Pen Testing Report: 7COM1068 Module, University of Hertfordshire
VerifiedAdded on 2022/08/18
|13
|2640
|12
Report
AI Summary
This report provides a comprehensive overview of penetration testing, covering various methodologies, legal considerations, and standard operating procedures (SOP). The report begins by comparing different pen testing methods, including black box, grey box, and white box testing, detailing their characteristics, advantages, and disadvantages. It then delves into the statutory and legal considerations that penetration testers must be aware of, such as laws related to port scanning and the Computer Fraud and Abuse Act, emphasizing the importance of ethical conduct and authorized permissions. Furthermore, the report outlines a Standard Operating Procedure (SOP) for IT security penetration testing, including introductions, purposes, scope, roles, and responsibilities of the testing team, and processes for managing the penetration test. The SOP also specifies the roles of the Pen Test Point of Contact (POC), activities, and procedures involved in a penetration testing project, from introductory briefings to technical meetings and policy reviews. The report highlights the significance of each aspect of the penetration testing process to ensure that the tests are conducted ethically, legally, and effectively.

Running head: PEN TESTING
PEN TESTING
Name of the Student
Name of the University
Author note
PEN TESTING
Name of the Student
Name of the University
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PEN TESTING
Table of Contents
Comparison in between pen testing methods..................................................................................2
Statutory and legal consideration for a penetration tester...............................................................5
SOP for task 2..................................................................................................................................7
Decision making tree.....................................................................................................................10
References......................................................................................................................................11
PEN TESTING
Table of Contents
Comparison in between pen testing methods..................................................................................2
Statutory and legal consideration for a penetration tester...............................................................5
SOP for task 2..................................................................................................................................7
Decision making tree.....................................................................................................................10
References......................................................................................................................................11
2
PEN TESTING
Comparison in between pen testing methods
The different pen testing methods that are considered are namely black box penetration
testing, grey box penetration testing and white box penetration testing.
Serial Number Black box Testing Grey Box Testing White Box Testing
1. In case of black box
testing the internal
working of the
application is not
required to be known
by the tester.
In case of the Grey
box testing partial
knowledge of the
internal working of
the application is
known to the tester.
In case of the White
Box testing process,
the internal working
of the application is
completely known to
the tester (Rani and
Nagpal 2019).
2. The process of black
box testing is also
known as the data
driven testing. The
data that are required
for the testing process
is provided to the
tester and hence wise
the tester performs
the test. The tester
acts non functional
Grey box testing is
also known as
translucent testing
process. In this
process the tester is
provided with partial
data and the tester
hence wise gathers
the other important
data and hence wise
this benefits the
White box testing is
also known as clear
box testing. It is also
termed as structured
testing. It is also
known as code based
testing (Khera,
Kumar and Garg
2019).
PEN TESTING
Comparison in between pen testing methods
The different pen testing methods that are considered are namely black box penetration
testing, grey box penetration testing and white box penetration testing.
Serial Number Black box Testing Grey Box Testing White Box Testing
1. In case of black box
testing the internal
working of the
application is not
required to be known
by the tester.
In case of the Grey
box testing partial
knowledge of the
internal working of
the application is
known to the tester.
In case of the White
Box testing process,
the internal working
of the application is
completely known to
the tester (Rani and
Nagpal 2019).
2. The process of black
box testing is also
known as the data
driven testing. The
data that are required
for the testing process
is provided to the
tester and hence wise
the tester performs
the test. The tester
acts non functional
Grey box testing is
also known as
translucent testing
process. In this
process the tester is
provided with partial
data and the tester
hence wise gathers
the other important
data and hence wise
this benefits the
White box testing is
also known as clear
box testing. It is also
termed as structured
testing. It is also
known as code based
testing (Khera,
Kumar and Garg
2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
PEN TESTING
when there is no data
provided.
entire operational
process. The tester is
allowed till a certain
level of internal
infrastructure.
3. The testing process
includes joint efforts
of end users, testers
and the developers.
As there is no access
to the internal
framework of the
application, the tester
needs to proper
guidance of the end
user and the
developer for gaining
proper data sets.
This testing process
is also performed
with the efforts of the
developers, end users
and the testers (Choi
et al 2019). As access
to the internal
framework of the
application is limited,
there is a requirement
of the developer and
the end user to get
into the process.
This testing is
performed only with
the help of the tester
and the developer.
There is no such
requirement
regarding the
presence of the end
user in the process of
testing.
4. The entire testing is
made on the
processing of the
external behavior.
Internal behavior is
The testing process is
performed as per the
understanding of the
database diagram.
This ensures that the
In this case the
internal working is
already known and
hence there is no such
requirement of the
PEN TESTING
when there is no data
provided.
entire operational
process. The tester is
allowed till a certain
level of internal
infrastructure.
3. The testing process
includes joint efforts
of end users, testers
and the developers.
As there is no access
to the internal
framework of the
application, the tester
needs to proper
guidance of the end
user and the
developer for gaining
proper data sets.
This testing process
is also performed
with the efforts of the
developers, end users
and the testers (Choi
et al 2019). As access
to the internal
framework of the
application is limited,
there is a requirement
of the developer and
the end user to get
into the process.
This testing is
performed only with
the help of the tester
and the developer.
There is no such
requirement
regarding the
presence of the end
user in the process of
testing.
4. The entire testing is
made on the
processing of the
external behavior.
Internal behavior is
The testing process is
performed as per the
understanding of the
database diagram.
This ensures that the
In this case the
internal working is
already known and
hence there is no such
requirement of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
PEN TESTING
not known in the
process. External
expectation have
been the prime
analysis point.
data that are derived
in the processing of
the data flow
diagrams acts as the
major prospect for
the testers (Al Shebli
and Beheshti 2018).
data flow diagram,
database diagrams
and the external
expectation for
completion of the
testing process.
5. This process
consumers the least
time. This ensures
that the time that is
required in proper
processing of the
testing method is
very low. It is also
least exhaustive in
nature as well.
This process
consumes more time
than that of the black
box testing method. It
can be stated that the
exhaustiveness of the
process have been
higher as well.
This type of testing is
considered to be the
most time consuming
process. This ensures
that exhaustiveness of
the process have been
the highest as well.
6. This testing process
is considered to be
not suited for the
algorithm testing.
This testing process
is also not suited for
the algorithm testing
process.
This process is suited
for performing the
algorithm testing
process.
7. The sole method that
can be used in the
In this testing
process, the data
In this testing
process, data domains
PEN TESTING
not known in the
process. External
expectation have
been the prime
analysis point.
data that are derived
in the processing of
the data flow
diagrams acts as the
major prospect for
the testers (Al Shebli
and Beheshti 2018).
data flow diagram,
database diagrams
and the external
expectation for
completion of the
testing process.
5. This process
consumers the least
time. This ensures
that the time that is
required in proper
processing of the
testing method is
very low. It is also
least exhaustive in
nature as well.
This process
consumes more time
than that of the black
box testing method. It
can be stated that the
exhaustiveness of the
process have been
higher as well.
This type of testing is
considered to be the
most time consuming
process. This ensures
that exhaustiveness of
the process have been
the highest as well.
6. This testing process
is considered to be
not suited for the
algorithm testing.
This testing process
is also not suited for
the algorithm testing
process.
This process is suited
for performing the
algorithm testing
process.
7. The sole method that
can be used in the
In this testing
process, the data
In this testing
process, data domains
5
PEN TESTING
process is trial and
error method
domains and the
internal boundaries
are tested.
and internal
boundaries are
properly tested and is
performed in a better
manner (Krasniqi and
Bejtullahu 2018).
Statutory and legal consideration for a penetration tester
There are certain laws that are to be known by the penetration tester. This section ensures
that there have been a proper assessment of the latest legal consideration that are to be followed
before performing the penetration testing. The pen testers needs to properly stay aware of the law
suits that are present surrounding the port scanning process. There are certain aspects that are to
be considered. This section ensures that there are presence of several laws that are to be followed
(Pozzobo et al 2018). There have been pen testers who have been arrested due to the violation of
the Computer Fraud and Abuse act of America Section 1030(a).(5).(B). The case was later
dismissed due to lack of merit in the case. In several nations there are stringent laws that have
been providing stricter assessment of the pen testing process. The major security issue that have
been seen whole performing penetration testing ensures that there have been presence of security
tools that are based on the intent of the user (Baloch 2017). Analyzing of ethics while performing
the testing process is also considered and this is the main scope for pen tester to be proven
innocent. The pen tester needs to perform proper analysis of the activities that a pen tester is
allowed in each of the project. It is seen that there is setting of different limitation for the testers
for performing the testing process. The pen testers needs to properly get their job authorized
PEN TESTING
process is trial and
error method
domains and the
internal boundaries
are tested.
and internal
boundaries are
properly tested and is
performed in a better
manner (Krasniqi and
Bejtullahu 2018).
Statutory and legal consideration for a penetration tester
There are certain laws that are to be known by the penetration tester. This section ensures
that there have been a proper assessment of the latest legal consideration that are to be followed
before performing the penetration testing. The pen testers needs to properly stay aware of the law
suits that are present surrounding the port scanning process. There are certain aspects that are to
be considered. This section ensures that there are presence of several laws that are to be followed
(Pozzobo et al 2018). There have been pen testers who have been arrested due to the violation of
the Computer Fraud and Abuse act of America Section 1030(a).(5).(B). The case was later
dismissed due to lack of merit in the case. In several nations there are stringent laws that have
been providing stricter assessment of the pen testing process. The major security issue that have
been seen whole performing penetration testing ensures that there have been presence of security
tools that are based on the intent of the user (Baloch 2017). Analyzing of ethics while performing
the testing process is also considered and this is the main scope for pen tester to be proven
innocent. The pen tester needs to perform proper analysis of the activities that a pen tester is
allowed in each of the project. It is seen that there is setting of different limitation for the testers
for performing the testing process. The pen testers needs to properly get their job authorized
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PEN TESTING
(Denis, Zena and Hayajneh 2016). This section ensures that there is a need of proper
understanding of exactly how tight, the entire pent testing process will be performed. Permission
for each and every step is to be taken on order to perform the pen testing. In case authorized
permission is present, there will not be any kind of issue regarding the penetration testing
process. Another consideration that is to be maintained is that external networks need not be
getting affected in the process. In case the external network gets affected the entire working
process will be getting unethical in nature. Then this will also be considered as an offence from
the pen testers (Chen et al 2018). There are new laws that are being formed and framed in a
regular basis. This ensures that there have been a proper assessment of the rules that are present
in the organization. Clear security process have been another aspect that is to be considered and
this have been the major aspect that have been playing an important role in the security clearance
practice. The rules that are ever evolving will be another aspect that will be providing a better
result. It have been seen that there have been instances that pen testers have been arrested due to
improper penetration process (Seng, Ithnin and Shaid 2018). Thus it can be stated that the
penetration testing process needs to be verified by the higher authorities. It have been seen that in
case the pen testing process that is considered is not verified by the higher authority, the entire
work process gets affected in a negative manner. This can lead to heavy penalization to the tester
and even get arrested (Jan et al 2016). Again it have been seen that there have been few instances
where the tester have performed the testing process and while performing the testing process, the
tester have lost control over the process and crossed its limits. Despite the fact that it was not
deliberate, the entire working process will be considered to be a deliberate act of gaining data in
an unauthorized manner.
PEN TESTING
(Denis, Zena and Hayajneh 2016). This section ensures that there is a need of proper
understanding of exactly how tight, the entire pent testing process will be performed. Permission
for each and every step is to be taken on order to perform the pen testing. In case authorized
permission is present, there will not be any kind of issue regarding the penetration testing
process. Another consideration that is to be maintained is that external networks need not be
getting affected in the process. In case the external network gets affected the entire working
process will be getting unethical in nature. Then this will also be considered as an offence from
the pen testers (Chen et al 2018). There are new laws that are being formed and framed in a
regular basis. This ensures that there have been a proper assessment of the rules that are present
in the organization. Clear security process have been another aspect that is to be considered and
this have been the major aspect that have been playing an important role in the security clearance
practice. The rules that are ever evolving will be another aspect that will be providing a better
result. It have been seen that there have been instances that pen testers have been arrested due to
improper penetration process (Seng, Ithnin and Shaid 2018). Thus it can be stated that the
penetration testing process needs to be verified by the higher authorities. It have been seen that in
case the pen testing process that is considered is not verified by the higher authority, the entire
work process gets affected in a negative manner. This can lead to heavy penalization to the tester
and even get arrested (Jan et al 2016). Again it have been seen that there have been few instances
where the tester have performed the testing process and while performing the testing process, the
tester have lost control over the process and crossed its limits. Despite the fact that it was not
deliberate, the entire working process will be considered to be a deliberate act of gaining data in
an unauthorized manner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PEN TESTING
SOP for task 2
The Standard Operating Process ensures that there have been a proper assessment of the
procedures that will be helpful in performing the IT security penetration testing. The SOP will be
having a basic introduction to the process and hence wise the purpose and the scope of the SOP
will be stated. After these, basic understanding of the data analysis will be made.
Introduction
Penetration testing is considered to be an activity, in which the testing team tries to evade
the security process. The testing team is supposed to gain access to the privileged access to the
information. This ensures the fact that there have been proper assessment of the scope of the
tests. This ensures that there have been a proper management of the minimization of the impact
imposed on the usefulness of the test results.
Purpose
The purpose of the Standard Operating Process is to gain a proper understanding of the
rules that are important in the operating process. Different rules of engagement is also stated in
the process. Creating a proper understanding of the different technologies that can be
implemented for performing the penetration testing is also provided.
Scope
The scope of the project is to perform proper analysis of the employees as well as
contractors and this ensures that there have been proper granting of the project activities as per
the testing methodology.
Roles and Responsibilities
PEN TESTING
SOP for task 2
The Standard Operating Process ensures that there have been a proper assessment of the
procedures that will be helpful in performing the IT security penetration testing. The SOP will be
having a basic introduction to the process and hence wise the purpose and the scope of the SOP
will be stated. After these, basic understanding of the data analysis will be made.
Introduction
Penetration testing is considered to be an activity, in which the testing team tries to evade
the security process. The testing team is supposed to gain access to the privileged access to the
information. This ensures the fact that there have been proper assessment of the scope of the
tests. This ensures that there have been a proper management of the minimization of the impact
imposed on the usefulness of the test results.
Purpose
The purpose of the Standard Operating Process is to gain a proper understanding of the
rules that are important in the operating process. Different rules of engagement is also stated in
the process. Creating a proper understanding of the different technologies that can be
implemented for performing the penetration testing is also provided.
Scope
The scope of the project is to perform proper analysis of the employees as well as
contractors and this ensures that there have been proper granting of the project activities as per
the testing methodology.
Roles and Responsibilities

8
PEN TESTING
The major role of the testing team includes the fact that there will be a proper analysis of
the penetration testing and hence wise schedule the planned activities. After this process, the next
role and responsibility of the team members includes the likes of maintaining a proper
coordination among the activities that are being performed. Proper alignment with the Site POC
have been one of the major aspect that is considered in the operating process. Another
responsibilities that are considered in the section is that the data that are generated in the process
needs to be properly related with the ITS Security Penetration testing process. Another
responsibility that is considered in the process is that after completion of the pen testing process,
the entire data set of the penetration test is to be deleted.
Pen Test Point of Contact (POC)
There are 6 major factors that affect the Point of Contact. They are namely being
responsible for performing the penetration testing and hence wise create a primary interface with
the help of the Site POC. This POC will be in use for all the penetration testing process. The
second factor that is considered in the process is that proper documentation of data is performed.
This processing of the data collection will be helping in maintaining the data sets and this will be
benefitting the entire project completion process. The third aspect that is considered in the
process is that proper roles are to be assigned to the pen tester as per the job roles that have been
assigned. Proper identifying of the estimated dates have been another aspect that is to be
considered. The forth aspect that is considered in the process is that it helps in performing proper
assessment of the Test plan, its results and hence wise the final deliverable have been provided.
The fifth important aspect that is considered in the process is that there is a proper coordination
of the IT security penetration testing with the Site POC is maintained. The sixth aspect that is
PEN TESTING
The major role of the testing team includes the fact that there will be a proper analysis of
the penetration testing and hence wise schedule the planned activities. After this process, the next
role and responsibility of the team members includes the likes of maintaining a proper
coordination among the activities that are being performed. Proper alignment with the Site POC
have been one of the major aspect that is considered in the operating process. Another
responsibilities that are considered in the section is that the data that are generated in the process
needs to be properly related with the ITS Security Penetration testing process. Another
responsibility that is considered in the process is that after completion of the pen testing process,
the entire data set of the penetration test is to be deleted.
Pen Test Point of Contact (POC)
There are 6 major factors that affect the Point of Contact. They are namely being
responsible for performing the penetration testing and hence wise create a primary interface with
the help of the Site POC. This POC will be in use for all the penetration testing process. The
second factor that is considered in the process is that proper documentation of data is performed.
This processing of the data collection will be helping in maintaining the data sets and this will be
benefitting the entire project completion process. The third aspect that is considered in the
process is that proper roles are to be assigned to the pen tester as per the job roles that have been
assigned. Proper identifying of the estimated dates have been another aspect that is to be
considered. The forth aspect that is considered in the process is that it helps in performing proper
assessment of the Test plan, its results and hence wise the final deliverable have been provided.
The fifth important aspect that is considered in the process is that there is a proper coordination
of the IT security penetration testing with the Site POC is maintained. The sixth aspect that is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PEN TESTING
considered in the process is that data that are collected in the process are stored in a proper and
safe manner.
Activities that are performed for performing the penetration process
The very first step that is performed in the process is introductory briefing. In this stage,
providing an overview of pen tester capabilities will be performed. In this stage, proper
explaining of the objectives to the tester is performed.
In the second step, technical and administrative face to face meeting is conducted. This
ensures that there will be a proper assessment of the finalizing of the penetration testing plan is
conducted. In the third part, the main aspect that is considered in the process reviewing of the IT
security and policies. With proper assessment of the IT security, robustness of the entire process
have been better. After this section proper assessment of outsider penetration testing is
performed. Insider penetration testing is also performed in this section. After this section, the
data that have been collected have been proposing the fact data finding is performed and hence
this ensures that analysis finding is performed in a proper manner. After this process, exit
briefing is performed.
PEN TESTING
considered in the process is that data that are collected in the process are stored in a proper and
safe manner.
Activities that are performed for performing the penetration process
The very first step that is performed in the process is introductory briefing. In this stage,
providing an overview of pen tester capabilities will be performed. In this stage, proper
explaining of the objectives to the tester is performed.
In the second step, technical and administrative face to face meeting is conducted. This
ensures that there will be a proper assessment of the finalizing of the penetration testing plan is
conducted. In the third part, the main aspect that is considered in the process reviewing of the IT
security and policies. With proper assessment of the IT security, robustness of the entire process
have been better. After this section proper assessment of outsider penetration testing is
performed. Insider penetration testing is also performed in this section. After this section, the
data that have been collected have been proposing the fact data finding is performed and hence
this ensures that analysis finding is performed in a proper manner. After this process, exit
briefing is performed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
PEN TESTING
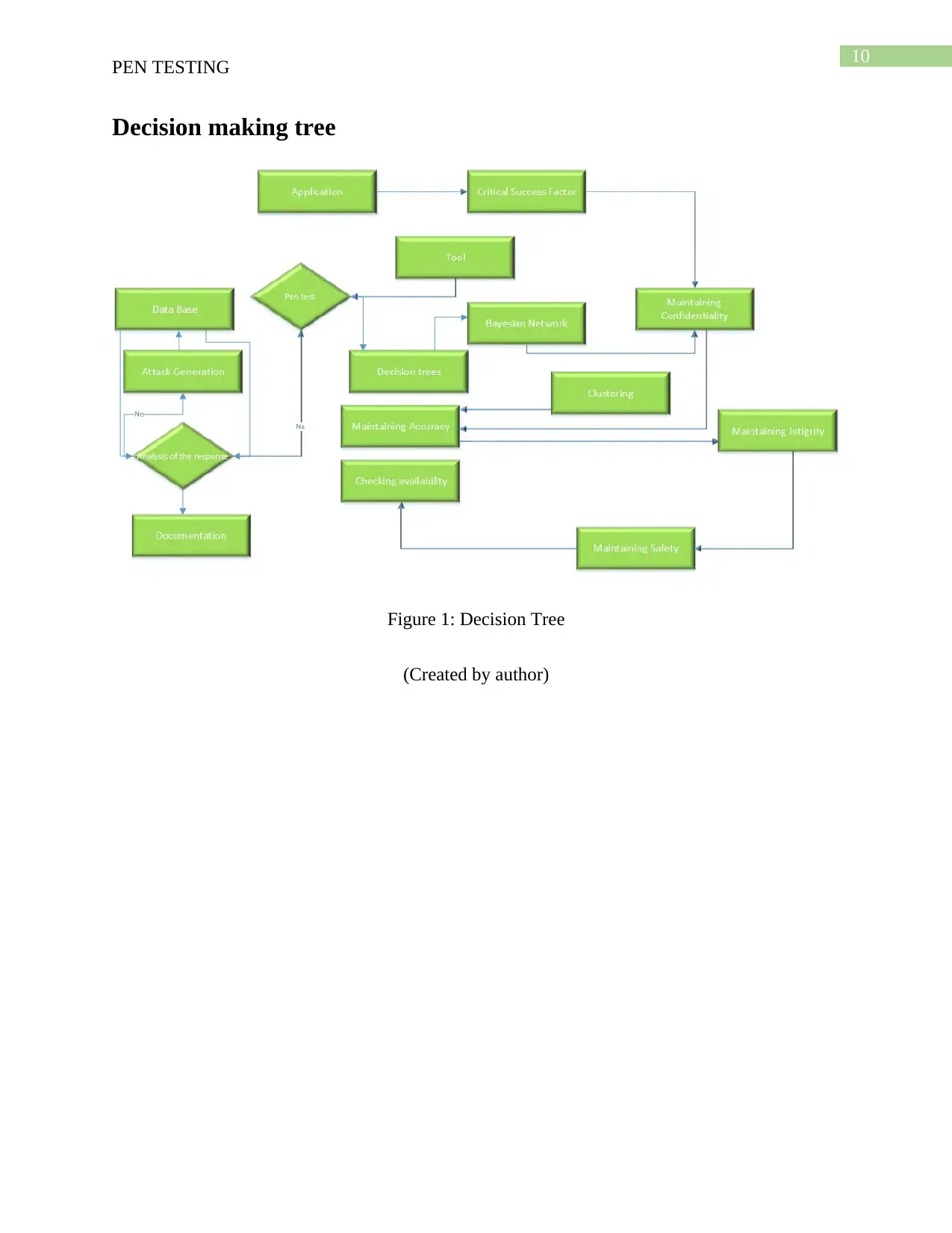
Decision making tree
Figure 1: Decision Tree
(Created by author)
PEN TESTING
Decision making tree
Figure 1: Decision Tree
(Created by author)

11
PEN TESTING
References
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT) (pp.
1-7). IEEE.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Chen, C.K., Zhang, Z.K., Lee, S.H. and Shieh, S., 2018. Penetration testing in the iot
age. Computer, 51(4), pp.82-85.
Choi, J., Jang, J., Han, C. and Cha, S.K., 2019, May. Grey-box concolic testing on binary code.
In 2019 IEEE/ACM 41st International Conference on Software Engineering (ICSE) (pp. 736-
747). IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An innovative approach to
investigate various software testing techniques and strategies. International Journal of Scientific
Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-1990.
Khera, Y., Kumar, D. and Garg, N., 2019, February. Analysis and Impact of Vulnerability
Assessment and Penetration Testing. In 2019 International Conference on Machine Learning,
Big Data, Cloud and Parallel Computing (COMITCon) (pp. 525-530). IEEE.
Krasniqi, G. and Bejtullahu, V., 2018. Vulnerability Assessment & Penetration Testing: Case
study on web application security.
PEN TESTING
References
Al Shebli, H.M.Z. and Beheshti, B.D., 2018, May. A study on penetration testing process and
tools. In 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT) (pp.
1-7). IEEE.
Baloch, R., 2017. Ethical hacking and penetration testing guide. CRC Press.
Chen, C.K., Zhang, Z.K., Lee, S.H. and Shieh, S., 2018. Penetration testing in the iot
age. Computer, 51(4), pp.82-85.
Choi, J., Jang, J., Han, C. and Cha, S.K., 2019, May. Grey-box concolic testing on binary code.
In 2019 IEEE/ACM 41st International Conference on Software Engineering (ICSE) (pp. 736-
747). IEEE.
Denis, M., Zena, C. and Hayajneh, T., 2016, April. Penetration testing: Concepts, attack
methods, and defense strategies. In 2016 IEEE Long Island Systems, Applications and
Technology Conference (LISAT) (pp. 1-6). IEEE.
Jan, S.R., Shah, S.T.U., Johar, Z.U., Shah, Y. and Khan, F., 2016. An innovative approach to
investigate various software testing techniques and strategies. International Journal of Scientific
Research in Science, Engineering and Technology (IJSRSET), Print ISSN, pp.2395-1990.
Khera, Y., Kumar, D. and Garg, N., 2019, February. Analysis and Impact of Vulnerability
Assessment and Penetration Testing. In 2019 International Conference on Machine Learning,
Big Data, Cloud and Parallel Computing (COMITCon) (pp. 525-530). IEEE.
Krasniqi, G. and Bejtullahu, V., 2018. Vulnerability Assessment & Penetration Testing: Case
study on web application security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





