Ethical Dilemma Analysis: Privacy Tipping Point in 2016, CSU
VerifiedAdded on 2021/06/15
|7
|2314
|24
Homework Assignment
AI Summary
This assignment from Charles Sturt University analyzes the ethical implications of the 2016 "Privacy will hit tipping point" case study. It applies four ethical theories: utilitarianism, deontology, virtue theory, and contract theory, to dissect the ethical dilemmas presented. The analysis examines how each theory views the actions of companies like Google and Apple in addressing privacy concerns, such as targeted advertising and data protection measures. The paper also delves into the actions of regulatory bodies and the impact of data breach laws. The conclusion emphasizes the importance of proactive strategies like authentication, information leak prevention, and regulatory actions to mitigate privacy risks. The student recommends various strategies, including blocking ads, and utilizing regulatory actions. The assignment concludes by highlighting the need for robust ethical frameworks to address privacy challenges and ensure data security.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Privacy will hit tipping point in 2016
Assignment 3: Applying Ethical Theory
Your Name
Student Number
Privacy will hit tipping point in 2016
Assignment 3: Applying Ethical Theory
Your Name
Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Privacy will hit tipping point in 2016
1. Introduction
Ethical dilemma is mainly referred as one of the situation in which choice is generally
needed to be created between two options but none of the options on which choices are made is
helpful in mitigating the problem associated with the situation in a proper ethical way (Lucas, Van &
Maat, 2016). The paper mainly focusses on the case “Privacy will hit tipping point in 2016” for
discussing the case scenario in context to four ethical theories inclusive of virtue, contract,
deontology as well as utilitarianism.
The paper discuss the ethical dilemma that is related with the case study by utilizing the
four ethical theories. In addition to this, proper recommendations are also provided in this paper
which are very much helpful in resolving the issues as well as challenges that are mainly associated
with ethical dilemma.
2. Utilitarianism Theory
It is stated by Van and Roeser (2013) that Utilitarianism is referred as one of the theory of
ethics that generally assists in enlisting the locus of correct and wrong only on the results of
selection one action or policies over other actions as well as policies. As per the theory of
utilitarianism it is identified that the action that is taken for minimizing the privacy issues are ethical.
It is found that there are number of privacy related concerns as a result of which online privacy will
be useful in getting the tipping point 2016 by prompting number of regulators for properly cracking
down on consumers for more protection (Taylor, 2017).
The businesses are also facing number of privacy issues. In order to resolve the issues as well
as challenges that the business generally faces the business must adopt strategies including paying
for less ads, blocking various types of advertisements, proper regulatory actions against different
privacy violators as this type of actions generally act as incubator for various types of privacy
protections. It is identified that in order to avoid privacy related issues as well as challenges, Google
is proactively testing various types of alternatives in order to monetize the data of the users with the
help of various types of targeted ads and as result the contributor of the company generally pays
$2to $10 per month for getting fewer number of ads when they generally visit the website. Thus, it is
identified that the action that is taken by Google for reducing the privacy issues is considered to be
ethical.
3. Deontology Theory
Deontology is mainly referred as one of the ethical theories that generally helps in
determining the morality that is associated with an action that is further dependent on some of the
specific rules and regulations (Vinnari, Vinnari & Kupsala, 2017). It is found that as the trends which
are generally forecasted by the Forrester is considered to be moral as the tendencies are quite
useful in preserving the privacy by minimizing the impact of various types of issues that are
generally with privacy. Google proactively engages in beta testing that is considered as an alternative
method that helps in monetizing different types of information and data with their help of various
types of targeted ads. It is found that contributors of Goggle generally pays around $2 to $10 so that
they visit less number of ads while browsing.
Your Name
1. Introduction
Ethical dilemma is mainly referred as one of the situation in which choice is generally
needed to be created between two options but none of the options on which choices are made is
helpful in mitigating the problem associated with the situation in a proper ethical way (Lucas, Van &
Maat, 2016). The paper mainly focusses on the case “Privacy will hit tipping point in 2016” for
discussing the case scenario in context to four ethical theories inclusive of virtue, contract,
deontology as well as utilitarianism.
The paper discuss the ethical dilemma that is related with the case study by utilizing the
four ethical theories. In addition to this, proper recommendations are also provided in this paper
which are very much helpful in resolving the issues as well as challenges that are mainly associated
with ethical dilemma.
2. Utilitarianism Theory
It is stated by Van and Roeser (2013) that Utilitarianism is referred as one of the theory of
ethics that generally assists in enlisting the locus of correct and wrong only on the results of
selection one action or policies over other actions as well as policies. As per the theory of
utilitarianism it is identified that the action that is taken for minimizing the privacy issues are ethical.
It is found that there are number of privacy related concerns as a result of which online privacy will
be useful in getting the tipping point 2016 by prompting number of regulators for properly cracking
down on consumers for more protection (Taylor, 2017).
The businesses are also facing number of privacy issues. In order to resolve the issues as well
as challenges that the business generally faces the business must adopt strategies including paying
for less ads, blocking various types of advertisements, proper regulatory actions against different
privacy violators as this type of actions generally act as incubator for various types of privacy
protections. It is identified that in order to avoid privacy related issues as well as challenges, Google
is proactively testing various types of alternatives in order to monetize the data of the users with the
help of various types of targeted ads and as result the contributor of the company generally pays
$2to $10 per month for getting fewer number of ads when they generally visit the website. Thus, it is
identified that the action that is taken by Google for reducing the privacy issues is considered to be
ethical.
3. Deontology Theory
Deontology is mainly referred as one of the ethical theories that generally helps in
determining the morality that is associated with an action that is further dependent on some of the
specific rules and regulations (Vinnari, Vinnari & Kupsala, 2017). It is found that as the trends which
are generally forecasted by the Forrester is considered to be moral as the tendencies are quite
useful in preserving the privacy by minimizing the impact of various types of issues that are
generally with privacy. Google proactively engages in beta testing that is considered as an alternative
method that helps in monetizing different types of information and data with their help of various
types of targeted ads. It is found that contributors of Goggle generally pays around $2 to $10 so that
they visit less number of ads while browsing.
Your Name

Privacy will hit tipping point in 2016
In addition to this, apple latest operating system has a feature through which the users can
be able to block adds, Furthermore the European union generally sets various types of new data
protection acts that helps in making the entire company liable of 5 percent of the entire revenue if
they are generally found violating the security or privacy (Taylor, 2017). This act is found to be very
much advantageous as it generally helps in reducing the issues as well as challenges related with
security by providing by taking proper privacy associated actions.
4. Virtue Theory
Virtue is mainly referred as a method that is mainly advantageous in emphasizing a
character of a specific person as one of the effective key element for ethical thinking rather
focussing on the act or the consequence (Rousseau, 2013). It is identified that as per the theory of
virtue the European Union leads the company Apple to pay an amount of $32.5 million as a refund
for all the customers in order to settle federal trade complainant that is done by the users. The
complainant is mainly done in charge of app purchasing by the kinds without taking consent from
parents.
In addition to this, it is identified that AT&T generally pays amount of around $25 million in
order to settle the investigation around the case of data breaches. The law that is created generally
impacts the organization and helps in maintaining ethics by resolving the privacy as well as security
related challenges within the organization (Taylor, 2017). It is identified that the actions that are
generally taken by the various organization is considered to be ethical and in order to resolve the
privacy related challenges it is necessary to adopt proper ethical actions.
5. Contract Theory
The social contract theory is considered as a philosophical responsibility that is mainly found
to be based on the substantial contract agreement for successfully forming the society in which they
generally live (Kotzin et al., 2016). As per the theory of contract 2 laws are generally signed with the
help of the government of California in the year 2016. It is found that as per the contract theory the
authorities generally want court warranty for accessing the electronic communication that is mainly
associated with data and information that is mainly helpful in preventing the data breach regulation.
It is identified that the action that is generally taken by the California government is very much
helpful in reducing as well as minimizing security as well as privacy related challenges and issues.
Some of the organizations generally take calculated risks by assuming that only customers with
California based IP can only reside in the state however this act is totally wrong as it is very much
difficult to maintain two sets of data management rule due to their expense. It is found that the
likelihood of getting the geography of the customer is wrong.
6. Conclusion
It can be concluded from the entire assignment that there are numerous security related
issues that mainly affects the privacy. It is found that the business organizations that are generally at
risk due to number of attacks as well as regulatory related oversight can be resolved by taking
proper actions. It is found that in order to resolve the problems as well as issues it is very much
important to adopt strategies including blockage of ads, paying for the ads, utilization of various
types of regulatory actions as well as various types of privacy violators. It is identified that in order to
reduce the issues and challenges Google contributors generally pays 2-10 dollar per month so that
they can be bale to see less number of ads while browsing. In addition to this, the Apple also
Your Name
In addition to this, apple latest operating system has a feature through which the users can
be able to block adds, Furthermore the European union generally sets various types of new data
protection acts that helps in making the entire company liable of 5 percent of the entire revenue if
they are generally found violating the security or privacy (Taylor, 2017). This act is found to be very
much advantageous as it generally helps in reducing the issues as well as challenges related with
security by providing by taking proper privacy associated actions.
4. Virtue Theory
Virtue is mainly referred as a method that is mainly advantageous in emphasizing a
character of a specific person as one of the effective key element for ethical thinking rather
focussing on the act or the consequence (Rousseau, 2013). It is identified that as per the theory of
virtue the European Union leads the company Apple to pay an amount of $32.5 million as a refund
for all the customers in order to settle federal trade complainant that is done by the users. The
complainant is mainly done in charge of app purchasing by the kinds without taking consent from
parents.
In addition to this, it is identified that AT&T generally pays amount of around $25 million in
order to settle the investigation around the case of data breaches. The law that is created generally
impacts the organization and helps in maintaining ethics by resolving the privacy as well as security
related challenges within the organization (Taylor, 2017). It is identified that the actions that are
generally taken by the various organization is considered to be ethical and in order to resolve the
privacy related challenges it is necessary to adopt proper ethical actions.
5. Contract Theory
The social contract theory is considered as a philosophical responsibility that is mainly found
to be based on the substantial contract agreement for successfully forming the society in which they
generally live (Kotzin et al., 2016). As per the theory of contract 2 laws are generally signed with the
help of the government of California in the year 2016. It is found that as per the contract theory the
authorities generally want court warranty for accessing the electronic communication that is mainly
associated with data and information that is mainly helpful in preventing the data breach regulation.
It is identified that the action that is generally taken by the California government is very much
helpful in reducing as well as minimizing security as well as privacy related challenges and issues.
Some of the organizations generally take calculated risks by assuming that only customers with
California based IP can only reside in the state however this act is totally wrong as it is very much
difficult to maintain two sets of data management rule due to their expense. It is found that the
likelihood of getting the geography of the customer is wrong.
6. Conclusion
It can be concluded from the entire assignment that there are numerous security related
issues that mainly affects the privacy. It is found that the business organizations that are generally at
risk due to number of attacks as well as regulatory related oversight can be resolved by taking
proper actions. It is found that in order to resolve the problems as well as issues it is very much
important to adopt strategies including blockage of ads, paying for the ads, utilization of various
types of regulatory actions as well as various types of privacy violators. It is identified that in order to
reduce the issues and challenges Google contributors generally pays 2-10 dollar per month so that
they can be bale to see less number of ads while browsing. In addition to this, the Apple also
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Privacy will hit tipping point in 2016
provides the facility of blockage of ads. All this actions that are generally taken by the companies are
helpful in maintaining privacy. In addition to this, number of recommendations that needs to be
followed in order to resolve privacy related issues as well as challenges.
Authentication: Proper password cracking related technology generally creates number of
security related challenges and therefore in order to resolve the problem, it is very much necessary
to utilize proper method of authentication in order to secure both data and information.
Plugging from information leaks: It is found that sensitive information generally flows from
the organization with the help of instant messaging as well as email and therefore proper security
policies must be used in order to restrict the leakage of various types of information.
7.
Your Name
provides the facility of blockage of ads. All this actions that are generally taken by the companies are
helpful in maintaining privacy. In addition to this, number of recommendations that needs to be
followed in order to resolve privacy related issues as well as challenges.
Authentication: Proper password cracking related technology generally creates number of
security related challenges and therefore in order to resolve the problem, it is very much necessary
to utilize proper method of authentication in order to secure both data and information.
Plugging from information leaks: It is found that sensitive information generally flows from
the organization with the help of instant messaging as well as email and therefore proper security
policies must be used in order to restrict the leakage of various types of information.
7.
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Privacy will hit tipping point in 2016
References
Kotzin, J. J., Spencer, S. P., McCright, S. J., Kumar, D. B. U., Collet, M. A., Mowel, W. K., ... & Harman,
C. C. (2016). The long non-coding RNA Morrbid regulates Bim and short-lived myeloid cell
lifespan. Nature, 537(7619), 239.
Lucas, K., Van Wee, B., & Maat, K. (2016). A method to evaluate equitable accessibility: combining
ethical theories and accessibility-based approaches. Transportation, 43(3), 473-490.
Mansell, S. (2015). Book Review: Rejoinder to Veldman’s review of Capitalism, Corporations and the
Social Contract: A Critique of Stakeholder Theory (Vol. 22, No. 2, pp. 271-275). Sage UK:
London, England: Sage Publications.
Rousseau, J. J. (2013). Ethics and deontology in public administration.
Sacco, D. F., Brown, M., Lustgraaf, C. J., & Hugenberg, K. (2017). The adaptive utility of deontology:
deontological moral decision-making fosters perceptions of trust and
likeability. Evolutionary Psychological Science, 3(2), 125-132.
Taylor, H. (2017). Privacy will hit tipping point next year: Study. CNBC. Retrieved 14 September 2017,
from https://www.cnbc.com/2015/11/09/privacy-will-hit-tipping-point-in-2016.html
Van Wee, B., & Roeser, S. (2013). Ethical theories and the cost–benefit analysis-based ex ante
evaluation of transport policies and plans. Transport reviews, 33(6), 743-760.
Vinnari, M., Vinnari, E., & Kupsala, S. (2017). Sustainability Matrix: Interest Groups and Ethical
Theories as the Basis of Decision-Making. Journal of Agricultural and Environmental
Ethics, 30(3), 349-366.
Your Name
References
Kotzin, J. J., Spencer, S. P., McCright, S. J., Kumar, D. B. U., Collet, M. A., Mowel, W. K., ... & Harman,
C. C. (2016). The long non-coding RNA Morrbid regulates Bim and short-lived myeloid cell
lifespan. Nature, 537(7619), 239.
Lucas, K., Van Wee, B., & Maat, K. (2016). A method to evaluate equitable accessibility: combining
ethical theories and accessibility-based approaches. Transportation, 43(3), 473-490.
Mansell, S. (2015). Book Review: Rejoinder to Veldman’s review of Capitalism, Corporations and the
Social Contract: A Critique of Stakeholder Theory (Vol. 22, No. 2, pp. 271-275). Sage UK:
London, England: Sage Publications.
Rousseau, J. J. (2013). Ethics and deontology in public administration.
Sacco, D. F., Brown, M., Lustgraaf, C. J., & Hugenberg, K. (2017). The adaptive utility of deontology:
deontological moral decision-making fosters perceptions of trust and
likeability. Evolutionary Psychological Science, 3(2), 125-132.
Taylor, H. (2017). Privacy will hit tipping point next year: Study. CNBC. Retrieved 14 September 2017,
from https://www.cnbc.com/2015/11/09/privacy-will-hit-tipping-point-in-2016.html
Van Wee, B., & Roeser, S. (2013). Ethical theories and the cost–benefit analysis-based ex ante
evaluation of transport policies and plans. Transport reviews, 33(6), 743-760.
Vinnari, M., Vinnari, E., & Kupsala, S. (2017). Sustainability Matrix: Interest Groups and Ethical
Theories as the Basis of Decision-Making. Journal of Agricultural and Environmental
Ethics, 30(3), 349-366.
Your Name
Privacy will hit tipping point in 2016
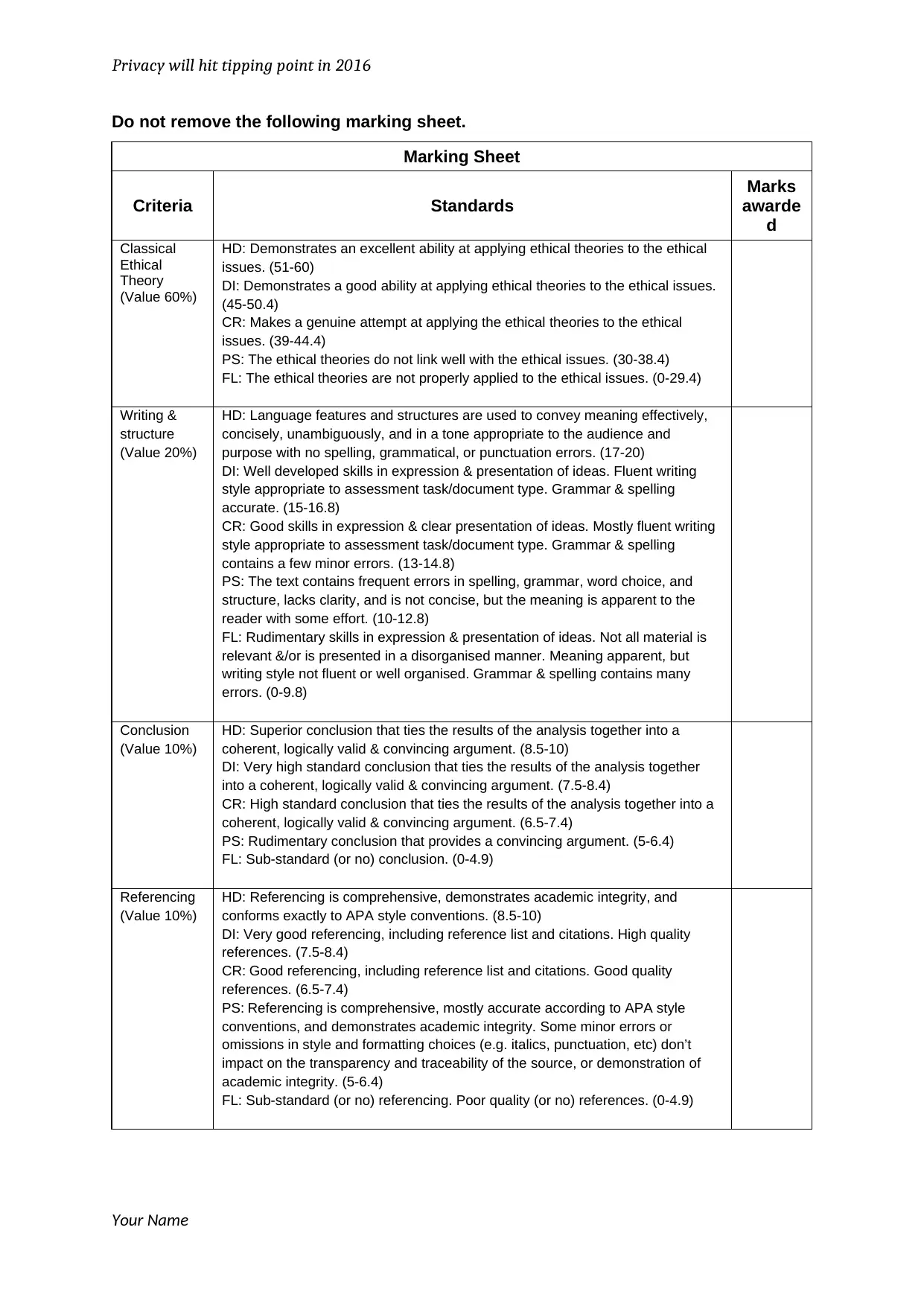
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
awarde
d
Classical
Ethical
Theory
(Value 60%)
HD: Demonstrates an excellent ability at applying ethical theories to the ethical
issues. (51-60)
DI: Demonstrates a good ability at applying ethical theories to the ethical issues.
(45-50.4)
CR: Makes a genuine attempt at applying the ethical theories to the ethical
issues. (39-44.4)
PS: The ethical theories do not link well with the ethical issues. (30-38.4)
FL: The ethical theories are not properly applied to the ethical issues. (0-29.4)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey meaning effectively,
concisely, unambiguously, and in a tone appropriate to the audience and
purpose with no spelling, grammatical, or punctuation errors. (17-20)
DI: Well developed skills in expression & presentation of ideas. Fluent writing
style appropriate to assessment task/document type. Grammar & spelling
accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly fluent writing
style appropriate to assessment task/document type. Grammar & spelling
contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice, and
structure, lacks clarity, and is not concise, but the meaning is apparent to the
reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all material is
relevant &/or is presented in a disorganised manner. Meaning apparent, but
writing style not fluent or well organised. Grammar & spelling contains many
errors. (0-9.8)
Conclusion
(Value 10%)
HD: Superior conclusion that ties the results of the analysis together into a
coherent, logically valid & convincing argument. (8.5-10)
DI: Very high standard conclusion that ties the results of the analysis together
into a coherent, logically valid & convincing argument. (7.5-8.4)
CR: High standard conclusion that ties the results of the analysis together into a
coherent, logically valid & convincing argument. (6.5-7.4)
PS: Rudimentary conclusion that provides a convincing argument. (5-6.4)
FL: Sub-standard (or no) conclusion. (0-4.9)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations. High quality
references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good quality
references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc) don’t
impact on the transparency and traceability of the source, or demonstration of
academic integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references. (0-4.9)
Your Name
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
awarde
d
Classical
Ethical
Theory
(Value 60%)
HD: Demonstrates an excellent ability at applying ethical theories to the ethical
issues. (51-60)
DI: Demonstrates a good ability at applying ethical theories to the ethical issues.
(45-50.4)
CR: Makes a genuine attempt at applying the ethical theories to the ethical
issues. (39-44.4)
PS: The ethical theories do not link well with the ethical issues. (30-38.4)
FL: The ethical theories are not properly applied to the ethical issues. (0-29.4)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey meaning effectively,
concisely, unambiguously, and in a tone appropriate to the audience and
purpose with no spelling, grammatical, or punctuation errors. (17-20)
DI: Well developed skills in expression & presentation of ideas. Fluent writing
style appropriate to assessment task/document type. Grammar & spelling
accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly fluent writing
style appropriate to assessment task/document type. Grammar & spelling
contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice, and
structure, lacks clarity, and is not concise, but the meaning is apparent to the
reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all material is
relevant &/or is presented in a disorganised manner. Meaning apparent, but
writing style not fluent or well organised. Grammar & spelling contains many
errors. (0-9.8)
Conclusion
(Value 10%)
HD: Superior conclusion that ties the results of the analysis together into a
coherent, logically valid & convincing argument. (8.5-10)
DI: Very high standard conclusion that ties the results of the analysis together
into a coherent, logically valid & convincing argument. (7.5-8.4)
CR: High standard conclusion that ties the results of the analysis together into a
coherent, logically valid & convincing argument. (6.5-7.4)
PS: Rudimentary conclusion that provides a convincing argument. (5-6.4)
FL: Sub-standard (or no) conclusion. (0-4.9)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations. High quality
references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good quality
references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc) don’t
impact on the transparency and traceability of the source, or demonstration of
academic integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references. (0-4.9)
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Privacy will hit tipping point in 2016
Total
Marks
Your Name
Total
Marks
Your Name
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





