Pen Testing SOP Report: Methodologies, Considerations, and SOP
VerifiedAdded on 2022/08/12
|13
|3107
|17
Report
AI Summary
This report provides a detailed exploration of Pen Testing (PT), encompassing its methodologies, ethical and statutory considerations, and the development of Standard Operation Procedures (SOP). It begins by defining PT as a crucial ethical hacking procedure for detecting security threats, highlighting various PT types like Black Box, Network, Application, Wireless, and Client-side testing. The report then delves into diverse PT methodologies such as data collection, vulnerability assessment, exploitation, and result analysis. It addresses the limitations of PT, including server crashes and data exposure, as well as tool limitations. The report emphasizes the importance of ethical considerations, such as maintaining ethical hacking procedures, analyzing potential impacts, and indemnification. Furthermore, it outlines the development of an SOP for a full-scale penetration test, including intelligence gathering, vulnerability analysis, and exploitation, using tools like Kali Linux and nmap. A decision-making tree (DMT) is presented to illustrate the decision process in PT, and the report concludes by summarizing the significance of PT in improving network infrastructure and reducing downtime.

Running head: SOP FOR PEN TESTING
SOP for Pen Testing
Name of the Student
Name of the University
Author Note
SOP for Pen Testing
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SOP FOR PEN TESTING
Table of Contents
1. Introduction............................................................................................................................2
2. Types of penetration testing methodologies..........................................................................3
3. Critical Reflection..................................................................................................................4
4. Statutory considerations of a penetration tester.....................................................................4
5. Ethical considerations of a penetration tester.........................................................................5
6. Development of Standard Operation Procedure....................................................................5
7. Decision Making Tree (DMT)...............................................................................................6
8. Conclusion..............................................................................................................................7
9. Reference..............................................................................................................................10
Table of Contents
1. Introduction............................................................................................................................2
2. Types of penetration testing methodologies..........................................................................3
3. Critical Reflection..................................................................................................................4
4. Statutory considerations of a penetration tester.....................................................................4
5. Ethical considerations of a penetration tester.........................................................................5
6. Development of Standard Operation Procedure....................................................................5
7. Decision Making Tree (DMT)...............................................................................................6
8. Conclusion..............................................................................................................................7
9. Reference..............................................................................................................................10

2SOP FOR PEN TESTING
1. Introduction
Pen Testing (PT) is defined as the type of ethical hacking procedure which is
increasingly deployed by the IT experts to arrange and detect the diverse categories of
security threats (Najera-Gutierrez and Ansari 2018). The monitoring necessities of a private
network can be identified with the help of penetration testing. This procedure is very much
useful to improve the network downtime, at the same time it can also be said that different
categories of network security breaches can be minimized with the help of pen testing as
well. There are diverse categories of PT techniques which are increasingly deployed by the
IT experts such as the followings:
Black Box PT: It is defined as the type of testing which is conducted by ethical
hackers who has no knowledge of the system being attacked. The dynamic analysis of
the current situation is analysed with the currently running programs in this
penetration testing.
Network PT: It is defined as the type of ethical hacking procedure which is very
much required to identify the security vulnerabilities of a network (Wolf 2019). This
type of testing can be conducted with the help of diverse categories of software or
manually by the pen testers.
Application PT: The effectiveness of a security protocol can be identified in the first
place with the help of application penetration testing. The probable risks of a network
can be highlighted using this PT.
Wireless PT: It is defined as the type of third party audit procedure to look after the
security of all the wireless devices which exists in an organizational network (Shah et
al. 2019). All the licensed links which are used in the organizational settings are
1. Introduction
Pen Testing (PT) is defined as the type of ethical hacking procedure which is
increasingly deployed by the IT experts to arrange and detect the diverse categories of
security threats (Najera-Gutierrez and Ansari 2018). The monitoring necessities of a private
network can be identified with the help of penetration testing. This procedure is very much
useful to improve the network downtime, at the same time it can also be said that different
categories of network security breaches can be minimized with the help of pen testing as
well. There are diverse categories of PT techniques which are increasingly deployed by the
IT experts such as the followings:
Black Box PT: It is defined as the type of testing which is conducted by ethical
hackers who has no knowledge of the system being attacked. The dynamic analysis of
the current situation is analysed with the currently running programs in this
penetration testing.
Network PT: It is defined as the type of ethical hacking procedure which is very
much required to identify the security vulnerabilities of a network (Wolf 2019). This
type of testing can be conducted with the help of diverse categories of software or
manually by the pen testers.
Application PT: The effectiveness of a security protocol can be identified in the first
place with the help of application penetration testing. The probable risks of a network
can be highlighted using this PT.
Wireless PT: It is defined as the type of third party audit procedure to look after the
security of all the wireless devices which exists in an organizational network (Shah et
al. 2019). All the licensed links which are used in the organizational settings are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SOP FOR PEN TESTING
verified with the help of this penetration. The role of a wireless engineer is very much
significant to conduct wireless PT.
Client side PT: There are diverse categories of security vulnerabilities which exists in
client software and it has a direct adverse impact on the data which comes in and
moves out of a network. The essential critical assets of a network are assessed with
the help of this PT.
This portfolio shall be focussing on the different categories of PT methodologies,
statutory and ethical considerations of the penetration testers, development of Standard
Operation Procedure (SOP), and the significance of a decision making tree.
2. Types of penetration testing methodologies
There are diverse categories of PM methodologies which are practised by the pen
testers such as the followings:
Data collection: Web page source code analysis is one of the prime ways to collected
data about a target system data (Satria et al. 2018). Information about the use of
database, name of the tables, use of the different versions of software and hardware,
and role of the third party vendors can be understood with the help of the data
collected from web page source code analysis.
Vulnerability assessment: Security vulnerabilities have to be detected from the data
collected from web page source code analysis (Seng, Ithnin and Shaid 2018). The
entry points can be understood from the vulnerability assessment procedure.
Actual exploitation: IT Skills of the experienced penetration testers must be very
much on the higher side to exploit the security vulnerabilities of a network.
verified with the help of this penetration. The role of a wireless engineer is very much
significant to conduct wireless PT.
Client side PT: There are diverse categories of security vulnerabilities which exists in
client software and it has a direct adverse impact on the data which comes in and
moves out of a network. The essential critical assets of a network are assessed with
the help of this PT.
This portfolio shall be focussing on the different categories of PT methodologies,
statutory and ethical considerations of the penetration testers, development of Standard
Operation Procedure (SOP), and the significance of a decision making tree.
2. Types of penetration testing methodologies
There are diverse categories of PM methodologies which are practised by the pen
testers such as the followings:
Data collection: Web page source code analysis is one of the prime ways to collected
data about a target system data (Satria et al. 2018). Information about the use of
database, name of the tables, use of the different versions of software and hardware,
and role of the third party vendors can be understood with the help of the data
collected from web page source code analysis.
Vulnerability assessment: Security vulnerabilities have to be detected from the data
collected from web page source code analysis (Seng, Ithnin and Shaid 2018). The
entry points can be understood from the vulnerability assessment procedure.
Actual exploitation: IT Skills of the experienced penetration testers must be very
much on the higher side to exploit the security vulnerabilities of a network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SOP FOR PEN TESTING
Result analysis and report preparation: Corrective actions are required to be taken
by the penetration testers (Shaukat, et al. 2016). A detailed vulnerability format has to
be created to understand the effectiveness of penetration testing.
3. Critical Reflection
According to Baloch (2017), crashing of servers and expose of the sensitive data are
the two most significant limitations of pen-testing. The research of this article suggested that
employee data or the production data of a commercial establishment can get corrupted due to
pen testing. On the other hand, as discussed by Dürrwang et al. (2018), limitations of the
tools required in pen testing and access to the penetration testers are the prime limitations PM
methodologies.
As discussed by Najera-Gutierrez and Ansari (2018), the use of Kali Linux is very
much useful to identify the networking security of a network. The researchers of this paper
help in identifying that set of Kali Linux is much simpler than the other penetration tools. On
the other hand, as elaborated by Ottosson and Lindquist (2018), open Source Security Testing
Methodology Manual is very much useful for the penetration testers to make use of Kali
Linux Commands. Apart from Kali Linux, there are other PT tools which are used in PT such
as Metasploit, Wire shark, and John the Ripper (Linux 2019). The researchers of this paper
helped in understanding that Nessus scanners is the other major PT tool which can be used by
the pen testers as the reliability of this scanning technique is very much on the higher side as
compared with the other PT tools.
4. Statutory considerations of a penetration tester
Having access to sensitive data is one of the notable statutory considerations of a
pentester (Najera-Gutierrez and Ansari 2018). Guaranteeing the security of the data which is
lost due to pen testing is a major statutory consideration from the perspective of a pentester
Result analysis and report preparation: Corrective actions are required to be taken
by the penetration testers (Shaukat, et al. 2016). A detailed vulnerability format has to
be created to understand the effectiveness of penetration testing.
3. Critical Reflection
According to Baloch (2017), crashing of servers and expose of the sensitive data are
the two most significant limitations of pen-testing. The research of this article suggested that
employee data or the production data of a commercial establishment can get corrupted due to
pen testing. On the other hand, as discussed by Dürrwang et al. (2018), limitations of the
tools required in pen testing and access to the penetration testers are the prime limitations PM
methodologies.
As discussed by Najera-Gutierrez and Ansari (2018), the use of Kali Linux is very
much useful to identify the networking security of a network. The researchers of this paper
help in identifying that set of Kali Linux is much simpler than the other penetration tools. On
the other hand, as elaborated by Ottosson and Lindquist (2018), open Source Security Testing
Methodology Manual is very much useful for the penetration testers to make use of Kali
Linux Commands. Apart from Kali Linux, there are other PT tools which are used in PT such
as Metasploit, Wire shark, and John the Ripper (Linux 2019). The researchers of this paper
helped in understanding that Nessus scanners is the other major PT tool which can be used by
the pen testers as the reliability of this scanning technique is very much on the higher side as
compared with the other PT tools.
4. Statutory considerations of a penetration tester
Having access to sensitive data is one of the notable statutory considerations of a
pentester (Najera-Gutierrez and Ansari 2018). Guaranteeing the security of the data which is
lost due to pen testing is a major statutory consideration from the perspective of a pentester

5SOP FOR PEN TESTING
(Pozzobon et al. 2018). Maintaining the confidentiality of the PT procedure is also one of the
prime statutory considerations of a penetration tester.
5. Ethical considerations of a penetration tester
Maintaining the procedures of ethical hacking is one of the major ethical
considerations faced by the pen testers all over the world (Gunawan et al. 2018). Analysing
the potential impact is the other ethical considerations related to the PT procedure.
Indemnification is the process which causes damage after a PT procedure and this process is
the other ethical consideration of pen-testing. Development of the scope of work is also
considered as the ethical considerations of internal pen-testing (Ibrahim and Kant 2018).
Identification of the realistic challenges of a pen-testing procedure is one of the prime ethical
considerations of pen-testing. Maintaining the skill set is one of the other ethical
considerations of a penetration tester.
6. Development of Standard Operation Procedure
The second task of this assignment shall be assessing the ability to conduct a full-
scale penetration test. A target organization will be shared where penetration testing has to be
conducted. This task shall be conducted with the help of a VPN, the details of the detected
vulnerabilities shall be assessed in the report along with the mitigation strategies. The tasks
which will be undertaken in the second assignment can be understood from the following
table.
SOP for Pen testing
Name of the organization Bright Star
Approval of the process Harry Kane
Purpose of the testing To detect the security threats
in the organization.
To reduce the rate of the
network downtime.
Procedure Intelligence gathering: Vulnerability analysis: The
(Pozzobon et al. 2018). Maintaining the confidentiality of the PT procedure is also one of the
prime statutory considerations of a penetration tester.
5. Ethical considerations of a penetration tester
Maintaining the procedures of ethical hacking is one of the major ethical
considerations faced by the pen testers all over the world (Gunawan et al. 2018). Analysing
the potential impact is the other ethical considerations related to the PT procedure.
Indemnification is the process which causes damage after a PT procedure and this process is
the other ethical consideration of pen-testing. Development of the scope of work is also
considered as the ethical considerations of internal pen-testing (Ibrahim and Kant 2018).
Identification of the realistic challenges of a pen-testing procedure is one of the prime ethical
considerations of pen-testing. Maintaining the skill set is one of the other ethical
considerations of a penetration tester.
6. Development of Standard Operation Procedure
The second task of this assignment shall be assessing the ability to conduct a full-
scale penetration test. A target organization will be shared where penetration testing has to be
conducted. This task shall be conducted with the help of a VPN, the details of the detected
vulnerabilities shall be assessed in the report along with the mitigation strategies. The tasks
which will be undertaken in the second assignment can be understood from the following
table.
SOP for Pen testing
Name of the organization Bright Star
Approval of the process Harry Kane
Purpose of the testing To detect the security threats
in the organization.
To reduce the rate of the
network downtime.
Procedure Intelligence gathering: Vulnerability analysis: The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SOP FOR PEN TESTING
Before the selection of the
test goals detailed
information must be
gathered by the tester. Test
goals of the project must be
defined in the first place.
target vulnerabilities must
be uncovered by the
penetration testers. The APT
must be managing the
perimeters of this testing
procedure in a systemized
modus.
Vulnerability
identification: There are
diverse categories of tools
which can be used to scan
the networking vulnerability
of an organization such as
Kali Linux (Chu and Lisitsa
2018). This licensed tool has
different types of commands
such as nmap which can be
used to the entire network of
the selected organization
(Dawson and McDonald
2016). The open ports and
the security risks of the
organization can be easily
detected using the nmap
(Dürrwang et al. 2018)
Target exploitation: The
effectiveness of using the
Web Application Firewall in
the organization has to be
assessed with the help of
online platforms like
imperva (Gaddam and
Nandhini 2017). Most of the
suspicious activities in the
network can be detected in
the first place if the WAF is
configured in a systemized
modus.
Table 1: SOP for PT
(Source: Created by author)
7. Decision Making Tree (DMT)
DMT is defined as the type of tree which are very much useful to predict the outcome
of a decision-making process. The traces of each path to the conclusion can be identified with
the help of the DMT (Casola et al. 2018). The decision nodes can also be identified with the
help of the DMT. The set of activities which has to be conducted in the second phase of this
assignment is illustrated with the help of the following decision tree diagram.
Before the selection of the
test goals detailed
information must be
gathered by the tester. Test
goals of the project must be
defined in the first place.
target vulnerabilities must
be uncovered by the
penetration testers. The APT
must be managing the
perimeters of this testing
procedure in a systemized
modus.
Vulnerability
identification: There are
diverse categories of tools
which can be used to scan
the networking vulnerability
of an organization such as
Kali Linux (Chu and Lisitsa
2018). This licensed tool has
different types of commands
such as nmap which can be
used to the entire network of
the selected organization
(Dawson and McDonald
2016). The open ports and
the security risks of the
organization can be easily
detected using the nmap
(Dürrwang et al. 2018)
Target exploitation: The
effectiveness of using the
Web Application Firewall in
the organization has to be
assessed with the help of
online platforms like
imperva (Gaddam and
Nandhini 2017). Most of the
suspicious activities in the
network can be detected in
the first place if the WAF is
configured in a systemized
modus.
Table 1: SOP for PT
(Source: Created by author)
7. Decision Making Tree (DMT)
DMT is defined as the type of tree which are very much useful to predict the outcome
of a decision-making process. The traces of each path to the conclusion can be identified with
the help of the DMT (Casola et al. 2018). The decision nodes can also be identified with the
help of the DMT. The set of activities which has to be conducted in the second phase of this
assignment is illustrated with the help of the following decision tree diagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
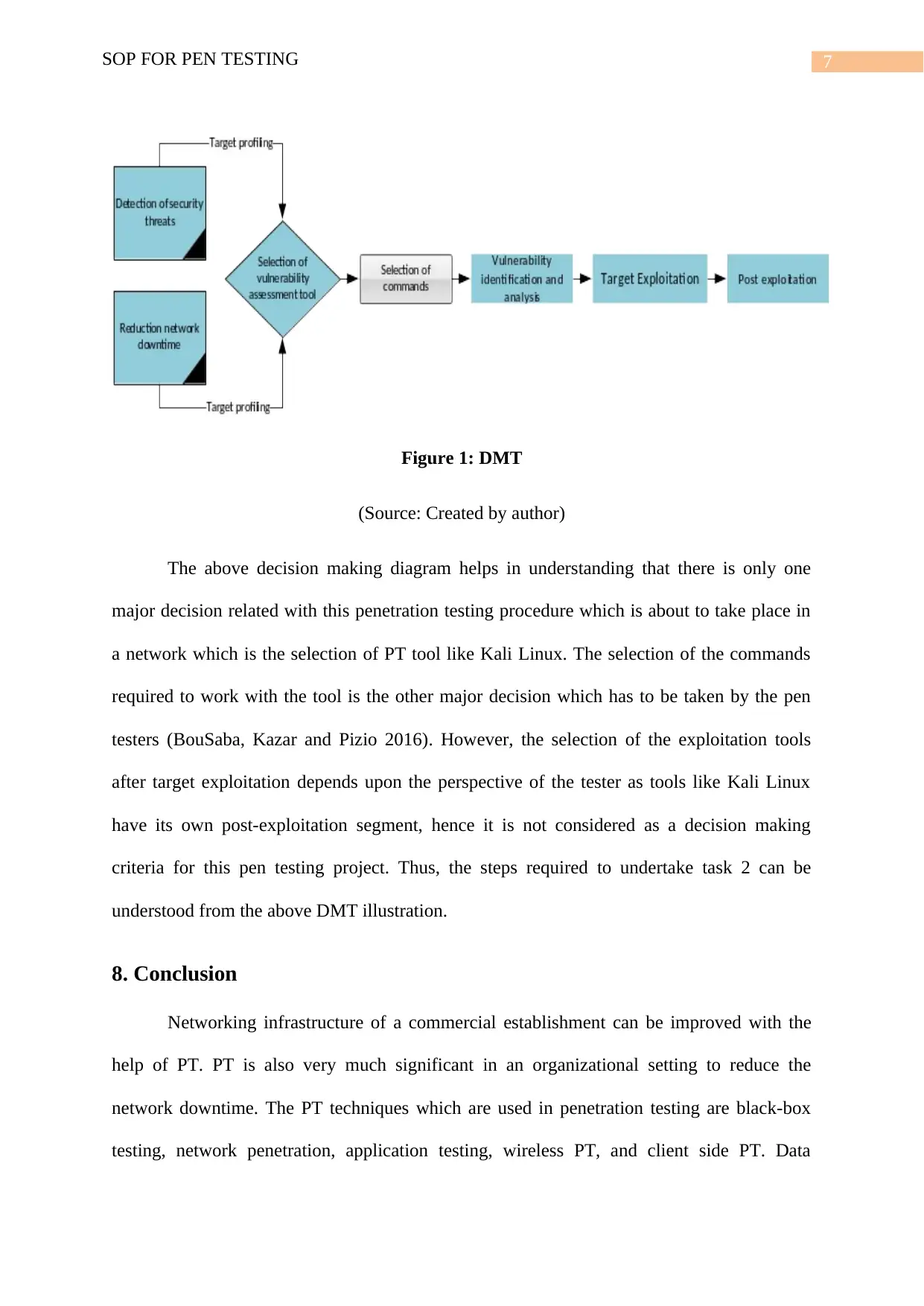
7SOP FOR PEN TESTING
Figure 1: DMT
(Source: Created by author)
The above decision making diagram helps in understanding that there is only one
major decision related with this penetration testing procedure which is about to take place in
a network which is the selection of PT tool like Kali Linux. The selection of the commands
required to work with the tool is the other major decision which has to be taken by the pen
testers (BouSaba, Kazar and Pizio 2016). However, the selection of the exploitation tools
after target exploitation depends upon the perspective of the tester as tools like Kali Linux
have its own post-exploitation segment, hence it is not considered as a decision making
criteria for this pen testing project. Thus, the steps required to undertake task 2 can be
understood from the above DMT illustration.
8. Conclusion
Networking infrastructure of a commercial establishment can be improved with the
help of PT. PT is also very much significant in an organizational setting to reduce the
network downtime. The PT techniques which are used in penetration testing are black-box
testing, network penetration, application testing, wireless PT, and client side PT. Data
Figure 1: DMT
(Source: Created by author)
The above decision making diagram helps in understanding that there is only one
major decision related with this penetration testing procedure which is about to take place in
a network which is the selection of PT tool like Kali Linux. The selection of the commands
required to work with the tool is the other major decision which has to be taken by the pen
testers (BouSaba, Kazar and Pizio 2016). However, the selection of the exploitation tools
after target exploitation depends upon the perspective of the tester as tools like Kali Linux
have its own post-exploitation segment, hence it is not considered as a decision making
criteria for this pen testing project. Thus, the steps required to undertake task 2 can be
understood from the above DMT illustration.
8. Conclusion
Networking infrastructure of a commercial establishment can be improved with the
help of PT. PT is also very much significant in an organizational setting to reduce the
network downtime. The PT techniques which are used in penetration testing are black-box
testing, network penetration, application testing, wireless PT, and client side PT. Data

8SOP FOR PEN TESTING
collection is the primary step of penetration testing which can be done with the help of web
page source code analysis. Entry points can be identified from the vulnerability assessment
procedure. The IT skills of the penetration tester is very much significant to exploit the
security vulnerabilities of a network. Corrective actions are needed to be taken by the
penetration testers to order to improve the reliability of the testing procedure. The
effectiveness of penetration testing can be identified in the first place with the help of a
detailed vulnerability report. Based on the literature analysis, it can be concluded that pen
testing can not only help to detect the security loopholes of a network but also helps to deal
with challenges such as crashing of servers, and minimizing data exposure. Limitation of PT
tools and access of the penetration testers are the prime drawbacks of penetration testing. Kali
Linux is defined as the type of tool which is very much useful to detect the networking
security of an organization. The other PT tools which are increasingly used by the pen testers
such as the Metaspoilt, Wire Shirk, and John the Ripper. Apart from these penetration tools,
Nessus can also be used in the penetration testing process as the reliability of this scanning
technique is very much on the higher side. Having access to the sensitive data and
guaranteeing the security of the data is one of the most significant statutory considerations of
a penetration tester. Maintaining the procedure of ethical hacking is the major ethical
considerations faced by the penetration tester. Analysing the impact of penetration testing is
the other ethical considerations of a penetration tester. Consistency of a project or a process
can be improved in the first place with the help of Standard Operation Procedure. The SOP of
task 2 is intelligence gathering where test goals shall be defined, the vulnerabilities shall be
identified with the help of PT tools like Kali Linux and its commands like nmap. The
perimeters of penetration testing shall be identified with the help of APT and online platforms
like imperva will play a huge role to find the effectiveness of WAF. The importance of the
significant decision in a process or a project can be understood with the help of decision
collection is the primary step of penetration testing which can be done with the help of web
page source code analysis. Entry points can be identified from the vulnerability assessment
procedure. The IT skills of the penetration tester is very much significant to exploit the
security vulnerabilities of a network. Corrective actions are needed to be taken by the
penetration testers to order to improve the reliability of the testing procedure. The
effectiveness of penetration testing can be identified in the first place with the help of a
detailed vulnerability report. Based on the literature analysis, it can be concluded that pen
testing can not only help to detect the security loopholes of a network but also helps to deal
with challenges such as crashing of servers, and minimizing data exposure. Limitation of PT
tools and access of the penetration testers are the prime drawbacks of penetration testing. Kali
Linux is defined as the type of tool which is very much useful to detect the networking
security of an organization. The other PT tools which are increasingly used by the pen testers
such as the Metaspoilt, Wire Shirk, and John the Ripper. Apart from these penetration tools,
Nessus can also be used in the penetration testing process as the reliability of this scanning
technique is very much on the higher side. Having access to the sensitive data and
guaranteeing the security of the data is one of the most significant statutory considerations of
a penetration tester. Maintaining the procedure of ethical hacking is the major ethical
considerations faced by the penetration tester. Analysing the impact of penetration testing is
the other ethical considerations of a penetration tester. Consistency of a project or a process
can be improved in the first place with the help of Standard Operation Procedure. The SOP of
task 2 is intelligence gathering where test goals shall be defined, the vulnerabilities shall be
identified with the help of PT tools like Kali Linux and its commands like nmap. The
perimeters of penetration testing shall be identified with the help of APT and online platforms
like imperva will play a huge role to find the effectiveness of WAF. The importance of the
significant decision in a process or a project can be understood with the help of decision
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9SOP FOR PEN TESTING
nodes of the DMT. The decision tree was very much useful to understand that the selection
of the PT tool is one of the prime decision which has to be taken by the pen testers in the pen
testing procedure which will be conducted on the next assignment.
nodes of the DMT. The decision tree was very much useful to understand that the selection
of the PT tool is one of the prime decision which has to be taken by the pen testers in the pen
testing procedure which will be conducted on the next assignment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SOP FOR PEN TESTING
9. Reference
Baloch, R., 2017. Ethical hacking and penetration testing guide. Auerbach Publications.
BouSaba, C., Kazar, T. and Pizio, W.C., 2016. Wireless network security using Raspberry Pi.
In 2016 ASEE Annual Conference & Exposition Proceedings.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chu, G. and Lisitsa, A., 2018, June. Penetration testing for internet of things and its
automation. In 2018 IEEE 20th International Conference on High Performance Computing
and Communications; IEEE 16th International Conference on Smart City; IEEE 4th
International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp. 1479-
1484). IEEE.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp.
51-58). IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
9. Reference
Baloch, R., 2017. Ethical hacking and penetration testing guide. Auerbach Publications.
BouSaba, C., Kazar, T. and Pizio, W.C., 2016. Wireless network security using Raspberry Pi.
In 2016 ASEE Annual Conference & Exposition Proceedings.
Casola, V., De Benedictis, A., Rak, M. and Villano, U., 2018, June. Towards automated
penetration testing for cloud applications. In 2018 IEEE 27th International Conference on
Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE) (pp. 24-29).
IEEE.
Chu, G. and Lisitsa, A., 2018, June. Penetration testing for internet of things and its
automation. In 2018 IEEE 20th International Conference on High Performance Computing
and Communications; IEEE 16th International Conference on Smart City; IEEE 4th
International Conference on Data Science and Systems (HPCC/SmartCity/DSS) (pp. 1479-
1484). IEEE.
Dawson, J. and McDonald, J.T., 2016, April. Improving Penetration Testing Methodologies
for Security-Based Risk Assessment. In 2016 Cybersecurity Symposium (CYBERSEC) (pp.
51-58). IEEE.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.
Dürrwang, J., Braun, J., Rumez, M., Kriesten, R. and Pretschner, A., 2018. Enhancement of
automotive penetration testing with threat analyses results. SAE International Journal of
Transportation Cybersecurity and Privacy, 1(11-01-02-0005), pp.91-112.

11SOP FOR PEN TESTING
Gaddam, R. and Nandhini, M., 2017, March. An analysis of various snort based techniques to
detect and prevent intrusions in networks proposal with code refactoring snort tool in Kali
Linux environment. In 2017 International Conference on Inventive Communication and
Computational Technologies (ICICCT) (pp. 10-15). IEEE.
Gunawan, T.S., Lim, M.K., Zulkurnain, N.F. and Kartiwi, M., 2018. On the Review and
Setup of Security Audit Using Kali Linux. Indonesian Journal of Electrical Engineering and
Computer Science, 11(1), pp.51-59.
Ibrahim, A.B. and Kant, S., 2018. Penetration Testing Using SQL Injection to Recognize the
Vulnerable Point on Web Pages. International Journal of Applied Engineering Research,
13(8), pp.5935-5942.
Linux, K., 2019. Kali Linux.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Ottosson, H. and Lindquist, P., 2018. Penetration testing for the inexperienced ethical hacker:
A baseline methodology for detecting and mitigating web application vulnerabilities.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.
Satria, D., Alanda, A., Erianda, A. and Prayama, D., 2018. Network Security Assessment
Using Internal Network Penetration Testing Methodology. JOIV: International Journal on
Informatics Visualization, 2(4-2), pp.360-365.
Gaddam, R. and Nandhini, M., 2017, March. An analysis of various snort based techniques to
detect and prevent intrusions in networks proposal with code refactoring snort tool in Kali
Linux environment. In 2017 International Conference on Inventive Communication and
Computational Technologies (ICICCT) (pp. 10-15). IEEE.
Gunawan, T.S., Lim, M.K., Zulkurnain, N.F. and Kartiwi, M., 2018. On the Review and
Setup of Security Audit Using Kali Linux. Indonesian Journal of Electrical Engineering and
Computer Science, 11(1), pp.51-59.
Ibrahim, A.B. and Kant, S., 2018. Penetration Testing Using SQL Injection to Recognize the
Vulnerable Point on Web Pages. International Journal of Applied Engineering Research,
13(8), pp.5935-5942.
Linux, K., 2019. Kali Linux.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Najera-Gutierrez, G. and Ansari, J.A., 2018. Web Penetration Testing with Kali Linux:
Explore the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Ottosson, H. and Lindquist, P., 2018. Penetration testing for the inexperienced ethical hacker:
A baseline methodology for detecting and mitigating web application vulnerabilities.
Pozzobon, E., Weiss, N., Renner, S. and Hackenberg, R., 2018. A Survey on Media Access
Solutions for CAN Penetration Testing.
Satria, D., Alanda, A., Erianda, A. and Prayama, D., 2018. Network Security Assessment
Using Internal Network Penetration Testing Methodology. JOIV: International Journal on
Informatics Visualization, 2(4-2), pp.360-365.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





