7COM1068 Penetration Testing Report: Assessment and Analysis
VerifiedAdded on 2022/08/17
|11
|2643
|13
Report
AI Summary
This report provides a detailed overview of penetration testing, a critical method in ethical hacking used to identify vulnerabilities in computer systems, web applications, and networks. It explores various penetration testing methodologies, including external, internal, targeted, blind, and double-blind testing, along with black box, white box, and gray box testing approaches. The report emphasizes the importance of statutory and ethical considerations for penetration testers, including professional codes of conduct and the need for informed decision-making. A Standard Operating Procedure (SOP) for penetration testing is also outlined, covering information gathering, planning, scanning, gaining access, maintaining access, and analysis phases. The report concludes by highlighting the primary purpose of penetration testing: to detect security weaknesses and enhance staff awareness within an organization.

Running head: PENETRATION TESTING
PENETRATION TESTING
Name of the Student
Name of the University
Author Note
PENETRATION TESTING
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PENETRATION TESTING 1
Table of Contents
Introduction:...............................................................................................................................2
Penetration testing:.....................................................................................................................2
Penetration testing methodologies:............................................................................................2
Statutory and ethical consideration:...........................................................................................5
SOP for penetration testing:.......................................................................................................6
Conclusion:................................................................................................................................8
References:.................................................................................................................................9
Table of Contents
Introduction:...............................................................................................................................2
Penetration testing:.....................................................................................................................2
Penetration testing methodologies:............................................................................................2
Statutory and ethical consideration:...........................................................................................5
SOP for penetration testing:.......................................................................................................6
Conclusion:................................................................................................................................8
References:.................................................................................................................................9

2PENETRATION TESTING
Introduction:
The purpose of this paper is to discuss about the penetration testing. Penetration
testing is a testing method related to ethical hacking. This method is used for testifying the
computer system, web application and network for searching the vulnerabilities. Ethical
hacker can use this technology for finding the vulnerabilities (Bock, Hughey and Levin,
2018). This technique has been performed manually. In this task the pen testing
methodologies will be discussed. In this report the ethical consideration will be also
discussed. A SOP will be also developed for undertaking the task 2.
Penetration testing:
Software application can automate the penetration testing method. This method not
only focused on the information of the system that has been penetrated but also works as the
protector of the IT infrastructure organization by making their security system strong
(Buchanan and Ramachandran, 2017). By the help of this technique after detecting the
vulnerabilities that is exploited by the actor after that this method helps in informing those
detected vulnerabilities to the client and the mitigation strategies are recommended by this
method.
Before the test one can gather the necessary information about the target and this can
be identified possibly the entry points and breaks in the points. For identifying the fault or the
weak point of the network security, this method has been used (Pozzobon et al., 2018). It is
also used for finding the weakness of the security of an organization. Identifying the
information about the weakness of the security of an organization or any company has
exploited through the help of this testing method.
Introduction:
The purpose of this paper is to discuss about the penetration testing. Penetration
testing is a testing method related to ethical hacking. This method is used for testifying the
computer system, web application and network for searching the vulnerabilities. Ethical
hacker can use this technology for finding the vulnerabilities (Bock, Hughey and Levin,
2018). This technique has been performed manually. In this task the pen testing
methodologies will be discussed. In this report the ethical consideration will be also
discussed. A SOP will be also developed for undertaking the task 2.
Penetration testing:
Software application can automate the penetration testing method. This method not
only focused on the information of the system that has been penetrated but also works as the
protector of the IT infrastructure organization by making their security system strong
(Buchanan and Ramachandran, 2017). By the help of this technique after detecting the
vulnerabilities that is exploited by the actor after that this method helps in informing those
detected vulnerabilities to the client and the mitigation strategies are recommended by this
method.
Before the test one can gather the necessary information about the target and this can
be identified possibly the entry points and breaks in the points. For identifying the fault or the
weak point of the network security, this method has been used (Pozzobon et al., 2018). It is
also used for finding the weakness of the security of an organization. Identifying the
information about the weakness of the security of an organization or any company has
exploited through the help of this testing method.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PENETRATION TESTING
Penetration testing methodologies:
This penetration testing has defined within the scope. By the help of this scope of
penetration testing one can detect the members of the team and the defenders whom has the
full allowance for accessing the systems of an organization or a company. This penetration
testing method is also referred as pen test method. Sometimes as the entry points are being
attempted by the good guys it is also called white hat attacks (Baloch, 2017). Main purpose of
the penetration testing is that the weakness of the security of an organization is detected and
the awareness of the staff is determined for the issues related to the security and the security
policy has been measured. Although a security policy can focus on detecting and preventing
an attack on the system of an enterprise. The policy might not include a procedure for
expelling a hacker.
If any organization affix the new infrastructure of the network or the applications then
this testing method has performed. As the penetration testing method is costly so the
organization with low budget can conduct it but a company with low budget may conduct it
once in every two years (Singh et al., 2018). A pen tester can use the penetration testing tool
for the testing method as this tools are used for detecting the malicious code from the code of
an application. The tools are used for going through the encryption technique of the data and
the hard code value that is user name, password are identified also. As an employee puts its
details like password on the sight that helps the hacker and that is also the relevance of the
worst security practice. For this purpose there are several numbers of methods to perform this
testing method that are as follows:
External testing method: In this testing method the details of the employees like email,
domain, web server and fire wall and devices which is visible outside the members of the
company or an organization that gives the hacker all necessary information about its target
and one can easily access it externally.
Penetration testing methodologies:
This penetration testing has defined within the scope. By the help of this scope of
penetration testing one can detect the members of the team and the defenders whom has the
full allowance for accessing the systems of an organization or a company. This penetration
testing method is also referred as pen test method. Sometimes as the entry points are being
attempted by the good guys it is also called white hat attacks (Baloch, 2017). Main purpose of
the penetration testing is that the weakness of the security of an organization is detected and
the awareness of the staff is determined for the issues related to the security and the security
policy has been measured. Although a security policy can focus on detecting and preventing
an attack on the system of an enterprise. The policy might not include a procedure for
expelling a hacker.
If any organization affix the new infrastructure of the network or the applications then
this testing method has performed. As the penetration testing method is costly so the
organization with low budget can conduct it but a company with low budget may conduct it
once in every two years (Singh et al., 2018). A pen tester can use the penetration testing tool
for the testing method as this tools are used for detecting the malicious code from the code of
an application. The tools are used for going through the encryption technique of the data and
the hard code value that is user name, password are identified also. As an employee puts its
details like password on the sight that helps the hacker and that is also the relevance of the
worst security practice. For this purpose there are several numbers of methods to perform this
testing method that are as follows:
External testing method: In this testing method the details of the employees like email,
domain, web server and fire wall and devices which is visible outside the members of the
company or an organization that gives the hacker all necessary information about its target
and one can easily access it externally.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PENETRATION TESTING
Internal testing method: Mimics is one of the insider attacks that it situated between the
firewall by the users who are authorized with a standard access privileges.
Targeted testing: An organization or IT sector has performed this testing method and this is
done together as a whole team. As this testing method is being carried out and this is shown
by everyone that's why it is called lights turned on approach (Najera-Gutierrez and Ansari,
2018).
Blind testing: The actions and procedures of a real attacker is simulated the blind testing
method and the information which is related to this testing procedure has given to the tester
or the team by which this method is tested. The considerable amount of time for
reconnaissance is required for this method. This method is an expensive one.
Double blind testing method: It follows steps the blind testing method. Actually it is similar
to the blind testing method fully. None but the one and two members of the team that have
consciousness about the penetration testing method, has performed this double blind testing
method. For the incident identification and its procedure this testing method is used. This is
also used for the security monitoring of an organization.
Black box testing: Black box testing is a penetration testing procedure by which a tester can
testify the weak spot and the vulnerabilities of the software. This is also the same as blind
testing method. For this method the internal structure of coding is not needed but graphical
user interface is only needed for this method (Casola et al., 2018). This method is also
referred as functional testing or closed box testing. This can be used by the tester, developer
and user. For this method detecting the hidden errors can be difficult as this penetration
testing procedure does not require the internal coding knowledge.
Internal testing method: Mimics is one of the insider attacks that it situated between the
firewall by the users who are authorized with a standard access privileges.
Targeted testing: An organization or IT sector has performed this testing method and this is
done together as a whole team. As this testing method is being carried out and this is shown
by everyone that's why it is called lights turned on approach (Najera-Gutierrez and Ansari,
2018).
Blind testing: The actions and procedures of a real attacker is simulated the blind testing
method and the information which is related to this testing procedure has given to the tester
or the team by which this method is tested. The considerable amount of time for
reconnaissance is required for this method. This method is an expensive one.
Double blind testing method: It follows steps the blind testing method. Actually it is similar
to the blind testing method fully. None but the one and two members of the team that have
consciousness about the penetration testing method, has performed this double blind testing
method. For the incident identification and its procedure this testing method is used. This is
also used for the security monitoring of an organization.
Black box testing: Black box testing is a penetration testing procedure by which a tester can
testify the weak spot and the vulnerabilities of the software. This is also the same as blind
testing method. For this method the internal structure of coding is not needed but graphical
user interface is only needed for this method (Casola et al., 2018). This method is also
referred as functional testing or closed box testing. This can be used by the tester, developer
and user. For this method detecting the hidden errors can be difficult as this penetration
testing procedure does not require the internal coding knowledge.

5PENETRATION TESTING
This is not appropriate for algorithm testing. This process takes little time as how much a
process consumes the time. This method also cover the resistance and security which is
against the viral attack.
White box testing: This penetration testing method is required for testifying the
vulnerabilities of the software and the application and also the internal structure of the
coding. Tester and developer can automate this testing method. The tester and the developer
have the knowledge of the coding which is required for this testing method. It is also referred
as clear box testing or glass box testing or code based testing method. By the use of this
testing method hidden errors are easily detected as internal structure of the coding is known
to the tester and developer. It is appropriate for the algorithm testing. It takes long time for
design the testing procedure as it has long code. By this penetration testing method resistance
cannot be covered and also the security is not covered.
Gray box testing: This is also a penetration testing procedure which determines the
vulnerabilities of the software. For this procedure tester and developer can have the partial
knowledge about the internal structure of coding. It can also be accessible by the end users. It
is also referred as translucent testing method. It is also same as the black box penetration
testing but in black box tester does not know the coding where as in gray box testing internal
structure of the is partially known to the tester. It is also not appropriate for algorithm testing.
It takes less time than white box testing. Here in this testing method resistance and the
security is not covered. Depending on the high level datagram and database this method is
performed. It is partially based on coding and also graphical user interface.
Statutory and ethical consideration:
The penetration testers those are professional fall back inevitable to the codes those
are professional in order to provide advice on their conduct. These codes need to very broad
This is not appropriate for algorithm testing. This process takes little time as how much a
process consumes the time. This method also cover the resistance and security which is
against the viral attack.
White box testing: This penetration testing method is required for testifying the
vulnerabilities of the software and the application and also the internal structure of the
coding. Tester and developer can automate this testing method. The tester and the developer
have the knowledge of the coding which is required for this testing method. It is also referred
as clear box testing or glass box testing or code based testing method. By the use of this
testing method hidden errors are easily detected as internal structure of the coding is known
to the tester and developer. It is appropriate for the algorithm testing. It takes long time for
design the testing procedure as it has long code. By this penetration testing method resistance
cannot be covered and also the security is not covered.
Gray box testing: This is also a penetration testing procedure which determines the
vulnerabilities of the software. For this procedure tester and developer can have the partial
knowledge about the internal structure of coding. It can also be accessible by the end users. It
is also referred as translucent testing method. It is also same as the black box penetration
testing but in black box tester does not know the coding where as in gray box testing internal
structure of the is partially known to the tester. It is also not appropriate for algorithm testing.
It takes less time than white box testing. Here in this testing method resistance and the
security is not covered. Depending on the high level datagram and database this method is
performed. It is partially based on coding and also graphical user interface.
Statutory and ethical consideration:
The penetration testers those are professional fall back inevitable to the codes those
are professional in order to provide advice on their conduct. These codes need to very broad
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6PENETRATION TESTING
in order to cover the concerns and the conflicts those are ethical yet they are particular
enough to guide the making of decisions in situations those are actual (Dürrwang et al.,
2018). The penetration testers are expected to take some decisions those are informed and
that is based on their understanding of the situation and it is supported by ethical, procedural
and technical training they have taken. A statement of intent should always be drawn and it
should be signed by both the tester and the client before any penetration testing It should be
outlined clearly the scope of the activity and the things that should and should not be done
while executing the penetration testing. For the penetration tester is essential to know that
who has the ownership of the systems or the business that are to be worked on and the
infrastructure between the systems those are to be tested and the targets that can get affected
by the penetration testing. The examination if the information technology breaches can reveal
so many things about an organisation. The breaches could have been prevented if the security
protocol were tested and maintained properly. However, most of the data breaches happens
for the smartness of the attacker as they were able to detect the security holes. The attack
could have been avoided if the organisation had identified the security holes in advance.
SOP for penetration testing:
During scanning, an application codes is being inspected during running and its
performance is provided a real-time-view. In third phase, taking control of the system has
been required after gaining the access. In fourth step, the system is needed for maintaining
the access and the target environment has involved persistently this step. And the last step
provides analytical summarization about the systems which is processed by this testing
method (Ross, Baji and Barnett, 2019). The penetration testing standards of execution covers
everything those are related to the testing of penetration. From the communication those are
initial, the gathering of information covers the phase of threat modelling where the
in order to cover the concerns and the conflicts those are ethical yet they are particular
enough to guide the making of decisions in situations those are actual (Dürrwang et al.,
2018). The penetration testers are expected to take some decisions those are informed and
that is based on their understanding of the situation and it is supported by ethical, procedural
and technical training they have taken. A statement of intent should always be drawn and it
should be signed by both the tester and the client before any penetration testing It should be
outlined clearly the scope of the activity and the things that should and should not be done
while executing the penetration testing. For the penetration tester is essential to know that
who has the ownership of the systems or the business that are to be worked on and the
infrastructure between the systems those are to be tested and the targets that can get affected
by the penetration testing. The examination if the information technology breaches can reveal
so many things about an organisation. The breaches could have been prevented if the security
protocol were tested and maintained properly. However, most of the data breaches happens
for the smartness of the attacker as they were able to detect the security holes. The attack
could have been avoided if the organisation had identified the security holes in advance.
SOP for penetration testing:
During scanning, an application codes is being inspected during running and its
performance is provided a real-time-view. In third phase, taking control of the system has
been required after gaining the access. In fourth step, the system is needed for maintaining
the access and the target environment has involved persistently this step. And the last step
provides analytical summarization about the systems which is processed by this testing
method (Ross, Baji and Barnett, 2019). The penetration testing standards of execution covers
everything those are related to the testing of penetration. From the communication those are
initial, the gathering of information covers the phase of threat modelling where the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
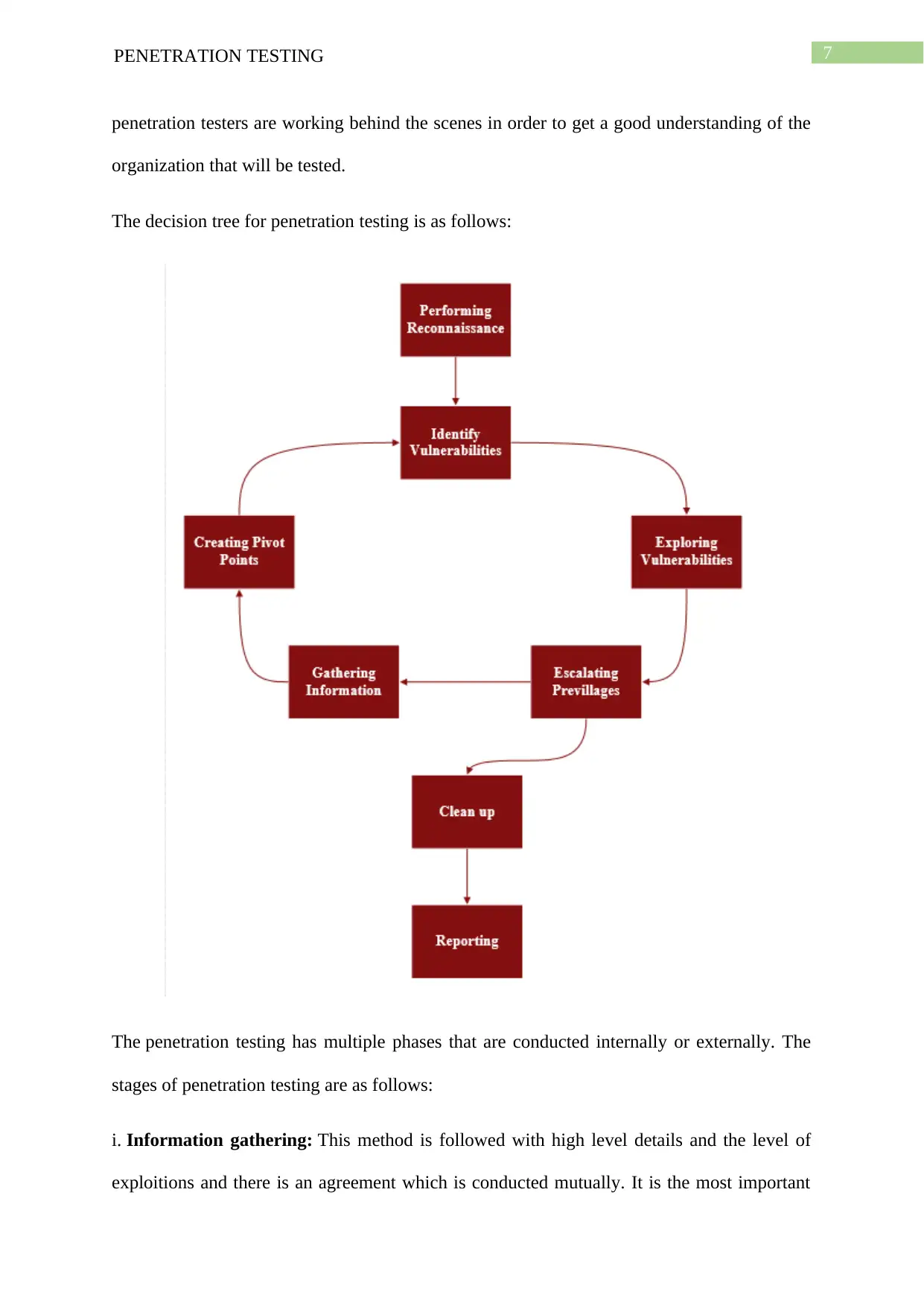
7PENETRATION TESTING
penetration testers are working behind the scenes in order to get a good understanding of the
organization that will be tested.
The decision tree for penetration testing is as follows:
The penetration testing has multiple phases that are conducted internally or externally. The
stages of penetration testing are as follows:
i. Information gathering: This method is followed with high level details and the level of
exploitions and there is an agreement which is conducted mutually. It is the most important
penetration testers are working behind the scenes in order to get a good understanding of the
organization that will be tested.
The decision tree for penetration testing is as follows:
The penetration testing has multiple phases that are conducted internally or externally. The
stages of penetration testing are as follows:
i. Information gathering: This method is followed with high level details and the level of
exploitions and there is an agreement which is conducted mutually. It is the most important

8PENETRATION TESTING
phase of penetration testing. In this testing phase one can gather the information about the
target and then this process is done.
ii. Planning and Reconnaissance: In this method additional information can be identified by
the penetration tester that is not being provided or have been overlooked. This method is used
for internal or external penetration testing of the network. In mobile phone application, web
application this testing method is not needed.
iii. Scanning: This is the step after the Reconnaissance is performed. In this step the intrusion
attempts can be responded and in what manner can be understood by the tester. This is also
performed in two ways named static analysis and dynamic analysis (Shmaryahu et al., 2017).
In dynamic analysis application code which is running out can be inspected. The real time
view of the application has been provided. In static analysis the application code is inspected
and the behavior of the application code is estimated during execution.
iv. Gaining access: In this step tester has given allowance to exploit the vulnerabilities of the
system. The damage like stealing data, intercepting, traffic that is caused, can understand by
the penetration testing method.
iv. Maintaining access: The aim of the penetration testing method is to maintain the
vulnerabilities which can be used for achieving the persistence of the system.
v. Analysis: In this step the vulnerabilities will be analyzed and suitable actions will be
taken.
Conclusion:
Thus, it can be concluded from the entire report that the primary purpose of the
penetration testing is to find the weakness of the security technologies within an organization
is detected and the awareness. In addition, the staffs are determined and aware of the issues
phase of penetration testing. In this testing phase one can gather the information about the
target and then this process is done.
ii. Planning and Reconnaissance: In this method additional information can be identified by
the penetration tester that is not being provided or have been overlooked. This method is used
for internal or external penetration testing of the network. In mobile phone application, web
application this testing method is not needed.
iii. Scanning: This is the step after the Reconnaissance is performed. In this step the intrusion
attempts can be responded and in what manner can be understood by the tester. This is also
performed in two ways named static analysis and dynamic analysis (Shmaryahu et al., 2017).
In dynamic analysis application code which is running out can be inspected. The real time
view of the application has been provided. In static analysis the application code is inspected
and the behavior of the application code is estimated during execution.
iv. Gaining access: In this step tester has given allowance to exploit the vulnerabilities of the
system. The damage like stealing data, intercepting, traffic that is caused, can understand by
the penetration testing method.
iv. Maintaining access: The aim of the penetration testing method is to maintain the
vulnerabilities which can be used for achieving the persistence of the system.
v. Analysis: In this step the vulnerabilities will be analyzed and suitable actions will be
taken.
Conclusion:
Thus, it can be concluded from the entire report that the primary purpose of the
penetration testing is to find the weakness of the security technologies within an organization
is detected and the awareness. In addition, the staffs are determined and aware of the issues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PENETRATION TESTING
related to the security. The organisations have to make sure that the security policy has been
measured. The penetration testing tools are utilized to go through the encryption technique of
the data and for finding the vulnerabilities existed within the system such as the hard code
value that is user name, password are identified also.
References:
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Bock, K., Hughey, G. and Levin, D., 2018. King of the Hill: A Novel Cybersecurity
Competition for Teaching Penetration Testing. In 2018 {USENIX} Workshop on Advances in
Security Education ({ASE} 18).
Buchanan, C. and Ramachandran, V., 2017. Kali Linux Wireless Penetration Testing
Beginner's Guide: Master wireless testing techniques to survey and attack wireless networks
with Kali Linux, including the KRACK attack. Packt Publishing Ltd.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.
related to the security. The organisations have to make sure that the security policy has been
measured. The penetration testing tools are utilized to go through the encryption technique of
the data and for finding the vulnerabilities existed within the system such as the hard code
value that is user name, password are identified also.
References:
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Bock, K., Hughey, G. and Levin, D., 2018. King of the Hill: A Novel Cybersecurity
Competition for Teaching Penetration Testing. In 2018 {USENIX} Workshop on Advances in
Security Education ({ASE} 18).
Buchanan, C. and Ramachandran, V., 2017. Kali Linux Wireless Penetration Testing
Beginner's Guide: Master wireless testing techniques to survey and attack wireless networks
with Kali Linux, including the KRACK attack. Packt Publishing Ltd.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PENETRATION TESTING
Ross, R., Baji, A. and Barnett, D., 2019. Inner Profile Measurement for Pipes Using
Penetration Testing. Sensors, 19(2), p.237.
Shmaryahu, D., Shani, G., Hoffmann, J. and Steinmetz, M., 2017. Partially observable
contingent planning for penetration testing. In Iwaise: First international workshop on
artificial intelligence in security (Vol. 33).
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
Ross, R., Baji, A. and Barnett, D., 2019. Inner Profile Measurement for Pipes Using
Penetration Testing. Sensors, 19(2), p.237.
Shmaryahu, D., Shani, G., Hoffmann, J. and Steinmetz, M., 2017. Partially observable
contingent planning for penetration testing. In Iwaise: First international workshop on
artificial intelligence in security (Vol. 33).
Singh, A., Jaswal, N., Agarwal, M. and Teixeira, D., 2018. Metasploit Penetration Testing
Cookbook: Evade antiviruses, bypass firewalls, and exploit complex environments with the
most widely used penetration testing framework. Packt Publishing Ltd.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





