PRT 574 Assignment 1 S2 2018: Report on Privacy Violation Incidents
VerifiedAdded on 2021/06/16
|6
|2097
|434
Report
AI Summary
This report, submitted as PRT 574 Assignment 1, examines privacy violations and data breaches, focusing on incidents like the 2017 Yahoo data breach and the case of JP Morgan. It explores the causes of privacy violations, including misuse by hackers, loss of assets, phishing, malicious users, and third-party software vulnerabilities. The report provides a detailed analysis of data breaches, presenting examples from various companies such as Adult Friend Finder, eBay, Equifax, and others. It delves into the specific impacts of breaches, such as the exposure of customer data and financial losses. Furthermore, the report suggests preventive measures, including immediate notification of breaches, forming task forces, thorough security testing, and seeking support from local authorities. The conclusion emphasizes the need for continuous auditing and analysis to mitigate the risks of future privacy violations. The report offers a comprehensive overview of data security challenges and potential solutions in the digital age.

PRT 574 Assignment 1 S2 2018
Abstract
Privacy violation is a type of vulnerability, which is related with the misuse of private information. It
might include the credentials of customers, password and SSN. In recent years, we can see there are
number of incidents happened related with privacy violation. In this report we are going to discuss
one of the privacy violation incidence of yahoo. This incidence took place in 2017 and the main cause
of this privacy violation issue was failing in identification of authenticated users and scanning all the
Email accounts illegally for advertisement.
Table of Contents
Abstract.................................................................................................................................................1
Introduction...........................................................................................................................................1
Data breaches........................................................................................................................................1
Causes of privacy violation....................................................................................................................2
Case Study of JP Morgan.......................................................................................................................3
Preventive measures.............................................................................................................................4
References.............................................................................................................................................5
Introduction
The privacy of data and information is legal right for individual in era of digital communication. The
privacy of information has many advantages and it is usually related with the security if personal
data while it is saved in computer systems. The secured information is preferred in almost all the
fields such as the medical records of patients, the financial records of companies, the bank details of
customers, the examination results of students and many more (smith, 2016). The privacy of
information is also called as the privacy of data (HOLLISTER, 2018). In today’s world of big data,
where in every second the huge amount of digital data is generating continuously, the privacy of this
information is the most crucial factor for everybody. It is not possible to save all data in personal
devices as the memory is limited for all the devices, so the concept of cloud is most popular
nowadays. In cloud storage, the data is saved on remote locations thus the security of this data is on
highest priority. In this report we are going to analyse the data breach which was happened in the
year 2017 in J P Morgan. As per the report of financial regulator the JP Morgan chase & co. have to
pay around $2.8 million amount to its customers. The privacy violation was happened in JP Morgan
in year 2017, due to which millions of customers were affected.
The privacy of information can be ensured in many ways such as by using encryption, data masking
and implementing authorization.
Data breaches
Privacy violations are very common in present scenario. According to a survey done by CSO in 2018,
some of the biggest data breaches of present century are (Armerding, 2018):
1
Abstract
Privacy violation is a type of vulnerability, which is related with the misuse of private information. It
might include the credentials of customers, password and SSN. In recent years, we can see there are
number of incidents happened related with privacy violation. In this report we are going to discuss
one of the privacy violation incidence of yahoo. This incidence took place in 2017 and the main cause
of this privacy violation issue was failing in identification of authenticated users and scanning all the
Email accounts illegally for advertisement.
Table of Contents
Abstract.................................................................................................................................................1
Introduction...........................................................................................................................................1
Data breaches........................................................................................................................................1
Causes of privacy violation....................................................................................................................2
Case Study of JP Morgan.......................................................................................................................3
Preventive measures.............................................................................................................................4
References.............................................................................................................................................5
Introduction
The privacy of data and information is legal right for individual in era of digital communication. The
privacy of information has many advantages and it is usually related with the security if personal
data while it is saved in computer systems. The secured information is preferred in almost all the
fields such as the medical records of patients, the financial records of companies, the bank details of
customers, the examination results of students and many more (smith, 2016). The privacy of
information is also called as the privacy of data (HOLLISTER, 2018). In today’s world of big data,
where in every second the huge amount of digital data is generating continuously, the privacy of this
information is the most crucial factor for everybody. It is not possible to save all data in personal
devices as the memory is limited for all the devices, so the concept of cloud is most popular
nowadays. In cloud storage, the data is saved on remote locations thus the security of this data is on
highest priority. In this report we are going to analyse the data breach which was happened in the
year 2017 in J P Morgan. As per the report of financial regulator the JP Morgan chase & co. have to
pay around $2.8 million amount to its customers. The privacy violation was happened in JP Morgan
in year 2017, due to which millions of customers were affected.
The privacy of information can be ensured in many ways such as by using encryption, data masking
and implementing authorization.
Data breaches
Privacy violations are very common in present scenario. According to a survey done by CSO in 2018,
some of the biggest data breaches of present century are (Armerding, 2018):
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PRT 574 Assignment 1 S2 2018
Company Description
Yahoo During September 2016, around 3 billion user accounts of yahoo
were attacked. According to Yahoo the main victims of this privacy
violation were the passwords. In October 2017 it was stated that the
security question and answers were also affected and it was
considered as the biggest data breach in the history (GREEN, 2018).
Adult Friend
Finder
It was happened during October-2016 and around 412.2 million
accounts were affected due to this data breach. Six databases were
hacked by hackers. Due to this around 20 years of user’s data which
included addresses, name, passwords and emails were impacted
(Weinstein, 2016). The main cause of this data breach was the weak
encryption algorithm used in database.
eBay In May 2014, this cyber-attack was happened due to which near
about 145 million users were affected. The private data of users were
exposed because of this attack. It was basically a network attack, in
which hackers entered in the network using personal credentials of
some employees of organization and they accessed the network for
229 days.
Equifax It is the biggest credit bureau in US. On September 7, 2017 due to
one application vulnerability, the security of private data of around
147.9 million customers was compromised.
Heartland
payment
systems
In this privacy violation incidence, around 134 million credit cards of
users were exposed due to SQL injection.
Target stores Due to this data breach the debit and credit card details of 110
million users were affected. The breach was started just before the
thanksgiving note. In this breach, hackers got the accessibility rights
through a third party software named HVAC at the POS and collected
the personal details of plastic money.
TJX Companies
Inc.
In this data breach around 94 million credit cards were affected.
Hackers took the advantage of weak encryption algorithm and
captured the details of credit card during wireless transmission.
Uber In 2016, around 57 million of users and drivers personal information
was affected in this data breach. In personal information there were
no clues of credit and debit card information only the names,
addresses, contact numbers and email ID of users were affected.
JP Morgan
Chase
This is one of the largest bank in the world. Due to data breach
around 76 million households were affected and around 7 million of
small businesses lost their personal information.
US Office
personnel
management
In this data breach, hackers of China were entered in the OPM
system but could not be detected till 2014 March. The information of
users were exposed and later misuse this data.
Causes of privacy violation
2
Company Description
Yahoo During September 2016, around 3 billion user accounts of yahoo
were attacked. According to Yahoo the main victims of this privacy
violation were the passwords. In October 2017 it was stated that the
security question and answers were also affected and it was
considered as the biggest data breach in the history (GREEN, 2018).
Adult Friend
Finder
It was happened during October-2016 and around 412.2 million
accounts were affected due to this data breach. Six databases were
hacked by hackers. Due to this around 20 years of user’s data which
included addresses, name, passwords and emails were impacted
(Weinstein, 2016). The main cause of this data breach was the weak
encryption algorithm used in database.
eBay In May 2014, this cyber-attack was happened due to which near
about 145 million users were affected. The private data of users were
exposed because of this attack. It was basically a network attack, in
which hackers entered in the network using personal credentials of
some employees of organization and they accessed the network for
229 days.
Equifax It is the biggest credit bureau in US. On September 7, 2017 due to
one application vulnerability, the security of private data of around
147.9 million customers was compromised.
Heartland
payment
systems
In this privacy violation incidence, around 134 million credit cards of
users were exposed due to SQL injection.
Target stores Due to this data breach the debit and credit card details of 110
million users were affected. The breach was started just before the
thanksgiving note. In this breach, hackers got the accessibility rights
through a third party software named HVAC at the POS and collected
the personal details of plastic money.
TJX Companies
Inc.
In this data breach around 94 million credit cards were affected.
Hackers took the advantage of weak encryption algorithm and
captured the details of credit card during wireless transmission.
Uber In 2016, around 57 million of users and drivers personal information
was affected in this data breach. In personal information there were
no clues of credit and debit card information only the names,
addresses, contact numbers and email ID of users were affected.
JP Morgan
Chase
This is one of the largest bank in the world. Due to data breach
around 76 million households were affected and around 7 million of
small businesses lost their personal information.
US Office
personnel
management
In this data breach, hackers of China were entered in the OPM
system but could not be detected till 2014 March. The information of
users were exposed and later misuse this data.
Causes of privacy violation
2
PRT 574 Assignment 1 S2 2018
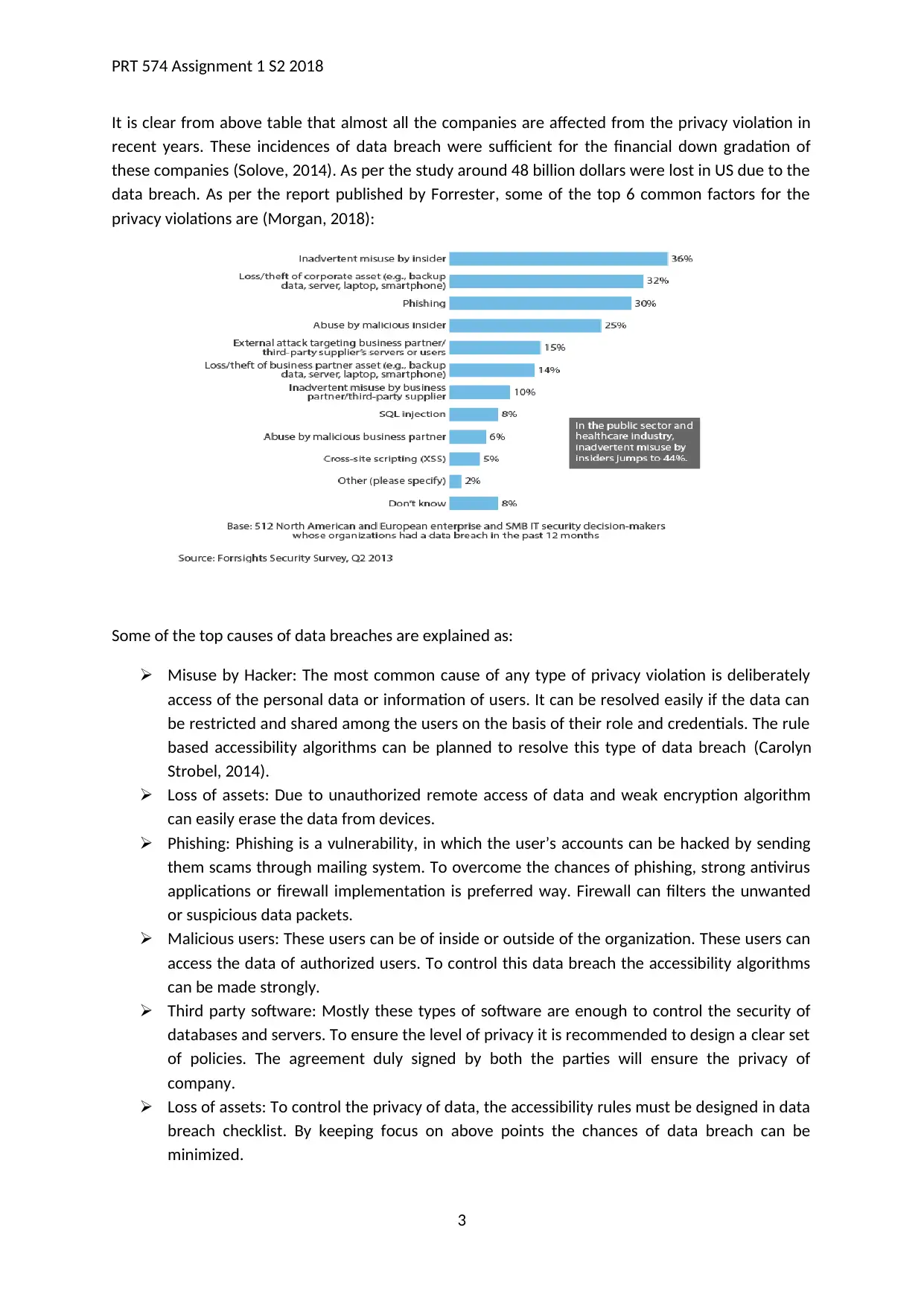
It is clear from above table that almost all the companies are affected from the privacy violation in
recent years. These incidences of data breach were sufficient for the financial down gradation of
these companies (Solove, 2014). As per the study around 48 billion dollars were lost in US due to the
data breach. As per the report published by Forrester, some of the top 6 common factors for the
privacy violations are (Morgan, 2018):
Some of the top causes of data breaches are explained as:
Misuse by Hacker: The most common cause of any type of privacy violation is deliberately
access of the personal data or information of users. It can be resolved easily if the data can
be restricted and shared among the users on the basis of their role and credentials. The rule
based accessibility algorithms can be planned to resolve this type of data breach (Carolyn
Strobel, 2014).
Loss of assets: Due to unauthorized remote access of data and weak encryption algorithm
can easily erase the data from devices.
Phishing: Phishing is a vulnerability, in which the user’s accounts can be hacked by sending
them scams through mailing system. To overcome the chances of phishing, strong antivirus
applications or firewall implementation is preferred way. Firewall can filters the unwanted
or suspicious data packets.
Malicious users: These users can be of inside or outside of the organization. These users can
access the data of authorized users. To control this data breach the accessibility algorithms
can be made strongly.
Third party software: Mostly these types of software are enough to control the security of
databases and servers. To ensure the level of privacy it is recommended to design a clear set
of policies. The agreement duly signed by both the parties will ensure the privacy of
company.
Loss of assets: To control the privacy of data, the accessibility rules must be designed in data
breach checklist. By keeping focus on above points the chances of data breach can be
minimized.
3
It is clear from above table that almost all the companies are affected from the privacy violation in
recent years. These incidences of data breach were sufficient for the financial down gradation of
these companies (Solove, 2014). As per the study around 48 billion dollars were lost in US due to the
data breach. As per the report published by Forrester, some of the top 6 common factors for the
privacy violations are (Morgan, 2018):
Some of the top causes of data breaches are explained as:
Misuse by Hacker: The most common cause of any type of privacy violation is deliberately
access of the personal data or information of users. It can be resolved easily if the data can
be restricted and shared among the users on the basis of their role and credentials. The rule
based accessibility algorithms can be planned to resolve this type of data breach (Carolyn
Strobel, 2014).
Loss of assets: Due to unauthorized remote access of data and weak encryption algorithm
can easily erase the data from devices.
Phishing: Phishing is a vulnerability, in which the user’s accounts can be hacked by sending
them scams through mailing system. To overcome the chances of phishing, strong antivirus
applications or firewall implementation is preferred way. Firewall can filters the unwanted
or suspicious data packets.
Malicious users: These users can be of inside or outside of the organization. These users can
access the data of authorized users. To control this data breach the accessibility algorithms
can be made strongly.
Third party software: Mostly these types of software are enough to control the security of
databases and servers. To ensure the level of privacy it is recommended to design a clear set
of policies. The agreement duly signed by both the parties will ensure the privacy of
company.
Loss of assets: To control the privacy of data, the accessibility rules must be designed in data
breach checklist. By keeping focus on above points the chances of data breach can be
minimized.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PRT 574 Assignment 1 S2 2018
Case Study of JP Morgan
JP Morgan is one of the largest bank in the history of US. It is one of the main victim of privacy
violation in US (CROWE, 2016). At the time of data breach in this bank the US attorney Ms. Preet
Bharara claimed about three people for the biggest theft of data and information of this financial
organization. It is one of the main bank in US having assets of $2.5 trillion. Suddenly news arises that
nearly 76 million of customers and around 7 million small businesses were affected due to the
privacy issues. In this incidence the main effects were seen are (Lin, 2017):
The contact information or personal data of the customers was mainly impacted. It included
the name, contact information, address and email contacts of the customers.
The information of debit and credit card was also accessed by the third party applications.
The hackers entered in the network of bank through unleashed applications and controlled
the network, the infrastructure of bank and accessed huge amount of information.
Preventive measures
Every organization wants the security of data and to ensure this, the companies are advised to
prepare a checklist for the security parameters. As per the experts the following steps must be taken
by CIO’s and CISOs:
Notify the data breach immediately: Whatever is done wrong in the organization, must be reported
on urgent basis. Experts says that the solution of privacy violation must be taken as soon as possible.
As per the RKON technologies, when the database server is recognized for the data breach, the disk
image of this server must be prepared in order to preserve the state of the server. These images
must be read only and password authenticated (Roman, 2016).
Prepare a task force: A team of technical experts must be prepared immediately so that the breach
can be reported to the legal authorities (Brandon, 2017).
Do proper testing of security issues: It is recommended that before disclosing the breach towards
the outside of the organization, the data breach must be completely resolved.
Take support from local authorities: To communicate about the privacy violation with internal and
public departments, a clear and concise report must be prepared along with the solution.
Immediate resolve the problem: It is obvious that the company must mention all the implications
included in the data breach and about the expected related issues of the organization. The remedial
process of data breach is recommended and full-fledged precautions are recommended.
Conclusion
The violation of privacy cannot be completely prevented through any mode of communication, as
there are multiple modes of communication present. But if the companies follow some standard
guidelines, it can be controlled to some extent. Companies are also recommended to generate an
impressive plan to handle the security issues. It is concluded that the causes and solutions will come
4
Case Study of JP Morgan
JP Morgan is one of the largest bank in the history of US. It is one of the main victim of privacy
violation in US (CROWE, 2016). At the time of data breach in this bank the US attorney Ms. Preet
Bharara claimed about three people for the biggest theft of data and information of this financial
organization. It is one of the main bank in US having assets of $2.5 trillion. Suddenly news arises that
nearly 76 million of customers and around 7 million small businesses were affected due to the
privacy issues. In this incidence the main effects were seen are (Lin, 2017):
The contact information or personal data of the customers was mainly impacted. It included
the name, contact information, address and email contacts of the customers.
The information of debit and credit card was also accessed by the third party applications.
The hackers entered in the network of bank through unleashed applications and controlled
the network, the infrastructure of bank and accessed huge amount of information.
Preventive measures
Every organization wants the security of data and to ensure this, the companies are advised to
prepare a checklist for the security parameters. As per the experts the following steps must be taken
by CIO’s and CISOs:
Notify the data breach immediately: Whatever is done wrong in the organization, must be reported
on urgent basis. Experts says that the solution of privacy violation must be taken as soon as possible.
As per the RKON technologies, when the database server is recognized for the data breach, the disk
image of this server must be prepared in order to preserve the state of the server. These images
must be read only and password authenticated (Roman, 2016).
Prepare a task force: A team of technical experts must be prepared immediately so that the breach
can be reported to the legal authorities (Brandon, 2017).
Do proper testing of security issues: It is recommended that before disclosing the breach towards
the outside of the organization, the data breach must be completely resolved.
Take support from local authorities: To communicate about the privacy violation with internal and
public departments, a clear and concise report must be prepared along with the solution.
Immediate resolve the problem: It is obvious that the company must mention all the implications
included in the data breach and about the expected related issues of the organization. The remedial
process of data breach is recommended and full-fledged precautions are recommended.
Conclusion
The violation of privacy cannot be completely prevented through any mode of communication, as
there are multiple modes of communication present. But if the companies follow some standard
guidelines, it can be controlled to some extent. Companies are also recommended to generate an
impressive plan to handle the security issues. It is concluded that the causes and solutions will come
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PRT 574 Assignment 1 S2 2018
together. After taking the remedial steps in data breach, continuous auditing and analysis of security
breaches must be done to reduce the chances of privacy violation.
References
Armerding, T. (2018, January 26). the-biggest-data-breaches-of-the-21st-century.html. Retrieved
from www.csoonline.com: https://www.csoonline.com/article/2130877/data-breach/the-
biggest-data-breaches-of-the-21st-century.html
Brandon, J. (2017, October 7). 5-steps-to-take-when-a-data-breach-hits.html. Retrieved from
www.csoonline.com: https://www.csoonline.com/article/2692565/data-breach/5-steps-to-
take-when-a-data-breach-hits.html
Carolyn Strobel, D. (2014, June 26). top-6-causes-of-data-breach. Retrieved from www.druva.com:
https://www.druva.com/blog/top-6-causes-of-data-breach/
CROWE, P. (2016, November 10). 49739816.cms. Retrieved from www.businessinsider.in:
https://www.businessinsider.in/JPMorgan-is-the-chief-victim-in-the-largest-theft-of-
customer-data-from-a-financial-institution-in-US-history/articleshow/49739816.cms
GREEN, D. (2018, April 3). If-you-shopped-at-these-7-stores-in-the-last-year-your-data-might-have-
been-stolen. Retrieved from www.businessinsider.in: https://www.businessinsider.in/If-you-
shopped-at-these-7-stores-in-the-last-year-your-data-might-have-been-stolen/articleshow/
63601056.cms
HOLLISTER, S. (2018, April 13). yahoo-aol-oath-privacy-policy-verizon-emails-messages. Retrieved
from www.cnet.com: https://www.cnet.com/news/yahoo-aol-oath-privacy-policy-verizon-
emails-messages
Lin, D. (2017, November 10). JPMorgan-is-the-chief-victim-in-the-largest-theft-of-customer-data-
from-a-financial-institution-in-US-history. Retrieved from www.businessinsider.in:
https://www.businessinsider.in/JPMorgan-is-the-chief-victim-in-the-largest-theft-of-
customer-data-from-a-financial-institution-in-US-history/articleshow/49739816.cms
Morgan, L. (2018, May 20). list-of-data-breaches-and-cyber-attacks-in-march-2018. Retrieved from
www.itgovernance.co.uk: https://www.itgovernance.co.uk/blog/list-of-data-breaches-and-
cyber-attacks-in-march-2018/
Roman, J. (2016, September 15). jpmorgan-a-7319. Retrieved from www.bankinfosecurity.com:
https://www.bankinfosecurity.com/jpmorgan-a-7319
smith, R. (2016, February 12). information-privacy. Retrieved from www.techopedia.com:
https://www.techopedia.com/definition/10380/information-privacy
Solove, D. S. (2014, July 2). privacy-data-security-violations-whats-harm. Retrieved from
teachprivacy.com: https://teachprivacy.com/privacy-data-security-violations-whats-harm/
5
together. After taking the remedial steps in data breach, continuous auditing and analysis of security
breaches must be done to reduce the chances of privacy violation.
References
Armerding, T. (2018, January 26). the-biggest-data-breaches-of-the-21st-century.html. Retrieved
from www.csoonline.com: https://www.csoonline.com/article/2130877/data-breach/the-
biggest-data-breaches-of-the-21st-century.html
Brandon, J. (2017, October 7). 5-steps-to-take-when-a-data-breach-hits.html. Retrieved from
www.csoonline.com: https://www.csoonline.com/article/2692565/data-breach/5-steps-to-
take-when-a-data-breach-hits.html
Carolyn Strobel, D. (2014, June 26). top-6-causes-of-data-breach. Retrieved from www.druva.com:
https://www.druva.com/blog/top-6-causes-of-data-breach/
CROWE, P. (2016, November 10). 49739816.cms. Retrieved from www.businessinsider.in:
https://www.businessinsider.in/JPMorgan-is-the-chief-victim-in-the-largest-theft-of-
customer-data-from-a-financial-institution-in-US-history/articleshow/49739816.cms
GREEN, D. (2018, April 3). If-you-shopped-at-these-7-stores-in-the-last-year-your-data-might-have-
been-stolen. Retrieved from www.businessinsider.in: https://www.businessinsider.in/If-you-
shopped-at-these-7-stores-in-the-last-year-your-data-might-have-been-stolen/articleshow/
63601056.cms
HOLLISTER, S. (2018, April 13). yahoo-aol-oath-privacy-policy-verizon-emails-messages. Retrieved
from www.cnet.com: https://www.cnet.com/news/yahoo-aol-oath-privacy-policy-verizon-
emails-messages
Lin, D. (2017, November 10). JPMorgan-is-the-chief-victim-in-the-largest-theft-of-customer-data-
from-a-financial-institution-in-US-history. Retrieved from www.businessinsider.in:
https://www.businessinsider.in/JPMorgan-is-the-chief-victim-in-the-largest-theft-of-
customer-data-from-a-financial-institution-in-US-history/articleshow/49739816.cms
Morgan, L. (2018, May 20). list-of-data-breaches-and-cyber-attacks-in-march-2018. Retrieved from
www.itgovernance.co.uk: https://www.itgovernance.co.uk/blog/list-of-data-breaches-and-
cyber-attacks-in-march-2018/
Roman, J. (2016, September 15). jpmorgan-a-7319. Retrieved from www.bankinfosecurity.com:
https://www.bankinfosecurity.com/jpmorgan-a-7319
smith, R. (2016, February 12). information-privacy. Retrieved from www.techopedia.com:
https://www.techopedia.com/definition/10380/information-privacy
Solove, D. S. (2014, July 2). privacy-data-security-violations-whats-harm. Retrieved from
teachprivacy.com: https://teachprivacy.com/privacy-data-security-violations-whats-harm/
5

PRT 574 Assignment 1 S2 2018
Weinstein, M. (2016, December 18). 13-ways-your-privacy-violated-9479084. Retrieved from
www.mirror.co.uk: https://www.mirror.co.uk/tech/13-ways-your-privacy-violated-9479084
6
Weinstein, M. (2016, December 18). 13-ways-your-privacy-violated-9479084. Retrieved from
www.mirror.co.uk: https://www.mirror.co.uk/tech/13-ways-your-privacy-violated-9479084
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





