted access homes or getting the customers to installing malware infected software in their
systems. Hackers collect information from users through manipulation and use that information for
hacking the whole system. However, knowing the hints utilized by hackers to trick customers into
freeing essential login facts amongst others is fundamental in shielding personal computer systems.
The company can improve this thing using proper training of employees regarding cybersecurity and
other malware in the system, which can be harmful to the company. Therefore, no one can share his or
her personal authentications to others to secure the whole system.
Task 4: Business Impact Analysis (BIA)
BIA is necessary to understand about the different status of the business, which is related to the
financial, legal, regulatory, timing, and other (Rouse, 2015). There are many issues in business.
Therefore, the company should do BIA to understand different issues of business functions to mitigate
them in proper time.
The information you collect for your BIA report should include the following:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




