Comprehensive Penetration Testing Project: Analysis and Implementation
VerifiedAdded on 2023/01/18
|26
|3368
|66
Project
AI Summary
This penetration testing project provides a comprehensive overview of ethical hacking and cybersecurity. It begins with a critical discussion on the legality of hacking, defining computer crime and differentiating between ethical and malicious hacking practices. The project then outlines a Standard Operating Procedure (SOP) for penetration testing, including intelligence gathering, threat modeling, vulnerability analysis, exploitation, and reporting. The core of the project involves a hands-on penetration test using Kali Linux and Metasploit, detailing the attack narrative, information gathering, scanning and enumeration, and vulnerability assessment and mitigation. The student demonstrates practical application of these tools, including network configuration, port scanning, and attempts at exploitation, with the goal of identifying and addressing vulnerabilities in a target system. The project concludes with a reflection on the process and findings, reinforcing the student's understanding of penetration testing methodologies and their role in securing computer systems.

University
Semester
PENETRATION TESTING
Student ID
Student Name
Submission Date
1
Semester
PENETRATION TESTING
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...........................................................................................................................................3
Task 1 A Critical Discussion on the Legality of Hacking......................................................................3
1. Computer Crime Definition.......................................................................................................3
2. Criminal Activity Discussion.....................................................................................................4
3. Hacking Definition & Explanation............................................................................................4
4. Critical Discussion.....................................................................................................................5
Task 2 SOP for Pen - Testing................................................................................................................5
1. Pen Test Methodology Discussion.............................................................................................5
2. SOP for Pen Testing..................................................................................................................6
3. Decision Making Tree...............................................................................................................7
Task 3 Penetration Test.........................................................................................................................7
1. Attack Narrative........................................................................................................................8
2. Information Gathering.............................................................................................................13
3. Scanning and Enumeration......................................................................................................17
4. Vulnerability Detail & Mitigation............................................................................................19
4.1 Vulnerability Detail.............................................................................................................19
4.2 Vulnerability Mitigation......................................................................................................20
Conclusion and Reflection...................................................................................................................22
References...........................................................................................................................................23
2
Introduction...........................................................................................................................................3
Task 1 A Critical Discussion on the Legality of Hacking......................................................................3
1. Computer Crime Definition.......................................................................................................3
2. Criminal Activity Discussion.....................................................................................................4
3. Hacking Definition & Explanation............................................................................................4
4. Critical Discussion.....................................................................................................................5
Task 2 SOP for Pen - Testing................................................................................................................5
1. Pen Test Methodology Discussion.............................................................................................5
2. SOP for Pen Testing..................................................................................................................6
3. Decision Making Tree...............................................................................................................7
Task 3 Penetration Test.........................................................................................................................7
1. Attack Narrative........................................................................................................................8
2. Information Gathering.............................................................................................................13
3. Scanning and Enumeration......................................................................................................17
4. Vulnerability Detail & Mitigation............................................................................................19
4.1 Vulnerability Detail.............................................................................................................19
4.2 Vulnerability Mitigation......................................................................................................20
Conclusion and Reflection...................................................................................................................22
References...........................................................................................................................................23
2

Introduction
Main spot of this project is critically analysis and discussing the “Penetration Test”.
This project is divided into three tasks. The first task is used to provide the understanding of
the ethical and legal issues surrounding the hacking. To understand, the ethical and legal
issues of discussing why “Hacking” is not a criminal activity. Therefore, we shall define the
computer crime and a table will be constructed which will correlate the traditional crime to
the computer crime. It is used for providing the logical link for discussing the criminal
activity and also provides the definition and explanation of the hacking. The second task is
used for providing the understanding of the process of penetration testing and to critically
compare the penetration testing methodologies, design and develop a SOP (Standard
Operating Procedure) and also include the decision making tree which are used to describe
the information gathering, vulnerability identification and analysis, and target profiling. The
third task is used to provide the ability for conducting a full scale penetration testing in kali
Linux. These will be discussed and analysed in detail.
Task 1 A Critical Discussion on the Legality of Hacking
In this task, we shall discuss “why hacking is not a criminal activity”. It likely defines
the computer crime and a table is constructed which correlates the traditional crime with the
computer crime. In the discussion of criminal activity, the constructed table is used to provide
a logical link. Further, discussing what constitutes a criminal activity and provide the
definition as well as explain hacking. It is believed to give explanation on the opinion of
threat representative in hacking and it is used to appropriate the classifications of threat agent
and it will make use of opportunity, motivation and capability like the classifying attributes.
At last, the supported opinion related to why hacking is not a criminal activity will be
concluded.
1. Definition of Computer Crime
Computer crime is can be called as cyber-crime as well (Edwards, 2019). It refers to an
action which is completed by a user who is knowledgeable in computer and who is at times
denoted as the hacker. The hackers steal or browse the information of a company, on illegal
terms. Computer crimes comprises of various activities such as,
3
Main spot of this project is critically analysis and discussing the “Penetration Test”.
This project is divided into three tasks. The first task is used to provide the understanding of
the ethical and legal issues surrounding the hacking. To understand, the ethical and legal
issues of discussing why “Hacking” is not a criminal activity. Therefore, we shall define the
computer crime and a table will be constructed which will correlate the traditional crime to
the computer crime. It is used for providing the logical link for discussing the criminal
activity and also provides the definition and explanation of the hacking. The second task is
used for providing the understanding of the process of penetration testing and to critically
compare the penetration testing methodologies, design and develop a SOP (Standard
Operating Procedure) and also include the decision making tree which are used to describe
the information gathering, vulnerability identification and analysis, and target profiling. The
third task is used to provide the ability for conducting a full scale penetration testing in kali
Linux. These will be discussed and analysed in detail.
Task 1 A Critical Discussion on the Legality of Hacking
In this task, we shall discuss “why hacking is not a criminal activity”. It likely defines
the computer crime and a table is constructed which correlates the traditional crime with the
computer crime. In the discussion of criminal activity, the constructed table is used to provide
a logical link. Further, discussing what constitutes a criminal activity and provide the
definition as well as explain hacking. It is believed to give explanation on the opinion of
threat representative in hacking and it is used to appropriate the classifications of threat agent
and it will make use of opportunity, motivation and capability like the classifying attributes.
At last, the supported opinion related to why hacking is not a criminal activity will be
concluded.
1. Definition of Computer Crime
Computer crime is can be called as cyber-crime as well (Edwards, 2019). It refers to an
action which is completed by a user who is knowledgeable in computer and who is at times
denoted as the hacker. The hackers steal or browse the information of a company, on illegal
terms. Computer crimes comprises of various activities such as,
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1) Cyber - Terrorism
2) Financial fraud crimes
3) Cyber warfare
4) Cyber extortion and more.
2. Criminal Activity Discussion
In general, the impression about hackers is that they are criminals, but is this right? It is
a wrong view which is limited, as it reflects on the black hat hackers, who in global hacking
community are only a minority community (Rayner, 2018). Thus, hacking is not necessarily a
criminal activity, as the computer hacker/ white hat hacker could be the individuals who
have knowledge of how to avoid the device/software’s limitations. The ethical hackers
always take permission prior to breaking into someone’s computer systems, with an intension
to identify the vulnerabilities and to improvise the system security. Thus, hacking can be
regarded as crime only if the individuals access system without the permission of the owner
(Edwards, 2019).
It is a common type of cybercrime and it includes identity theft, online predatory
crimes, unauthorized computer access and online bank information theft. It generally
comprises of a various activities, but these activities can likely be categorised as follows:
The crimes which target the computer devices/networks such crimes contain
DoS (denial of service) attacks along with viruses.
The crime which uses the computer network for advancing the other criminal
activities such crimes contain cyber talking, fraud, identity theft and phishing.
Cyber - Crime versus Traditional Crime
The cybercrime is a separate entity to traditional crime and it is carried out by the same
types of criminal for the same type of reasons. Both traditional and cyber - crimes conduct
the either omission or act which runs breach and fouls the rule of law. The cybercrimes
contain criminal activities which are conventional in nature like, fraud, theft, scam, intrusion,
defamation etc.
Computer crime and traditional crime are used to provide the logical link to the criminal
activity.
4
2) Financial fraud crimes
3) Cyber warfare
4) Cyber extortion and more.
2. Criminal Activity Discussion
In general, the impression about hackers is that they are criminals, but is this right? It is
a wrong view which is limited, as it reflects on the black hat hackers, who in global hacking
community are only a minority community (Rayner, 2018). Thus, hacking is not necessarily a
criminal activity, as the computer hacker/ white hat hacker could be the individuals who
have knowledge of how to avoid the device/software’s limitations. The ethical hackers
always take permission prior to breaking into someone’s computer systems, with an intension
to identify the vulnerabilities and to improvise the system security. Thus, hacking can be
regarded as crime only if the individuals access system without the permission of the owner
(Edwards, 2019).
It is a common type of cybercrime and it includes identity theft, online predatory
crimes, unauthorized computer access and online bank information theft. It generally
comprises of a various activities, but these activities can likely be categorised as follows:
The crimes which target the computer devices/networks such crimes contain
DoS (denial of service) attacks along with viruses.
The crime which uses the computer network for advancing the other criminal
activities such crimes contain cyber talking, fraud, identity theft and phishing.
Cyber - Crime versus Traditional Crime
The cybercrime is a separate entity to traditional crime and it is carried out by the same
types of criminal for the same type of reasons. Both traditional and cyber - crimes conduct
the either omission or act which runs breach and fouls the rule of law. The cybercrimes
contain criminal activities which are conventional in nature like, fraud, theft, scam, intrusion,
defamation etc.
Computer crime and traditional crime are used to provide the logical link to the criminal
activity.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. Hacking Definition & Explanation
Hacking refers to an attempt of exploiting the computer network and devices. It can be
denoted as an unauthorized access for controlling the computer network’s security system for
the purpose of crime. While hacking might not be the way for malicious purpose, now a days,
most of hacking or hackers are used to being characterized as unlawful activity by
cybercriminal and it is motivated by the protest, financial gain, information gathering and to
have fun challenges (Gupta and Anand, 2017).
It is used to correct the characterizing of hacking as an over-arching umbrella term for
activity behind most if not all of the malware and malicious cyber-attacks on the computing
public, businesses, and governments. Besides social engineering and malvertising, common
hacking techniques includes (Malwarebytes, 2019),
DoS (Denial of service) attacks
Botnets
Viruses
Worms
Trojans
Ransom ware
Browser hijacks
Rootkits
4. Critical Discussion
Generally, hacking is referred to be identical to the illegal access of computer. So,
hacking is not any type of criminal activity. Always, the ethical hackers access the computer
systems with the permission for determining the appropriate vulnerabilities along with the
necessary improvement in system security.
The ethical hacking cannot be referred as criminal activity and it is not a crime if
legally accepted to hack. For instance, the intelligence gathering which is the first stage of
hacking is not essential a crime because the information collected in the process could be
used for research purposes rather than for the purposes of malicious activity. However,
hacking was not a crime from beginning when true hacking was linked with studying the
computer system and programming languages with hope of making the new innovations to
solve problems.
5
Hacking refers to an attempt of exploiting the computer network and devices. It can be
denoted as an unauthorized access for controlling the computer network’s security system for
the purpose of crime. While hacking might not be the way for malicious purpose, now a days,
most of hacking or hackers are used to being characterized as unlawful activity by
cybercriminal and it is motivated by the protest, financial gain, information gathering and to
have fun challenges (Gupta and Anand, 2017).
It is used to correct the characterizing of hacking as an over-arching umbrella term for
activity behind most if not all of the malware and malicious cyber-attacks on the computing
public, businesses, and governments. Besides social engineering and malvertising, common
hacking techniques includes (Malwarebytes, 2019),
DoS (Denial of service) attacks
Botnets
Viruses
Worms
Trojans
Ransom ware
Browser hijacks
Rootkits
4. Critical Discussion
Generally, hacking is referred to be identical to the illegal access of computer. So,
hacking is not any type of criminal activity. Always, the ethical hackers access the computer
systems with the permission for determining the appropriate vulnerabilities along with the
necessary improvement in system security.
The ethical hacking cannot be referred as criminal activity and it is not a crime if
legally accepted to hack. For instance, the intelligence gathering which is the first stage of
hacking is not essential a crime because the information collected in the process could be
used for research purposes rather than for the purposes of malicious activity. However,
hacking was not a crime from beginning when true hacking was linked with studying the
computer system and programming languages with hope of making the new innovations to
solve problems.
5

Task 2 SOP for Pen - Testing
In this task, we will critically compare the penetration testing methodologies, design and
develop a SOP(Standard Operating Procedure) and also include the decision making tree
which are used to describe the following phases such as,
Intelligence Gathering
Vulnerability Identification and Analysis
Target Exploitation and Post exploitation
These are discussed in detail.
1. Pen Test Methodology Discussion
The main objective of ethical hacking or manual penetration testing is to test the
infrastructure and application for vulnerabilities and security flaws by using the techniques by
hackers without causing the intentional damage. It can be used to test the desktop, mobile and
web based applications or network for security vulnerabilities (RedTeam Security, 2019).
The penetration testing methodologies and standards are used to cover everything related
to a penetration test. The penetration testing is used for determining the vulnerability and
digging deep for finding how much compromise can be afforded by the target, for legitimate
attack. It contains exploiting servers, firewalls, computers, networks and more for uncovering
the vulnerabilities. It highlights the practical risks that can be caused with the recognized
vulnerabilities. The following phases are present in penetration test:
Intelligence Gathering
Threat Modelling
Vulnerability Analysis
Exploitation
Reporting
2. SOP for Pen Testing
The SOP for Pen testing is used to describe the following phases.
Intelligence gathering
Intelligence gathering is used for gathering data or intelligence to assist in
managing the assessment actions. It is conducted to gather information about the
employee in an organization that can help us to get access, potentially private intelligence
of information that is otherwise related to the target (Infosec Resources, 2019).
6
In this task, we will critically compare the penetration testing methodologies, design and
develop a SOP(Standard Operating Procedure) and also include the decision making tree
which are used to describe the following phases such as,
Intelligence Gathering
Vulnerability Identification and Analysis
Target Exploitation and Post exploitation
These are discussed in detail.
1. Pen Test Methodology Discussion
The main objective of ethical hacking or manual penetration testing is to test the
infrastructure and application for vulnerabilities and security flaws by using the techniques by
hackers without causing the intentional damage. It can be used to test the desktop, mobile and
web based applications or network for security vulnerabilities (RedTeam Security, 2019).
The penetration testing methodologies and standards are used to cover everything related
to a penetration test. The penetration testing is used for determining the vulnerability and
digging deep for finding how much compromise can be afforded by the target, for legitimate
attack. It contains exploiting servers, firewalls, computers, networks and more for uncovering
the vulnerabilities. It highlights the practical risks that can be caused with the recognized
vulnerabilities. The following phases are present in penetration test:
Intelligence Gathering
Threat Modelling
Vulnerability Analysis
Exploitation
Reporting
2. SOP for Pen Testing
The SOP for Pen testing is used to describe the following phases.
Intelligence gathering
Intelligence gathering is used for gathering data or intelligence to assist in
managing the assessment actions. It is conducted to gather information about the
employee in an organization that can help us to get access, potentially private intelligence
of information that is otherwise related to the target (Infosec Resources, 2019).
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Threat Modelling
The threat modelling is a process for optimization of network security by
identifying the vulnerabilities and defining the counter measures to mitigate and prevent
the effects of threats to the system. It is used to determine where the most effort must be
applied to keep a system secure.
Vulnerability analysis
This phase is used for identifying and to evaluate the security risk posed by
vulnerabilities identification. The vulnerability analysis is divided into two steps such
as identification and validation. The identification is used for discovering the
vulnerability and it is main task of vulnerabilities analysis. The validation is used to
reduce the number of identified vulnerabilities to only those that are actually valid (IT
Security Concepts, 2019).
Exploitation
If vulnerabilities are identified, we try to exploit those vulnerabilities that can
breach the system and its security. The exploitation involves actually carrying out the
vulnerability to exploit in an effort to make certain if vulnerability is truly exploitable.
This phase consists of employing the heavy manual testing tactics and it often quite
time intensive. It may include overflow. SQL injection and OS commending and
more.
Post Exploitation
This phase is used for determining the machine value is compromised and to
maintain the machine control for later use. The machine value is determined by
understanding of the data stored on it and machine utility in additional negotiating the
network.
Reporting
The reporting phase is used to report the findings in a way that is
understandable and acceptable by the organization that owns the hardware or system.
It includes the defects which allow an attacker to violate an explicit security policy to
achieve the some impact. It is used to gain increased levels of access or interfere with
the normal operation of systems which are vulnerable. (Pentest People, 2019).
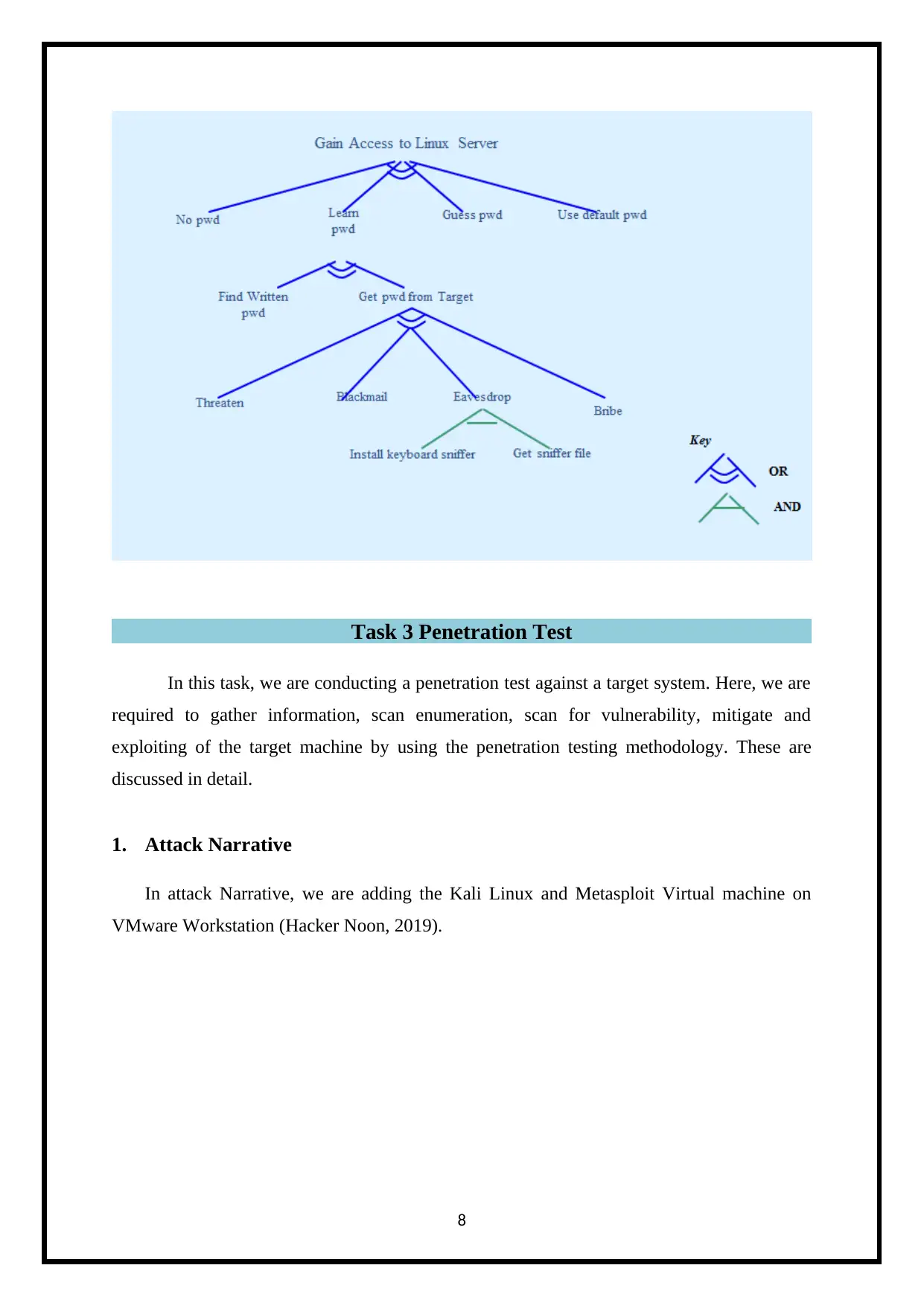
3. Decision Making Tree
Decision making tree for Penetration test is illustrated as below.
7
The threat modelling is a process for optimization of network security by
identifying the vulnerabilities and defining the counter measures to mitigate and prevent
the effects of threats to the system. It is used to determine where the most effort must be
applied to keep a system secure.
Vulnerability analysis
This phase is used for identifying and to evaluate the security risk posed by
vulnerabilities identification. The vulnerability analysis is divided into two steps such
as identification and validation. The identification is used for discovering the
vulnerability and it is main task of vulnerabilities analysis. The validation is used to
reduce the number of identified vulnerabilities to only those that are actually valid (IT
Security Concepts, 2019).
Exploitation
If vulnerabilities are identified, we try to exploit those vulnerabilities that can
breach the system and its security. The exploitation involves actually carrying out the
vulnerability to exploit in an effort to make certain if vulnerability is truly exploitable.
This phase consists of employing the heavy manual testing tactics and it often quite
time intensive. It may include overflow. SQL injection and OS commending and
more.
Post Exploitation
This phase is used for determining the machine value is compromised and to
maintain the machine control for later use. The machine value is determined by
understanding of the data stored on it and machine utility in additional negotiating the
network.
Reporting
The reporting phase is used to report the findings in a way that is
understandable and acceptable by the organization that owns the hardware or system.
It includes the defects which allow an attacker to violate an explicit security policy to
achieve the some impact. It is used to gain increased levels of access or interfere with
the normal operation of systems which are vulnerable. (Pentest People, 2019).
3. Decision Making Tree
Decision making tree for Penetration test is illustrated as below.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 3 Penetration Test
In this task, we are conducting a penetration test against a target system. Here, we are
required to gather information, scan enumeration, scan for vulnerability, mitigate and
exploiting of the target machine by using the penetration testing methodology. These are
discussed in detail.
1. Attack Narrative
In attack Narrative, we are adding the Kali Linux and Metasploit Virtual machine on
VMware Workstation (Hacker Noon, 2019).
8
In this task, we are conducting a penetration test against a target system. Here, we are
required to gather information, scan enumeration, scan for vulnerability, mitigate and
exploiting of the target machine by using the penetration testing methodology. These are
discussed in detail.
1. Attack Narrative
In attack Narrative, we are adding the Kali Linux and Metasploit Virtual machine on
VMware Workstation (Hacker Noon, 2019).
8
Then, click the power on to open the kali Linux and it is illustrated as below.
And, also click the power on to open the Metasploit and it is illustrated as below.
9
And, also click the power on to open the Metasploit and it is illustrated as below.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
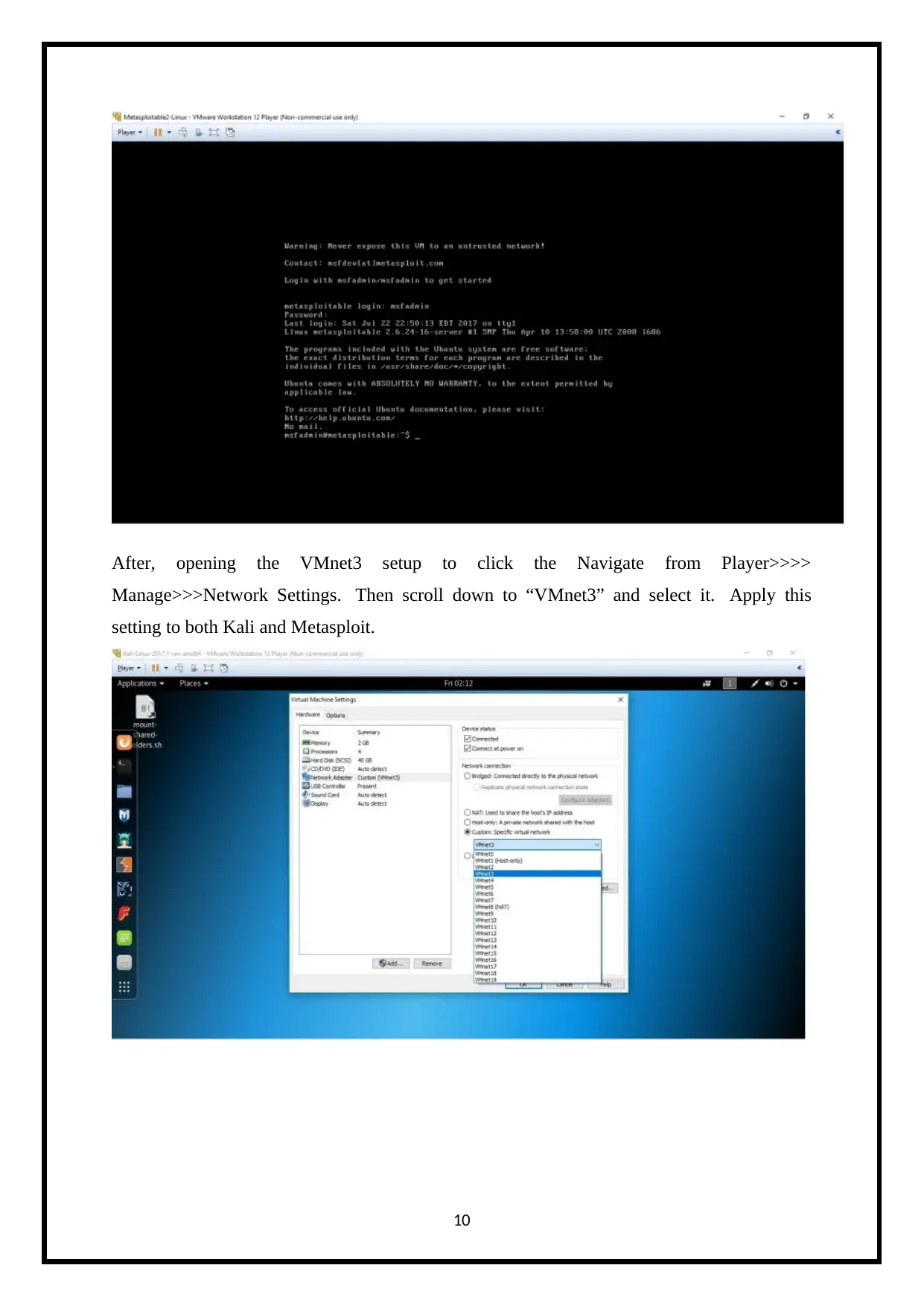
After, opening the VMnet3 setup to click the Navigate from Player>>>>
Manage>>>Network Settings. Then scroll down to “VMnet3” and select it. Apply this
setting to both Kali and Metasploit.
10
Manage>>>Network Settings. Then scroll down to “VMnet3” and select it. Apply this
setting to both Kali and Metasploit.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
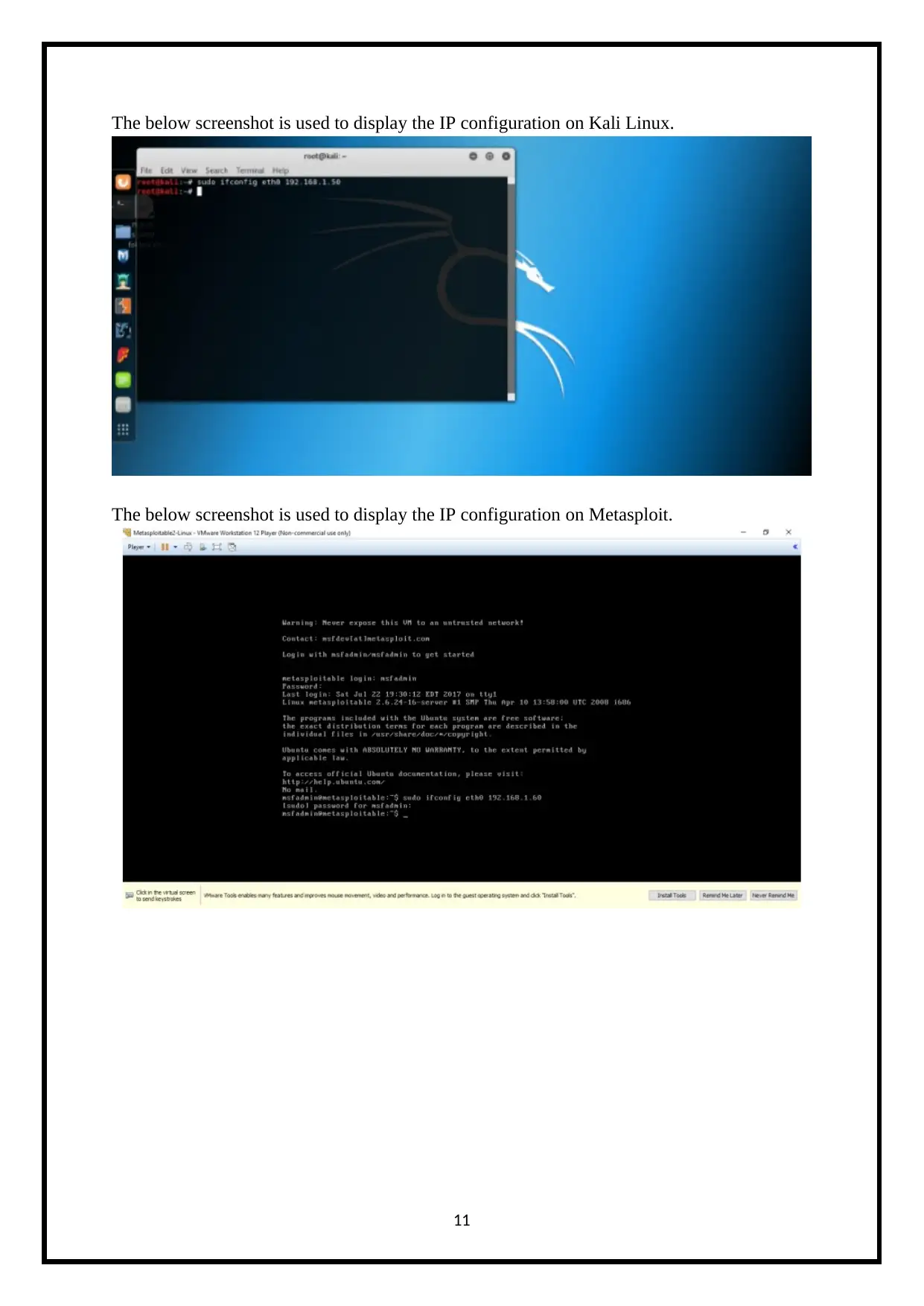
The below screenshot is used to display the IP configuration on Kali Linux.
The below screenshot is used to display the IP configuration on Metasploit.
11
The below screenshot is used to display the IP configuration on Metasploit.
11
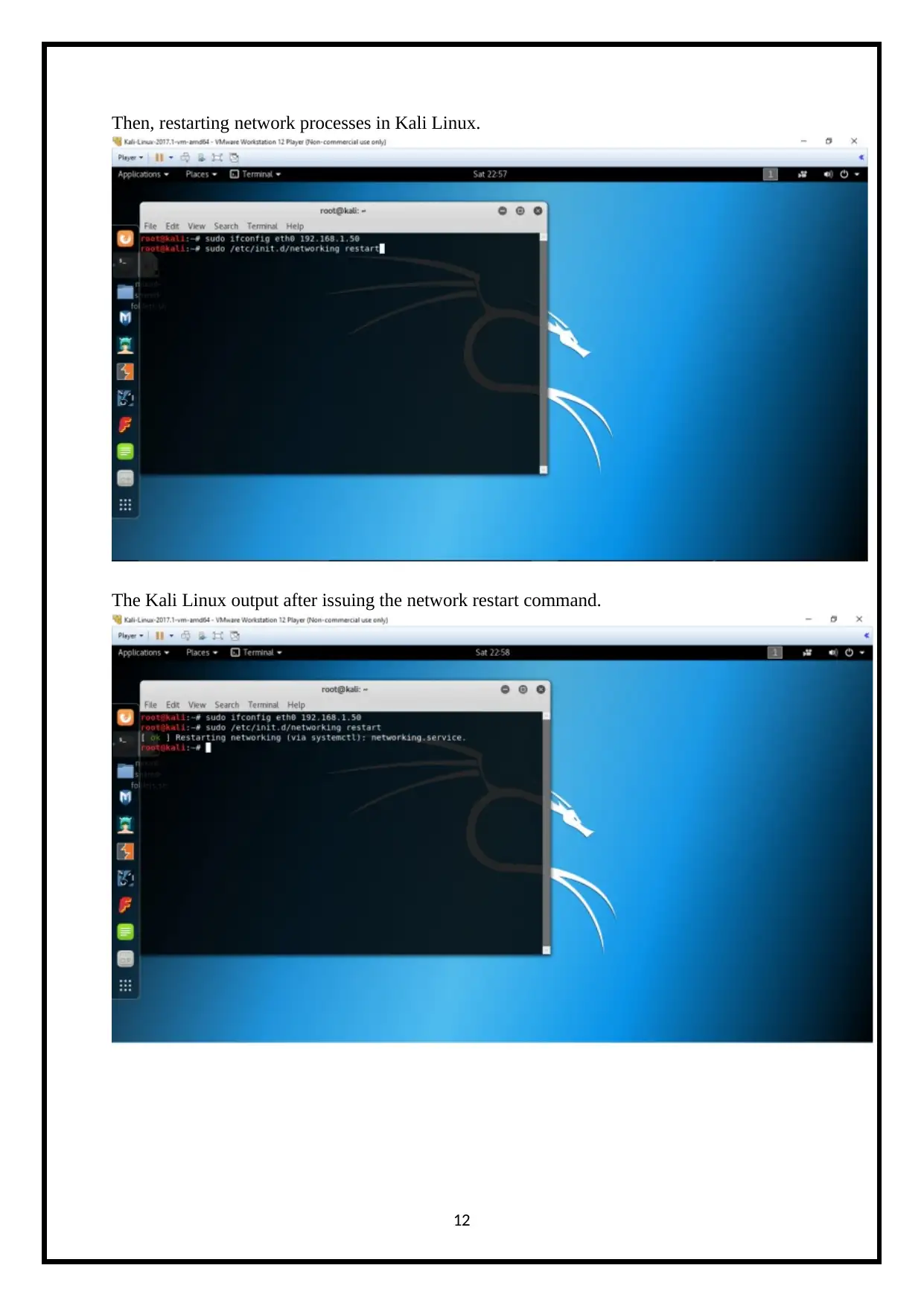
Then, restarting network processes in Kali Linux.
The Kali Linux output after issuing the network restart command.
12
The Kali Linux output after issuing the network restart command.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





