ITSA2005 Project: Planning and Implementing a Server Solution
VerifiedAdded on 2023/03/31
|12
|2556
|99
Report
AI Summary
This project report details the planning and implementation of a server solution, focusing on automation strategies for companies like Adatum and Contoso. The report covers the design and deployment of a network infrastructure, emphasizing the importance of synchronized application services and centralized server management for improved performance and data accessibility. It outlines hardware and software requirements, proposes a solution for automating server installation, and discusses considerations for domain controller configuration and data collection optimization. The report concludes by highlighting the crucial role of strategic planning and quality hardware/software in ensuring a secure and efficient server implementation.

Planning and Implementing Server 1
PLANNING AND IMPLEMENTING SERVER
Affiliate Information
PLANNING AND IMPLEMENTING SERVER
Affiliate Information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Planning and Implementing Server 2
Executive Summary
Technological advancements provide new techniques that can be used for processes such as
automation. Improvements and the paradigms in which these technologies operate is dependent on the
methodologies that each of the technology follows during its implementation.
An automation strategy is a process that involves the creation of a self-managing system that can be
used in the process of management, monitoring, and analysis. The design and deployment of a network
is a procedure that involves configuration and assessment of the network model.
The assessment of a server is based on several processes that it can accomplish when subjected to a
given task. The process of implementation starts with the planning phase, where the design is laid out
and all the requirements required for the application of the product are determined.
After meeting the criterion for the design and planning, the product is then developed using the
available resource taking care of the objectives and the final product. The installation of the server
products is done in a secure place free from interruptions. Each of the application service product needs
to remain in synch with the data node to ensure concurrency of the data collected by the server from the
nodes. The server is centralized to improve the performance and the speed with which data is available
to each of the node.
Executive Summary
Technological advancements provide new techniques that can be used for processes such as
automation. Improvements and the paradigms in which these technologies operate is dependent on the
methodologies that each of the technology follows during its implementation.
An automation strategy is a process that involves the creation of a self-managing system that can be
used in the process of management, monitoring, and analysis. The design and deployment of a network
is a procedure that involves configuration and assessment of the network model.
The assessment of a server is based on several processes that it can accomplish when subjected to a
given task. The process of implementation starts with the planning phase, where the design is laid out
and all the requirements required for the application of the product are determined.
After meeting the criterion for the design and planning, the product is then developed using the
available resource taking care of the objectives and the final product. The installation of the server
products is done in a secure place free from interruptions. Each of the application service product needs
to remain in synch with the data node to ensure concurrency of the data collected by the server from the
nodes. The server is centralized to improve the performance and the speed with which data is available
to each of the node.

Planning and Implementing Server 3
Contents
Introduction..............................................................................................................................................4
Design and Implementation................................................................................................................4
Project Scope........................................................................................................................................5
Requirements for the project..................................................................................................................6
Hardware Requirements.....................................................................................................................6
The proposed solution to the project......................................................................................................7
Conclusion................................................................................................................................................8
Recommendation......................................................................................................................................9
References...............................................................................................................................................11
APPENDIX.............................................................................................................................................12
Contents
Introduction..............................................................................................................................................4
Design and Implementation................................................................................................................4
Project Scope........................................................................................................................................5
Requirements for the project..................................................................................................................6
Hardware Requirements.....................................................................................................................6
The proposed solution to the project......................................................................................................7
Conclusion................................................................................................................................................8
Recommendation......................................................................................................................................9
References...............................................................................................................................................11
APPENDIX.............................................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Planning and Implementing Server 4
Introduction
Advancement in the networking field has led to the increased deployment of servers and server-based
application from homes to offices. This proposal focuses on the implementation of an automated
installation strategy for a server. The solution implemented in this proposal is based on developing
hundreds of servers.
The network infrastructure will serve as the basis for the emergence of new technology for the Contoso
corporation. The foundation is designed to follow the guidelines and the methodologies of the Top-
Down design paradigms which include: Analyzing the requirements, Development of a logical plan,
testing and monitoring the performance.
Design and Implementation
The corporation has two companies, the Adatum company, and Contoso itself. An automation strategy
is to be developed for both of the companies to automate the processes of installation. The process of
installation of new hundreds of servers is a redundant task which needs some automation. The
corporation suggests a new product which is supposed to ease the process. The product to be
developed must be synchronized with the server's, which is the central system for collecting and
analyzing the data from the wireless nodes. Some of the application services used by the corporation
include the Microsoft and SQL server services which are incorporated into the first services at the
headquarters.
The server for collection and recording of the data from the nodes remains in sync with the windows
internal database, which can be used as a reference for the collected data from the nodes. The interior
windows server can also be used as a backup in case of the failure in the operation of the server.
The product developed must remain in sync with the primary application services, including the
servers to improve the efficiency and the operation of the cooperation in its services. The quality
control team is charged with the mandate to access and test the products developed. After testing by the
quality control team, the next step involves shipping the product to the customers.
Introduction
Advancement in the networking field has led to the increased deployment of servers and server-based
application from homes to offices. This proposal focuses on the implementation of an automated
installation strategy for a server. The solution implemented in this proposal is based on developing
hundreds of servers.
The network infrastructure will serve as the basis for the emergence of new technology for the Contoso
corporation. The foundation is designed to follow the guidelines and the methodologies of the Top-
Down design paradigms which include: Analyzing the requirements, Development of a logical plan,
testing and monitoring the performance.
Design and Implementation
The corporation has two companies, the Adatum company, and Contoso itself. An automation strategy
is to be developed for both of the companies to automate the processes of installation. The process of
installation of new hundreds of servers is a redundant task which needs some automation. The
corporation suggests a new product which is supposed to ease the process. The product to be
developed must be synchronized with the server's, which is the central system for collecting and
analyzing the data from the wireless nodes. Some of the application services used by the corporation
include the Microsoft and SQL server services which are incorporated into the first services at the
headquarters.
The server for collection and recording of the data from the nodes remains in sync with the windows
internal database, which can be used as a reference for the collected data from the nodes. The interior
windows server can also be used as a backup in case of the failure in the operation of the server.
The product developed must remain in sync with the primary application services, including the
servers to improve the efficiency and the operation of the cooperation in its services. The quality
control team is charged with the mandate to access and test the products developed. After testing by the
quality control team, the next step involves shipping the product to the customers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Planning and Implementing Server 5
The application services for the network at Adatum needs to be redesigned. The domain controller is a
computer-based application that is used to authenticate users to a service using a combination of a
username and a password. The controller can respond to the authentication requests within the domain.
A domain is a concept that allows a user to be granted access to several services If the provided
credentials to that service are correct. In case of the failure of the domain, a backup domain takes
control of the operations.
Daily activity is accomplished through automation of simple tasks. However, the misuse of these
technologies reduces the ability of the devices to work efficiently and effectively. This project focuses
on the importance and implementation of a flexible design that can adapt to changes in pattern and
incorporate new design patterns.
The new infrastructure is implemented to improve efficiency to the numerous services such as users’
connectivity within a range of limited resources. Configuration and deployment of the network
resources are dependent on the traffic of the number of users that are accessing the resources at a given
instance.
Project Scope
This project aims to develop an automation installation system that can be used for monitoring home
security and medical types of equipment. It also focuses on the configuration and the deployment of a
network infrastructure. Due to the fact, there have been new improvements in the areas of technology,
and the architectural redesign is a crucial aspect to consider.
The product that is considered in the design is centered around a server. The purpose of the product is
the monitoring and assessment of the home and hospital equipment. Wireless nodes are situated at
different sections within the area where the server is located. The functions of the server include:
Collection of data from the wireless nodes.
Analysis of the collected data.
Storage of collected and analyzed data.
The application services for the network at Adatum needs to be redesigned. The domain controller is a
computer-based application that is used to authenticate users to a service using a combination of a
username and a password. The controller can respond to the authentication requests within the domain.
A domain is a concept that allows a user to be granted access to several services If the provided
credentials to that service are correct. In case of the failure of the domain, a backup domain takes
control of the operations.
Daily activity is accomplished through automation of simple tasks. However, the misuse of these
technologies reduces the ability of the devices to work efficiently and effectively. This project focuses
on the importance and implementation of a flexible design that can adapt to changes in pattern and
incorporate new design patterns.
The new infrastructure is implemented to improve efficiency to the numerous services such as users’
connectivity within a range of limited resources. Configuration and deployment of the network
resources are dependent on the traffic of the number of users that are accessing the resources at a given
instance.
Project Scope
This project aims to develop an automation installation system that can be used for monitoring home
security and medical types of equipment. It also focuses on the configuration and the deployment of a
network infrastructure. Due to the fact, there have been new improvements in the areas of technology,
and the architectural redesign is a crucial aspect to consider.
The product that is considered in the design is centered around a server. The purpose of the product is
the monitoring and assessment of the home and hospital equipment. Wireless nodes are situated at
different sections within the area where the server is located. The functions of the server include:
Collection of data from the wireless nodes.
Analysis of the collected data.
Storage of collected and analyzed data.

Planning and Implementing Server 6
The server also keeps track of the data using the assistance of the Windows internal database, which is
a relational database that is used to keep track and maintain information that is relayed to it. The
process involves testing of the new products developed before they are shipped. The quality of the
products is determined during the process of testing. Before the new products can be sent to the
customers, the products are tested and configured for the new users.
Implementation of new servers is done frequently, and this means that the solution needs to meet the
evolving requirements and updates. The server needs to be configured in such a way that the process of
upgrading is automatic, this ensures that the servers are up to date with the new security features and
the current trends in technological advancements.
Roll outs of new servers is done to replace the old inventories of the old ones. Backup copies of the old
servers are maintained (Ducatelle, Di Caro and Gambardella, 2010).
Requirements for the project.
Implementation of the project requires both hardware and software products. The number of products is
dependent on the architecture and size of the product that is being developed, hardware requirements
are the physical devices that are used to build the network while software requirement is products that
are used to control the operation of the product.
Subsequent upgrade of a network design involves the update from the previous one.
Hardware Requirements
The hardware requirements for the node servers includes the following. Hardware requirements are part
of implementing a secure proper infrastructure. The physical strength of the product in Development is
dependent on the continued improvement of the hardware features.
The cost of the requirements has a direct impact in the Development of the product, the aim is
sometimes to reduce the cost of production and at the same time, produce a quality product that has
improved performance. All these factors need to be considered in the first phase of the design strategy
to ensure a progressive move in the development phase.
Management node Conference Node
The server also keeps track of the data using the assistance of the Windows internal database, which is
a relational database that is used to keep track and maintain information that is relayed to it. The
process involves testing of the new products developed before they are shipped. The quality of the
products is determined during the process of testing. Before the new products can be sent to the
customers, the products are tested and configured for the new users.
Implementation of new servers is done frequently, and this means that the solution needs to meet the
evolving requirements and updates. The server needs to be configured in such a way that the process of
upgrading is automatic, this ensures that the servers are up to date with the new security features and
the current trends in technological advancements.
Roll outs of new servers is done to replace the old inventories of the old ones. Backup copies of the old
servers are maintained (Ducatelle, Di Caro and Gambardella, 2010).
Requirements for the project.
Implementation of the project requires both hardware and software products. The number of products is
dependent on the architecture and size of the product that is being developed, hardware requirements
are the physical devices that are used to build the network while software requirement is products that
are used to control the operation of the product.
Subsequent upgrade of a network design involves the update from the previous one.
Hardware Requirements
The hardware requirements for the node servers includes the following. Hardware requirements are part
of implementing a secure proper infrastructure. The physical strength of the product in Development is
dependent on the continued improvement of the hardware features.
The cost of the requirements has a direct impact in the Development of the product, the aim is
sometimes to reduce the cost of production and at the same time, produce a quality product that has
improved performance. All these factors need to be considered in the first phase of the design strategy
to ensure a progressive move in the development phase.
Management node Conference Node
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
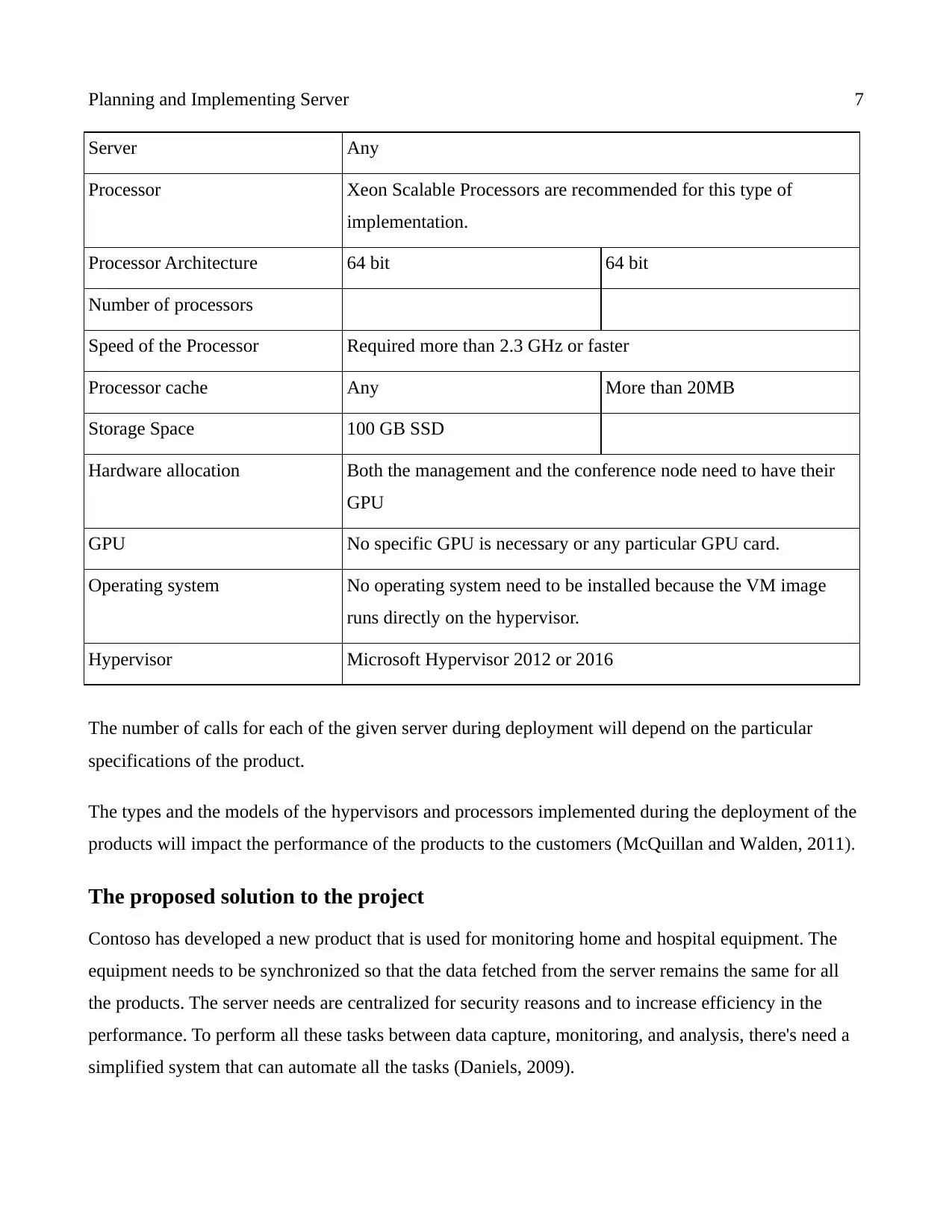
Planning and Implementing Server 7
Server Any
Processor Xeon Scalable Processors are recommended for this type of
implementation.
Processor Architecture 64 bit 64 bit
Number of processors
Speed of the Processor Required more than 2.3 GHz or faster
Processor cache Any More than 20MB
Storage Space 100 GB SSD
Hardware allocation Both the management and the conference node need to have their
GPU
GPU No specific GPU is necessary or any particular GPU card.
Operating system No operating system need to be installed because the VM image
runs directly on the hypervisor.
Hypervisor Microsoft Hypervisor 2012 or 2016
The number of calls for each of the given server during deployment will depend on the particular
specifications of the product.
The types and the models of the hypervisors and processors implemented during the deployment of the
products will impact the performance of the products to the customers (McQuillan and Walden, 2011).
The proposed solution to the project
Contoso has developed a new product that is used for monitoring home and hospital equipment. The
equipment needs to be synchronized so that the data fetched from the server remains the same for all
the products. The server needs are centralized for security reasons and to increase efficiency in the
performance. To perform all these tasks between data capture, monitoring, and analysis, there's need a
simplified system that can automate all the tasks (Daniels, 2009).
Server Any
Processor Xeon Scalable Processors are recommended for this type of
implementation.
Processor Architecture 64 bit 64 bit
Number of processors
Speed of the Processor Required more than 2.3 GHz or faster
Processor cache Any More than 20MB
Storage Space 100 GB SSD
Hardware allocation Both the management and the conference node need to have their
GPU
GPU No specific GPU is necessary or any particular GPU card.
Operating system No operating system need to be installed because the VM image
runs directly on the hypervisor.
Hypervisor Microsoft Hypervisor 2012 or 2016
The number of calls for each of the given server during deployment will depend on the particular
specifications of the product.
The types and the models of the hypervisors and processors implemented during the deployment of the
products will impact the performance of the products to the customers (McQuillan and Walden, 2011).
The proposed solution to the project
Contoso has developed a new product that is used for monitoring home and hospital equipment. The
equipment needs to be synchronized so that the data fetched from the server remains the same for all
the products. The server needs are centralized for security reasons and to increase efficiency in the
performance. To perform all these tasks between data capture, monitoring, and analysis, there's need a
simplified system that can automate all the tasks (Daniels, 2009).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Planning and Implementing Server 8
The solution to this problem involves the creation of a single automated system since the installation of
new servers is a cumbersome and intermittent task which automates the process of installation needs to
be automated.
The suggestion to the problem of installation is a new system that can be able to automate the process
of installation. The original product is configured and implemented as follows:
The server can monitor the performance of other products since they are synchronized together. During
each of the installation, the product has a record of the properties of the number of servers that need be
implemented. The process is done repetitively until all the amount of servers are achieved.
Due to the nature of the domain controller, the best practices dictates that the purposes of the controller
should be dedicated only to the domain services. The domain should not be used for purposes such as
file sharing or printer services. Additional services other than the domain can slow or crash the system.
Once a user is authenticated to the domain, all the updates should be done using the primary controller,
which can then propagate these changes to the domain.
If the primary domain controller is not available, the update to the domain results to failure, it is,
therefore, recommend to configure a domain controller which can be used for backup in case the
primary controller is not available. The backup domain controller can be used for carrying out the
updates is the primary domain is not available (Jajszczyk, 2015).
To improve the speed with which the data is collected and analyzed using the server, the server needs to
be positioned in a strategic place that is central to the nodes and the other application services. All the
services need to be in synchronization and working together to improve the speed with which the data
is transmitted from the nodes to the central server.
Conclusion
In conclusion, the overall design and implementation of a system is the most crucial aspect to consider
before the initial build of the product. The architectural design of a product is dependent on the strategy
used for its planning. The efficiency and performance of the product can also be determined by the
quality of the hardware and software requirements used.
The solution to this problem involves the creation of a single automated system since the installation of
new servers is a cumbersome and intermittent task which automates the process of installation needs to
be automated.
The suggestion to the problem of installation is a new system that can be able to automate the process
of installation. The original product is configured and implemented as follows:
The server can monitor the performance of other products since they are synchronized together. During
each of the installation, the product has a record of the properties of the number of servers that need be
implemented. The process is done repetitively until all the amount of servers are achieved.
Due to the nature of the domain controller, the best practices dictates that the purposes of the controller
should be dedicated only to the domain services. The domain should not be used for purposes such as
file sharing or printer services. Additional services other than the domain can slow or crash the system.
Once a user is authenticated to the domain, all the updates should be done using the primary controller,
which can then propagate these changes to the domain.
If the primary domain controller is not available, the update to the domain results to failure, it is,
therefore, recommend to configure a domain controller which can be used for backup in case the
primary controller is not available. The backup domain controller can be used for carrying out the
updates is the primary domain is not available (Jajszczyk, 2015).
To improve the speed with which the data is collected and analyzed using the server, the server needs to
be positioned in a strategic place that is central to the nodes and the other application services. All the
services need to be in synchronization and working together to improve the speed with which the data
is transmitted from the nodes to the central server.
Conclusion
In conclusion, the overall design and implementation of a system is the most crucial aspect to consider
before the initial build of the product. The architectural design of a product is dependent on the strategy
used for its planning. The efficiency and performance of the product can also be determined by the
quality of the hardware and software requirements used.

Planning and Implementing Server 9
To completely secure a product from malicious use, the product needs to be designed to fit the
customers need. With the increased use of the application services, the products need to be
synchronized and linked with the services to enable them to improve their operations effectively. The
implementation of a product takes into account, the features that need be developed of the product and
the cost incurred for the product.
It is essential to lay out all the required procedures, and design layouts before the final product can be
developed and shipped. This feature ensures that the progressive Development of the product is faster
and meets the required criteria. Previous design models should be analyzed, and suggestions made for
the next design should emanate from the recommended procedures and guidelines of the prior design.
Recommendation
The redesign and implementation of a new network design require knowledge of how the previous one
operated and its challenges. Each of the consecutive design strategies is an implementation and a
redesign of the last product.
The process of restructuring the design ensures improved performance of the consecutive models. The
implementation of a secure domain controller can be based on the number of users with access to the
domain at the same time. Users not authenticated to the domain service should be blocked to prevent
malicious intent.
Security of a product is dependent on the design and the theory behind the model of the plan. A good
design can be thought as one that is flexible, adaptable to change, and rapid to change in the evolving
technological advancements.
Security patches applied to the new architectural design should be done automatically using the
automated system. Each of the progress patches should be a development of the previous security
fixture of the system.
Limiting the number of users with access to the domain controller improves its security features since
multiple users cannot be able to access the same control at the same time. This feature prevents users
from sending streams of data at the same time into the domain controllers, which might crush them.
To completely secure a product from malicious use, the product needs to be designed to fit the
customers need. With the increased use of the application services, the products need to be
synchronized and linked with the services to enable them to improve their operations effectively. The
implementation of a product takes into account, the features that need be developed of the product and
the cost incurred for the product.
It is essential to lay out all the required procedures, and design layouts before the final product can be
developed and shipped. This feature ensures that the progressive Development of the product is faster
and meets the required criteria. Previous design models should be analyzed, and suggestions made for
the next design should emanate from the recommended procedures and guidelines of the prior design.
Recommendation
The redesign and implementation of a new network design require knowledge of how the previous one
operated and its challenges. Each of the consecutive design strategies is an implementation and a
redesign of the last product.
The process of restructuring the design ensures improved performance of the consecutive models. The
implementation of a secure domain controller can be based on the number of users with access to the
domain at the same time. Users not authenticated to the domain service should be blocked to prevent
malicious intent.
Security of a product is dependent on the design and the theory behind the model of the plan. A good
design can be thought as one that is flexible, adaptable to change, and rapid to change in the evolving
technological advancements.
Security patches applied to the new architectural design should be done automatically using the
automated system. Each of the progress patches should be a development of the previous security
fixture of the system.
Limiting the number of users with access to the domain controller improves its security features since
multiple users cannot be able to access the same control at the same time. This feature prevents users
from sending streams of data at the same time into the domain controllers, which might crush them.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Planning and Implementing Server 10
To ensure progressive installation for each of the continuous processes, the logs for the previous
installation need to be captured and analyzed to check for anomalies and failure in the installation
process. The operation of the progressive systems needs to be an advanced mechanism procedure from
the previous installations.
The paradigms followed in the design should be architecturally based and follow the top-down design
strategy which is based on the map, implementation, testing, and verification of the developed product
to ensure that the product meets the criteria needed for use by the end customers.
The cost for the products need be determined before the products can be designed, this is to ensure
improved features of the current product, this aspect is used to improve the quality of products that are
being developed.
To ensure progressive installation for each of the continuous processes, the logs for the previous
installation need to be captured and analyzed to check for anomalies and failure in the installation
process. The operation of the progressive systems needs to be an advanced mechanism procedure from
the previous installations.
The paradigms followed in the design should be architecturally based and follow the top-down design
strategy which is based on the map, implementation, testing, and verification of the developed product
to ensure that the product meets the criteria needed for use by the end customers.
The cost for the products need be determined before the products can be designed, this is to ensure
improved features of the current product, this aspect is used to improve the quality of products that are
being developed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Planning and Implementing Server 11
References
Daniels, J., 2009. Server virtualization architecture and implementation.XRDS: Crossroads, The ACM
Magazine for Students,16(1), 8-12.
Ducatelle, F., Di Caro, G.A. and Gambardella, L.M., 2010. Principles and applications of swarm
intelligence for adaptive routing in telecommunications networks. Swarm Intelligence, 4(3), pp.173-
198.
Jajszczyk, A., 2015. Routing, Flow, and Capacity Design in Communication and Computer Networks-
[Book Review]. IEEE Communications Magazine, 43(5), pp.26-26.
McQuillan, J.M. and Walden, D.C., 2011. The ARPA network design decisions. Computer Networks
(1976), 1(5), pp.243-289.
References
Daniels, J., 2009. Server virtualization architecture and implementation.XRDS: Crossroads, The ACM
Magazine for Students,16(1), 8-12.
Ducatelle, F., Di Caro, G.A. and Gambardella, L.M., 2010. Principles and applications of swarm
intelligence for adaptive routing in telecommunications networks. Swarm Intelligence, 4(3), pp.173-
198.
Jajszczyk, A., 2015. Routing, Flow, and Capacity Design in Communication and Computer Networks-
[Book Review]. IEEE Communications Magazine, 43(5), pp.26-26.
McQuillan, J.M. and Walden, D.C., 2011. The ARPA network design decisions. Computer Networks
(1976), 1(5), pp.243-289.

Planning and Implementing Server 12
APPENDIX
Concept of operation
Design and implementation of the proposed system should be done by teams with the expertise of the
specific area. The testing team is involved in automated product testing and approval of the product.
New System Description
Implementation of new systems can involve Development of both interfaces the command line tools
that can be used in accessing the system functionality.
Gaining access to the central server and other application services can use administrator commands to
successively run and carry out the proper security patches and audits.
APPENDIX
Concept of operation
Design and implementation of the proposed system should be done by teams with the expertise of the
specific area. The testing team is involved in automated product testing and approval of the product.
New System Description
Implementation of new systems can involve Development of both interfaces the command line tools
that can be used in accessing the system functionality.
Gaining access to the central server and other application services can use administrator commands to
successively run and carry out the proper security patches and audits.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


