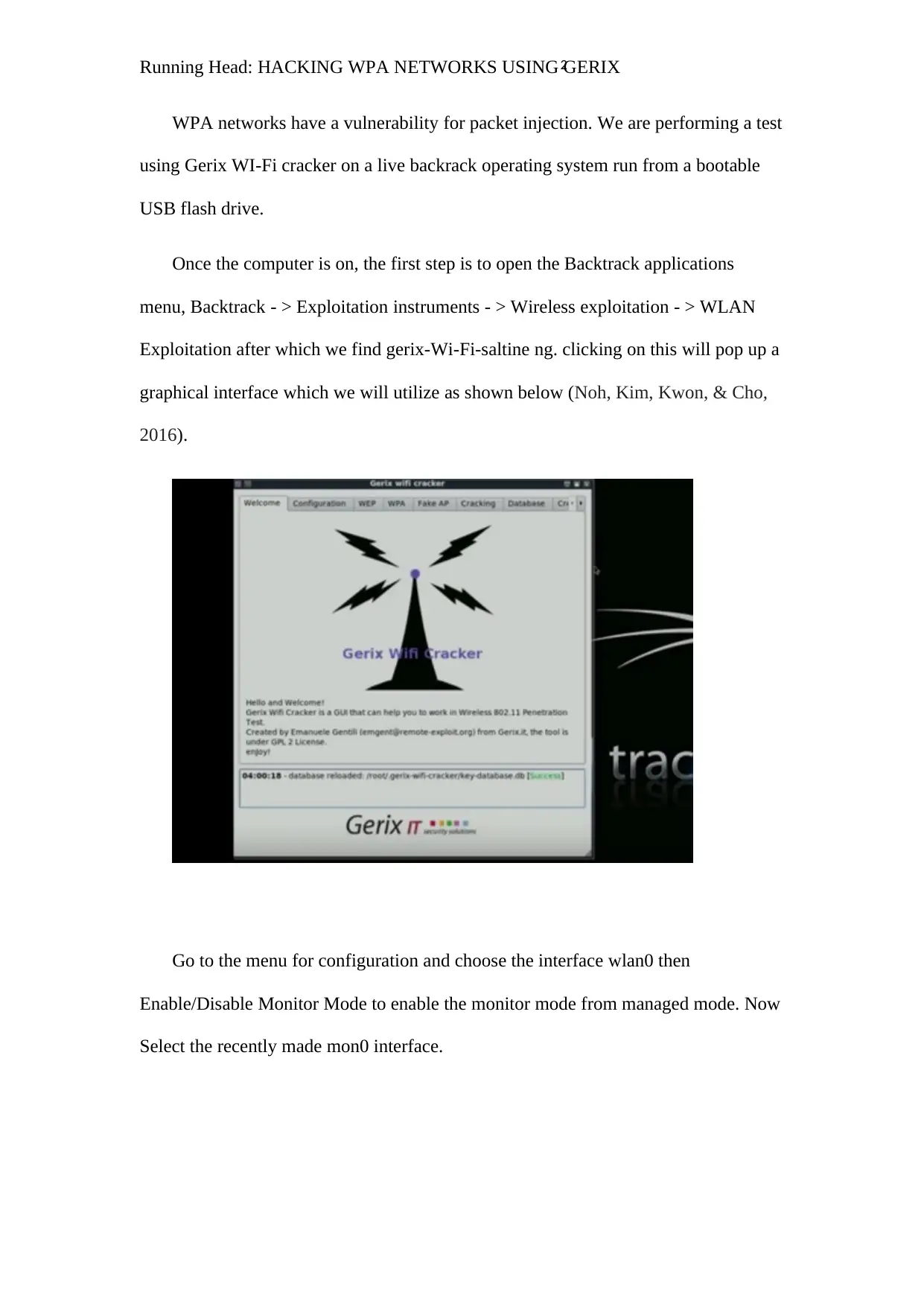
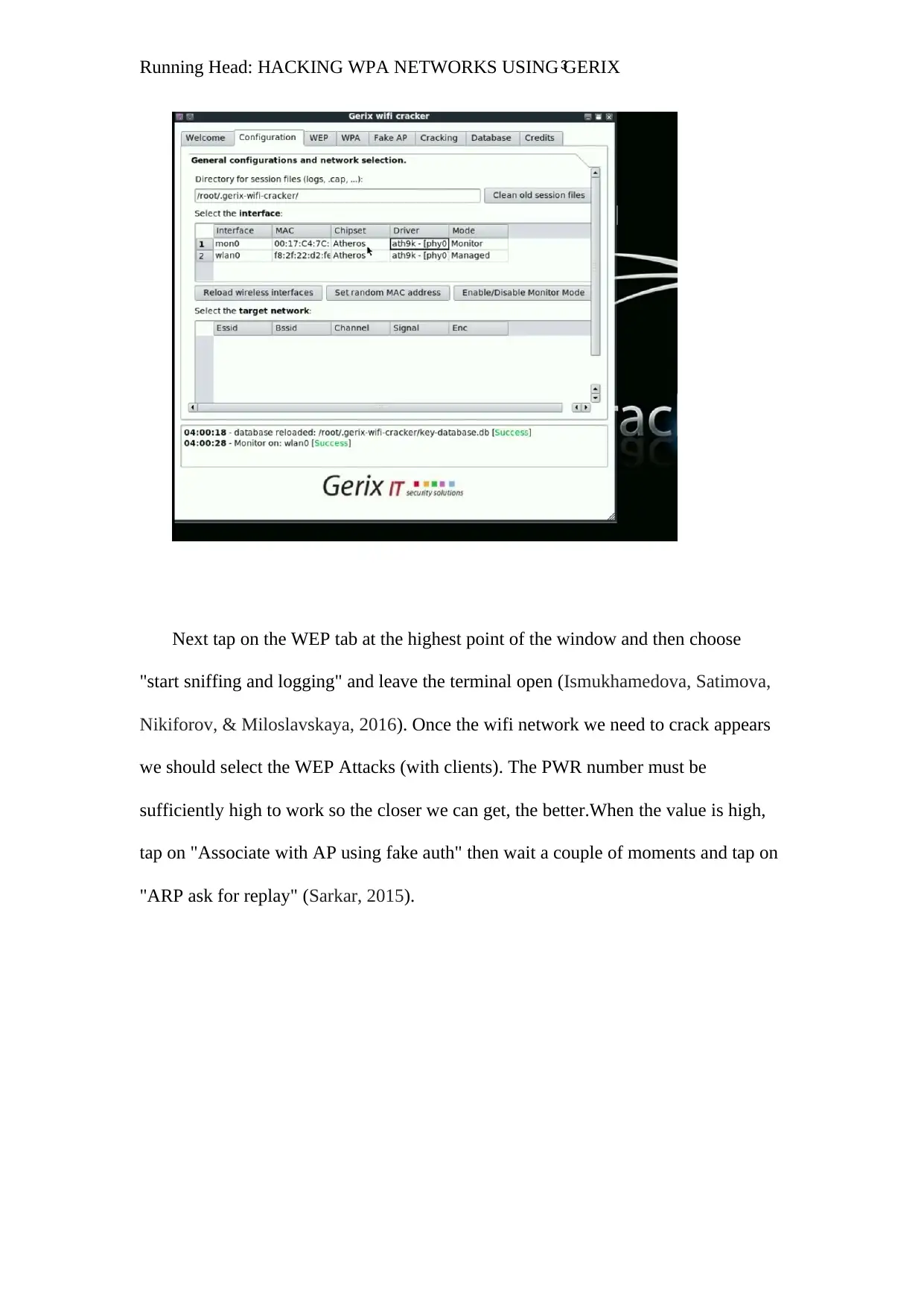
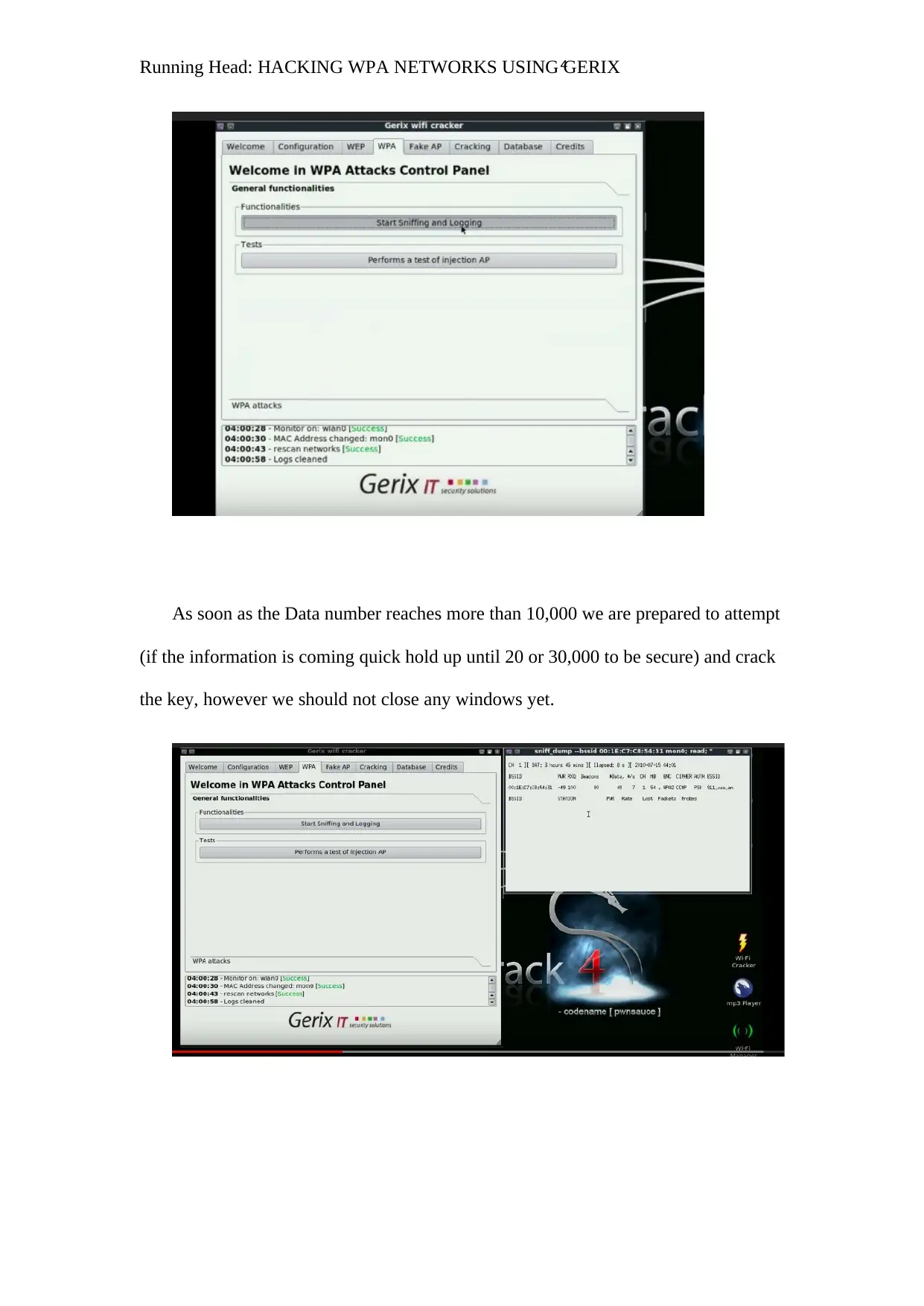
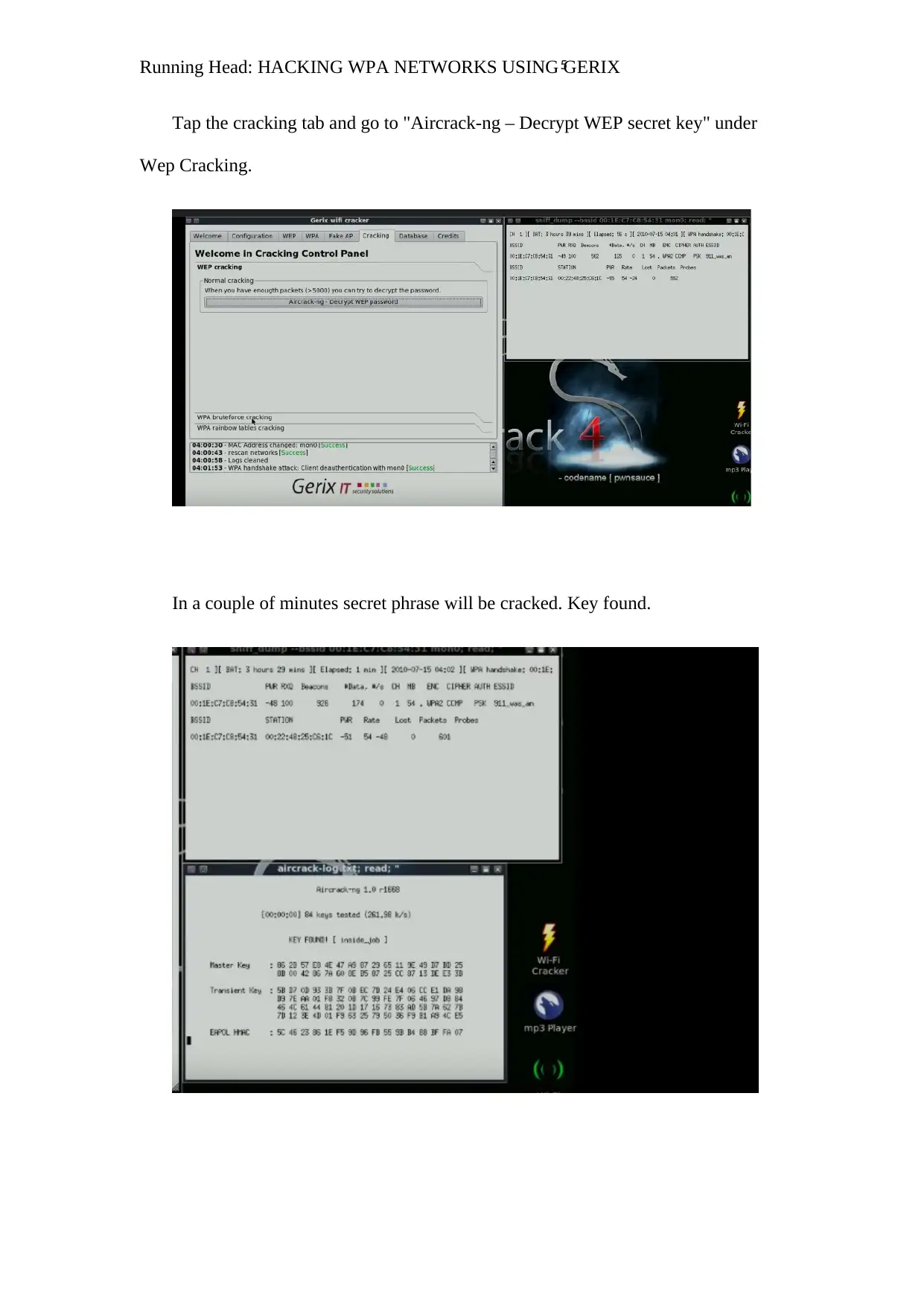
Comprehensive Guide: Hacking WPA Networks with Gerix Wi-Fi Cracker
VerifiedAdded on 2023/04/22
|6
|545
|224
Practical Assignment
AI Summary
This assignment provides a step-by-step guide on how to hack WPA networks using the Gerix Wi-Fi cracker on a Backtrack operating system. It details the process from enabling monitor mode and sniffing packets to performing WEP attacks and cracking the WEP key. The guide emphasizes the importance of packet injection vulnerability in WPA networks and provides practical instructions for exploiting these vulnerabilities using tools available in Backtrack. It also includes references to research papers that discuss the vulnerabilities in WPA networks and key exchange schemes.
1 out of 6



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)