MN623 T2 2019: Penetration Testing Tool Demonstration
VerifiedAdded on 2022/09/17
|8
|300
|24
Report
AI Summary
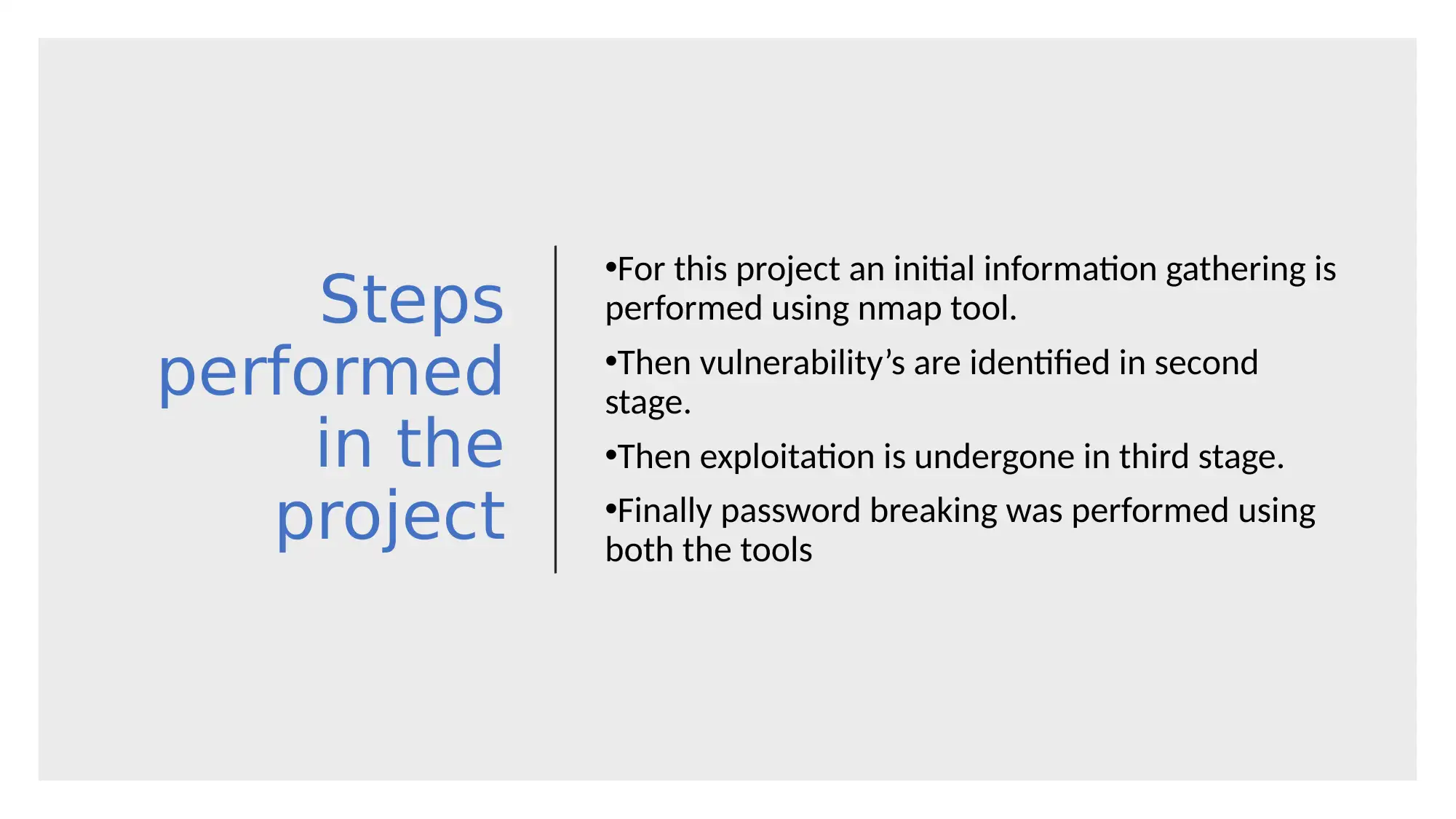
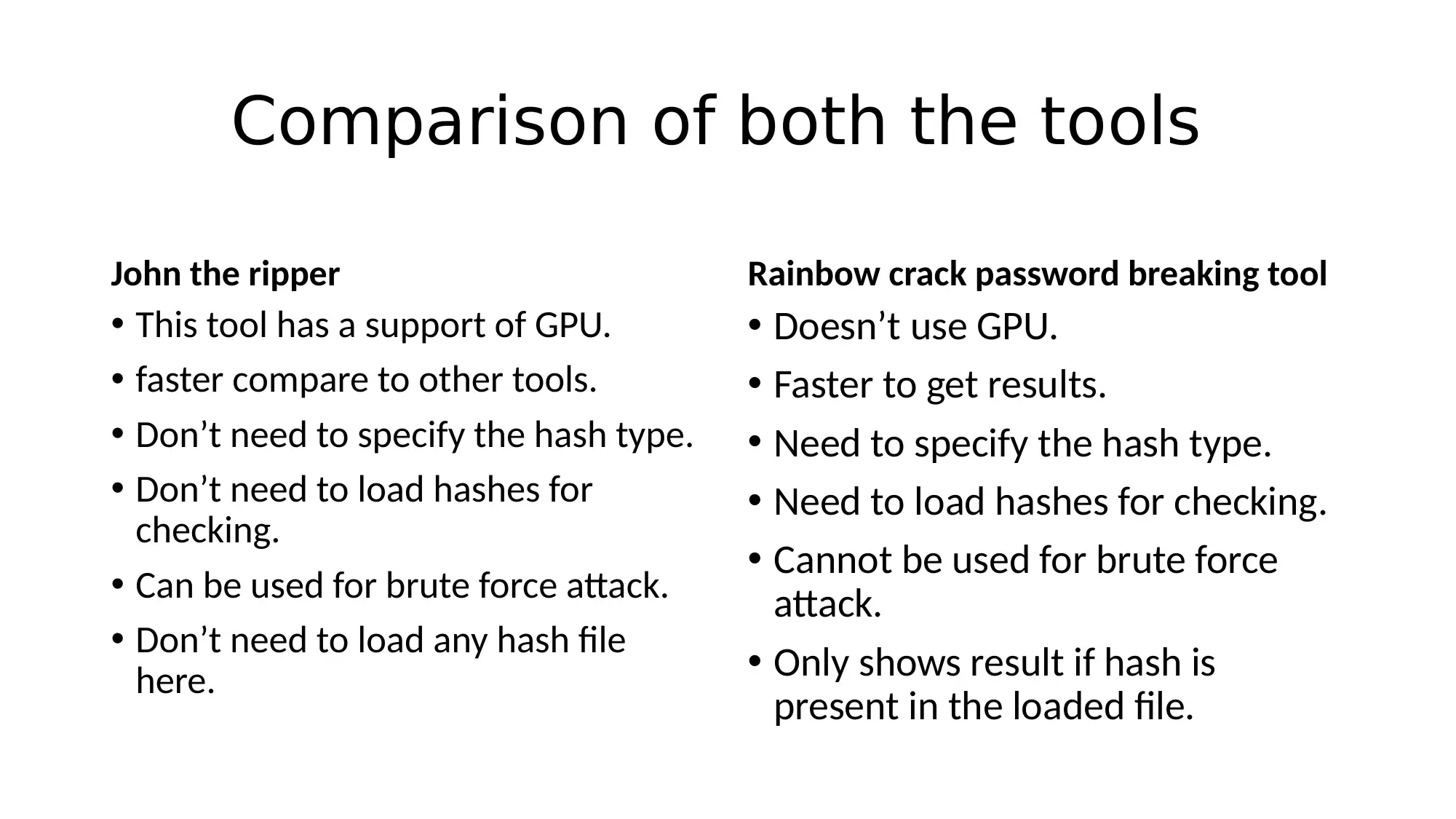
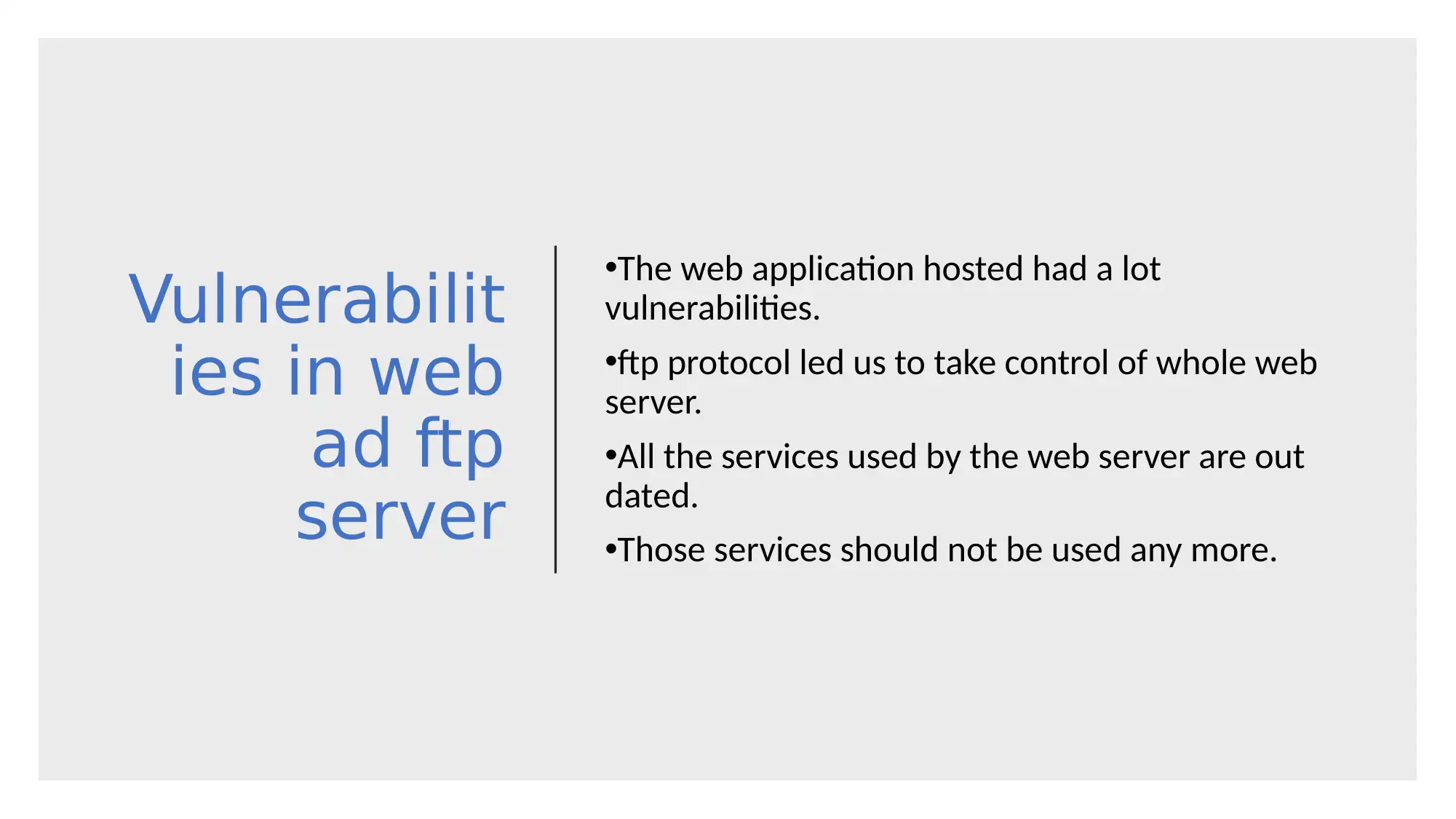
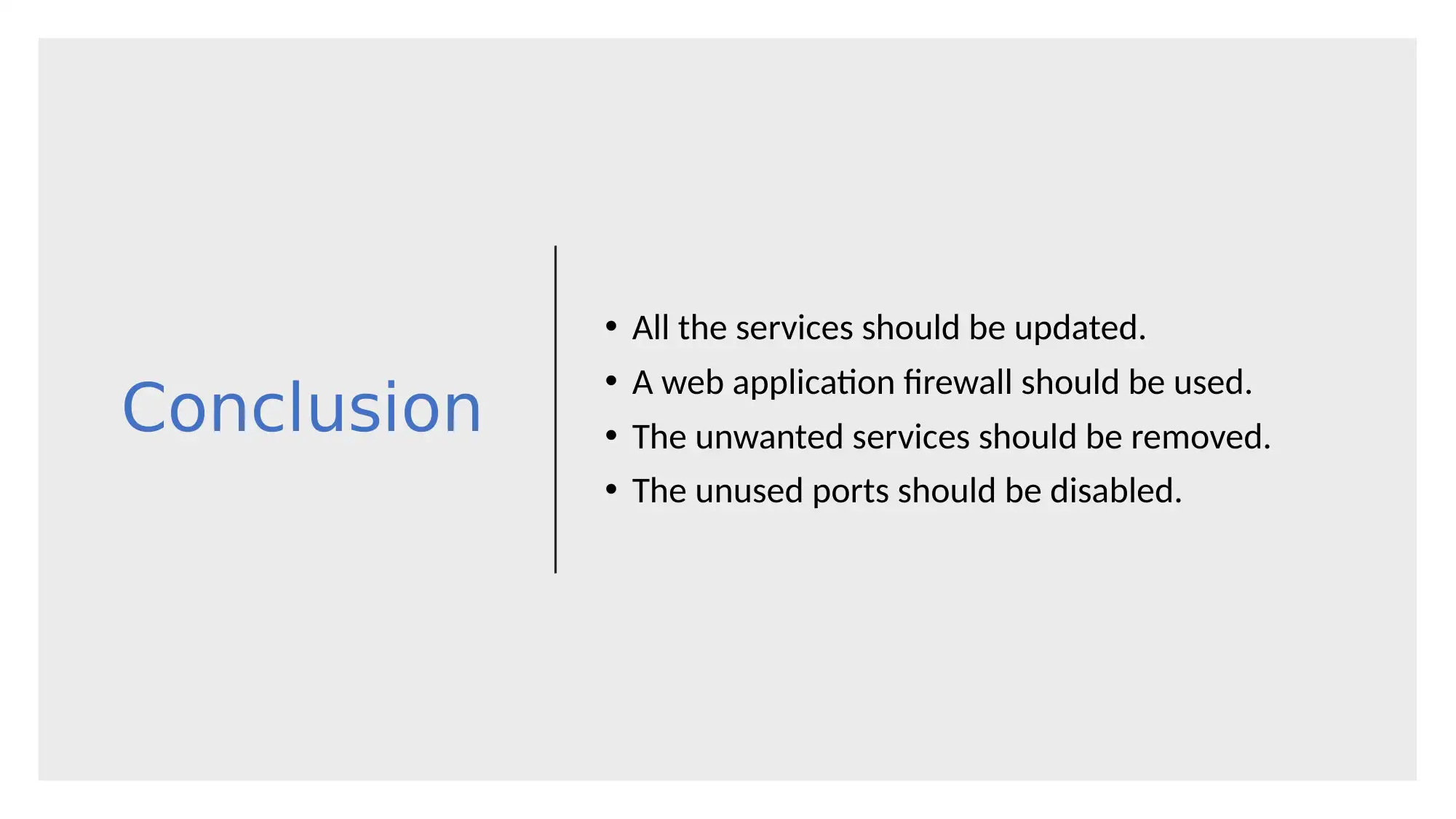
This report provides a comparative analysis of two password cracking tools, John the Ripper and RainbowCrack, used in penetration testing. The project involved initial information gathering using nmap, vulnerability identification, exploitation, and password breaking. The report details the steps performed, including the use of both tools, and compares their features, such as GPU support, hash type specification, and brute force capabilities. Analysis reveals John the Ripper's advantages in ease of use, while RainbowCrack excels in performance with large datasets. The report also highlights vulnerabilities in a web and FTP server, concluding with recommendations for service updates, web application firewalls, and disabling unused services and ports. References to relevant cybersecurity resources are included.
1 out of 8










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)