Comprehensive Privacy Strategy Proposal for DAS: SaaS Implementation
VerifiedAdded on 2022/09/29
|13
|3256
|23
Report
AI Summary
This report presents a comprehensive privacy strategy proposal for the Department of Administrative Services (DAS) in Australia, addressing the challenges and risks associated with implementing Software as a Service (SaaS) solutions for HR management within a cloud-first environment. The report identifies key security threats, including immature identification management, weak cloud infrastructure, data security issues, and lack of data logging. It outlines a detailed privacy strategy, emphasizing the importance of data collection, use, disclosure, and security, with a focus on digital identity, quality and correction of personal information, and personal data protection strategies. The proposal includes recommendations for official standards, employee training, strict security measures, frequent monitoring, data backup, and adherence to privacy policies to mitigate risks and ensure compliance with Australian privacy laws. The report concludes with a discussion on personal data protection and privacy policy, including data deletion, confidentiality, and data security measures.

1
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
Topic
Student’s Name
University Affiliation
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
Topic
Student’s Name
University Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
1. Introduction
The purpose of the report is discussing and evaluating the case study scenario of the the
Department of Administrative Services (DAS) in Australia, where it delivers a number of
services to the departments that are in the patronage by the Australian Government. The
main service that it offers is comprise of HR and personal management, contract,
tendering, contractor management and procurement. The services are depends on the data
centers of the DAS department. (Rittinghouse & Ransome, 2017).
In the light of revised policy change that has been prepared by the Australian
government, the department working under the patronage of system is bound to come
down beneath the shared Service system. In regard of specific system, all the services
under the government that are looked at after by the DAS are instructed to come under
the umbrella of one centralized system under the government. To achieve the goal of
centralizing the system under one unit, the government has confirmed and recommended
the implementation of the new tactic which is known as the CLOUD FIRST process. The
changes by the governmental organization require the assistance of the SAAS solution
and implementation which will buy form a US undertaking company.
In the previous report the development technique and the utilization dynamics of the
SaaS technology for the administration of the HR personal within the DAS infrastructure
has been stated, it has been estimated that the implementation of the SaaS technology was
one of the dynamic process that has been used for achieving the desired result.
(Lewandowski, Salako & Garcia-Perez, 2013).
The SaaS Solutions is called the Software as a Security solution. It belongs with a model
which advances the software for the security operation of the organization. This is
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
1. Introduction
The purpose of the report is discussing and evaluating the case study scenario of the the
Department of Administrative Services (DAS) in Australia, where it delivers a number of
services to the departments that are in the patronage by the Australian Government. The
main service that it offers is comprise of HR and personal management, contract,
tendering, contractor management and procurement. The services are depends on the data
centers of the DAS department. (Rittinghouse & Ransome, 2017).
In the light of revised policy change that has been prepared by the Australian
government, the department working under the patronage of system is bound to come
down beneath the shared Service system. In regard of specific system, all the services
under the government that are looked at after by the DAS are instructed to come under
the umbrella of one centralized system under the government. To achieve the goal of
centralizing the system under one unit, the government has confirmed and recommended
the implementation of the new tactic which is known as the CLOUD FIRST process. The
changes by the governmental organization require the assistance of the SAAS solution
and implementation which will buy form a US undertaking company.
In the previous report the development technique and the utilization dynamics of the
SaaS technology for the administration of the HR personal within the DAS infrastructure
has been stated, it has been estimated that the implementation of the SaaS technology was
one of the dynamic process that has been used for achieving the desired result.
(Lewandowski, Salako & Garcia-Perez, 2013).
The SaaS Solutions is called the Software as a Security solution. It belongs with a model
which advances the software for the security operation of the organization. This is

3
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
designed by a third party who develops and facilitate the software applications which the
users can access in a form of online web browser page. But there are a number of security
risks associated by the use of SAAS in HR management, which cannot be neglected and
are of crucial importance.
2. The security threats confronted by DAS using SAAS for HR management
The assurance of security of an organization determine the overall strength of cyber
security characteristics of the organization. The security structure of DAS is effected by
the use of SAAS technology for the cloud first technology. The security of Das is
affected in the following ways which includes:
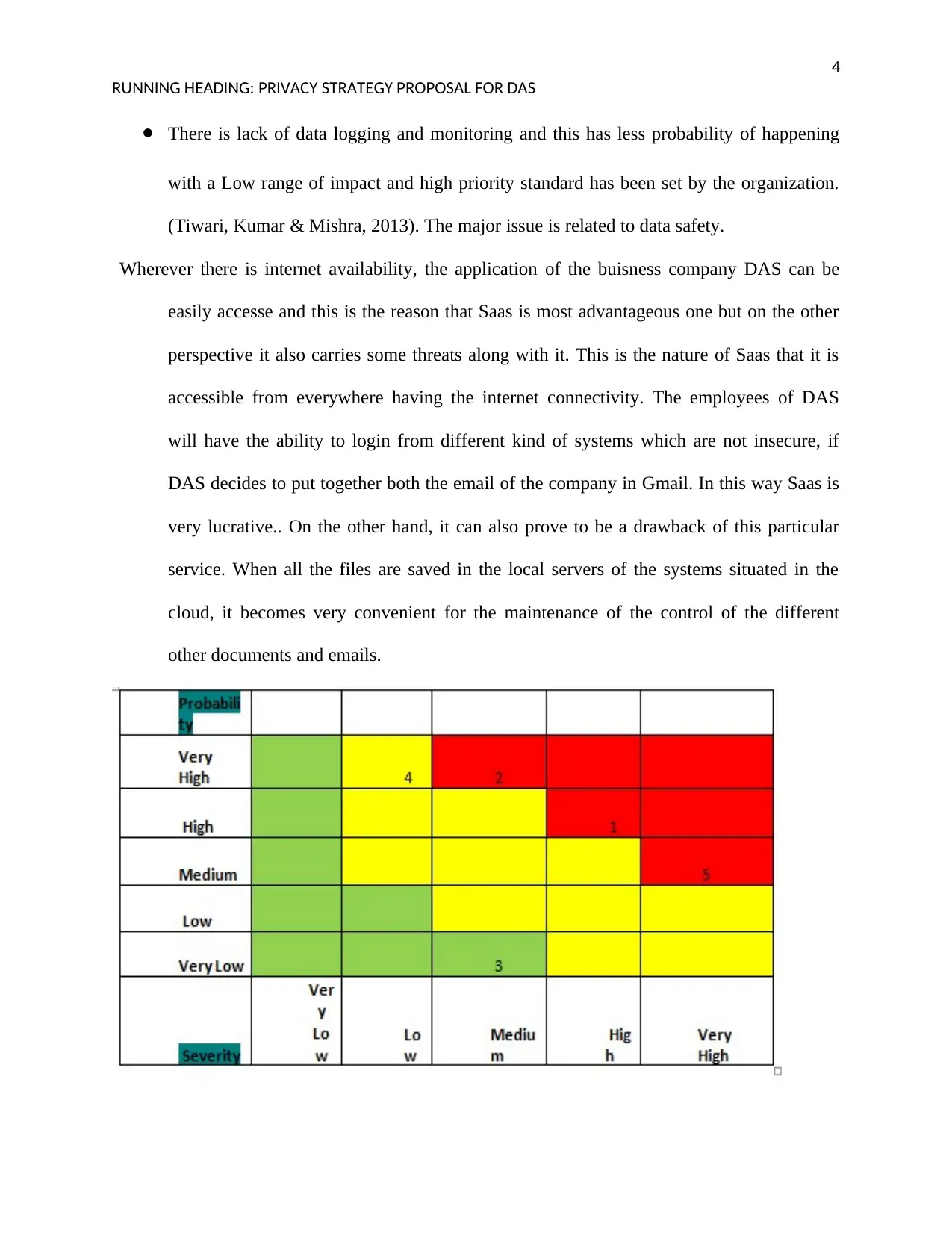
⚫ The Immature identification management has Average likelihood assessed by the
organization or the organization that has applied in the solution in the DAS. The
consequences that has been recorded is high.
⚫ Weak cloud infrastructure can be assessed by the organization that has applied in the
solution in the DAS. The effect that has been recorded is Very High.
⚫ Data security issues is the main problem and has high chances of happening with a Very
High range of impact and high priority standard for the alleviation of the problem.
⚫ The data can be accessed from everywhere so this is the main threat of very high
probability of happening with a High range of impact and high priority standard.
⚫ Data can be located from unknown location and this has very high probability of
happening with a High range of impact and high priority standard has been designed by
the organization.
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
designed by a third party who develops and facilitate the software applications which the
users can access in a form of online web browser page. But there are a number of security
risks associated by the use of SAAS in HR management, which cannot be neglected and
are of crucial importance.
2. The security threats confronted by DAS using SAAS for HR management
The assurance of security of an organization determine the overall strength of cyber
security characteristics of the organization. The security structure of DAS is effected by
the use of SAAS technology for the cloud first technology. The security of Das is
affected in the following ways which includes:
⚫ The Immature identification management has Average likelihood assessed by the
organization or the organization that has applied in the solution in the DAS. The
consequences that has been recorded is high.
⚫ Weak cloud infrastructure can be assessed by the organization that has applied in the
solution in the DAS. The effect that has been recorded is Very High.
⚫ Data security issues is the main problem and has high chances of happening with a Very
High range of impact and high priority standard for the alleviation of the problem.
⚫ The data can be accessed from everywhere so this is the main threat of very high
probability of happening with a High range of impact and high priority standard.
⚫ Data can be located from unknown location and this has very high probability of
happening with a High range of impact and high priority standard has been designed by
the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
⚫ There is lack of data logging and monitoring and this has less probability of happening
with a Low range of impact and high priority standard has been set by the organization.
(Tiwari, Kumar & Mishra, 2013). The major issue is related to data safety.
Wherever there is internet availability, the application of the buisness company DAS can be
easily accesse and this is the reason that Saas is most advantageous one but on the other
perspective it also carries some threats along with it. This is the nature of Saas that it is
accessible from everywhere having the internet connectivity. The employees of DAS
will have the ability to login from different kind of systems which are not insecure, if
DAS decides to put together both the email of the company in Gmail. In this way Saas is
very lucrative.. On the other hand, it can also prove to be a drawback of this particular
service. When all the files are saved in the local servers of the systems situated in the
cloud, it becomes very convenient for the maintenance of the control of the different
other documents and emails.
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
⚫ There is lack of data logging and monitoring and this has less probability of happening
with a Low range of impact and high priority standard has been set by the organization.
(Tiwari, Kumar & Mishra, 2013). The major issue is related to data safety.
Wherever there is internet availability, the application of the buisness company DAS can be
easily accesse and this is the reason that Saas is most advantageous one but on the other
perspective it also carries some threats along with it. This is the nature of Saas that it is
accessible from everywhere having the internet connectivity. The employees of DAS
will have the ability to login from different kind of systems which are not insecure, if
DAS decides to put together both the email of the company in Gmail. In this way Saas is
very lucrative.. On the other hand, it can also prove to be a drawback of this particular
service. When all the files are saved in the local servers of the systems situated in the
cloud, it becomes very convenient for the maintenance of the control of the different
other documents and emails.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
3. Development of a privacy strategy proposal for DAS
For the sake of conduct their business activities, collection Overview Agencies require an
individual to provide a specific range of personal information about themselves in
Agencies need to secure that clients are aware that their personal information
needs to be assemble, why it need to be assemble where the data is stored and who
has access to it.
● The agency should check the information periodically that who has tried to access
the information. It should check that either the information being collected is use
for lawful purpose or not being used for a purpose that is directly related to the
agency’s functions or activities. DAS has to adopt this strategy and should check
that staff are operating within the good practice rules and make it ensure that
company directly communicate with client only.
● The staff should have the knowledge of privacy statement and explain to clients
who do not understand the written language in a simple manner. The organization
can utilize the translating and interpreting service National (TIS). If anyone do not
know how to read.
a. Collection of solicited person data
The organization should deal confidentially with the collection of solicited personal
information including sensitive information. There should be a Companion Guide notes that
personal information should only be collected where it is essential for, or directly related to, one
or more of the entity's functions or activities. It should note that information should only
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
3. Development of a privacy strategy proposal for DAS
For the sake of conduct their business activities, collection Overview Agencies require an
individual to provide a specific range of personal information about themselves in
Agencies need to secure that clients are aware that their personal information
needs to be assemble, why it need to be assemble where the data is stored and who
has access to it.
● The agency should check the information periodically that who has tried to access
the information. It should check that either the information being collected is use
for lawful purpose or not being used for a purpose that is directly related to the
agency’s functions or activities. DAS has to adopt this strategy and should check
that staff are operating within the good practice rules and make it ensure that
company directly communicate with client only.
● The staff should have the knowledge of privacy statement and explain to clients
who do not understand the written language in a simple manner. The organization
can utilize the translating and interpreting service National (TIS). If anyone do not
know how to read.
a. Collection of solicited person data
The organization should deal confidentially with the collection of solicited personal
information including sensitive information. There should be a Companion Guide notes that
personal information should only be collected where it is essential for, or directly related to, one
or more of the entity's functions or activities. It should note that information should only

6
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
provide when a review of current legislation may be required to ensure that, where
needed. (commision, 2008)
In case of emergency situations, where an individual is unable to give agreement, the use of
disclosure of personal information should only in the situations where the Prime Minister or a
minister has declared an emergency or disaster. Or it should only be possible to disclose the data
when there is threat of life and the individual is unable to give consent.
b. Use and disclosure of personal information
There are some key elements of consent which are as following. If the individual is adequately
knowledgeable before giving agreement and the person gives consent voluntarily. It can also be
possible if the person is capable to understand and communicate his consent.
c. Use and security of Digital identity
The digital identity expose the activity of a user on internet and connections to associates; user
intentions; revelations, and admissions. The unknown person can be found through internet due
to this digital identity. It has now become a part of life in many countries and the norm as the
government has digitalize services and transactions. Due to it a person is able to operate in this
new virtual world. This is also defined by the attractive nature of the identity material required
for transactions and its unique link with an individual. These two significant features are a result
practical and legal issues for that individual when identity is not correctly recognized by the
system or when it allows the identity to be misused by a person. With the discovery of cloud
computing there may not be a transmission of data across a border but there can be expose. For
this DAS should adopt the Australian approach which is a preferable model. It provides much
security to the information of a person in the contemporary scenario which is identified by the
growing importance of digital identity and the rampant use of cloud computing. DAS should
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
provide when a review of current legislation may be required to ensure that, where
needed. (commision, 2008)
In case of emergency situations, where an individual is unable to give agreement, the use of
disclosure of personal information should only in the situations where the Prime Minister or a
minister has declared an emergency or disaster. Or it should only be possible to disclose the data
when there is threat of life and the individual is unable to give consent.
b. Use and disclosure of personal information
There are some key elements of consent which are as following. If the individual is adequately
knowledgeable before giving agreement and the person gives consent voluntarily. It can also be
possible if the person is capable to understand and communicate his consent.
c. Use and security of Digital identity
The digital identity expose the activity of a user on internet and connections to associates; user
intentions; revelations, and admissions. The unknown person can be found through internet due
to this digital identity. It has now become a part of life in many countries and the norm as the
government has digitalize services and transactions. Due to it a person is able to operate in this
new virtual world. This is also defined by the attractive nature of the identity material required
for transactions and its unique link with an individual. These two significant features are a result
practical and legal issues for that individual when identity is not correctly recognized by the
system or when it allows the identity to be misused by a person. With the discovery of cloud
computing there may not be a transmission of data across a border but there can be expose. For
this DAS should adopt the Australian approach which is a preferable model. It provides much
security to the information of a person in the contemporary scenario which is identified by the
growing importance of digital identity and the rampant use of cloud computing. DAS should
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
ensure the inculcation of that technology, which determines that the information is leaked by
somebody. The level of specificity is required to tell the individuals of their rights about the
handling of data. The awareness of rights and responsibilities is imperative than ever, at the
instant when the ability of transaction of a person is dependent on the performance and integrity
of digital identity.
c. Quality and correction of personal information
This a basic requirement to check the accuracy of the information like birth sex and gender do
not change, but age change annually. So it should be updated according to date of birth of an
individual. There should be an automated systed incorporated in DAS, which update the age of
an individual every year. Address of an individual can also be changed, the staff or the resource
person has this responsibility to call the individual person that if they want to do any update then
it should performed by their presence. Like address, partner etc. It is also necessary to take
significant steps to ensure the accuracy of information and the organization should prepare a
document with his signature in the case of information update, so that the quality of data could
be insured.
d. .Personal data protection strategy
For the protection of personal data, it is essential to adopt the following strategies, which
is mention below.
I. Official standards: There should be an official written document of data protection. It
should be free of ambiguity and well-documented with corrected procedures to deal with
security flaws, if it originates.
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
ensure the inculcation of that technology, which determines that the information is leaked by
somebody. The level of specificity is required to tell the individuals of their rights about the
handling of data. The awareness of rights and responsibilities is imperative than ever, at the
instant when the ability of transaction of a person is dependent on the performance and integrity
of digital identity.
c. Quality and correction of personal information
This a basic requirement to check the accuracy of the information like birth sex and gender do
not change, but age change annually. So it should be updated according to date of birth of an
individual. There should be an automated systed incorporated in DAS, which update the age of
an individual every year. Address of an individual can also be changed, the staff or the resource
person has this responsibility to call the individual person that if they want to do any update then
it should performed by their presence. Like address, partner etc. It is also necessary to take
significant steps to ensure the accuracy of information and the organization should prepare a
document with his signature in the case of information update, so that the quality of data could
be insured.
d. .Personal data protection strategy
For the protection of personal data, it is essential to adopt the following strategies, which
is mention below.
I. Official standards: There should be an official written document of data protection. It
should be free of ambiguity and well-documented with corrected procedures to deal with
security flaws, if it originates.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
II. Training of employ: Actually, most of the security issue are due to user mistakes.
The network admins of the organization should be well trained in proper data
maintenance standards, and the workforce of organization should be trained to handle the
non-public information.
III. Strict Security measures: It is the responsibility of organization that no one should
have access to confidential data. There should specific installation in the system, that
block the access of any unauthorized user.
IV. Frequent monitoring and reporting: There should be daily testing of Security
policies and there should be verification of its efficiency. The frequent and efficient
reporting will help the organization to detect any unauthorized activity.
V. Backup of data: When the file is moved to a secure server site for backup, then data
is stored in a reliable source then if any there is any danger of threat, then it is completely
secured. (https://www.abcservices.com/5-best-practices-for-your-data-protection-
strategy/)
4. Personal Data Protection and Privacy Policy
When an individual is visited any website then the information of that individualism is kept
confidential through a confidential agreement by website. The individual hereby accept the
condition which is in the Confidential Agreement and when he visits this website and request.
The information of a customer is kept confidential by the website and is not shared to third party
due to data confidential policy. The protection of Personal data is the essential policy of website.
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
II. Training of employ: Actually, most of the security issue are due to user mistakes.
The network admins of the organization should be well trained in proper data
maintenance standards, and the workforce of organization should be trained to handle the
non-public information.
III. Strict Security measures: It is the responsibility of organization that no one should
have access to confidential data. There should specific installation in the system, that
block the access of any unauthorized user.
IV. Frequent monitoring and reporting: There should be daily testing of Security
policies and there should be verification of its efficiency. The frequent and efficient
reporting will help the organization to detect any unauthorized activity.
V. Backup of data: When the file is moved to a secure server site for backup, then data
is stored in a reliable source then if any there is any danger of threat, then it is completely
secured. (https://www.abcservices.com/5-best-practices-for-your-data-protection-
strategy/)
4. Personal Data Protection and Privacy Policy
When an individual is visited any website then the information of that individualism is kept
confidential through a confidential agreement by website. The individual hereby accept the
condition which is in the Confidential Agreement and when he visits this website and request.
The information of a customer is kept confidential by the website and is not shared to third party
due to data confidential policy. The protection of Personal data is the essential policy of website.

9
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
An organization undertake to adhere to all responsibilities of Privacy Act. The main principle of
an organization is to protect personal data. DAS should determine the data of a customer
according to the purpose. Then important data should be transferred to the data storage system of
the company. There should only be storage of necessary data, unnecessary information should be
deleted. The data of health, education, designation of an individual should save in the concerned
department, so that it is easy to withdraw as per need.
ll. Deletion of personal Data
When the maintenance period is expire and there is no requirement of data then it is deleted
automatically by the company or the request of the relevant person so that it cannot be misused
by any third party.
III. Confidentiality and data security
Personal data of any individual are confidential obeys the rule of confidentiality. They are
accessed by only authorized persons. The technical and administrative preventive measure is
only taken for the sake of an individual to prevent himself from any sort of data breeching. It has
the identity information like contact number, Sur name, financial information and date of birth.
Customer reviews are also taken in order to improve the service of the organization and website.
In the application of membership of any website, the information regarding the important things
is taken and it is deleted when any individual leave a membership. If a customer has contractual
relationship with a organization then data is used without the approval of the customers. But this
cannot be misuse, it is only for beneficial purpose. If the contractual relationship is ended then
this data is deleted due to the risk of breeching by any third party.
(https://www.voyagehotel.com/kvkk-en)
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
An organization undertake to adhere to all responsibilities of Privacy Act. The main principle of
an organization is to protect personal data. DAS should determine the data of a customer
according to the purpose. Then important data should be transferred to the data storage system of
the company. There should only be storage of necessary data, unnecessary information should be
deleted. The data of health, education, designation of an individual should save in the concerned
department, so that it is easy to withdraw as per need.
ll. Deletion of personal Data
When the maintenance period is expire and there is no requirement of data then it is deleted
automatically by the company or the request of the relevant person so that it cannot be misused
by any third party.
III. Confidentiality and data security
Personal data of any individual are confidential obeys the rule of confidentiality. They are
accessed by only authorized persons. The technical and administrative preventive measure is
only taken for the sake of an individual to prevent himself from any sort of data breeching. It has
the identity information like contact number, Sur name, financial information and date of birth.
Customer reviews are also taken in order to improve the service of the organization and website.
In the application of membership of any website, the information regarding the important things
is taken and it is deleted when any individual leave a membership. If a customer has contractual
relationship with a organization then data is used without the approval of the customers. But this
cannot be misuse, it is only for beneficial purpose. If the contractual relationship is ended then
this data is deleted due to the risk of breeching by any third party.
(https://www.voyagehotel.com/kvkk-en)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
5.Recommended privacy control for Personal data protection strategy
There are some recommended personal data protection strategies which are as following.
⮚ Data mapping is a significant step for compliance, the purpose of which is to understand
that how data transfer in the organization. The flow of information in the company is by
making an inventory.
⮚ Review and upgrading of private policy is the first step that customer will check for
compliance. In addition of all these, the website and organization should provide
sufficient information to the people in simple language.
⮚ To make your website better it is essential fot an individual to check the website of
opponent party. So that to keep an eye on the performance of others, to make your
website better.
⮚ The relevant persons of the organization should must report the breeching of data to the
supervisor authority within 72 hours unless the personal information is encrypted. The
organization should be smart in setting up the data breech matrix.
⮚ Privacy is a continuous phenomenon to make sure the safety of data with an appropriate
scope. The company should review its procedure that it collect the data of right person. It
means the data of the relevant individual is deleted, not the data of irrelevant person.
⮚ The Data Protection Impact Assessments (DPIAs) is necessary for organizations which
are involved in high risk, such as inclusion of new technology.
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
5.Recommended privacy control for Personal data protection strategy
There are some recommended personal data protection strategies which are as following.
⮚ Data mapping is a significant step for compliance, the purpose of which is to understand
that how data transfer in the organization. The flow of information in the company is by
making an inventory.
⮚ Review and upgrading of private policy is the first step that customer will check for
compliance. In addition of all these, the website and organization should provide
sufficient information to the people in simple language.
⮚ To make your website better it is essential fot an individual to check the website of
opponent party. So that to keep an eye on the performance of others, to make your
website better.
⮚ The relevant persons of the organization should must report the breeching of data to the
supervisor authority within 72 hours unless the personal information is encrypted. The
organization should be smart in setting up the data breech matrix.
⮚ Privacy is a continuous phenomenon to make sure the safety of data with an appropriate
scope. The company should review its procedure that it collect the data of right person. It
means the data of the relevant individual is deleted, not the data of irrelevant person.
⮚ The Data Protection Impact Assessments (DPIAs) is necessary for organizations which
are involved in high risk, such as inclusion of new technology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
⮚ If there is restriction in your organization and website that is could not access by the
children under the age of 16, then you should ensure that you have appropriate system
installed into your website. The purpose of this system is to verify the age of individuals.
6. Recommended personal data protection control
It is necessary for the technical staff and for data protection experts that they should be updated
with technological development and the software’s belonging to data implementation
protection requirement. They should be aware of new data design and privacy enhanced
technologies for better protection. Modules and functions for re-use should be selected so
that they do not bother to perform processing operations. For example it should be
ensured by the access control that data can be read, modify and delete by only the
authorized persons. These control are best in term of security perspective to achieve
confidentiality and integrity. When data is processed by It system then it should be make
assured by the built-in controls, that a user can only access the specific data to perform
his duties and the data should only be accessed by the authorized person. Thus access
control is helpful to ensure that the use of personal data is limited to authorized purposes
(purpose limitation) and data is protected by a third party. From market, standard
software can be acquired, and it should keep in mind the life cycle of standard software.
For the selection of a software the requirements should be keep in mind, in this way it
will be easy to choose the specific software for specific purpose. So there should be
proper planning about the selection of software. The software should be customized in
accordance of the requirement and obligation of the institution. For the installation of
software there is a need of an effective version control and license. The rules and
procedures should be reviewed daily, so that there is no any risk of error. The three line
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
⮚ If there is restriction in your organization and website that is could not access by the
children under the age of 16, then you should ensure that you have appropriate system
installed into your website. The purpose of this system is to verify the age of individuals.
6. Recommended personal data protection control
It is necessary for the technical staff and for data protection experts that they should be updated
with technological development and the software’s belonging to data implementation
protection requirement. They should be aware of new data design and privacy enhanced
technologies for better protection. Modules and functions for re-use should be selected so
that they do not bother to perform processing operations. For example it should be
ensured by the access control that data can be read, modify and delete by only the
authorized persons. These control are best in term of security perspective to achieve
confidentiality and integrity. When data is processed by It system then it should be make
assured by the built-in controls, that a user can only access the specific data to perform
his duties and the data should only be accessed by the authorized person. Thus access
control is helpful to ensure that the use of personal data is limited to authorized purposes
(purpose limitation) and data is protected by a third party. From market, standard
software can be acquired, and it should keep in mind the life cycle of standard software.
For the selection of a software the requirements should be keep in mind, in this way it
will be easy to choose the specific software for specific purpose. So there should be
proper planning about the selection of software. The software should be customized in
accordance of the requirement and obligation of the institution. For the installation of
software there is a need of an effective version control and license. The rules and
procedures should be reviewed daily, so that there is no any risk of error. The three line

12
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
model is a good practice to improve the effectiveness of an organization. And is
internationally recognized. And it is known as the three lines of defense 52. This model
can also work as a reference for the protection of data and is helpful to establish good
governance structure and enhance the accountability of an organization. Thus
organization should adopt this type of model for the protection of data of all of its stake
holders. The senior management should also involve in the protection of data and it is
their responsibility that they design effective policy of data protection. To check the
reliability of the implemented measure and to demonstrate compliance with data
protection rule, the operational management set proper processes, roles, and
responsibilities of the members. Their duty is to set the control activities in the relevant
processes. All these elements are related and link to an internal control system of the
organization. Internal control system has a very important role. It helps the institution to
achieve the desired outcomes. It also comprises of policies, procedures and technical and
organizational protection. The protection of data influence assessments, codes of conduct
and security and privacy certification. When there is establishment of an internal audit
work plan, it is suggested to ensure that the planning also covers processes and functions
in the institution which is related to the protection and processing of personal data. These
type of audits ensure the effectiveness of the system and mitigate the risk of violating the
rules of data protection. (eurpeon data protection supervisor, 2018)
RUNNING HEADING: PRIVACY STRATEGY PROPOSAL FOR DAS
model is a good practice to improve the effectiveness of an organization. And is
internationally recognized. And it is known as the three lines of defense 52. This model
can also work as a reference for the protection of data and is helpful to establish good
governance structure and enhance the accountability of an organization. Thus
organization should adopt this type of model for the protection of data of all of its stake
holders. The senior management should also involve in the protection of data and it is
their responsibility that they design effective policy of data protection. To check the
reliability of the implemented measure and to demonstrate compliance with data
protection rule, the operational management set proper processes, roles, and
responsibilities of the members. Their duty is to set the control activities in the relevant
processes. All these elements are related and link to an internal control system of the
organization. Internal control system has a very important role. It helps the institution to
achieve the desired outcomes. It also comprises of policies, procedures and technical and
organizational protection. The protection of data influence assessments, codes of conduct
and security and privacy certification. When there is establishment of an internal audit
work plan, it is suggested to ensure that the planning also covers processes and functions
in the institution which is related to the protection and processing of personal data. These
type of audits ensure the effectiveness of the system and mitigate the risk of violating the
rules of data protection. (eurpeon data protection supervisor, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





