University Cryptography Assignment: MD5, SHA and Data Integrity
VerifiedAdded on 2022/09/12
|6
|576
|14
Homework Assignment
AI Summary
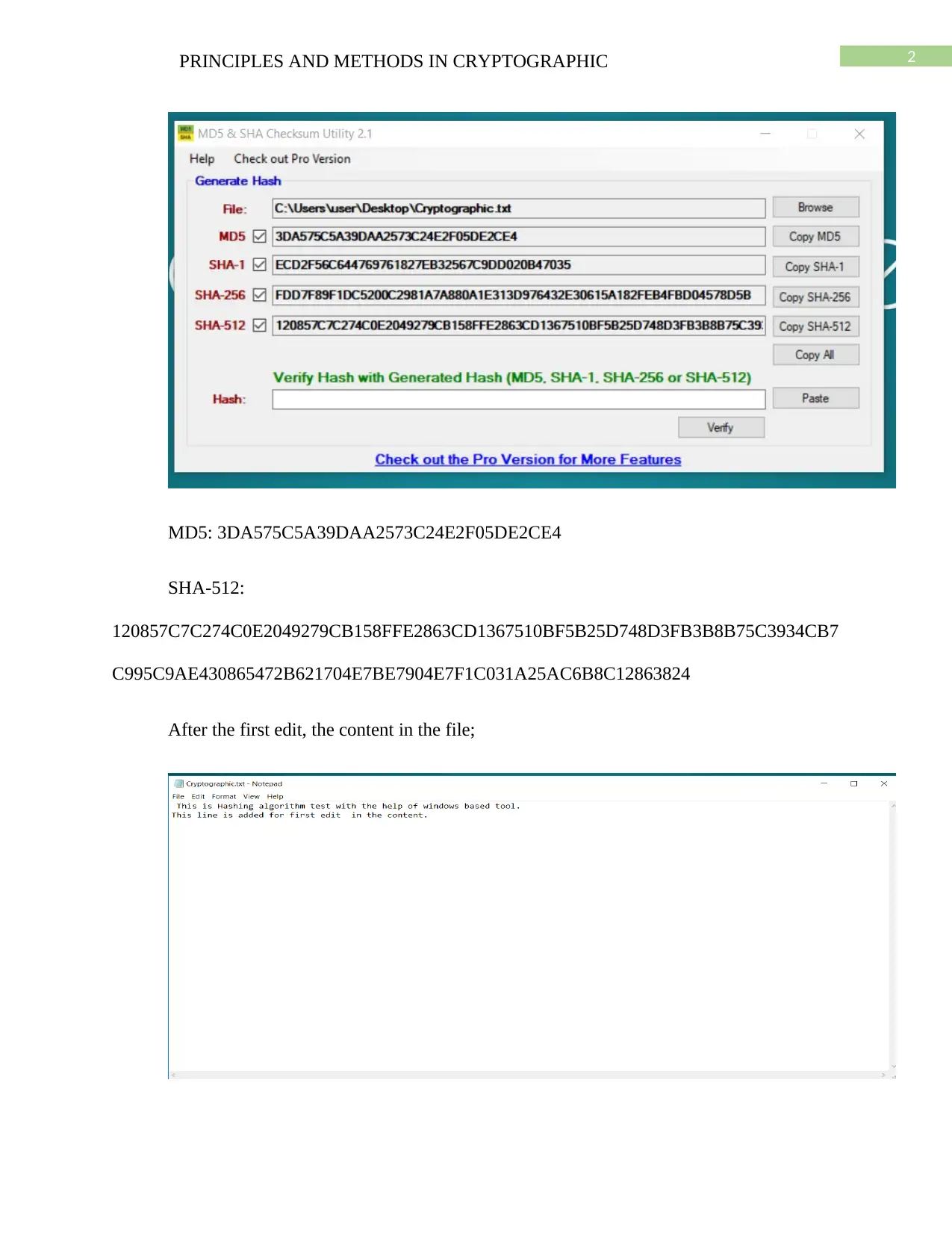
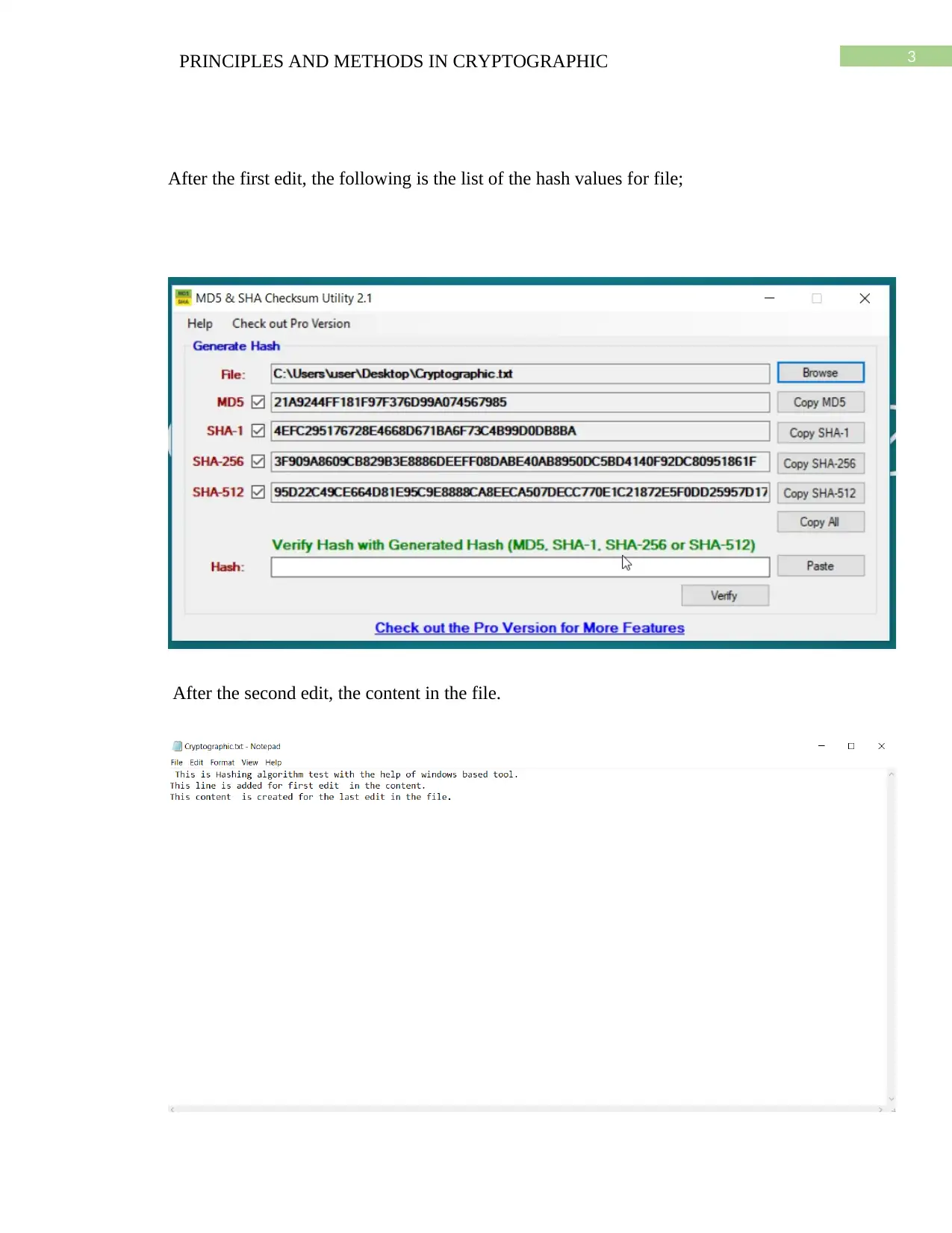
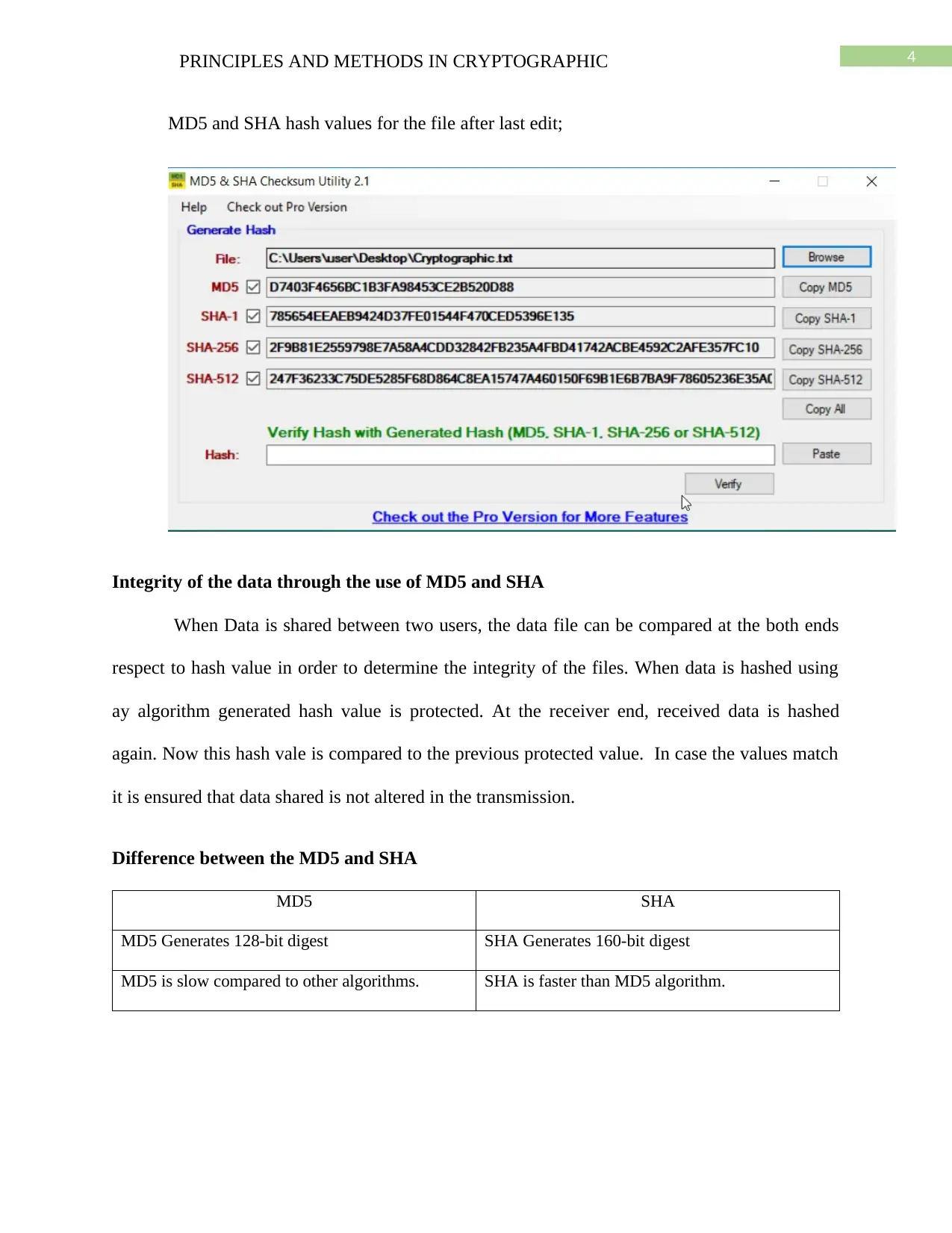
This assignment solution delves into cryptographic principles, specifically focusing on hashing algorithms such as MD5 and SHA. It explains how these algorithms convert data strings into fixed-length numeric strings, crucial for data integrity and collision resistance. The document outlines the MD5 algorithm's operation, including padding and digest calculation, and presents the hash values for a sample file after edits. It also discusses how MD5 and SHA are used to ensure data integrity when shared between users, by comparing hash values at both ends. The solution further highlights the differences between MD5 and SHA, including digest length, speed, and vulnerability to cryptanalytic attacks, and references several academic sources. This assignment helps students understand the practical application of these algorithms in securing data.
1 out of 6









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)