Pervasive Systems Project: Emergency Control Room and Network Design
VerifiedAdded on 2023/06/07
|16
|3285
|398
Project
AI Summary
This project explores pervasive systems, focusing on the application of pervasive computing in healthcare and emergency control room design. Section A discusses the integration of pervasive technologies in healthcare, including participatory e-learning, clinical decision support systems, patient empowerment, and the legal aspects of telehealth. Section B details the design of a pervasive system for an emergency control room, emphasizing user interface design, software reuse, and adherence to the SDLC. Section C focuses on network design, comparing wireless bridge and long-range wireless bridge technologies using OPNET simulation to connect two campus sites. The project further explores connecting buildings within the main site using point-to-point connections and directional antennas, concluding with a discussion of access point technologies such as IEEE 802.11 Wi-Fi and IEEE 802.15.4 ZigBee.

Pervasive Systems 1
PERVASIVE SYSTEMS
Student’s Name
University
Course
Date
PERVASIVE SYSTEMS
Student’s Name
University
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pervasive Systems 2
Pervasive Systems
Section A (A1)
The widespread use of Pervasive Computing and Information technologies in the
healthcare sector results in the need of educating the health care providers and the patients. The
training strategy to be adopted in the education sessions is known as participatory e-learning.
The nurse uses the system to make data entries regarding the patients’ medical history, diagnosis,
and lab reports (Stanford, 2002). The patients would effectively use the educational materials to
familiarize themselves with the system to increase their confidence level.
Pervasive systems facilitates the decision-making process through the use of Clinical Decision
Support System. The system provides a platform upon which the medical practitioners use
evidence to arrive at decisions and not opinion-based decisions. According to Greenfield (2010),
nurses require documenting all information regarding a respective patient’s health status in the
EHR. In the documentation process, the nurses use a standardized nursing language entailing
standardized terminologies (Satyanarayanan, 2001).
Patient empowerment and engagement is the cornerstone of determining the impact of
telehealth as well as wireless devices applications on the outcomes of health. It provides a
convenient platform for the improvement of patient engagement. According to Glinkowski, et al.
(2013), lack of patient empowerment and engagement results in an increased rate of mortality
that would have been preventable. Therefore, patients are encouraged to get involved in their
respective healthcare management. Communication and feedback are crucial in patient
engagement through effective management of changes in patient health behaviour. Patient
engagement is increased through the use of telehealth since the health care providers can
conveniently reach their patients; as a result, improving the relationship between the patient and
the healthcare provider.
Pervasive Systems
Section A (A1)
The widespread use of Pervasive Computing and Information technologies in the
healthcare sector results in the need of educating the health care providers and the patients. The
training strategy to be adopted in the education sessions is known as participatory e-learning.
The nurse uses the system to make data entries regarding the patients’ medical history, diagnosis,
and lab reports (Stanford, 2002). The patients would effectively use the educational materials to
familiarize themselves with the system to increase their confidence level.
Pervasive systems facilitates the decision-making process through the use of Clinical Decision
Support System. The system provides a platform upon which the medical practitioners use
evidence to arrive at decisions and not opinion-based decisions. According to Greenfield (2010),
nurses require documenting all information regarding a respective patient’s health status in the
EHR. In the documentation process, the nurses use a standardized nursing language entailing
standardized terminologies (Satyanarayanan, 2001).
Patient empowerment and engagement is the cornerstone of determining the impact of
telehealth as well as wireless devices applications on the outcomes of health. It provides a
convenient platform for the improvement of patient engagement. According to Glinkowski, et al.
(2013), lack of patient empowerment and engagement results in an increased rate of mortality
that would have been preventable. Therefore, patients are encouraged to get involved in their
respective healthcare management. Communication and feedback are crucial in patient
engagement through effective management of changes in patient health behaviour. Patient
engagement is increased through the use of telehealth since the health care providers can
conveniently reach their patients; as a result, improving the relationship between the patient and
the healthcare provider.

Pervasive Systems 3
The legal concept of telehealth and Information technology application in health sector
through the monitoring is defined by the American Recovery and Reinvestment Act which
focuses on healthcare technological developments. According to the article pervasive computing
is an economic stimulus package that uses incentives to promote meaningful use of technologies
such as the electronic healthcare records. The technological enactment is majorly aimed at
improving healthcare services of the nation at large (Satyanarayanan, 2001). Vendors of the
wireless as well as communication devices are tasked with ensuring safety and security of the
public health sector are enforced through the issue of telehealth licensure compact. The licensure
compact issued to a specific nurse serves as a multistate license that allows nursing practice
through telehealth in several states remotely.
Pervasive computing platform is not managed by customers but managed by another person on
behalf of the customers. The service providers have advanced their services to reduce the worries
of the customers such us viruses on the data stored in their databases (Munir, 2007). Service
provider only does the work and leaves it in the hands of another person who solves the problem
of provision of dependable computing to another person.
The service providers are not only majoring on acquiring more and more customers but are also
focusing on the wellbeing of the patients in terms security and its compliance. This is achieved
through provisions of a framework or a model that define compliance of security subsystems and
processes (Ranganathan, 2004). Pervasive systems promote best practices in security assurance
in medicine environments. They have established security accreditation mechanism for cloud
computing in their wireless networks
Section A (A2)
Many of the medical service providers today have limited space required for the increasing
number of patients. The demand of the patients outweighs the services from the providers. This
The legal concept of telehealth and Information technology application in health sector
through the monitoring is defined by the American Recovery and Reinvestment Act which
focuses on healthcare technological developments. According to the article pervasive computing
is an economic stimulus package that uses incentives to promote meaningful use of technologies
such as the electronic healthcare records. The technological enactment is majorly aimed at
improving healthcare services of the nation at large (Satyanarayanan, 2001). Vendors of the
wireless as well as communication devices are tasked with ensuring safety and security of the
public health sector are enforced through the issue of telehealth licensure compact. The licensure
compact issued to a specific nurse serves as a multistate license that allows nursing practice
through telehealth in several states remotely.
Pervasive computing platform is not managed by customers but managed by another person on
behalf of the customers. The service providers have advanced their services to reduce the worries
of the customers such us viruses on the data stored in their databases (Munir, 2007). Service
provider only does the work and leaves it in the hands of another person who solves the problem
of provision of dependable computing to another person.
The service providers are not only majoring on acquiring more and more customers but are also
focusing on the wellbeing of the patients in terms security and its compliance. This is achieved
through provisions of a framework or a model that define compliance of security subsystems and
processes (Ranganathan, 2004). Pervasive systems promote best practices in security assurance
in medicine environments. They have established security accreditation mechanism for cloud
computing in their wireless networks
Section A (A2)
Many of the medical service providers today have limited space required for the increasing
number of patients. The demand of the patients outweighs the services from the providers. This
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Pervasive Systems 4
is a problem that every service provider is looking into to ensure that many of the clients in the
need of the services are satisfied and guaranteed of data expansion regarding volumes.
It's clear that cloud computing has transformed the face of information technology from the
management of owns IT infrastructure to leave the responsibility to someone else (Abowd,
2005). Adoption of the pervasive computing has widely been experienced in many of the
healthcare facilities all around the globe. Pervasive computing is associated with low costs and
flexible business processes (Hoffman, 2013). The concept of cloud computing got way in IT
after the innovation of virtual machines. Further advances were experienced when the
technology was introduced in telecommunications. Researchers have carried study to identify the
impact of pervasive computing to ICT and predict the future of service delivery. Extending
pervasive computing to greater heights, with challenges like security drawbacks being taken into
considerations. Security attacks such as brute force and DOS attacks are of major concern in
future of pervasive computing (Banavar, 2000). Major advancements in pervasive computing
ranging from managements, demand equilibrium and security and compliance make pervasive
systems better suited to the future.
Section A (A3)
Pervasive computing has nurtured the conceptual and the infrastructural arguments about the
computing world in the future days. There is experienced a rapid changed from the indigenous
way of computing (stand-alone computing) to a wireless-based way of computing. The
advantages of cloud-based computing are the driving factors towards the achievement of the
advanced technological level for more diversified services in health sector, higher security
aspects and evolved service provisions. Security in pervasive computing has remained a major
point of focus for those adopting the technology. New medication trends are evolving based on
pervasive computing with service provision across geographically dispersed health environments
is a problem that every service provider is looking into to ensure that many of the clients in the
need of the services are satisfied and guaranteed of data expansion regarding volumes.
It's clear that cloud computing has transformed the face of information technology from the
management of owns IT infrastructure to leave the responsibility to someone else (Abowd,
2005). Adoption of the pervasive computing has widely been experienced in many of the
healthcare facilities all around the globe. Pervasive computing is associated with low costs and
flexible business processes (Hoffman, 2013). The concept of cloud computing got way in IT
after the innovation of virtual machines. Further advances were experienced when the
technology was introduced in telecommunications. Researchers have carried study to identify the
impact of pervasive computing to ICT and predict the future of service delivery. Extending
pervasive computing to greater heights, with challenges like security drawbacks being taken into
considerations. Security attacks such as brute force and DOS attacks are of major concern in
future of pervasive computing (Banavar, 2000). Major advancements in pervasive computing
ranging from managements, demand equilibrium and security and compliance make pervasive
systems better suited to the future.
Section A (A3)
Pervasive computing has nurtured the conceptual and the infrastructural arguments about the
computing world in the future days. There is experienced a rapid changed from the indigenous
way of computing (stand-alone computing) to a wireless-based way of computing. The
advantages of cloud-based computing are the driving factors towards the achievement of the
advanced technological level for more diversified services in health sector, higher security
aspects and evolved service provisions. Security in pervasive computing has remained a major
point of focus for those adopting the technology. New medication trends are evolving based on
pervasive computing with service provision across geographically dispersed health environments
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pervasive Systems 5
put in priority (Bell, 2015). With the research and innovations of various vendors, the wireless-
based computing has enriched future based on diversification of the knowledge and security
enrichment (Buttyan and Hubaux, 2007). Drawbacks to the greater heights of wireless-based
computing should be on the major lookout to ensure credibility and consistency of the
technology are nourished. This paper presents a review on the major evolutions towards the
future of pervasive computing, inherent security issues and drawback resolutions on the
pervasive computing infrastructure.
Section B
Section B (B1)
Design of the pervasive system components that will be utilized for emergency control room for
a vehicle discovery component
Figure 1:Design of Pervasive System
In the design of call logger and vehicle discovery system, the interfaces should be in the
line with the rules of User Interface Design (Shneiderman, 2003). One of the requirement of the
user interface design if make it user centered meaning that the whole design should have in mind
that the system will be used by human that have certain critical limitation that need consideration
(Henricksen and Indulska, 2006).
put in priority (Bell, 2015). With the research and innovations of various vendors, the wireless-
based computing has enriched future based on diversification of the knowledge and security
enrichment (Buttyan and Hubaux, 2007). Drawbacks to the greater heights of wireless-based
computing should be on the major lookout to ensure credibility and consistency of the
technology are nourished. This paper presents a review on the major evolutions towards the
future of pervasive computing, inherent security issues and drawback resolutions on the
pervasive computing infrastructure.
Section B
Section B (B1)
Design of the pervasive system components that will be utilized for emergency control room for
a vehicle discovery component
Figure 1:Design of Pervasive System
In the design of call logger and vehicle discovery system, the interfaces should be in the
line with the rules of User Interface Design (Shneiderman, 2003). One of the requirement of the
user interface design if make it user centered meaning that the whole design should have in mind
that the system will be used by human that have certain critical limitation that need consideration
(Henricksen and Indulska, 2006).

Pervasive Systems 6
These design diagrams are made up of two specific sides. The left side displays the
required interfaces necessary for the component, while the right side illustrates the provided
interfaces for the components.
Section B (B2)
In the design of the systems software reuses is applied for a more user centered design and
save the time spend in the design from scratch (Henricksen and Indulska, 2004). Software
engineering field centred much on the design processes that was originally developed but slowly
by slowly new features are being integrated in the development to achieve more advanced
software, with less time spent and lower cost associated (Mili, 2001). To meet these goals there
has been adoption of systematic software reuse design process.
Section B (B3)
In the development of emergency control room, the design must follow all the steps as laid
by the SDLC it is a system that will involve the human character in the operations (Stefaner,
2009). Each step should be clearly defined in the system functionality achievement.
Section B (B4)
Development of the user development of emergency control room both for the call logger
and the vehicle discovery should concentrate in the issue that this is a safety system where
traversal should be easy (Shneiderman, 2003). The cognitive load for users in this system should
also be given a consideration because if it is overcrowded in the design therefore level of
confusion while in the system will be increased and at some point the response to the calls an
vehicle discovery affected (Oppermann, 2002).
Section B (B5)
The effective of the development of emergency control room will can only be known
through the testing of the users. The performance and time taken to learn the systems have to
These design diagrams are made up of two specific sides. The left side displays the
required interfaces necessary for the component, while the right side illustrates the provided
interfaces for the components.
Section B (B2)
In the design of the systems software reuses is applied for a more user centered design and
save the time spend in the design from scratch (Henricksen and Indulska, 2004). Software
engineering field centred much on the design processes that was originally developed but slowly
by slowly new features are being integrated in the development to achieve more advanced
software, with less time spent and lower cost associated (Mili, 2001). To meet these goals there
has been adoption of systematic software reuse design process.
Section B (B3)
In the development of emergency control room, the design must follow all the steps as laid
by the SDLC it is a system that will involve the human character in the operations (Stefaner,
2009). Each step should be clearly defined in the system functionality achievement.
Section B (B4)
Development of the user development of emergency control room both for the call logger
and the vehicle discovery should concentrate in the issue that this is a safety system where
traversal should be easy (Shneiderman, 2003). The cognitive load for users in this system should
also be given a consideration because if it is overcrowded in the design therefore level of
confusion while in the system will be increased and at some point the response to the calls an
vehicle discovery affected (Oppermann, 2002).
Section B (B5)
The effective of the development of emergency control room will can only be known
through the testing of the users. The performance and time taken to learn the systems have to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Pervasive Systems 7
come out as soon the users start carrying out their operations (Galitz, 2007). If the through the
traversal and learning in the system makes the user feel out of the system then it should be
redesigned and modifications done since when safety is compromised it is a failed achievement
in the system (Cohen, 2004) (Yau, 2002). A user can handle up to between seven and maximum
nine system items at a go in the memory thus this should even go to the lower to make it more
effective.
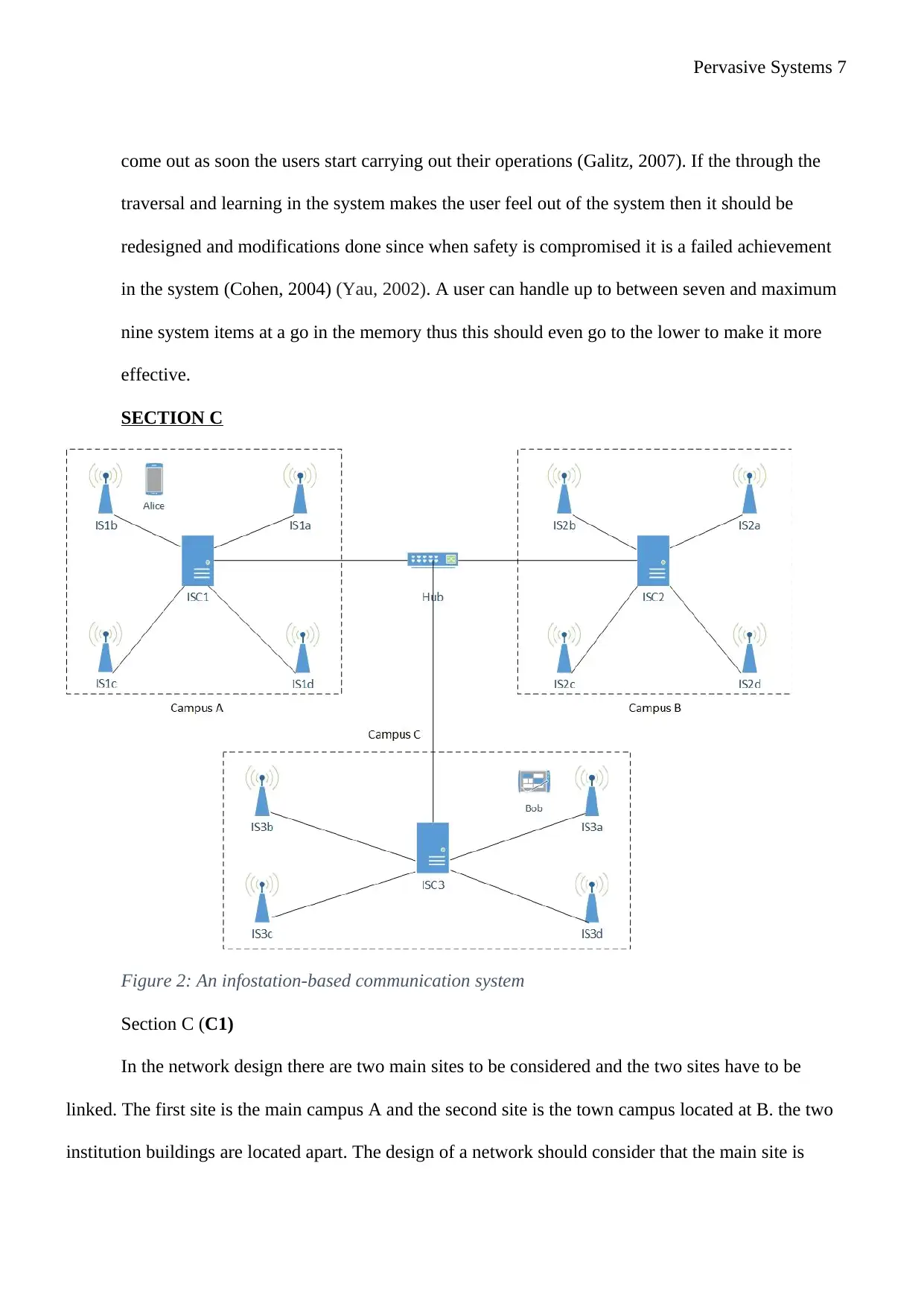
SECTION C
Figure 2: An infostation-based communication system
Section C (C1)
In the network design there are two main sites to be considered and the two sites have to be
linked. The first site is the main campus A and the second site is the town campus located at B. the two
institution buildings are located apart. The design of a network should consider that the main site is
come out as soon the users start carrying out their operations (Galitz, 2007). If the through the
traversal and learning in the system makes the user feel out of the system then it should be
redesigned and modifications done since when safety is compromised it is a failed achievement
in the system (Cohen, 2004) (Yau, 2002). A user can handle up to between seven and maximum
nine system items at a go in the memory thus this should even go to the lower to make it more
effective.
SECTION C
Figure 2: An infostation-based communication system
Section C (C1)
In the network design there are two main sites to be considered and the two sites have to be
linked. The first site is the main campus A and the second site is the town campus located at B. the two
institution buildings are located apart. The design of a network should consider that the main site is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Pervasive Systems 8
where the main network infrastructure is located. Operations and data retrieval is done from the main
campus and in campus be gets a replica (McCullough, 2004).
Section C (C2)
The choice of link in this case should be clearly looked into to avoid a situation where the
distance and data transfer rate are not put into consideration. The most two network set up to connect
over 4km apart system include wireless bridge and long-range wireless bridge wireless technologies
(Beresford and Stajano, 2003). These two network setups are found favorites due to the services they
offer when connecting wireless networks (Sun, 2001).
Section C (C3)
OPNET simulation tool was used to determine the most appropriate network for this network
infrastructure connecting two sites 4 km apart. After the analysis of wireless bridge against long-range
wireless bridge, wireless bridge was found more appropriate (Saha and Mukherjee, 2003). Wireless
bridge connects up to 4.8km (3 miles) apart from each other with variations happening due to
geographic and atmospheric conditions. It utilizes spread-spectrum radio technology in the creation of a
wireless backbone which ties locations together despite the distances and thus connecting the LANs
where the main network infrastructure is located. Operations and data retrieval is done from the main
campus and in campus be gets a replica (McCullough, 2004).
Section C (C2)
The choice of link in this case should be clearly looked into to avoid a situation where the
distance and data transfer rate are not put into consideration. The most two network set up to connect
over 4km apart system include wireless bridge and long-range wireless bridge wireless technologies
(Beresford and Stajano, 2003). These two network setups are found favorites due to the services they
offer when connecting wireless networks (Sun, 2001).
Section C (C3)
OPNET simulation tool was used to determine the most appropriate network for this network
infrastructure connecting two sites 4 km apart. After the analysis of wireless bridge against long-range
wireless bridge, wireless bridge was found more appropriate (Saha and Mukherjee, 2003). Wireless
bridge connects up to 4.8km (3 miles) apart from each other with variations happening due to
geographic and atmospheric conditions. It utilizes spread-spectrum radio technology in the creation of a
wireless backbone which ties locations together despite the distances and thus connecting the LANs
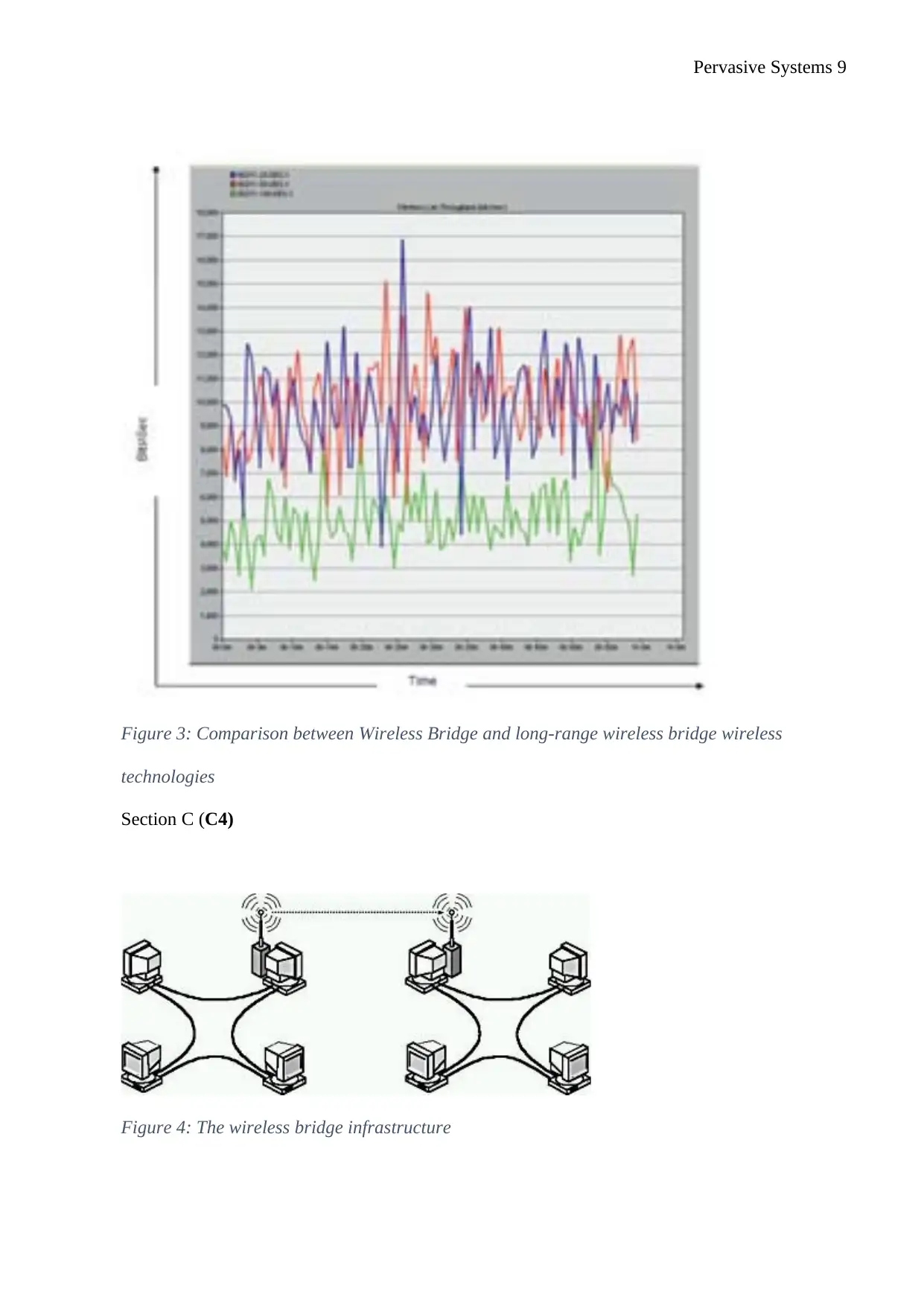
Pervasive Systems 9
Figure 3: Comparison between Wireless Bridge and long-range wireless bridge wireless
technologies
Section C (C4)
Figure 4: The wireless bridge infrastructure
Figure 3: Comparison between Wireless Bridge and long-range wireless bridge wireless
technologies
Section C (C4)
Figure 4: The wireless bridge infrastructure
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
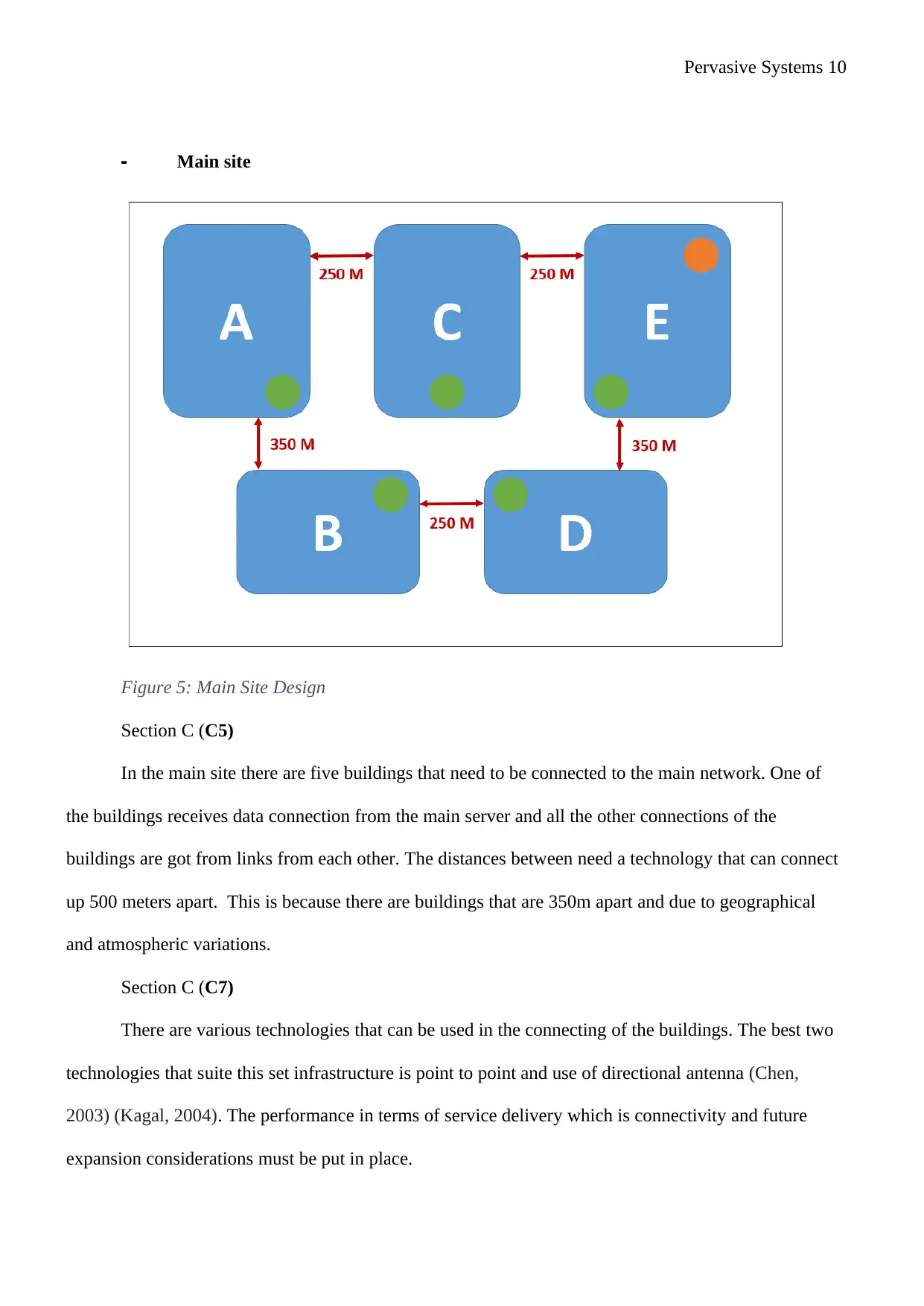
Pervasive Systems 10
- Main site
Figure 5: Main Site Design
Section C (C5)
In the main site there are five buildings that need to be connected to the main network. One of
the buildings receives data connection from the main server and all the other connections of the
buildings are got from links from each other. The distances between need a technology that can connect
up 500 meters apart. This is because there are buildings that are 350m apart and due to geographical
and atmospheric variations.
Section C (C7)
There are various technologies that can be used in the connecting of the buildings. The best two
technologies that suite this set infrastructure is point to point and use of directional antenna (Chen,
2003) (Kagal, 2004). The performance in terms of service delivery which is connectivity and future
expansion considerations must be put in place.
- Main site
Figure 5: Main Site Design
Section C (C5)
In the main site there are five buildings that need to be connected to the main network. One of
the buildings receives data connection from the main server and all the other connections of the
buildings are got from links from each other. The distances between need a technology that can connect
up 500 meters apart. This is because there are buildings that are 350m apart and due to geographical
and atmospheric variations.
Section C (C7)
There are various technologies that can be used in the connecting of the buildings. The best two
technologies that suite this set infrastructure is point to point and use of directional antenna (Chen,
2003) (Kagal, 2004). The performance in terms of service delivery which is connectivity and future
expansion considerations must be put in place.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
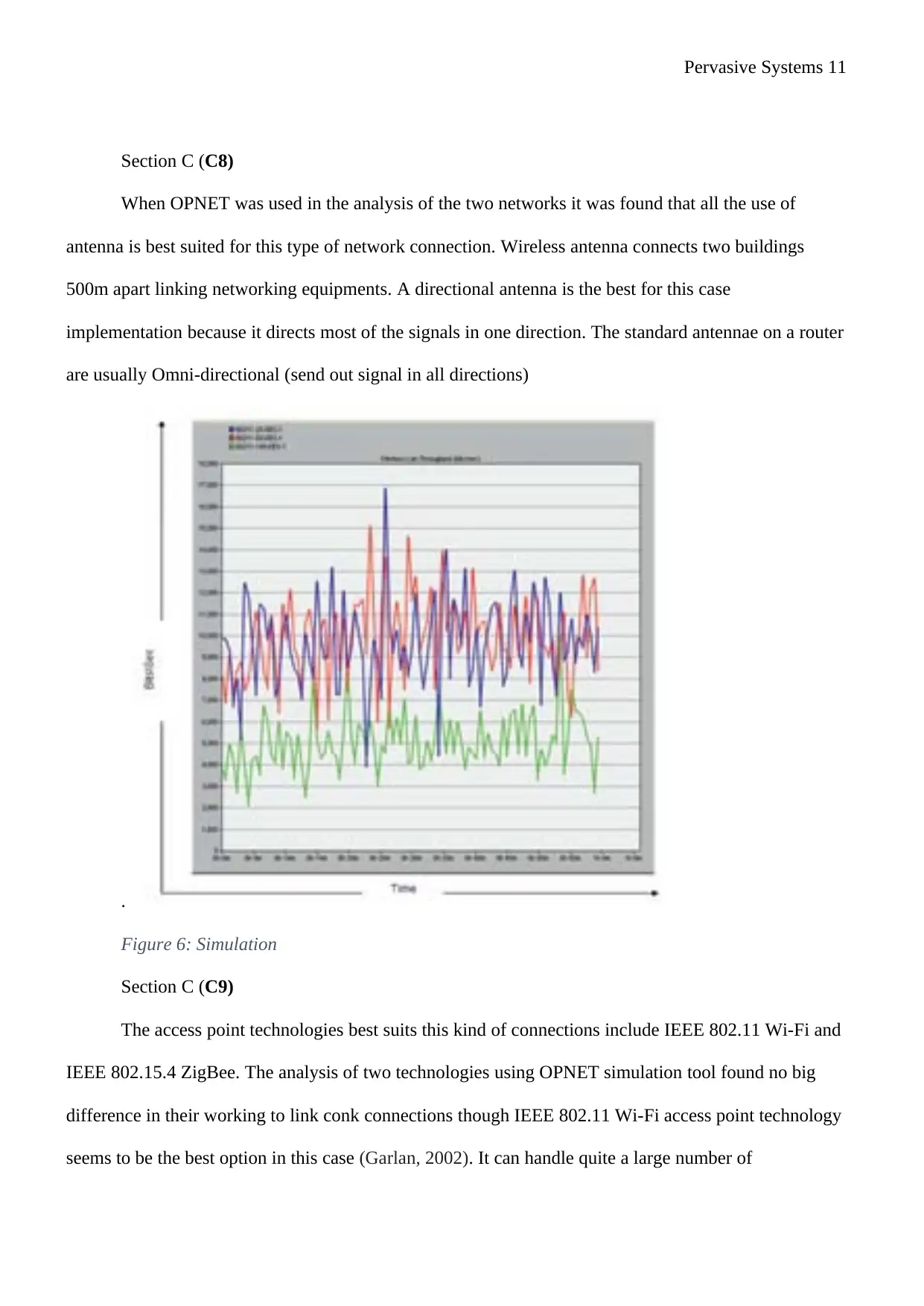
Pervasive Systems 11
Section C (C8)
When OPNET was used in the analysis of the two networks it was found that all the use of
antenna is best suited for this type of network connection. Wireless antenna connects two buildings
500m apart linking networking equipments. A directional antenna is the best for this case
implementation because it directs most of the signals in one direction. The standard antennae on a router
are usually Omni-directional (send out signal in all directions)
.
Figure 6: Simulation
Section C (C9)
The access point technologies best suits this kind of connections include IEEE 802.11 Wi-Fi and
IEEE 802.15.4 ZigBee. The analysis of two technologies using OPNET simulation tool found no big
difference in their working to link conk connections though IEEE 802.11 Wi-Fi access point technology
seems to be the best option in this case (Garlan, 2002). It can handle quite a large number of
Section C (C8)
When OPNET was used in the analysis of the two networks it was found that all the use of
antenna is best suited for this type of network connection. Wireless antenna connects two buildings
500m apart linking networking equipments. A directional antenna is the best for this case
implementation because it directs most of the signals in one direction. The standard antennae on a router
are usually Omni-directional (send out signal in all directions)
.
Figure 6: Simulation
Section C (C9)
The access point technologies best suits this kind of connections include IEEE 802.11 Wi-Fi and
IEEE 802.15.4 ZigBee. The analysis of two technologies using OPNET simulation tool found no big
difference in their working to link conk connections though IEEE 802.11 Wi-Fi access point technology
seems to be the best option in this case (Garlan, 2002). It can handle quite a large number of
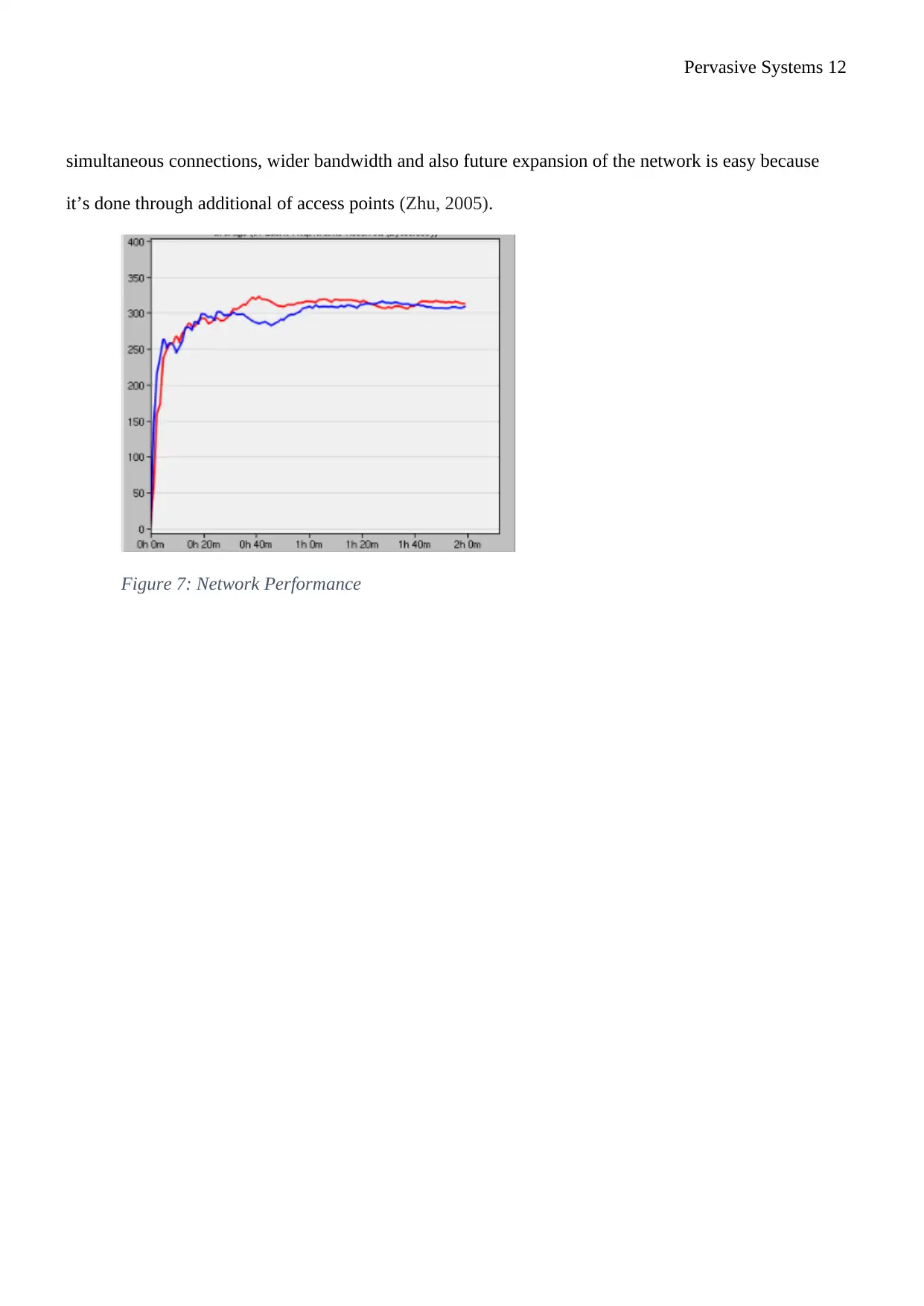
Pervasive Systems 12
simultaneous connections, wider bandwidth and also future expansion of the network is easy because
it’s done through additional of access points (Zhu, 2005).
Figure 7: Network Performance
simultaneous connections, wider bandwidth and also future expansion of the network is easy because
it’s done through additional of access points (Zhu, 2005).
Figure 7: Network Performance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





