Computer Networks Report: Perfect Home Lettings Agency - STC Training
VerifiedAdded on 2023/06/15
|18
|4952
|346
Report
AI Summary
This report provides a comprehensive analysis of computer networks for Perfect Home Lettings agency. It begins by examining the existing network infrastructure, comparing 10base T with newer Ethernet versions and Wi-Fi, recommending an upgrade to Fast Ethernet with additional Wi-Fi hotspots. The report details the differences between networking devices like hubs, switches, wireless access points, and routers, explaining their operation within the OSI model's seven layers. It identifies and explains the purpose of protocols such as FTP, IMAP, SMTP, and TLS, crucial for the company's operations. Addressing is thoroughly discussed, differentiating between MAC and IP addresses, IPv4 and IPv6, and the role of DHCP, ARP, default gateways, subnet masks, and IP routing tables. Security vulnerabilities are addressed, with recommendations for network safety and secure connections, including a wireless guest network. A logical network diagram is presented, outlining hardware components and secure connection strategies. Finally, the report explores Voice over IP (VoIP) and its potential incorporation into the Perfect Home Lettings system. Desklib offers a wealth of similar solved assignments and past papers for students.

Presented by Saverio Davide Migale Computer Networks
COMPUTER NETWORKS
Perfect Home Lettings agency
Presented by
SAVERIO DAVIDE MIGALE
ID: 172977
(STC Training, Malta)
February 2018
COMPUTER NETWORKS
Perfect Home Lettings agency
Presented by
SAVERIO DAVIDE MIGALE
ID: 172977
(STC Training, Malta)
February 2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Presented by Saverio Davide Migale Computer Networks
TABLE OF CONTENTS
Table of Contents............................................................................................................................................... 2
Introduction....................................................................................................................................................... 3
Task 1: Network Infrastructure and Protocols.................................................................................................... 4
a) 10base T over Cat 5 UTP, newer versions of Ethernet and Wi-Fi................................................................4
b) Networking devices/components.............................................................................................................. 5
c) OSI Model.................................................................................................................................................. 7
d) Protocols used by Perfect Home Lettings................................................................................................... 9
Task 2: Addressing........................................................................................................................................... 10
a) The need for addresses in network components.....................................................................................10
b) Differences between a private and a public IPv4 address........................................................................10
c) DHCP........................................................................................................................................................ 12
d) ARP.......................................................................................................................................................... 12
e) Default Gateway and Subnet Mask.......................................................................................................... 13
f) IP routing table......................................................................................................................................... 13
Task 3: Security................................................................................................................................................ 15
a) Company weaknesses in security............................................................................................................. 15
b) How to keep a network safe?.................................................................................................................. 15
c) Biggest threat for the System of Perfect Home Lettings...........................................................................15
d) Secure connection................................................................................................................................... 15
e) Wireless Guest Network.......................................................................................................................... 16
Task 4: Diagram and explanation..................................................................................................................... 17
a) Logical network diagram (Perfect Home Lettings).................................................................................... 17
b) How to keep a network safe?.................................................................................................................. 17
C) Hardware Components............................................................................................................................ 17
d) Secure connection................................................................................................................................... 17
Task 5: Telephony............................................................................................................................................ 18
a) Voice over IP............................................................................................................................................ 18
b) Incorporate VoIP into a system................................................................................................................ 18
Conclusion....................................................................................................................................................... 19
References:...................................................................................................................................................... 20
2 | P a g e
TABLE OF CONTENTS
Table of Contents............................................................................................................................................... 2
Introduction....................................................................................................................................................... 3
Task 1: Network Infrastructure and Protocols.................................................................................................... 4
a) 10base T over Cat 5 UTP, newer versions of Ethernet and Wi-Fi................................................................4
b) Networking devices/components.............................................................................................................. 5
c) OSI Model.................................................................................................................................................. 7
d) Protocols used by Perfect Home Lettings................................................................................................... 9
Task 2: Addressing........................................................................................................................................... 10
a) The need for addresses in network components.....................................................................................10
b) Differences between a private and a public IPv4 address........................................................................10
c) DHCP........................................................................................................................................................ 12
d) ARP.......................................................................................................................................................... 12
e) Default Gateway and Subnet Mask.......................................................................................................... 13
f) IP routing table......................................................................................................................................... 13
Task 3: Security................................................................................................................................................ 15
a) Company weaknesses in security............................................................................................................. 15
b) How to keep a network safe?.................................................................................................................. 15
c) Biggest threat for the System of Perfect Home Lettings...........................................................................15
d) Secure connection................................................................................................................................... 15
e) Wireless Guest Network.......................................................................................................................... 16
Task 4: Diagram and explanation..................................................................................................................... 17
a) Logical network diagram (Perfect Home Lettings).................................................................................... 17
b) How to keep a network safe?.................................................................................................................. 17
C) Hardware Components............................................................................................................................ 17
d) Secure connection................................................................................................................................... 17
Task 5: Telephony............................................................................................................................................ 18
a) Voice over IP............................................................................................................................................ 18
b) Incorporate VoIP into a system................................................................................................................ 18
Conclusion....................................................................................................................................................... 19
References:...................................................................................................................................................... 20
2 | P a g e

Presented by Saverio Davide Migale Computer Networks
INTRODUCTION
My name is Saverio Davide Migale and I am currently studying information technology from
NCC Education (Level 4 Diploma Computing) at STC Higher Education in Malta. I am working
as a German Content Manager for a betting company, but I would like to change my career path
and become a good software developer. I decided to take this step since I would like to have
not just a job which I like but a job which I love. Totally in accordance with the quotation:
“Choose a job you love, and you will never have to work a day in your life.” (Confucius)
I apologize in advance for the “few” spelling mistakes and other language errors in my
assignment, but my English is still not on a good level. However, I will try my best!
3 | P a g e
INTRODUCTION
My name is Saverio Davide Migale and I am currently studying information technology from
NCC Education (Level 4 Diploma Computing) at STC Higher Education in Malta. I am working
as a German Content Manager for a betting company, but I would like to change my career path
and become a good software developer. I decided to take this step since I would like to have
not just a job which I like but a job which I love. Totally in accordance with the quotation:
“Choose a job you love, and you will never have to work a day in your life.” (Confucius)
I apologize in advance for the “few” spelling mistakes and other language errors in my
assignment, but my English is still not on a good level. However, I will try my best!
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Presented by Saverio Davide Migale Computer Networks
TASK 1: NETWORK INFRASTRUCTURE AND
PROTOCOLS
The building has an existing 10base T infrastructure. The MD has asked you to provide a report
to clarify the following:
A) 10BASE T OVER CAT 5 UTP, NEWER VERSIONS OF ETHERNET
AND WI-FI
It has been suggested that there are THREE (3) major options for providing the network: Use
the existing 10base T infrastructure, Replace it with newer Ethernet components/ cabling, or
Use Wi-Fi. Explain the differences between 10base T over Cat 5 UTP; newer versions of
Ethernet; and Wi-Fi. Based on the THREE (3) options, recommend which technology the
company should use. You should discuss differences in data rate, the type of cable required,
and network contention. A good answer will relate your recommendation to the business
requirements.
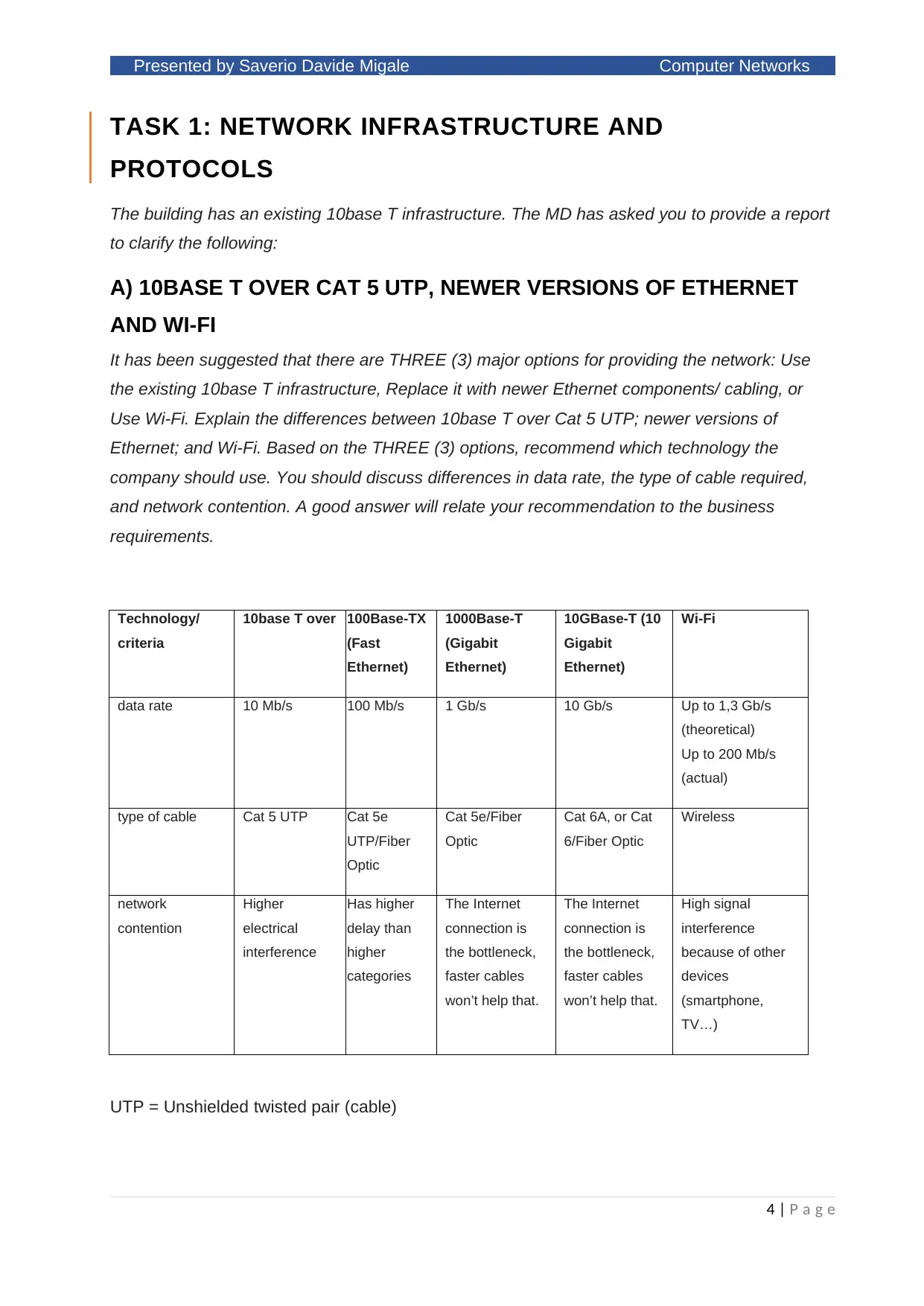
Technology/
criteria
10base T over 100Base-TX
(Fast
Ethernet)
1000Base-T
(Gigabit
Ethernet)
10GBase-T (10
Gigabit
Ethernet)
Wi-Fi
data rate 10 Mb/s 100 Mb/s 1 Gb/s 10 Gb/s Up to 1,3 Gb/s
(theoretical)
Up to 200 Mb/s
(actual)
type of cable Cat 5 UTP Cat 5e
UTP/Fiber
Optic
Cat 5e/Fiber
Optic
Cat 6A, or Cat
6/Fiber Optic
Wireless
network
contention
Higher
electrical
interference
Has higher
delay than
higher
categories
The Internet
connection is
the bottleneck,
faster cables
won’t help that.
The Internet
connection is
the bottleneck,
faster cables
won’t help that.
High signal
interference
because of other
devices
(smartphone,
TV…)
UTP = Unshielded twisted pair (cable)
4 | P a g e
TASK 1: NETWORK INFRASTRUCTURE AND
PROTOCOLS
The building has an existing 10base T infrastructure. The MD has asked you to provide a report
to clarify the following:
A) 10BASE T OVER CAT 5 UTP, NEWER VERSIONS OF ETHERNET
AND WI-FI
It has been suggested that there are THREE (3) major options for providing the network: Use
the existing 10base T infrastructure, Replace it with newer Ethernet components/ cabling, or
Use Wi-Fi. Explain the differences between 10base T over Cat 5 UTP; newer versions of
Ethernet; and Wi-Fi. Based on the THREE (3) options, recommend which technology the
company should use. You should discuss differences in data rate, the type of cable required,
and network contention. A good answer will relate your recommendation to the business
requirements.
Technology/
criteria
10base T over 100Base-TX
(Fast
Ethernet)
1000Base-T
(Gigabit
Ethernet)
10GBase-T (10
Gigabit
Ethernet)
Wi-Fi
data rate 10 Mb/s 100 Mb/s 1 Gb/s 10 Gb/s Up to 1,3 Gb/s
(theoretical)
Up to 200 Mb/s
(actual)
type of cable Cat 5 UTP Cat 5e
UTP/Fiber
Optic
Cat 5e/Fiber
Optic
Cat 6A, or Cat
6/Fiber Optic
Wireless
network
contention
Higher
electrical
interference
Has higher
delay than
higher
categories
The Internet
connection is
the bottleneck,
faster cables
won’t help that.
The Internet
connection is
the bottleneck,
faster cables
won’t help that.
High signal
interference
because of other
devices
(smartphone,
TV…)
UTP = Unshielded twisted pair (cable)
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Presented by Saverio Davide Migale Computer Networks
In general, it is important to keep the network as wired as possible in a company. (Wi-Fi is more
insecure and has higher interference.) Other important factors are money, infrastructure and
required amount of data.
In the case of Perfect Home Lettings, the company needs a separate Wi-Fi access point for the
guests (Wireless guest network). The most convenient solution for the local area network would
be upgrading to Fast Ethernet and additional use Wi-Fi Hotspots (For Tab orSmartphone).
Reason: Upgrading to Fast Ethernet is the least expensive solution and the bandwidth of 100
MB/s is sufficient in the case of Perfect Home Lettings.
B) NETWORKING DEVICES/COMPONENTS
A hub, a switch, a wireless access point and a router are networking components. Explain the
differences between them and identify the OSI layer at which each component operates. For
each component, support your answer with ONE (1) reason.
Hub:
Hub is a device that connects network computers in an Ethernet Network. All connected devices
are interconnected and form a single network (local area network). A hub operates in the first
level of the OSI model (Physical layer).
Switch:
A switch looks similar to a hub and serves as a controller. Unlike a hub, a switch is determined
as a device whose ports are connected to the devices and it sends the data packets to the
correct address (to the target device). A Switch works at the Data Link layer i.e. the second
layer of the OSI model.
Wireless access point:
A wireless access point acts as an interface between wireless devices and a wired device. The
signal is converted without the other devices being aware of it. A device usually has only one
cable connection, which in most cases is connected to a switch. A Wireless access point
operates in the Data Link layer.
Router:
A Router is a network device that operates in the Network Layer. It connects different networks
together. In general, a router sends a data packet to another router and this in turn sends it on
in its Local Area Network until the destination node is reached.
5 | P a g e
In general, it is important to keep the network as wired as possible in a company. (Wi-Fi is more
insecure and has higher interference.) Other important factors are money, infrastructure and
required amount of data.
In the case of Perfect Home Lettings, the company needs a separate Wi-Fi access point for the
guests (Wireless guest network). The most convenient solution for the local area network would
be upgrading to Fast Ethernet and additional use Wi-Fi Hotspots (For Tab orSmartphone).
Reason: Upgrading to Fast Ethernet is the least expensive solution and the bandwidth of 100
MB/s is sufficient in the case of Perfect Home Lettings.
B) NETWORKING DEVICES/COMPONENTS
A hub, a switch, a wireless access point and a router are networking components. Explain the
differences between them and identify the OSI layer at which each component operates. For
each component, support your answer with ONE (1) reason.
Hub:
Hub is a device that connects network computers in an Ethernet Network. All connected devices
are interconnected and form a single network (local area network). A hub operates in the first
level of the OSI model (Physical layer).
Switch:
A switch looks similar to a hub and serves as a controller. Unlike a hub, a switch is determined
as a device whose ports are connected to the devices and it sends the data packets to the
correct address (to the target device). A Switch works at the Data Link layer i.e. the second
layer of the OSI model.
Wireless access point:
A wireless access point acts as an interface between wireless devices and a wired device. The
signal is converted without the other devices being aware of it. A device usually has only one
cable connection, which in most cases is connected to a switch. A Wireless access point
operates in the Data Link layer.
Router:
A Router is a network device that operates in the Network Layer. It connects different networks
together. In general, a router sends a data packet to another router and this in turn sends it on
in its Local Area Network until the destination node is reached.
5 | P a g e
Presented by Saverio Davide Migale Computer Networks
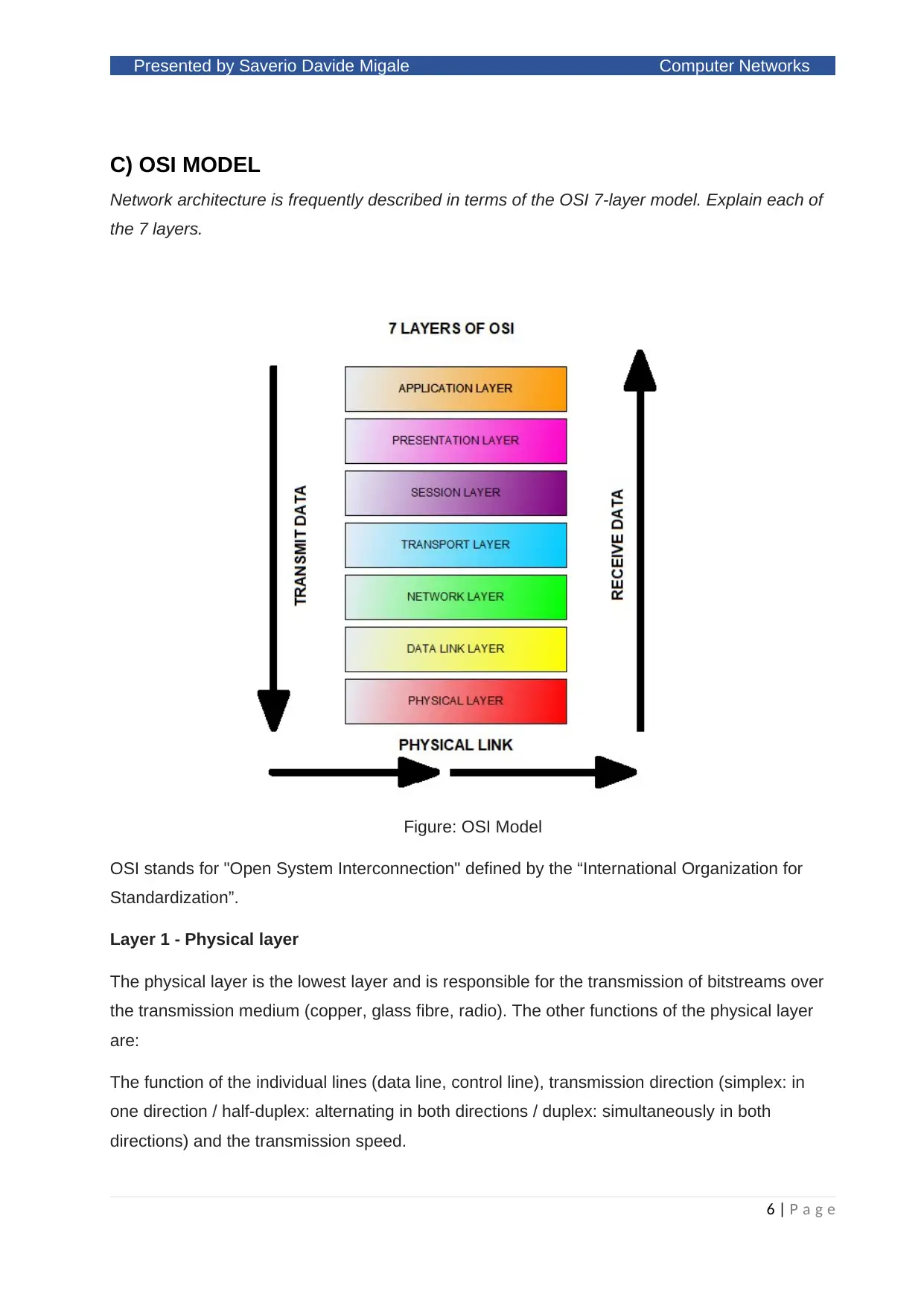
C) OSI MODEL
Network architecture is frequently described in terms of the OSI 7-layer model. Explain each of
the 7 layers.
Figure: OSI Model
OSI stands for "Open System Interconnection" defined by the “International Organization for
Standardization”.
Layer 1 - Physical layer
The physical layer is the lowest layer and is responsible for the transmission of bitstreams over
the transmission medium (copper, glass fibre, radio). The other functions of the physical layer
are:
The function of the individual lines (data line, control line), transmission direction (simplex: in
one direction / half-duplex: alternating in both directions / duplex: simultaneously in both
directions) and the transmission speed.
6 | P a g e
C) OSI MODEL
Network architecture is frequently described in terms of the OSI 7-layer model. Explain each of
the 7 layers.
Figure: OSI Model
OSI stands for "Open System Interconnection" defined by the “International Organization for
Standardization”.
Layer 1 - Physical layer
The physical layer is the lowest layer and is responsible for the transmission of bitstreams over
the transmission medium (copper, glass fibre, radio). The other functions of the physical layer
are:
The function of the individual lines (data line, control line), transmission direction (simplex: in
one direction / half-duplex: alternating in both directions / duplex: simultaneously in both
directions) and the transmission speed.
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Presented by Saverio Davide Migale Computer Networks
Devices and network components associated with the physical layer include the connector and
socket for the network cable, the repeater, the hub, the transceiver and the terminator.
Layer 2 - Data Link layer
The function of the data link layer is to perform reliable exchange of data packets between the
systems. It is divided into two sublayers: The Medium Access Control (MAC) layer adjacent to
the Physical Layer (Layer 1) and the LLC (Logical Link Control) layer adjacent to the Network
Layer (Layer 3).
The Mac layer controls the use of the transmission media and writes the physical address and
sends and receives address in the protocol of the data packets. The LLC layer divides the bit
stream into frames and performs error detection and correction. - Sample devices assigned to
this layer are Bridge and Switch.
Layer 3 - Network layer
The network layer controls the exchange of data packets, since these cannot be conveyed
directly to the destination and therefore be provided with intermediate destinations. The data
packets are then transmitted from node to node until they reach their destination. To implement
this, the network layer identifies the individual network nodes, sets up and disconnects
connection channels and takes care of route control (routing) and data flow control. Sample
device assigned to this layer is a router.
Layer 4 - Transport Layer
The transport layer is the top layer of the transport system and is the interface to the application
system. The transport layer converts the data packets according to protocol information and
ensures the correct composition of the packets at the receiver.
Layer 5 - Session Layer
The session layer is the lowest layer of the application system and establishes, controls and
terminates logical connections between the sender and the receiver.
Layer 6 - Presentation layer
The presentation layer acts as an interpreter by translating the data packets into the appropriate
format of the sender or recipient node. Data compression and encryption are also part of their
job(Forouzan, 2007).
Layer 7 - Application Layer
7 | P a g e
Devices and network components associated with the physical layer include the connector and
socket for the network cable, the repeater, the hub, the transceiver and the terminator.
Layer 2 - Data Link layer
The function of the data link layer is to perform reliable exchange of data packets between the
systems. It is divided into two sublayers: The Medium Access Control (MAC) layer adjacent to
the Physical Layer (Layer 1) and the LLC (Logical Link Control) layer adjacent to the Network
Layer (Layer 3).
The Mac layer controls the use of the transmission media and writes the physical address and
sends and receives address in the protocol of the data packets. The LLC layer divides the bit
stream into frames and performs error detection and correction. - Sample devices assigned to
this layer are Bridge and Switch.
Layer 3 - Network layer
The network layer controls the exchange of data packets, since these cannot be conveyed
directly to the destination and therefore be provided with intermediate destinations. The data
packets are then transmitted from node to node until they reach their destination. To implement
this, the network layer identifies the individual network nodes, sets up and disconnects
connection channels and takes care of route control (routing) and data flow control. Sample
device assigned to this layer is a router.
Layer 4 - Transport Layer
The transport layer is the top layer of the transport system and is the interface to the application
system. The transport layer converts the data packets according to protocol information and
ensures the correct composition of the packets at the receiver.
Layer 5 - Session Layer
The session layer is the lowest layer of the application system and establishes, controls and
terminates logical connections between the sender and the receiver.
Layer 6 - Presentation layer
The presentation layer acts as an interpreter by translating the data packets into the appropriate
format of the sender or recipient node. Data compression and encryption are also part of their
job(Forouzan, 2007).
Layer 7 - Application Layer
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Presented by Saverio Davide Migale Computer Networks
The application layer is the interface to the actual user application. Here, the network data is
converted into “usable data”. E.g. of applications: Google Chrome, Microsoft Excel, Word etc.
D) PROTOCOLS USED BY PERFECT HOME LETTINGS
Based on the applications that will be used by Perfect Home Lettings, and making any suitable
assumptions, identify and briefly explain the purpose of FOUR (4) protocols used. For each
protocol, identify the layer at which they operate.
FTP (File Transfer Protocol)
The File Transfer Protocol is a network protocol specified in RFC 959 of 1985. It is used to
transfer files over IP networks. FTP operates in the application layer of the OSI layer model. It is
used to download or upload files from/to the server. In addition, directories can be created and
read out, and directories and files can be renamed or deleted (with the necessary rights). The
connection is possible via web browser or applications such as: WinSCP, FileZilla…
IMAP (Internet Messaged Access Protocol)
Since employees work with different devices, an IMAP protocol makes more sense than a
POP3 protocol. With IMAP, the messages are always synchronized with the mail server, so that
any changes are made in the mail client (e.g. Outlook) are immediately displayed in the webmail
inbox, and so the change is visible immediately upon access via other device.
SMTP (Simple Mail Transfer Protocol)
The SMTP protocol is mainly used for sending email. Like the FTP and IMAP protocol, SMTP
also operates in layer 7 of the OSI model.
TLS (Transport Layer Security)
The Transport Layer Security Protocol is used to protect the privacy and data integrity of
network communications. The TLS protocol works at the session layer of the OSI model for
managing sessions(Rouse, 2007).
8 | P a g e
The application layer is the interface to the actual user application. Here, the network data is
converted into “usable data”. E.g. of applications: Google Chrome, Microsoft Excel, Word etc.
D) PROTOCOLS USED BY PERFECT HOME LETTINGS
Based on the applications that will be used by Perfect Home Lettings, and making any suitable
assumptions, identify and briefly explain the purpose of FOUR (4) protocols used. For each
protocol, identify the layer at which they operate.
FTP (File Transfer Protocol)
The File Transfer Protocol is a network protocol specified in RFC 959 of 1985. It is used to
transfer files over IP networks. FTP operates in the application layer of the OSI layer model. It is
used to download or upload files from/to the server. In addition, directories can be created and
read out, and directories and files can be renamed or deleted (with the necessary rights). The
connection is possible via web browser or applications such as: WinSCP, FileZilla…
IMAP (Internet Messaged Access Protocol)
Since employees work with different devices, an IMAP protocol makes more sense than a
POP3 protocol. With IMAP, the messages are always synchronized with the mail server, so that
any changes are made in the mail client (e.g. Outlook) are immediately displayed in the webmail
inbox, and so the change is visible immediately upon access via other device.
SMTP (Simple Mail Transfer Protocol)
The SMTP protocol is mainly used for sending email. Like the FTP and IMAP protocol, SMTP
also operates in layer 7 of the OSI model.
TLS (Transport Layer Security)
The Transport Layer Security Protocol is used to protect the privacy and data integrity of
network communications. The TLS protocol works at the session layer of the OSI model for
managing sessions(Rouse, 2007).
8 | P a g e

Presented by Saverio Davide Migale Computer Networks
TASK 2: ADDRESSING
Perfect Home Lettings wants you to provide a clear explanation about network addressing.
A) THE NEED FOR ADDRESSES IN NETWORK COMPONENTS
Explain why network components need addresses. Explain clearly the differences between a
MAC address and an IP address. Distinguish briefly between IPv4 and IPv6.
Why an online shop needs the addresses of their customers? So that they can send the
products directly to the right person or communicate directly with the right customer!
E.g. If an online shop doesn’t know the right address it would have to send the goods to each
person in a city or in the worst case over the world and the wrong recipients would hopefully
send it back until it arrives at the right receiver.
It works exactly that way within a network. It is essential to know where to send the information.
This ensures that the goods or data end up directly at the right recipient. This means that each
network component should have an individual address, or it comes to communication problems.
MAC address and IP address complete important network functions but both addresses serve
different purposes and are visible in several ways.
MAC address IP address
The MAC address is different for every sending
device (WLAN stick, router, etc.). It is like a serial
number of a device that connect to a network.
The IP number can (if DHCP is used) change from
device to device again and again.
MAC address operates in OSI layer 2 (data link layer) IP address operates in OSI layer 3 (network layer)
E.g.: MAC is like the name of “your house”. E.g.: IP the exact address of “your house”.
“So, to sum all that up, remember that an IP address is a logical address which is configured via
the operating system, while the MAC address is a hardware address, burnt into the network
card's ROM (read only memory) during the manufacturing process.”
(Partsenidis, 2003)
IPV4 AND IPV6
9 | P a g e
TASK 2: ADDRESSING
Perfect Home Lettings wants you to provide a clear explanation about network addressing.
A) THE NEED FOR ADDRESSES IN NETWORK COMPONENTS
Explain why network components need addresses. Explain clearly the differences between a
MAC address and an IP address. Distinguish briefly between IPv4 and IPv6.
Why an online shop needs the addresses of their customers? So that they can send the
products directly to the right person or communicate directly with the right customer!
E.g. If an online shop doesn’t know the right address it would have to send the goods to each
person in a city or in the worst case over the world and the wrong recipients would hopefully
send it back until it arrives at the right receiver.
It works exactly that way within a network. It is essential to know where to send the information.
This ensures that the goods or data end up directly at the right recipient. This means that each
network component should have an individual address, or it comes to communication problems.
MAC address and IP address complete important network functions but both addresses serve
different purposes and are visible in several ways.
MAC address IP address
The MAC address is different for every sending
device (WLAN stick, router, etc.). It is like a serial
number of a device that connect to a network.
The IP number can (if DHCP is used) change from
device to device again and again.
MAC address operates in OSI layer 2 (data link layer) IP address operates in OSI layer 3 (network layer)
E.g.: MAC is like the name of “your house”. E.g.: IP the exact address of “your house”.
“So, to sum all that up, remember that an IP address is a logical address which is configured via
the operating system, while the MAC address is a hardware address, burnt into the network
card's ROM (read only memory) during the manufacturing process.”
(Partsenidis, 2003)
IPV4 AND IPV6
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Presented by Saverio Davide Migale Computer Networks
IPv4 addresses consist of 32-bit and a maximum of 12 characters, which are divided into four
blocks. IPv6 instead is 128 bits long and divided into 8 sections of 4 characters each. Unlike
IPv4, letters are allowed here as well.
IPv4 address IPv6 addresss
Consist of 32-bit Consists of 128-bit
Divided into 4 blocks Divided into 8 blocks
Only numbers allowed (Decimals) Letters and numbers allowed (Hexadecimals)
B) DIFFERENCES BETWEEN A PRIVATE AND A PUBLIC IPV4
ADDRESS
Perfect Home Lettings would like you to explain the differences between a private IPv4 address
and a public IPv4 address. Ensure you explain where the private IPv4 and public IPv4
addresses will be use in their network. State the Private IP address ranges.
PRIVATE IPV4 ADDRESS AND A PUBLIC IPV4 ADDRESS
The private IPv4 address (also called a local IP address) is not visible in the internet and
reserved for use behind a router or other network address translation device. In addition, the
private IPv4 address is needed for personal use in home and business networks.
Three IP address ranges are for home use:
10.0.0.1 to 10.255.255.254 (Class A)
172.16.0.1 to 172.31.255.254 (Class B)
192.168.0.1 to 192.168.255.254 (Class C)
(These are the internationally specified privately usable address ranges.)
By contrast, public IPv4, as the name implies, is used publicly and cannot be used in a home or
business network compared to IPv4.
In the case of Perfect Home Lettings the private IPv4 address will be in use in their offices to
connect each device to each other and the public IPv4 address will be in use on their website so
that everyone on the world has possibility to access to it(Pyles, 2016).
10 | P a g e
IPv4 addresses consist of 32-bit and a maximum of 12 characters, which are divided into four
blocks. IPv6 instead is 128 bits long and divided into 8 sections of 4 characters each. Unlike
IPv4, letters are allowed here as well.
IPv4 address IPv6 addresss
Consist of 32-bit Consists of 128-bit
Divided into 4 blocks Divided into 8 blocks
Only numbers allowed (Decimals) Letters and numbers allowed (Hexadecimals)
B) DIFFERENCES BETWEEN A PRIVATE AND A PUBLIC IPV4
ADDRESS
Perfect Home Lettings would like you to explain the differences between a private IPv4 address
and a public IPv4 address. Ensure you explain where the private IPv4 and public IPv4
addresses will be use in their network. State the Private IP address ranges.
PRIVATE IPV4 ADDRESS AND A PUBLIC IPV4 ADDRESS
The private IPv4 address (also called a local IP address) is not visible in the internet and
reserved for use behind a router or other network address translation device. In addition, the
private IPv4 address is needed for personal use in home and business networks.
Three IP address ranges are for home use:
10.0.0.1 to 10.255.255.254 (Class A)
172.16.0.1 to 172.31.255.254 (Class B)
192.168.0.1 to 192.168.255.254 (Class C)
(These are the internationally specified privately usable address ranges.)
By contrast, public IPv4, as the name implies, is used publicly and cannot be used in a home or
business network compared to IPv4.
In the case of Perfect Home Lettings the private IPv4 address will be in use in their offices to
connect each device to each other and the public IPv4 address will be in use on their website so
that everyone on the world has possibility to access to it(Pyles, 2016).
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Presented by Saverio Davide Migale Computer Networks
C) DHCP
Explain what DHCP is, and why you would use it.
DHCP stands for Dynamic Host Configuration Protocol and describes a procedure that
automatically assigns configuration data to clients on a network. The idea is a Plug 'n Play
network: Example in real life:A person who is travelling a lot, does not always want to manually
configure the network connection of the tablet/notebook.
Why use DHCP?
Without DHCP, one would have to manually enter the IP address for each computer in a
company. As soon as the computer changes the location and thus the network, one would also
have to adjust the IP address manually. Using DHCP, a network administrator can view and
automatically assign IP addresses from a central location whenever a computer connects to
another network(Forouzan, 2007).
D) ARP
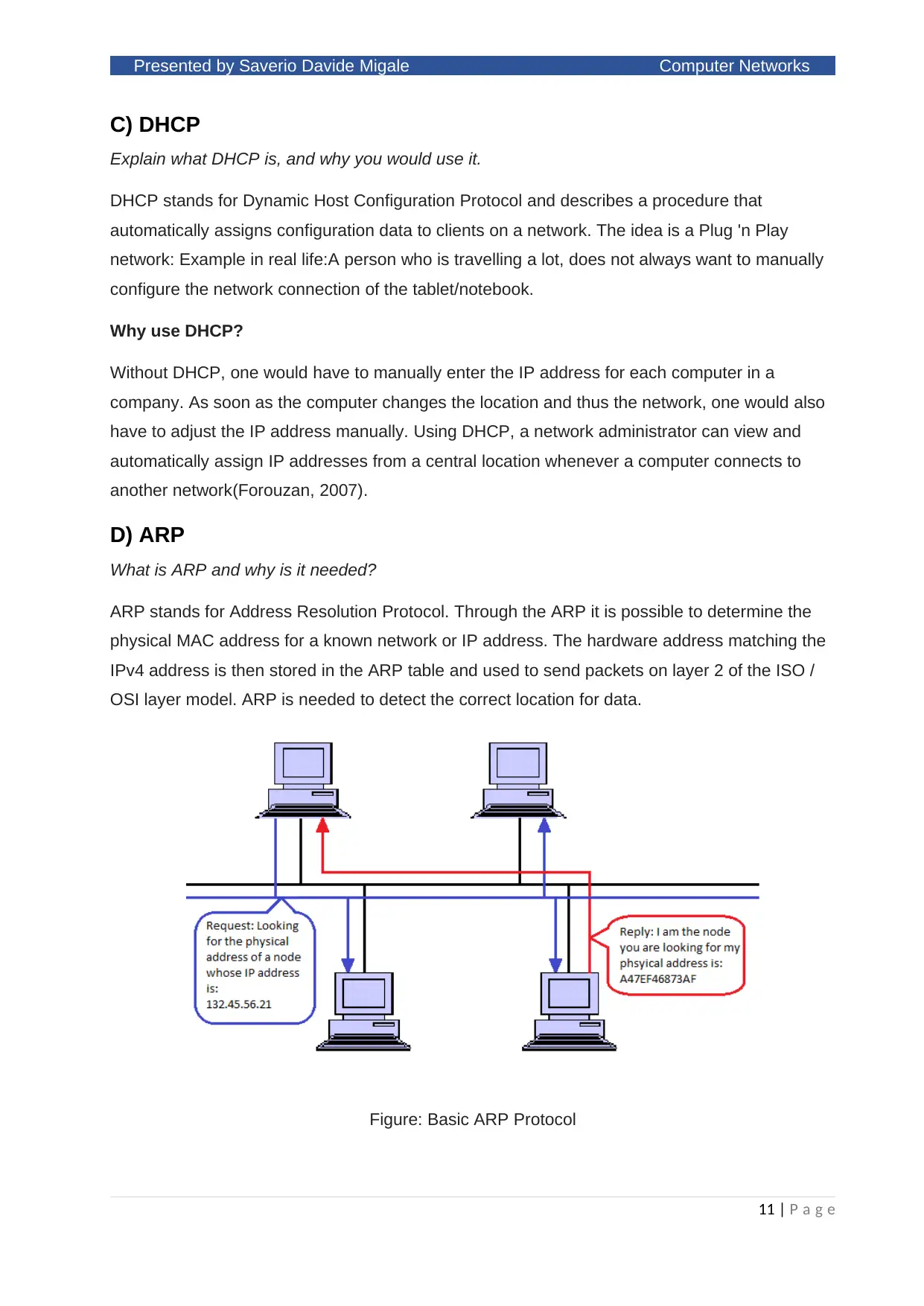
What is ARP and why is it needed?
ARP stands for Address Resolution Protocol. Through the ARP it is possible to determine the
physical MAC address for a known network or IP address. The hardware address matching the
IPv4 address is then stored in the ARP table and used to send packets on layer 2 of the ISO /
OSI layer model. ARP is needed to detect the correct location for data.
Figure: Basic ARP Protocol
11 | P a g e
C) DHCP
Explain what DHCP is, and why you would use it.
DHCP stands for Dynamic Host Configuration Protocol and describes a procedure that
automatically assigns configuration data to clients on a network. The idea is a Plug 'n Play
network: Example in real life:A person who is travelling a lot, does not always want to manually
configure the network connection of the tablet/notebook.
Why use DHCP?
Without DHCP, one would have to manually enter the IP address for each computer in a
company. As soon as the computer changes the location and thus the network, one would also
have to adjust the IP address manually. Using DHCP, a network administrator can view and
automatically assign IP addresses from a central location whenever a computer connects to
another network(Forouzan, 2007).
D) ARP
What is ARP and why is it needed?
ARP stands for Address Resolution Protocol. Through the ARP it is possible to determine the
physical MAC address for a known network or IP address. The hardware address matching the
IPv4 address is then stored in the ARP table and used to send packets on layer 2 of the ISO /
OSI layer model. ARP is needed to detect the correct location for data.
Figure: Basic ARP Protocol
11 | P a g e

Presented by Saverio Davide Migale Computer Networks
E) DEFAULT GATEWAY AND SUBNET MASK
Define the terms Default Gateway and Subnet Mask and briefly explain why both are required in
this project.
Default Gateway:
A default gateway is used to connect IP networks. Because this gateway is used by default, it is
also called "default network". If no application specifies another gateway, the default gateway is
used.
Subnet Mask
A subnet mask is a 32-bit number, disguising the IP address and segmenting it into a network
address and host address. It it connected by routers and form a large interconnected network.
https://www.iplocation.net/subnet-mask
Required for this project, because:
- The default gateway allows communication with a subnet. For Perfect Home Lettings, a
standard gateway is essential.
- The subnet mask is needed to identify the network address of the IP address on the default
gateway.
F) IP ROUTING TABLE
Explain what is meant by an IP Routing Table and provide ONE (1) example of how a router
uses its routing table on the Internet. You do NOT have to explain every field in the routing
table. In your example, explain how a packet gets from source to destination.
A routing table is a set of rules that are often output in table format. These rules are used to
decide which data packets are routed to where in an IP network. All devices that use IP (e.g.
switches and routers) use routing tables.
Screenshot: Scan of IP Routing table in Windows
Example: We have the destination 66.211.185.25 (ebay.com), if we now want to send a packet
to this destination the following happens: In the IP routing table it is checked if the destination
already exists, if not, the default Gateway is used (10.0.2.2). Now our router sends the packet to
12 | P a g e
E) DEFAULT GATEWAY AND SUBNET MASK
Define the terms Default Gateway and Subnet Mask and briefly explain why both are required in
this project.
Default Gateway:
A default gateway is used to connect IP networks. Because this gateway is used by default, it is
also called "default network". If no application specifies another gateway, the default gateway is
used.
Subnet Mask
A subnet mask is a 32-bit number, disguising the IP address and segmenting it into a network
address and host address. It it connected by routers and form a large interconnected network.
https://www.iplocation.net/subnet-mask
Required for this project, because:
- The default gateway allows communication with a subnet. For Perfect Home Lettings, a
standard gateway is essential.
- The subnet mask is needed to identify the network address of the IP address on the default
gateway.
F) IP ROUTING TABLE
Explain what is meant by an IP Routing Table and provide ONE (1) example of how a router
uses its routing table on the Internet. You do NOT have to explain every field in the routing
table. In your example, explain how a packet gets from source to destination.
A routing table is a set of rules that are often output in table format. These rules are used to
decide which data packets are routed to where in an IP network. All devices that use IP (e.g.
switches and routers) use routing tables.
Screenshot: Scan of IP Routing table in Windows
Example: We have the destination 66.211.185.25 (ebay.com), if we now want to send a packet
to this destination the following happens: In the IP routing table it is checked if the destination
already exists, if not, the default Gateway is used (10.0.2.2). Now our router sends the packet to
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

