Report on Privacy and Data Protection Strategies for MyLicense Portal
VerifiedAdded on 2023/06/06
|5
|803
|294
Report
AI Summary
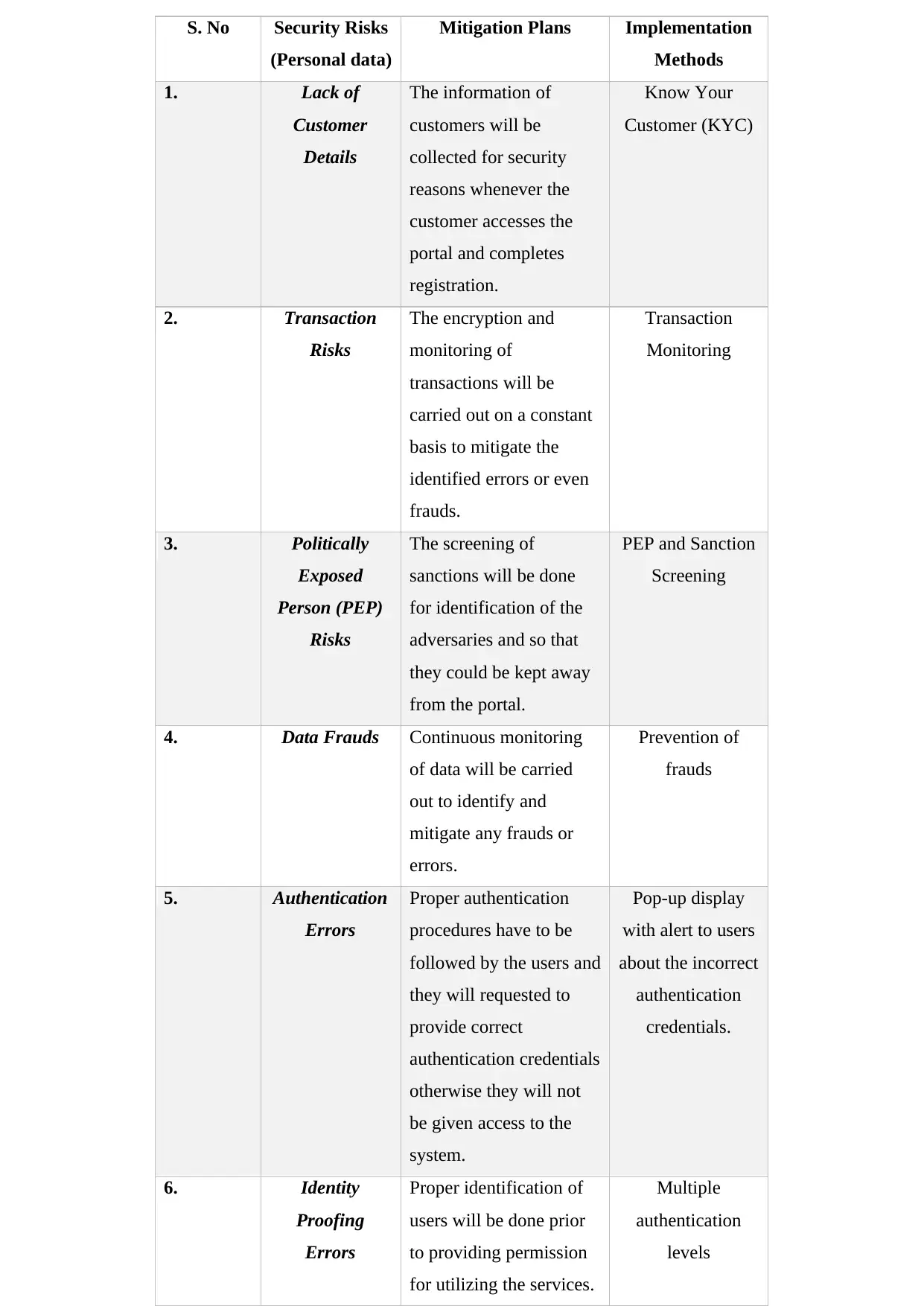
This report focuses on the privacy and data protection strategies employed for the MyLicense portal, emphasizing the importance of maintaining informal data identity. It details the monitoring of transactions and user registration processes, highlighting the use of user IDs and passwords as digital identities managed by the DAS system. The report addresses security risks such as lack of KYC details, transaction risks, PEP screening, data frauds, and authentication errors, proposing mitigation plans including encryption, transaction monitoring, PEP screening, continuous data monitoring, and proper authentication procedures. Control mechanisms like attribute collection, standards adherence, attribute exchange, authentication, service delivery, and authorization are also discussed to secure the digital identity of DAS consumers. The report provides references to support the discussed strategies and solutions.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)