PeopleSharz Cyber Security Report
VerifiedAdded on 2019/10/18
|10
|3873
|488
Report
AI Summary
This report details a cybersecurity risk assessment for the social networking website, PeopleSharz, following a data breach. The analysis begins with an executive summary outlining a risk-based cybersecurity framework incorporating industry best practices. The report then investigates the potential vulnerabilities, focusing on both client-side and server-side weaknesses. Methods like SQL injection, Remote Code Execution (RCE), phishing, and Cross-Site Scripting (XSS) are explored as potential attack vectors. A data collection methodology is proposed, emphasizing the importance of gathering information from various sources, including logs, malware analysis, and open-source intelligence. The report then delves into vulnerability analysis, utilizing threat metrics and threat models to assess the severity and likelihood of different threats. A threat matrix is presented to visually represent the vulnerabilities and their associated threats. The report concludes with recommendations for improving PeopleSharz's cybersecurity posture, including network segmentation, firewall implementation, secure remote access, role-based access controls, patch management, mobile device security policies, employee training, and the development of an incident response plan. The overall goal is to provide a comprehensive and actionable plan to enhance the security of PeopleSharz and prevent future breaches.

Executive Summary
In recognition to the importance of proactive cyber security management of a social networking
website PeopleSharz, we have tried to lay down a risk-based cyber security framework that is a
set of industry standards and best practices in the field of managing cyber security risks. The
voluntary guidance provided here offers the capability to customize and enhance the quality
adjustments to the cyber security programs that utilize cost effective security controls and the
various techniques regarding risk management. The employees of the organization should have a
sound understanding as to how the basic security is to be provided for the computer systems and
networks. This report also provides cost-effective approach to secure the computer system
platforms as per the business needs.
The key points of this report are that it provides an essential organization wide cyber security
plan, the utilization of different methodologies for data collection, the effective and efficient
ways with which the threats could be analyzed, the information regarding different forms cyber
security threats and their utilization by the hackers, the effective use of threat metrics and threat
models in the analysis of the security threats of the organization and finally, the key success
factors and valuable recommendations for the cyber security threats.
Background and Problem Analysis
A website has various important elements that make it function properly and, therefore, these
elements are needed to be working in sync. Today, millions of users frequently visit thousands of
social networking websites without any idea that their accounts are at the mercy of potential
hackers. So, once information is posted in a social networking platform, it is not a private
information any longer and the more information is being posted, the more vulnerable it gets.
The IT infrastructure houses various web servers, which in turn houses Domain Name System
with which various websites are registered to. Thus, a complex ecosystem is created that has
numerous interconnected nodes around the internet. Most of these features are provided by
service providers that make it relatively easy for the businesses to make an online presence.
These service providers also provide hosting space that makes operating of websites easy.
In the present scenario, firstly we have to analyze that whether the problem is at the server side
or client side. So, as per the facts of the case, at the very outset, the vulnerability seems to be at
the client side. The hackers of a social networking website have various methods by which they
break into users’ account and steal crucial information from there. The SQL injection is the most
common server-side vulnerability that allows the hackers to inject the code into the database of a
website (Al Hasib, 2009). There are other vulnerabilities such as Remote Code Execution (RCE)
as well at the dispensation of attackers, which enables the hackers to interact with the system
directly. Most probably, the hackers of PeopleSharz might have used Trojan horses, malwares,
logic bombs, computer worms, snipping tools, phishing tools and a wider spectrum of other
sources. This attack must have been a coordinated one as they might have been successful in
locating flaws in network topologies as well as bugs and defects in software configuration. These
days, with the help of Netspionage, it is relatively for the attackers to access highly sensitive
information from the accounts of the social media users.
In recognition to the importance of proactive cyber security management of a social networking
website PeopleSharz, we have tried to lay down a risk-based cyber security framework that is a
set of industry standards and best practices in the field of managing cyber security risks. The
voluntary guidance provided here offers the capability to customize and enhance the quality
adjustments to the cyber security programs that utilize cost effective security controls and the
various techniques regarding risk management. The employees of the organization should have a
sound understanding as to how the basic security is to be provided for the computer systems and
networks. This report also provides cost-effective approach to secure the computer system
platforms as per the business needs.
The key points of this report are that it provides an essential organization wide cyber security
plan, the utilization of different methodologies for data collection, the effective and efficient
ways with which the threats could be analyzed, the information regarding different forms cyber
security threats and their utilization by the hackers, the effective use of threat metrics and threat
models in the analysis of the security threats of the organization and finally, the key success
factors and valuable recommendations for the cyber security threats.
Background and Problem Analysis
A website has various important elements that make it function properly and, therefore, these
elements are needed to be working in sync. Today, millions of users frequently visit thousands of
social networking websites without any idea that their accounts are at the mercy of potential
hackers. So, once information is posted in a social networking platform, it is not a private
information any longer and the more information is being posted, the more vulnerable it gets.
The IT infrastructure houses various web servers, which in turn houses Domain Name System
with which various websites are registered to. Thus, a complex ecosystem is created that has
numerous interconnected nodes around the internet. Most of these features are provided by
service providers that make it relatively easy for the businesses to make an online presence.
These service providers also provide hosting space that makes operating of websites easy.
In the present scenario, firstly we have to analyze that whether the problem is at the server side
or client side. So, as per the facts of the case, at the very outset, the vulnerability seems to be at
the client side. The hackers of a social networking website have various methods by which they
break into users’ account and steal crucial information from there. The SQL injection is the most
common server-side vulnerability that allows the hackers to inject the code into the database of a
website (Al Hasib, 2009). There are other vulnerabilities such as Remote Code Execution (RCE)
as well at the dispensation of attackers, which enables the hackers to interact with the system
directly. Most probably, the hackers of PeopleSharz might have used Trojan horses, malwares,
logic bombs, computer worms, snipping tools, phishing tools and a wider spectrum of other
sources. This attack must have been a coordinated one as they might have been successful in
locating flaws in network topologies as well as bugs and defects in software configuration. These
days, with the help of Netspionage, it is relatively for the attackers to access highly sensitive
information from the accounts of the social media users.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

There is an equal possibility that the hackers have utilized Server Side Request Forgery (SSRF)
that might have enabled them to read all the files and raw tables of the database of PeopleSharz.
The technique of phishing must have been used in this case, where the hackers had targeted
PeopleSharz with a keen focus on the vulnerabilities as well as used social engineering tricks.
Also, there are certain techniques meant for the authorization bypass. The other possible attacks
are Cross Site Scripting (XSS) attacks and Broken Authentication and Session Management
attacks. The hackers must have sent file packet to the web browser and bypass the validation
process. It causes the user’s session ID to be sent to the attacker’s website, allowing the hacker to
hijack the user’s current session (Tankard, 2011). The website was attacked in such a manner
that the relevant information was scrapped directly from the database. The following report
contains a thorough analysis of threat faced by PeopleSharz, dependencies on critical success
measures followed by the recommendations.
Threat Analysis
Being an IT security consultant and analyst, my job is to delve deeper and deeper to probe
PeopleSharz security and also to determine potential entry points that could have exploited by
the hackers. It should be noted that the social media websites are needed to take extra caution for
the cyber security threats, so the possibilities also are that PeopleSharz had spared no expense
regarding cyber security system. I can expect that the administrators had been conscientious
about ensuring that all the security patches and antivirus updates had applied to their processes. It
can be said that someone would be impressed with the level of security that this website had put
in place (Gao, Hu, Huang, Wang, & Chen, 2011). However, after the extensive assessment, it
will certainly be revealed that PeopleSharz was still extremely vulnerable to a security breach.
In order to analyze, the cyber security breach, I will perform data collection and vulnerability
analysis. While the Scope will provide information as to what needs to be included and what
needs to be excluded in the process of analysis. So, in case of cyber security, the items that will
be considered will be those aspects of PeopleSharz that must be protected and they will be
identified first.
(a) Data Collection
In almost all the social media companies there are certain kind of policies and procedures that are
required to be identified for the compliance purposes. In actuality around one-fourth security
mechanisms that the organizations have, miserably fail to fulfill minimum security standards. So,
the first step will be to collect the detailed information regarding the security breach. Such as
URLs to virus links, phishing email header and content, malicious command and controls and
domain names and IP addresses etc. As an analyst, it is very important for me to get unrestricted
access to data for transforming it into intelligence. My sources of information will be knowledge
of intrusion incidents, detection system logs, firewall logs, reverse engineering of malware, open
source links, honeypots so on and so forth. Once all of this data is collected, the examination and
examination will be done as to whether they match the compliance level in the organization
(Ralston, Graham, & Hieb, 2007).
that might have enabled them to read all the files and raw tables of the database of PeopleSharz.
The technique of phishing must have been used in this case, where the hackers had targeted
PeopleSharz with a keen focus on the vulnerabilities as well as used social engineering tricks.
Also, there are certain techniques meant for the authorization bypass. The other possible attacks
are Cross Site Scripting (XSS) attacks and Broken Authentication and Session Management
attacks. The hackers must have sent file packet to the web browser and bypass the validation
process. It causes the user’s session ID to be sent to the attacker’s website, allowing the hacker to
hijack the user’s current session (Tankard, 2011). The website was attacked in such a manner
that the relevant information was scrapped directly from the database. The following report
contains a thorough analysis of threat faced by PeopleSharz, dependencies on critical success
measures followed by the recommendations.
Threat Analysis
Being an IT security consultant and analyst, my job is to delve deeper and deeper to probe
PeopleSharz security and also to determine potential entry points that could have exploited by
the hackers. It should be noted that the social media websites are needed to take extra caution for
the cyber security threats, so the possibilities also are that PeopleSharz had spared no expense
regarding cyber security system. I can expect that the administrators had been conscientious
about ensuring that all the security patches and antivirus updates had applied to their processes. It
can be said that someone would be impressed with the level of security that this website had put
in place (Gao, Hu, Huang, Wang, & Chen, 2011). However, after the extensive assessment, it
will certainly be revealed that PeopleSharz was still extremely vulnerable to a security breach.
In order to analyze, the cyber security breach, I will perform data collection and vulnerability
analysis. While the Scope will provide information as to what needs to be included and what
needs to be excluded in the process of analysis. So, in case of cyber security, the items that will
be considered will be those aspects of PeopleSharz that must be protected and they will be
identified first.
(a) Data Collection
In almost all the social media companies there are certain kind of policies and procedures that are
required to be identified for the compliance purposes. In actuality around one-fourth security
mechanisms that the organizations have, miserably fail to fulfill minimum security standards. So,
the first step will be to collect the detailed information regarding the security breach. Such as
URLs to virus links, phishing email header and content, malicious command and controls and
domain names and IP addresses etc. As an analyst, it is very important for me to get unrestricted
access to data for transforming it into intelligence. My sources of information will be knowledge
of intrusion incidents, detection system logs, firewall logs, reverse engineering of malware, open
source links, honeypots so on and so forth. Once all of this data is collected, the examination and
examination will be done as to whether they match the compliance level in the organization
(Ralston, Graham, & Hieb, 2007).

The different types of vulnerabilities that are needed to be tested in this case are as follows:
Injection and Cross-site Vulnerabilities: these are the two most severe flaws that occur in web
applications and all of these work by sending malicious data to an application in the form of
command and query. In SQL injection, the hackers utilize data from the websites that generate
SQL queries by using user-supplied data without ensuring that it is valid. Thereafter, the hackers
submit malicious SQL queries and transfer commands directly to the database. While, in Cross-
site scripting, the attackers target the website’s users by injecting code, particularly JavaScript
into the output of a web application. When that page is being viewed, the browser executes the
code that allows the hacker to redirect users to a malicious site.
Broken authentication and session management: of many important purposes of web
applications, user authentications is one of the most prominent in order to keep track of users’
request as http. Now, if a hacker discovers that a user did not log out, then he uses XSS to hack
his account (Greitzer, & Frincke, 2010). So, the company is required to perform code review and
penetration tests as well.
Security misconfiguration: the platform that supports web applications constitutes complicated
variety of devices as well as software such as servers, firewalls, databases, operating systems and
application software. All these different components are required to be securely configured as
well as maintained. So, a poor management of web applications may be caused by never
undergoing the necessary training. The poor application designs can also be the source of cyber
security breach in organizations.
(b) Vulnerability Analysis
This stage is very vital as I will have to test the gathered information so that the level of exposure
would be determined. It will give us a fair idea as to whether the current defenses were solid
enough to remove threats in terms of their availability, confidentiality and integrity. In this we
will evaluate whether the existing procedures, policies and security measures were adequate. It
should be highlighted that threat analysis, especially in the Social networking sites such as
PeopleSharz, is a continual process that should be reviewed once in a while to ensure that all
safeguard mechanisms are working properly. So, the evaluation of risks is an integral part of the
organization’s overall lifecycle (Kuhl, Kistner, Costantini, & Sudit, 2007).
So, on the basis of vulnerability and risk assessment, we have to determine as to what security
measures will be needed to be taken and also remove the ineffective ones.
Threat Metrics: the effective threat measurement facilitates analysis with the help of improved
understanding of how software anomalies occur. The imminence of certain forms of
vulnerabilities and connecting missing links between potential threats and possible consequences
will be crucial in threat analysis. In light of this, my abilities of analysis will be greatly enhanced
by using unambiguous and clear metric. It will improve our ability to understand the threat as
well as control and defend against it to a certain extent (Knapp, 2009). For example, a
quantitative assessment about the number of cyber-attacks per month and the pattern and count
of these attacks would reveal the hackers’ capability and intent.
Injection and Cross-site Vulnerabilities: these are the two most severe flaws that occur in web
applications and all of these work by sending malicious data to an application in the form of
command and query. In SQL injection, the hackers utilize data from the websites that generate
SQL queries by using user-supplied data without ensuring that it is valid. Thereafter, the hackers
submit malicious SQL queries and transfer commands directly to the database. While, in Cross-
site scripting, the attackers target the website’s users by injecting code, particularly JavaScript
into the output of a web application. When that page is being viewed, the browser executes the
code that allows the hacker to redirect users to a malicious site.
Broken authentication and session management: of many important purposes of web
applications, user authentications is one of the most prominent in order to keep track of users’
request as http. Now, if a hacker discovers that a user did not log out, then he uses XSS to hack
his account (Greitzer, & Frincke, 2010). So, the company is required to perform code review and
penetration tests as well.
Security misconfiguration: the platform that supports web applications constitutes complicated
variety of devices as well as software such as servers, firewalls, databases, operating systems and
application software. All these different components are required to be securely configured as
well as maintained. So, a poor management of web applications may be caused by never
undergoing the necessary training. The poor application designs can also be the source of cyber
security breach in organizations.
(b) Vulnerability Analysis
This stage is very vital as I will have to test the gathered information so that the level of exposure
would be determined. It will give us a fair idea as to whether the current defenses were solid
enough to remove threats in terms of their availability, confidentiality and integrity. In this we
will evaluate whether the existing procedures, policies and security measures were adequate. It
should be highlighted that threat analysis, especially in the Social networking sites such as
PeopleSharz, is a continual process that should be reviewed once in a while to ensure that all
safeguard mechanisms are working properly. So, the evaluation of risks is an integral part of the
organization’s overall lifecycle (Kuhl, Kistner, Costantini, & Sudit, 2007).
So, on the basis of vulnerability and risk assessment, we have to determine as to what security
measures will be needed to be taken and also remove the ineffective ones.
Threat Metrics: the effective threat measurement facilitates analysis with the help of improved
understanding of how software anomalies occur. The imminence of certain forms of
vulnerabilities and connecting missing links between potential threats and possible consequences
will be crucial in threat analysis. In light of this, my abilities of analysis will be greatly enhanced
by using unambiguous and clear metric. It will improve our ability to understand the threat as
well as control and defend against it to a certain extent (Knapp, 2009). For example, a
quantitative assessment about the number of cyber-attacks per month and the pattern and count
of these attacks would reveal the hackers’ capability and intent.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
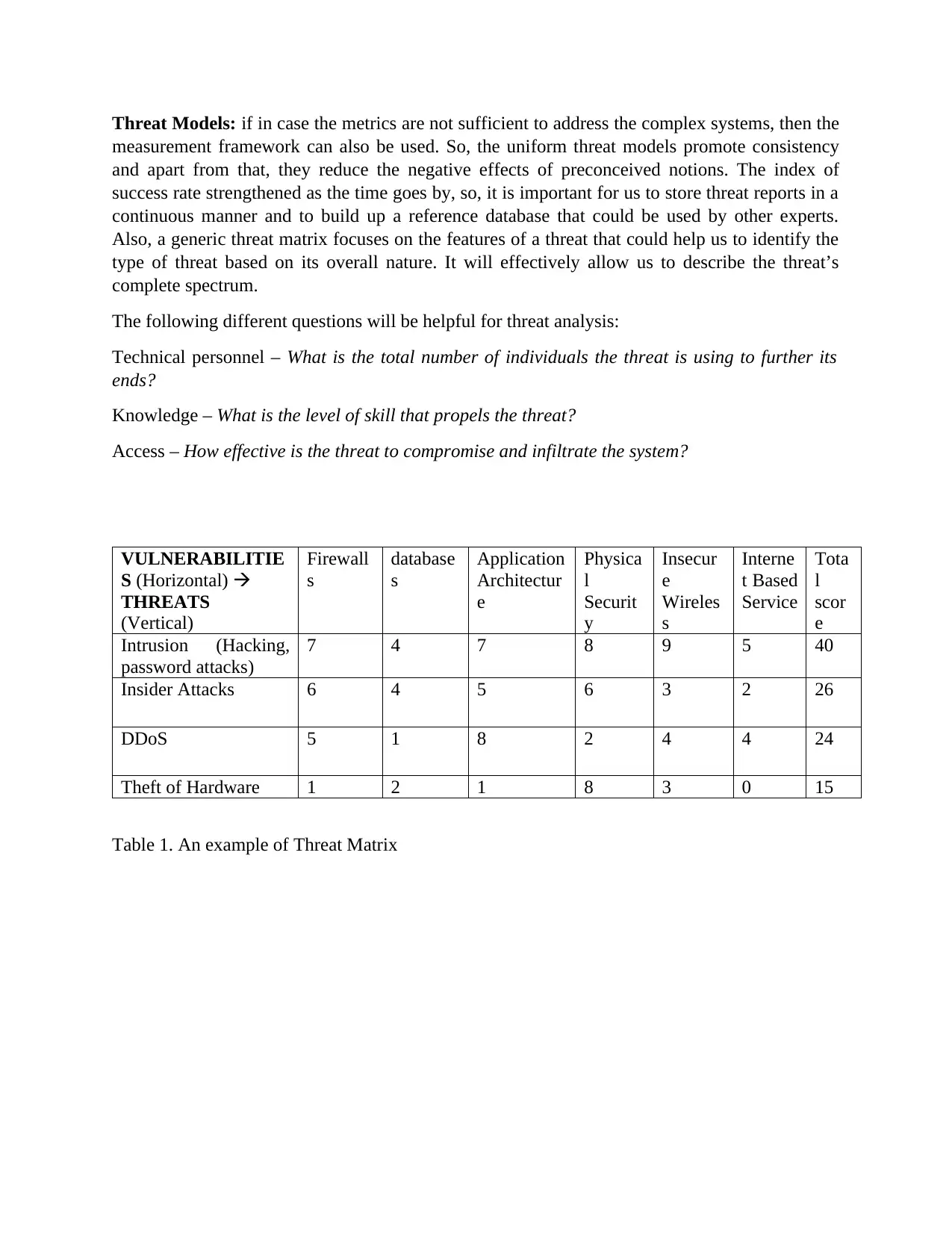
Threat Models: if in case the metrics are not sufficient to address the complex systems, then the
measurement framework can also be used. So, the uniform threat models promote consistency
and apart from that, they reduce the negative effects of preconceived notions. The index of
success rate strengthened as the time goes by, so, it is important for us to store threat reports in a
continuous manner and to build up a reference database that could be used by other experts.
Also, a generic threat matrix focuses on the features of a threat that could help us to identify the
type of threat based on its overall nature. It will effectively allow us to describe the threat’s
complete spectrum.
The following different questions will be helpful for threat analysis:
Technical personnel – What is the total number of individuals the threat is using to further its
ends?
Knowledge – What is the level of skill that propels the threat?
Access – How effective is the threat to compromise and infiltrate the system?
VULNERABILITIE
S (Horizontal)
THREATS
(Vertical)
Firewall
s
database
s
Application
Architectur
e
Physica
l
Securit
y
Insecur
e
Wireles
s
Interne
t Based
Service
Tota
l
scor
e
Intrusion (Hacking,
password attacks)
7 4 7 8 9 5 40
Insider Attacks 6 4 5 6 3 2 26
DDoS 5 1 8 2 4 4 24
Theft of Hardware 1 2 1 8 3 0 15
Table 1. An example of Threat Matrix
measurement framework can also be used. So, the uniform threat models promote consistency
and apart from that, they reduce the negative effects of preconceived notions. The index of
success rate strengthened as the time goes by, so, it is important for us to store threat reports in a
continuous manner and to build up a reference database that could be used by other experts.
Also, a generic threat matrix focuses on the features of a threat that could help us to identify the
type of threat based on its overall nature. It will effectively allow us to describe the threat’s
complete spectrum.
The following different questions will be helpful for threat analysis:
Technical personnel – What is the total number of individuals the threat is using to further its
ends?
Knowledge – What is the level of skill that propels the threat?
Access – How effective is the threat to compromise and infiltrate the system?
VULNERABILITIE
S (Horizontal)
THREATS
(Vertical)
Firewall
s
database
s
Application
Architectur
e
Physica
l
Securit
y
Insecur
e
Wireles
s
Interne
t Based
Service
Tota
l
scor
e
Intrusion (Hacking,
password attacks)
7 4 7 8 9 5 40
Insider Attacks 6 4 5 6 3 2 26
DDoS 5 1 8 2 4 4 24
Theft of Hardware 1 2 1 8 3 0 15
Table 1. An example of Threat Matrix
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 1: Information Security Life Cycle
Dependencies and Critical Success Factors
The various dependencies about the job of the assessment and proposals regarding the security
breach in PeopleSharz are the proper communications with the stakeholders and employees. The
key employees of PeopleSharz as well as HotHost 1 consists of the cyber security team and the
expert code developers of different software modules of the organization. It will be very
important to interview these important people as to what were the possible glitches that could
have culminated into such a huge attack. It is certainly not known yet as where was the problem
PeopleSharz or HotHost1. But the fact that the webservers of both the companies are to be
investigated into. So these employees will be an important source of information for analyzing
the threats and laying down recommendations in case future threats are concerned (Xie, et al,
2010).
Key Success Factors
It is not suffice for the organizations to undermine the necessity of developing and executing
effective as well as efficient cyber security measures. Which is why, it is very pertinent to
incorporate a Cyber security Management Program (CMP) that will affect virtually each and
every employee and group in the organization (PeopleSharz). So, it is also very important that
the overall cyber security program will be able to meet everyone’s needs. Therefore, if the
Dependencies and Critical Success Factors
The various dependencies about the job of the assessment and proposals regarding the security
breach in PeopleSharz are the proper communications with the stakeholders and employees. The
key employees of PeopleSharz as well as HotHost 1 consists of the cyber security team and the
expert code developers of different software modules of the organization. It will be very
important to interview these important people as to what were the possible glitches that could
have culminated into such a huge attack. It is certainly not known yet as where was the problem
PeopleSharz or HotHost1. But the fact that the webservers of both the companies are to be
investigated into. So these employees will be an important source of information for analyzing
the threats and laying down recommendations in case future threats are concerned (Xie, et al,
2010).
Key Success Factors
It is not suffice for the organizations to undermine the necessity of developing and executing
effective as well as efficient cyber security measures. Which is why, it is very pertinent to
incorporate a Cyber security Management Program (CMP) that will affect virtually each and
every employee and group in the organization (PeopleSharz). So, it is also very important that
the overall cyber security program will be able to meet everyone’s needs. Therefore, if the

Peoplesharz apply the following measures, it is highly likely that it will achieve a highest
probability of successful development and implementation of CMP:
1) Identifying and obtaining support and commitment from the concerned members of the
Senior Leadership Team for effective implementation of cyber security program.
2) Developing an overall organization wide charter regarding cyber security program, which
essentially should include effective cyber security strategies for PeopleSharz. This charter
should be submitted to the sponsor of CMP for the purpose of socialization with the SLT and
endorsement by the CEO.
3) Developing a cyber-security work plan whose primary task would be to develop the policies
regarding cyber security. In bigger organizations, however, there are multiple project
managers as per the need.
Establishing and mandating a review process of the documents as well as version management
system in order to provide a support for the ongoing management of cyber security
documentation (Torres, Sarriegi, Santos, & Serrano, 2006).
4) The strategic components regarding the Cyber security Management Framework should be
completed first. However, it is also the case that more and more number of components will
be required to develop in parallel, particularly when there are very few dependencies between
the components.
5) Identifying and treating the key components as high-priority developmental efforts that have
organization wide impacts. For example organization related components as well as core
components that form a crucial foundation for other components.
6) Dedicating time and efforts I order to develop consistent, congruent and easily understood
documentation responsible for all the actions required by the cyber security program.
Recommendations
After the thorough analysis and evaluation of different threats and their impacts, it is very
important for PeopleSharz to implement the following recommendations:
1) Identify the weakest areas in the cyber security infrastructure
The process of plugging holes in the overall security infrastructure is a time-taking but necessary
evil. So, to start with, it is really important to identify as to where the weakest point of the entire
chain is. What are the areas where the network data could be compromised? It is precisely what
hackers do. With the help of patch management tools, we can succeed by strengthening the
chain link. The vulnerability scanners and application control could limit the possibility of threat.
2) Implementation of network segmentation and application of firewalls
The network segmentation is process of IT assets, data and people into specific groups and
restricting the access to these groups so that the compromise of one area should not be translated
into the compromise of the whole system. This process can be done by isolating them completely
from one another. Also, by using firewall will help in filtering incoming and outgoing
information. It reduces the number of pathways into the network and uses security protocols on
probability of successful development and implementation of CMP:
1) Identifying and obtaining support and commitment from the concerned members of the
Senior Leadership Team for effective implementation of cyber security program.
2) Developing an overall organization wide charter regarding cyber security program, which
essentially should include effective cyber security strategies for PeopleSharz. This charter
should be submitted to the sponsor of CMP for the purpose of socialization with the SLT and
endorsement by the CEO.
3) Developing a cyber-security work plan whose primary task would be to develop the policies
regarding cyber security. In bigger organizations, however, there are multiple project
managers as per the need.
Establishing and mandating a review process of the documents as well as version management
system in order to provide a support for the ongoing management of cyber security
documentation (Torres, Sarriegi, Santos, & Serrano, 2006).
4) The strategic components regarding the Cyber security Management Framework should be
completed first. However, it is also the case that more and more number of components will
be required to develop in parallel, particularly when there are very few dependencies between
the components.
5) Identifying and treating the key components as high-priority developmental efforts that have
organization wide impacts. For example organization related components as well as core
components that form a crucial foundation for other components.
6) Dedicating time and efforts I order to develop consistent, congruent and easily understood
documentation responsible for all the actions required by the cyber security program.
Recommendations
After the thorough analysis and evaluation of different threats and their impacts, it is very
important for PeopleSharz to implement the following recommendations:
1) Identify the weakest areas in the cyber security infrastructure
The process of plugging holes in the overall security infrastructure is a time-taking but necessary
evil. So, to start with, it is really important to identify as to where the weakest point of the entire
chain is. What are the areas where the network data could be compromised? It is precisely what
hackers do. With the help of patch management tools, we can succeed by strengthening the
chain link. The vulnerability scanners and application control could limit the possibility of threat.
2) Implementation of network segmentation and application of firewalls
The network segmentation is process of IT assets, data and people into specific groups and
restricting the access to these groups so that the compromise of one area should not be translated
into the compromise of the whole system. This process can be done by isolating them completely
from one another. Also, by using firewall will help in filtering incoming and outgoing
information. It reduces the number of pathways into the network and uses security protocols on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the existing pathways. So, creating boundaries and segments enhances the security ("Best
Practices to Reduce Exploitable Weaknesses and Attacks", 2015).
3) Use secure remote access methods
The remote connection to a network has made it convenient for the users, however, the security
is at a great risk if the remote connection is made without a virtual private network. The VPN is
basically an encrypted data channel for the purpose of securely sending and receiving data
through internet. So, with the help of VPN, we can be able to remotely access some of the
internal assets such as files, printers, databases and websites as if they are directly connected to
the internet. Reducing the number of IP addresses can also be helpful.
4) Establish Role-Based Access Controls and Implement System Logging
The primary function of role-based access control is limiting the ability of individual hackers so
that the important parts of the system should not be accessed by them. So, defining the
permissions based on the level of access each job function needs an effective strategy. Also, the
implementation of a logging capability helps in monitoring the system activity. With the help of
this, the organizations conduct root cause analysis.
5) Maintain Awareness of Vulnerabilities and Implement Necessary Patches and Updates
It is always a diligent process to develop patches for identified vulnerabilities. However, even
after all this, the systems remain vulnerable because the organizations do not implement these
fixes. In order to protect the organizations from the opportunistic attack of massive levels, a
system of monitoring and application of patches and updates are needed to be implemented.
Also, it would be helpful to auto-update the system software in order to avoid missing critical
updates (Lehrman, 2010).
6) Develop and Enforce Cyber Security Policies on Mobile Devices
The growing use of laptops, tablets and smartphones in the work stations can pose considerable
security challenges. The obvious mobile nature of these devices amounts to their potential
exposure to the external malicious environment. Thus, it is very important to make policies
regarding reasonable limit on the mobile devices being used at work places. These policies
should be strongly enforced on all the employees and other stakeholders of the organization.
Failing to do so, the organizations will be attracting numerous hackers to get access to the
restricted networks. These devices are at constant risk of getting infected.
7) Implement an Employee Cyber security Training Program
The fact that if the employees wouldn’t get themselves involved in cyber security, not only could
the vulnerabilities and threats go unchallenged but the employees themselves could become for
the execution of attacks. Therefore, they should get periodic cyber-security training (Ngoma,
2012).
8) Implement Measures for Detecting Compromises and Develop a Cyber security Incident
Response Plan
Practices to Reduce Exploitable Weaknesses and Attacks", 2015).
3) Use secure remote access methods
The remote connection to a network has made it convenient for the users, however, the security
is at a great risk if the remote connection is made without a virtual private network. The VPN is
basically an encrypted data channel for the purpose of securely sending and receiving data
through internet. So, with the help of VPN, we can be able to remotely access some of the
internal assets such as files, printers, databases and websites as if they are directly connected to
the internet. Reducing the number of IP addresses can also be helpful.
4) Establish Role-Based Access Controls and Implement System Logging
The primary function of role-based access control is limiting the ability of individual hackers so
that the important parts of the system should not be accessed by them. So, defining the
permissions based on the level of access each job function needs an effective strategy. Also, the
implementation of a logging capability helps in monitoring the system activity. With the help of
this, the organizations conduct root cause analysis.
5) Maintain Awareness of Vulnerabilities and Implement Necessary Patches and Updates
It is always a diligent process to develop patches for identified vulnerabilities. However, even
after all this, the systems remain vulnerable because the organizations do not implement these
fixes. In order to protect the organizations from the opportunistic attack of massive levels, a
system of monitoring and application of patches and updates are needed to be implemented.
Also, it would be helpful to auto-update the system software in order to avoid missing critical
updates (Lehrman, 2010).
6) Develop and Enforce Cyber Security Policies on Mobile Devices
The growing use of laptops, tablets and smartphones in the work stations can pose considerable
security challenges. The obvious mobile nature of these devices amounts to their potential
exposure to the external malicious environment. Thus, it is very important to make policies
regarding reasonable limit on the mobile devices being used at work places. These policies
should be strongly enforced on all the employees and other stakeholders of the organization.
Failing to do so, the organizations will be attracting numerous hackers to get access to the
restricted networks. These devices are at constant risk of getting infected.
7) Implement an Employee Cyber security Training Program
The fact that if the employees wouldn’t get themselves involved in cyber security, not only could
the vulnerabilities and threats go unchallenged but the employees themselves could become for
the execution of attacks. Therefore, they should get periodic cyber-security training (Ngoma,
2012).
8) Implement Measures for Detecting Compromises and Develop a Cyber security Incident
Response Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The intrusion detection systems can greatly help to detect compromises in the early stages and
servers should be monitored signs of infections. Whereas, the incident response plan is highly
critical component of emergency purposes. It can limit the damage, increase the confidence of
partners and customers and reduce time and costs.
servers should be monitored signs of infections. Whereas, the incident response plan is highly
critical component of emergency purposes. It can limit the damage, increase the confidence of
partners and customers and reduce time and costs.

References
Al Hasib, A. (2009). Threats of online social networks. IJCSNS International Journal of
Computer Science and Network Security, 9(11), 288-93.
Best Practices to Reduce Exploitable Weaknesses and Attacks. (2015). ics-cert.us-cert.gov.
Retrieved 21 October 2016, from
https://ics-cert.us-cert.gov/sites/default/files/documents/10_Basic_Cybersecurity_Measures-
WaterISAC_June2015_S508C.pdf
Gao, H., Hu, J., Huang, T., Wang, J., & Chen, Y. (2011). Security issues in online social
networks. IEEE Internet Computing, 15(4), 56-63.
Greitzer, F. L., & Frincke, D. A. (2010). Combining traditional cyber security audit data with
psychosocial data: towards predictive modeling for insider threat mitigation. In Insider
Threats in Cyber Security (pp. 85-113). Springer US.
Knapp, K. J. (Ed.). (2009). Cyber Security and Global Information Assurance: Threat Analysis
and Response Solutions: Threat Analysis and Response Solutions. IGI Global.
Kuhl, M. E., Kistner, J., Costantini, K., & Sudit, M. (2007, December). Cyber attack modeling
and simulation for network security analysis. In Proceedings of the 39th Conference on
Winter Simulation: 40 years! The best is yet to come (pp. 1180-1188). IEEE Press.
Lehrman, Y. (2010). The Weakest Link: The Risks Associated with Social Networking
Websites.Scholarcommons.usf.edu. Retrieved 21 October 2016, from
http://scholarcommons.usf.edu/cgi/viewcontent.cgi?article=1014&context=jss
Ngoma, S. (2012). Vulnerability of IT Infrastructures: Internal and External
Threats. congovision.com. Retrieved 21 October 2016, from
http://www.congovision.com/IT-Security-Pub.pdf
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for SCADA
and DCS networks. ISA transactions, 46(4), 583-594.
Tankard, C. (2011). Advanced persistent threats and how to monitor and deter them. Network
security, 2011(8), 16-19.
Torres, J. M., Sarriegi, J. M., Santos, J., & Serrano, N. (2006, August). Managing information
systems security: critical success factors and indicators to measure effectiveness.
In International Conference on Information Security (pp. 530-545). Springer Berlin
Heidelberg.
Al Hasib, A. (2009). Threats of online social networks. IJCSNS International Journal of
Computer Science and Network Security, 9(11), 288-93.
Best Practices to Reduce Exploitable Weaknesses and Attacks. (2015). ics-cert.us-cert.gov.
Retrieved 21 October 2016, from
https://ics-cert.us-cert.gov/sites/default/files/documents/10_Basic_Cybersecurity_Measures-
WaterISAC_June2015_S508C.pdf
Gao, H., Hu, J., Huang, T., Wang, J., & Chen, Y. (2011). Security issues in online social
networks. IEEE Internet Computing, 15(4), 56-63.
Greitzer, F. L., & Frincke, D. A. (2010). Combining traditional cyber security audit data with
psychosocial data: towards predictive modeling for insider threat mitigation. In Insider
Threats in Cyber Security (pp. 85-113). Springer US.
Knapp, K. J. (Ed.). (2009). Cyber Security and Global Information Assurance: Threat Analysis
and Response Solutions: Threat Analysis and Response Solutions. IGI Global.
Kuhl, M. E., Kistner, J., Costantini, K., & Sudit, M. (2007, December). Cyber attack modeling
and simulation for network security analysis. In Proceedings of the 39th Conference on
Winter Simulation: 40 years! The best is yet to come (pp. 1180-1188). IEEE Press.
Lehrman, Y. (2010). The Weakest Link: The Risks Associated with Social Networking
Websites.Scholarcommons.usf.edu. Retrieved 21 October 2016, from
http://scholarcommons.usf.edu/cgi/viewcontent.cgi?article=1014&context=jss
Ngoma, S. (2012). Vulnerability of IT Infrastructures: Internal and External
Threats. congovision.com. Retrieved 21 October 2016, from
http://www.congovision.com/IT-Security-Pub.pdf
Ralston, P. A., Graham, J. H., & Hieb, J. L. (2007). Cyber security risk assessment for SCADA
and DCS networks. ISA transactions, 46(4), 583-594.
Tankard, C. (2011). Advanced persistent threats and how to monitor and deter them. Network
security, 2011(8), 16-19.
Torres, J. M., Sarriegi, J. M., Santos, J., & Serrano, N. (2006, August). Managing information
systems security: critical success factors and indicators to measure effectiveness.
In International Conference on Information Security (pp. 530-545). Springer Berlin
Heidelberg.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Xie, P., Li, J. H., Ou, X., Liu, P., & Levy, R. (2010, June). Using Bayesian networks for cyber
security analysis. In 2010 IEEE/IFIP International Conference on Dependable Systems
& Networks (DSN) (pp. 211-220). IEEE.
security analysis. In 2010 IEEE/IFIP International Conference on Dependable Systems
& Networks (DSN) (pp. 211-220). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





