Comprehensive Analysis: Privacy Issues of IoT Devices and Solutions
VerifiedAdded on 2023/03/17
|12
|3390
|89
Report
AI Summary
This report, authored by Rajat, delves into the multifaceted privacy issues associated with the Internet of Things (IoT). It begins by outlining key research questions and the methodology of secondary data collection, emphasizing the use of peer-reviewed papers to identify privacy concerns. The report provides a comprehensive background study, citing various researchers and their findings on security vulnerabilities like side-channel attacks, data aggregation issues, and the impact of social engineering. It explores the role of insufficient testing and updating in IoT device security, discussing the threats posed by DDoS attacks and Mirai botnets. Furthermore, the report examines the significance of data security and privacy in commercial IoT applications, addressing networking issues and the importance of regular security updates. The report also highlights the impact of user ignorance on IoT security, emphasizing the financial losses faced by organizations due to cyberattacks and the need for risk mitigation strategies. Finally, the report concludes by summarizing the security vulnerabilities of IoT devices and proposes several unanswered questions about IoT privacy, including identifying security issues, BYOD, ethical considerations, risk management plans, and public Wi-Fi concerns.

Running head: PRIVACY ISSUES OF IOT
Privacy issues of IoT
Name of the Student:rajat
Name of the University
Author’s Note:
Privacy issues of IoT
Name of the Student:rajat
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1PRIVACY ISSUES OF IOT
Table of Contents
Introduction................................................................................................................................2
Research Questions................................................................................................................2
Date Collection.......................................................................................................................2
Background study.......................................................................................................................2
Aims and Significance...............................................................................................................8
Research Plan.............................................................................................................................9
Publication Plan.....................................................................................................................9
Conclusion..................................................................................................................................9
Reference..................................................................................................................................11
Table of Contents
Introduction................................................................................................................................2
Research Questions................................................................................................................2
Date Collection.......................................................................................................................2
Background study.......................................................................................................................2
Aims and Significance...............................................................................................................8
Research Plan.............................................................................................................................9
Publication Plan.....................................................................................................................9
Conclusion..................................................................................................................................9
Reference..................................................................................................................................11

2PRIVACY ISSUES OF IOT
Introduction
The incorporation of the IoT based devices may have numerous security issues on our
society as well as in commercial organizations in terms of the security issues. This research
proposal will be identifying the privacy issues of the IoT based devices. The following unit of
this research proposal will be listing the research questions in an organized manner.
Research Questions
o What are the privacy issues of IoT?
o How can be issues be resolved?
Date Collection
Secondary data collection procedure will be followed in the paper. 30 peer-reviewed
papers will be considered in the paper in the background study which will be helping to
address the research gap. The paper will be concluding with a Gantt chart presenting the task
plan and the publication plan. The ensuing unit of this research proposal will be providing the
background story of the paper where reputed scholars have stated and argue about the
security issues of the IoT devices.
Background study
As discussed by Balte, Kashid and Patil (2015), there are lots of security issues with
IoT devices such as the side channel attacks. The researcher of the paper focuses on the
different categories of security issues of the IoT devices which are used in the automobile
industry. The investigators of the paper stated that the side channel attacks are very much
common in the IoT devices which are connected in the open network (Alrawaiset al. 2015).
The information of the IoT devices are compromised during this security attack as mentioned
by the researcher of this resource, at the same time it can also be said that the compromise in
Introduction
The incorporation of the IoT based devices may have numerous security issues on our
society as well as in commercial organizations in terms of the security issues. This research
proposal will be identifying the privacy issues of the IoT based devices. The following unit of
this research proposal will be listing the research questions in an organized manner.
Research Questions
o What are the privacy issues of IoT?
o How can be issues be resolved?
Date Collection
Secondary data collection procedure will be followed in the paper. 30 peer-reviewed
papers will be considered in the paper in the background study which will be helping to
address the research gap. The paper will be concluding with a Gantt chart presenting the task
plan and the publication plan. The ensuing unit of this research proposal will be providing the
background story of the paper where reputed scholars have stated and argue about the
security issues of the IoT devices.
Background study
As discussed by Balte, Kashid and Patil (2015), there are lots of security issues with
IoT devices such as the side channel attacks. The researcher of the paper focuses on the
different categories of security issues of the IoT devices which are used in the automobile
industry. The investigators of the paper stated that the side channel attacks are very much
common in the IoT devices which are connected in the open network (Alrawaiset al. 2015).
The information of the IoT devices are compromised during this security attack as mentioned
by the researcher of this resource, at the same time it can also be said that the compromise in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3PRIVACY ISSUES OF IOT
the location settings of the IoT devices is the other privacy concern of the IoT devices (Yi,
Qin and Li 2015). The investigators of this resources stated that data visualization and the
data aggregation are the other security concerns of most of the IoT devices which are used in
the global commercial organizations for transferring data (Iyengar, Kundu, and Pallis 2018).
The paper also discusses the configuration issues of the IoT devices which can lead to other
issues such as the compatibility issues and scalability issue (Yang et al. 2017). The
investigator of the paper argued that cyber security attacks such as the side channel attacks
could have an undesirable impact on the users of the IoT devices. Most of the sensitive
information are compromised during these security attacks as instructed by the researchers
(Lee and Lee 2015). The paper also identifies the role and the ability of the social engineers
who are involved in this type of security breaches. This paper have both benefits as well as
limitations, the prime advantage of the paper is that it focuses on most of the complexities of
the side channel attacks are increasingly found in most of the IoT devices. The usage of the
cryptographic keys during the attacks was mentioned by the researcher of the paper in a
professional manner (Lee et al. 2015). Though, the paper has lots of limitations as well. The
prime disadvantage of the paper is it does not discuss the other cyber security risks such as
the threats of ransomware in the IoT devices. But Caron et al. (2016), stated that cyber
security issues such as the threat coming from IoT malware and ransomware can have a
significant undesirable impact in the IoT devices which are always connected in open private
networks. This investigator contradicts with the discussion made by Balte, Kashid and Patil
(2015) who stated that side channel attacks are the most common security attacks in the IoT
devices. The gap in the literature of these two paper is both of them failed to discuss the
effective risk coming from cyber security issues such as the side channel attacks and
ransomeware.
the location settings of the IoT devices is the other privacy concern of the IoT devices (Yi,
Qin and Li 2015). The investigators of this resources stated that data visualization and the
data aggregation are the other security concerns of most of the IoT devices which are used in
the global commercial organizations for transferring data (Iyengar, Kundu, and Pallis 2018).
The paper also discusses the configuration issues of the IoT devices which can lead to other
issues such as the compatibility issues and scalability issue (Yang et al. 2017). The
investigator of the paper argued that cyber security attacks such as the side channel attacks
could have an undesirable impact on the users of the IoT devices. Most of the sensitive
information are compromised during these security attacks as instructed by the researchers
(Lee and Lee 2015). The paper also identifies the role and the ability of the social engineers
who are involved in this type of security breaches. This paper have both benefits as well as
limitations, the prime advantage of the paper is that it focuses on most of the complexities of
the side channel attacks are increasingly found in most of the IoT devices. The usage of the
cryptographic keys during the attacks was mentioned by the researcher of the paper in a
professional manner (Lee et al. 2015). Though, the paper has lots of limitations as well. The
prime disadvantage of the paper is it does not discuss the other cyber security risks such as
the threats of ransomware in the IoT devices. But Caron et al. (2016), stated that cyber
security issues such as the threat coming from IoT malware and ransomware can have a
significant undesirable impact in the IoT devices which are always connected in open private
networks. This investigator contradicts with the discussion made by Balte, Kashid and Patil
(2015) who stated that side channel attacks are the most common security attacks in the IoT
devices. The gap in the literature of these two paper is both of them failed to discuss the
effective risk coming from cyber security issues such as the side channel attacks and
ransomeware.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4PRIVACY ISSUES OF IOT
As stated by Borgohain, Kumar and Sanyal (2015), insufficient testing and updating
can be one of the prime reasons behind the security concerns of the IoT devices. The
researcher of the paper stated about the different categories of testing procedures which can
help the users of the IoT devices to get rid of the security issues (Weber 2015). The
researcher of the paper stated that unit testing, black box testing procedure and white box
testing procedure can be very much important to identify the bugs or the security loop holes
of the IoT devices which are the reason behind privacy issues like data encryption (Balte,
Kashid and Patil 2015). The researcher of the paper stated that Mirai botnet is one of the
deadliest DDoS attacks among most of the IoT devices, the investigator added that these
botnets quickly identify the loopholes of the IoT devices. The loopholes of the IoT devices
can be managed in the first place using the different types of testing procedures which are
stated above (Ngu et al. 2017). The researcher of the paper added that that the efficiency of
the IoT devices are fully compromised during the DDoS attacks. This paper have both
advantages as well as limitations. The foremost advantage of this paper is that it helps in
identifying most of the security issues associated with the IoT devices such as the DDoS
attack and the threats coming from the Mirai botnets (Porambage et al. 2016). However, it
can also be said that that the paper have numerous limitations, as well as the paper, failed to
discuss the mitigation strategies of these security issues which is very much common in most
of the IoT based devices.
As discussed by Celik et al. (2018), data security and data privacy of the IoT devices
which are used in commercial organizations are the two most desired requirements in today’s
world. The researcher of the paper stated that there are lots of privacy issues associated with
most of the IoT devices which are used in our society such as the temperature sensors. The
networking issues of the IoT devices such as the thermostats and other equipment’s which are
used in the manufacturing industries (Razzaq et al. 2017). The paper suggested that the
As stated by Borgohain, Kumar and Sanyal (2015), insufficient testing and updating
can be one of the prime reasons behind the security concerns of the IoT devices. The
researcher of the paper stated about the different categories of testing procedures which can
help the users of the IoT devices to get rid of the security issues (Weber 2015). The
researcher of the paper stated that unit testing, black box testing procedure and white box
testing procedure can be very much important to identify the bugs or the security loop holes
of the IoT devices which are the reason behind privacy issues like data encryption (Balte,
Kashid and Patil 2015). The researcher of the paper stated that Mirai botnet is one of the
deadliest DDoS attacks among most of the IoT devices, the investigator added that these
botnets quickly identify the loopholes of the IoT devices. The loopholes of the IoT devices
can be managed in the first place using the different types of testing procedures which are
stated above (Ngu et al. 2017). The researcher of the paper added that that the efficiency of
the IoT devices are fully compromised during the DDoS attacks. This paper have both
advantages as well as limitations. The foremost advantage of this paper is that it helps in
identifying most of the security issues associated with the IoT devices such as the DDoS
attack and the threats coming from the Mirai botnets (Porambage et al. 2016). However, it
can also be said that that the paper have numerous limitations, as well as the paper, failed to
discuss the mitigation strategies of these security issues which is very much common in most
of the IoT based devices.
As discussed by Celik et al. (2018), data security and data privacy of the IoT devices
which are used in commercial organizations are the two most desired requirements in today’s
world. The researcher of the paper stated that there are lots of privacy issues associated with
most of the IoT devices which are used in our society such as the temperature sensors. The
networking issues of the IoT devices such as the thermostats and other equipment’s which are
used in the manufacturing industries (Razzaq et al. 2017). The paper suggested that the

5PRIVACY ISSUES OF IOT
networking security of the IoT devices must be managed using the networking experts who
knows the insights and the loopholes of the private network which are used by the social
engineers as the entry points.
The researchers of the paper also highlight the important of the data prevention
techniques can help the users of the IoT devices to address the threats coming from the
privacy issues of the IoT devices. The researcher of the paper stated that the security patches
of the IoT devices must be regularly updated so that there are no internal security loopholes
in the IoT devices (Cook et al. 2018). The researcher of the paper stated that compromise of
data security can be a leading reason huge financial loss for business organizations as most of
them uses advanced IoT devices in their working environment (Tank, Upadhyay and Patel
2016). The researcher of this resource discussed most of the ways to improve the security of
the IoT products such as the use of the separate network and setting stronger alphanumeric
passwords in the IoT devices (Rehman et al. 2016). The paper has both limitations as well as
advantages. The most significant contribution of the paper is it helps in identifying the role of
the guest network which can keep the IoT devices safe from the threats coming from cyber
security attacks such as the Phishing emails. However, Farooq et al. (2015), stated that
ignorance d the users if the IoT devices can be a significant reason behind most of the
security vulnerabilities of the advanced IoT devices which are used in our society such as the
speaker systems and smart alarm clocks (Sivaraman et al. 2015). The researcher mentioned
that none of the IoT devices should be connected in the open network which can be a reason
behind the security issues of the cyber securities (Roy and Manoj 2016). The investigator of
the paper stated that the privacy issues of the vending machines is mainly caused due to the
ignorance of the IoT users. The paper successfully identifies the financial loss of the
healthcare organization where the IoT devices are compromised due to the cyber security
issues such as Ransomeware (Song et al. 2017). The researcher of the paper also criticized
networking security of the IoT devices must be managed using the networking experts who
knows the insights and the loopholes of the private network which are used by the social
engineers as the entry points.
The researchers of the paper also highlight the important of the data prevention
techniques can help the users of the IoT devices to address the threats coming from the
privacy issues of the IoT devices. The researcher of the paper stated that the security patches
of the IoT devices must be regularly updated so that there are no internal security loopholes
in the IoT devices (Cook et al. 2018). The researcher of the paper stated that compromise of
data security can be a leading reason huge financial loss for business organizations as most of
them uses advanced IoT devices in their working environment (Tank, Upadhyay and Patel
2016). The researcher of this resource discussed most of the ways to improve the security of
the IoT products such as the use of the separate network and setting stronger alphanumeric
passwords in the IoT devices (Rehman et al. 2016). The paper has both limitations as well as
advantages. The most significant contribution of the paper is it helps in identifying the role of
the guest network which can keep the IoT devices safe from the threats coming from cyber
security attacks such as the Phishing emails. However, Farooq et al. (2015), stated that
ignorance d the users if the IoT devices can be a significant reason behind most of the
security vulnerabilities of the advanced IoT devices which are used in our society such as the
speaker systems and smart alarm clocks (Sivaraman et al. 2015). The researcher mentioned
that none of the IoT devices should be connected in the open network which can be a reason
behind the security issues of the cyber securities (Roy and Manoj 2016). The investigator of
the paper stated that the privacy issues of the vending machines is mainly caused due to the
ignorance of the IoT users. The paper successfully identifies the financial loss of the
healthcare organization where the IoT devices are compromised due to the cyber security
issues such as Ransomeware (Song et al. 2017). The researcher of the paper also criticized
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6PRIVACY ISSUES OF IOT
the connectivity issues of the smart thermostats which are used in our society (Stergiou et al.
2018). The prime limitation of the paper is that the paper fails to provide case study
description to support the discussion of the paper. The benefits of the paper is that it
successfully identifies the privacy issues of most of the IoT devices which are regularly used
in our society (Sharma, Chen and Sheth 2018). Thus, based on the above paper the gap in
literature which can be identified is these paper have not provided a case study description of
the privacy issues of the IoT devices which could have helped the readers of this document to
identify the appropriate risk mitigation strategy for these risks.
Aims and Significance
The foremost determination of this proposal is to highlight the security vulnerabilities
of the IoT devices used in our society as well as in commercial organizations.
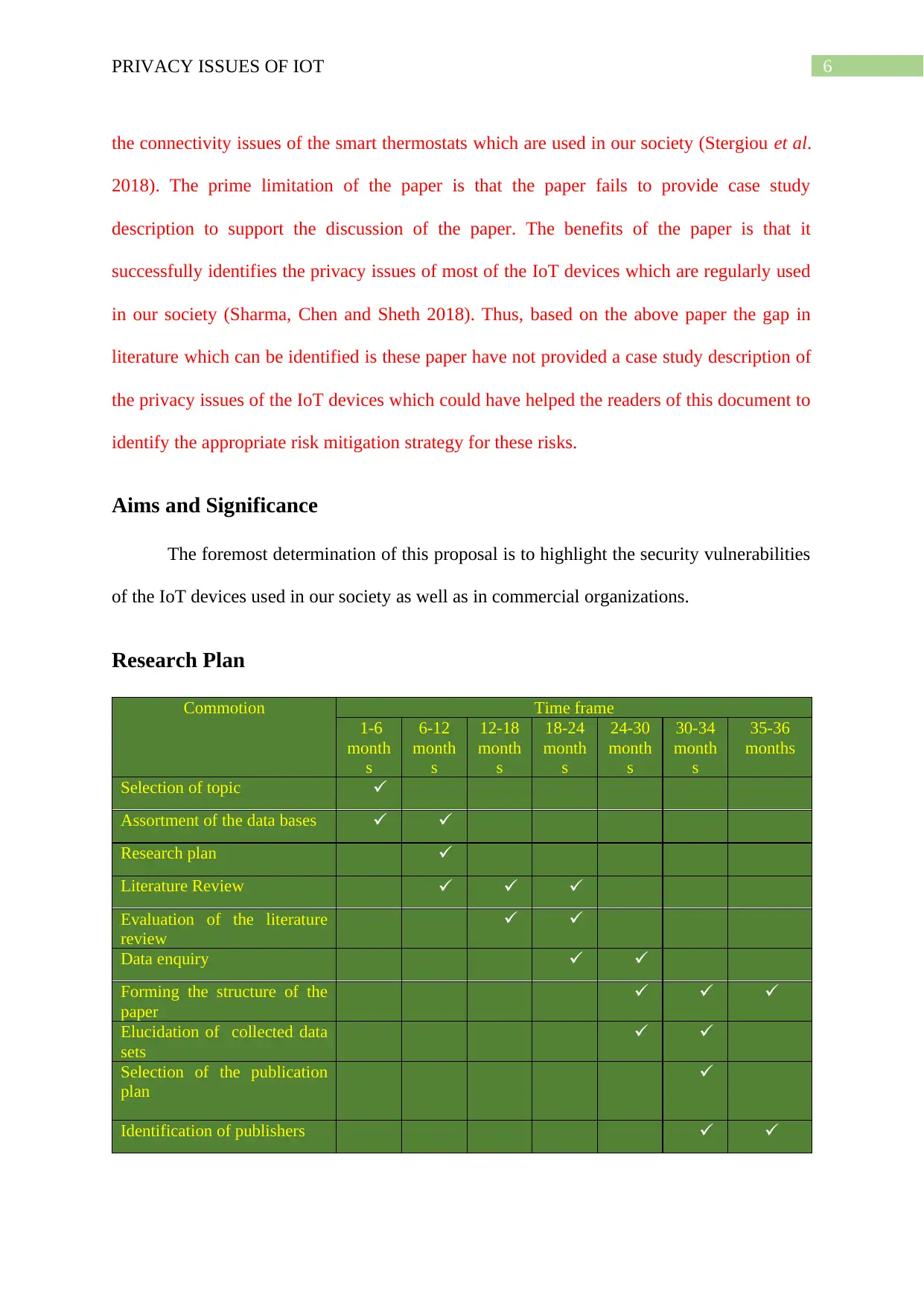
Research Plan
Commotion Time frame
1-6
month
s
6-12
month
s
12-18
month
s
18-24
month
s
24-30
month
s
30-34
month
s
35-36
months
Selection of topic
Assortment of the data bases
Research plan
Literature Review
Evaluation of the literature
review
Data enquiry
Forming the structure of the
paper
Elucidation of collected data
sets
Selection of the publication
plan
Identification of publishers
the connectivity issues of the smart thermostats which are used in our society (Stergiou et al.
2018). The prime limitation of the paper is that the paper fails to provide case study
description to support the discussion of the paper. The benefits of the paper is that it
successfully identifies the privacy issues of most of the IoT devices which are regularly used
in our society (Sharma, Chen and Sheth 2018). Thus, based on the above paper the gap in
literature which can be identified is these paper have not provided a case study description of
the privacy issues of the IoT devices which could have helped the readers of this document to
identify the appropriate risk mitigation strategy for these risks.
Aims and Significance
The foremost determination of this proposal is to highlight the security vulnerabilities
of the IoT devices used in our society as well as in commercial organizations.
Research Plan
Commotion Time frame
1-6
month
s
6-12
month
s
12-18
month
s
18-24
month
s
24-30
month
s
30-34
month
s
35-36
months
Selection of topic
Assortment of the data bases
Research plan
Literature Review
Evaluation of the literature
review
Data enquiry
Forming the structure of the
paper
Elucidation of collected data
sets
Selection of the publication
plan
Identification of publishers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7PRIVACY ISSUES OF IOT
Project Closure
Table 2: Timeframe of the activities
(Source: Created by the author)
Publication Plan
All the data of this paper was collected from recent peer-reviewed sources so it can be
used in the future research works. Most of the information of this report can be considered in
research proposal, dissertation, exhibition, conference paper and journal articles. Book
publishers will be targeted for publishing the content of this report.
The five unanswered open questions about the privacy in IoT devices are listed below.
How can non-technical users identify the security issues of IoT devices?
Can BYOD help in resolving network security of the IoT devices?
What are the ethical considerations of the IoT devices?
What is the exact risk management plan for IoT security vulnerabilities?
How can public Wi-Fi be a source of concern for IoT smart watches?
Conclusion
From the above proposal, it can be identified that there are lots of security
vulnerabilities associated with the IoT devices which are used in commercial organizations
and in our society.
Project Closure
Table 2: Timeframe of the activities
(Source: Created by the author)
Publication Plan
All the data of this paper was collected from recent peer-reviewed sources so it can be
used in the future research works. Most of the information of this report can be considered in
research proposal, dissertation, exhibition, conference paper and journal articles. Book
publishers will be targeted for publishing the content of this report.
The five unanswered open questions about the privacy in IoT devices are listed below.
How can non-technical users identify the security issues of IoT devices?
Can BYOD help in resolving network security of the IoT devices?
What are the ethical considerations of the IoT devices?
What is the exact risk management plan for IoT security vulnerabilities?
How can public Wi-Fi be a source of concern for IoT smart watches?
Conclusion
From the above proposal, it can be identified that there are lots of security
vulnerabilities associated with the IoT devices which are used in commercial organizations
and in our society.

8PRIVACY ISSUES OF IOT
Reference
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Balte, A., Kashid, A. and Patil, B., 2015. Security issues in Internet of Things (IoT): a survey.
International Journal of Advanced Research in Computer Science and Software Engineering,
5(4).
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Caron, X., Bosua, R., Maynard, S.B. and Ahmad, A., 2016. The Internet of Things (IoT) and
its impact on individual privacy: An Australian perspective. Computer Law & Security
Review, 32(1), pp.4-15.
Celik, Z.B., Fernandes, E., Pauley, E., Tan, G. and McDaniel, P., 2018. Program Analysis of
Commodity IoT Applications for Security and Privacy: Challenges and Opportunities. arXiv
preprint arXiv:1809.06962.
Cook, A., Robinson, M., Ferrag, M.A., Maglaras, L.A., He, Y., Jones, K. and Janicke, H.,
2018. Internet of cloud: Security and privacy issues. In Cloud Computing for Optimization:
Foundations, Applications, and Challenges (pp. 271-301). Springer, Cham.
Du, X., Chen, H.H., Zhu, L., Li, J. and Chang, Z., 2018. Security and Privacy in Wireless
IoT. IEEE Wireless Communications, 25(6), pp.10-11.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer Applications,
111(7).
Reference
Alrawais, A., Alhothaily, A., Hu, C. and Cheng, X., 2017. Fog computing for the internet of
things: Security and privacy issues. IEEE Internet Computing, 21(2), pp.34-42.
Balte, A., Kashid, A. and Patil, B., 2015. Security issues in Internet of Things (IoT): a survey.
International Journal of Advanced Research in Computer Science and Software Engineering,
5(4).
Borgohain, T., Kumar, U. and Sanyal, S., 2015. Survey of security and privacy issues of
internet of things. arXiv preprint arXiv:1501.02211.
Caron, X., Bosua, R., Maynard, S.B. and Ahmad, A., 2016. The Internet of Things (IoT) and
its impact on individual privacy: An Australian perspective. Computer Law & Security
Review, 32(1), pp.4-15.
Celik, Z.B., Fernandes, E., Pauley, E., Tan, G. and McDaniel, P., 2018. Program Analysis of
Commodity IoT Applications for Security and Privacy: Challenges and Opportunities. arXiv
preprint arXiv:1809.06962.
Cook, A., Robinson, M., Ferrag, M.A., Maglaras, L.A., He, Y., Jones, K. and Janicke, H.,
2018. Internet of cloud: Security and privacy issues. In Cloud Computing for Optimization:
Foundations, Applications, and Challenges (pp. 271-301). Springer, Cham.
Du, X., Chen, H.H., Zhu, L., Li, J. and Chang, Z., 2018. Security and Privacy in Wireless
IoT. IEEE Wireless Communications, 25(6), pp.10-11.
Farooq, M.U., Waseem, M., Khairi, A. and Mazhar, S., 2015. A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer Applications,
111(7).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9PRIVACY ISSUES OF IOT
Frustaci, M., Pace, P., Aloi, G. and Fortino, G., 2018. Evaluating critical security issues of
the IoT world: Present and Future challenges. IEEE Internet of Things Journal, 5(4),
pp.2483-2495.
Geneiatakis, D., Kounelis, I., Neisse, R., Nai-Fovino, I., Steri, G. and Baldini, G., 2017, May.
Security and privacy issues for an IoT based smart home. In 2017 40th International
Convention on Information and Communication Technology, Electronics and
Microelectronics (MIPRO) (pp. 1292-1297). IEEE.
Gope, P. and Hwang, T., 2015. BSN-Care: A secure IoT-based modern healthcare system
using body sensor network. IEEE sensors journal, 16(5), pp.1368-1376.
Hossain, M.M., Fotouhi, M. and Hasan, R., 2015, June. Towards an analysis of security
issues, challenges, and open problems in the internet of things. In 2015 IEEE World
Congress on Services (pp. 21-28). IEEE.
Hwang, Y.H., 2015, April. Iot security & privacy: threats and challenges. In Proceedings of
the 1st ACM Workshop on IoT Privacy, Trust, and Security (pp. 1-1). ACM.
Iyengar, A., Kundu, A. and Pallis, G., 2018. Healthcare Informatics and Privacy. IEEE
Internet Computing, 22(2), pp.29-31.
Lee, I. and Lee, K., 2015. The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), pp.431-440.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Ngu, A.H., Gutierrez, M., Metsis, V., Nepal, S. and Sheng, Q.Z., 2017. IoT middleware: A
survey on issues and enabling technologies. IEEE Internet of Things Journal, 4(1), pp.1-20.
Frustaci, M., Pace, P., Aloi, G. and Fortino, G., 2018. Evaluating critical security issues of
the IoT world: Present and Future challenges. IEEE Internet of Things Journal, 5(4),
pp.2483-2495.
Geneiatakis, D., Kounelis, I., Neisse, R., Nai-Fovino, I., Steri, G. and Baldini, G., 2017, May.
Security and privacy issues for an IoT based smart home. In 2017 40th International
Convention on Information and Communication Technology, Electronics and
Microelectronics (MIPRO) (pp. 1292-1297). IEEE.
Gope, P. and Hwang, T., 2015. BSN-Care: A secure IoT-based modern healthcare system
using body sensor network. IEEE sensors journal, 16(5), pp.1368-1376.
Hossain, M.M., Fotouhi, M. and Hasan, R., 2015, June. Towards an analysis of security
issues, challenges, and open problems in the internet of things. In 2015 IEEE World
Congress on Services (pp. 21-28). IEEE.
Hwang, Y.H., 2015, April. Iot security & privacy: threats and challenges. In Proceedings of
the 1st ACM Workshop on IoT Privacy, Trust, and Security (pp. 1-1). ACM.
Iyengar, A., Kundu, A. and Pallis, G., 2018. Healthcare Informatics and Privacy. IEEE
Internet Computing, 22(2), pp.29-31.
Lee, I. and Lee, K., 2015. The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), pp.431-440.
Lee, K., Kim, D., Ha, D., Rajput, U. and Oh, H., 2015, September. On security and privacy
issues of fog computing supported Internet of Things environment. In 2015 6th International
Conference on the Network of the Future (NOF) (pp. 1-3). IEEE.
Ngu, A.H., Gutierrez, M., Metsis, V., Nepal, S. and Sheng, Q.Z., 2017. IoT middleware: A
survey on issues and enabling technologies. IEEE Internet of Things Journal, 4(1), pp.1-20.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10PRIVACY ISSUES OF IOT
Porambage, P., Ylianttila, M., Schmitt, C., Kumar, P., Gurtov, A. and Vasilakos, A.V., 2016.
The quest for privacy in the internet of things. IEEE Cloud Computing, 3(2), pp.36-45.
Razzaq, M.A., Gill, S.H., Qureshi, M.A. and Ullah, S., 2017. Security issues in the Internet of
Things (IoT): a comprehensive study. International Journal of Advanced Computer Science
and Applications (IJACSA), 8(6), pp.383-388.
Rehman, S.U., Khan, I.U., Moiz, M. and Hasan, S., 2016. Security and privacy issues in IoT.
International journal of communication networks and information security, 8(3), p.147.
Roy, S. and Manoj, B.S., 2016. IoT enablers and their security and privacy issues. In Internet
of Things (IoT) in 5G Mobile Technologies (pp. 449-482). Springer, Cham.
Sharma, S., Chen, K. and Sheth, A., 2018. Toward practical privacy-preserving analytics for
iot and cloud-based healthcare systems. IEEE Internet Computing, 22(2), pp.42-51.
Sivaraman, V., Gharakheili, H.H., Vishwanath, A., Boreli, R. and Mehani, O., 2015, October.
Network-level security and privacy control for smart-home IoT devices. In 2015 IEEE 11th
International conference on wireless and mobile computing, networking and communications
(WiMob) (pp. 163-167). IEEE.
Song, T., Li, R., Mei, B., Yu, J., Xing, X. and Cheng, X., 2017. A privacy preserving
communication protocol for IoT applications in smart homes. IEEE Internet of Things
Journal, 4(6), pp.1844-1852.
Stergiou, C., Psannis, K.E., Kim, B.G. and Gupta, B., 2018. Secure integration of IoT and
cloud computing. Future Generation Computer Systems, 78, pp.964-975.
Tank, B., Upadhyay, H. and Patel, H., 2016, March. A survey on IoT privacy issues and
mitigation techniques. In Proceedings of the Second International Conference on
Information and Communication Technology for Competitive Strategies (p. 2). ACM.
Porambage, P., Ylianttila, M., Schmitt, C., Kumar, P., Gurtov, A. and Vasilakos, A.V., 2016.
The quest for privacy in the internet of things. IEEE Cloud Computing, 3(2), pp.36-45.
Razzaq, M.A., Gill, S.H., Qureshi, M.A. and Ullah, S., 2017. Security issues in the Internet of
Things (IoT): a comprehensive study. International Journal of Advanced Computer Science
and Applications (IJACSA), 8(6), pp.383-388.
Rehman, S.U., Khan, I.U., Moiz, M. and Hasan, S., 2016. Security and privacy issues in IoT.
International journal of communication networks and information security, 8(3), p.147.
Roy, S. and Manoj, B.S., 2016. IoT enablers and their security and privacy issues. In Internet
of Things (IoT) in 5G Mobile Technologies (pp. 449-482). Springer, Cham.
Sharma, S., Chen, K. and Sheth, A., 2018. Toward practical privacy-preserving analytics for
iot and cloud-based healthcare systems. IEEE Internet Computing, 22(2), pp.42-51.
Sivaraman, V., Gharakheili, H.H., Vishwanath, A., Boreli, R. and Mehani, O., 2015, October.
Network-level security and privacy control for smart-home IoT devices. In 2015 IEEE 11th
International conference on wireless and mobile computing, networking and communications
(WiMob) (pp. 163-167). IEEE.
Song, T., Li, R., Mei, B., Yu, J., Xing, X. and Cheng, X., 2017. A privacy preserving
communication protocol for IoT applications in smart homes. IEEE Internet of Things
Journal, 4(6), pp.1844-1852.
Stergiou, C., Psannis, K.E., Kim, B.G. and Gupta, B., 2018. Secure integration of IoT and
cloud computing. Future Generation Computer Systems, 78, pp.964-975.
Tank, B., Upadhyay, H. and Patel, H., 2016, March. A survey on IoT privacy issues and
mitigation techniques. In Proceedings of the Second International Conference on
Information and Communication Technology for Competitive Strategies (p. 2). ACM.

11PRIVACY ISSUES OF IOT
Weber, R.H., 2015. Internet of things: Privacy issues revisited. Computer Law & Security
Review, 31(5), pp.618-627.
Yang, Y., Wu, L., Yin, G., Li, L. and Zhao, H., 2017. A survey on security and privacy issues
in Internet-of-Things. IEEE Internet of Things Journal, 4(5), pp.1250-1258.
Yi, S., Qin, Z. and Li, Q., 2015, August. Security and privacy issues of fog computing: A
survey. In International conference on wireless algorithms, systems, and applications (pp.
685-695). Springer, Cham.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based
IoT: Challenges. IEEE Communications Magazine, 55(1), pp.26-33.
Weber, R.H., 2015. Internet of things: Privacy issues revisited. Computer Law & Security
Review, 31(5), pp.618-627.
Yang, Y., Wu, L., Yin, G., Li, L. and Zhao, H., 2017. A survey on security and privacy issues
in Internet-of-Things. IEEE Internet of Things Journal, 4(5), pp.1250-1258.
Yi, S., Qin, Z. and Li, Q., 2015, August. Security and privacy issues of fog computing: A
survey. In International conference on wireless algorithms, systems, and applications (pp.
685-695). Springer, Cham.
Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based
IoT: Challenges. IEEE Communications Magazine, 55(1), pp.26-33.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




