INSE 6980 Security Project: Penetration Test Recommendations Report
VerifiedAdded on 2022/08/23
|11
|1209
|12
Project
AI Summary
This project provides a comprehensive security analysis and recommendations for a food distribution network facing data mismatch and unauthorized access issues. The project begins with a recommendation for conducting both external and internal penetration tests, followed by a three-phase approach: reconnaissance, scanning, and exploitation. It then lists penetration testing software, relevant federal laws (UK Computer Misuse Act 1990, UK Data Protection Act 1998, etc.), and recommended security policies (limiting data access, employee training, incident response plans, etc.) to prevent future incidents. The document also suggests specific applications and equipment like IDS/IPS systems, firewalls, and DLP technologies. Furthermore, it details vulnerabilities found in Google Chrome, Microsoft Edge, Microsoft Office 2016, and Oracle Database, along with solutions such as patching and license management. Finally, it includes instructions for checking Microsoft Office 2016 license expiration dates and provides a bibliography of cited sources.

INSE 6980 SECURITY
PROJECT
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
PROJECT
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RECOMMENDATION FOR PENETRATION
TESTS ON FOOD DISTRIBUTION NETWORK
STRUCTURE
• A PENETRATION TESTING IS NEEDED TO BE CONDUCTED ON THE NETWORK OF THE FOOD DISTRIBUTION
COMPANY FOR MITIGATING THE CURRENT PROBLEM OF DATA MISMATCH, DATA BACKUP, DATA DELETION
UNAUTHROISED ACCESS, ETC.
• IT IS RECOMMENDED THAT BOTH EXTERNAL AND INTERNAL PENETRATION TEST IS NEEDED TO BE
PERFORMED ON THE ORGANIZATIONAL NETWORK.
• THE EXTERNAL PENTEST HELPS IN VIEWING THE ENVIRONMENT SECURITY POSTURE FROM THE OUTSIDE
SECURITY PERIMETER FROM THE INTERNET FOR REVIEWING THE VULNERABILITY THAT IS EXPLOITED BY
EXTERNAL HACKER.
• THE INTERNAL PENTEST HELPS IN IDENTIFYING A TRUSTED INSIDER INSIDE THE PERIMETER DEFENSE. IT CAN
HELP IN IDENTIFYING THE POTENTIAL DAMAGE CAUSED BY AN INSIDER.
• THE PENTEST IS NEEDED TO BE CONDUCTED IN THREE PHASE I.E. RECONNAISSANCE, SCANNING AND
EXPLOITATION AND ACCESS MAINTAINED, BACKDOORS AND ROOTKITS ARE ALSO NEEDED TO BE IDENTIFIED.
TESTS ON FOOD DISTRIBUTION NETWORK
STRUCTURE
• A PENETRATION TESTING IS NEEDED TO BE CONDUCTED ON THE NETWORK OF THE FOOD DISTRIBUTION
COMPANY FOR MITIGATING THE CURRENT PROBLEM OF DATA MISMATCH, DATA BACKUP, DATA DELETION
UNAUTHROISED ACCESS, ETC.
• IT IS RECOMMENDED THAT BOTH EXTERNAL AND INTERNAL PENETRATION TEST IS NEEDED TO BE
PERFORMED ON THE ORGANIZATIONAL NETWORK.
• THE EXTERNAL PENTEST HELPS IN VIEWING THE ENVIRONMENT SECURITY POSTURE FROM THE OUTSIDE
SECURITY PERIMETER FROM THE INTERNET FOR REVIEWING THE VULNERABILITY THAT IS EXPLOITED BY
EXTERNAL HACKER.
• THE INTERNAL PENTEST HELPS IN IDENTIFYING A TRUSTED INSIDER INSIDE THE PERIMETER DEFENSE. IT CAN
HELP IN IDENTIFYING THE POTENTIAL DAMAGE CAUSED BY AN INSIDER.
• THE PENTEST IS NEEDED TO BE CONDUCTED IN THREE PHASE I.E. RECONNAISSANCE, SCANNING AND
EXPLOITATION AND ACCESS MAINTAINED, BACKDOORS AND ROOTKITS ARE ALSO NEEDED TO BE IDENTIFIED.
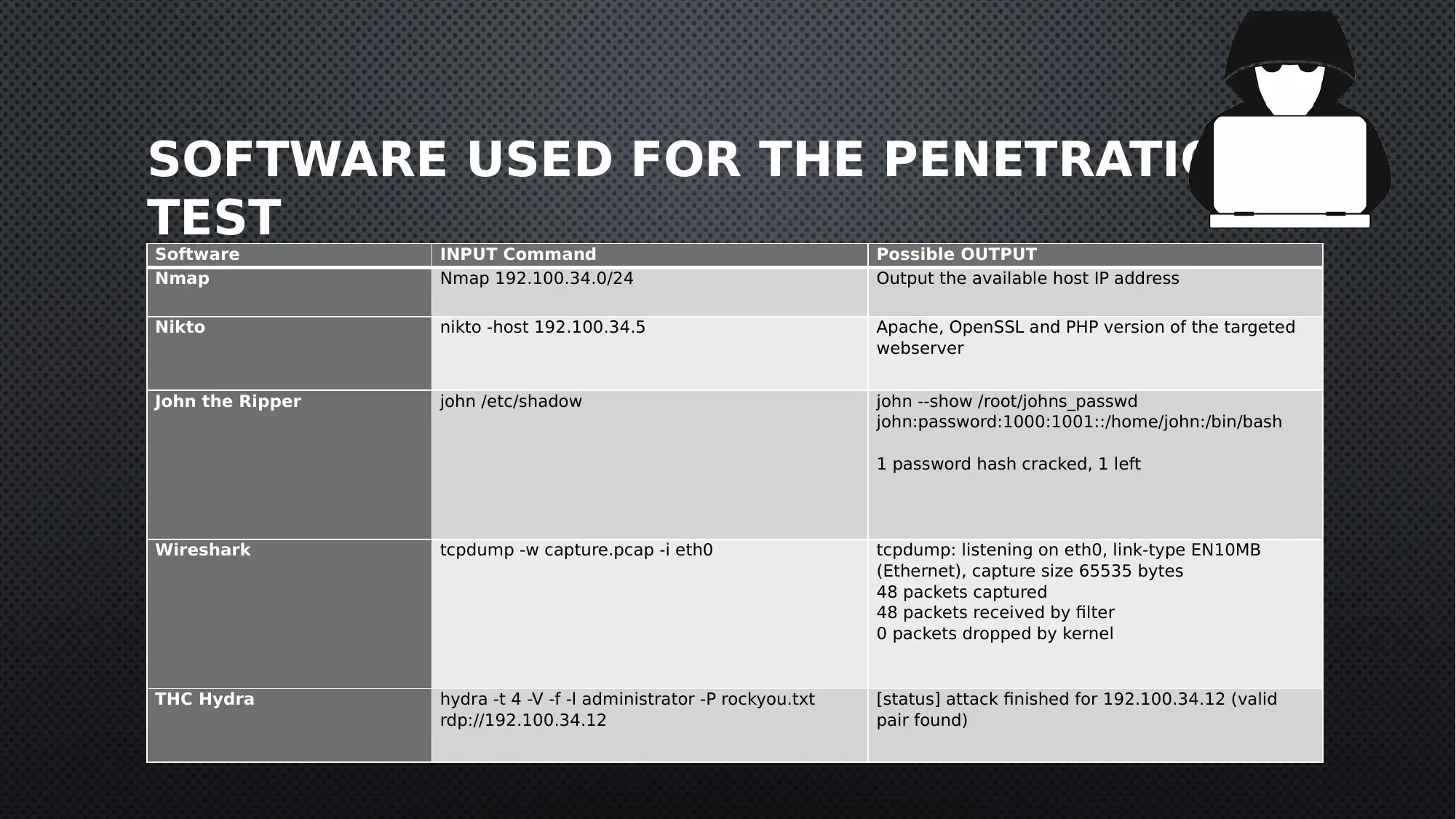
SOFTWARE USED FOR THE PENETRATION
TEST
Software INPUT Command Possible OUTPUT
Nmap Nmap 192.100.34.0/24 Output the available host IP address
Nikto nikto -host 192.100.34.5 Apache, OpenSSL and PHP version of the targeted
webserver
John the Ripper john /etc/shadow john --show /root/johns_passwd
john:password:1000:1001::/home/john:/bin/bash
1 password hash cracked, 1 left
Wireshark tcpdump -w capture.pcap -i eth0 tcpdump: listening on eth0, link-type EN10MB
(Ethernet), capture size 65535 bytes
48 packets captured
48 packets received by filter
0 packets dropped by kernel
THC Hydra hydra -t 4 -V -f -l administrator -P rockyou.txt
rdp://192.100.34.12
[status] attack finished for 192.100.34.12 (valid
pair found)
TEST
Software INPUT Command Possible OUTPUT
Nmap Nmap 192.100.34.0/24 Output the available host IP address
Nikto nikto -host 192.100.34.5 Apache, OpenSSL and PHP version of the targeted
webserver
John the Ripper john /etc/shadow john --show /root/johns_passwd
john:password:1000:1001::/home/john:/bin/bash
1 password hash cracked, 1 left
Wireshark tcpdump -w capture.pcap -i eth0 tcpdump: listening on eth0, link-type EN10MB
(Ethernet), capture size 65535 bytes
48 packets captured
48 packets received by filter
0 packets dropped by kernel
THC Hydra hydra -t 4 -V -f -l administrator -P rockyou.txt
rdp://192.100.34.12
[status] attack finished for 192.100.34.12 (valid
pair found)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RECOMMENDATIONS OF LAWS
THE FOLLOWING ARE THE FEDERATION LAWS THAT ARE NEEDED TO BE
FOLLOWED FOR CONDUCTING THE PENETRATION TESTING AND CAPTURE
THE SCOPE OF TEST:
• UK COMPUTER MISUSE ACT 1990
• UK DATA PROTECTION ACT 1998
• HUMAN RIGHTS ACT 1998
• POLICE AND JUSTICE ACT 2006
• HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT (HIPAA)
THE FOLLOWING ARE THE FEDERATION LAWS THAT ARE NEEDED TO BE
FOLLOWED FOR CONDUCTING THE PENETRATION TESTING AND CAPTURE
THE SCOPE OF TEST:
• UK COMPUTER MISUSE ACT 1990
• UK DATA PROTECTION ACT 1998
• HUMAN RIGHTS ACT 1998
• POLICE AND JUSTICE ACT 2006
• HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT (HIPAA)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RECOMMENDED POLICIES FOR AVOIDING
FUTURE INCIDENT
THE FOLLOWING ARE THE POLICIES THAT ARE NEEDED TO BE IMPLEMENTED BY THE
FOOD DISTRIBUTION COMPANY FOR THE PREVENTION OF SIMILAR SECURITY
INCIDENTS:
• LIMITING THE ACCESS OF VALUABLE DATA
• COMPLIANCE CHECK OF THE THIRD PARTY VENDORS
• CONDUCTING EMPLOYEE TRAINING FOR SECURITY AWARENESS
• PERFORMING REGULAR UPDATE OF SOFTWARE
• DEVELOPMENT OF SECURITY INCIDENT RESPONSE PLAN
• USE OF UNIQUE STRONG PASSWORD IN DIFFERENT FIELDS
FUTURE INCIDENT
THE FOLLOWING ARE THE POLICIES THAT ARE NEEDED TO BE IMPLEMENTED BY THE
FOOD DISTRIBUTION COMPANY FOR THE PREVENTION OF SIMILAR SECURITY
INCIDENTS:
• LIMITING THE ACCESS OF VALUABLE DATA
• COMPLIANCE CHECK OF THE THIRD PARTY VENDORS
• CONDUCTING EMPLOYEE TRAINING FOR SECURITY AWARENESS
• PERFORMING REGULAR UPDATE OF SOFTWARE
• DEVELOPMENT OF SECURITY INCIDENT RESPONSE PLAN
• USE OF UNIQUE STRONG PASSWORD IN DIFFERENT FIELDS

RECOMMENDED APPLICATION OR
EQUIPMENT’S FOR AVOIDING FUTURE
PROBLEMS
• THE FOLLOWING ARE THE EQUIPMENT’S AND APPLICATION THAT ARE RECOMMENDED FOR AVOIDING THE FUTURE SECURITY BREACH
INCIDENT:
• IDS AND IPS SYSTEM – IT IS USED FOR SCANNING TRAFFIC AGAINST A DATABASE CONTAINING DETECTED MALWARE SIGNATURES. IDS
MONITORS THE NETWORK PASSIVELY FOR THE DETECTION OF CLASSIFIED THREATS AND IPS CAN ADDITIONALLY PREVENT ATTACKS BY
SCANNING MALICIOUS FILES.
• FIREWALLS – IT HELPS IN CREATING BARRIER BETWEEN INTERNALS AND OUTSIDE NETWORK. THE INCOMING AND OUTGOING DATA TRAFFIC
IS MONITORED AND COMPARED AGAINST THE RULES FOR ALLOWING OR DROPPING THE PACKETS.
• NETWORK ACCESS CONTROL PRODUCTS – IT ENSURES THAT SECURITY POLICY IS FOLLOWED AND THE POTENTIAL ATTACKERS ARE KEPT OUT.
THE DEVICES CAN BE MONITORED THAT ARE ATTEMPTING TO CONNECT OR CONNECTED WITH THE NETWORK AND IT CAN ALSO CONTROL
THE DATA ACCESSED BY USER AND GUEST USERS CAN ALSO BE MANAGED.
• APPLICATION SECURITY PRODUCTS – IT CAN BE HARDWARE OR SOFTWARE USED FOR PROTECTING THE APPLICATIONS. IT MAY BE
APPLICATION FIREWALL, ROUTER PREVENTING IP ADDRESS TO BE AVAILABLE ON INTERNET.
• DATA LOSS PREVENTION TECHNOLOGIES – DLP TOOLS PREVENTS SENSITIVE INFORMATION TO LEAVE THE INTERNAL NETWORK WHETHER VIA
EMAIL, FILE TRANSFER, WEBSITE FORUM OR INSTANT MESSAGES.
• WEB SECURITY SOLUTIONS – IT CAN BLOCK RISK SITES AND OTHER THREATS BASED ON WEB AND PERFORM A TEST FOR THE UNKNOWN
SITES BEFORE LINKING THEM. THE NETWORK ACTIVITY IS ALSO MONITORED FOR THE DETECTION OF THREATS AND REPAIR THE DAMAGES.
EQUIPMENT’S FOR AVOIDING FUTURE
PROBLEMS
• THE FOLLOWING ARE THE EQUIPMENT’S AND APPLICATION THAT ARE RECOMMENDED FOR AVOIDING THE FUTURE SECURITY BREACH
INCIDENT:
• IDS AND IPS SYSTEM – IT IS USED FOR SCANNING TRAFFIC AGAINST A DATABASE CONTAINING DETECTED MALWARE SIGNATURES. IDS
MONITORS THE NETWORK PASSIVELY FOR THE DETECTION OF CLASSIFIED THREATS AND IPS CAN ADDITIONALLY PREVENT ATTACKS BY
SCANNING MALICIOUS FILES.
• FIREWALLS – IT HELPS IN CREATING BARRIER BETWEEN INTERNALS AND OUTSIDE NETWORK. THE INCOMING AND OUTGOING DATA TRAFFIC
IS MONITORED AND COMPARED AGAINST THE RULES FOR ALLOWING OR DROPPING THE PACKETS.
• NETWORK ACCESS CONTROL PRODUCTS – IT ENSURES THAT SECURITY POLICY IS FOLLOWED AND THE POTENTIAL ATTACKERS ARE KEPT OUT.
THE DEVICES CAN BE MONITORED THAT ARE ATTEMPTING TO CONNECT OR CONNECTED WITH THE NETWORK AND IT CAN ALSO CONTROL
THE DATA ACCESSED BY USER AND GUEST USERS CAN ALSO BE MANAGED.
• APPLICATION SECURITY PRODUCTS – IT CAN BE HARDWARE OR SOFTWARE USED FOR PROTECTING THE APPLICATIONS. IT MAY BE
APPLICATION FIREWALL, ROUTER PREVENTING IP ADDRESS TO BE AVAILABLE ON INTERNET.
• DATA LOSS PREVENTION TECHNOLOGIES – DLP TOOLS PREVENTS SENSITIVE INFORMATION TO LEAVE THE INTERNAL NETWORK WHETHER VIA
EMAIL, FILE TRANSFER, WEBSITE FORUM OR INSTANT MESSAGES.
• WEB SECURITY SOLUTIONS – IT CAN BLOCK RISK SITES AND OTHER THREATS BASED ON WEB AND PERFORM A TEST FOR THE UNKNOWN
SITES BEFORE LINKING THEM. THE NETWORK ACTIVITY IS ALSO MONITORED FOR THE DETECTION OF THREATS AND REPAIR THE DAMAGES.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
VULNERABILITIES OF THE PROGRAM
• THE FOLLOWING ARE THE LIST FO VULNERABILITY THAT ARE FOUND ON THE SOFTWARE APPLICATION USED BY THE EMPLOYEES:
GOOGLE CHROME –
• INTEGER OVERFLOW IN ICU.
• OUT OF BOUNDS MEMORY ACCESS IN STREAMS (CVE-2020-6407).
• TYPE CONFUSION IN V8 (CVE-2020-6418).
MICROSOFT EDGE –
• FILE BASED – A MALICIOUS DOCUMENT CAN BE CRAFTED BY ATTACKER FOR LEVERAGING ISSUE AND PERFORM SOME ACTION ON BEHALF
• EMAILS AND OTHER MEANS CAN BE USED FOR DISTRIBUTING THE MALICIOUS DOCUMENT AND INVITES A USER FOR OPENING IT.
• ON OPENING THE DOCUMENT, THE ISSUE IS TRIGGERED
• WEB BASED –
• A MALICIOUS WEBPAGE IS CRAFTED BY THE ATTACKER FOR LEVERAGING THE ISSUE AND PERFORM SOME ACTION ON BEHALF. MALICIOUS CODE
MAY BE INCLUDED IN THE CRAFTED PAGE, REPLACEMENT OF MEMORY ADDRESS AND NOP INSTRUCTION
• EMAILS AND OTHER MEANS CAN BE USED FOR DISTRIBUTING THE MALICIOUS DOCUMENT AND INVITES A USER FOR OPENING IT.
• ON OPENING OR VIEWING THE PAGE, THE ISSUE IS TRIGGERED
• THE FOLLOWING ARE THE LIST FO VULNERABILITY THAT ARE FOUND ON THE SOFTWARE APPLICATION USED BY THE EMPLOYEES:
GOOGLE CHROME –
• INTEGER OVERFLOW IN ICU.
• OUT OF BOUNDS MEMORY ACCESS IN STREAMS (CVE-2020-6407).
• TYPE CONFUSION IN V8 (CVE-2020-6418).
MICROSOFT EDGE –
• FILE BASED – A MALICIOUS DOCUMENT CAN BE CRAFTED BY ATTACKER FOR LEVERAGING ISSUE AND PERFORM SOME ACTION ON BEHALF
• EMAILS AND OTHER MEANS CAN BE USED FOR DISTRIBUTING THE MALICIOUS DOCUMENT AND INVITES A USER FOR OPENING IT.
• ON OPENING THE DOCUMENT, THE ISSUE IS TRIGGERED
• WEB BASED –
• A MALICIOUS WEBPAGE IS CRAFTED BY THE ATTACKER FOR LEVERAGING THE ISSUE AND PERFORM SOME ACTION ON BEHALF. MALICIOUS CODE
MAY BE INCLUDED IN THE CRAFTED PAGE, REPLACEMENT OF MEMORY ADDRESS AND NOP INSTRUCTION
• EMAILS AND OTHER MEANS CAN BE USED FOR DISTRIBUTING THE MALICIOUS DOCUMENT AND INVITES A USER FOR OPENING IT.
• ON OPENING OR VIEWING THE PAGE, THE ISSUE IS TRIGGERED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

VULNERABILITIES OF THE PROGRAM
(CONTD.)
MICROSOFT OFFICE 2016 –
• THERE ARE DIFFERENT REMOTE CODE EXECUTION VULNERABILITIES PRESENT IN MICROSOFT OFFICE THAT IS CAUSED WHEN
OBJECTS CANNOT BE HANDLED IN MEMORY BY THE SOFTWARE.
• IT IS VULNERABLE TO INFORMATION DISCLOSURE BECAUSE IT CAN IMPROPERLY DISCLOSE THE MEMORY CONTENTS
• A DOS VULNERABILITY ALSO EXISTS SINCE IT MAY REQUIRE OUTBOUND MEMORY FOR THE VARIABLES THAT ARE UNINITIALIZED.
• THERE IS AN EXISTENCE OF SECURITY FEATURE BYPASS IF THE LYNC FOR MAC 2011 CLIENT FAILS IN VALIDATING THE CERTIFICATE
• PRIVILEGE ELEVATION VULNERABILITY IS PRESENT IF THE SHAREPOINT SERVER DOES NOT SANITIZE THE CRAFTED WEB REQUEST
TO THE AFFECTED SERVER OF SHARE POINT.
ORACLE DATABASE –
• VULNERABILITY IS PRESENT IN ORACLE DATABASE THAT CAN COMPROMISE THE DATABASE AND THE SHELL ACCESSING THE
SERVER HOSTING. THE JAVA VM COMPONENT HAVE THE VULNERABILITY AND IT DO NOT NEED THE INTERACTION OF THE USER. IN
THE VULNERABILITY THE ATTACKER WITH LOW PRIVILEGE ARE ALLOWED TO CREATE SESSION WITH THE USE OF NETWORK ACCESS
USING ORACLE NET FOR COMPROMISING THE JAVA VM COMPONENT. IT CAN BE PATCHED USING THE PATCH PROVIDED BY ORACLE
SECURITY ALERT FOR MITIGATING THE PROBLEM.
(CONTD.)
MICROSOFT OFFICE 2016 –
• THERE ARE DIFFERENT REMOTE CODE EXECUTION VULNERABILITIES PRESENT IN MICROSOFT OFFICE THAT IS CAUSED WHEN
OBJECTS CANNOT BE HANDLED IN MEMORY BY THE SOFTWARE.
• IT IS VULNERABLE TO INFORMATION DISCLOSURE BECAUSE IT CAN IMPROPERLY DISCLOSE THE MEMORY CONTENTS
• A DOS VULNERABILITY ALSO EXISTS SINCE IT MAY REQUIRE OUTBOUND MEMORY FOR THE VARIABLES THAT ARE UNINITIALIZED.
• THERE IS AN EXISTENCE OF SECURITY FEATURE BYPASS IF THE LYNC FOR MAC 2011 CLIENT FAILS IN VALIDATING THE CERTIFICATE
• PRIVILEGE ELEVATION VULNERABILITY IS PRESENT IF THE SHAREPOINT SERVER DOES NOT SANITIZE THE CRAFTED WEB REQUEST
TO THE AFFECTED SERVER OF SHARE POINT.
ORACLE DATABASE –
• VULNERABILITY IS PRESENT IN ORACLE DATABASE THAT CAN COMPROMISE THE DATABASE AND THE SHELL ACCESSING THE
SERVER HOSTING. THE JAVA VM COMPONENT HAVE THE VULNERABILITY AND IT DO NOT NEED THE INTERACTION OF THE USER. IN
THE VULNERABILITY THE ATTACKER WITH LOW PRIVILEGE ARE ALLOWED TO CREATE SESSION WITH THE USE OF NETWORK ACCESS
USING ORACLE NET FOR COMPROMISING THE JAVA VM COMPONENT. IT CAN BE PATCHED USING THE PATCH PROVIDED BY ORACLE
SECURITY ALERT FOR MITIGATING THE PROBLEM.
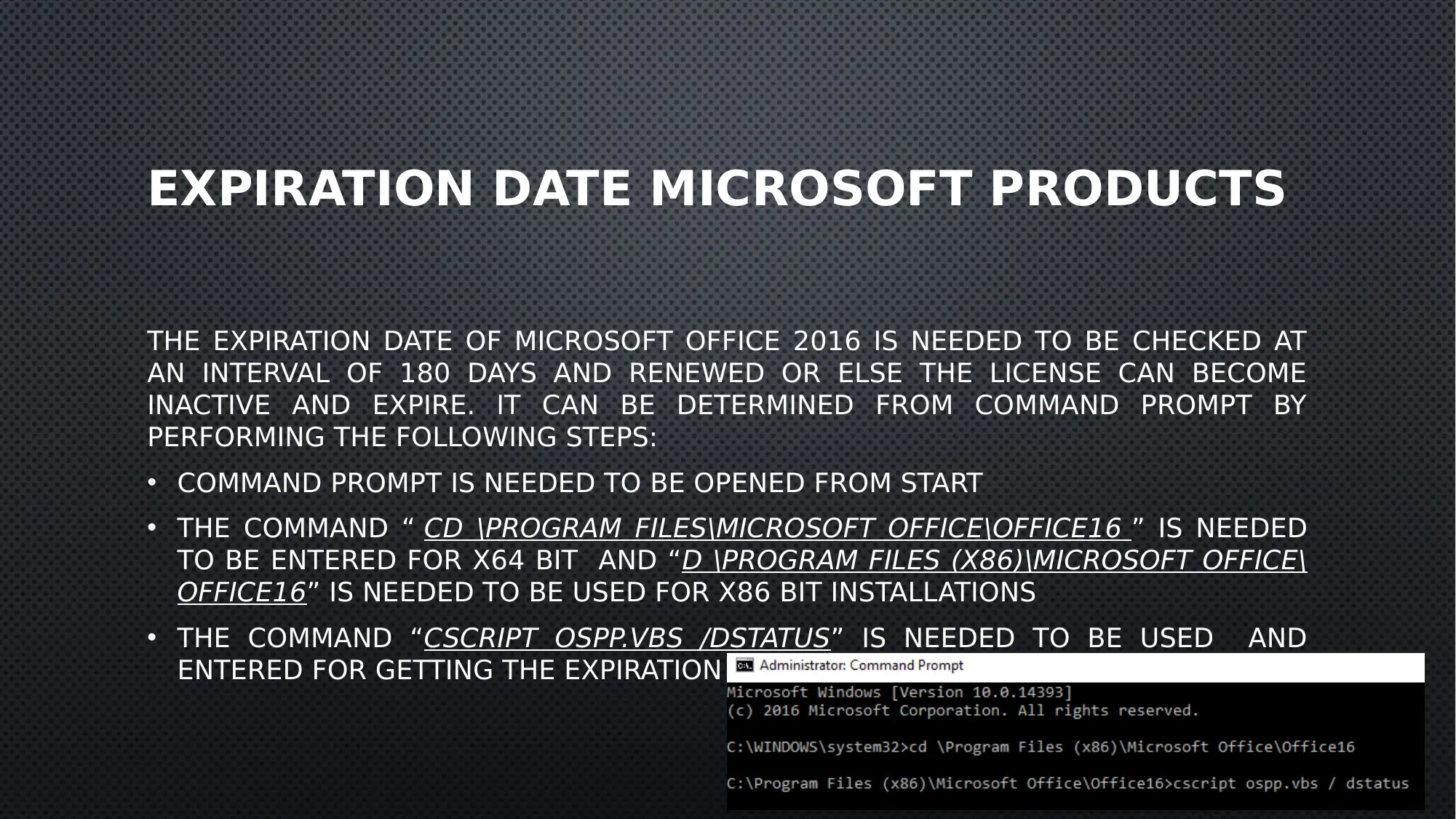
EXPIRATION DATE MICROSOFT PRODUCTS
THE EXPIRATION DATE OF MICROSOFT OFFICE 2016 IS NEEDED TO BE CHECKED AT
AN INTERVAL OF 180 DAYS AND RENEWED OR ELSE THE LICENSE CAN BECOME
INACTIVE AND EXPIRE. IT CAN BE DETERMINED FROM COMMAND PROMPT BY
PERFORMING THE FOLLOWING STEPS:
• COMMAND PROMPT IS NEEDED TO BE OPENED FROM START
• THE COMMAND “ CD \PROGRAM FILES\MICROSOFT OFFICE\OFFICE16 ” IS NEEDED
TO BE ENTERED FOR X64 BIT AND “D \PROGRAM FILES (X86)\MICROSOFT OFFICE\
OFFICE16” IS NEEDED TO BE USED FOR X86 BIT INSTALLATIONS
• THE COMMAND “CSCRIPT OSPP.VBS /DSTATUS” IS NEEDED TO BE USED AND
ENTERED FOR GETTING THE EXPIRATION DATE OF THE LICENSE.
THE EXPIRATION DATE OF MICROSOFT OFFICE 2016 IS NEEDED TO BE CHECKED AT
AN INTERVAL OF 180 DAYS AND RENEWED OR ELSE THE LICENSE CAN BECOME
INACTIVE AND EXPIRE. IT CAN BE DETERMINED FROM COMMAND PROMPT BY
PERFORMING THE FOLLOWING STEPS:
• COMMAND PROMPT IS NEEDED TO BE OPENED FROM START
• THE COMMAND “ CD \PROGRAM FILES\MICROSOFT OFFICE\OFFICE16 ” IS NEEDED
TO BE ENTERED FOR X64 BIT AND “D \PROGRAM FILES (X86)\MICROSOFT OFFICE\
OFFICE16” IS NEEDED TO BE USED FOR X86 BIT INSTALLATIONS
• THE COMMAND “CSCRIPT OSPP.VBS /DSTATUS” IS NEEDED TO BE USED AND
ENTERED FOR GETTING THE EXPIRATION DATE OF THE LICENSE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

BIBLIOGRAPHY
• AL SHEBLI, H.M.Z. AND BEHESHTI, B.D., 2018, MAY. A STUDY ON PENETRATION TESTING PROCESS AND TOOLS.
IN 2018 IEEE LONG ISLAND SYSTEMS, APPLICATIONS AND TECHNOLOGY CONFERENCE (LISAT) (PP. 1-7). IEEE.
• BALOCH, R., 2017. ETHICAL HACKING AND PENETRATION TESTING GUIDE. CRC PRESS.
• CIS. (2020). A VULNERABILITY IN ORACLE DATABASE COULD ALLOW FOR COMPLETE COMPROMISE - CIS.
[ONLINE] AVAILABLE AT: HTTPS://WWW.CISECURITY.ORG/ADVISORY/A-VULNERABILITY-IN-ORACLE-DATABASE-
COULD-ALLOW-FOR-COMPLETE-COMPROMISE_2018-089/ [ACCESSED 31 MAR. 2020].
• CVEDETAILS.COM. (2020). GOOGLE CHROME : LIST OF SECURITY VULNERABILITIES. [ONLINE] AVAILABLE AT:
HTTPS://WWW.CVEDETAILS.COM/VULNERABILITY-LIST/VENDOR_ID-1224/PRODUCT_ID-15031/OPEC-1/GOOGLE-
CHROME.HTML [ACCESSED 30 MAR. 2020].
• SOFTWARE.GROK.LSU.EDU. (2020). MICROSOFT OFFICE 2016: VERIFY ACTIVATION & DETERMINE EXPIRATION
DATE - GROK KNOWLEDGE BASE . [ONLINE] AVAILABLE AT: HTTPS://SOFTWARE.GROK.LSU.EDU/ARTICLE.ASPX?
ARTICLEID=18020 [ACCESSED 31 MAR. 2020].
• AL SHEBLI, H.M.Z. AND BEHESHTI, B.D., 2018, MAY. A STUDY ON PENETRATION TESTING PROCESS AND TOOLS.
IN 2018 IEEE LONG ISLAND SYSTEMS, APPLICATIONS AND TECHNOLOGY CONFERENCE (LISAT) (PP. 1-7). IEEE.
• BALOCH, R., 2017. ETHICAL HACKING AND PENETRATION TESTING GUIDE. CRC PRESS.
• CIS. (2020). A VULNERABILITY IN ORACLE DATABASE COULD ALLOW FOR COMPLETE COMPROMISE - CIS.
[ONLINE] AVAILABLE AT: HTTPS://WWW.CISECURITY.ORG/ADVISORY/A-VULNERABILITY-IN-ORACLE-DATABASE-
COULD-ALLOW-FOR-COMPLETE-COMPROMISE_2018-089/ [ACCESSED 31 MAR. 2020].
• CVEDETAILS.COM. (2020). GOOGLE CHROME : LIST OF SECURITY VULNERABILITIES. [ONLINE] AVAILABLE AT:
HTTPS://WWW.CVEDETAILS.COM/VULNERABILITY-LIST/VENDOR_ID-1224/PRODUCT_ID-15031/OPEC-1/GOOGLE-
CHROME.HTML [ACCESSED 30 MAR. 2020].
• SOFTWARE.GROK.LSU.EDU. (2020). MICROSOFT OFFICE 2016: VERIFY ACTIVATION & DETERMINE EXPIRATION
DATE - GROK KNOWLEDGE BASE . [ONLINE] AVAILABLE AT: HTTPS://SOFTWARE.GROK.LSU.EDU/ARTICLE.ASPX?
ARTICLEID=18020 [ACCESSED 31 MAR. 2020].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





