Power AI ICT Security: Management Program Development Report
VerifiedAdded on 2023/04/04
|10
|1280
|151
Report
AI Summary
This report outlines the development of an ICT security program for Power AI, a company specializing in AI systems for power management. It addresses the critical need to protect Power AI's intellectual property, particularly source codes and documentation, within their private onsite network. The report details the benefits of a robust security management plan, including data protection, cyber-attack resilience, and cost reduction. It proposes a security policy based on risk assessment findings, emphasizing controlled access to critical information and regular security updates. Key roles and responsibilities, such as the Chief Information Officer and Information Security Officer, are defined. The report also incorporates state machine models and the Bell-LaPadula Model for security implementation. A risk management plan is presented, focusing on risk identification, mitigation strategies, and a risk register. Finally, it touches upon the cost-benefit analysis of implementing the security measures.

Running head: INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT AND GOVERNANCE 1
Executive summary:
The purpose of this paper is to develop an ICT security program for Power AI. Power AI is
an organization that creates and develops software for the IT related industry, home and
business use. The focus of power AI is on developing of AI systems for controlling power
use. This report will discuss the requirements and the needs for implementing an ICT security
program for the Power AI. This paper will also provide a risk management plan and cost
benefit analysis according to the requirements.
Executive summary:
The purpose of this paper is to develop an ICT security program for Power AI. Power AI is
an organization that creates and develops software for the IT related industry, home and
business use. The focus of power AI is on developing of AI systems for controlling power
use. This report will discuss the requirements and the needs for implementing an ICT security
program for the Power AI. This paper will also provide a risk management plan and cost
benefit analysis according to the requirements.

2INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
Table of Contents
Introduction:...............................................................................................................................4
Benefits of security management plan:......................................................................................4
Development of security policy and security management plan:..............................................5
Roles and responsibilities:..........................................................................................................5
Models and methods:.................................................................................................................6
Statutory requirements:..............................................................................................................6
Risk assessment:.........................................................................................................................6
Table of Contents
Introduction:...............................................................................................................................4
Benefits of security management plan:......................................................................................4
Development of security policy and security management plan:..............................................5
Roles and responsibilities:..........................................................................................................5
Models and methods:.................................................................................................................6
Statutory requirements:..............................................................................................................6
Risk assessment:.........................................................................................................................6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
Introduction:
Power AI is an organization that is privately owned, situated in Preston as well as it is
having a total number of 50 employees. Among them 25 of the employees are involved
directly in the development, design, implementing and testing the products. The major
security concerns with Power AI is with the intellectual property (Alnatheer, 2014). At
present, the company is working within a private onsite network. The illegal or loss of the
source codes and the documentations that are associated can be a significant blow for the
PAI. The purpose of this paper is to develop an ICT security program for Power AI. The
focus of power AI is on developing of AI systems for controlling power use (Fischhoff,
2015). This report will discuss the requirements and the needs for implementing an ICT
security program for the Power AI as well as will also provide a risk management plan and
cost benefit analysis according to the requirements.
Benefits of security management plan:
The major advantages that can be gained from the security management plan are as
follows:
It secures the data and information in all of the forms of it and helps to protect all of the data
and information that includes paper based, digital, intellectual property, secrets of the
company, cloud device security devices (Lu et al., 2013).
The security management increases the resilience of the cyber-attacks.
Offers wide protection to the organisation.
The security management plan also helps in responds to the security related threats
that are evolving.
It also decreases the costs that are related to IT.
Introduction:
Power AI is an organization that is privately owned, situated in Preston as well as it is
having a total number of 50 employees. Among them 25 of the employees are involved
directly in the development, design, implementing and testing the products. The major
security concerns with Power AI is with the intellectual property (Alnatheer, 2014). At
present, the company is working within a private onsite network. The illegal or loss of the
source codes and the documentations that are associated can be a significant blow for the
PAI. The purpose of this paper is to develop an ICT security program for Power AI. The
focus of power AI is on developing of AI systems for controlling power use (Fischhoff,
2015). This report will discuss the requirements and the needs for implementing an ICT
security program for the Power AI as well as will also provide a risk management plan and
cost benefit analysis according to the requirements.
Benefits of security management plan:
The major advantages that can be gained from the security management plan are as
follows:
It secures the data and information in all of the forms of it and helps to protect all of the data
and information that includes paper based, digital, intellectual property, secrets of the
company, cloud device security devices (Lu et al., 2013).
The security management increases the resilience of the cyber-attacks.
Offers wide protection to the organisation.
The security management plan also helps in responds to the security related threats
that are evolving.
It also decreases the costs that are related to IT.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
The plan provides protection towards confidentiality, availability as well as the
integrity of the information and data.
Development of security policy and security management plan:
The security policy have to be on the basis of the results of the risk assessment. The
findings that will be gained from the risk assessment will provide the creators of the policy
with the picture that is accurate for the requirement of the security (Marcelino et al., 2014).
The security policy for the Power AI will be as follows:
Overall approach: Most of the people requires to gain access to most of the information.
(Relaxed)
Critical information: Especial pricing as well as contracts, payroll (only the accountant will
be able to set and alter the limit of the credits for the customers), inventory and customer
records.
General rules: Each of the client will be having an individual user profile; the users have to
change the passcodes in every 60 days as well as the users have to utilize the recent security
patches.
For the protection for an organisation by a nicely planned security management. The
most important enabler requires recognition as one of the most important component of the
company. The efficient and effective security program needs co-operation from the leaders of
the business as well as the personnel who are within the organisation (Skopik, Settanni and
Fiedler, 2016). Cyber security and Information assurance are the function that are integrated
which needs the effective collaboration that will be throughput the entire organisation.
Roles and responsibilities:
Chief Information officer:
The plan provides protection towards confidentiality, availability as well as the
integrity of the information and data.
Development of security policy and security management plan:
The security policy have to be on the basis of the results of the risk assessment. The
findings that will be gained from the risk assessment will provide the creators of the policy
with the picture that is accurate for the requirement of the security (Marcelino et al., 2014).
The security policy for the Power AI will be as follows:
Overall approach: Most of the people requires to gain access to most of the information.
(Relaxed)
Critical information: Especial pricing as well as contracts, payroll (only the accountant will
be able to set and alter the limit of the credits for the customers), inventory and customer
records.
General rules: Each of the client will be having an individual user profile; the users have to
change the passcodes in every 60 days as well as the users have to utilize the recent security
patches.
For the protection for an organisation by a nicely planned security management. The
most important enabler requires recognition as one of the most important component of the
company. The efficient and effective security program needs co-operation from the leaders of
the business as well as the personnel who are within the organisation (Skopik, Settanni and
Fiedler, 2016). Cyber security and Information assurance are the function that are integrated
which needs the effective collaboration that will be throughput the entire organisation.
Roles and responsibilities:
Chief Information officer:

5INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
The CIO will be having the responsibility for ensuring the adoption and development
for the information security strategy.
Information security officer:
The officer will be designated by CIO and will be having the responsibility for
maintaining, building the information security plan for the organisation.
Data proprietor:
This person is having the responsibilities for the oversight of the data or the
computing systems along with the access for the data that are protected as well as the major
responsibility to determine the function and purpose of any resource of the data.
Models and methods:
State machine models: This model refers to a framework, which can remain always in
secure mode for the operational state.
Bell-LaPadula Model: The bell-LaPadula model was developed for formalizing the US
DoD. It is multi level security policy (Stewart and Mueller, 2013). This model is on the basis
of the state machine model.
Statutory requirements:
These requirements are strong authentication, strong encryption as well as the
organisational and technical security measures.
Risk assessment:
The risk assessment are utilized for identifying, estimating as well as for prioritizing
the risks for the organisational assets and operations that are resulting from the utilization of
The CIO will be having the responsibility for ensuring the adoption and development
for the information security strategy.
Information security officer:
The officer will be designated by CIO and will be having the responsibility for
maintaining, building the information security plan for the organisation.
Data proprietor:
This person is having the responsibilities for the oversight of the data or the
computing systems along with the access for the data that are protected as well as the major
responsibility to determine the function and purpose of any resource of the data.
Models and methods:
State machine models: This model refers to a framework, which can remain always in
secure mode for the operational state.
Bell-LaPadula Model: The bell-LaPadula model was developed for formalizing the US
DoD. It is multi level security policy (Stewart and Mueller, 2013). This model is on the basis
of the state machine model.
Statutory requirements:
These requirements are strong authentication, strong encryption as well as the
organisational and technical security measures.
Risk assessment:
The risk assessment are utilized for identifying, estimating as well as for prioritizing
the risks for the organisational assets and operations that are resulting from the utilization of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
the information systems (Tarkoma and Ailisto, 2013). The risk manager is having the
responsibility for the risk managing procedure. The responsibilities are:
Implement and develop the risk mitigation strategy.
Consolidate, clarify as well as document the risk.
Monitor and maintain information in the risk register.
The identification of the risks can have the effect on the outcome of the project. The risk
register is including the following:
Unique identifier for every risk
Methods that are proposed to deal with the risk (Wilhite, Sivakumar and Pulwarty, 2014).
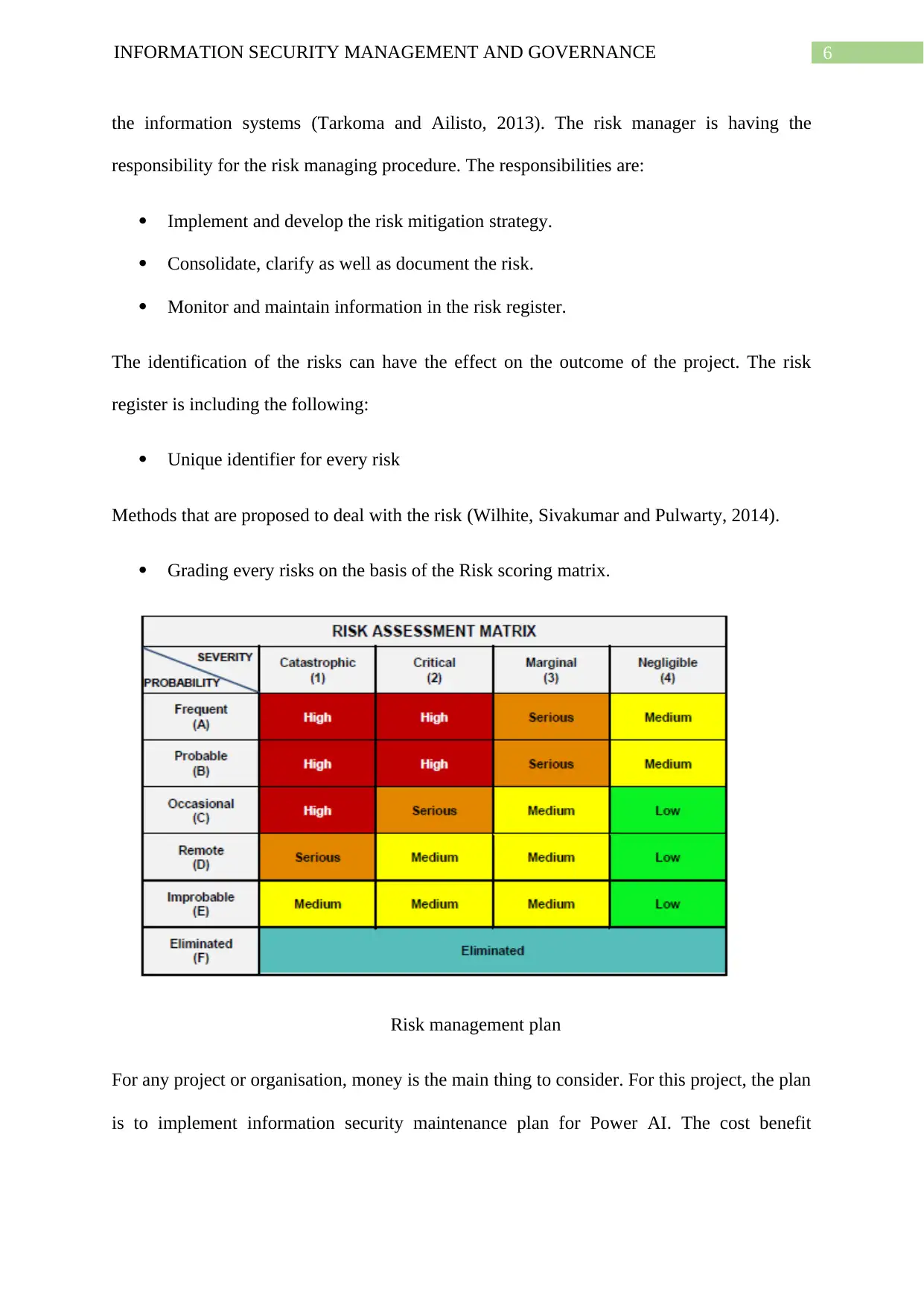
Grading every risks on the basis of the Risk scoring matrix.
Risk management plan
For any project or organisation, money is the main thing to consider. For this project, the plan
is to implement information security maintenance plan for Power AI. The cost benefit
the information systems (Tarkoma and Ailisto, 2013). The risk manager is having the
responsibility for the risk managing procedure. The responsibilities are:
Implement and develop the risk mitigation strategy.
Consolidate, clarify as well as document the risk.
Monitor and maintain information in the risk register.
The identification of the risks can have the effect on the outcome of the project. The risk
register is including the following:
Unique identifier for every risk
Methods that are proposed to deal with the risk (Wilhite, Sivakumar and Pulwarty, 2014).
Grading every risks on the basis of the Risk scoring matrix.
Risk management plan
For any project or organisation, money is the main thing to consider. For this project, the plan
is to implement information security maintenance plan for Power AI. The cost benefit
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
analysis estimates the total value of money as well as costs and the benefits to the community
of the project.
analysis estimates the total value of money as well as costs and the benefits to the community
of the project.

8INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
References:
Alnatheer, M.A., 2014. A conceptual model to understand information security
culture. International Journal of Social Science and Humanity, 4(2), p.104.
Fischhoff, B., 2015. The realities of risk-cost-benefit analysis. Science, 350(6260),
p.aaa6516.
International Test Commission (ITC), 2016. The International Test Commission Guidelines
on the Security of Tests, Examinations, and Other Assessments: International Test
Commission (ITC). International Journal of Testing, 16(3), pp.181-204.
Lu, T., Guo, X., Xu, B., Zhao, L., Peng, Y. and Yang, H., 2013, September. Next big thing in
big data: the security of the ICT supply chain. In 2013 International Conference on Social
Computing (pp. 1066-1073). IEEE.
Marcelino-Sádaba, S., Pérez-Ezcurdia, A., Lazcano, A.M.E. and Villanueva, P., 2014. Project
risk management methodology for small firms. International journal of project
management, 32(2), pp.327-340.
Skopik, F., Settanni, G. and Fiedler, R., 2016. A problem shared is a problem halved: A
survey on the dimensions of collective cyber defense through security information
sharing. Computers & Security, 60, pp.154-176.
Stewart, M.G. and Mueller, J., 2013. Terrorism risks and cost‐benefit analysis of aviation
security. Risk Analysis, 33(5), pp.893-908.
Tarkoma, S. and Ailisto, H., 2013. The internet of things program: the finnish
perspective. IEEE Communications Magazine, 51(3), pp.10-11.
References:
Alnatheer, M.A., 2014. A conceptual model to understand information security
culture. International Journal of Social Science and Humanity, 4(2), p.104.
Fischhoff, B., 2015. The realities of risk-cost-benefit analysis. Science, 350(6260),
p.aaa6516.
International Test Commission (ITC), 2016. The International Test Commission Guidelines
on the Security of Tests, Examinations, and Other Assessments: International Test
Commission (ITC). International Journal of Testing, 16(3), pp.181-204.
Lu, T., Guo, X., Xu, B., Zhao, L., Peng, Y. and Yang, H., 2013, September. Next big thing in
big data: the security of the ICT supply chain. In 2013 International Conference on Social
Computing (pp. 1066-1073). IEEE.
Marcelino-Sádaba, S., Pérez-Ezcurdia, A., Lazcano, A.M.E. and Villanueva, P., 2014. Project
risk management methodology for small firms. International journal of project
management, 32(2), pp.327-340.
Skopik, F., Settanni, G. and Fiedler, R., 2016. A problem shared is a problem halved: A
survey on the dimensions of collective cyber defense through security information
sharing. Computers & Security, 60, pp.154-176.
Stewart, M.G. and Mueller, J., 2013. Terrorism risks and cost‐benefit analysis of aviation
security. Risk Analysis, 33(5), pp.893-908.
Tarkoma, S. and Ailisto, H., 2013. The internet of things program: the finnish
perspective. IEEE Communications Magazine, 51(3), pp.10-11.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY MANAGEMENT AND GOVERNANCE
Wilhite, D.A., Sivakumar, M.V. and Pulwarty, R., 2014. Managing drought risk in a
changing climate: The role of national drought policy. Weather and Climate Extremes, 3,
pp.4-13.
Wilhite, D.A., Sivakumar, M.V. and Pulwarty, R., 2014. Managing drought risk in a
changing climate: The role of national drought policy. Weather and Climate Extremes, 3,
pp.4-13.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

